Chapter 17
Content and Endpoint Security
CISCO CCNA SECURITY EXAM OBJECTIVES COVERED IN THIS CHAPTER:
 7.1 Describe mitigation technology for email-based threats
7.1 Describe mitigation technology for email-based threats
- Spam filtering, anti-malware filtering, DLP, blacklisting, email encryption
 7.2 Describe mitigation technology for web-based threats
7.2 Describe mitigation technology for web-based threats
- Local and cloud-based web proxies
- Blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, TLS/SSL decryption
 7.3 Describe mitigation technology for endpoint threats
7.3 Describe mitigation technology for endpoint threats
- Anti-virus/anti-malware
- Personal firewall/HIPS
- Hardware/software encryption of local data
 Endpoint devices in the network such as laptops, printers, workstations, scanners, cameras, and other such devices represent one of our biggest challenges in securing the environment. First, there are so many more of these than there are infrastructure devices. Moreover, these devices are most likely in the hands of users who either lack security knowledge or just don’t care about it. In this chapter, you’ll learn how to overcome these challenges and secure the endpoints in the environment.
Endpoint devices in the network such as laptops, printers, workstations, scanners, cameras, and other such devices represent one of our biggest challenges in securing the environment. First, there are so many more of these than there are infrastructure devices. Moreover, these devices are most likely in the hands of users who either lack security knowledge or just don’t care about it. In this chapter, you’ll learn how to overcome these challenges and secure the endpoints in the environment.
In this chapter, you will learn the following:
- Mitigation technology for email-based threats, including SPAM filtering, anti-malware filtering, data loss prevention (DLP), blacklisting, and email encryption
- Mitigation technology for web-based threats, including local and cloud-based web proxies, blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, and TLS/SSL decryption
- Mitigation technology for endpoint threats, including antivirus/anti-malware, personal firewall/HIPS, and hardware/software encryption of local data
Mitigating Email Threats
Threats to email strike at the very heart of your enterprise communication system. It has become evident that even tech-savvy users can fall prey to these threats. In this section, you’ll learn about a few methods you can use to mitigate these threats. These methods are not mutually exclusive, and when deployed together, they stand as a good example of exercising the principle of a layered defense or defense in depth. Following that, you’ll learn about the ways the Cisco Email Security Appliance (ESA) can address these threats.
Spam Filtering
Spam is both an annoyance to users and an aggravation to email administrators who must deal with the extra space the spam takes up on the servers. Spam filters are designed to prevent spam from being delivered to mailboxes. The issue with spam filters is that often legitimate email is marked as spam. Finding the right setting can be challenging. Users should be advised that no filter is perfect and that they should regularly check quarantined email for legitimate emails.
Reputation-based filtering relies on the identification of email servers that have become known for sending spam. When a system can do this, it must rely on some service for developing these “reputations.” As you will see later, an example is the Cisco SenderBase. This is the system the Cisco Email Security Appliance (ESA) uses. This repository manages reputation “scores” for servers based on any malicious activity in which the server is reported to have been involved.
Context-Based Filtering
Context-based filtering filters the message and attachments for sender identities, message content, embedded URLs, and email formatting. These systems use algorithms to examine these items to identify spam.
Anti-malware Filtering
Email can also introduce malware into the environment through both malicious attachments and deceptive links in emails. While user training is the best approach to preventing email-based malware, we know that it doesn’t always work. Even security professionals have inadvertently clicked malicious links and attachments by mistake. To augment training, the examination of all email for malware and the filtering of such malicious mail should be parts of providing secure email.
DLP
Data leakage occurs when sensitive data is disclosed to unauthorized personnel either intentionally or inadvertently. Data loss prevention (DLP) software attempts to prevent data leakage. It does this by maintaining awareness of actions that can and cannot be taken with respect to a document. For example, it might allow printing of a document but only at the company office. It might also disallow sending the document through email. DLP software uses ingress and egress filters to identify sensitive data that is leaving the organization and can prevent such leakage. Another scenario might be the release of product plans that should be available only to the sales group. The policy you could set for that document is as follows:
- It cannot be emailed to anyone other than sales group members.
- It cannot be printed.
- It cannot be copied.
There are two locations at which DLP can be implemented.
Network DLP Installed at network egress points near the perimeter, network DLP analyzes network traffic.
Endpoint DLP Endpoint DLP runs on end-user workstations or servers in the organization.
You can use both precise and imprecise methods to determine what is sensitive.
Precise methods These methods involve content registration and trigger almost zero false-positive incidents.
Imprecise methods These can include keywords, lexicons, regular expressions, extended regular expressions, metadata tags, Bayesian analysis, and statistical analysis.
The value of a DLP system resides in the level of precision with which it can locate and prevent the leakage of sensitive data.
Blacklisting
Blacklisting identifies bad senders. Whitelisting occurs when a list of acceptable e-mail addresses, Internet addresses, websites, applications, or other identifiers are configured as good senders or as allowed. Graylisting is somewhere in between the two when an entity cannot be identified as a whitelist or blacklist item. In the case of graylisting, the new entity must pass through a series of tests to determine whether it will be whitelisted or blacklisted. Whitelisting, blacklisting, and graylisting are commonly used with spam filtering tools.
Email Encryption
Email traffic, like any other traffic type, can be captured in its raw form with a protocol analyzer. If the email is clear text, it can be read. For this reason, encryption should be used for all emails of a sensitive nature. While this can be done using the digital certificate of the intended recipient, this is typically possible only if the recipient is part of your organization and your company has a public key infrastructure (PKI). Many email products include native support for digital signing and encryption of messages using digital certificates.
While it is possible to use email encryption programs like Pretty Good Privacy (PGP), it is confusing for many users to use these products correctly without training. Another option is to use an encryption appliance or service that automates the encryption of email. Regardless of the specific approach, encryption of messages is the only mitigation for information disclosure from captured packets.
Cisco Email Security Appliance
The Cisco Email Security Appliance can address each of these concerns. The features that address email issues in the ESA are covered in this section. At the end of the section is a discussion of the message flow when using ESA.
Reputation and Context-Based Filtering
ESA performs both types of filtering. When utilizing the Cisco SenderBase, the actions taken by ESA depend on the reputation score of the source. If the sender score is between –1 and +10, the email is accepted. If it is –1 and –3, the email is accepted but additional emails are throttled. If it is between –10 and –3, it is blocked.
Viruses and Anti-malware
ESA uses a multilayer approach to this issue. The three layers of defense are as follows:
Outbreak Filters Downloaded from the Cisco SenderBase. These filters are generated by watching global email traffic patterns and looking for signs of an outbreak. When an email is received from a server on the list, it is quarantined until antivirus signatures are updated that address the risk.
Antivirus Signatures Used in the same way any anti-malware product uses them: to identify the presence of malware in the email.
Outbound Scanning Scans email that is leaving for the presence of malware.
Email Data Loss Prevention and Encryption
ESA’s DLP features use rules for identifying classes of sensitive information such as personally identifiable information (PII), payment card numbers, bank routing numbers, financial account information, government ID numbers, personal names, addresses and phone numbers, and healthcare records. Moreover, you can design your own classes that include data not in these categories. Encryption is also possible to protect any sensitive information that must be sent.
Advanced Malware Protection
Advanced Malware Protection (AMP) is the malware component in ESA that uses a combination of several technologies to protect you from email-based malware.
File Reputation A fingerprint of every file that traverses the Cisco email security gateway is sent to AMP’s cloud-based intelligence network for a reputation verdict. Based on these results, you can block malicious files identified as having a bad reputation.
File Retrospection Sometimes files enter the network and are later identified as being a threat. This allows for the identification and removal of these files later. If malicious behavior is spotted later, AMP sends a retrospective alert so that you can contain and remediate the malware. This process is depicted in Figure 17.1 .
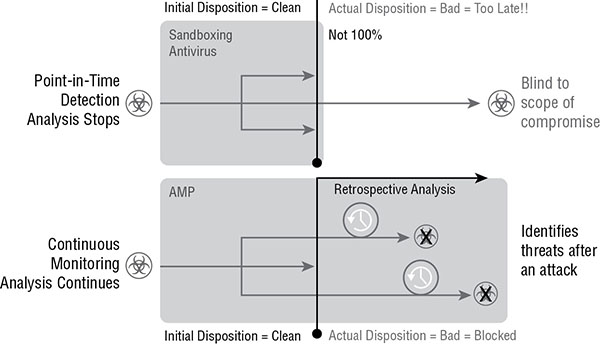
FIGURE 17.1 File retrospection
File Sandboxing This provides the ability to analyze files that traverse the gateway. Then in the safe sandboxed environment, AMP can obtain details about the threat level of the malware and communicate that information to the Cisco Talos intelligence network to update the AMP cloud data for all.
ESA Message Flow
ESA performs its job by acting as a message transfer agent (MTA) in the email system. Another name for this function is email relay. Figure 17.2 shows a normal inbound message flow.

FIGURE 17.2 ESA inbound
Figure 17.3 shows a normal outbound message flow.
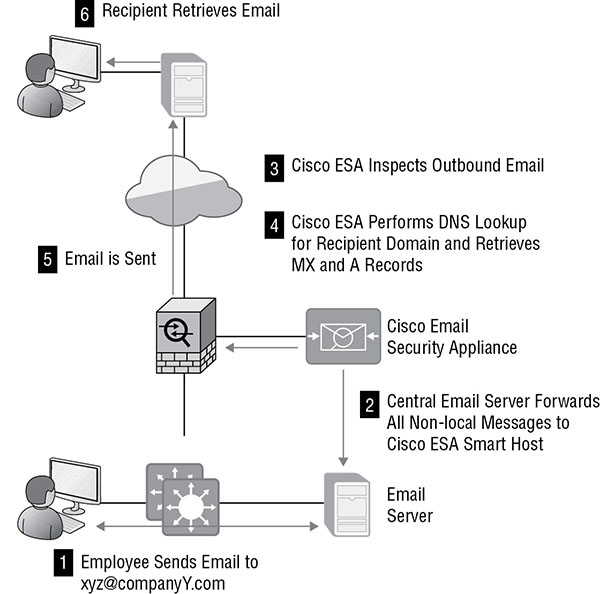
FIGURE 17.3 ESA outbound
Putting the Pieces Together
The various components that ESA brings to bear in its role as an email security utility work together in an integrated fashion, as shown in Figure 17.4 , which is how ESA operates against incoming email.

FIGURE 17.4 Incoming mail processing
Regarding email that is leaving the organization, the operations of these components are depicted in Figure 17.5 .
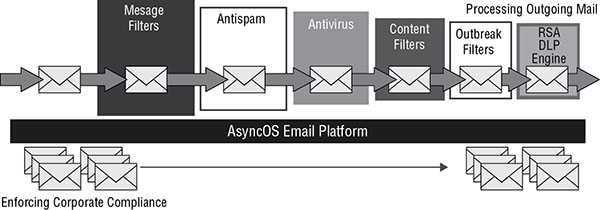
FIGURE 17.5 Outgoing mail processing
Mitigating Web-Based Threats
Another threat that presents itself to most enterprises is aimed at their web services. While not every organization has the need for an e-commerce server, almost every organization has a website or some type of web presence. Even a defacing of a public website, while not costly from a monetary standpoint, hurts the reputation and image of an organization.
One of the common ways of addressing threats against web applications and the web server software upon which they operate is a web proxy. Proxy servers in general stand between internal users or internal applications and potentially malicious requests coming from the Internet. Web proxies are a type of proxy that stands between a web application and web request coming from the Internet. This section discusses web proxies and the functions they perform.
Understanding Web Proxies
Proxy servers can be appliances, or they can be installed on a server operating system. These servers act like a proxy firewall in that they create the web connection between systems on their behalf, but they can typically allow and disallow traffic on a more granular basis. For example, a proxy server may allow the sales group to go to certain websites while not allowing the data entry group access to those same sites. The functionality extends beyond HTTP to other traffic type, such as FTP traffic.
Proxy servers can provide an additional beneficial function called web caching. When a proxy server is configured to provide web caching, it saves a copy of all web pages that have been delivered to internal computers in a web cache. If any user requests the same page later, the proxy server has a local copy and need not spend the time and effort to retrieve it from the Internet. This greatly improves web performance for frequently requested pages.
From a deployment perspective, web proxies can be implemented in two ways.
Local
A local proxy is one that is installed on the premises in which all of the processing occurs on the local web proxy.
Cloud-Based
A cloud-based web proxy is one that transmits the traffic to a cloud location where all the operations that would occur on a local web proxy occur in the cloud. In some cases, this offers the advantage of additional intelligence services that can aggregate and analyze telemetry data from billions of web requests, malware samples, and emerging attack methods.
Cisco Web Security Appliance
The Cisco Web Security Appliance (WSA) is a web proxy that integrates with other network components to monitor and control outbound requests for web content. Traffic can be directed to the WSA explicitly on the end host or by using Web Cache Control Protocol on an inline device like the perimeter router. The features it provides are covered in this section and will be followed by a description of traffic flow when using a WSA.
Blacklisting
Blacklisting and whitelisting can be used to create and support the acceptable use policy (AUP) of the organization. Moreover, it helps to prevent malware from malicious sites from entering the network.
URL Filtering
The WSA reputation filters operate much like the reputation filters used in ESA, with the difference being that they operate against web domains rather than email sources. By leveraging Cisco Security Intelligence Operations (SIO), Cisco Ironport reputation filters analyze more than 50 web and network parameters to evaluate a website’s trustworthiness.
Malware Scanning
The WSA anti-malware system uses multiple scanning engines in a single appliance. It uses the Dynamic Vectoring and Streaming Engine and verdict engines from both WebRoot and McAfee.
URL Categorization
The Cisco URL filters can also be managed using access policies based on 52 predefined categories and an unlimited number of customer categories of sites. These can be used along with time-based polices to add additional flexibility.
Web Application Filtering
WSA uses Application Visibility and Control (AVC) to allow for the control of the use of web applications. Granular policy control allows administrators to permit the use of applications such as Dropbox or Facebook while blocking users from activities such as uploading documents or clicking the Like button.
TLS/SSL Decryption
In Cisco AsyncOS 9.0.0-485, the operating system in WSA, you can now enable and disable SSL v3 and various versions of TLS for several services. Disabling SSL v3 for all services is recommended for best security. You also can enable a protocol fallback option.
Mitigating Endpoint Threats
This section discusses the protection of endpoints. Many of the items discussed in this section can be managed manually or with third-party tools, but many of the items can be managed automatically using the Identity Services Engine (ISE). Before we discuss the security measures in this section and their potential relationship with ISE, let’s take a brief look at ISE.
Cisco Identity Services Engine (ISE)
Finally, if the organization is implementing a BYOD policy, it can streamline this with self-service onboarding and management. While many of these features are beyond the scope of this book, we are going to discuss how it can handle the settings in this section.
Antivirus/Anti-malware
The Cisco ISE posture service interrogates a device requesting access for information regarding the presence of and proper configuration of antivirus and/or anti-malware software. It also checks for the presence of the latest available updates. Only when the machine is fully compliant is it allowed full access to the network.
Personal Firewall
While the Cisco ISE posture service verifies the presence of and proper configuration of antivirus and/or anti-malware software, it doesn’t stop there. It can also verify the function and settings of the personal firewall. It can compare this with a baseline for compliance in the same way it verifies the antivirus and/or anti-malware software.
Hardware/Software Encryption of Local Data
Finally, sensitive data located in endpoints should be secured with either hardware or software encryption. Cisco ISE can be used to implement a mobile management solution that can require encryption of the storage in both easily stolen mobile devices and other devices that may contain sensitive information.
HIPS
While not a function that can be controlled through ISE or TrustSec, a host-based IPS (HIPS) monitors traffic on a single system. Its primary responsibility is to protect the system on which it is installed. An HIPS typically works closely with anti-malware products and host firewall products. They generally monitor the interaction of sites and applications with the operating system and stop any malicious activity or, in some cases, ask the user to approve changes that the application or site would like to make to the system.
These systems can use several methods of detecting intrusions. The two main methods are as follows:
- Signature based: Analyzes traffic and compares patterns, called signatures, that reside within the IDS database. This requires constant updating of the signature database.
- Anomaly based: Analyzes traffic and compares it to normal traffic to determine whether the traffic is a threat. This means any traffic out of the ordinary will set off an alert.
Summary
In this chapter, you learned mitigation techniques available when using the Cisco Email Security Appliance. This included reputation and context-based filtering. You also were introduced to the Cisco Web Security Appliance, which can use blacklisting, URL filtering, and malware scanning to secure web traffic and web applications. Finally, the chapter discussed endpoint protection provided by the Cisco Identity Services Engine and Cisco TrustSec technology.
Exam Essentials
Identify the processes used by Cisco ESA to protect email. These processes include spam filtering, reputation-based filtering, context-based filtering, anti-malware filtering, data loss prevention, blacklisting, and email encryption.
Describe the actions of which the Cisco Web Security Appliance is capable. Some examples of these actions are blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, and TLS/SSL decryption.
Differentiate endpoint threats. These threats include viruses and malware, data disclosure, peer-to-peer attacks, and unauthorized access.
Identify techniques employed by the Cisco Identity Services Engine. These include access management, 802.1x, health and patch assessment, and verification of settings in the personal firewall.
Review Questions
-
Which of the following relies on the identification of email servers that have become known for sending spam?
- Context-based filtering
- Reputation-based filtering
- Data-based filtering
- Domain-based filtering
-
Which of the following occurs when sensitive data is disclosed to unauthorized personnel either intentionally or inadvertently?
- Data leakage
- Data egress
- Information corruption
- Unintended release
-
Which of the following is installed at network egress points near the perimeter?
- Client DLP
- Network DLP
- Endpoint DLP
- Composite DLP
-
Which of the following trigger almost zero false-positive incidents?
- Precise methods
- Complete methods
- Imprecise methods
- Sparse methods
-
With which sender score does ESA accept an email?
- Between –1 and +10
- Between –1 and –3
- Between –10 and –3
- Between +10 and +20
-
Which of the following is the malware component in ESA?
- AMP
- MAP
- CMP
- EMP
-
Which capability of AMP sends a fingerprint of every file that traverses the Cisco email security gateway to AMP’s cloud-based intelligence network?
- File reputation
- File retrospection
- File sandboxing
- File examination
-
Which of the following uses real-time analysis on a vast, diverse, and global dataset to detect URLs that contain some form of malware?
- SPAN
- WBRS
- WCCP
- SIO
-
Which of the following is a web proxy that integrates with other network components to monitor and control outbound requests for web content?
- ESA
- AMP
- WSA
- ISE
-
Which component analyzes more than 50 web and network parameters to evaluate a website’s trustworthiness?
- Cisco Ironport
- Dynamic Vectoring and Streaming Engine
- Web Cache Control Protocol
- Message Transfer Agent (MTA)
-
With which sender score does ESA block the email?
- Between –1 and +10
- Between –1 and –3
- Between –10 and –3
- Between +10 and +20
-
Which capability of AMP provides the ability to analyze files that traverse the gateway?
- File reputation
- File retrospection
- File sandboxing
- File examination
-
Which of the following uses the Dynamic Vectoring and Streaming Engine?
- ESA
- AMP
- WSA
- ISE
-
Which of the following allows administrators to permit the use of applications such as Dropbox or Facebook?
- ESA
- AMP
- WSA
- AVC
-
Which of the following can provide AAA services so that you can deploy 802.1x security?
- ESA
- ISE
- WSA
- AVC
-
Which capability of AMP allows for the identification and removal of these files after they are accepted?
- File reputation
- File retrospection
- File sandboxing
- File examination
-
With which sender score does ESA accept the email but additional emails are throttled?
- Between –1 and +10
- Between –1 and –3
- Between –10 and –3
- Between +10 and +20
-
Which of the following can include keywords, lexicons, and regular expressions?
- Precise methods
- Complete methods
- Imprecise methods
- Sparse methods
-
Which of the following is installed on end-user workstations?
- Client DLP
- Network DLP
- Endpoint DLP
- Composite DLP
-
Which of the following filters the message and attachments for sender identities, message content, embedded URLs, and email formatting?
- Context-based filtering
- Reputation-based filtering
- Data-based filtering
- Domain-based filtering
