CHAPTER 10
Trojans and Other Attacks
In this chapter, you will
• Describe malware types and their purpose
• Identify malware deployment methods
• Describe the malware analysis process
• Identify malware countermeasures
• Describe DoS attacks and techniques
• Identify DoS detection and countermeasure action
• Describe session hijacking and sequence prediction
My early memories, forged in the stomping grounds of my childhood upbringing in LA (Lower Alabama), most often revolve around fishing, hunting, camping, or blowing stuff up. Back then, fireworks were a wee bit stronger than they are now, parental supervision wasn’t, and we were encouraged to get out of the house to amuse ourselves and spare our mothers a little bit of sanity. And while my cousins and I certainly went through our fair share of gunpowder, running around my uncle’s property in Mount Vernon, Alabama, we found many other ways to bring about destruction in our little neck of the woods. In one of these memories, my cousin wound up nearly decimating an entire pond’s worth of fish with nothing but a bag and a shovel.
The day before going up to my uncle’s farm, I’d heard one of my dad’s friends talking about walnuts and how dangerous they were. It turns out the hulls have loads of tannin and natural herbicides in them, which can be lethal to plants growing around the watershed of any walnut tree. It was definitely a cool and fun fact, but it didn’t do anything for me until I heard the last little nugget of the conversation: “Just don’t ever throw them in your pond. They’ll displace all the oxygen and kill all your fish.”
Armed with this knowledge, my cousin and I filled a big burlap sack full of walnut husks and drug it out to one of the farm ponds to see whether it would work. We thought that simply chucking it into the pond wouldn’t be very effective, and because sweet tea seemed to be better (and steep faster) when the tea bags were moved around, we decided to cover as much of the surface area of the pond as possible. So, we dunked the bag into the water and started dragging it around the bank of the pond. While not a perfect circle, the pond wasn’t so big or weirdly shaped that we couldn’t make it all the way around, and in about 10 minutes we’d made our first lap. We left the bag in the water and sat down to watch what would happen. With a few minutes, we saw the first fish come to the top of the water, lazily swimming about trying to gasp for oxygen. We scooped him up and tossed him into the bucket. Then the second appeared. And a third. Then suddenly, in a scene right out of a horror story, hundreds of fish just popped up to the surface all at once.
We panicked. What had we done? This was supposed to result, if it worked at all, in a few fish we could take home and maybe convince Uncle Donny to fry up for dinner. Instead, we had farm pond genocide on our hands, and more fish than we knew what to do with. We pulled the bag out of the water and flung it out into the woods and then grabbed up as many bodies as we could carry and took them home. And before confessing to our parents what we’d done, we cleaned all the fish and had them on ice, ready for cooking. We may have been innocent kids caught in a weird situation, but we weren’t dumb—a fried fish meal prepared in advance could make up for a lot of naughtiness.
So, what does all this have to do with our book on attacking systems? While dragging a bag full of old walnuts through a pond isn’t the “normal” way to catch a mess of fish for a dinner, it certainly works—sometimes surprisingly well. Just like the bag of walnuts, malware and other attacks may be something you overlook as available options, but they can really work well for your end goal. Never forget that you can often catch more than you expect by using tools and circumstances in unexpected ways. A lot of the terms and issues we discuss here may not necessarily seem like a hacker’s paradise, but I can promise you it’s all relevant. And we’ll cover these terms and issues for two important reasons: you’ll be a better pen test member by taking advantage of everything at your disposal, and it’s all on your test!
The “Malware” Attacks
Malware is generally defined as software designed to harm or secretly access a computer system without the owner’s informed consent. And, more often than not, people in our profession think of it as hostile, intrusive, annoying, and definitely something to be avoided. From the perspective of a hacker, though, some of this may actually be usable, provided it’s done within the confines of an agreed-upon contract in a pen test. Let me be absolutely clear here: I am not encouraging you to write, promote, or forward viruses or malware of any kind. I’m simply providing you with what you need to be successful on your exam.
I read somewhere that software is considered to be malware based on the perceived intent of the creator rather than any particular features. That’s actually a good way to think of it from the ethical hacking perspective. Whereas most people think of viruses, worms, and Trojans as a means to spread destruction and as a huge inconvenience to computing life, to an ethical hacker the Trojan might actually look like a good means to pull off a successful exploit or to retain access to a machine—it’s simply one of many tools in the arsenal. Additionally, there are a ton of “legitimate” applications, add-ons, toolbars, and the like that aren’t intended to be malware, but they may as well be. For example, is “stealing” data for advertising purposes malware in nature?
And what about intent as seen from the eye of an antivirus (AV) application? Netcat is routinely flagged as malware, even though all it does is open and close ports. There are countless tools and examples like that. Perhaps the best way to think of intent regarding malware is that almost no tool is inherently evil—it’s the operator that makes it so. That said, there are some tool types that are classified as malware from the get-go, and although we’ll avoid the in-depth minutiae that’s sure to bore you into dropping this undertaking altogether and send you screaming into another vocation—like maybe wedding planning or something similar—we will spend a little time on the highlights of Trojans, viruses, worms, and the like.
Regardless of type, there needs to be a way to distribute the malware and get it installed on machines. After all, surely no one purposefully clicks on something that says “Click here for the latest malware infection on your machine! Guaranteed not to be noticed by your current AV signatures! Hurry, this is a limited-time offer!” (Although sometimes it certainly seems that people do.) No, malware creators need to resort to other means to distribute their work, and it’s usually through innocent-appearing means.
Most malware is simply downloaded from the Internet with or without the user’s knowledge. Sometimes legitimate sites get compromised, leading to infections on visiting systems. Other times drive-by downloading infects the system, usually via some weird Java vulnerability delivered through an ad stream or something like it. Peer-to-peer applications or web application “features” are often hijacked to distribute malware, and an IRC channel is always a great way to distribute malware.
The absolute easiest way you can get a target to install your malware, thereby providing you with access to their machine, is to just ask them to do it for you. Send malware (usually a Trojan) via e-mail, file sharing, or a browser and, more often than not, they’ll open it and happily install whatever you want. Of course, the e-mail can’t say “Click this so I can infect and own your system,” and your imbedded malware must be hidden enough so as not to trip any AV signatures. So the question becomes, then, how do you make it look like a legitimate application? Well, there are a couple of options available for you.
First, wrappers are programs that allow you to bind an executable of your choice (Trojan) to an innocent file your target won’t mind opening. For example, you might use a program such as EliteWrap to embed a backdoor application with a game file (.exe). Your target opens the latest version of Elf Bowling and starts rolling strikes. Meanwhile, your backdoor is installing and sits there waiting for your use later. Wrappers do have their own signatures and can definitely show up on AV scans. If you’ve wrapped 20 items, you’d wind up with a single malware discovery in your antivirus.
Assuming you’ve found a way to get User Joe to open files you send him, it’s another thing altogether to bypass the antivirus system on his machine. After all, what good does it do to find a hapless user clicking on everything you send him, only to have each attempt quashed by the antivirus? Packers and crypters are two methods that can help with this. They are tools that alter malware to hide it from signature-based antivirus.
Crypters are software tools that use a combination of encryption and code manipulation to render malware undetectable to AV and other security-monitoring products (in Internet lingo, it’s referred to as fud, for “fully undetectable”). Packers use compression to pack the malware executable into a smaller size. While this does reduce the file size, it also serves to make the malware harder to detect for some antivirus engines. Regardless of which type is used, both work much like a ZIP file, except that the extraction occurs in memory and not on the disk. There are several crypters out there, but be forewarned—delving into this stuff can take you to some really dark places on the interwebs. ECC mentions a few in the courseware but, for many reasons, doesn’t give links to download them—which is probably a good thing.
And finally, let’s not forget about the exploit kits. There are tons of platforms from which you can deliver exploits and payloads, and many are used primarily to deploy Trojans on target systems. Some examples include Infinity, Bleeding Life, Crimepack, and Blackhole Exploit Kit.
Trojans
A Trojan is software that appears to perform a desirable function for the user prior to running or installing it but instead performs a function, usually without the user’s knowledge, that steals information or otherwise harms the system (or data). To hackers—ethical or not—a Trojan is a method to gain, and maintain, access on a target machine.
The idea of a Trojan is pretty simple. First, send an innocent-looking file to your target, inviting them to open it. They open it and, unaware to what’s going on, merrily install software that makes your job easier. This software might be designed to steal specific types of information to send back, act as a keylogger, or perform 1000 other equally devious tasks. Some of them can even provide remote control–type access to a hacker any time he feels like it. For us ethical hackers, the ultimate goal is to provide something we can go back to later—a means to maintain our access. Although a backdoor isn’t a Trojan, and a Trojan isn’t a backdoor, they’re tied together in this discussion and on your exam: the Trojan is the means of delivery, and the backdoor provides the open access.
There are innumerable Trojans, and uses for them, in the computing world today. In CEH parlance, they’ve been categorized into different groups, each fairly easy to understand without much comment or explanation on my part. For example, I’m fairly certain you could understand that a Trojan that changes the title bar of an Excel spreadsheet to read “YOU’VE BEEN HACKED!” would fall into the defacement Trojan category, as opposed to the proxy server Trojan, which allows an attacker to use the target system as a proxy. Others include botnet Trojans (like Tor-based Chewbacca and Skynet), remote access Trojans (like RAT, MoSucker, Optix Pro, and Blackhole), and e-banking Trojans (like Zeus and Spyeye).
A command shell Trojan is intended to provide a backdoor to the system that you connect to via command-line access. An example of this called out by EC-Council is Netcat—and although all the purists out there are screaming “NETCAT IS NOT A TROJAN!” just bear with me for a minute. It’s talked about in this section for a reason (mainly because ECC talks about it here), and it can be used to illustrate the point. Going back to our discussion on intent, Netcat is as much of a Trojan as I am a professional basketball player, but it does provide a means to open and close listening ports—in effect providing a method to backdoor your way into a system. In and of itself, that (opening and closing ports) doesn’t seem malicious at all—but add malicious intent to it, and…
Known as the “Swiss Army knife” of TCP/IP hacking, Netcat provides all sorts of control over a remote shell on a target (see Figure 10-1). For example, to establish command-line access to the machine, type nc -e IPaddress Port#. Tired of Telnet? Just type the -t option. And for the main point of this section (backdoor access to a machine), when installed and executed on a remote machine, Netcat opens a listening port of your choice. From your attack machine, you connect using the open port—and voilà! For example’s sake, typing nc -l -p 5555 opens port 5555 in a listening state on the target machine. You can then type nc IPaddress -p 5555 and connect to the target machine—a raw “Telnet-like” connection. And, just for fun, do you think the following command might provide something interesting (assuming we’re connecting to a Linux box)?
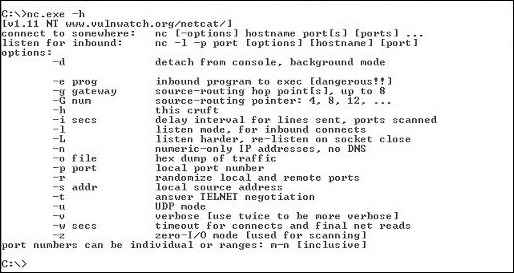
Figure 10-1 Netcat help
![]()
And finally in our discussion of Trojans, we have to include port number comparisons through both real-world, normal discussion and ECC-world “this will probably be on your exam” lenses as well. Default port numbers used by specific Trojans most definitely fall into the realm of “not real world,” but will no doubt appear on your exam. Some of the more common port numbers used by various Trojans are shown in Table 10-1, and for test purposes you should definitely know them. To be completely honest, though, these won’t be of value to you in the real world—a real hacker simply won’t bother with protocols you’re going to be watching for. For example, port 21 may be the default for an FTP server, but several known Trojans make use of it for illicit purposes. And port 80, for HTTP traffic? Please—don’t get me started. To quote our beloved tech editor here, “Any malware that doesn’t use SSL over 443, DNS over 53, or some other easy-to-hide mechanism was likely written by 14-year-olds who hate their parents or in some country still using a 486DX (yes, that DX, with the math co-processor) to code.”
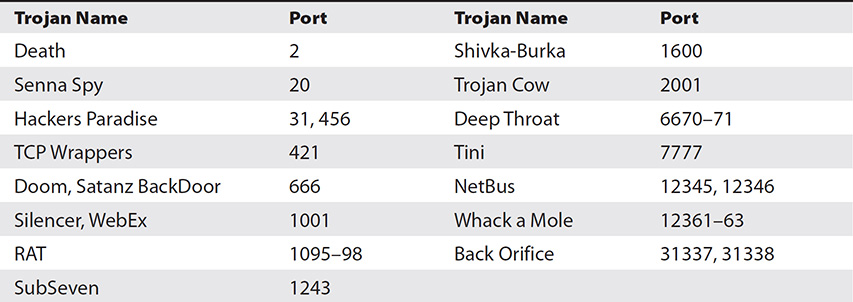
Table 10-1 Trojan Port Numbers
You’ll definitely see some of these on your exam, but in actual practice a hacker is not going to just blast forward with a sign reading “I’m here to hack you.” Nor will he use some ridiculously named thing like “Whack a Mole.” In fact, if you’re chasing something down on these default numbers in the real world, somebody has done something wrong, or you’re being set up.
So, whether you’re lazily checking for default port numbers or legitimately concerned about what is actually being used on your system, how would you spot port usage? By looking for it, of course. Several programs are available to you to keep an eye on the port numbers you have in use on your system. An old standby built into your Windows system command line is netstat. Entering the command netstat -an will show you all the connections and listening ports in numerical form, as shown in Figure 10-2.

Figure 10-2 netstat
Netstat will show all connections in one of several states—everything from SYN_SEND (indicating active open) to CLOSED (the server has received an ACK from the client and closed the connection). In Figure 10-2, you can see several port numbers in a listening state—waiting for something to come along and ask for them to open. Another useful netstat command is netstat -b. This displays all active connections and the processes or applications that are using them, which is pretty valuable information in ferreting out spyware and malware.
Also, port-scanning tools can make this easier for you. Fport is a free tool from McAfee that reports all open TCP/IP and UDP ports and maps them to the owning applications. Per the McAfee site, “This is the same information you would see using the ‘netstat -an’ command, but it also maps those ports to running processes with the PID, process name, and path.” What’s Running, TCPView, and IceSword are also nice port-monitoring tools you can download and try.
If you’re on a Windows machine, you’ll also want to keep an eye on the registry, drivers, and services being used, as well as your startup routines. When it comes to the registry, you can try to monitor it manually, but I bet within a day you’d be reduced to a blubbering fool curled into the fetal position in the corner. It’s far easier to use monitoring tools designed for just that purpose. Some of the options are SysAnalyzer, Tiny Watcher, Active Registry Monitor, and Regshot. Additionally, many antivirus and malware scanners will watch out for registry errors. Malwarebytes will display all questionable registry settings it finds on a scan, for example.
Services and processes you don’t recognize or that seem to be acting out of sorts can be indicators of Trojan activity on a machine. Aside from old, reliable Task Manager, processes and services can be monitored using gobs of different tools. Just a few mentioned for your perusal are Windows Service Manager, Service Manager Plus, and Smart Utility. And don’t forget to check the startup routines, where most of these will be present; it won’t do you much good to identify a bad service or process and kill it, only to have it pop up again at the next start. On a Windows machine, a simple msconfig command will open a configuration window showing you all sorts of startup (and other) settings you can work with (see Figure 10-3).

Figure 10-3 msconfig
Lastly, I think the EC-Council folks would probably revoke my CEH certification if I neglected to mention Tripwire and SIGVERIF here. See, verifying the integrity of critical files is considered one of those bedrock-type actions you need to take in protecting against/detecting Trojans. Tripwire has been mentioned before in this book and bears repeating here. It is a well-respected integrity verifier that can act as an HIDS in protection against Trojans. SIGVERIF is built into Windows machines to help verify the integrity of critical files on the system.
Viruses and Worms
The good news regarding viruses and worms is there’s not a whole lot here for you to remember for your exam, and what you do need to know are simple definitions and a few new, newsworthy attacks. There’s just simply not a lot on the exam regarding malware as a whole, so we’ll try to keep it short, sweet, and right to the point.
A virus is a self-replicating program that reproduces its code by attaching copies into other executable codes. In other words, viruses create copies of themselves in other programs, then activate on some sort of trigger event (such as a specific user task, a particular time, or an event of some sort). They usually get installed on a system via file attachments, user clicks on embedded e-mails, or the installation of pirated software, and while some are nothing more than just annoyances, many cause substantial harm to the system and, if you’re crazy enough to pay for it, financial loss to the system owner.
Assuming your system does get infected, other than your AV going bananas and alerting that something crazy has happened, just how would you know your system has actually been infected? Well, obvious things like much slower response time, computer and browser freezes, and repeated, continual hard drive accesses should be indicators. Others may not be as immediately obvious—for example, drive letters might change and files and folders may disappear or become inaccessible. In any event, recovery may be as simple as a minor cleaning effort using software designed to clean the infection, or a major undertaking including reloads from known good backups.
There are multiple virus types listed in the official courseware, and it’s impossible to determine exactly which you’ll see on your exam. However, one in particular gets a lot of page time in the official courseware, and study groups online, and so warrants some extra attention here: ransomware. According to US-CERT (https://www.us-cert.gov/Ransomware), ransomware is a type of malicious software designed to deny access to a computer system or data until a ransom is paid, and typically spreads through phishing e-mails or by unknowing visits to an infected website. In other words, ransomware locks you out of your own system resources and demands an online payment of some sort in order to release them back to you. While usually the payment is smaller than the cost it would take to remove the malware and recover anything lost, sometimes it’s enormous, and paying off the bad guys simply brings about more online terror.
Ransomware as a term seemingly came out of nowhere over the past couple years and is now a dominating focus of attention and conversation in the security world. Unfortunately, it’s ubiquitous and there’s little doubt you’ll see it somewhere, sometime in your travels. As a matter of fact, I’m betting most of you reading this have at least a cursory knowledge of possibly the most famous, and most “effective,” ransomware attack in history—WannaCry.
On May 12, 2017, at approximately 07:44 UTC, a system in Asia was the first to fall victim to the WannaCry ransomware. Within 24 hours, it had spread to over 230,000 machines in 150 countries by taking advantage of an unpatched SMB exploit known as “Eternal Blue.” In Eternal Blue, Microsoft’s implementation of SMBv1 mishandled specially crafted targets, which allowed remote attackers to execute code on the machine. Interestingly enough, the Eternal Blue exploit was, by all accounts, discovered by the NSA and released to Microsoft for patch creation in early March of the same year. Microsoft did indeed create the patch and made it available in April, but many organizations—for reasons involving everything from timing issues, patch management policies (the patch was not marked as “critical”), testing and evaluations, and, yes, even lazy security implementation—did not have it in place to prevent the exploit.
Other virus types are listed here for your memorization:
• Boot sector virus Also known as a system virus, this virus type actually moves the boot sector to another location on the hard drive, forcing the virus code to be executed first. These viruses are almost impossible to get rid of once you get infected. You can re-create the boot record—old-school fdisk or mbr could do the trick for you—but it’s not necessarily a walk in the park. As a side note, Petya (another bit of nasty ransomware that made itself newsworthy by using the Eternal Blue exploit like WannaCry) overwrote the Master Boot Record (MBR) until payment was received.
• Shell virus Working just like the boot sector virus, this virus type wraps itself around an application’s code, inserting its own code before the application’s. Every time the application is run, the virus code is run first.
• Cluster virus This virus type modifies directory table entries so that user or system processes are pointed to the virus code itself instead of the application or action intended. A single copy of the virus “infects” everything by launching when any application is initiated.
• Multipartite virus Attempts to infect both files and the boot sector at the same time. This generally refers to a virus with multiple infection vectors. This link describes one such DOS-type virus: www.f-secure.com/v-descs/neuroqui.shtml. It was multipartite, polymorphic, retroviral, boot sector, and generally a pretty wild bit of code.
• Macro virus Probably one of the most common malware types you’ll see in today’s world, this is usually written with Visual Basic for Applications (VBA). This virus type infects template files created by Microsoft Office, normally Word and Excel. The Melissa virus was a prime example of this.
• Polymorphic code virus This virus mutates its code using a built-in polymorphic engine. This type of virus is difficult to find and remove because its signature constantly changes. No part of the virus stays the same from infection to infection.
• Encryption virus Shockingly, this type of virus uses encryption to hide the code from antivirus scanners.
• Metamorphic virus This virus type rewrites itself every time it infects a new file.
• Stealth virus Also known as a “tunneling virus,” this one attempts to evade antivirus (AV) applications by intercepting the AV’s requests to the operating system (OS) and returning them to itself instead of the OS. The virus then alters the requests and sends them back to AV as uninfected, making the virus now appear “clean.”
• Cavity virus Cavity viruses overwrite portions of host files so as not to increase the actual size of the file. This is done using the null content sections of the file and leaves the file’s actual functionality intact.
• Sparse infector virus This virus type only infects occasionally. For example, maybe the virus only fires every tenth time a specific application is run.
• File extension virus This virus type changes the file extensions of files to take advantage of most people having file extension view turned off. For example, readme.txt.vbs might appear as readme.txt with extensions turned off.
Another malware definition you’ll need to know is the worm. A worm is a self-replicating malware computer program that uses a computer network to send copies of itself to other systems without human intervention. Usually it doesn’t alter files, but it resides in active memory and duplicates itself, eating up resources and wreaking havoc along the way. The most common use for a worm in the hacking world is the creation of botnets, which we’ve already discussed. This army of robot systems can then be used to accomplish all sorts of bad things.
When it comes to worms and your exam, in earlier versions of the exam EC-Council wanted you not only to know and understand what a worm does but also to identify specific famous named worms based on a variety of characteristics. For example, the Conficker worm disabled services, denied access to administrator shared drives, locked users out of directories, and restricted access to security-related sites. Symptoms included an “Open folder to view files—Publisher not specified” message in the AutoPlay dialog box (the original, and legitimate, Windows option reads “Open folder to view files using Windows Explorer.”)
In the latest version of the official courseware, however, it doesn’t appear they care much about it at all. In fact, the only one making an appearance is something called “Ghost Eye Worm,” which really isn’t much of a worm at all. It’s a hacking tool that uses random messaging on Facebook and other sites to perform a host of malicious efforts. I’m not positive they’ll ignore worms altogether, so I decided to list these for your perusal, should you happen to see a random question about one of them:
• Code Red Named after the soft drink the eEye Digital guys were drinking when they discovered it, Code Red exploited indexing software on IIS servers in 2001. The worm used a buffer overflow and defaced hundreds of thousands of servers.
• Darlloz Known as the worm for “the Internet of Things,” darlloz is a Linux-based worm that targets running ARM, MIPS, and PowerPC architectures—which are usually routers, set-top boxes, and security cameras.
• Slammer Also known as SQL Slammer, this was a denial-of-service worm attacking buffer overflow weaknesses in Microsoft SQL Services. Also called Sapphire, SQL_HEL, and Helkern, it spread quickly using UDP, and its small size (the entire worm could fit inside a single packet) allowed it to bypass many sensors.
• Nimda This worm’s name comes from the word admin spelled backward. Nimda was a successful file infection virus that modified and touched nearly all web content on a machine. It spread so quickly it became the most widespread worm in history within about 22 minutes of its first sighting. Nimda spread through e-mail, open network shares, and websites, and it also took advantage of backdoors left on machines infected by the Code Red worm.
• Bug Bear Propagating over open network shares and e-mail, Bug Bear terminated AV applications and set up a backdoor for later use. It also contained keylogging capabilities.
• Pretty Park Pretty Park spread via e-mail (attempting a send every 30 minutes) and took advantage of IRC to propagate stolen passwords and the like. Running the worm executable often displayed the 3D Pipe screensaver on Windows machines.
Finally, the last topics we’re required to cover here are malware analysis, countermeasures, and mitigation. Analysis may be something your particular organization makes a habit of, but outside antivirus companies and the like, I’m not sure this is something valid for your day-to-day work. That said, ECC wants you to know about it, so here goes.
The first step in analyzing malware is to make sure you have a good test bed. Using a virtual machine with the NIC in host-only mode and no open shares is a good start. Next, analyze the malware on that isolated VM while it’s in a static state. Tools such as binText and UPX can help in examining the binary itself as well as the compression and packaging technique. Next, fire up the malware and check out the processes in use (with Process Monitor and Process Explorer, for example). Review network traffic using NetResident, TCPview, or maybe even Wireshark. Lastly, check to see what files are added, changed, or deleted, what processes continue to spawn, and any changes to the registry. Tools that can help you with malware analysis include, but are not limited to, IDA Pro (www.hex-rays.com), VirusTotal (www.virustotal.com), Anubis (Anubis.iseclab.org), and Threat Analyzer (www.threattracksecurity.com).
And just how are you supposed to protect against viruses and worms? Well, first off, you should probably know what’s running on and being used by your system. Trojans take advantage of unused ports, so if you’re looking at your system and see something using a weird port, that would probably be a good indication you may be infected. Use tools such as TCPView and CurrPorts (not to mention netstat) to see what ports are in use, and by what. Check out which processes are in use with Process Monitor and Process Explorer, and keep an eye on any registry changes with Regscanner or any of a number of registry-scanning tools. Lastly, keep an eye on system files and folders with tools such as SIGVERIF and Tripwire.
For study purposes, a good antivirus program is also a must, and keeping it up to date is key (the system is only as good as your signature files, and if you’re asleep at the wheel in keeping them updated, you’re opening yourself up to infection). In the real world, most of us have a blind, seething hatred of AV programs. Malware moves quickly in the modern world, and most of it runs and is kept in memory versus on the disk. Signature-based AV simply can’t keep up, and heuristic AV simply isn’t much better. In fact, I think you could make a strong argument in an enterprise network that the false sense of security created by the mere existence of desktop antivirus makes the system less secure. I can’t tell you the number of times during our incident response process a victim has said, “Well, yes, of course, but don’t you have antivirus installed on this machine to protect me?” Feel free to load one up if it makes you feel better, but in addition to frustrating your attempts at loading and playing with genuine security tools, you’re likely just wasting time.
Another good option, at least as far as ECC is concerned, is the sheepdip computer. A sheepdip system is set up to check physical media, device drivers, and other files for malware before it is introduced to the network. Typically, this computer is used for nothing else and is isolated from the other computers, meaning it is not connected to the network at all. Sheepdip computers are usually configured with a couple of different AV programs, port monitors, registry monitors, and file integrity verifiers.
Remaining Attacks
Have you ever been on a really long road trip? You know the ones I’m talking about, right? When you leave, you’re really excited, and the miles just seem to pass along happily. Then, somewhere along the way, things change. The excitement dies down, and before you know it, the miles become a burden instead of a joy. Everything seems like it takes forever, and the road becomes the enemy, with each road sign mocking your progress instead of marking it. Then, just as things are near their worst, you see the sign with your destination listed on it. It might read 200 miles, it might read 500, but instantly your spirits are lifted.
Have you noticed that at that point you start driving faster? Do you know why? Because you can see the end from there. Once the destination is within reach, once you can see that proverbial light at the end of the tunnel, your natural instinct is to sprint. There’s no need for bathroom breaks—no need to stop and look at the world’s largest ball of twine—because you are so close to the end you just want to get there and rest. It’s perfectly natural, and it’s the way our minds work.
Well, dear reader, we both find ourselves at an interesting juncture here. You and I have been on a long journey so far. It started out exciting, and there was a lot to look at and pass the time with. Now we’re getting close to the end (you’ve no doubt looked at the table of contents and know where we are), and you’re tired of reading. Heck, I’m tired of writing, and the temptation for both of us is to sprint—to blast through the rest and just finish, for goodness’ sake. Trust me, though, we’ve got just two big topics to get through here. I’ll keep them short and to the point, but I’ll need to know you’re willing to do your part and stick with me. Come on, we’re almost there.
Denial of Service
We’ve already defined a denial-of-service attack and a distributed denial-of-service attack, but this section is here to go into a little more detail (namely because there are CEH objectives yet to cover on the subject, and ECC has devoted an entire chapter to DoS). For example, you may or may not be aware that a DoS is generally thought of as a last-resort attack. This isn’t always true—there are plenty of examples where DoS was the whole point. In some cases, the attacker just wants to embarrass the target or maybe prevent the spread of information. But, sometimes, when a hacker is tired of trying to break through your defenses, she may simply resort to “blowing it up” out of frustration.
Obviously, this is completely different for the ethical hacker. We’re not going to perform DoS attacks purposely, unless our client wants or allows us to do so. Sure, there may be some unintended DoS symptoms against a particular system or subnet, but we’re generally not going after DoS as an end result. As an aside, you’ll need to make sure your client understands the risks involved with testing; sometimes knocking on doors causes the security system to lock them all, and you don’t want your client coming back at you unaware this could have happened.
The standard DoS attack seeks to accomplish nothing more than taking down a system or simply denying access to it by authorized users. From this standpoint, the DoS might prove useful to an ethical hacker. For example, what if you removed the security personnel’s rights to watch the network? This could allow you a few minutes to hack at will, without worry of getting caught (until they notice they have no rights, of course, which won’t take long).
The distributed denial-of-service (DDoS) attack, obviously, comes not from one system but many, and they’re usually part of a botnet. The botnet is a network of zombie computers the hacker can use to start a distributed attack from (examples of botnet software/Trojans are Shark and Poison Ivy). These systems can sit idly by, doing other work for, literally, months before being called into action. That action may be as simple as sending a ping or performing some other task relevant to the attack at hand. For study purposes, the preferred communications channel used to signal the bots is IRC or Internet Chat Query (ICQ). In the real world, it’s just as likely (perhaps even more so) to see HTTP or HTTPS employed.
DoS and DDoS attacks are as numerous and varied as the items in the buffet lines in Las Vegas. They can range from the simple to the fairly complex, and can require one system or many to pull off. For a simple example, just try someone’s login credentials incorrectly three times in a row on a government network. Bingo! You’ve successfully DoS’d their account. Other relatively simple methods could be sending corrupt SMB messages on Windows machines to “blue screen” the device. Or maybe you simply “arp” the machine to death, leaving it too confused to actually send a message anywhere. The methods are innumerable.
ECC lists four basic categories of DoS/DDoS, and several examples of DoS/DDoS attacks:
• Fragmentation attacks These attacks take advantage of the system’s ability (or lack thereof) to reconstruct fragmented packets.
• Volumetric attacks Also known as bandwidth attacks, these consume all available bandwidth for the system or service.
• Application attacks These attacks consume the resources necessary for the application to run, effectively making it unavailable to others.
• TCP state-exhaustion attacks These attacks go after load balancers, firewalls, and application servers by attempting to consume their connection state tables.
• SYN attack The hacker will send thousands upon thousands of SYN packets to the machine with a false source IP address. The machine will attempt to respond with a SYN/ACK but will be unsuccessful (because the address is false). Eventually, all the machine’s resources are engaged, and it becomes a giant paperweight.
• SYN flood In this attack, the hacker sends thousands of SYN packets to the target but never responds to any of the return SYN/ACK packets. Because there is a certain amount of time the target must wait to receive an answer to the SYN/ACK, it will eventually bog down and run out of available connections.
• ICMP flood Here, the attacker sends ICMP Echo packets to the target with a spoofed (fake) source address. The target continues to respond to an address that doesn’t exist and eventually reaches a limit of packets per second sent.
• Smurf The attacker sends a large number of pings to the broadcast address of the subnet, with the source IP spoofed to that of the target. The entire subnet will then begin sending ping responses to the target, exhausting the resources there. A fraggle attack is similar but uses UDP for the same purpose.
• Ping of death In the ping of death, an attacker fragments an ICMP message to send to a target. When the fragments are reassembled, the resultant ICMP packet is larger than the maximum size and crashes the system. (Note that this isn’t a valid attack with modern systems, but is still a definition you may need to know.)
• Teardrop In a teardrop attack, a large number of garbled IP fragments with overlapping, oversized payloads are sent to the target machine. On older operating systems (such as Windows 3.1x, Windows 95, and Windows NT operating systems), this takes advantage of weaknesses in the fragment reassembly functionality of their TCP/IP stack, causing the system to crash or reboot.
• Peer to peer In this attack, clients of a peer-to-peer file-sharing hub are disconnected and directed to connect with the target system.
• Permanent Phlashing refers to a DoS attack that causes permanent damage to a system. Usually this includes damage to the hardware and can also be known as bricking a system.
More than a few tools are dedicated to performing DoS on systems. Low Orbit Ion Cannon (LOIC) is a simple-to-use DDoS tool that floods a target with TCP, UDP, or HTTP requests (see Figure 10-4). Originally written open source to attack various Scientology websites, the tool has many people voluntarily joining a botnet to support all sorts of attacks. As recently as 2011, LOIC (a DDoS tool originally created and used by Anonymous) was used in a coordinated attack against Sony’s PlayStation network, and the tool has a track record of other successful hits: the Recording Industry Association of America, PayPal, MasterCard, and several other companies have all fallen victim to LOIC.

Figure 10-4 LOIC
Other tools include Trinity, Tribe Flood Network, and R-U-Dead-Yet. Trinity is a Linux-based DDoS tool much like LOIC. Tribe Flood Network is much the same, using voluntary botnet systems to launch massive flood attacks on targets. R-U-Dead-Yet (known by its acronym RUDY) performs DoS with HTTP POST via long-form field submissions. We could go on here, but I think you get the point. Do a quick Google search for “DoS Tool” or “DDoS Tool”—you’ll find more than you need to know.
Finally, when it comes to countermeasures against DoS attacks, you’ve probably heard all this before, so we don’t need to spend a large amount of time on the subject. Actions such as disabling unnecessary services, using a good firewall policy, and keeping security patches and upgrades up to date are pretty standard fare. Additionally, the use of a good NIDS can help against attacks from across the network. Strong, security-conscious code should be an absolute for your applications, and the use of tools such as Skydance can help detect and prevent DoS attacks. You might also look into network ingress filtering as well as some network auditing tools to help along the way.
Session Hijacking
Unlike DoS attacks, session hijacking attempts aren’t trying to break anything or shut off access necessarily. The idea is fairly simple: the attacker waits for a session to begin and, after all the pesky authentication gets done, jumps in to steal the session for himself. This differs a little from the spoofing attacks we’ve talked about to this point. In spoofing, you’re pretending to be someone else’s address with the intent of sniffing their traffic while they work. Hijacking refers to the active attempt to steal the entire session from the client: the server isn’t even aware of what happened, and the client simply connects again in a different session.
From a high-level view, TCP session hijacking sounds relatively easy. First, the hacker tracks the session, watching the sequence numbers and the flow of packet headers. Next, the hacker “desynchronizes” the connection by sending a TCP RST or FIN to the client, causing it to close its side of the session. Lastly (at the same time), using the information gathered during the first step, the hacker begins sending packets to the server with the predicted (guessed) session ID, which is generated by an algorithm using the sequence numbers. If the hacker gets it right, he has taken over the session because the server thinks it’s the original client’s next packet in the series. The following more completely describes the session hijack steps (per EC-Council):
1. Sniff the traffic between the client and the server.
2. Monitor the traffic and predict the sequence numbering.
3. Desynchronize the session with the client.
4. Predict the session token and take over the session.
5. Inject packets to the target server.
TCP session hijacking is possible because of the way TCP works. As a session-oriented protocol, it provides unique numbers to each packet, which allows the receiving machine to reassemble them in the correct, original order, even if they are received out of order. The synchronized packets we’ve talked about throughout the book set up these sequence numbers (SNs). With more than 4 billion combinations available, the idea is to have the process begin as randomly as possible. However, it is statistically possible to repeat sequence numbers and, even easier, to guess what the next one in line will be.
So, just for clarity’s sake, let’s go back to the earlier discussion on TCP packets flying through the ether. The initial sequence number (ISN) is sent by the initiator of the session in the first step (SYN). This is acknowledged in the second handshake (SYN/ACK) by incrementing that ISN by one, and another ISN is generated by the recipient. This second number is acknowledged by the initiator in the third step (ACK), and from there on out communication can occur. The window size field will tell the recipient how much he can send before expecting a return acknowledgment. Combine all of them together and, over time, you can watch the whole thing in action. For example, consider Figure 10-5. It’s worth mentioning these types of attacks are considered very rare in the real world: outside of a very rare MITM attack, you’re as likely to see this (and ping of death) as you are to see a flying peacock.

Figure 10-5 TCP communication
After the handshake, for every data payload transmitted, the sequence number is incremented. In the first two steps of the three-way handshake, the ISNs are exchanged (in this case, 100 and 500) and then are incremented based on the delivery of data. In our example here, Computer A sends 3 bytes with an initial sequence number of 102, so each packet sequence number will increment accordingly—102, 103, and 104, respectively. The receiver then sends an acknowledgment of 105 because that is the next byte it expects to receive in the next packet.
It seems easy enough, but once you add the window size and take into account that the numbers aren’t simple (like the 100 and 500 in our example), it can get hairy pretty quickly. The window size, you may recall, tells the sender how many outstanding bytes it can have on the network without expecting a response. The idea is to improve performance by allowing more than one byte at a time before requiring the “Hey, I got it” acknowledgment. This sometimes complicates things because the sender may cut back within the window size based on what’s going on network-wise and what it’s trying to send.
Thankfully, a multitude of tools are available to assist in session hijacking. We’ve mentioned Ettercap before—a packet sniffer on steroids—but not in the context of actively hijacking sessions. It’s an excellent man-in-the-middle tool and can be run from a variety of platforms (although it is Linux native). Hunt and T-sight are probably the two best-known session hijacking tools. Hunt can sniff, hijack, and reset connections at will, whereas T-sight (commercially available) can easily hijack sessions as well as monitor additional network connections. Some other tools are Zaproxy and Paros (both known more as a proxy), Burp Suite, Juggernaut (a well-known Linux-based tool), Hamster, and Ferret.
Countermeasures for session hijacking are, again, usually commonsense issues. For one thing, using unpredictable session IDs in the first place protects against hijacking (remember this one). Other options include limiting incoming connections, minimizing remote access, and regenerating the session key after authentication is complete. Lastly, a really good choice is to use encryption to protect the channel. We’ll cover IPSec more when we get around to cryptography, but a small refresher here (or introduction, if you know nothing about it) is a great idea—mainly because this is where ECC covers it, and its encryption and authentication is considered good prevention against session hijacking.
IPSec is used to secure IP communication by providing encryption and authentication services to each packet, and it has several architectural components you’ll need to know. First, IPSec works in two modes. In transport mode, the payload and ESP trailer are encrypted; however, the IP header of the original packet is not. Transport can be used in network address translation (NAT) because the original packet is still routed in exactly the same manner as it would have been without IPSec. Tunnel mode, however, encrypts the whole thing, encapsulating the entire original packet in a new IPSec shell. This makes it incompatible with NAT. The rest of IPSec architecture includes the following protocols:
• Authentication Header AH is a protocol within IPSec that guarantees the integrity and authentication of the IP packet sender.
• Encapsulating Security Payload ESP is a protocol that also provides origin authenticity and integrity, but it can take care of confidentiality (through encryption) too. ESP does not provide integrity and authentication for the entire IP packet in transport mode, but in tunnel mode protection is provided to the entire IP packet.
• Internet Key Exchange IKE is the protocol that produces the keys for the encryption process.
• Oakley A protocol that uses Diffie-Hellman to create master and session keys.
• Internet Security Association Key Management Protocol Software that facilitates encrypted communication between two endpoints.
If it’s possible to put into action in your environment (and it’s actually pretty easy to set up), IPSec is a good choice as a countermeasure. Not the only one, but a good one. I would say user education is key. Oftentimes an uneducated user won’t think twice about clicking past the security certificate warning, or reconnecting after being suddenly shut down, and education can help with one or two instances here and there—but don’t rely on it.
Chapter Review
Malware is generally defined as software designed to harm or secretly access a computer system without the owner’s informed consent. Some states also define malware as computer contaminant. Malvertising involves embedding malware into ad networks in an effort to throw malware across many legitimate sites. Other definition terms of note include overt channels (legitimate communication channels used by programs across a system or a network) and covert channels (used to transport data in unintended ways).
Most malware is simply downloaded from the Internet with or without the user’s knowledge. Sometimes legitimate sites get compromised, leading to infections on visiting systems. Other times drive-by downloading infects the system, usually via some weird Java vulnerability delivered through an ad stream or something like it. Peer-to-peer applications or web application “features” are often hijacked to distribute malware, and an IRC channel is always a great way to distribute malware. Sending malware (usually a Trojan) via e-mail, file sharing, or a browser is also a good distribution method.
Wrappers are programs that allow you to bind an executable of your choice (Trojan) to an innocent file your target won’t mind opening. EliteWrap is an example. Crypters are software tools that use a combination of encryption, obfuscation, and code manipulation to render malware as undetectable to AV and other security-monitoring products. Exploit kit examples include Infinity, Bleeding Life, Crimepack, and Blackhole Exploit Kit.
A Trojan is software that appears to perform a desirable function for the user prior to running or installing it but instead performs a function, usually without the user’s knowledge, that steals information or otherwise harms the system (or data). Although a backdoor isn’t a Trojan, and a Trojan isn’t a backdoor, they’re tied together in this discussion and on your exam: the Trojan is the means of delivery, and the backdoor provides the open access.
Trojan types include defacement Trojans, proxy server Trojans, botnet Trojans (Tor-based Chewbacca and Skynet), remote access Trojans (RAT, MoSucker, Optix Pro, and Blackhole), and e-banking Trojans (Zeus and Spyeye). Covert Channel Tunneling Trojan (CCTT) is one form of remote access Trojan that uses a variety of exploitation techniques to create data transfer channels in previously authorized data streams. It’s designed to provide an external shell from within the internal environment.
A command shell Trojan is intended to provide a backdoor to the system that you connect to via command-line access. Netcat is known as the “Swiss Army knife” of TCP/IP hacking and provides all sorts of control over a remote shell on a target. Netcat can be used for outbound or inbound connections, over TCP or UDP, to or from any port on the machine. It offers DNS forwarding, port mapping and forwarding, and proxying. You can even use it as a port scanner if you’re really in a bind.
Port numbers in use by Trojans should be memorized for your exam:
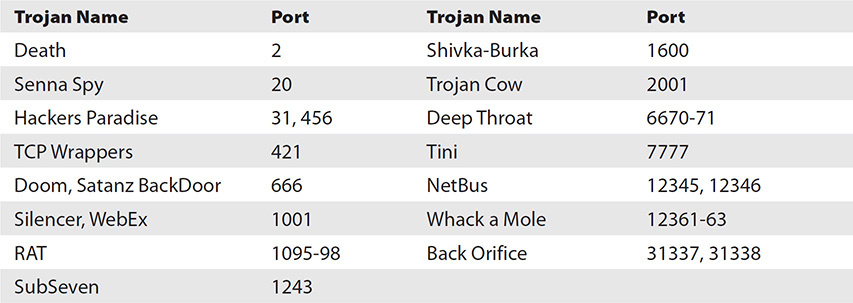
Netstat will show all connections in one of several states—everything from SYN_SEND (indicating active open) to CLOSED (the server has received an ACK from the client and closed the connection). Fport is a free tool from McAfee that reports all open TCP/IP and UDP ports and maps them to the owning applications. Process Explorer is a free tool from Microsoft (formerly from SysInternals) that can tell you almost anything you’d want to know about a running process. Some of the options for monitoring the registry are SysAnalyzer, Tiny Watcher, Active Registry Monitor, and Regshot.
Windows will automatically run everything located in Run, RunServices, RunOnce, and RunServicesOnce, and you’ll find that most questions on the exam are centered around or show you settings from HKEY_LOCAL_MACHINE.
A virus is a self-replicating program that reproduces its code by attaching copies into other executable codes. In other words, viruses create copies of themselves in other programs, then activate on some sort of trigger event (such as a specific user task, a particular time, or an event of some sort). One method for getting viruses onto a system is known as a virus hoax or fake antivirus. The process involves letting a target know about a terrible virus running rampant through the world, then providing them an antivirus program (or signature file) to protect themselves with.
Here are the virus types for exam memorization:
• Ransomware This malware locks you out of your own system resources and demands an online payment of some sort in order to release them back to you. The ransomware “family” includes examples such as Cryptorbit, CryptoLocker, CryptoDefense, and police-themed. Specific versions to know include WannaCry and Petya.
• Boot sector virus Also known as a system virus, this virus type actually moves the boot sector to another location on the hard drive, forcing the virus code to be executed first.
• Shell virus Working just like the boot sector virus, this virus type wraps itself around an application’s code, inserting its own code before the application’s. Every time the application is run, the virus code is run first.
• Cluster virus This virus modifies directory table entries so that user or system processes are pointed to the virus code itself instead of the application or action intended.
• Multipartite virus Attempts to infect both files and the boot sector at the same time. This generally refers to a virus with multiple infection vectors.
• Macro virus Usually written with Visual Basic for Applications (VBA), this virus type infects template files created by Microsoft Office, normally Word and Excel.
• Polymorphic code virus This virus type mutates its code using a built-in polymorphic engine. These viruses are difficult to find and remove because their signatures constantly change. No part of the virus stays the same from infection to infection.
• Encryption virus Shockingly, these viruses use encryption to hide the code from antivirus scanners.
• Metamorphic virus This virus type rewrites itself every time it infects a new file.
• Stealth virus Also known as a “tunneling virus,” this one attempts to evade antivirus (AV) applications by intercepting the AV’s requests to the operating system (OS) and returning them to itself instead of OS.
• Cavity virus Cavity viruses overwrite portions of host files so as not to increase the actual size of the file. This is done using the null content sections of the file and leaves the file’s actual functionality intact.
• Sparse infector virus This virus type only infects occasionally.
• File extension virus These viruses change the file extensions of files to take advantage of most people having file extension view turned off.
A worm is a self-replicating malware computer program that uses a computer network to send copies of itself to other systems without human intervention. Usually it doesn’t alter files, but it resides in active memory and duplicates itself, eating up resources and wreaking havoc along the way. The most common use for a worm in the hacking world is the creation of botnets. “Ghost Eye Worm” is a hacking tool that uses random messaging on Facebook and other sites to perform malicious actions. Other worms include the following:
• Code Red Exploited indexing software on IIS servers in 2001.
• Darlloz The worm for the “Internet of Things,” darlloz is a Linux-based worm that targets running ARM, MIPS, and PowerPC architectures.
• Slammer Also known as SQL Slammer, this was a denial-of-service worm attacking buffer overflow weaknesses in Microsoft SQL Services.
• Nimda A successful file infection virus that modified and touched nearly all web content on a machine.
• Bug Bear Propagating over open network shares and e-mail, Bug Bear terminated AV applications and set up a backdoor for later use.
• Pretty Park Pretty Park spread via e-mail (attempting a send every 30 minutes) and took advantage of IRC to propagate stolen passwords and the like.
Tools like binText and UPX can help in malware analysis. Others that can help are IDA Pro (www.hex-rays.com), VirusTotal (www.virustotal.com), Anubis (Anubis.iseclab.org), and Threat Analyzer (www.threattracksecurity.com).
The standard DoS attack seeks to accomplish nothing more than taking down a resource or denying access to it by authorized users. The distributed denial-of-service (DDoS) attack comes not from one system but many, and they’re usually part of a botnet. The botnet is a network of zombie computers the hacker can use to start a distributed attack from (examples of botnet software/Trojans are Shark and Poison Ivy). For study purposes, the preferred communications channel used to signal the bots is IRC or Internet Chat Query (ICQ). Another way of saying “botnet” may be the distributed reflection denial of service (DRDoS) attack, also known as a spoof attack. It uses multiple intermediary machines to pull off the denial of service, by having the secondary machine send the attack at the behest of the attacker. The attacker remains hidden because the attack appears to originate from the secondary machine.
ECC lists four basic categories of Dos/DDoS as well as several examples of DoS/DDoS attacks. The categories are as follows:
• Fragmentation attacks These attacks take advantage of the system’s ability (or lack thereof) to reconstruct fragmented packets.
• Volumetric attacks Also known as bandwidth attacks, these consume all available bandwidth for the system or service.
• Application attacks These attacks consume resources necessary for the application to run, effectively making it unavailable to others.
• TCP state-exhaustion attacks These attacks go after load balancers, firewalls, and application servers by attempting to consume their connection state tables.
Here’s a short list of attacks, with all the salient information you’ll need:
• SYN attack The hacker will send thousands upon thousands of SYN packets to the machine with a false source IP address. The machine will attempt to respond with a SYN/ACK but will be unsuccessful (because the address is false). Eventually, all the machine’s resources are engaged, and it becomes a giant paperweight.
• SYN flood In this attack, the hacker sends thousands of SYN packets to the target but never responds to any of the return SYN/ACK packets. Because there is a certain amount of time the target must wait to receive an answer to the SYN/ACK, it will eventually bog down and run out of available connections.
• ICMP flood Here, the attacker sends ICMP Echo packets to the target with a spoofed (fake) source address. The target continues to respond to an address that doesn’t exist and eventually reaches a limit of packets per second sent.
• Smurf The attacker sends a large number of pings to the broadcast address of the subnet, with the source IP spoofed to that of the target. The entire subnet will then begin sending ping responses to the target, exhausting the resources there. A fraggle attack is similar but uses UDP for the same purpose.
• Ping of death (This isn’t a valid attack with modern systems, but is still a definition you may need to know.) In the ping of death, an attacker fragments an ICMP message to send to a target. When the fragments are reassembled, the resultant ICMP packet is larger than the maximum size and crashes the system.
• Teardrop In a teardrop attack, a large number of garbled IP fragments with overlapping, oversized payloads are sent to the target machine. On older operating systems (such as Windows 3.1x, Windows 95, and Windows NT operating systems), this takes advantage of weaknesses in the fragment reassembly functionality of their TCP/IP stack, causing the system to crash or reboot.
• Peer to peer In this attack, clients of a peer-to-peer file-sharing hub are disconnected and directed to connect with the target system.
• Permanent Phlashing refers to a DoS attack that causes permanent damage to a system. Usually this includes damage to the hardware and can also be known as bricking a system.
The real answer to a true DDoS is the involvement of your ISP up channel. It will be next to impossible for you, at an endpoint locale, to keep up with attacks from a sophisticated global, or even geographically close, botnet. The ISP may wind up blocking a lot of legitimate traffic too, but it may be all you can do until the storm passes.
In session hijacking, an attacker waits for a session to begin and, after all the pesky authentication gets done, jumps in to steal the session for himself. The server isn’t even aware of what happened, and the client simply connects again in a different session. The following more completely describes the session hijack steps (per EC-Council):
1. Sniff the traffic between the client and the server.
2. Monitor the traffic and predict the sequence numbering.
3. Desynchronize the session with the client.
4. Predict the session token and take over the session.
5. Inject packets to the target server.
You’ll need to remember that the sequence numbers increment on acknowledgment. Additionally, you’ll almost certainly get asked a scenario version of sequence numbering. You’ll need to know, given an acknowledgment number and a window size, what sequence number would be acceptable to the system. For example, an acknowledgment of 105 with a window size of 200 means you could expect sequence numbering from 105 through 305.
IPSec is used to secure IP communication by providing encryption and authentication services to each packet, and it has several architectural components you’ll need to know. First, IPSec works in two modes. In transport mode, the payload and ESP trailer are encrypted; however, the IP header of the original packet is not. Transport can be used in network address translation (NAT) because the original packet is still routed in exactly the same manner as it would have been without IPSec. Tunnel mode, however, encrypts the whole thing, encapsulating the entire original packet in a new IPSec shell. This makes it incompatible with NAT. The rest of IPSec architecture includes the following protocols:
• Authentication Header AH is a protocol within IPSec that guarantees the integrity and authentication of the IP packet sender.
• Encapsulating Security Payload ESP is a protocol that also provides origin authenticity and integrity, but it can take care of confidentiality (through encryption) too. ESP does not provide integrity and authentication for the entire IP packet in transport mode, but in tunnel mode protection is provided to the entire IP packet.
• Internet Key Exchange IKE is the protocol that produces the keys for the encryption process.
• Oakley A protocol that uses Diffie-Hellman to create master and session keys.
• Internet Security Association Key Management Protocol Software that facilitates encrypted communication between two endpoints.
Questions
1. Which of the following doesn’t define a method of transmitting data that violates a security policy?
A. Backdoor channel
B. Session hijacking
C. Covert channel
D. Overt channel
2. Which virus type is only executed when a specific condition is met?
A. Sparse infector
B. Multipartite
C. Metamorphic
D. Cavity
3. Which of the following propagates without human interaction?
A. Trojan
B. Worm
C. Virus
D. MITM
4. Which of the following don’t use ICMP in the attack? (Choose two.)
A. SYN flood
B. Ping of death
C. Smurf
D. Peer to peer
5. Which of the following is not a recommended step in recovering from a malware infection?
A. Delete system restore points.
B. Back up the hard drive.
C. Remove the system from the network.
D. Reinstall from original media.
6. Which of the following is a recommendation to protect against session hijacking? (Choose two.)
A. Use only nonroutable protocols.
B. Use unpredictable sequence numbers.
C. Use a file verification application, such as Tripwire.
D. Use a good password policy.
E. Implement IPSec throughout the environment.
7. Which of the following attacks an already-authenticated connection?
A. Smurf
B. Denial of service
C. Session hijacking
D. Phishing
8. How does Tripwire (and programs like it) help against Trojan attacks?
A. Tripwire is an AV application that quarantines and removes malware immediately.
B. Tripwire is an AV application that quarantines and removes malware after a scan.
C. Tripwire is a file-integrity-checking application that rejects malware packets intended for the kernel.
D. Tripwire is a file-integrity-checking application that notifies you when a system file has been altered, potentially indicating malware.
9. Which of the following DoS categories consumes all available bandwidth for the system or service?
A. Fragmentation attacks
B. Volumetric attacks
C. Application attacks
D. TCP state-exhaustion attacks
10. During a TCP data exchange, the client has offered a sequence number of 100, and the server has offered 500. During acknowledgments, the packet shows 101 and 501, respectively, as the agreed-upon sequence numbers. With a window size of 5, which sequence numbers would the server willingly accept as part of this session?
A. 102 through 104
B. 102 through 501
C. 102 through 502
D. Anything above 501
11. Which of the following is the proper syntax on Windows systems for spawning a command shell on port 56 using Netcat?
A. nc -r 56 -c cmd.exe
B. nc -p 56 -o cmd.exe
C. nc -L 56 -t -e cmd.exe
D. nc -port 56 -s -o cmd.exe
12. Which of the following best describes a DRDoS?
A. Multiple intermediary machines send the attack at the behest of the attacker.
B. The attacker sends thousands upon thousands of SYN packets to the machine with a false source IP address.
C. The attacker sends thousands of SYN packets to the target but never responds to any of the return SYN/ACK packets.
D. The attack involves sending a large number of garbled IP fragments with overlapping, oversized payloads to the target machine.
13. Which of the following best describes a teardrop attack?
A. The attacker sends a packet with the same source and destination address.
B. The attacker sends several overlapping, extremely large IP fragments.
C. The attacker sends UDP Echo packets with a spoofed address.
D. The attacker uses ICMP broadcast to DoS targets.
Answers
1. D. Overt channels are legitimate, and used legitimately. Everything else listed would be in violation of a security policy.
2. A. Sparse infector viruses only fire when a specific condition is met. For example, maybe the fifth time Calculator is run, whammo!—virus execution.
3. B. Much like Skynet from the Terminator movies, worms do not need us.
4. A, D. A SYN flood doesn’t use ICMP at all, nor does a peer-to-peer attack.
5. B. Backing up a hard drive that’s already infected makes as much sense as putting ketchup on a doughnut. The malicious files are on the drive, so backing it up does nothing but ensure you’ll reinfect something later on.
6. B, E. Unpredictable sequence numbers make session hijacking nearly impossible, and implementing IPSec—which provides encryption and authentication services—is also probably a good idea.
7. C. Session hijacking takes advantage of connections already in place and already authenticated.
8. D. Tripwire is one of the better-known file integrity verifiers, and it can help prevent Trojans by notifying you immediately when an important file is altered.
9. B. Volumetric attacks consume all available bandwidth for the system or service.
10. A. Starting with the acknowledged sequence number of 101, the server will accept packets between 102 and 106 before sending an acknowledgment.
11. C. This is the correct syntax for using Netcat to leave a command shell open on port 56.
12. A. The distributed reflection denial-of-service (DRDoS) attack is, for all intents and purposes, a botnet. Secondary systems carry out the attacks so the attacker remains hidden.
13. B. In a teardrop attack, the reassembly of fragments takes down the target.