1. Get Your Free Credit Cards Here
Phoenix cannot believe what is in front of his eyes. You would think a bank statement would not make such an impact on a person, but this one does. The statement from PDXO Financial Bank informs Phoenix that his credit card rate has just gone up to 29% because he was late one payment. With an interest rate like this, Phoenix has little hope of ever paying off his $12,000 balance. In his frustration Phoenix begins to plot a way to get back at the bank.
At first Phoenix thinks he will hack into the bank and obliterate his credit card debt. This, however, might be too obvious and raise too much suspicion. Instead, he must find a way to pay off his debt without making it appear like any system is compromised. After much deliberation Phoenix comes up with the perfect plan.
First, Phoenix will gather information about the bank’s Web site and find a way to compromise the bank through its Web site. Then he will hack into the bank’s Web site and attempt to steal credit card information. Although he could just use someone else’s card to pay off his debt, he thinks this might raise too much suspicion when the card owner discovers a $12,000 payment. Instead, Phoenix plans on selling the credit cards that he steals from the bank on the underground market. After receiving payment, he can pay off his debt.
To mitigate the chances of getting caught, Phoenix will also use a popular hacker technique of distraction, whereby he will launch a secondary attack that the bank will discover and investigate. By distracting the bank with a secondary attack, it will spend so much time investigating that attack that it will not be suspicious of somebody paying off a credit card debt of $12,000. Phoenix decides he will try Web site defacement as his secondary attack.
In summary, the steps Phoenix will take are
1. Enumerate the Web site.
2. Enumerate the credit card database.
3. Steal credit card information from the Web site.
4. Sell the credit card information on the underground market.
5. Deface the Web site.
This chapter details the steps Phoenix takes and concludes with possible countermeasures to mitigate the risk.
Enumeration
Enumeration is the process of getting more information about a victim or target. In this chapter, enumeration refers to discovering information about the Web site and credit card database. For example, it is helpful for Phoenix to enumerate the operating system that the Web site is running on because this information helps Phoenix to know what type of vulnerabilities he can try to exploit.
This section includes the details of each step in Phoenix’s chained exploit, including
• Enumerating the PDXO Web Site
• Enumerating the Credit Card Database
• Stealing Credit Card Information from the Web Site
• Selling the Credit Card Information on the Underground Market
• Defacing the PDXO Web Site
The section ends with a summary of this chained exploit.
The first step for Phoenix is to enumerate the Web site for PDXO Financial Bank. Contrary to what you might think, he does not start with pulling up the Web site. That is not going to help him with his first step of enumeration. Instead, he needs to discover the operating system and Web server version running on the site. One excellent means of accomplishing this is to examine the HyperText Transfer Protocol (HTTP) header. HTTP is a request/response standard between a client and a server. When you connect to a Web server with your browser, an HTTP request is sent. Every Web server returns HTTP response headers formatted according to Request for Comments 2616 (RFC 2616). Valuable information is found inside this response, such as the Web server version. Knowing the Web server version helps the hacker because it allows the hacker to know which exploits to try based on the Web server version. For example, after the hacker knows it is a Microsoft IIS server, the hacker can use the vulnerabilities associated with that server. It makes no sense to try an exploit designed to attack an Apache Web server when the target server is running Microsoft IIS (and vice versa).
Normally you never see what is sent in an HTTP response. Your browser merely receives the information from the Web server, interprets it as necessary, and displays the Web site in your browser. Phoenix needs to see this response so that he can know which Web server version is running. He begins by going to a command prompt on his computer. Next he connects to the Web server using Telnet. Instead of using the standard Telnet TCP port of 23, however, he connects to the Web server on the HTTP port of 80 by typing the following:
C: elnet www.PDXOfinancial.com 80
This command connects Phoenix directly to the Web server. Nothing will be returned however when this command is entered because Phoenix has not yet sent an HTTP request. To get the response Phoenix needs he sends an HTTP HEAD command to view the HTTP header. The HTTP header reveals information as to the type of Web server software used by PDXO Financial Bank. Phoenix types this command followed by two carriage returns (cr):
HEAD / http / 1.1
[cr]
[cr]
The response comes back as follows:
HTTP/1.1 200 OK
Server: Microsoft-IIS/5.0
Date: Thu, 07 Jul 2005 13:08:16 GMT
Content-Length: 1270
From this output Phoenix discovers that the bank is using Microsoft IIS v5.0 server. This helps Phoenix as he now knows that he needs to look for ways to exploit an IIS 5.0 server.
GoolagScan
One tool you should look at for discovering possible vulnerabilities on your Web site is GoolagScan by Cult of the Dead Cow (http://www.cultdeadcow.com). This tool uses the Google hacking techniques discovered by Johnny Long (johnny.ihackstuff.com). This tool executes specially crafted Google searches against a Web site to discover weaknesses such as files containing passwords, vulnerable files, and sensitive directories. It is a must-have tool for anyone involved in assessing the weaknesses of a Web site.
Phoenix thinks about what else he knows about PDXO Financial Bank. He remembers that it recently sent out a notice that it had just merged with a bank in Chicago. Bank mergers inevitably mean changes to a bank’s Web site. Often, companies make the mistake of leaving on the Web server development sites that might not be as secure as the production site. Phoenix begins to look for these development sites. He tries entering the following addresses in his browser:
This last one worked! It pulls up the page shown in Figure 1.1. The page is simple and is used by Web developers for testing code. Bank users should not be able to access this developer site, but chances are the developers were not careful in locking it down.
The developer site has a form for logging in to the bank. Phoenix smiles because he knows that this form might just give him the access he needs to get the credit card information.
The next step for Phoenix is to enumerate the database used to store the account information. The login form will connect to the database that he needs information from. So, by using the username field, he can attempt to enter Structured Query Language (SQL) commands to discover the name of the database. This requires several weaknesses in the Web site to line up, so Phoenix is crossing his fingers that the developers left the vulnerabilities on the site. These weaknesses include
• The database is stored on the same server as the Web site.
• Microsoft SQL Server is used to host the database.
• The default username of SA with no password is being used to connect to the database.
• The Web site is installed in the default location (c:inetpubwwwroot).
• The Web site directory allows write access.
Because the Web site is running Microsoft IIS Server (discovered earlier in Web site enumeration), it is likely that the database is Microsoft SQL Server. The other weaknesses are probably present because the site is for developers only and therefore might not be as secure as a production site.
Note
It might sound like we are picking on developers for having weak security. On the contrary, the weaknesses exist not because of poor code and implementation from developers but because management does not see the need for allotting time to put security measures in place for developer teams. Usually the push is for developers to meet deadlines and often that means cutting corners on security. Management needs to be aware of the importance of application security and access control and ensure that procedures are in place to implement security from the beginning to the end of the development life cycle.
SQL injection is a technique of entering SQL commands directly into a SQL server from a Web site. Normally, this developer Web site should not allow any SQL commands to be entered in the form. Instead, only usernames and passwords should be allowed. However, unless code is entered to sanitize the input, a hacker could potentially send SQL commands directly to the database. This is dangerous because it allows hackers to grab all data from your database.
The first step Phoenix takes is to discover a list of databases on the server. On Microsoft SQL Server there is a default database called Master. Each database has several tables that consist of columns and rows that store data. Inside the Master database is a table called sysdatabases that lists all the databases on the server. The command to view a list of all databases is
select * from master..sysdatabases
Unfortunately for Phoenix, he cannot just enter the command and view the output. Instead, he needs to trick the server into allowing him to enter this command. Currently the Web site is expecting a username to be entered in the first form field. Phoenix needs to enter a new command that the server is not expecting. In SQL, a semicolon is used to end a command. Phoenix will trick the server into thinking a previous command is over and a new command is about to be entered by preceding his SQL command with a semicolon:
; select * from master..sysdatabases
To ensure that no other commands are entered after his SQL command, Phoenix needs to comment out the rest of any remaining SQL code programmed on the Web site. By commenting out the remaining code following his SQL command, it will trick the SQL server into thinking that any code following his command is strictly comments written by a SQL developer and not actual code to be executed. To comment out any code following Phoenix’s SQL command he follows his command with two dashes as follows:
; select * from master..sysdatabases--
Although this command would work it will not generate any output on the screen. Phoenix will need to send output to another file on the Web site that he can retrieve. One method of sending this data to a file is to use the command-line utility OSQL. OSQL is included with Microsoft SQL Server and allows you to enter SQL commands from an MS-DOS command prompt. By entering commands from a command prompt you can then pipe, or send, the output to a text file. The OSQL command-line options are shown here:
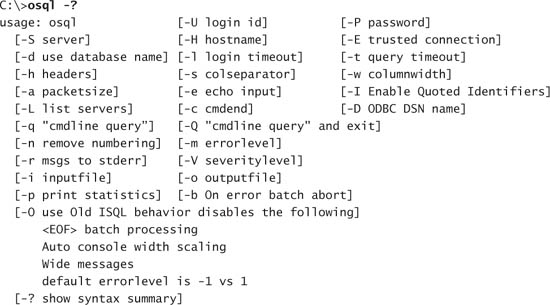
The parameters Phoenix will use and their explanations are shown in Table 1.1.
Phoenix will attempt to send his output of his command to a new text file on the server. The default location of a Web site on Microsoft IIS 5.0 Server is c:inetpubwwwroot. Phoenix will send the output of his command to a new file that he will store in this directory so that he can view it in his Web browser. His complete OSQL command is
osql -U sa -P "" -Q "select * from master..sysdatabases" -o c:inetpubwwwroot
Phoenix is not done yet though. OSQL is a command-line utility and therefore needs to be entered from an MS-DOS command prompt. However, Phoenix is not on a command prompt on the server. Instead, he is accessing a Web form on a developer Web site. Luckily for him, Microsoft includes stored procedures, which are a precompiled set of SQL statements. One such stored procedure is xp_cmdshell, which allows you to enter a command from a command prompt from within SQL. To execute this stored procedure, Phoenix would type
exec xp_cmdshell ' <insert command here>'
Putting the command all together, Phoenix types the complete command as follows in the username field:
; exec xp_cmdshell 'osql -U sa -P "" -Q "select * from master..sysdatabases" -o
c:inetpubwwwrootoutput.txt'--
There are a lot of components in this command. Figure 1.2 summarizes the process Phoenix is taking to enumerate the database. Phoenix accesses the developer Web site, which allows him to enter SQL commands. He enters the xp_cmdshell stored procedure, which allows him to use the OSQL command-line utility. He uses OSQL so that he can enter a SQL command and send the output to a text file. The output is sent to a text file accessible from his Web browser.
Phoenix clicks the Login button. A few seconds later a Web page is returned saying The page cannot be displayed. Phoenix doesn’t worry, though, because he knows that his command was executed successfully. The Web site returns this page because it was expecting a username and password and not the SQL command Phoenix entered. Phoenix changes the URL to http://www.pbxofinancial.com/output.txt to view the output of his SQL command. Here is a partial output:
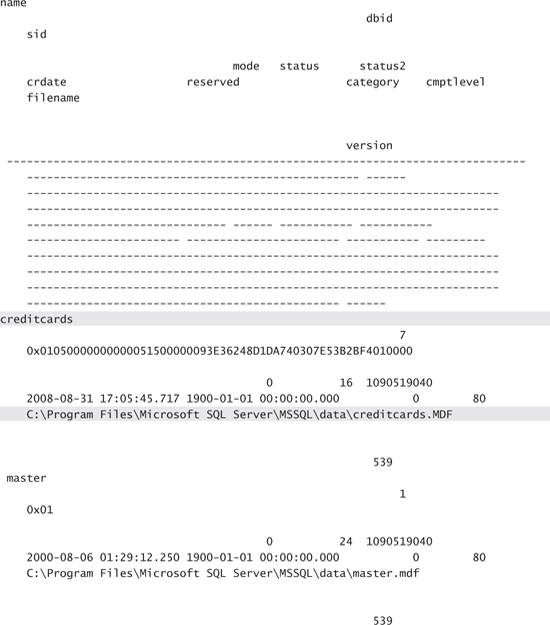
Phoenix found what he was looking for. There is a database called creditcards. In fact, the output even tells Phoenix that the path to the database file is C:Program FilesMicrosoft SQL ServerMSSQLdatacreditcards.MDF.
Phoenix now needs to determine the list of table names within this credit card database. The command to enumerate the table names is
select * from creditcards..sysobjects
Phoenix returns to the login page and enters the complete command to enumerate the tables and output the results to a text file:
; exec xp_cmdshell 'osql -U sa -P "" -Q "select * from creditcards..sysobjects" -o
c:inetpubwwwroot ables.txt'--
After clicking Login, Phoenix waits a few seconds for the command to complete. As before, nothing will be shown on his screen but a Page Not Found message, but he knows that the output is sent to tables.txt. He pulls up the page www.PDXOfinancial.com/tables.txt in his Web browser. A few pages of output fill his screen. He scrolls through it looking for anything that might contain the actual credit card numbers. Eventually he comes across the following output:

His eyes fall on the table named cardnumbers. This is his jackpot. What he needs to do now is extract the credit card values from this table.
Each row in a table is one credit card account. Therefore the first step to stealing the credit card information is to select all the rows in the credit card table. To select all rows, his command would be
select * from creditcards..cardnumbers
Returning to the login page, he enters the following command to send the information stored in the cardnumbers table to a file called cards.txt:
; exec xp_cmdshell 'osql -U sa -P "" -Q "select * from creditcards..cardnumbers" -o
c:inetpubwwwrootcards.txt'--
Phoenix lets out a slight smile as he prepares to view his results. He navigates in his Web browser to www.PDXOfinancial.com/cards.txt. What he finds is astonishing; the output contains not only the numbers, but also the names of the account holders, the expiration dates, and the credit card verification (CCV) codes on the back of the cards! Here is a partial output that appears on his screen:

Phoenix saves this file on his local hard drive.
With the credit card numbers in his possession, Phoenix now can start looking for a prospective buyer for these account numbers. He launches NewsRover, a common newsgroup-viewing application, and logs in to the alt.2600 newsgroup. This newsgroup is for readers for 2600 magazine (http://www.2600.com), a popular magazine that discusses telephony hacking (called phreaking) and computer hacking. Phoenix is going to post a message about his cards here because he knows it will reach the highest number of people who might be looking for this kind of information.
Phoenix is concerned, however, that with the newsgroup being public it may catch the eye of law enforcement. He certainly cannot use his real e-mail address, so he quickly sets up an anonymous Gmail account called [email protected]. He knows he cannot simply offer to sell credit cards because law enforcement would quickly spot that. Instead, he visits the site www.spammimic.com. This is a site that will disguise a message into what looks like a spam advertisement but in reality contains your message. Figure 1.3 shows the Spammimic Web site. It gives you the additional options of encoding the message with a password, encoding as a fake PGP message, or encoding as fake Russian text.
After clicking the Encode button, he is shown the output in Figure 1.4. Although it looks like a typical spam advertisement, those familiar with this site will know to take the message and decode it on Spammimic’s Web site.
Phoenix copies the encoded message and posts it in the alt.2600 newsgroup.
Now Phoenix sits back and waits for someone to view his posting and respond. He isn’t worried that it looks like spam because he knows that people who browse these types of newsgroups know to copy the spam message into Spammimic’s Web site. As soon as someone copies the text into the Spammimic Web site and clicks the Decode button he will see this message:
Credit cards for sale. E-mail me at [email protected]. $12,000 for 50,000 cards with names, CCV numbers, and expiration dates.
The next day, Phoenix checks his e-mail account and discovers four e-mail messages from people who want to purchase his stolen credit card numbers. He responds back to the first one and arranges payment to an offshore bank account in Switzerland. Within a few hours the money is transferred and Phoenix has $12,000. That $12,000 is enough to pay off his bill, so he writes PDXO Financial Bank a check for $12,000. He also realizes that he just gave his credit card number away to a stranger so he immediately cancels his card.
Although Phoenix could have made off with a lot more money by using the stolen credit cards, it is much easier to track down the person using the stolen credit cards than it is the one who sold the cards in the first place.
Now that Phoenix has sold the credit card information, he wants to deface the bank’s Web site to teach the bank a lesson. His goal in defacing the Web site is to send a message to the bank that it should not raise interest rates because there will be consequences. Defacing a Web site is a common attack used by malicious hackers when they want to get a message across. Often it is a form of hacktivism, where malicious hackers want to deface a site for political or religious reasons. But in this case Phoenix is doing it to protest the recent rise in the credit card interest rate.
Phoenix returns to the bank’s Web site. At this point he already knows the following about the site:
• It is running on a Microsoft IIS 5.0 Web server.
• It is using Microsoft SQL Server.
• The SQL server software is using the default username of SA with no password.
• The SQL server software is hosted on the same computer as the Web site.
• SQL stored procedures are on the server, which allow him to use the xp_cmdshell command.
In the previous attack Phoenix used the xp_cmdshell stored procedure to copy the credit cards to a text file. Now, Phoenix will attempt to use the same stored procedure to overwrite the default home page on the site. By default the home page is installed on Microsoft IIS 5.0 in the c:inetpubwwwroot directory and is called default.asp. It is good practice to change the default home page to a different directory because leaving it in the default location makes it easier for malicious hackers to deface the site. Considering the other weaknesses in the site, including installing Microsoft SQL Server on the same computer as IIS 5.0, keeping the credit card database on the C partition instead of a separate partition, and using the default install path of c:inetpubwwwroot, Phoenix knows that defacing the site will be easy. All it takes is a single command in the username prompt on the Web site.
On the Web site Phoenix types the following command in the username box.
; exec xp_cmdshell 'echo You've-been-hacked! > c:inetpubwwwrootdefault.asp'--
This command overwrites the default.asp page with a new page that says “You’ve-been-hacked!” Phoenix cannot believe how easy this is.
Note
You can view archived copies of many defaced sites by visiting http://www.zone-h.org. Here you will find defaced Web pages from around the world, including many that belong to government and military organizations.
The following are the steps Phoenix took in this chained exploit:
1. Phoenix enumerated the Web site to gather as much information as possible, including operating system and Web server software version.
2. Phoenix then enumerated the credit card database to learn of the database table names.
3. Using SQL injection, Phoenix stole the entire credit card database from the bank’s Web site.
4. Phoenix posted a message on a newsgroup and sold all the credit cards.
5. Phoenix defaced the Web site.
If you run a Web site that stores people’s credit card information, you might be at risk to the type of attack Phoenix performed in this chapter. Luckily there are several countermeasures you can employ to safeguard against this type of attack.
Earlier in the chapter Phoenix was able to determine that the target Web site was running Microsoft IIS. This helped him to make an educated guess that the database server was running Microsoft SQL Server (it is common in Microsoft-based environments to use IIS with SQL Server). Phoenix grabbed this information by sending an HTTP HEAD request to the Web server and reading its response. You can change this response on your Web server so that incorrect information is given back to potential hackers to confuse them. You can use URLScan, which allows you to remove the default Server HTTP header and substitute a custom entry. URLScan is a Microsoft utility that you can download from Microsoft’s Web site. To view more information on this useful utility, visit http://support.microsoft.com/support/kb/articles/q307/6/08.asp.
In this chapter Phoenix was able to hack into the bank using the developer site. It is common for developers to set up staging sites for testing before updating the code on a production site. The danger lies in the possibility that a developer site might not implement the same level of effective security controls to protect against attacks. You should never allow public access to any developer staging sites. All development sites should be on a separate network internal to an organization. Furthermore, the development site should not be attached to the corporate network to prevent against insider attacks. Ideally, you should have a separate network for development/staging work, one for quality testing prior to production, and a third for your production site.
Phoenix was able to execute the commands in this attack because the SQL Server installation was on the same computer as the IIS Web server. SQL Server should be installed on a separate computer to make it more difficult for attackers to enter SQL commands through a Web site.
Phoenix entered SQL commands directly through a Web form. This is very dangerous. A Web form should be programmed to allow only a certain number and type of characters. For example, it would have made Phoenix’s attack much more difficult if the form field still allowed only up to eight characters and those eight characters could be only letters or numbers. There are ways for Phoenix to get around this limitation, but this countermeasure would make it more difficult for him.
This example had IIS installed in the default location of c:inetpubwwwroot. This is dangerous because it is too predictable for hackers to deface Web pages and create new pages because they know the path to the Web site. Never install IIS in this location. Also, install it on a partition separate from the C partition. This prevents hackers from some directory traversal attacks (not discussed in this chapter).
If possible, make your Web site read-only. Phoenix was able to send the output of his SQL commands to new files that he created. By making the directories of your Web site read-only, Phoenix would not have been able to create new files.
Phoenix used the xp_cmdshell stored procedure to execute his attack. If you do not need the default Microsoft stored procedures, remove them from your database. This is a minor countermeasure, however, because there are commands you can enter to re-create the default stored procedure. It is also unrealistic in many environments that have come to depend on Microsoft stored procedures for managing their database. Nevertheless, it is an option to consider.
Phoenix was able to hack the database because it used the default username of SA with the default blank password. In later versions of SQL Server this is removed, and you are forced to enter a username and password. But earlier versions defaulted to SA with no password. When you install SQL Server, make sure that you always use a secure password.
In addition to these countermeasures for companies, there are also some considerations for the customers. None of these would prevent the attack performed in this chapter, but they are useful tips to help you be a smart consumer.
Frequently check your bank account for any suspicious activity. Look for purchases you are not aware of or sudden changes in your balance as signs that your account might have been compromised. Do not always assume that hackers will make a large purchase. Often, they will start with a few small purchases to verify that the account is good and that they can use your card without raising suspicion. Be sure to verify all transactions, no matter how small.
Most financial institutions offer insurance to protect you in the event of a security compromise. Many even offer this service at no cost. Check with your bank to see what insurance you have if your card is stolen.
Some popular Web browsers offer you the option of saving your password when visiting sites. You should not save the password to your online banking site because doing so would give someone who gains unauthorized access to your computer the ability to automatically log in to your account. Although this countermeasure would not prevent the attack performed by Phoenix in this chapter, you should make sure you never save your password in case your computer is stolen.
In the event that your account is compromised, your bank may close your account. You might be without access to funds for a while until a new account is opened and a new card is issued in your name. In the interim, make sure you have a backup account that you can use to get you by while you wait for the new card. Hopefully you will never have to use it, but it is a good idea to have an extra account with enough funds to get you by for a short period before you get access to your account again.
The attack Phoenix performed in this chapter is just one of many ways hackers will compromise banking sites. Each year these attacks cost banks millions in losses. Most of the weaknesses in the fictitious bank in this chapter are ultimately the result of poor management and not poor technology. Security should start from the top down, and that means management needs to recognize the importance of security and push that importance down to all facets of an organization. Code and infrastructure security audits should hold the same value as producing the code and implementing the network. If the management in PDXO Financial Bank recognized this and ensured that processes were in place to ensure security prior to rolling out code into production, none of the vulnerabilities in this chapter would have existed.