VPN with Point-to-Point Tunneling Protocol (PPTP)
Starting with Version 5.1 of the PIX IOS, Cisco provides support for Microsoft PPTP VPN clients as an alternative to IPSec. Although PPTP is a less secure technology than IPSec, PPTP is easier to configure and maintain. PPTP also enjoys a great deal of support, especially from Microsoft clients. The PPTP is an OSI Layer 2 tunneling protocol that allows a remote client to communicate securely through the Internet. PPTP is described by RFC 2637. The PIX Firewall only supports inbound PPTP, and only a single interface can have PPTP enabled at any given time. PPTP through the PIX has been tested with Windows 95 using DUN1.3, Windows 98, Windows NT 4.0 with SP6, and Windows 2000.
The PIX Firewall supports Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), and Microsoft Challenge Handshake Authentication Protocol (MS-CHAP), using an external AAA server or the PIX local username and password database. Point-to-Point Protocol (PPP) with Combined Packet Protocol (CCP) negotiations with Microsoft Point-To-Point Encryption (MPPE) extensions using the RSA/RC4 algorithm and either 40- or 128-bit encryption is also supported. The compression features of MPPE are not currently supported.
To enable PPTP support, you first need to have the PIX configured to allow and deny packets in the normal fashion. The interfaces must be configured and the passwords set. After this is accomplished, you can add additional features. The sections regarding VPN in this chapter do not show all of the commands necessary to configure the PIX. Instead, this section concentrates on those commands that require configuration changes from previously shown examples or that are new commands.
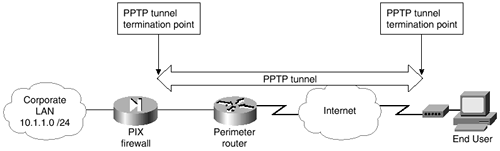
Take a moment to look at Figure 4-10. Notice that the VPN tunnel is terminated on the outside interface of the PIX. Although you could terminate the VPN on the perimeter router, there are a few reasons why terminating at the PIX is preferred. The first reason is that the PIX is optimized for security operations, including VPN termination. The PIX is able to handle a much larger number of VPN terminations than most routers. The second reason is that if you terminate on the perimeter router, then only the perimeter router ensures security on the packets after the VPN tunnel has been decrypted. Because the PIX is considered the primary defense, it makes logical sense to keep packets encrypted all the way to the PIX, even if the perimeter router is running the PIX Firewall IOS.
Figure 4-10. PIX PPTP VPN
The sample configuration used throughout this chapter requires changes to enable PPTP. These are shown in the following configuration. This section examines each of the new commands, after the following new configuration:
ip local pool thelocalpool 10.1.1.50-10.1.1.75 vpdn enable outside vpdn group 1 accept dialin pptp vpdn group 1 ppp authentication mschap vpdn group 1 client configuration address local thelocalpool vpdn group 1 client configuration dns 10.1.1.41 vpdn group 1 client configuration wins 10.1.1.9 vpdn group 1 client authentication local vpdn username joe password joespassword vpdn username mary password marryspassword sysopt connection permit-pptp
ip local pool Command
An IP local pool is used with VPNs to reserve a range of IP addresses that will be assigned to hosts using VPNs. The addresses in this range must not be in use by any other hosts and should not be used in any other commands. Use the show form of the command to display all of the IP addresses within a pool. The command, reserving IP addresses of 10.1.1.50 through 10.1.1.75 and using the name thelocalpool follows.
ip local pool thelocalpool 10.1.1.50-10.1.1.75
vpdn Command
The vpdn command takes many forms. The first line, the vpdn enable outside command, accomplishes two tasks. First, this enables virtual private dial-up network (VPDN) support on the PIX itself. Second, VPDN is enabled on the interface labeled outside by the nameif command. Multiple interfaces accepting PPTP traffic each require a separate vpdn enable interface command. Note that the PIX Firewall only accepts incoming PPTP traffic and cannot be used to initiate a PPTP tunnel.
The basic form of the command, vpdn group 1 accept dialin pptp, associates the VPDN group numbered 1 within other commands. Assuming that multiple PPTP tunnels are to be terminated on this interface, you might wish to set up some users on one tunnel and other users on a different tunnel. In this case, multiple tunnels allow you to accomplish such tasks as assigning different WINS or DNS severs to individuals. The accept dialin pptp portion of this command tells the PIX that it should accept PPTP connections requested by outside entities.
The vpdn group 1 ppp authentication mschap command shown next ensures that the password authentication protocol used within VPDN group 1 is mschap. The other options available on this command are pap and chap.
NOTE
You must also ensure that any associated Windows devices needing to use a PPTP tunnel into your network are also configured correctly. Unless you have set a Microsoft Windows client to require encrypted passwords, the client will first use a clear-text PAP password. This attempt will fail because of your PIX configuration that requires encryption. The client will then attempt to connect using the same password in an encrypted form, which will be successful. Even though the connection is ultimately successful, the password has been sent in clear text and might have been revealed to hackers. Therefore, ensure that encrypted passwords are required on all Microsoft Windows clients used with tunneled connections.
The vpdn group 1 client configuration address local thelocalpool command is used to assign the IP address used by the client while the client is connected through the PPTP connection. Because you created a group called thelocalpool and assigned the addresses of 10.1.1.50 through 10.1.1.75 to that pool, this command assigns the client to look to that pool for one of these available addresses. Limiting the total number of available IP addresses in the pool in turn limits the total number of PPTP connections that can be used simultaneously.
The client configuration form of the vpdn command is used to assign WINS and DNS servers for use by the PPTP client while the client is connected into your system. Both of these commands can take either one or two IP addresses. The order that these IP addresses are entered within the command reflects the order of their use by Windows clients.
The vpdn group 1 client authentication local command tells the PIX to look to the local user database to check passwords. If you are using a AAA server for client authentication, you would need to set up the PIX to recognize the AAA server and the need to authenticate PPTP users with lines similar to the following:
aaa-server TACACS+ (inside) host 10.1.1.41 thekey timeout 20 client authentication aaa TACACS+
The vpdn username joe password joespassword command enters Joe as a user within the local database and assigns joespassword to Joe. This is the password whose hash result will be sent over the connection through the MS-CHAP authentication process. You have also enabled Mary as a user with a unique password. Once the system is configured to allow one user, allowing other users involves adding a username and password to the PIX configuration.
sysopt Command
The previous commands shown in this example have set up the PPTP tunnel and users. What has not been done is to allow the users access through the firewall. The sysopt connection permit-pptp command allows for all authenticated PPTP clients to traverse the PIX interfaces. The sysopt command is used to change the default security behavior of the PIX Firewall in a number of different ways. There are many forms of this command, each acting slightly differently. Table 4-5 contains a list of the sysopt commands and a description of each of their functions. Each of these commands also has an associated no form of the command, which is used to reverse the behavior associated with the command.
