CHAPTER 3
Scanning and Enumeration
In this chapter, you will
• Understand EC-Council’s scanning methodology
• Describe scan types and the objectives of scanning
• Understand the use of various scanning and enumeration tools
• Describe TCP communication (three-way handshake and flag types)
• Understand basic subnetting
• Understand enumeration and enumeration techniques
• Describe vulnerability scanning concepts and actions
• Describe the steps involved in performing enumeration
Imagine this is a movie instead of a book, about a guy beginning a career in ethical hacking. At some point, probably during the previews for Aquaman, someone’s cell phone will ring and we all momentarily flash with unbridled rage before going back to the screen. The opening credits roll, showing us that this is a story about a young man deciding to put his hacker training to use. In the first scenes he’s researching vulnerabilities and keeping track of the latest news, checking on websites, and playing with tools in his secret lab. Soon thereafter, he gets his first break and signs a contract to test a client—a client holding a secret that could change the very fabric of modern society.
Before we’re even halfway through the buttered popcorn, he has completed some footprinting work and has tons of information on potential targets. Some of it seems harmless enough, while some is so bizarre he’s not really sure what it even is. He leans in, looking at the multitude of monitors all around him (while foreboding music leads us all to the edge of our seats). The camera zooms in for a close-up, showing his eyes widening in wonder. The crescendo of music hits as he says, “OK…so what do I do now?”
Welcome to scanning and enumeration, where you learn what to do with all those targets you identified in the last chapter. You know how to footprint your client; now it’s time to learn how to dig around what you found for relevant, salient information. As somewhat of an interesting side note here (and a brief glimpse into the “real” world of pen testing versus exam study), it’s important for you to consider which targets are worth scanning and which aren’t. If you know some targets are easy, don’t risk discovery by scanning them. If you know an army of nerds are arrayed against you, maybe social engineering is a better option. In any case, scanning can be viewed as a necessary evil, but it needs to be approached with caution and respect.
When it comes to your CEH study, which is what all this is supposed to be about, you’ll need to stick with the flow, move through the steps as designed, and pay attention to tools, scan types, outputs, and the like. So, after footprinting, you’ll need to scan for basics—the equivalent of knocking on all your neighbors’ doors to see who is home and what they look like, or maybe checking out homes for sale to find out as much as you can before going inside them. This ensures that when you find a machine up and about, you’ll get to know it really well by asking some rather personal questions—but don’t worry, systems don’t get upset. We’ll go over all you’ll need to know for the exam regarding scanning and enumeration and show you how to play with some pretty fun tools along the way. And the movie? Well, until someone pays me to write a script, it probably won’t happen. If it did happen, though, undoubtedly you’d get to the end and somebody would say, “Yeah, but the book was better.”
Fundamentals
Our first step after footprinting a target is to get started with scanning. Before we dive into it, I think it’s important to knock out a few basics first. While in the footprinting stage, we were gathering freely available, “10,000-foot-view” information. With scanning, though, we’re talking about a much more focused effort. Footprinting may have shown us the range of network addresses the organization uses, but now scanning is going to tell us which of those addresses are in use and ideally what’s using those addresses.
In short, scanning is the process of discovering systems on the network and taking a look at what open ports and applications may be running. With footprinting, we wanted to know how big the network was and some general information about its makeup. In scanning, we’ll go into the network and start touching each device to find out more about it. But before we get to the actual scanning, though, we really need to cover some basic TCP/IP networking knowledge.
TCP/IP Networking
We covered some networking basics earlier in this book, but if we’re going to talk scanning intelligently, we’re going to need to dive just a bit deeper. As you’ll recall, when a recipient system gets a frame, it checks the physical address to see who the message is intended for. If the address is indeed correct, the recipient opens the frame, checks to make sure the frame is valid, and then ditches the header and trailer, passing the remainder up to the Network layer. There, the Layer 3 address is verified in the packet header, along with a few other items, and the header is stripped off. The remaining PDU (protocol data unit), now called a segment, is passed to Layer 4. At the Transport layer, a whole host of important stuff happens—end-to-end delivery, segment order, reliability, and flow control are all Layer 4 functions—including a couple of salient issues in the discussion here: TCP flags and port numbering.
Connectionless Communication
When two IP-enabled hosts communicate with each other, as you no doubt already know, two methods of data transfer are available at the Transport layer: connectionless communication and connection-oriented communication. Connectionless communication is fairly simple to understand: the sender doesn’t care whether the recipient has the bandwidth (at the moment) to accept the message, nor does the sender really seem to care whether the recipient gets the message at all. Connectionless communication is “fire and forget.” In a much faster way of sending datagrams, the sender can simply fire as many segments as it wants out to the world, relying on other upper-layer protocols to handle any problems. This obviously comes with some disadvantages as well (no error correction, retransmission, and so on).
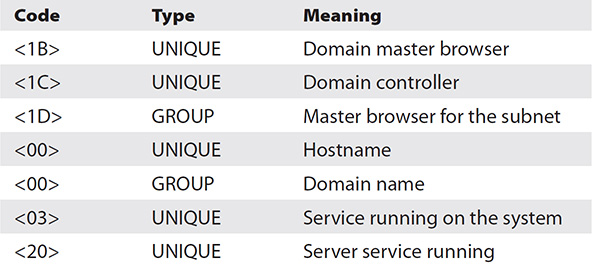
At the Transport layer, connectionless communication is accomplished with UDP. UDP, as you can tell from the datagram structure shown in Figure 3-1, is a low-overhead, simple, and fast transport protocol. Generally speaking, the application protocols that use this transport method are moving small amounts of data (sometimes just a single packet or two) and usually are moving them inside a network structure (not across the Internet). Examples of protocols using UDP are TFTP, DNS (for lookups), and DHCP.
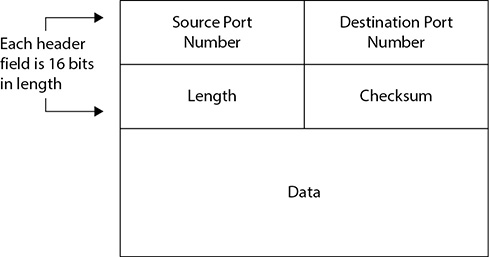
Figure 3-1 UDP datagram structure
Connection-Oriented Communication
Connection-oriented communication using TCP, although it requires a lot more overhead and if oftentimes a lot slower than connectionless communication, is a much more orderly form of data exchange and makes a lot more sense for transporting large files or communicating across network boundaries. Senders will reach out to recipients, before data is ever even sent, to find out whether they’re available and whether they’d be willing to set up a data channel. Once the data exchange begins, the two systems continue to talk with one another, making sure flow control is accomplished, so the recipient isn’t overwhelmed and can find a nice way to ask for retransmissions in case something gets lost along the way. How does all this get accomplished? It’s through the use of header flags and something known as the three-way handshake. Figure 3-2 shows the TCP segment structure.
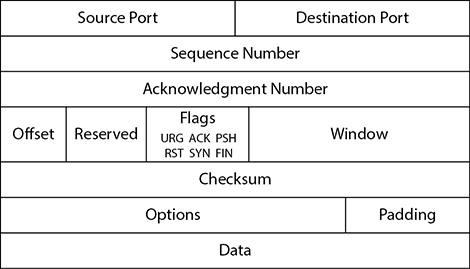
Figure 3-2 TCP segment structure
Taking a look at Figure 3-2, you can see that six flags can be set in the TCP header. Depending on what the segment is intended to do, some or all of these flags may be put into use. The TCP header flags are as follows:
• SYN (Synchronize) This flag is set during initial communication establishment. It indicates negotiation of parameters and sequence numbers.
• ACK (Acknowledgment) This flag is set as an acknowledgment to SYN flags. This flag is set on all segments after the initial SYN flag.
• RST (Reset) This flag forces a termination of communications (in both directions).
• FIN (Finish) This flag signifies an ordered close to communications.
• PSH (Push) This flag forces the delivery of data without concern for any buffering. In other words, the receiving device need not wait for the buffer to fill up before processing the data.
• URG (Urgent) When this flag is set, it indicates the data inside is being sent out of band. Cancelling a message mid-stream is one example.
To fully understand these flags and their usage, consider what is most often accomplished during a normal TCP data exchange. First, a session must be established between the two systems. To do this, the sender forwards a segment with the SYN flag set, indicating a desire to synchronize a communications session. This segment also contains a sequence number—a pseudorandom number that helps maintain the legitimacy and uniqueness of this session. As an aside, the generation of these numbers isn’t necessarily all that random after all, and plenty of attack examples point that out. For study purposes, though, just remember what the sequence number is and what its purpose is.
When the recipient gets this segment, it responds with the SYN and ACK flags set and acknowledges the sequence number by incrementing it by one. Additionally, the return segment contains a sequence number generated by the recipient. All this tells the sender, “Yes, I acknowledge your request to communicate and will agree to synchronize with you. I see your sequence number and acknowledge it by incrementing it. Please use my sequence number in further communications with me so I can keep track of what we’re doing.” Figure 3-3 illustrates the three-way handshake.
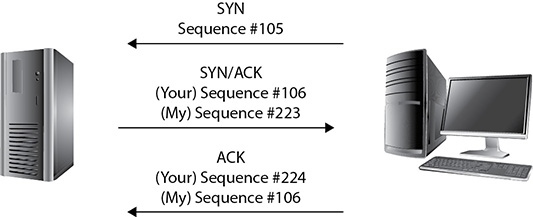
Figure 3-3 The three-way handshake
When this segment is received by the original sender, it generates one more segment to finish off the synchronization. In this segment, the ACK flag is set, and the recipient’s own sequence number is acknowledged. At the end of this three-way handshake, a communications channel is opened, sequence numbers are established on both ends, and data transfer can begin.
Knowing the TCP flags and the communications setup process, I think it’s fairly obvious how a hacker (with a tool capable of crafting segments and manipulating flags) could manipulate, disrupt, manufacture, and even hijack communications between two systems. Want to see for yourself? Jump on the Internet and download and install Colasoft’s Packet Builder (www.colasoft.com/download/products/download_packet_builder.php, shown in Figure 3-4). Open it, click the Add button in the menu line, and pick a TCP packet. You can then maneuver up and down the segment to change TCP flags and create all sorts of mischief.
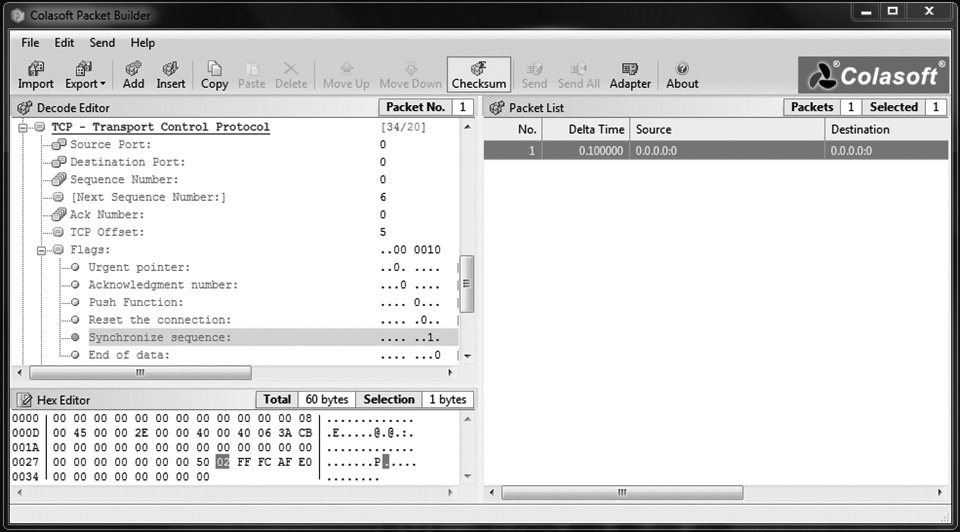
Figure 3-4 Colasoft Packet Builder
We’ve spent some good time discussing the flags within a segment (keep repeating “SYN, SYN/ACK, ACK” in your head), but there are at least a couple other fields of great importance while we’re on the subject. The source and destination port fields in TCP or UDP communication define the protocols that will be used to process the data. Better stated, they actually define a channel on which to work, and that channel has been generally agreed upon by default to support a specific protocol, but you get the point.
Port Numbering
Why the heck do we even need port numbers in networking? Well, consider a communications process in its early stages. The recipient has verified the frame and packet that belongs to it and knows it has a segment available for processing. But how does it know which Application layer entity is supposed to process it? Maybe it’s an FTP datagram. Or maybe a Telnet request. Or maybe even e-mail. Without something to identify which upper-layer protocol to hand this information to, the system sits there like a government mid-level manager, paralyzed by indecision.
A port number, inside the Transport layer protocol header (TCP or UDP), identifies which upper-layer protocol should receive the information contained within. Systems use port numbers to identify to recipients what they’re trying to accomplish—that is, assuming the default ports are still being used for their default purposes, but we’ll get to that later. The port numbers range from 0 to 65,535 and are split into three different groups:
• Well-known ports 0–1023
• Registered ports 1024–49,151
• Dynamic ports 49,152–65,535
Of particular importance to you on the CEH exam are the well-known port numbers. No, you don’t need to memorize all 1024 of them, but you do need to know many of them. The ports listed in Table 3-1 are absolutes—you simply must memorize them or quit reading and studying for your exam here.
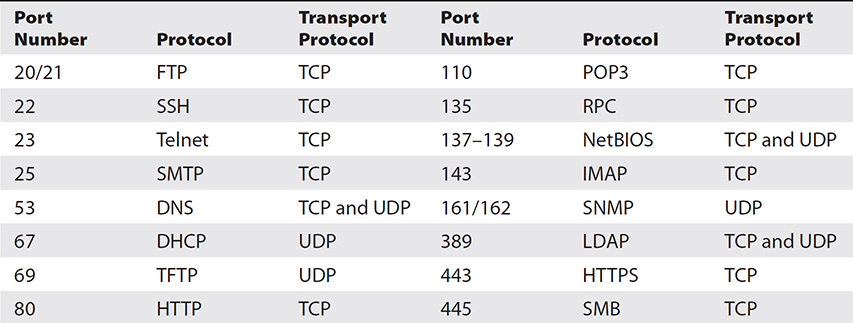
Table 3-1 Important Port Numbers
Assuming you know which well-known port number is associated with which upper-layer protocol, you can tell an awful lot about what a system is running just by knocking on the port doors to see what is open. A system is said to be listening for a port when it has that port open. For example, assume you have a server hosting a website and an FTP service. When the server receives a message, it needs to know which application is going to handle the message. At the same time, the client that made the request needs to open a port on which to hold the conversation (anything above 1023 will work). Figure 3-5 demonstrates how this is accomplished—the server keeps track of which application to use via the port number in the destination port field of the header and answers to the source port number.
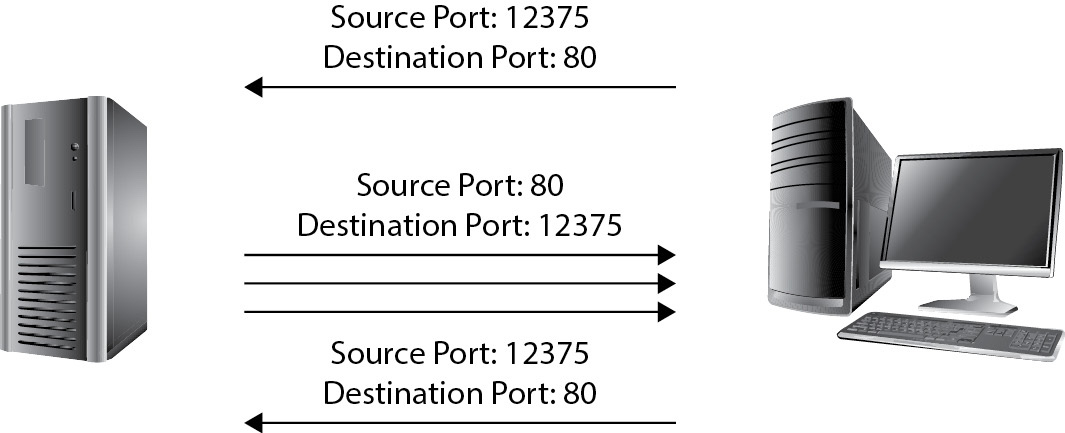
Figure 3-5 Port numbers in use
In reading this, you may be wondering just how those ports are behaving on your own machine. The answer comes from the state the port is in. Suppose you have an application running on your computer that is waiting for another computer to connect to it. Whatever port number your application is set to use is said to be in a listening state. Once a remote system goes through all the handshaking and checking to establish a session over that open port on your machine, your port is said to be in an established state. In short, a listening port is one that is waiting for a connection, while an established port is one that is connected to a remote computer.
Ports can be in other states as well. For instance, remember that packets can be received out of order and sometimes take a while to get in? Imagine your port sitting there in a listening state. A remote system connects, and off you go—with the data exchange humming along. Eventually either your system or the remote system will close the session. But what happens to any outstanding packets that haven’t made their way yet? A port state of CLOSE_WAIT shows that the remote side of your connection has closed the connection, whereas a TIME_WAIT state indicates that your side has closed the connection. The connection is kept open for a little while to allow any delayed packets to be matched to the connection and handled appropriately. If you’d like to see this in action on your Windows machine, open a command prompt and use an old standby: netstat. Typing netstat -an (see Figure 3-6) displays all connections and listening ports, with addresses and port numbers in numerical form. If you have admin privileges on the box, use netstat -b, and you can see the executable tied to the open port.
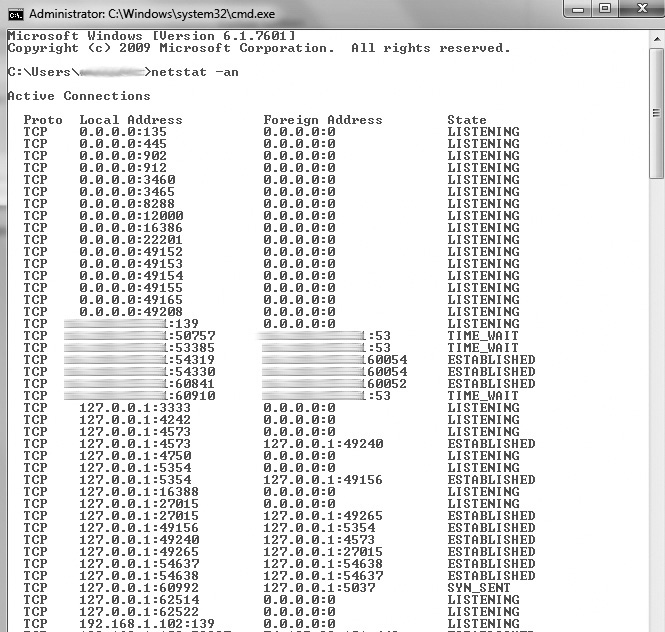
Figure 3-6 The command netstat
Subnetting
Want to know something neat? You won’t find subnetting mentioned anywhere in EC-Council’s official courseware for the CEHv10 certification. So you may be asking, “Why do we even need subnetting? What’s the point?” The answer, dear reader, is that depending on which version of the exam you get, you will most likely be asked about it. Supposedly you know this already, so this section will be a breeze (and I promise to keep it as short as possible); however, in keeping with my promise to cover everything, we just have to get into it.
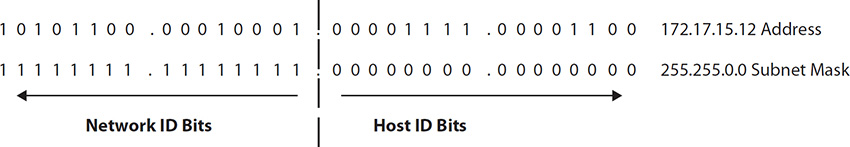
As I’m sure you’re already aware, your system has no idea about the rest of the world, and frankly doesn’t care. As far as it is concerned, its responsibility is to pass messages it receives to whatever application inside needs them, and to send messages only to systems inside its own neighborhood (network)—in effect, only systems it can see and touch. It’s the job of someone else in the neighborhood (the router) to get the messages delivered to outside, unknown systems. And the only way that device has to identify which networks are local and which networks are remote is the subnet mask. So what is a subnet mask? To answer that, let’s first talk about an IPv4 address.
As you’re already aware (because you are supposed to know this already), IP addresses are really 32 bits, each set to 1 or 0, separated into four octets by decimal points. Each one of these addresses is made up of two sections—a network identifier and a host identifier. The bits making up the network portion of the address are used much like the ZIP code on letters. Local post offices (like routers) don’t care about who, individually, a message is addressed for; they only care about which post office (network) to get the message to. For example, the friendly sorting clerk here at my local post office doesn’t care that the letter I put in the box to mail is addressed to Scarlett Johansson; he only cares about the ZIP code—and 90210 letters get tossed into the “bound for the West Coast” bucket. Once my letter gets to the post office serving 90210 customers, the individual address will be looked at. It’s the same with IP addresses—something inside that destination network will be responsible for getting it to the right host. It’s the router’s job to figure out what the network address is for any given IP, and the subnet mask is the key.
A subnet mask is a binary pattern that is matched against any IP address to determine which bits belong to the network side of the address, with the binary starting from left to right, turning on all the 1’s until the mask is done. For example, if your subnet mask wants to identify the first 12 bits as the network identification bits, the mask will look like this: 11111111.11110000.00000000.00000000. Translate this to decimal and you get 255.240.0.0. Were you to pair this with an IP address, it would appear something like 12.197.44.8, 255.240.0.0. Another common way of expressing this is to simply use a slash followed by the number of network bits. Continuing our example, the same pair would appear as 12.197.44.8/12.
Here are some rules you’ll need to know about IP addresses and the bits that make them up:
• If all the bits in the host field are 1’s, the address is a broadcast (that is, anything sent to that address will go to everything on that network).
• If all the bits in the host field are set to 0’s, that’s the network address.
• Any combination other than these two present the usable range of addresses in that network.
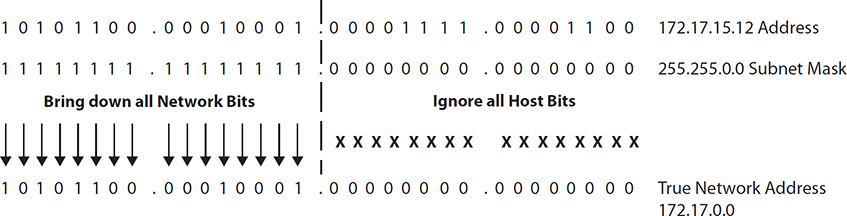
Let’s take a look at an example. Say you have an address of 172.17.15.12, and your subnet mask is 255.255.0.0. To see the network and host portions of the address, first convert the IP address to binary, convert the subnet mask to binary, and stack the two, as shown here:

Every bit from left to right is considered part of the network ID until you hit a zero in the subnet ID. This is all done in the flash of an eye by an XOR comparison (sometimes called an XOR gate) in the router. An XOR compares two binary inputs and creates an output: if the two inputs are the same, the output is 0; if they’re different, the output is 1. If you look at the subnet underneath the address (in binary), it’s easy to see how the XOR creates the network ID, but for most beginners (and not to complicate the issue further), it’s just as easy to draw the line and see where the division happens:
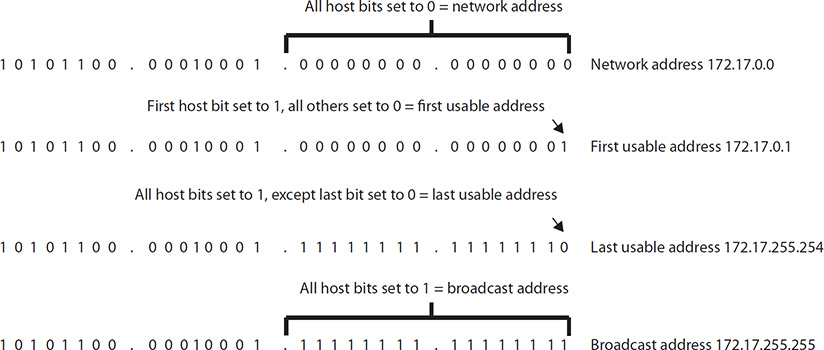
So what this shows us is that the address 172.17.15.12 is part of a network addressed as 172.17.0.0, demonstrated by turning all the host bits to zero, as shown next:
The usable addresses within the 172.17.0.0 network can be found by changing the host bits. The first bit available is the first address, and all bits turned on except the last one comprise the last address (all bits turned on represent the broadcast address). This is displayed in the following illustration:
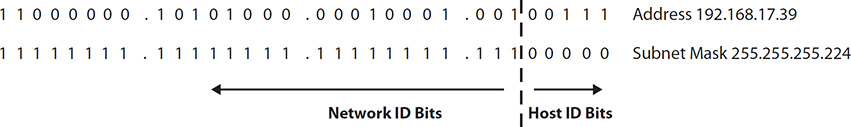
This is easy enough when “the line” is drawn right on a decimal point. But what about when it falls in the middle of an octet? For example, consider the address 192.168.17.39 with a subnet mask of 255.255.255.224. The same process can be followed, but notice the line demarking the network and host bits now falls in the middle of the last octet:
Although it looks difficult, if you follow the same process discussed earlier—bringing down all the network bits and manipulating the host bits to show all zeros, all host bits off except the first, all host bits on except the last, and all host bits on—you can show the network ID, first, last, and broadcast addresses with ease:

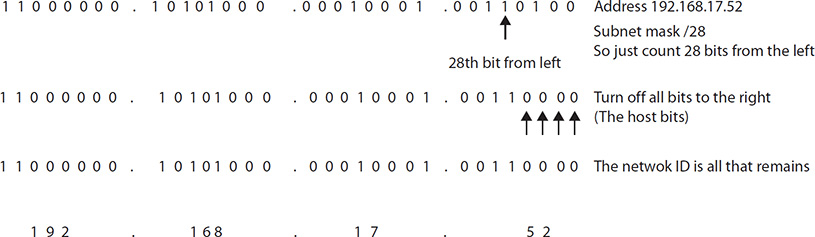
One final thing you may be asked about involving subnetting is applying the mask to a host and determining what network it’s on. For example, suppose you have an IP address of 192.168.17.52/28 and you need to find out what network it’s on. If you use the same principles we just talked about—that is, translate the IP and mask into bits, stack them, draw your line, turn all host bits to zero—you’ll get your answer. Another, quicker way is to simply look at the first 28 bits only and…voilà! See the following illustration for a little more clarity:
Clear as mud, right? Trust me, don’t worry too much about it—we’re only talking a couple of questions here and there. This is a skill you’ll need in the real world, and you’ll find tips and tricks to help you out (for example, the network ID will always be some multiple of the decimal value of the last bit of the mask). Check out Internet resources for subnetting tips and tricks and use whatever feels best for you. Draw out a few using the procedures listed earlier—if you take it out to bits, you’ll never get it wrong—and you’ll be fine. There is a whole lot more involved in addressing and routing that we’re just not going to get into here because it’s not a concern on the exam. You’ll be asked to identify a network ID, or figure out which address belongs to which network, or something like that. And that’s what I’ve laid out here for you.
Scanning Methodology
As you’re probably aware by now, EC-Council is in love with methodology. Sure, in the real world you may not follow the steps blindly in order, but I don’t think that’s the point of listing something in a methodology format. A methodology—no matter how silly it may seem on a test or when you’re sitting there performing a real pen test—ensures you don’t miss anything and that all your bases are covered. In that regard, I guess it’s a lot like a preflight checklist, and this is EC-Council’s version of making sure your scanning flight goes smoothly.
Just as the steps of the overall hacking process can blend into one another, though, keep in mind these steps are simply guidelines and not hard-and-fast rules to follow. When you’re on the job, situations and circumstances will occur that might force you to change the order of things. Sometimes the process of completing one phase will seamlessly blend directly into another. Don’t fret—just go with the flow and get your job done. EC-Council’s scanning methodology phases include the following steps:
1. Check for live systems. Something as simple as a ping can provide this. This gives you a list of what’s actually alive on your network subnet.
2. Check for open ports. Once you know which IP addresses are active, find what ports they’re listening on.
3. Scan beyond IDS. Sometimes your scanning efforts need to be altered to avoid those pesky intrusion detection systems.
4. Perform banner grabbing. Banner grabbing and OS fingerprinting will tell you what operating system is on the machines and which services they are running.
5. Scan for vulnerabilities. Perform a more focused look at the vulnerabilities these machines haven’t been patched for yet.
6. Draw network diagrams. A good network diagram will display all the logical and physical pathways to targets you might like.
7. Prepare proxies. This obscures your efforts to keep you hidden.
This methodology has about as much to do with real life as I have to do with an Oscar nomination, but it’s a memorization effort you have to do. ECC didn’t intend it as much a step-by-step procedure as a checklist to make sure you get to everything you are supposed to during this phase. Despite which order you proceed in, if you hit all the steps, you’re probably going to be successful in your scanning efforts. We’ll delve more into each step later in this chapter, but first we need to revisit some networking knowledge essential for successful scanning.
Identifying Targets
In the ECC scanning methodology, checking for live systems is the first step. The simplest and easiest way to do this is to take advantage of a protocol that’s buried in the stack of every TCP/IP-enabled device on the planet—Internet Control Message Protocol (ICMP). As I’m sure you’re already aware, IP is what’s known as a connectionless, “fire-and-forget” protocol. It creates a packet by taking data and appending a header, which holds bunches of information, including the “From” and “To” addresses, and allows the sender to fire packets away without regard, as quickly as the stack on the machine will allow. This is done by relying on other layer protocols for transport, error correction, and so on.
However, some shortfalls needed to be addressed at the Network layer. IP itself has no error messaging function, so ICMP was created to provide for it. It allows for error messaging at the Network layer and presents the information to the sender in one of several ICMP types. Table 3-2 lists some of the more relevant message type codes you’ll need to know for the exam. The most common of these are Type 8 (Echo Request) and Type 0 (Echo Reply). An ICMP Type 8 packet received by a host tells the recipient, “Hey! I’m sending you a few packets. When you get them, reply with the same number so I know you’re there.” The recipient will respond with an ICMP Type 0, stating, “Sure, I’m alive. Here are the data packets you just sent me as proof !”

Table 3-2 Relevant ICMP Message Types
Because ICMP is built into each TCP/IP device and the associated responses provide detailed information about the recipient host, it makes a good place to start when network scanning. For example, consider an Echo Request (Type 8) sent to a host that returns a Type 3. The code could tell us whether the host is down (Code 1), the network route is missing or corrupt in our local route tables (Type 0), or a filtering device, such as a firewall, is preventing ICMP messages altogether (Type 13).
A few intrusion detection system (IDS) signatures do look for this. For example, a lot of ping utilities designed to take advantage of this have default signatures that any decent IDS can pick up on; in Nmap, a “0 byte field” can trigger it, for example. Windows and other operating systems have specific defaults that are supposed to be found in the packet, and their alteration or omission can also trigger a hit. But none of this changes the fact that it’s still a cool hack.
This process, called a ping, has been part of networking since its inception, and combining pings to every address within a range is known as a ping sweep. A ping sweep is the easiest method available to identify active machines on the network, and there are innumerable tools to help you pull it off (Figure 3-7 shows Zenmap, Nmap’s GUI Windows version, pulling it off on my little wireless network). Just keep in mind that this is not necessarily the only, or even best, way to do it. Although ICMP is part of every TCP/IP stack, it’s not always enabled. In fact, many administrators will disable ping responses on many network systems and devices and will configure firewalls to block them. Lastly, if you add IPv6 to the mix it really muddies the waters. Scanning in IPv6 is much more difficult and complex, and ping sweeps often don’t work at all in most tools.

Figure 3-7 Using Nmap to perform a ping sweep
Additionally, not only will a great many devices not respond to the ping, the actual ping sweep itself can be noisy, and the systems may alert anyone and everyone as to what’s going on. Network intrusion detection systems (NIDSs) and host-based IDS (HIDS) can easily and readily pick up on a ping sweep from an external source if not carried out slowly and with some stealth. With this in mind, be cautious and deliberate with your sweep—slow and random are your friends here. Remember, hacking isn’t a race; it’s a test of will, patience, and preparation.
Several applications are available to make the ping sweep as simple as possible for you to pull off. Nmap is, of course, probably the most referenced scanning tool on the exam and in the real world. Angry IP Scanner is another well-know tool; just be careful with it because a lot of antivirus programs consider it a virus. Some other tools of note are SolarWinds Engineer Toolset, Network Ping, OPUtils, SuperScan, Advanced IP Scanner, and a wacky little tool called Pinkie.
One last quick note on scanning for active machines before we move forward: Remember at the opening of this section that I mentioned the scanning steps may bleed into one another? Identifying active machines on the network using a ping sweep is not the only method available. Sometimes it’s just as easy to combine the search for active machines with a port scan, especially if you’re trying to be sneaky about it. Granted, this isn’t the steadfast “follow the methodology” mindset of the exam, but it is reality. So, what is a port scan? Glad you asked.
Port Scanning
Imagine you’re a bad guy in a movie sizing up a neighborhood for a potential run of nighttime thievery. You’ll probably do a little harmless driving around, checking out the perimeter and seeing what’s between the neighborhood and the rest of the world. You’ll also pay attention to which houses are “live,” with residents and stuff inside you may find valuable. But that gives you only background information. It’s really valuable if you can figure out which doors are locked, which windows are open, and which ones have alarms on them. Walk with me in the virtual world, my movie-villain thief, and let’s go knock on some computer doors to see what’s hiding there.
“How do we do it?” you may ask. The answer is, of course, by using several different methods and with several different tools. We can’t possibly cover them all here, but we’ll definitely spend some time on those you’ll see most often on your exam. Regardless, all port scanners work by manipulating Transport layer protocol flags in order to identify active hosts and scan their ports. And now that you know a little more about this process, let’s take a look at the different types of port scans we have available to us.
Port Scan Types
A scan type will be defined by three things: what flags are set in the packets before delivery, what responses you expect from ports, and how stealthily the scan works. As far as your exam is concerned, count on being asked about each of these scan types at least once. Generally speaking, there are seven generic scan types for port scanning:
• Full connect Also known as a TCP connect or full open scan, this runs through a full connection (three-way handshake) on ports, tearing it down with an RST at the end. It is the easiest to detect but it’s possibly the most reliable. Open ports will respond with a SYN/ACK, and closed ports will respond with an RST.
• Stealth Also known as a half-open scan (and also as a SYN scan). Only SYN packets are sent to ports (no completion of the three-way handshake ever takes place). Responses from ports are the same as they are for a TCP connect scan. This technique is useful in hiding your scanning efforts, possibly bypassing firewalls and monitoring efforts by hiding as normal traffic (it simply doesn’t get noticed because there is no connection to notice).
• Inverse TCP flag This scan uses the FIN, URG, or PSH flag (or, in one version, no flags at all) to poke at system ports. If the port is open, there will be no response at all. If the port is closed, an RST/ACK will be sent in response. You know, the inverse of everything else.
• XMAS A Christmas scan is so named because all flags are turned on, so the packet is “lit up” like a Christmas tree. Port responses are the same as with an inverse TCP scan. XMAS scans do not work against Microsoft Windows machines due Microsoft’s TCP/IP stack implementation (Microsoft TCP/IP is not RFC 793 compliant).
• ACK flag probe According to ECC, there are two versions of this scan, both of which use the same method: the attacker sends the ACK flag and looks at the return header (TTL or Window fields) to determine the port status. In the TTL version, if the TTL of the returned RST packet is less than 64, the port is open. In the Window version, if the WINDOW size on the RST packet has anything other than zero, the port is open.
• IDLE This uses a spoofed IP address (an idle zombie system) to elicit port responses during a scan. Designed for stealth, this scan uses a SYN flag and monitors responses as with a SYN scan.
All of these scans should be easy enough to decipher given a cursory understanding of TCP flags and what each one is for, with the possible exception of the IDLE scan. Sure, the IDLE scan makes use of TCP flags (the SYN and ACK flags, in this case), but the way it’s all used is brilliant (heck, it’s almost elegant) and provides the additional benefit of obfuscation. Because the machine actually receiving the response from the targets is not your own, the source of the scan is obscured. Confused? No worries—keep reading.
Every IP packet uses something called an IP identifier (IPID) to help with the pesky problem of keeping track of fragmentation (IP packets can be only so big, so a single packet is sometimes fragmented and needs to be put back together at the destination). Most systems simply increase this IPID by one when they send a packet out. For example, the first packet of the day might have an IPID of 31487, and the second 31488. If you understand this concept, can spoof an IP address, and have a remote machine that’s not doing anything, this all makes perfect sense.
First, an attacker sets up or makes use of a machine that isn’t doing anything at all (sitting IDLE). He next sends a packet (SYN/ACK) to this idle machine and makes note of the IPID in response; the zombie machine isn’t expecting a SYN/ACK and will respond with an RST packet, basically stating “Can we start over? I don’t really recognize this communications session.” With the current IPID number in hand, he sends a packet with a spoofed IP (matching the lazy zombie system) and the SYN flag set to the target. If the port is open, the target will happily respond to the zombie with a SYN/ACK packet to complete the three-way handshake. The zombie machine will respond to the target system with an RST packet, which of course increments the IPID by one. All the attacker has to do now is send another SYN/ACK to the zombie and note the IPID. If it increased by two, the idle system sent a packet and, therefore, the port is open. If it’s not open, it will have increased by only one. If this seems clear as mud or you’re one of those “visual learners,” check out Figure 3-8 for an example of an open port exchange, and see Figure 3-9 for the closed port example.

Figure 3-8 IDLE scanning: port open
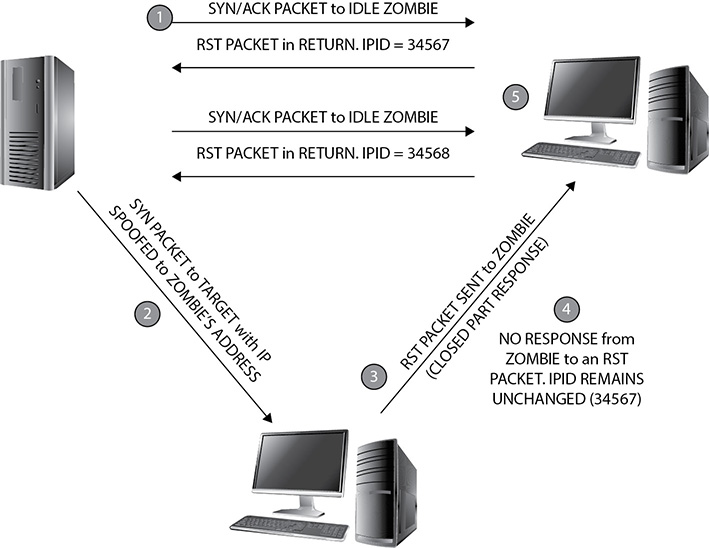
Figure 3-9 IDLE scanning: port closed
In addition to knowing how to read the responses from an IDLE scan, you’ll be asked repeatedly on the exam about the other scan types and what response to expect from an open or closed port. If you know the flags and what they do, this is easy. If not, Table 3-3 should be of help in studying this.

Table 3-3 Network Scan Types
Lastly, there’s one more that may see the light of day on your exam, so we’ll cover it here just in case. A UDP scan is exactly what it sounds like: send a datagram to the port and see what you get in response. Because there is no handshake, if the port is open, you won’t receive a thing back—if the port is closed, you’ll receive an ICMP port unreachable message.
Nmap
So now that we know what the scan types are called, how do we pull them off? Why with a port scanner, of course, and without a doubt, the most widely used scanning and enumeration tool on the planet is Nmap. Nmap can perform many different types of scans (from simply identifying active machines to port scanning and enumeration) and can also be configured to control the speed at which a scan operates. In general, the slower the scan, the less likely you are to be discovered. It comes in both a command-line version and a GUI version (now known as Zenmap), works on multiple OS platforms, and can even scan over TCP and UDP. And the best thing of all? It’s free.
The Nmap syntax is fairly straightforward:
![]()
The target for Nmap can be a single IP address, multiple individual IPs separated by spaces, or an entire subnet range (using CIDR notation). For example, to scan a single IP, the command might look like
![]()
whereas scanning multiple IPs would look like
![]()
and scanning an entire subnet would appear as
![]()
Starting Nmap without any of the options runs a “regular” scan and provides information for you. But to get really sneaky and act like a true ethical hacker, you’ll need to learn the option switches—and there are a bunch of them. The good news is, almost an endless assortment of help is available for you on the Web. For example, the web page located at https://svn.nmap.org/nmap/docs/nmap.usage.txt shows a screen pull of Nmap run without any option switches or targets set at all, and a simple search for “Nmap switches” will provide tons of sites with full-syntax command samples for you to mix around for your own needs. For a full and complete rundown of every switch and option, visit Nmap’s man page, or check with the originator’s documentation page at http://nmap.org/docs.html. Table 3-4 lists some of the more relevant Nmap switches you’ll need to know.
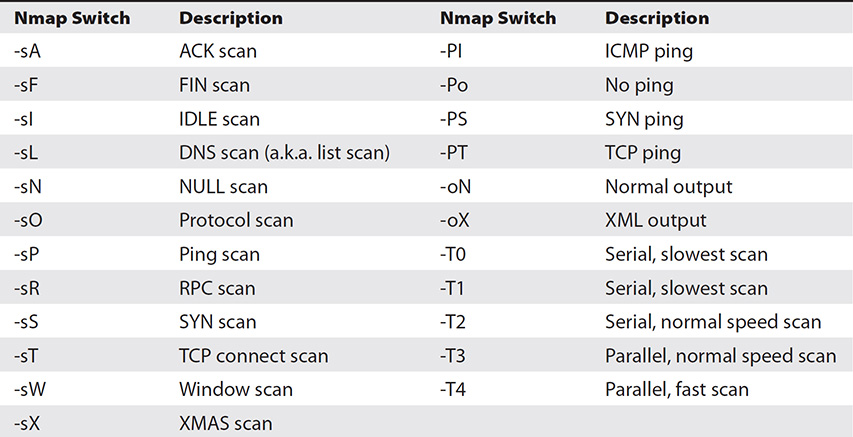
Table 3-4 Nmap Switches
As you can see, quite a few option switches are available for the command. The “s” commands determine the type of scan to perform, the “P” commands set up ping sweep options, and the “o” commands deal with output. The “T” commands deal with speed and stealth, with the serial methods taking the longest amount of time. Parallel methods are much faster because they run multiple scans simultaneously. Again, the slower you run scans, the less likely you are to be discovered. The choice of which one to run is yours.
Combining option switches can produce specific output on any given target. For example’s sake, suppose you wanted to run a SYN port scan on a target as quietly as possible. The syntax would look something like this:
![]()
If you wanted an aggressive XMAS scan, perhaps the following might be to your liking:
![]()
The combinations are endless and provide worlds of opportunity for your port-scanning efforts. You’ll need to know Nmap switches for the port scans very well, and how to compare different variations. For example, you can certainly turn on each switch you want for each feature, but using something like the -A switch enables OS detection, version detection, script scanning, and traceroute automatically for you.
Nmap handles all scan types we discussed in the previous section, using switches identified earlier. In addition to those listed, Nmap offers a “Window” scan. It works much like the ACK scan and provides information on open ports. Many more switches and options are available for the tool. Again, although it’s a good bet to study the information presented here, you absolutely need to download and play with the Nmap tool to be successful on the exam and in your career.
Knowing how to recognize and read Nmap output is just as important as learning the syntax of the command. The GUI version of the tool, Zenmap, makes reading this output easy, but the command-line output is just as simple. Additionally, the output is available via several methods. The default is called interactive, and it is sent to standard output (text sent to the terminal). Normal output displays less run-time information and fewer warnings because it is expected to be analyzed after the scan completes rather than interactively. You can also send output as XML (which can be parsed by graphical user interfaces or imported into databases) or in a “greppable” format (for easy searching). Figure 3-10 shows a brief example. Ports are displayed in output as open, closed, or filtered. Open is obvious, as is closed. Filtered means a firewall or router is interfering with the scan.
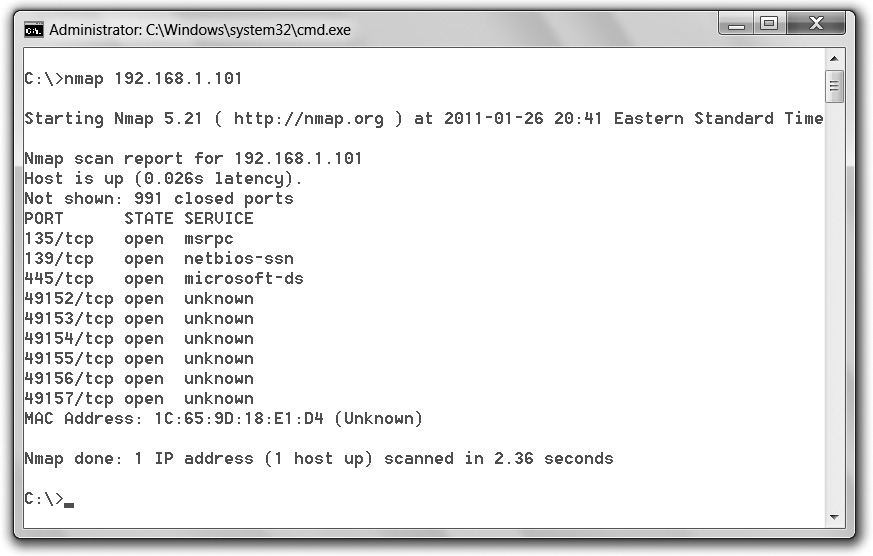
Figure 3-10 Nmap output
Hping
Although Nmap is the unquestioned leader of the port-scanning pack, plenty of other tools are available that are just as adept. Hping (Hping2 or Hping3) is another powerful tool for both ping sweeps and port scans, and is also a handy packet-crafting tool for TCP/IP. Hping works on Windows and Linux versions and runs nearly any scan Nmap can put out. The only real downside, for people like me who prefer pictures and clicking things, is that it’s still a command-line-only tool. Just as with Nmap, Hping3 has specific syntax for what you’re trying to accomplish, with tons of switches and options. For example, a simple ping sweep can be accomplished by typing in hping3 -1 IPaddress. A full and complete breakdown of all switches and syntax can be found on Hping’s man page, located www.hping.org/manpage.html. For study purposes, Table 3-5 lists a few of the switches you are likely to see on the exam.
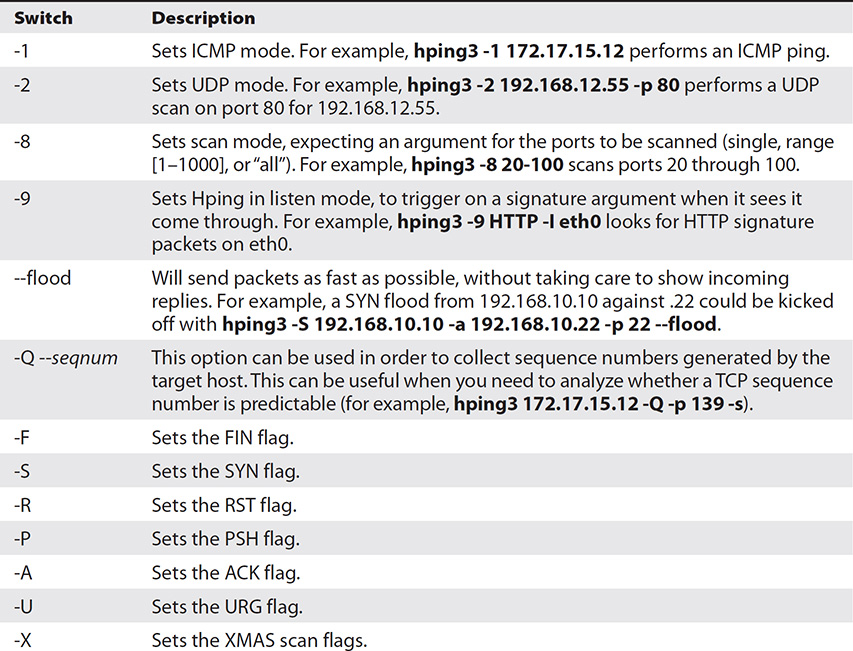
Table 3-5 Hping Switches
Other Scanning Tools
SuperScan, available as a free download (evaluation) from McAfee, is another easy-to-use GUI-based program. It works well and offers several options from an intuitive front-end interface, providing for ping sweeps and port scans against individual systems or entire subnets. Figure 3-11 shows SuperScan’s interface.

Figure 3-11 SuperScan
Some other tools for accomplishing port scanning fun include Advanced Port Scanner, MegaPing, Net Tools, and PRTG Network Monitor (be sure to check the tool list at the end of this book for more). And, of course, we shouldn’t neglect mentioning scanning tools designed for mobile use. IP Scanner (10base-t.com), Fing (www.fing.io), Hackode (play.google.com), zANTi (www.zimperium.com), and PortDroid Network Analysis (play.google.com) are all examples of tools designed for your mobile device, and all are worth your time in downloading and learning.
Regardless of whether your choice is running Nmap on a Linux machine, harnessing command-line option power like a pro, or using SuperScan’s simple GUI interface on a Windows machine, the goal is the same. Port scanning identifies which ports are open and gives you more information in building your attack vectors. Each scan type you attempt will react differently and take different lengths of time to pull off (a UDP scan of Linux machines can take a very long time, for instance), and you’ll definitely need to know the output to look for with each one. However, the tools are all designed to achieve the same overall end.
Evasion
Want more fun in scanning? Try doing it without being caught. Whether you’re port scanning, searching for wireless openings, or just wandering about looking for physical security clues, stealth is always important. Hiding your activities from prying security-professional eyes is something you’ll need to prepare for and master in each step of the hacking phases, and scanning is no exception. Sometimes scanning can be interrupted by pesky firewalls or monitoring devices, and you’ll be forced to disguise who you are and what you’re up to. Options for accomplishing this include fragmenting packets, spoofing an IP address, source routing, and proxies.
One of the most common (and possibly elegant) methods used to evade detection by an IDS is fragmenting packets. The idea isn’t to change the scan itself—you can still run a full connect scan, for instance—but to crack apart the packets before they’re sent so the IDS can’t recognize them. If you split the TCP header into several packets, all the IDS sees is useless chatter. Assuming you’re not flooding the network segment too fast with them, your scanning won’t even be noticed. For example, an Nmap command like nmap -sS -A -f 172.17.15.12 might work to fragment a SYN scan (while OS fingerprinting along the way).
Spoofing an IP address is exactly what it sounds like: the hacker uses a packet-crafting tool of some sort to obscure the source IP address of packets sent from her machine. Many tools are available for this—Hping, Scapy, and Komodia, for example. You can also find this functionality built into a variety of other scanning tools. Ettercap and Cain, usually thought of more for their sniffing capabilities, provide robust and powerful spoofing capabilities as well; heck, even Nmap can spoof if you really want. Just be cautious in spoofing—sometimes you can spoof so well the information you’re working so hard to obtain never finds its way back to you.
Source routing provides yet another means to disguise your identity on a network, assuming you come across something designed circa 1995. It was originally designed to allow applications to specify the route a packet takes to a destination, regardless of what the route tables between the two systems say, but was deprecated long, long ago. Its main benefit used to be assisting network managers in forcing traffic around areas of potential congestion. How was this useful to a hacker? The attacker could use an IP address of another machine on the subnet and have all the return traffic sent back, regardless of which routers are in transit. Protections against source-routing attacks are prevalent and effective, not to mention most firewalls and routers detect and block source-routed packets, so this just won’t work on modern networks. ECC loves it, though, and it’s testable, so learn it.
Finally, our last method of IDS evasion (at least so far as your exam is concerned) involves employing proxies to hide behind. A proxy is nothing more than a system you set up to act as an intermediary between you and your targets. In many instances, proxies are used by network administrators to control traffic and provide additional security for internal users, or for things like remotely accessing intranets. Hackers, though, can use that technology in reverse—sending commands and requests to the proxy and letting the proxy relay them to the targets. So, for evasion purposes, anyone monitoring the subnet sees the proxy trying all these actions, not the hacker.
Proxying can be done from a single location or spread across multiple proxies to further disguise the original source. Hundreds of free, public proxies are available to sign up for, and a simple Internet search will point you in the right direction. If you want to set up proxy chains, where multiple proxies further hide your activities, you can use tools such as Proxy Switcher (proxyswitcher.com), Proxy Workbench (proxyworkbench.com), ProxyChains (http://proxychains.sourceforge.net/), SoftCab’s Proxy Chain Builder (www.softcab.com/download.php), CyberGhost (cyberghostvpn.com), and Proxifier (www.proxifier.com).
Another great method for anonymity on the Web is The Onion Routing (Tor). Tor basically works by installing a small client on the machine, which then gets a list of other clients running Tor from a directory server. The client then bounces Internet requests across random Tor clients to the destination, with the destination end having very little means to trace the original request back. Communication between Tor clients is encrypted, with only the last leg in the journey—between the Tor “cloud” and the destination—sent unencrypted. One really important thing to keep in mind, though, is that anyone can be a Tor endpoint, so signing up to voluntarily have goodness-knows-what passing through your machine may not be in your best interests. Additionally, Tor is highly targeted, and there are multiple lawsuits pending—so be careful.
Finally, another ridiculously easy method for disguising your identity, at least for port 80 (HTTP) traffic, is to use an anonymizer. Anonymizers are services on the Internet that make use of a web proxy to hide your identity. Thousands of anonymizers are available—simply do a Google search and you’ll see what I mean. Be careful in your choice, though; some of them aren’t necessarily safe, and their owners are set up specifically to steal information and plant malware. Some anonymizers referenced by ECC are Guardster (guardster.com), Ultrasurf (ultrasurf.us), Psiphon (psiphon.ca), and Tails (tails.boum.org). Tails isn’t an application, per se; it’s an actual live OS you can run from a USB that anonymizes the source and leaves no trace on the system you’re on. Neat!
Nbtstat isn’t the only tool available for NetBIOS enumeration. SuperScan (www.mcafee.com) is not only a port scanner—it’s also a NetBIOS enumeration engine and a Windows host enumeration engine, can produce great reporting, and also does a fine job of banner grabbing. Hyena (www.systemtools.com) is another multipurpose tool to mention. It’s a GUI-based tool that shows shares, user logon names, services, and other data that would be useful in securing Microsoft systems. Some other tool options include Winfingerprint (https://packetstormsecurity.com/files/38356/winfingerprint-0.6.2.zip.html), NetBIOS Enumerator (nbtenum.sourceforge.net), and NSAuditor (nsauditor.com).
SNMP Enumeration
Another enumerating technique of note for your exam is exploiting Simple Network Management Protocol (SNMP). SNMP was designed to manage IP-enabled devices across a network. As a result, if it is in use on the subnet, you can find out loads of information with properly formatted SNMP requests. Later versions of SNMP make this a little more difficult, but plenty of systems are still using the protocol in version 1.
SNMP consists of a manager and agents, and it works much like a dispatch center. A central management system set up on the network will make requests of SNMP agents on the devices. These agents respond to the requests by going to a big virtual filing cabinet on each device called the Management Information Base (MIB). The MIB holds information, and it’s arranged with numeric identifiers (called object identifiers, or OIDs) from general information to the very specific. The request points out exactly what information is requested from the MIB installed on that device, and the agent responds with only what is asked for. MIB entries can identify what the device is, what operating system is installed, and even usage statistics. In addition, some MIB entries can be used to actually change configuration settings on a device. When the SNMP management station asks a device for information, the packet is known as an SNMP GET request. When it asks the agent to make a configuration change, the request is an SNMP SET request.
SNMP uses a community string as a form of password. The read-only version of the community string allows a requester to read virtually anything SNMP can drag out of the device, whereas the read-write version is used to control access for the SNMP SET requests. Two major downsides are involved in the use of both these community string passwords. First, the defaults, which are all active on every SNMP-enabled device right out of the box, are ridiculously easy. The read-only default community string is public, whereas the read-write string is private. Assuming the network administrator left SNMP enabled and/or did not change the default strings, enumerating with SNMP is a snap.
The second problem with the strings is that they are sent in clear text (at least in SNMPv1). So, even if the administrators took the time to change the default community strings on all devices (and chances are better than not they’ll miss a few here and there), all you’ll need to do to grab the new strings is watch the traffic—you’ll eventually catch them flying across the wire. However, keep in mind that versioning matters when it comes to SNMP. Because SNMP version 3 encrypts the community strings, enumeration is harder to pull off. Additionally, although public and private are the default strings, some devices are configured to use other strings by default. It might be worthwhile researching them before you begin your efforts.
Tools you can use to enumerate with SNMP are seemingly endless. Engineer’s Toolset (solarwinds.com), SNMPScanner (secure-bytes.com), OpUtils 5 (www.manageengine.com), and SNScan (mcafee.com) are all viable options.
Other Enumeration Options
The Lightweight Directory Access Protocol (LDAP) is designed to be queried, so it presents a perfect enumeration option. LDAP sessions are started by a client on TCP port 389 connecting to a Directory System Agent (DSA). The request queries the hierarchical/logical structure within LDAP and returns an answer using Basic Encoding Rules (BER). So what can you get out of LDAP using this? Oh, nothing important. Just things like valid user names, domain information, addresses and telephone numbers, system data, and organizational structure, among other items. Tools such as Softerra (ldapadministrator.com), JXplorer (jxplorer.com), Lex (ldapexplorer.com), and LDAP Admin Tool (sourceforge.net) all work well and are fairly intuitive and user friendly. Oh, and don’t forget the built-in Active Directory Explorer in Windows systems (Microsoft’s proprietary-ish version of LDAP). It can make LDAP information gathering quick and easy.
Other protocols of note for enumeration efforts include NTP and SMTP. Network Time Protocol (running UDP on port 123) does exactly what the name implies—it sets the time across your network. Querying the NTP server can give you information such as a list of systems connected to the server (name and IP) and possibly IP addresses of internal systems (that is, if the NTP box is in the DMZ and serves machines inside the network, information can be pulled on the internal machines). Several tools for NTP enumeration are available, including NTP Server Scanner (bytefusion.com) and AtomSync (atomsync.com), but you can also use Nmap and Wireshark if you know what you’re looking for. Commands for NTP enumeration include ntptrace, ntpdc, and ntpq.
We’ve already talked some about e-mail information gathering in previous sections, but a little more info on Simple Mail Transfer Protocol (SMTP) is required here for your exam and for enumeration. SMTP holds multiple commands (12), but three are commonly used and will probably find their way on your exam—VRFY (validates user), EXPN (provides the actual delivery addresses of mailing lists and aliases), and RCPT TO (defines recipients)—and servers respond differently to these commands. Their responses can tell us which are valid and which are invalid user names. An example of these responses in action can be seen in Figure 3-13.

Figure 3-13 SMTP commands
Chapter Review
Scanning is the process of discovering systems on the network and taking a look at what open ports and applications may be running. EC-Council’s scanning methodology phases include the following: check for live systems, check for open ports, scan beyond IDS, perform banner grabbing, scan for vulnerabilities, draw network diagrams, and prepare proxies.
When two TCP/IP-enabled hosts communicate with each other, data transfer is either connectionless or connection-oriented. Connectionless communication is “fire and forget,” meaning the sender can simply fire as many segments as it wants out to the world, relying on other upper-layer protocols to handle any problems. At the Transport layer, connectionless communication is accomplished with UDP. Application protocols that make use of this transport method are moving very small amounts of data and usually are moving them inside a network structure (not across the Internet). Examples of protocols making use of UDP are TFTP, DNS, and DHCP.
Connection-oriented communications using TCP are slower than connectionless but are a much more orderly form of data exchange. Senders will reach out to recipients, before data is ever even sent, to find out whether they’re available and whether they’d be willing to set up a data channel. Once data exchange begins, the two systems continue to talk with one another. Six flags can be set in the TCP header: URG (Urgent), ACK (Acknowledgment), PSH (Push), RST (Reset), SYN (Synchronize), and FIN (Finish). A session must be established between two systems for data exchange. This is accomplished via a three-way handshake, listed as “SYN, SYN/ACK, ACK.”
The source and destination port fields in TCP or UDP communication define the protocols that will be used to process the data. The port numbers range from 0 to 65,535 and are split into three different groups: well-known (0–1023), registered (1024–49,151), and dynamic (49,152–65,535). A system is said to be listening for a port when it has that port open. Typing netstat -an displays all connections and listening ports, with addresses and port numbers in numerical form.
IPv4 has three main address types—unicast (acted on by a single recipient), multicast (acted on only by members of a specific group), and broadcast (acted on by everyone in the network). To determine which network an IP address belongs to, the address must be looked at as network bits and host bits. A subnet mask is a binary pattern that is matched against any IP address to determine which bits belong to the network side of the address. Rules involving IPv4 addresses include the following:
• If all the bits in the host field are 1’s, the address is a broadcast (that is, anything sent to that address will go to everything on that network).
• If all the bits in the host field are set to 0’s, that’s the network address.
• Any combination other than these two present the usable range of addresses in that network.
To view the network and host portions of an address, first convert the IP address to binary, convert the subnet mask to binary, and stack the two. Every bit from left to right is considered part of the network ID until you hit a zero in the subnet ID. Next, you can manipulate the host bits to show all zeros, set all the host bits off except the first, set all the host bits on except the last, and set all the host bits on to show the network ID and the first, last, and broadcast addresses, respectively.
A ping sweep is the easiest method for identifying active machines on the network. An ICMP Echo Request (Type 8) message is sent to each address on the subnet. Those that are up (and not filtering ICMP) reply with an ICMP Echo Reply (Type 0).
Port scanning is the method by which systems on a network are queried to see which ports they are listening to. One of the more important port-scanning tools available is Nmap, which can perform many different types of scans (from simply identifying active machines to port scanning and enumeration) and can also be configured to control the speed at which the scan operates. In general, the slower the scan, the less likely you are to be discovered and the more reliable the results. Nmap comes in both a command-line version and a GUI version (known as Zenmap) and works on multiple OS platforms. The Nmap syntax is simple:
![]()
Multiple scan options (or switches) are available, and combining them can produce several scan options. The “s” commands determine the type of scan to perform, the “P” commands set up ping sweep options, and the “o” commands deal with output. The “T” commands deal with speed and stealth, with the serial methods taking the longest amount of time. Parallel methods are much faster because they run multiple scans simultaneously.
There are several generic scan types for port scanning: full connect (also known as TCP connect or full open scan), stealth (also known as a half-open scan and as a SYN scan), inverse TCP flag, XMAS, ACK flag probe, and IDLE. Full (TCP connect) and stealth scans receive a SYN/ACK on open ports and an RST on closed ports. XMAS and inverse TCP scans receive no response on an open port and an RST on closed ports. Additionally, neither work on Windows machines.
Hping (Hping2 or Hping3) is another powerful tool for both ping sweeps and port scans, and is also a handy packet-crafting tool for TCP/IP. Hping works on Windows and Linux versions and runs nearly any scan Nmap can put out. A full and complete breakdown of all switches and syntax can be found on Hping’s man page (www.hping.org/manpage.html).
Hiding your activities from prying security-professional eyes can be done using fragmented packets, IP address spoofing, source routing, and proxies. In fragmenting packets, the idea isn’t to change the scan itself but to crack apart the packets before they’re sent so that the IDS can’t recognize them. If you split the TCP header into several packets, all the IDS may see is useless chatter. For example, an Nmap command like nmap -sS -A -f 172.17.15.12 might work to fragment a SYN scan (while OS fingerprinting along the way).
Spoofing an IP address is exactly what it sounds like: you use a packet-crafting tool of some sort to obscure the source IP address of packets sent from your machine. Many tools are available for this—Hping, Scapy, and Komodia, for example. Spoofing an IP address means any data coming back to the fake address will not be seen by the attacker. For example, if you spoof an IP address and then perform a TCP scan, the information won’t make its way back to you.
Source routing was originally designed to allow applications to specify the route a packet takes to a destination, regardless of what the route tables between the two systems say. The attacker can use an IP address of another machine on the subnet and have all the return traffic sent back, regardless of which routers are in transit. Protections against source-routing attacks are prevalent and effective—not to mention most firewalls and routers detect and block source-routed packets—so this may not be your best option.
A proxy is nothing more than a system you set up to act as an intermediary between you and your targets. In many instances, proxies are used by network administrators to control traffic and provide additional security for internal users, or for things like remotely accessing intranets. Hackers, though, can use that technology in reverse—sending commands and requests to the proxy and letting the proxy relay them to the targets. So, for evasion purposes, anyone monitoring the subnet sees the proxy trying all these actions, not the hacker. It’s important to remember a proxy isn’t just a means for obfuscating the source. Proxies are used for a variety of things.
Proxying can be done from a single location or spread across multiple proxies to further disguise the original source. If you want to set up proxy chains, where multiple proxies further hide your activities, you can use tools such as Proxy Switcher, Proxy Workbench, ProxyChains, SoftCab’s Proxy Chain Builder, and Proxifier.
The Onion Routing (Tor) basically works by installing a small client on the machine, which then gets a list of other clients running Tor from a directory server. The client then bounces Internet requests across random Tor clients to the destination, with the destination end having very little means to trace the original request back. Communication between Tor clients is encrypted, with only the last leg in the journey—between the Tor “cloud” and the destination—sent unencrypted.
Another method for disguising your identity, at least for port 80 (HTTP) traffic, is to use an anonymizer. Anonymizers are services on the Internet that make use of a web proxy to hide your identity. Some anonymizers referenced by ECC include Guardster (guardster.com), Ultrasurf (ultrasurf.us), Psiphon (psiphon.ca), and Tails (tails.boum.org). Tails isn’t an application, per se; it’s an actual live OS you can run from a USB that anonymizes the source and leaves no trace on the system you’re on.
Vulnerability scanning involves running a tool against a target to see what vulnerabilities it may hold. Scanners of note include Nessus, MBSA, Retina CS, GFI LanGuard, Qualys FreeScan, and OpenVAS (www.openvas.com).
When we enumerate a target, we’re moving from passive information gathering to a much more active state. No longer satisfied with just knowing which ports are open, we now want to find things such as open shares and any easy-to-grab user account information.
Microsoft Windows machines—everything from old Windows 2000 to Windows 10 systems—will constitute the vast majority of your targets in the real world, so it’s important to know some security basics before enumerating them. User rights are granted via an account’s membership within a group and determine which system tasks an account is allowed to perform. Permissions are used to determine which resources an account has access to. The method by which Windows keeps track of which account holds what rights and permissions comes down to SIDs and RIDs. A security identifier (SID) identifies user, group, and computer accounts and follows a specific format. A resource identifier (RID) is a portion of the overall SID, identifying a specific user, computer, or domain.
SIDs are composed of an S, followed by a revision number, an authority value, a domain or computer indicator, and a RID. The RID portion of the identifier starts at 500 for the administrator account. The next account on the system, Guest, is RID 501. All users created for the system start at 1000 and increment from that point forward—even if their user names are re-created later.
Accounts are identified by their SID (and associated RID), of course, but the passwords for them must be stored somewhere, too. In Windows, passwords are stored in C:WindowsSystem 32ConfigSAM. The SAM database holds encrypted versions of all the local passwords for accounts on the machine. For those machines that are part of a domain, the passwords are stored and handled by the domain controller.
Linux systems use a user ID (UID) and a group ID (GID) in much the same way as Windows uses SIDs and RIDs. On a Linux machine, these can be found in the /etc/passwd file.
Banner grabbing involves sending an unsolicited request to an open port to see what, if any, default message (banner) is returned. Depending on what version of the application is running on the port, the returned banner (which could be an error message, HTTP header, or login message) can indicate a potential vulnerability for the hacker to exploit. ECC defines two different categories of banner grabbing—active and passive. Active banner grabbing involves sending specially crafted packets to remote systems and comparing responses to determine the OS. Passive banner grabbing involves reading error messages, sniffing network traffic, or looking at page extensions.
A common method of performing banner grabbing is to use a simple tool already built into most operating systems, Telnet. For example, if you simply type telnet <IPaddress>, you’ll send TCP packets to the recipient with the destination port set to 23. However, you can also point it at any other port number explicitly to test for connectivity. If the port is open, you’ll generate some form of banner response.
Another tool for banner grabbing (and other uses) is netcat. Known as the “Swiss Army knife of hacking tools,” netcat is a command-line networking utility that reads and writes data across network connections using TCP/IP. It’s also a tunneling protocol, a scanner, and an advanced hacking tool. To try banner grabbing with this little jewel, simply type nc <IPaddress or FQDN> <port number>.
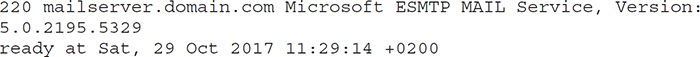
NetBIOS, a browser service that’s part of Microsoft Windows operating systems, was designed to host information about all the machines within the domain or TCP/IP network segment. A NetBIOS name is a 16-character ASCII string used to identify network devices—15 characters are used to define the name while the 16th character is reserved for the service or name record type. The built-in utility nbtstat can be used to provide NetBIOS information for enumeration purposes. Within the nbtstat response, the code, type, and name can be used to gather information. NetBIOS enumeration questions will generally be about three things:
• Identifying the code and type
• The fact NetBIOS name resolution doesn’t work at all on IPv6
• Which tools can be used to perform it
SNMP was designed to manage IP-enabled devices across a network. As a result, if it is in use on the subnet, you can find out loads of information with properly formatted SNMP requests. SNMP consists of a manager and agents, and it works much like a dispatch center. A central management system set up on the network will make requests of SNMP agents on the devices. These agents respond to the requests by going to a big virtual filing cabinet on each device called the Management Information Base (MIB). The MIB holds information, and it’s arranged with numeric identifiers (called object identifiers, or OIDs), from general information to the very specific. The request points out exactly what information is requested from the MIB installed on that device, and the agent responds with only what is asked for. MIB entries can identify what the device is, what operating system is installed, and even usage statistics. In addition, some MIB entries can be used to actually change configuration settings on a device. When the SNMP management station asks a device for information, the packet is known as an SNMP GET request. When it asks the agent to make a configuration change, the request is an SNMP SET request.
There are two types of managed objects in SNMP—scalar and tabular. Scalar defines a single object, whereas tabular defines multiple related objects that can be grouped together in MIB tables.
SNMP uses a community string as a form of password. The read-only version of the community string allows a requester to read virtually anything SNMP can drag out of the device, whereas the read-write version is used to control access for the SNMP SET requests. Two major downsides are involved in the use of both these community string passwords. First, the defaults, which are all active on every SNMP-enabled device right out of the box, are ridiculously easy. The read-only default community string is public, whereas the read-write string is private. Assuming the network administrator left SNMP enabled and/or did not change the default strings, enumerating with SNMP is a snap.
Lightweight Directory Access Protocol (LDAP) is designed to be queried, so it presents a perfect enumeration option. LDAP sessions are started by a client on TCP port 389 connecting to a Directory System Agent (DSA). The request queries the hierarchical/logical structure within LDAP and returns an answer using Basic Encoding Rules (BER). You can pull valid user names, domain information, addresses and telephone numbers, system data, and organizational structure information this way. Tools include Softerra (ldapadministrator.com), JXplorer (jxplorer.com), Lex (ldapexplorer.com), LDAP Admin Tool (sourceforge.net), and the built-in Active Directory Explorer in Windows systems.
Network Time Protocol (running UDP on port 123) sets the time across your network, and querying the NTP server can give you information such as a list of systems connected to the server (name and IP) and possibly the IP addresses of internal systems (if the NTP box is in the DMZ and serves machines inside the network, information can be pulled on the internal machines). Several tools for NTP enumeration are available, including NTP Server Scanner (bytefusion.com) and AtomSync (atomsync.com), but you can also use Nmap and Wireshark if you know what you’re looking for. Commands for NTP enumeration include ntptrace, ntpdc, and ntpq.
Simple Mail Transfer Protocol (SMTP) holds three commands helpful in enumeration—VRFY (which validates user), EXPN (which provides the actual delivery addresses of mailing lists and aliases), and RCPT TO (which defines recipients)—and servers respond differently to these commands. Their responses can tell us which are valid and which are invalid user names.
Questions
1. A member of your team enters the following command:
![]()
Which of the following Nmap commands performs the same task?
A. nmap -A IPAddress
B. nmap -all IPAddress
C. nmap -Os IPAddress
D. nmap -aA IPAddress
2. You want to perform banner grabbing against a machine (168.15.22.4) you suspect as being a web server. Assuming you have the correct tools installed, which of the following command-line entries will successfully perform a banner grab? (Choose all that apply.)
A. telnet 168.15.22.4 80
B. telnet 80 168.15.22.4
C. nc -v -n 168.15.22.4 80
D. nc -v -n 80 168.15.22.4
3. You’ve decided to begin scanning against a target organization but want to keep your efforts as quiet as possible. Which IDS evasion technique splits the TCP header among multiple packets?
A. Fragmenting
B. IP spoofing
C. Proxy scanning
D. Anonymizer
4. One of your team members is analyzing TTL fields and TCP window sizes in order to fingerprint the OS of a target. Which of the following is most likely being attempted?
A. Online OS fingerprinting
B. Passive OS fingerprinting
C. Aggressive OS fingerprinting
D. Active OS fingerprinting
5. What flag or flags are sent in the segment during the second step of the TCP three-way handshake?
A. SYN
B. ACK
C. SYN/ACK
D. ACK/FIN
6. You are port scanning a system and begin sending TCP packets with the ACK flag set. Examining the return packets, you see a return packet for one port has the RST flag set and the TTL is less than 64. Which of the following is true?
A. The response indicates an open port.
B. The response indicates a closed port.
C. The response indicates a Windows machine with a nonstandard TCP/IP stack.
D. ICMP is filtered on the machine.
7. An ethical hacker is ACK-scanning against a network segment he knows is sitting behind a stateful firewall. If a scan packet receives no response, what does that indicate?
A. The port is filtered at the firewall.
B. The port is not filtered at the firewall.
C. The firewall allows the packet, but the device has the port closed.
D. It is impossible to determine any port status from this response.
8. Which flag forces a termination of communications in both directions?
A. RST
B. FIN
C. ACK
D. PSH
9. You are examining a host with an IP address of 52.93.24.42/20 and want to determine the broadcast address for the subnet. Which of the following is the correct broadcast address for the subnet?
A. 52.93.24.255
B. 52.93.0.255
C. 52.93.32.255
D. 52.93.31.255
E. 52.93.255.255
10. Which port number is used by default for syslog?
A. 21
B. 23
C. 69
D. 514
11. Which of the following commands would you use to quickly identify live targets on a subnet? (Choose all that apply.)
A. nmap -A 172.17.24.17
B. nmap -O 172.17.24.0/24
C. nmap -sn 172.17.24.0/24
D. nmap -PI 172.17.24.0/24
12. You’re running an IDLE scan and send the first packet to the target machine. Next, the SYN/ACK packet is sent to the zombie. The IPID on the return packet from the zombie is 36754. If the starting IPID was 36753, in what state is the port on the target machine?
A. Open
B. Closed
C. Unknown
D. None of the above
13. Which ICMP message type/code indicates the packet could not arrive at the recipient due to exceeding its time to live?
A. Type 11
B. Type 3, Code 1
C. Type 0
D. Type 8
14. An ethical hacker is sending TCP packets to a machine with the SYN flag set. None of the SYN/ACK responses on open ports is being answered. Which type of port scan is this?
A. Ping sweep
B. XMAS
C. Stealth
D. Full
15. Which of the following statements is true regarding port scanning?
A. Port scanning’s primary goal is to identify live targets on a network.
B. Port scanning is designed to overload the ports on a target in order to identify which are open and which are closed.
C. Port scanning is designed as a method to view all traffic to and from a system.
D. Port scanning is used to identify potential vulnerabilities on a target system.
Answers
1. A. The -A switch turns on OS detection, version detection, script scanning, and traceroute, just as the -O, -sV, -sC, and -traceroute switches do in conjunctions with each other.
2. A, C. Both Telnet and netcat, among others, can be used for banner grabbing. The correct syntax for both has the port number last.
3. A. Fragmenting packets is a great way to evade an IDS, for any purpose. Sometimes referred to as IP fragments, splitting a TCP header across multiple packets can serve to keep you hidden while scanning.
4. B. Generally speaking, any activity noted in a question that does not explicitly state you are crafting packets and injecting them toward a system indicates you are passively observing traffic—in this case, most likely with a sniffed traffic log.
5. C. A three-way TCP handshake has the originator forward a SYN. The recipient, in step 2, sends a SYN and an ACK. In step 3, the originator responds with an ACK. The steps are referred to as SYN, SYN/ACK, ACK.
6. A. According to ECC, if the TTL of the returned RST packet is less than 64, the port is open.
7. A. An ACK packet received by a stateful firewall will not be allowed to pass unless it was “sourced” from inside the network. No response indicates the firewall filtered that port packet and did not allow it passage.
8. A. The RST flag forces both sides of the communications channel to stop. A FIN flag signifies an ordered close to the communications.
9. D. If you look at the address 52.93.24.42 in binary, it looks like this: 00110100.01011101.00011000.00101010. The subnet mask given, /20, tells us only the first 20 bits count as the network ID (which cannot change if we are to stay in the same subnet), and the remaining 12 bits belong to the host. Turning off all the host bits (after the 20th) gives us our network ID: 00110100.01011101.00010000.00000000 (52.93.16.0/20). Turning on all the host bits gives us our broadcast address: 00110100.01011101.00011111.11111111 (52.93.31.255/20).
10. D. Syslog uses 514 by default. Even if you had no idea, the other answers provided are very well-known default ports (FTP, Telnet, TFTP) that you can use to eliminate them as possible answers.
11. C, D. Both the -sn and -PI switches will accomplish the task quickly and efficiently.
12. B. Since the IPID incremented by only one, this means the zombie hasn’t sent anything since your original SYN/ACK to figure out the starting IPID. If the IPID had increased by two, then the port would be open because the zombie would have responded to the target machine’s SYN/ACK.
13. A. A Type 11 ICMP packet indicates the TTL for the packet has reached 0; therefore, it must take the Carrousel (from the movie Logan’s Run) and disappear to a better place.
14. C. ECC defines what most of us used to call a half-open scan (although I suppose it would actually make more sense mathematically to call it a two-third scan, since it’s a three-way handshake and only two are used) a stealth scan. This is also known as a SYN scan.
15. D. Port scanning has a singular purpose—to knock on ports and see if they’re open (listening). Does an open port necessarily mean something is wrong? No, but it does represent a potential vulnerability you can exploit later.