Chapter 3
Understanding Cryptography
CISCO CCNA SECURITY EXAM OBJECTIVES COVERED IN THIS CHAPTER:
 1.3 Cryptography concepts
1.3 Cryptography concepts
- Describe key exchange
- Describe hash algorithm
- Compare and contrast symmetric and asymmetric encryption
- Describe digital signatures, certificates, and PKI
 Cryptography is the use of mathematical algorithms to scramble data so it cannot be read if captured. In that role cryptography provides confidentiality, but that is not the only security goal it can achieve. Through the use of hash values and digital signatures, it can also provide assurance of data integrity and origin authentication. This chapter will cover the types of cryptography, their strengths and weaknesses, and some of the services that cryptography can provide.
Cryptography is the use of mathematical algorithms to scramble data so it cannot be read if captured. In that role cryptography provides confidentiality, but that is not the only security goal it can achieve. Through the use of hash values and digital signatures, it can also provide assurance of data integrity and origin authentication. This chapter will cover the types of cryptography, their strengths and weaknesses, and some of the services that cryptography can provide.
In this chapter, you will learn the following:
- Cryptography concepts
Symmetric and Asymmetric Encryption
There are two types of cryptography algorithms that you must understand, symmetric and asymmetric. A bit later in this section you will learn the differences between these two systems and the advantages and disadvantages of both. You’ll also learn when to apply these algorithms to secure both data at rest and data in transit.
But first let’s look at some basic concepts used in cryptography. First you’ll be introduced to some of the various ways algorithms scramble the data. Then you’ll learn about two different ways encryption algorithms operate on the data.
Ciphers
Cryptographic algorithms are often called ciphers for short, and these ciphers are mathematical formulas that move the data around in various ways to scramble it. The two main methods are substitution and transposition. I’ll cover these in this section, along with a method of addressing shortcomings of substitution. Ciphers also differ in the amount of data that is encrypted at a time. The two main types of algorithms with respect to this issue are block and stream ciphers, which will also be covered in this section.
Substitution
A substitution cipher uses a key to substitute characters or character blocks with different characters or character blocks. The Caesar cipher and the Vigenère cipher are two of the earliest forms of substitution ciphers. Figure 3.1 shows the ROT13, which is a Caesar cipher. It rotates the alphabet 13 positions. Therefore, the message “Hello” encrypts to the ciphertext URYYB.

FIGURE 3.1 ROT 13 Caesar cipher
One of the issues with substitution ciphers is if the message is of sufficient length, patterns in the encryption begin to become noticeable, which makes it vulnerable to a frequency attack. A frequency attack is when the attacker uses these recurring patterns to reverse engineer the message. For this reason, the polyalphabetic algorithm was created.
Polyalphabetic
To increase the difficulty of performing a frequency attack, polyalphabetic algorithms were created. They use multiple instances of the alphabet shifted in a 26 × 26 table called a tableau, shown in Figure 3.2 . The figure shows the Vigenère cipher, an example of a polyalphabetic cipher.

FIGURE 3.2 Vigenère cipher
As an example of a message on which the Vigenère cipher is applied, let’s use the security key SYBEX and the plaintext message of WE ATTACK AT FIVE. The first letter in the plaintext message is W, and the first letter in the key is S. We should locate the letter W across the headings for the columns. We follow that column down until it intersects with the row that starts with the letter S, resulting in the letter O. The second letter of the plaintext message is E, and the second letter in the key is Y. Using the same method, we obtain the letter C. We continue in this same manner until we run out of key letters, and then we start over with the key, which would result in the second A in the plaintext message working with the letter S of the key.
So, applying this technique to the entire message of WE ATTACK AT FIVE, the plaintext message converts to the OCBXQSALEQXGWI ciphertext message.
Transposition
A transposition cipher scrambles the letters of the original message in a different order. The key determines the positions to which the letters are moved.
The following is an example of a simple transposition cipher:
Original message SNOWFLAKES WILL FALLBroken into groups SNOW FLAK ESWI FALLKey 4231 2314 4231 2314Ciphertext message WONS LAFK IWSE ALFL
With this example, the original message is SNOWFLAKES WILL FALL, and the key is 4231 2314. The ciphertext message is WONS LAFK IWSE ALFL. So, you take the first four letters of the plaintext message (SNOW) and use the first four numbers (4231) as the key for transposition. The key describes the relative potions of the same characters in the ciphertext. In the new ciphertext, the letters would be WONS. Then you take the next four letters of the plaintext message (FLAK) and use the next four numbers (2314) as the key for transposition. In the new ciphertext, the letters would be LAFK. Then you take the next four letters of the original message and apply the first four numbers of the key because you do not have any more numbers in the key. Continue this pattern until complete.
Algorithms
While cryptographic algorithms can deploy either substitution or transposition, there is another key characteristic that differentiates two main classes of algorithms: symmetric and asymmetric. In the next two sections, I’ll talk about how they are different.
Symmetric
Symmetric algorithms use a private or secret key that must remain secret between the two parties. Each party pair requires a separate private key. Therefore, a single user would need a unique secret key for every user with whom she communicates.
Consider an example where there are 10 unique users. Each user needs a separate private key to communicate with the other users. To calculate the number of keys that would be needed in this example, you would use the following formula:
# of users × (# of users – 1) / 2
Using our example, you would calculate 10 × (10 – 1) / 2, or 45 needed keys.
With symmetric algorithms, the encryption key must remain secure. To obtain the secret key, the users must find a secure out-of-band method for communicating the secret key, including courier or direct physical contact between the users.
A special type of symmetric key called a session key encrypts messages between two users during one communication session. Symmetric algorithms can be referred to as single-key, secret-key, private-key, or shared-key cryptography.
Symmetric systems provide confidentiality but not authentication or nonrepudiation. If both users use the same key, determining where the message originated is impossible. Symmetric algorithms include DES, AES, 3DES, and RC4. Table 3.1 lists the strengths and weaknesses of symmetric algorithms.
TABLE 3.1 Symmetric algorithm strengths and weaknesses
| Strengths | Weaknesses |
| Cheaper to implement than asymmetric | Key compromise can occur more easily than with asymmetric |
| Faster than asymmetric | Difficulty in performing secure key distribution |
| Hard to crack | Key compromise occurs if one party compromised, thereby allowing impersonation |
The two broad types of symmetric algorithms are stream-based ciphers and block ciphers. Initialization vectors (IVs) are an important part of block ciphers. These three components will be discussed in the next sections.
Block
Another way in which ciphers can differ is in the amount of data that is encrypted at a time. Block ciphers perform encryption by breaking the message into fixed-length units. A message of 1,024 bits could be divided into 16 blocks of 64 bits each. Each of those 16 blocks is processed by the algorithm formulas, resulting in a single block of ciphertext.
Advantages of block ciphers include the following:
- The implementation is easier than stream-based cipher implementation.
- They are generally less susceptible to security issues.
- They are generally used more in software implementations.
Block ciphers employ both substitution and transposition.
Stream
Stream-based ciphers perform encryption on a bit-by-bit basis and use keystream generators. The keystream generators create a bit stream that is XORed with the plaintext bits. The result of this XOR operation is the ciphertext.
A synchronous stream-based cipher depends only on the key, and an asynchronous stream cipher depends on the key and plaintext. The key ensures that the bit stream that is XORed to the plaintext is random.
An example of a stream-based cipher is RC4.
Advantages of stream-based ciphers include the following:
- They generally have lower error propagation because encryption occurs on each bit.
- They are generally used more in hardware implementation.
- They use the same key for encryption and decryption.
- They are generally cheaper to implement than block ciphers.
- The employ only substitution.
Initialization Vectors
Some modes of symmetric key algorithms use initialization vectors to ensure that patterns are not produced during encryption. These IVs provide this service by using random values with the algorithms. Without using IVs, a repeated phrase within a plaintext message could result in the same ciphertext. Attackers can possibly use these patterns to break the encryption.
Digital Encryption Standard (DES)
Digital Encryption Standard (DES) uses a 64-bit key, 8 bits of which are used for parity. Therefore, the effective key length for DES is 56 bits. DES divides the message into 64-bit blocks. Sixteen rounds of transposition and substitution are performed on each block, resulting in a 64-bit block of ciphertext.
DES has mostly been replaced by 3DES and AES, both of which are discussed later in this chapter.
3DES
Because of the need to quickly replace DES, Triple DES (3DES), a version of DES that increases security by using three 56-bit keys, was developed. Although 3DES is resistant to attacks, it is up to three times slower than DES. 3DES did serve as a temporary replacement to DES. However, the National Institute of Standards and Technology (NIST) has actually designated the Advanced Encryption Standard (AES) as the replacement for DES, even though 3DES is still in use today.
DES can operate in a number of different modes, but the two most common are Electronic Code Book (ECB) and Cipher Block Chaining (CBC). In ECB, 64-bit blocks of data are processed by the algorithm using the key. The ciphertext produced can be padded to ensure that the result is a 64-bit block. If an encryption error occurs, only one block of the message is affected. ECB operations run in parallel, making it a fast method.
Although ECB is the easiest and fastest mode to use, it has security issues because every 64-bit block is encrypted with the same key. If an attacker discovers the key, all the blocks of data can be read. If an attacker discovers both versions of the 64-bit block (plaintext and ciphertext), the key can be determined. For these reasons, the mode should not be used when encrypting a large amount of data because patterns would emerge. ECB is a good choice if an organization needs encryption for its databases because ECB works well with the encryption of short messages.
Figure 3.3 shows the ECB encryption process.

FIGURE 3.3 ECB process
In CBC, each 64-bit block is chained together because each resultant 64-bit ciphertext block is applied to the next block. So, plaintext message block 1 is processed by the algorithm using an IV. The resultant ciphertext message block 1 is XORed with plaintext message block 2, resulting in ciphertext message 2. This process continues until the message is complete.
Unlike ECB, CBC encrypts large files without having any patterns within the resulting ciphertext. If a unique IV is used with each message encryption, the resultant ciphertext will be different every time even in cases where the same plaintext message is used.
Figure 3.4 shows the CBC encryption process.

FIGURE 3.4 CBC process
Advanced Encryption Standard (AES)
Advanced Encryption Standard (AES) is the replacement algorithm for DES. Although AES is considered the standard, the algorithm that is used in the AES standard is the Rijndael algorithm. The AES and Rijndael terms are often used interchangeably.
The three block sizes that are used in the Rijndael algorithm are 128, 192, and 256 bits. A 128-bit key with a 128-bit block size undergoes 10 transformation rounds. A 192-bit key with a 192-bit block size undergoes 12 transformation rounds. Finally, a 256-bit key with a 256-bit block size undergoes 14 transformation rounds.
Rijndael employs transformations composed of three layers: nonlinear layer, key addition layer, and linear-maxing layer. The Rijndael design is very simple, and its code is compact, which allows it to be used on a variety of platforms. It is the required algorithm for sensitive but unclassified U.S. government data.
RC4
A total of six RC algorithms have been developed by Ron Rivest. RC1 was never published, RC2 was a 64-bit block cipher, and RC3 was broken before release. RC4, also called ARC4, is one of the most popular stream ciphers. It is used in SSL and WEP. RC4 uses a variable key size of 40 to 2,048 bits and up to 256 rounds of transformation.
Asymmetric
Asymmetric algorithms use both a public key and a private or secret key. The public key is known by all parties, and the private key is known only by its owner. One of these keys encrypts the message, and the other decrypts the message.
In asymmetric cryptography, determining a user’s private key is virtually impossible even if the public key is known, although both keys are mathematically related. However, if a user’s private key is discovered, the system can be compromised.
Asymmetric algorithms can be referred to as dual-key or public-key cryptography.
Asymmetric systems provide confidentiality, integrity, authentication, and nonrepudiation. Because both users have one unique key that is part of the process, determining where the message originated is possible.
If confidentiality is the primary concern for an organization, a message should be encrypted with the receiver’s public key, which is referred to as a secure message format. If authentication is the primary concern for an organization, a message should be encrypted with the sender’s private key, which is referred to as an open message format. When using open message format, the message can be decrypted by anyone with the public key.
Perhaps the most widely known and used asymmetric algorithm is RSA. Oher asymmetric algorithms include RSA, El Gamal, DSA, and Elliptic Curve Cryptography (ECC).
RSA
RSA is the most popular asymmetric algorithm and was invented by Ron Rivest, Adi Shamir, and Leonard Adleman. RSA can provide key exchange, encryption, and digital signatures. The strength of the RSA algorithm is the difficulty of finding the prime factors of very large numbers. RSA uses a 1,024- to 4,096-bit key and performs one round of transformation.
As a key exchange protocol, RSA encrypts a DES or AES symmetric key for secure distribution. RSA uses a one-way function to provide encryption/decryption and digital signature verification/generation. The public key works with the one-way function to perform encryption and digital signature verification. The private key works with the one-way function to perform decryption and signature generation. These processes will be covered in detail in the section “Public Key Infrastructure (PKI).”
Hashing Algorithms
A hash function runs data through a cryptographic algorithm to produce a one-way message digest. The size of the message digest is determined by the algorithm used. The message digest represents the data but cannot be reversed in order to determine the original data. Because the message digest is unique, it can be used to check data integrity.
A one-way hash function reduces a message to a hash value. A comparison of the sender’s hash value to the receiver’s hash value determines message integrity. If the resultant hash values are different, then the message has been altered in some way, provided that both the sender and the receiver used the same hash function. Hash functions do not prevent data alteration but provide a means to determine whether data alteration has occurred.
Hash functions do have limitations. If an attacker intercepts a message that contains a hash value, the attacker can alter the original message to create a second invalid message with a new hash value. If the attacker then sends the second invalid message to the intended recipient, the intended recipient will have no way of knowing that he received an incorrect message. When the receiver performs a hash value calculation, the invalid message will look valid because the invalid message was appended with the attacker’s new hash value, not the original message’s hash value. To prevent this from occurring, the sender should use Message Authentication Code (MAC).
Encrypting the hash function with a symmetric key algorithm generates a keyed MAC. The symmetric key does not encrypt the original message. It is used only to protect the hash value. Figure 3.5 shows the basic steps of a hash function.

FIGURE 3.5 Hash process
Two major hash function vulnerabilities can occur: collisions and rainbow table attacks. A collision occurs when a hash function produces the same hash value on different messages. A rainbow table attack occurs when rainbow tables are used to reverse a hash by computing all possible hashes and looking up the matching value.
Because a message digest is determined by the original data, message digests can be used to compare different files to see whether they are identical down to the bit level. If a computed message digest does not match the original message digest value, then data integrity has been compromised.
Password hash values are often stored instead of the actual passwords to ensure that the actual passwords are not compromised.
When choosing which hashing function to use, it is always better to choose the function that uses a larger hash value. To determine the hash value for a file, you should use the hash function. As an example, let’s suppose you have a document named crypto.doc that you need to ensure is not modified in any way. To determine the hash value for the file using the md5 hash function, you would enter the following command:
md5 crypto.doc
This command would result in a hash value that you should record. Later, when users need access to the file, they should always issue the md5 command listed to recalculate the hash value. If the value is the same as the originally recorded value, the file is unchanged. If it is different, then the file has been changed.
MD5
The MD5 algorithm produces a 128-bit hash value. It performs four rounds of computations. It was originally created because of the issues with MD4, and it is more complex than MD4. However, MD5 is not collision free. For this reason, it should not be used for SSL certificates or digital signatures. The U.S. government requires the usage of SHA-2 instead of MD5. However, in commercial usage, many software vendors publish the MD5 hash value when releasing software patches so customers can verify the software’s integrity after download.
SHA-1
SHA-1 produces a 160-bit hash value after performing 80 rounds of computations on 512-bit blocks. SHA-1 corrected the flaw in SHA-0 that made it susceptible to attacks.
SHA-2
SHA-2 is actually a family of hash functions, each of which provides different functional limits. The SHA-2 family is as follows:
- SHA-224: Produces a 224-bit hash value after performing 64 rounds of computations on 512-bit blocks.
- SHA-256: Produces a 256-bit hash value after performing 64 rounds of computations on 512-bit blocks.
- SHA-384: Produces a 384-bit hash value after performing 80 rounds of computations on 1,024-bit blocks.
- SHA-512: Produces a 512-bit hash value after performing 80 rounds of computations on 1,024-bit blocks.
- SHA-512/224: Produces a 224-bit hash value after performing 80 rounds of computations on 1,024-bit blocks. The 512 designation here indicates the internal state size.
- SHA-512/256: Produces a 256-bit hash value after performing 80 rounds of computations on 1,024-bit blocks. Once again, the 512 designation indicates the internal state size.
HMAC
A hash MAC (HMAC) is a keyed-hash Message Authentication Code (MAC) that involves a hash function with symmetric key. HMAC provides data integrity and authentication. Any of the previously listed hash functions can be used with HMAC, with the HMAC name being appended with the hash function name, as in HMAC-SHA-1. The strength of HMAC is dependent upon the strength of the hash function, including the hash value size and the key size.
HMAC’s hash value output size will be the same as the underlying hash function. HMAC can help to reduce the collision rate of the hash function. Figure 3.6 shows the basic steps of an HMAC process.

FIGURE 3.6 HMAC process
Digital Signatures
A digital signature is a hash value encrypted with the sender’s private key. A digital signature provides authentication, nonrepudiation, and integrity. A blind signature is a form of digital signature where the contents of the message are masked before it is signed. Figure 3.7 shows the process.

FIGURE 3.7 Digital signature process
The process for creating a digital signature is as follows:
- The signer obtains a hash value for the data to be signed.
- The signer encrypts the hash value using his private key.
- The signer attaches the encrypted hash and a copy of his public key in a certificate to the data and sends the message to the receiver.
The process for verifying the digital signature is as follows:
- The receiver separates the data, encrypted hash, and certificate.
- The receiver obtains the hash value of the data.
- The receiver verifies that the public key is still valid using the PKI.
- The receiver decrypts the encrypted hash value using the public key.
- The receiver compares the two hash values. If the values are the same, the message has not been changed.
Public key cryptography, which is discussed later in this chapter, is used to create digital signatures. Users register their public keys with a certification authority (CA), which distributes a certificate containing the user’s public key and the CA’s digital signature. The digital signature is computed by the user’s public key and validity period being combined with the certificate issuer and digital signature algorithm identifier.
The Digital Signature Standard (DSS) is a federal digital security standard that governs the Digital Security Algorithm (DSA). DSA generates a message digest of 160 bits. The U.S. federal government requires the use of DSA, RSA, or Elliptic Curve DSA (ECDSA) and SHA for digital signatures.
DSA is slower than RSA and provides only digital signatures. RSA provides digital signatures, encryption, and secure symmetric key distribution.
Key Exchange
As you have learned, symmetric key algorithms are significantly more efficient at encrypting and decrypting data than are asymmetric algorithms. However, the best way to illustrate the hybrid cryptosystem is to explore the function of SSH.
Application: SSH
Secure Shell (SSH) is an application and protocol that is used to remotely log in to another computer using a secure tunnel. After a session key is exchanged and a secure channel is established, all communication between the two computers is encrypted over the secure channel. SSH is a solution that could be used to remotely access devices, including switches, routers, and servers.
SSH offers a good illustration of the use of asymmetric algorithms to generate and exchange a symmetric key and thereafter to use that key for data encryption. The steps are as follows:
- The client connects to the server, and the server presents its public key to the client.
- The client and server negotiate a group of settings that must match on both ends. It includes the symmetric algorithm they will use.
- The client creates a random session key and encrypts it with the server’s public key.
- The client sends this encrypted session key to the server, and the server decrypts it using its private key.
Using the symmetric key, which they both now possess, the two start encrypting everything that goes on from this point, including the authentication process.
Public Key Infrastructure
A public key infrastructure (PKI) includes systems, software, and communication protocols that distribute, manage, and control public key cryptography. A PKI publishes digital certificates. Because a PKI establishes trust within an environment, a PKI can certify that a public key is tied to an entity and verify that a public key is valid. Public keys are published through digital certificates.
The X.509 standard is a framework that enables authentication between networks and over the Internet. A PKI includes timestamping and certificate revocation to ensure that certificates are managed properly. A PKI provides confidentiality, message integrity, authentication, and nonrepudiation.
The structure of a PKI includes CAs, certificates, registration authorities, certificate revocation lists, and cross-certification. This section discusses these PKI components as well as a few other PKI concepts.
Public and Private Keys
In public key cryptography, two keys are used, a public key and a private key. These two keys are not the same, but they are mathematically related in such a way that if you encrypt data with one of them, you can decrypt it with the other. Users and devices are issued public/private key pairs that are bound to a digital document called a digital certificate. This certificate (more specifically the keys to which it is bound) can be used for a variety of things including the following:
- Encrypting data
- As a form of authentication
- Encrypting email
- Digitally signing software
Private Key
The private key that is generated as part of the key pair is made available only to the user or device to which it was issued. This key may be stored on software in the user’s computer, or it might be stored on a smart card if it is to be used for authentication. At any rate, the key concept here is that it is available only to the user or device to which it was issued.
Public Key
The public key that is generated as part of the key pair is made available to anyone to whom the certificate is presented because it is part of the information contained in this digital document. In some cases, public keys may be kept in a repository so they can be requested by an entity if required. Regardless of the method used to obtain the public key, the key concept here is that it is available to anyone.
Putting It Together
These keys work together to perform both encryption and digital signatures. To provide encryption, the data is encrypted with the receiver’s public key, which results in ciphertext that only the receiver’s private key can decrypt. Figure 3.8 shows this process.

FIGURE 3.8 PKI encryption
To digitally sign a document, the sender creates what is called a hash value of the data being sent, encrypts that value with the sender’s his private key, and sends this value along with the message. The receiver decrypts the hash using the sender’s public key. The receiver then, using the same hashing algorithm, hashes the message. The sender then compares the decrypted hash value to the one just generated. If they are the same, the signature (and the integrity of the data) has been verified. Figure 3.9 shows this process.

FIGURE 3.9 PKI digital signature
Certificates
A digital certificate provides an entity, usually a user, with the credentials to prove its identity and associates that identity with a public key. At minimum, a digital certification must provide the serial number, the issuer, the subject (owner), and the public key.
An X.509 certificate complies with the X.509 standard. An X.509 certificate contains the following fields:
- Version
- Serial Number
- Algorithm ID
- Issuer
- Validity
- Subject
- Subject Public Key Info
- Public Key Algorithm
- Subject Public Key
- Issuer Unique Identifier (optional)
- Subject Unique Identifier (optional)
- Extensions (optional)
Revocation
Certificates have a defined lifetime. When the validity period ends, the certificate must be renewed to continue to be valid. There are cases when a certificate must be revoked before its lifetime ends. Reasons for certificate revocation include the following:
- Compromise of the associated keys
- Improper issuance
- Compromise of the issuing CA
- Owner of the certificate no longer owning the domain for which it was issued
- Owner of the certificate ceasing operations entirely
- Original certificate being replaced with a different certificate from a different issuer
A certificate revocation list (CRL) is a list of digital certificates that a CA has revoked. To find out whether a digital certificate has been revoked, either the browser must check the CRL or the CA must push out the CRL values to clients. This can become quite daunting when you consider that the CRL contains every certificate that has ever been revoked.
One concept to keep in mind is the revocation request grace period. This period is the maximum amount of time between when the revocation request is received by the CA and when the revocation actually occurs. A shorter revocation period provides better security but often results in a higher implementation cost.
Uses
Certificates can be used for variety of operations. This can include authentication, encryption, digital signatures, and email to name a few. VeriSign first introduced the following digital certificate classes:
- Class 1: For individuals intended for email. These certificates get saved by web browsers.
- Class 2: For organizations that must provide proof of identity.
- Class 3: For servers and software signing in which independent verification and identity and authority checking is done by the issuing CA.
- Class 4: For online business transactions between companies.
- Class 5: For private organizations or governmental security.
Application: SSL/TLS
Certificates are often used when using SSL/TLS. Most modern systems today use TLS, but the term SSL is often still used to refer to the connection. SSL is used to protect many types of applications, the most common being HTTPS (as HTTP is called when used with SSL).
An SSL session is formed between a web server and the web browser of the client. Figure 3.10 depicts the process.
Certificate Authorities
A certification authority (CA) is the entity that creates and signs digital certificates, maintains the certificates, and revokes them when necessary. Every entity that wants to participate in the PKI must contact the CA and request a digital certificate. It is the ultimate authority for the authenticity for every participant in the PKI and signs each digital certificate. The certificate binds the identity of the participant to the public key.
Any participant that requests a certificate must first go through the registration authority (RA), which verifies the requestor’s identity and registers the requestor. After the identity is verified, the RA passes the request to the CA. In many cases, the CA and the RA are the same server.
There are different types of CAs. Organizations exist that provide a PKI as a payable service to companies that need them. An example is VeriSign. Some organizations implement their own private CAs so that the organization can control all aspects of the PKI process. If an organization is large enough, it might need to provide a structure of CAs, with the root CA being the highest in the hierarchy.
Because more than one entity is often involved in the PKI certification process, certification path validation allows the participants to check the legitimacy of the certificates in the certification path.
When implementing a PKI, most organizations rely on a hierarchical chain-of-trust model that uses three components at minimum: certificate authorities (CAs), registration authorities (RAs), and a central directory/distribution management mechanism.

FIGURE 3.10 SSL process
A CA issues certificates that bind a public key to a specific distinguished name (DN) issued to the certificate applicant (user). Before issuing a certificate, however, the CA validates the applicant’s identity.
When a subject’s public certificate is received, the system must verify its authenticity. Because the certificate includes the issuer’s information, the verification process checks to see whether it already has the issuer’s public certificate. If not, it must retrieve it.
A root CA is at the top of the certificate signing hierarchy. VeriSign, Comodo, and Entrust are examples of public root CAs. For organizations that maintain their own PKI, the first CA created will be the root CA.
Using the root certificate, the system verifies the issuer signature and ensures that the subject certificate is not expired or revoked. If verification is successful, the system accepts the subject certificate as valid.
Root CAs can delegate signing authority to other entities. These entities are known as intermediate CAs. Intermediate CAs are trusted only if the signature on their public key certificate is from a root CA or can be traced directly back to a root. Because a root CA can delegate to intermediate CAs, a lengthy chain of trust can exist.
Any system receiving a subject certificate can verify its authenticity by stepping up the chain of trust to the root.
PKI Standards
Public Key Cryptography Standards (PKCS) were created by RSA Security. While they were created to help promote techniques for which RSA had patents, many of these standards have become standards by the IETF. Table 3.2 shows the standards that have not since been abandoned or obsoleted.
TABLE 3.2 PKI standards
| Standard | Version | Name | Description |
| PKCS #1 | 2.2 | RSA Cryptography Standard | Defines the mathematical properties and format of RSA public and private keys and the basic algorithms and encoding/padding schemes for performing RSA encryption and decryption and for producing and verifying signatures. |
| PKCS #3 | 1.4 | Diffie-Hellman Key Agreement Standard | A cryptographic protocol that allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure communications channel. |
| PKCS #5 | 2.0 | Password-Based Encryption Standard | Provides recommendations for the implementation of password-based cryptography, covering key derivation functions, encryption schemes, message-authentication schemes, and ASN.1 syntax identifying the techniques. |
| PKCS #7 | 1.5 | Cryptographic Message Syntax Standard | Used to sign and/or encrypt messages under a PKI. Formed the basis for S/MIME. Often used for single sign-on. |
| PKCS #8 | 1.2 | Private-Key Information Syntax Standard | Used to carry private certificate key pairs (encrypted or unencrypted). |
| PKCS #9 | 2.0 | Selected Attribute Types | Defines selected attribute types for use in PKCS #6 extended certificates, PKCS #7 digitally signed messages, PKCS #8 private-key information, and PKCS #10 certificate-signing requests. |
| PKVS #10 | 1.7 | Certification Request Standard | Format of messages sent to a certification authority to request certification of a public key. |
| PKCS #11 | 2.4 | Cryptographic Token Interface | Also known as Cryptoki. An API defining a generic interface to cryptographic tokens (see also hardware security module). Often used in single sign-on, public-key cryptography and disk encryption. |
| PKCS #12 | 1.1 | Personal Information Exchange Syntax Standard | Defines a file format commonly used to store private keys with accompanying public key certificates, protected with a password-based symmetric key. |
| PKCS #15 | 1.1 | Cryptographic Token Information Format Standard | Defines a standard allowing users of cryptographic tokens to identify themselves to applications, independent of the application’s Cryptoki implementation (PKCS #11) or other API. |
PKI Topologies
A PKI can consist of a single server that operates as RA and CA and is the root certificate server. But in very large environments, you may be advised to create a hierarchy of CAs. When this is done, a single CA will be the root CA and the top of the hierarchy. Underneath this would be a number of subordinate CAs that actually issue the certificates to the entities. The root CA creates and signs the certificates of the subordinate CAs, which creates a trust path up to the root. Figure 3.11 shows this arrangement.

FIGURE 3.11 PKI hierarchy
In some cases, two organizations may have a need to trust one another’s certificates. This can be done by configuring cross certification. In cross certification, a trust is created between the two root CAs, which enable both systems to trust all certificates, as shown in Figure 3.12 .

FIGURE 3.12 Cross certification
Certificates in the ASA
The Cisco Adaptive Security Appliance (ASA) makes use of certificates and the associated keys to protect the connection of the administrator to the ASA using the Adaptive Security Device Manager (ADSM) and to support SSL VPN clients. In this section, you’ll learn about the default certificate that is present in the ASA, the process of adding a certificate and viewing the certificates that are present, and the use of the Simple Certificate Enrollment Protocol (SCEP).
Default Certificate
The ASA has a self-signed default certificate that can be used for the operations listed in the previous section. The issue with a self-signed certificate is that no browsers or devices will have the ASA listed as a trusted CA. Because of this, any HTTPS connections to the ASA will generate a warning message that the certificate being presented is not trusted. To avoid this issue, you can install a root certificate of the CA whose certificate is found in the browsers and devices that will interact with the ASA (either that you own or a public CA).
Viewing and Adding Certificates in the ASDM
To view the current certificates in the ADSM, select Configuration at the top of the ADSM console and Device Management from the tabs on the left side of the console, as shown in Figure 3.13 . As you can see, this ASA currently has no certificates installed other than the default.
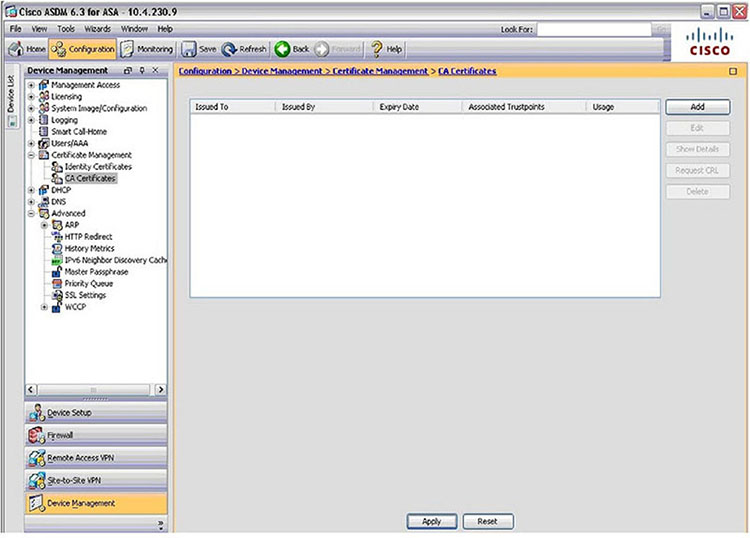
FIGURE 3.13 Viewing certificates
To add a certificate, follow these steps:
- In the Cisco ASDM Configuration Tool, select Configuration ➢ Device Management ➢ Certificate Management ➢ CA Certificates.
- Click Add. The Install Certificate dialog box appears. You have three options: install from a file, paste the information, or use SCEP. If the root CA represented by the root certificate supports SCEP, choose that option. Otherwise, use the next two steps.
- Enter a trustpoint name or use the default name that appears in the box.
- Click the Install From A File radio button and browse to the location of the Root.crt file that you are installing.
- Click the More Options button, and here you can configure how certificate revocation will be checked, the protocols to be used for certificate verification, and other settings.
SCEP
Simple Certificate Enrollment Protocol is a protocol used for enrollment and other PKI operations. It is supported on most Cisco devices. It simplifies the process of obtaining and installing both the root and the identity certificates. The process to use SCEP is as follows:
- Choose Configuration ➢ Device Management ➢ Certificate Management ➢ Identity Certificates and click Add.
- Click the Add A New Identity Certificate radio button and click the Advanced button.
- In the Advanced box, on the Enrollment Mode tab, select Request From A CA and then enter the IP address of the CA that supports SCEP. Click OK.
- In the Add A New Identity Certificate dialog box, select Add Certificate. If the enrollment is successful, you will receive an Enrollment Succeeded message.
Cryptanalysis
In cryptanalysis, cryptography attacks are categorized as either passive or active attacks. A passive attack is usually implemented just to discover information and is much harder to detect because it is usually carried out by eavesdropping or packet sniffing. Active attacks involve an attacker actually carrying out steps, such as message alteration or file modification. Cryptography is usually attacked via the key, algorithm, execution, data, or people. But most of these attacks are attempting to discover the key used.
Ciphertext-Only Attack
In a ciphertext-only attack, an attacker uses several encrypted messages (ciphertext) to figure out the key used in the encryption process. Although it is a common type of attack, it is usually not successful because so little is known about the encryption used.
Known Plaintext Attack
In a known plaintext attack, an attacker uses the plaintext and ciphertext versions of a message to discover the key used. This type of attack implements reverse engineering, frequency analysis, or brute force to determine the key so that all messages can be deciphered.
Chosen Plaintext Attack
In a chosen plaintext attack, an attacker chooses the plaintext to get encrypted to obtain the ciphertext. The attacker sends a message hoping that the user will forward that message as ciphertext to another user. The attacker captures the ciphertext version of the message and tries to determine the key by comparing the plaintext version he originated with the captured ciphertext version. Once again, key discovery is the goal of this attack.
Chosen Ciphertext Attack
A chosen ciphertext attack is the opposite of a chosen plaintext attack. In a chosen ciphertext attack, an attacker chooses the ciphertext to be decrypted to obtain the plaintext. This attack is more difficult because control of the system that implements the algorithm is needed.
Brute Force
As with a brute-force attack against passwords, a brute-force attack executed against a cryptographic algorithm uses all possible keys until a key is discovered that successfully decrypts the ciphertext. This attack requires considerable time and processing power and is difficult to complete.
Birthday Attack
A birthday attack uses the premise that finding two messages that result in the same hash value is easier than matching a message and its hash value. Most hash algorithms can resist simple birthday attacks.
Meet-in-the-Middle Attack
In a meet-in-the middle attack, an attacker tries to break the algorithm by encrypting from one end and decrypting from the other to determine the mathematical problem used.
Summary
In this chapter, you learned about symmetric and asymmetric key cryptography and how they differ. The chapter gave examples of each type of algorithm, and you learned how they can work together in a hybrid system. You also learned about the hashing process and looked at the major hashing algorithms. There was coverage of PKI and the components that make it function. Finally, you learned about common attacks on cryptography.
Exam Essentials
Differentiate between symmetric and asymmetric key cryptography. This includes the types of keys used, the scenarios in which they are used, and the disadvantages and advantages of each.
Describe the hashing process. This includes how hashing algorithms work, examples of hashing algorithms, and the role of hashing in digital signatures.
Explain the role of a PKI. Describe the components of a PKI, the certificate enrollment process, and the use of public and private keys in the process.
Define cryptanalytic attacks. These include ciphertext-only attack, chosen plaintext, chosen ciphertext, brute force, birthday, and meet-in-the-middle.
Review Questions
-
Which of the following is not true of symmetric algorithms?
- They use a public key.
- They are faster than asymmetric algorithms.
- They present key exchange issues.
- They are typically used for data at rest.
-
Which of the following is not true of asymmetric algorithms?
- They provide automatic key exchange.
- They are typically used for data at rest.
- They use a private and public key.
- They are slower than symmetric algorithms.
-
Which of the following is not an advantage of block ciphers?
- The implementation is easier than stream-based cipher implementation.
- Generally they are less susceptible to security issues.
- Generally they are used more in software implementations.
- They employ only substitution.
-
Which of the following ciphers perform encryption on a bit-by-bit basis?
- Block
- Stream
- Asymmetric
- Polyalphabetic
-
Which of the following is used to ensure that patterns are not produced during encryption?
- IVs
- HMAC
- RC4
- Salting
-
In which of the following modes of DES is every 64-bit block encrypted with the same key?
- CBC
- ECB
- ECC
- CFB
-
Which of the following is the replacement algorithm for 3DES?
- Blowfish
- AES
- IDEA
- RC4
-
Which of the following is the most popular asymmetric algorithm?
- RSA
- El Gamal
- DSA
- ECC
-
Which of the following occurs when a hash function produces the same hash value on different messages?
- Birthday attack
- Key exposure
- Collision
- Substitution
-
Which of the following hashing algorithms is required by the U.S. government?
- MD4
- MD5
- SHA1
- SHA2
-
Which of the following can help to reduce the collision rate of the hash function?
- MAC
- HMAC
- Digital signatures
- Substitution
-
Which of the following is a hash value encrypted with the sender’s private key?
- Salt
- Nonce
- Digital signature
- HMAC
-
Which of the following is true of a hybrid cryptosystem?
- Asymmetric algorithms are used for the key exchange.
- Symmetric keys are used for the key exchange.
- Asymmetric keys are used for the data encryption.
- Asymmetric keys are exchange automatically.
-
Which of the following is a digital document binding a key pair to an entity?
- Certificate
- Nonce
- Salt
- IV
-
Which of the following is the standard for digital certificates?
- X.500
- X.509
- IEEE 509
- RFC 500
-
Which of the following is a list of digital certificates that a CA has revoked?
- OSCP
- CRL
- SCEP
- REVC
-
Which of the following certificate classes is for individuals intended for email?
- 1
- 2
- 3
- 4
-
Which of the following PKI components verifies the requestor’s identity?
- CA
- RA
- DN
- CN
-
Which of the following can be used to allow one root CA to trust another root CA’s certificates?
- Subordination
- Cross certification
- Certlink
- Trust
-
What type of certificate does the ASA use out of the box?
- Public
- Self-signed
- Globally trusted
- Locally trusted
