6. Gain Physical Access to Healthcare Records
Derek is a courier at Regional Care Center. It is one of the larger medical facilities in the tri-county area. Derek’s primary day-to-day routine is to transport medical records to and from other medical facilities. He also helps with the daily input of information into the electronic medical records (EMR) program during downtime. This program was installed about a year ago and is very versatile with all the bells and whistles including prescription writing, document management, transcription, and more. After four years of dedicated employment at Regional Care Center, Derek is very well accepted by the nursing staff and administration. Everyone knows him because he has the unique position of meeting and interacting on a day-to-day basis with a large part of the staff. Recently, things at the office have been tense and he has heard some rumblings in the past week about cutbacks. He has been told that his position is being eliminated due to cutbacks. Derek can finish out the week and he will be provided a compensation package based on his time in-service.
Shock! Derek is devastated. He is the sole provider for his wife and two teenage children. He needs this job because the health benefits are helping pay for his wife’s medical bills.
Derek remembers that several months ago a very prominent politician came into Regional Care Center feeling ill. After various tests the results showed he had a bad case of flu, but a test also revealed that he was positive for HIV. This information was not to be disclosed to anyone because it might have serious implications for his political career. However, like a lot of other cases with juicy information, it didn’t take long for it to filter through the company. Blackmail? Could Derek ever think of this? Thoughts start racing through his head. How much money would that information be worth to the media or to the politician himself? How is he going to retrieve the records and what will he do with them after he gets them? He remembers watching a program on TV about how teenage kids could hack into computers. At the time this amused him because he couldn’t understand why anyone would want to break into a computer. Now he knows why.
Derek makes contact with the politician and works out a deal: Derek will change the politician’s medical information to erase any record of HIV in exchange for a large sum of money. Derek needs to hire someone to help him with this task.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA was initiated in 1996 and fully implemented in April 2006. It comprises rules that doctors, hospitals, insurance companies, self-insured organizations, and other healthcare providers must follow. HIPAA was designed to ensure that all medical records, medical billing, and patient accounts meet certain consistent standards with regard to documentation, handling, and privacy. These policies were created to protect you as the recipient of services from a healthcare provider and its affiliates within the United States.
The HIPAA policy on medical records is all well and good, but what if Derek just wants to change a medical record? HIPAA requires that all patients be able to access their own medical records, correct errors or omissions, and be informed how personal information is shared. Is changing a medical record allowed? Yes. Unless he wants to change the diagnosis, that is. Maybe he wants to change the diagnosis to avoid insurance complications. Or, as in this case, for financial gain. If Derek can get his hands on the politician’s medical records, he could use that information as leverage against the public figure.
Medical Record Tampering In The Real World
Country western singer Tammy Wynette’s medical records were sold to the National Enquirer for $2,610. World champion tennis pro Arthur Ashe’s records of testing positive for HIV were leaked to the press and subsequently published in the newspaper. If a person wanted to murder someone, they could just adjust their target’s EMR to increase their intake of potassium because they know the target has an IDC-9 code of 428.0 (congestive heart failure) and an increase of potassium would be very dangerous. Sounds rather James Bond–like, but it is very possible.
Now that you have an idea of why someone would want to obtain, change, or steal medical records, let’s look at one way that a person might go about actually obtaining or changing EMR.
First and foremost, Derek will need expert skills—skills he does not possess. Derek will have to hire someone to do his dirty work. He will need to gain physical access to the records department or at the very least a PC on the internal LAN. Derek’s hire (a Black Hat, code named Phoenix) might look at several avenues to do this transaction. The steps Phoenix is going to take to gain access to the institution and the data file are as follows:
1. Use social engineering and piggybacking to gain valuable information for the infiltration.
2. Use lock picking and defeat biometrics to gain access to the site.
3. Boot into Windows with Knoppix to commandeer a PC to modify personally identifiable information (PII) or protected medical information (PMI).
For years people have been breaking into computers for various reasons, but not necessarily for the reasons contemplated in this story. Most cyber crimes and hacks are random acts of destruction or deliberate theft of information for later sale. When looking at the healthcare industry, the reasons for acquiring information might be quite different.
• Financial medical identity theft: Someone is getting medical help using your name and/or other information.
• Criminal medical identity theft: You are being held responsible for the actions of another’s criminal behavior.
• Government benefit fraud: Your medical benefits are being used by another person.
The Identity Theft Resource Center (ITRC) reported a 30% increase of security breaches in a first quarter 2008 study as compared to that same study completed in 2007. This study also proved a 13.8% raise in the medical/healthcare record breaches from the previous year. These statistics are backed with ongoing incident reports, such as noted by a Network World article in the following story:
In February 2008, Tenet Healthcare, which owns more than 50 hospitals in a dozen states, last month disclosed a security breach involving a former billing center employee in Texas who pled guilty to stealing patient personal information. He got nine months in jail.
And in an identity fraud case in Sarasota, Fla. in January of 2008, an office cleaner who gained access to the patient files of an anesthesiologist who rented an office at HealthSouth Ridgelake Hospital pled guilty to fraud for ordering credit cards on the Internet with stolen patient personal information. He got two years jail time.
Lost and stolen laptops have also been a problem, with disclosure of missing personal information related to patients or employees at Duluth, Minn.-based Memorial Blood Center; Mountain View, Calif.-based Health Net; Sutter Lakeside Hospital at Lakeside, Calif.; and the West Penn Allegheny Health System revealed just within the last three months.
According to the November 20, 2006, issue of Radiology Today, “Medical identity theft is a fast-growing crime in this country, largely because Patient Healthcare Information (PHI) is a valuable commodity. Some estimate that the black market value of a name attached to medical and insurance record is as high as $60.00 compared with just $.07 for a resume.”
This section includes the details of each step in Phoenix’s chained exploit, including
• Social Engineering and Piggybacking
• Gaining Physical Access
• Booting into Windows with Knoppix
• Modifying Personally Identifiable Information (PII) or Protected Medical Information (PMI)
The section ends with a summary of this chained exploit.
Derek needs Phoenix to obtain PMI/PII of the aforementioned political figure so that he can blackmail him. Phoenix will need to gather as much information about Regional Care Center’s employees and physical addresses. After Phoenix has this information, he will use it to gain physical access to the building where the records are stored. When he’s inside, he can commandeer a local PC to collect all medical information.
A lot has been written about social engineering and piggybacking, and yet a lot of laypeople are unfamiliar with the terms. Sun Tzu’s Art of War states “Knowledge of the enemy’s dispositions can only be obtained from other men.” Sun Tzu was referring to spies gathering information about their enemy, but it is really all in the practice of social engineering. According to Kevin Mitnick, in his book The Art of Deception, “Social engineering uses influence and persuasion to deceive people by convincing them that the social engineer is someone he isn’t, or by manipulation. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.” Although the ILOVEYOU attack was a virus attack, it also used social engineering by exploiting the emotional weakness of curious people. The deception is the words “I love you.” The attacker deceived the e-mail recipient into believing that someone loves them and to open the attachment.
Piggybacking is the second method. Piggybacking is gaining access to a restricted communications channel by using the session another user already established. That is the computer-related definition. Another definition, which is more on the social engineering side, is the act of following close behind an individual as they walk through an entry way or physical barrier. This method is also referred to as tailgating.
Let’s look at the first definition of piggybacking. When Phoenix walks up to a computer and that computer has not been logged off yet, he assumes the active session and continues to work. This scenario is one of the Holy Grails of hacking: Walk right up and just start typing away. Launch the programs the user has and assume his identity. That is the easiest method, but what if the user has a password-protected screensaver that locks the workstation? Then Phoenix would need to know the user’s password. Given time he might be able to crack it.
The second definition of piggybacking doesn’t take much, if any, computer skill—it takes social engineering skills. Always remember that the general premise behind social engineering is that people want to help and to trust. An excellent example of one piggybacking scenario might go like this: Phoenix gets his hands full of stuff—a notepad, clipboard, heavy box, and his lunch. He walks up to the door at the same time as someone else and looks like he’s about to collapse. Quickly and with no hesitation he asks that person to open the door for him before he drops everything. That person will do so, of course. The victim might ask who Phoenix is after he is inside, but first things first. He’s inside. Another scenario, which is also very effective, is dressing and acting like a phone or power and light technician. Phoenix talks with conviction and no hesitation. And before you know it he will have full access to at least the brains of the organization—the phone and server closet.
Why is social engineering successful? Humans are the weakest security link in any organization. An organization can have the best, most expensive firewalls, anti-virus, IPS/IDS (intrusion prevention system/intrusion detection system), or other security devices, but all it takes is someone like Phoenix to social engineer a person into giving him their username or password or to install a rogue wireless access point, and none of the aforementioned controls matter. Social engineering will help Phoenix obtain a great deal of information about the target before he can attack. Because Phoenix wants to gain access to patient records, a type of PII, he must first gather all the information he can about the medical office where the records reside. The best way to do that is with social engineering.
Passwords
According to a recent European survey, when asked, “What is your password,” three out of four (75%) people immediately gave the information. Another 15% were prepared to give their password when the most rudimentary social engineering tricks were used. Two-thirds of the workers in the healthcare industry have given their password to a fellow worker in the last year, and 75% used accounts of other staff members when necessary.
What does Phoenix need to find out before he can attack? This is the reconnaissance stage. It can take weeks to gain enough information about a target to mount an attack.
The following is a partial list of information Phoenix will need before starting an attack:
• Names
• Internet presence
• Phone numbers
• Hours of operations
• Types of medical procedures
• Corporate IT personnel
• Outside vendors
• Types of software
• Operating systems
• Marketing company
• Web sites
• E-mail addresses and format
• Vacation schedules
• Offices and locations
• Entry points
• Physical security/access control
• Organizational charts
• Physical location of records room
• Automated attendant
The following sections describe how Phoenix uses social engineering and piggybacking to gain this information.
Phoenix needs to get the name of everybody in the organization or as many as he can. Why and how? He needs the names so that he can either contact a specific individual or impersonate a specific individual. It wouldn’t go over very well if he tried to convince someone inside the company that he is John Doe but no John Doe works there. Now here is the meat of social engineering. There are a lot of ways to get information from a company. Phoenix should take the direct approach first: ask. A lot of times the receptionist is more than willing to tell someone who is in charge of the Human Resources department or who is in the IT department. Phoenix has found that if you act lost, dazed, or confused, people will help. It’s human nature to want to help people. What works really well is if an attacker can get access to a phone system and adjust the outbound caller ID. If, during his reconnaissance, he found internal phone numbers, he could change the outbound caller ID from another number to that internal phone number. Phoenix will get a lot more answers if the person he is calling sees caller ID come up with an internal number. If that doesn’t work, Phoenix can try the infamous dumpster diving. When dumpster diving, he will need to grab every conceivable piece of paper he can carry. He needs to take it back to a safe location and start sifting through it. This process might take days, but it can reveal a lot. Phoenix has been amazed by what he has found inside a dumpster. He has found jewels of information such as corporate phone directories, organizational charts, budgets, and vacation schedules. Nancy Drew calls this “sleuthing.” Now Phoenix has names and possibly some phone numbers.
Phoenix will need to do some searching on the Internet. By going to the company’s Web site and trying the Contact Us page, Phoenix should find a corporate phone number. He can then run a simple Nslookup command such as the following:
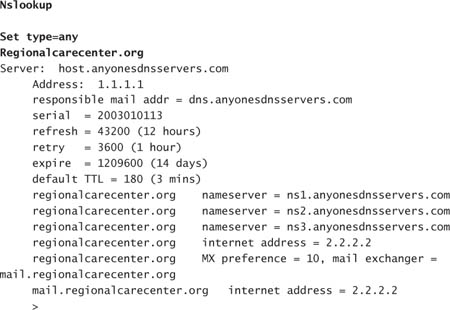
The previous Nslookup response displays several pieces of information. Does the medical center host its own mail? Where are its Web pages hosted? After Phoenix ran Nslookup, he could run the telnet command to see what was back there. This is referred to as footprinting.
Telnet mail.regionalcarecenter.org 25
220 mail.regionalcarecenter.org Microsoft ESMTP MAIL Service, Version: 6.0.3790.1830
ready at Mon, 26 Feb 2007 12:50:01 -0400
The response tells Phoenix that the Regional Care Center hosts its mail on a Microsoft Exchange Server.
Phone numbers are needed to stage a social engineering attack via the phone. Let’s say during his recon with the Web site Phoenix found Regional Care Center has several medical branches and one administrative office stretching out over several cities. Now he can make a couple of phone calls. The following might be one sample phone conversation:
Receptionist: “Thank you for calling Regional Care Center. This is Mary. How may I help you?”
Phoenix: “Hi Mary! I was at your Elm Street office to have a couple tests run and I need a copy of my record. Who might I speak to about that?”
Receptionist: “That would be the Records Department. Shall I transfer you?”
Phoenix: “Yes, thank you.”
He is transferred.
Ted in Records: “Records Department.”
Phoenix: “Hi. To whom am I speaking?”
Ted in Records: “This is Ted. How may I help you?”
Phoenix: “I need a copy of my medical records.”
Ted: “Your name, please?”
Phoenix: “John Doe.”
Ted: “Sorry, sir, I can’t find your records. When was the last time you were here for an exam?”
Phoenix: “Yesterday.”
Ted: “May I have your Social Security number?”
Phoenix: “I’m sorry, but I don’t give that out over the phone. I will come down there and get them. May I have your address?”
Ted: “Yes, 123 Main Street, Big City Canyon, Suite 203.”
Phoenix: “Thank you.”
Phoenix hangs up. He picked up two names. He learned that they search by Social Security number and, more importantly, he learned where the records are stored. The next day, he drives down to the Records Department. When entering he makes a mental note of every aspect of the office. What type and brand of locks are on the doors? Is there an alarm system and who is the manufacturer? Is there video surveillance? If so, what type of cameras? Are they digital cameras or IP cameras? Each variation has its own set of flaws.
When Phoenix gets inside, he asks for Ted because that is the person he spoke with the day before:
Phoenix: “Hi, I’m looking for Ted.”
Bill: “Ted is not here. Can I help you?”
Phoenix: “Sure, your name is?”
Bill: “Bill.”
Phoenix: “Hi, Bill. I need my medical records.”
Bill: “Your name, sir?”
Phoenix: “My name is John Doe.”
Now, Phoenix watches to see what type of computer and operating system Bill uses to look up the record. He will also try to see what program he is using to access the records, as well as the username and password he types:
Bill: “I don’t see them, sir. May I have your Social Security number?”
Phoenix: “Sure, it’s 078-05-1120.”
Bill: “Sorry, sir, I have no record.”
Phoenix: “Are you sure you are using that computer correctly? What kind is it, Linux?”
Bill: “No, sir, it’s Windows and it’s slow as ever.”
Phoenix: “Well, maybe you aren’t using the program correctly. It must not be a very good program.”
Bill: “I’m sorry, sir, but this is a very good program. It is called SOAPware and it is one of the best.”
Phoenix: “Well, maybe you aren’t inputting your username and password correctly.”
Bill: “If you will calm down, I will input it again.” (Phoenix watches this time.) “Sir, I’m sorry, but it’s just not here. At which of our facilities did you get your study done?”
Phoenix: “At Big Regional Care Center House over on Cedar Avenue.”
Bill: “Sir, I’m sorry, but we are Regional Care Center, not Big Regional Care Center House.”
Phoenix: “What, I’m at the wrong place? I’m terribly sorry. “Before I leave, may I use your restroom?”
Bill: “Yes, sir. It’s through that door, second door on the right.”
Phoenix: “Thank you.”
When Phoenix walks towards the restroom, he notices a door labeled Records.
Phoenix has just done a physical reconnaissance of the entry to the records office. What did he find? He has obtained the operating system of the PC, the name of the software the office uses and more importantly a username and password combination to get into the SOAPware software. He also noticed no cameras and no alarm system. He noticed only one door in the front and that the building appears to have good parking lot lighting. He walks around to the rear of the building and notices a loading dock and one door with poor lighting.
Phoenix is now starting the building blocks of deception.
This one is probably easy enough to find out—Phoenix just needs to call up and ask. It is public information. For that matter, it is probably on their Web site or printed on the door.
Phoenix will need to know types of medical procedures the target performs to be successful in his social engineering attack. If asked what medical exam he had done, and he tells them that he had a prostate exam, and the office is that of a podiatrist, he probably won’t get any answers. Again, this should be easy enough information to retrieve. It is probably on the company’s Web site, or he could again just call and ask them.
This information is a little tougher to get because IT personnel names generally are not publicized, or the company might use an outside IT firm. Why does Phoenix want the names of the IT personnel? If Phoenix sends an employee an e-mail from the IT director, he can almost guarantee that the employee will open it. He spoofs the IT director’s e-mail address, attaches a file to it, and maybe hides a root kit such as Hacker Defender, FU, or Vanquish in the alternate data stream. How does he get a name? As stated before, you might be surprised if you ask. In his previous phone conversation and site visit he managed to get three names: Mary, Ted, and Bill.
His phone conversation might go something like this.
Receptionist: “Thank you for calling Regional Care Center. This is Mary. How I may help you?”
Phoenix: “Hi, Mary. This is Bill over in Records.”
Receptionist: “Bill, you don’t sound like yourself.”
Phoenix: “I’m getting a darn cold, and I think my computer is too. I’m the only one here today and I need to get the computer guy here; what is his number?”
Receptionist: “Bill, you know it’s extension 2201.”
Phoenix: “Right, sorry. Must be this cold I’m getting. Thanks.”
Next phone call.
Receptionist: “Thank you for calling Regional Care Center. This is Mary. How may I help you?”
Phoenix: “Yes, extension 2201, please.”
Receptionist: “One moment.”
IT Dept. - Mark: “Hello, IT Department.”
Phoenix: “Hi, I think I have the wrong number. I’m so lost today. I’m new. What is your name?”
Mark: “My name is Mark; who are you looking for?”
Phoenix: “I was looking for HR.”
Mark: “It’s at extension 2205.”
Phoenix: “Oh good; thank you.”
Now Phoenix has the name of an internal IT person.
Because he is going to try to gain physical access, one method would be to impersonate an outside vendor. It’s easy to strap on a telephone test set (butt set) and walk right into a business. Companies are so accustomed to seeing the phone guy that these service personnel are rarely stopped. Phoenix researches the CLECs (competitive local exchange carriers) and ILEC (incumbent local exchange carrier) in the area.
When he was on site trying to get the medical records, Phoenix took note of the operating system and software the company used. In the world of EMR, there is a myriad of vendors. One item most of them have in common is the use of HL7 (health level 7) formatting to transfer clinical and administrative data.
Phoenix will need to check out the Web site again. It might tell who built the Web site. Maybe he needs to do a little bit of dumpster diving or Web site reconnaissance on the marketing company to see what little pieces of information he can pick up. Press releases are always good information. Companies do press releases for recent hires, recent promotions, and all types of valuable, yet seemingly innocuous information.
Phoenix reviews not just the Web site of the medical firm he is planning to attack, but the marketing company’s too. He might be able to obtain information from software vendors for the software his target is using.
These can be very helpful. If he sends an e-mail to someone inside the company from IT personnel, the recipient will open it. How can he spoof an e-mail address? It’s very simple:
telnet Regionalcarecenter.org 25
220 yoda.Regionalcarecenter.org ESMTP Novell
helo xyz.com
250 yoda.Regionalcarecenter.org
mail from: <[email protected]>
250 2.1.0 [email protected] OK
rcpt to: <[email protected] >
250 2.0.0 Ok
Data
354 3.0.0 End Data with <CR><LF>.<CR><LF>
Subject: Network Issues
"Please launch the attached file as we are having critical network connectivity
issues. This will help us isolate the problem."
<CR><LF>.<CR><LF>
The preceding is a simple example of how easy it would be for Phoenix to spoof an e-mail address. Here is a Visual Basic script that sends a file as an attachment:
Set objEmail = CreateObject("CDO.Message")
objEmail.From = " [email protected] "
objEmail.To = " [email protected] "
objEmail.Subject = "Network Slowdown"
objEmail.Textbody = "Please run the attached file it will run a diagnostic command
which will assist us in troubleshooting. "
objEmail.AddAttachment "C: empping.cmd"
objEmail.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/sendusing") = 2
objEmail.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpserver") = _
"smtpserver"
objEmail.Configuration.Fields.Item _
("http://schemas.microsoft.com/cdo/configuration/smtpserverport") = 25
objEmail.Configuration.Fields.Update
objEmail.Send
If Phoenix sends the preceding e-mail to someone inside the organization from inside the organization, the receiver will open it because it appears to be coming from Mark in the IT department.
Vacation schedule information might be tough to get, but it is important. Phoenix would not want to impersonate Mark from the IT department if Mark is on vacation. He might get lucky and find a vacation schedule in the dumpster. But this is not likely. So, what does he do? Perhaps the company has an intranet. Some companies use Microsoft SharePoint Server or a similar product for company calendars and contact lists. He could try to compromise the company’s intranet. There are some tips in other chapters that might help Phoenix. Another avenue would be to gain physical access. Often company calendars are posted in community areas such as kitchens, break rooms, or smoking areas.
An almost infallible method of gaining information is to have e-mails forwarded to your outside SMTP (Simple Mail Transfer Protocol) account. Vacation schedules as well as all types of company internal information are sent via e-mail.
Fortunately Phoenix previously spoke to Mark, so he knows Mark is not on vacation.
Entry points are physical access to offices. Phoenix needs to gain access to the Records office in particular. How many entry points are there? Which ones have less light? Which ones have more or less security? What else is at the Records office? Is it just a room in a fully operational 24×7 medical facility or is it a separate building that is locked after 5:00 p.m.? If the Records office is open and staffed 24×7, entry will entail overcoming some different obstacles.
Is there any in place? Does the company have guards? Does it have video surveillance? Perimeter and motion detection? Does the company use proximity cards? Does it have biometrics? Depending on the level of expertise, the physical access controls the company has implemented will influence Phoenix’s attack vector.
Organizational charts can provide a wealth of information. Phoenix will try to get his hands on a chart containing names and positions because that will give him the first big step in impersonation. Even if the organizational chart just shows positions, it is still helpful. A social engineer who has a good working knowledge of the company staff and departments will probably be more successful when making an approach than one without that information. Most staff members will assume that someone who knows a great deal about the company must surely be part of the staff. The chart might also tell Phoenix whether the company has an internal IT staff.
Where is the records room located? Phoenix found the Records office, but where is the records room? First floor? Second floor? Is it behind and through the bathroom? If he has to gain illegal entry to this office, he doesn’t want is to spend a lot of time searching for the records room.
If he calls the office and is greeted by an automated attendant; he will go through all the prompts and collect as many names, departments, and extension numbers as possible. With information like this he can begin to build his impersonation attack on the phone.
The following is a list of the information Phoenix has gathered through social engineering, piggybacking, and reconnaissance:
Names:
• Mary—Receptionist
• Ted—Records
• Bill—Records
• Mark—IT
• Jill—HR
Office Locations and Phone Numbers:

Hours of Operations:
• Records office—8:00 a.m. until 6:00 p.m.
• Main and all branch locations 24×7
• Administrative office—8:00 a.m. until 5:00 p.m.
• Web site is www.Regionalcarecenter.org.
• Mail is located at the same Internet address as the Web site.
• DNS servers—Three are in use.
Outside Vendors:
• Wendi’s Marketing—Marketing company
• Expensive Software—Software firm that provides EMR software
• My Local Phone Company—ILEC and phone system provider
• Secure Shredding and Disposal—Company hired to shred documents
• Expensive Radiology, Inc.—Performs all radiology studies
Marketing Company:
• Wendi’s Marketing, Inc.
987 Locust Street
Houston, TX
713-555-9875
Web Sites:
• Wendi’s Marketing—www.wendimarketing.com
• Phone company—www.yourlocalphonecompany.com
• Software vendor—www.expensiveEMRsoftware.com
• Shredding—www.SecureShreddingDisposal.com
• Radiology—www.ExpensiveRadiologyInc.com
Corporate IT Personnel:
• Mark—Inside IT—He is the only internal IT employee.
Types of Software and Operating Systems and Any Usernames and Passwords:
• Workstations—Microsoft Windows XP.
• Server—Microsoft 2000 or 2003.
• EMR—SOAPware: Username is 198764 and password is password.
E-mail Addresses and/or Format:
• First name followed by domain name
Example: [email protected]
This information might be found while dumpster diving.
Entry Points:
• Records office has three entry points. Front door, all glass, a back door used for employee entrance and access to the smoking area, and a loading dock.
Physical Security and Access Control:
• No alarm system, just locks on the doors for the perimeter.
• Standard 480 series deadbolt lock on perimeter door. See Figure 6.1.
• No guards.
Records Room:
• From back door, go straight down hall, second right, third door on left.
Automated Attendant:
• Yes, but only at night and to cover for missed calls when they are not answered by Mary.
• General medicine.
• Radiology is subcontracted out to Expensive Radiology, Inc.
Vacation Schedules:
• Was he able to retrieve any during the recon?
Organizational Chart:
• Yes. He has it. He found it in the dumpster.
Now that he has volumes of information, Phoenix can start to formulate an attack plan:
Should Phoenix attempt this during the day or at night? Each poses its own set of challenges. During the day he might not have to deal with locks, but he could have issues with the employees. At night, he will have to breach some locks. Based on his evaluation, Phoenix determines that night would be best because he does not want any confrontation with any employees.
To gain physical access, Phoenix must get past two locks. This can be done in two ways: He can break the doors down or pick the locks. Both methods are effective, but in different ways. If Phoenix doesn’t need to cover his tracks, the smash-and-grab technique is fine. If he wants to cover his tracks, he must pick the locks. Depending on how much practice he has at picking locks, it might take him 5 minutes or it might take 45 minutes. This is one of many skills Phoenix has to hone to perfection before attempting to pick a lock in the real world.
There are three styles of lock picking:
• Use a pick set and learn how to pick locks.
• Use a pick gun.
• Use a bump key.
Phoenix will use a bump key because he knows it doesn’t leave scaring on the tumblers like a pick gun and it is very effective.
A bump key is sometimes referred to as a “999 key” because all cuts are at the maximum depth of 9. Bump keys are effective and simple to make.
Notice in Figure 6.2 that all the keys have all the same cuts. All cuts are at the maximum depth of 9. You can cut bump keys for both regular pin tumbler locks as well as for dimple locks, whether or not they are “pin-in-pin.”
Phoenix can create his own bump keys with a file and some patience. He takes an old used key and files all the valleys down to the deepest cut already on the key.
The principle behind a bump key is to insert the key as far in as it will go, and then pull it back just one click. Phoenix will hear a click when the last pin settles in. Then he will turn the key as if he were opening the lock to put pressure on the pins. With a hammer handle, or something solid but not too heavy, he strikes the butt of the key continuously while keeping pressure on the key. If performed with the right turn pressure and strike force, the lock will open. If the lock does not turn, Phoenix has either applied too much pressure or he struck the key too softly or too harshly. The art of bumping locks is very effective in the hands of an accomplished practitioner.
If Phoenix is unsuccessful in bumping locks, he can move on to a pick gun. A pick gun, as shown in Figure 6.3, consists of one or more vibrating, pick-shaped pieces of metal. A pick gun performs an “automated” rake. When using a pick gun, Phoenix will also need several picks and a tension wrench. He inserts the tension wrench and a pick, and then pulls the trigger. This method can be fairly successful.
If the pick gun does not work, Phoenix might have to get a set of picks and pick the lock.
Most deadbolts use cylinder locks. A deadbolt is more secure than a spring-driven latch because it’s much harder to push the bolt in from the side of the door. Figure 6.4 shows an example of cylinder locks.
There are two main elements to lock picking: picks and tension wrenches. Picks are long and thin, similar to a dentist tool. A tension wrench is similar to a screwdriver. In fact, a screwdriver is a good tension wrench.
One common method of picking is raking. Raking is much less exact than picking and is used by lock picking novices. When you rake a lock, you insert a pick with a wider tip all the way to the back of the plug. Then you pull or rake out quickly as it bounces all of the pins up on its way out, while applying pressure with the tension wrench—similar to the tension you apply when you bump a lock. This causes the pins to catch on the shear line. The shear line is where the inner cylinder ends and the outer cylinder begins. If Phoenix has to pick the lock, he will not rake the lock because doing so scars the pins and can leave traces of his entry. Figure 6.5 shows the interior of a lock.
After he gains access to the building, Phoenix needs to gain access to the records room. The records room is locked using a biometric lock.
Defeating biometrics could take two nights. If forced to create a false print, Phoenix might not have the necessary tools, such as computer and printer, with him. Figure 6.6 shows a typical fingerprint lock.
There are three methods of defeating a fingerprint scanner:
• Reactivate the previous print on the scanner itself.
• Use latent prints from a bottle or glass.
• Create a dummy finger.
The first method is the easiest to try. Some fingerprint scanners will reactivate the previous print just by breathing on them. That’s correct. Phoenix gets close to the scanner and breathes slow deep breaths on it. When he breathes on it, the sensors detect the heat and humidity in his breath, and see the print left from the previous person. This method is quick and takes no skill at all. If that fails, Phoenix will have to move onto method number two.
The second method can be very successful because many scanners on the market today scan in only two dimensions, not three dimensions. That means a picture of a print is almost as good as the real finger. To defeat a fingerprint scanner using method number two, Phoenix will need some supplies.
A $35 latent fingerprint kit is the easiest way to use this method. Another option is a home-based kit as seen on certain Internet blogs:
• Super Glue
• Small bottle cap
Phoenix also needs the following:
• Digital camera with download cable.
• Some wood glue.
• Plastic straw.
• A type of glue other than Super Glue. That is, a glue that is skin friendly.
• Acetate sheets.
• Laser printer or high quality ink jet printer.
• Laptop computer.
• Some sort of photo-editing software, such as Microsoft Paint.
He will need to obtain a cup, a glass, or some other nonporous item that a person authorized to enter the records room has left lying around. Phoenix will look in the kitchen, dumpster, or around the person’s desk. In a worst case scenario, he can try to lift the latent print off the door lock itself.
After obtaining an object, Phoenix will need to lift a latent print from it. If he has the fingerprint kit, doing so will be very quick. If he does not have the kit, he will need to do the following.
Squirt some Super Glue into the small bottle cap and place it over the latent print. When the vapors from the glue fumigate the print, it will turn a light shade of grayish white.
After either dusting the item or using the Super Glue trick, Phoenix will need to take a photograph of the latent print from very close up. Then he will download that picture into his computer. He will clean up the picture using photo-editing software and print it on the acetate sheet. With the straw, he rolls out wood glue over the print—this will act as the new print. After the glue dries, Phoenix cuts out the print, making sure the print he cuts is the same size as the original latent print he lifted off the glass. After cutting out the new print, he uses the skin-friendly glue to glue the new print onto his finger.
Unfortunately some fingerprint readers won’t fall for the overlaid fingerprint. If that is the case, Phoenix will have to use method three, which is much more time-consuming, and he probably will have to spread out his entry over two visits.
Following are the steps to take if he attempts method three, creating a dummy finger.
After Phoenix has lifted the latent print, photographed it, and printed it as described previously, he will need to get some polymer clay. Phoenix will transfer the printed image onto the clay. Using a small drill, he will cut or chisel out the ridges and valleys in the molding material. Fingerprint scanners need only a small amount of minutia. Ridge endings and bifurcations are known as minutiae. After Phoenix creates the three-dimensional fingertip, he can use it to enter the records room.
Now that he’s in, Phoenix can do what he does best. Compromising a PC and editing the medical records are easy tasks for him. To get access to the EMR, he will need to get a username and password to log into the system. He will have to crack the password.
Phoenix already downloaded and created a bootable Linux CD. He prefers the Auditor Boot CD ISO from Remote-Exploit.org.
This ISO is based on Knoppix, from www.knoppix.net, which is a Linux OS that will run solely in RAM and burn it to a CD. This CD contains many security-auditing tools. The ones that Phoenix is interested in are bkhive, samdump2, and John the Ripper. With these three tools he has a very good chance of cracking through the local administrator’s password. This CD also includes several compressed files that contain some common password files.
Phoenix now begins to boot into the Auditor Boot CD and grab password hashes.
Phoenix will insert the Auditor Boot CD in the CD-ROM drive of the target PC and power up the PC. He will watch the screen carefully because it will ask him a couple questions. It will ask him what resolution he wants to use; Phoenix will usually pick options 1, 2, or 3 because they are pretty safe options. Then it might ask what language Phoenix wants to use. It is important that he pick the English US language. If he misses this step, the CD may boot into the Swiss/German keyboard set and then the commands will not work.
After booting into the Auditor CD, Phoenix needs to open up a terminal window. He can do this by clicking on the little icon of a terminal in the lower-left corner. When the terminal window is open Phoenix types the following command, which will make the local hard drive accessible to the Linux OS:
Mount /dev/hda1
The following command will allow access into the working directory of the Auditor Boot CD:
cd /ramdisk/
Phoenix will be using Ncuomo’s Samdump2 first, and then bkhive, and finally John the Ripper.
The next command will give him the system syskey, which is the encrypted hashed password:
bkhive-linux /mnt/hda1/WINDOWS/system32/config/system syskey.txt
Now Phoenix will run it against the SAM file:
samdump2-linux /mnt/hda1/WINDOWS/system32/config/sam syskey.txt>hash.txt
In /opt/auditor/full/share/wordlists/ on the CD are several different word lists he can use, as shown in Figure 6.7.
Phoenix is going to use the English.txt file first to perform a dictionary attack. If that doesn’t work, he can use others. First he must extract the file:
gunzip -c /opt/auditor/full/share/wordlists/english/english.txt.gz>
/ramdisk/englishtxt.txt
Notice all the subdirectories of different languages and categories. If the password is a common word, John the Ripper will find it.
Now that Phoenix has the hash file and a word list unzipped, he can try to crack it with the following command:
John hash.txt -w:englishtxt.txt
Loaded 4 password hashes with no different salts (NT LM DES [32/32 BS]
D (Administrator:2)
PASSWOR (Administrator:1)
Guesses: 2 time 0:00:00:02 100% c/s 2971272 trying: ZZYZX - ZZZZZZZ
The password is entirely in uppercase letters—this is an anomaly of John the Ripper. Phoenix can’t assume that the password is in all uppercase. He will have to try both uppercase and lowercase letters. John the Ripper also told Phoenix that password belongs to the Administrator account, so Phoenix is very pleased with his progress.
John the Ripper can also perform a brute-force attack as well, but that could take some time:
John hash.txt -i:all
Phoenix sees that John took two attempts at the hash. On the first attempt, it found
passwor
On the second attempt, it found
d
The password to the administrator’s account is “password.” Now, he has the local administrator’s password.
If Phoenix were unsuccessful with John the Ripper, he needs to copy the hash file to some removable media, such as a jump drive, and submit it to a Rainbow Crack at http://www.rainbowcrack.net/.
Now Phoenix can boot into the Windows PC using the local administrator’s account and password. He can restart the PC without the Auditor Boot CD in the drive. When prompted to log in, he enters the username “administrator” and the password “password.”
Fortunately for Phoenix, he has knowledge of the existing EMR system from his social engineering. Phoenix will log in with Bill’s username, which is “198764,” and his password, which is “password.”
When he launches the EMR software with Bill’s account, he will have all the records at his fingertips. The deal Derek struck with the politician was to change the diagnosis that he has HIV or destroy the record altogether, and to keep quiet about it, for a price—whichever was the easier to master. And that’s just what Derek hired Phoenix to do.
Phoenix does a search for ICD-9 code 079.53, removes it from the record, and then removes any reference to HIV. He then goes to get the physical file and remove or erase any record of HIV findings. Phoenix then prints a copy of the record for Derek to show the politician.
Phoenix has now just entered the world of questionable legalities. Yes, Phoenix has committed a crime. He has committed several for that matter. Among other crimes, this alteration of medical records would be followed by legal action and a prison term, when found guilty. And, although these methods might work to breach security and systems, this author does not recommend these practices. This scenario has been created to exemplify the techniques and possibilities of social engineering and hacking into a business of any size.
This section discusses the various countermeasures you can deploy to protect against these chained exploits.
Your organization must have written security policies and procedures and senior management must buy into them. Without these documents in place, you really don’t have any security. Good security is tough to implement. Too much security and it becomes too inconvenient. Even the most honest people will start to find ways around the system. If it’s too weak you will be wasting your money. To implement good security, you need to find the right mix of convenience and security.
Let’s start from the beginning of the chapter and take it step by step.
Social engineering is quite possibly the toughest vulnerability a company has to guard against. As a security-conscious individual you need to be very concerned about social engineering attacks. As Kevin Mitnick once said, “You could spend a fortune purchasing technology and services to protect your network...and your network infrastructure could still remain vulnerable to old-fashioned manipulation.” To say you need to educate your staff is an understatement. Regulations such as the Gramm-Leach-Bliley act, HIPAA, and others recommend that you train your staff in security awareness annually.
Here are some topics that you may want to cover.
• Online attacks:
There are many types of online attacks and the downside is they are very popular, cheap, and easy to perform. Send out an e-mail and wait to see what happens. Here are some types of online attacks that you’ll want to train your personnel to watch out for.
a) Phishing attacks: An e-mail or malicious Web site to solicit personal or financial information is a phishing attack. Be suspicious of unsolicited e-mails asking you to divulge personal information. You might remember the famous e-mail, purportedly coming from the bank, asking recipients to go to a Web site and enter their Social Security number and personal information as a confirmation of their records, allowing them to gather personal information for their use.
b) E-mail attacks: Any e-mail that has an attachment should be considered suspect. If you receive an e-mail solicited or unsolicited with an attachment call the sender and verify.
c) Downloading of software: Software should be downloaded only by the IT staff, and then downloaded on an isolated machine, otherwise known as a sheep dip, and checked for viruses. IT should also verify the hash of the file using an MD5 hash generator such as Chaos MD5, which is a free download from http://www.elgorithms.com. After verification, the software can be installed on end-user PCs.
d) Spyware: Spyware is legal. In fact most manufacturers of software state in the End User License Agreement (EULA) that by installing this software you agree to the terms of the EULA, and inside the EULA it states that they will install additional software. You agree to this when you accept the license. You need to run antispyware software on each system.
e) Web sites: Illicit Web sites can contain questionable hyperlinks in them. Click on the link and it may install a piece of code on your PC. You will need to install content filtering software or a Web filtering appliance to combat this.
f) Instant Messaging: IM can be a big problem because it circumvents your firewalls and Web filtering. Don’t allow IM in the company or at the very least restrict IM for internal use only.
• Telephone:
The telephone is a standard with social engineers. People are braver if they don’t have to look you in the eye. Thus, social engineers can be more assertive over a phone line connection than they might otherwise be between themselves and their victims.
a) Help Desk: The Help Desk in an organization might receive calls asking for passwords, or for passwords to be reset, or other confidential information. Train your personnel not to give out that information. In the event the Help Desk individual needs to give out or retrieve personal or confidential information, make it policy that there must be a call back and another layer of verification.
b) Receptionist: Receptionists are generally the first individuals to receive a call and will be the first one to receive an attack. They need to be trained on how to spot a social engineering assault and the course of action to take to report such actions. If the receptionist susects a social engineering attack it must be immediately reported to her superiors.
• Dumpster diving:
It’s a dirty job, but a hacker will do it. Hoards of information can be gained from sifting through someone else’s trash.
a) External dumpsters: It’s best practice to post “No Trespassing” signs, lock up your dumpsters, and shred everything. When in doubt, shred it. Or, better yet, find a bonded commercial shredding service that will come to your business and shred documents, removable media, journals, books, and more.
b) Internal trash: It is important to make sure trash is not left sitting around. Remember, fingerprints can easily be lifted off cups and bottles in the trash can. Clean it up. You should also have a background check done on the cleaning staff. History proves that company information was leaked out by unscrupulous cleaning people more than once.
• Piggybacking:
Piggybacking is another form of social engineering. An intruder might walk in behind someone when they don’t have a key or code to get in. The only way to prevent this is train, train, and retrain your employees. Just like social engineering, piggybacking is preventable when people are properly trained. Some physical deterrents for piggybacking would be to employ guards or install a mantrap. This is a set of double doors that creates a sandwich effect. Only one person at a time may pass through. Years ago, only high-end jewelry stores or banks used this method. Today it is becoming common for increased security in various government offices and businesses.
People have been picking locks for centuries. People will continue to pick locks for centuries. You can deter it with compensating controls. Don’t deploy just a lock; deploy a high security lock (one that is bump resistant), security cameras, and an alarm system. If someone wants in and that person’s motivation is high enough, they will get in. It’s your job to make doing so as difficult as possible.
As long as there is technology, there will be someone out there to break through the code. To prevent someone from defeating your biometric implementation, you need to install multiple layers of defense and compensating controls: Two-factor or multifactor sign-on, “something you know” (password), “something you are” (biometric), “something you have” (key fob). Any two or all three of these will make it much more difficult to defeat your biometric system.
You can prevent your PC from being compromised. You must first start with physical security. Also you should not allow the use of removable media. In the previous attack the intruder used several programs to learn what the password was to any accounts on that particular machine. This could have been prevented if there was only one local account and the Administrator account. This was done by looking into the system and finding the hash of the password. After the hash was obtained, it was only a matter of time before the password was revealed. This can be prevented by enforcing strong passwords. Passwords need to be at least nine characters and contain uppercase, lowercase, and special characters. In a highly secure area, the passwords should be greater than 15 characters. This will protect the hash from the Rainbow Crack.
Here are some suggestions that will make it more difficult to crack into a PC:
• Disable the administrator’s account.
• Make sure that there are no active local accounts on the PC.
• Disable cached logins from the domain.
• Implement a good patch management strategy.
All major operating systems need to be patched because all operating systems are built by humans and humans make mistakes. Patch your systems to make sure that all known vulnerabilities are corrected. Visit http://cve.mitre.org/ to see what vulnerabilities your operating system has.
• Put in place good auditing procedures.
• Use least-privilege methodology to prevent too much access.
• Use token-based authentication such as RSA Secure-ID or SafeWord from Secure Computing.
Modifying EMR seems obvious:
• Use proper employee exit strategies.
• Have proper controls in place to change and/or lock out accounts.
• Enforce password confidentiality and two-factor sign on.
• Enforce good auditing procedures.
• Use least-privilege methodology to prevent too much access.
• Use RSA Secure-ID (as discussed earlier).
After Phoenix successfully obtains the data files necessary to change the prominent politician’s medical records, he continued with contract work from the government official, as additional medical and insurance records required alteration. Derek made a handsome sum of money as the go-to man for both parties, while he landed job at another local radiology firm. Regional Care Center is unaware of the breach to its systems and naive to the magnitude of this security invasion that just took place. The promising politician furthered his conservative career and sought aggressive medical treatments under the practice of a private physician outside the United States.
Medical record violation for purposes of insurance fraud, medical identity theft, and financial gain happen hourly. With the recent advancements of online medical records and pharmacy/medical scripts via e-mail, access only becomes another chain of exploits for the mind of a hacker.