Cisco Security Solution
The Cisco Security Solution comprises five key elements. These elements enable a consistent approach to be administered that prevents unauthorized entry and protects valuable data and network resources from corruption and intrusion.
The key elements of the Cisco Security Solution are
Identity
Perimeter security
Secure connectivity
Security monitoring
Security management
For more information on the Cisco Security Solution, see www.cisco.com/warp/public/cc/so/neso/sqso/index.shtml.
Identity
The first element of the Cisco Security Solution is identity. This element is concerned with the unique and positive identification of network users, application services, and resources. You want to ensure that any entity accessing your network, whether it is a remote user or software agent, is authorized to do so. Standard technologies that enable identification include authentication protocols such as Remote Access Dial-In User Service (RADIUS), Terminal Access Controller Access Control System Plus (TACACS+), and Kerberos. New identification technologies include digital certificates, smart cards, and directory services.
Identity through authentication has to take place at the network boundary before the user or service has access to the secured network. This protects the inside network from unauthenticated users or services.
The Cisco Secure product that provides the security function at the identity level is Cisco Secure Access Control Server (ACS). This product provides authentication, authorization, and accounting (AAA) of all users trying to access the secured network.
Perimeter Security
Perimeter security provides the means to secure access to critical network applications, data, and services so that only authenticated and authorized users and information can pass through the network. As the name indicates, this level of security is applied at the perimeter of the network, which can be thought of as the point of entry that untrustworthy connections would take. This could be the point between the corporate network and the ISP network or the point between the corporate network and the Public Switched Telephone Network (PSTN). An example of a perimeter is displayed in Figure 3-1. It can also be a point between two organizations within the corporation (such as the marketing and engineering departments.)
Figure 3-1. Network Perimeter
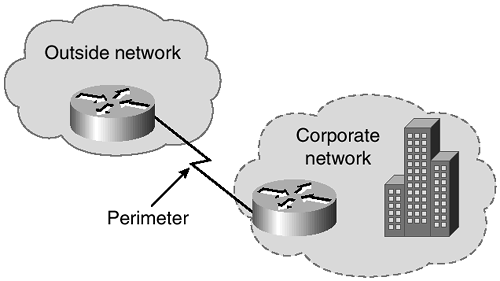
Security control is provided at the perimeter by access-limiting devices, commonly classified as firewalls These devices can be Cisco routers with traffic-limiting access lists and basic firewall features or dedicated firewall solutions such as a Cisco Secure PIX (Private Internet Exchange) Firewall.
Other tools that assist at the perimeter security level are virus scanners and content filters.
Security at the network perimeter is discussed in detail in Chapter 10, “Securing the Corporate Network.”
Secure Connectivity
When highly sensitive information is traversing your corporate network, it is very important to protect it from potential eavesdropping or sniffing of the network. You can achieve secure connectivity in three ways:
The traffic can be isolated from the rest of the network by employing a tunneling protocol, such as generic route encapsulation (GRE) or Layer 2 Tunneling Protocol (L2TP).
A simple way to increase data privacy is to implement Layer 2 switches to every client and server on the network. By design, a switch will only forward unicasts to the port on which the destination resides. Only broadcast traffic is flooded out on every port. Therefore, a network sniffer plugged into a switch would not automatically receive traffic that was not destined for the sniffer itself.
If a more secure method is required, a VPN technology, such as Internet Protocol Security (IPSec), can be used to encrypt the data against a 128-bit digital signature.
Secure connectivity is discussed in detail in Chapter 10.
Security Monitoring
Security management, like network management, is a dynamic, ever-changing process. Once you have designed and implemented a security solution, it has to be measured. One way of measuring the integrity of your solution is with a network scanner, which will scan every live IP address on your network and check the results against well-known vulnerabilities. A full report is then created, and actions can be taken to remedy any shortcomings in the design or implementation. It's important to make the changes and then scan the network again to ensure that the changes have been effective and their implementation hasn't caused any further security vulnerabilities. The security vulnerability database for all leading network scanners is upgradable on a periodic basis, ensuring that most new vulnerability that is discovered is added to the database. When you run a network scan, you can be sure that you are scanning for the latest vulnerabilities. Cisco Secure Scanner is a full, network-scanning utility that can be used for regular security monitoring purposes.
In addition to network scanning, the other aspect of security monitoring is intrusion detection. Intrusion detection systems monitor the network and respond to potential threats in real time. Shunning is a term widely used in intrusion detection and describes the capability of the intrusion detection system to actively reject all packets from a specific source if the system suspects sinister activity. As with the security scanner, an intrusion detection system operates by checking internal network traffic against a database of known vulnerabilities. Both the IP header and the payload are checked against these known threats.
Cisco Secure Intrusion Detection System (IDS) is an intrusion detection system that can be used for real-time network security.
Security Management
Today's networks are constantly growing in size; with this growth comes the need for centralized security management. There are various security management tools available, one of which is the Cisco Secure Policy Manager. This tool enables the administrator to centrally administer the security policy and distribute policy changes to a number of Cisco PIX and Cisco IOS Firewall devices by automated command-line configurations without detailed command-line interface (CLI) knowledge.
Cisco Secure Policy Manager is explained in great depth in Chapter 8, “Cisco Secure Policy Manager.”
