VPN with IPSec and Manual Keys
IOS versions of the PIX prior to 5.0 used a connection method involving the Private Link Encryption Card to connect between two PIX Firewalls. This method is no longer supported; IPSec is used as the alternative. If your system is still using Version 4 or earlier of the Cisco PIX IOS, it is time to upgrade.
In this configuration, you will use IPSec to connect two networks over the Internet. You will also use manual keys for this example. In this example, your main corporate office uses an internal IP address of 10.1.1.0 with a 24-bit subnet mask, while your branch office uses10.1.2.0 with a 24-bit subnet mask. (As with any interface accessible from the Internet, the outside interface of the PIX must have a routable IP address.) Figure 4-11 shows a diagram of how these networks are connected.
Figure 4-11. VPN with IPSec
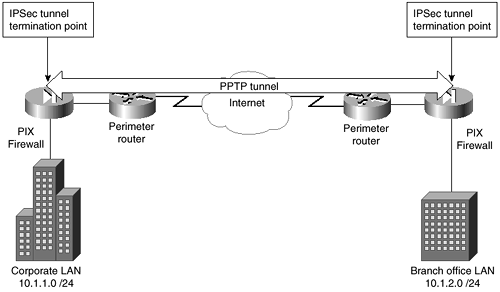
You need to configure both PIX Firewalls to enable a secure tunnel between them. The configurations that follow show only the items associated with setting up the IPSec tunnels. You will see both configurations and then a discussion of the ramifications of using the commands. Keep in mind that these are examples1 and, therefore, do not have routable IP addresses on the outside interfaces. In real life, the outside interfaces would need routable IP addresses; inside the corporate LANs, the IP addresses do not need to be routable. The corporate PIX configuration changes are as follows:
ip address outside 172.30.1.1 255.255.255.252
access-list 20 permit 10.1.2.0 255.255.255.0
crypto map mymap 10 ipsec-manual
crypto map mymap 10 set transform-set myset
crypto ipsec transform-set myset ah-md5-hmac esp-des
crypto map mymap 10 match address 20
crypto map mymap 10 set peer 172.30.1.2
crypto map mymap 10 set session-key inbound ah 400
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
crypto map mymap 10 set session-key outbound ah 300
bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
crypto map mymap 10 set session-key inbound esp 400 cipher
cccccccccccccccccccccccccccccccc
crypto map mymap 10 set session-key outbound esp 300 cipher
dddddddddddddddddddddddddddddddd
crypto map mymap interface outside
sysopt connection permit-ipsec
The branch office PIX configuration changes are as follows:
ip address outside 172.30.1.2 255.255.255.252
access-list 20 permit 10.1.1.0 255.255.255.0
crypto map mymap 10 ipsec-manual
crypto map mymap 10 set transform-set myset
crypto ipsec transform-set myset ah-md5-hmac esp-des
crypto map mymap 10 match address 20
crypto map mymap 10 set peer 172.30.1.1
crypto map mymap 10 set session-key inbound ah 300
bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
crypto map mymap 10 set session-key outbound ah 400
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
crypto map mymap 10 set session-key inbound esp 300 cipher
dddddddddddddddddddddddddddddddd
crypto map mymap 10 set session-key outbound esp 400 cipher
cccccccccccccccccccccccccccccccc
crypto map mymap interface outside
sysopt connection permit-ipsec
In this example, after assigning your outside IP addresses, you added an access list. Because you decided to use manual keys, this access list might contain only a single permit. If you used preshared keys, the access list could contain multiple permit statements. The access list is used to invoke your IPSec connection. When packets are sent to this address, your PIX establishes a connection with the peer, and all data traveling between the two is carried over your tunnel.
crypto map Commands
The crypto map command is used extensively with IPSec. This section examines the forms of this command in Table 4-6 before examining exactly what has to be configured in the examples. The crypto map command's first parameter is always the mapname. The mapname parameter is an arbitrary name assigned to distinguish one map from another. Table 4-6 assumes that crypto map mapname precedes the command. As with most commands, the no form of a command removes the configuration.
crypto ipsec Command
You have also seen the crypto ipsec command used within the configurations. There are two major forms of this command, the crypto ipsec transform-set and the crypto ipsec security-association lifetime forms. Both of these can be removed with the no form of the command. These commands are explained in Table 4-7.
| Crypto Command | Description |
|---|---|
| crypto ipsec set security-association lifetime seconds seconds | kilobytes kilobytes | If the keyword seconds is used, the seconds parameter specifies how many seconds before an SA will remain active without renegotiation. The default is 28,800 seconds, which is 8 hours. If the keyword kilobytes is used, the kilobytes parameter specifies how many kilobytes of data can pass between peers before a renegotiation must occur. The default value is 4,608,000 KB, which is approximately 4.5 GB. |
| crypto ipsec transform-set transform-set-name | This command defines the transform sets that can be used with the map entry. There can be up to a total of six transform-set-names used within a single line. The transform set attempts to establish an SA in the order that the sets are specified. |
Now that you have seen the syntax and uses of the crypto map and crypto ipsec commands, look again at the sample configurations.
You tell the PIX that your crypto map is named mymap with a map number of 10 and that IKE should not be used. This is done with the following line:
crypto map mymap 10 ipsec-manual
Next, you define the name of the transform with the following:
crypto map mymap 10 set transform-set myset
The transform set is defined with the following line:
crypto ipsec transform-set myset ah-md5-hmac esp-des
You previously created an access list 20 and permitted packets originating from the remote site's network. You then set the PIX to look at access list 20. If the packets are traveling to or from an address within this access list, they will be encrypted.
crypto map mymap 10 match address 20
Set the other end of the IPSec tunnel to terminate at 172.30.1.2, which is the outside interface of the branch office's PIX:
crypto map mymap 10 set peer 172.30.1.2
Set up the inbound and outbound session keys:
crypto map mymap 10 set session-key inbound ah 400
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
crypto map mymap 10 set session-key outbound ah 300
bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
crypto map mymap 10 set session-key inbound esp 400 cipher
cccccccccccccccccccccccccccccccc
crypto map mymap 10 set session-key outbound esp 300 cipher
dddddddddddddddddddddddddddddddd
Associate the crypto map with the outside interface.
crypto map mymap interface outside
Finally, permit IPSec packets into the network with the sysopt command.
sysopt connection permit-ipsec
The branch office PIX configuration is almost identical. The following section points out where it differs.
The branch office PIX has a different outside IP address.
ip address outside 172.30.1.2 255.255.255.252
The access list must reflect the main office's IP addresses.
access-list 20 permit 10.1.1.0 255.255.255.0
The peer is the outside IP address of the main office's PIX.
crypto map mymap 10 set peer 172.30.1.1
The session keys for the branch office are configured in the opposite order of what is configured on the main office's PIX. The inbound key on one side of a connection must equal the outbound key on the opposite side of the connection. The inbound AH session key on the Branch office is equal to the outbound AH session key on the main office's PIX. The inbound AH session key must match the main office's outbound AH session key in order for the connection to be established. The inbound ESP session key matches the main office's inbound ESP session key and the outbound ESP session key matches the main office's inbound ESP session key:
crypto map mymap 10 set session-key inbound ah 300
bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb
crypto map mymap 10 set session-key outbound ah 400
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
crypto map mymap 10 set session-key inbound esp 300 cipher
dddddddddddddddddddddddddddddddd
crypto map mymap 10 set session-key outbound esp 400 cipher
cccccccccccccccccccccccccccccccc
