Cisco Secure ACS Configuration
This section covers the configuration of Cisco Secure ACS, including information on the client configuration and the server configuration. In this section, the client is a Cisco router running IOS 12 and supporting both RADIUS and TACACS+. The server is a Windows NT server that is authenticated against the Windows NT domain and also a remote ODBC data source. The section shows the configuration of RADIUS and TACACS+ for authentication and accounting both for EXEC and network connections.
This section starts by looking at the configuration options for the Cisco Secure ACS server. Nothing can be demonstrated with the ACS client until the ACS server is fully functional. Configuring an ACS client for authentication against a server that is not live can actually lock you out of the service. If you use this service to authenticate yourself for logging in to the router, you will not be able to log in. This section includes techniques to ensure that you can log in to the router at all times, even if the ACS server is offline for whatever reason.
As soon as you have successfully installed Cisco Secure ACS, you are ready to configure it.
Web-Based Configuration and the ACS Admin Site
Cisco Secure ACS is configured through a web-based application that is called ACS Admin. When you install Cisco Secure ACS, you also install a complete web server to which the ACS Admin site is bound. This web server only operates on port 2002, and it runs as a Windows NT service on the Windows NT version and as an application on the UNIX version. This service is called CSAdmin and can be stopped and started like any other Windows NT service.
An icon is created on the desktop and also on the Start menu for ACS Admin. Double-clicking this icon launches the ACS Admin web interface. If you are running the ACS Admin application from another machine, you have to enter the IP address of the machine followed by the port 2002. For example, if the ACS server was installed on 194.73.134.2, the URL would be http://194.73.134.2:2002. The colon indicates that the port number will follow. This connects to 194.73.134.2 on port 2002. Port 2002 is serviced by CSAdmin, therefore, the ACS Admin application is executed.
Figure 9-2 shows the ACS Admin configuration screen that you get when you log in.
Figure 9-2. Cisco Secure ACS Admin Application
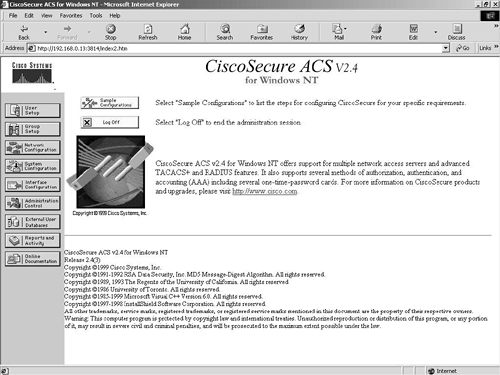
From here, you can see the main configuration options. These are represented as buttons down the left side of the screen.
These configuration options include:
User Setup
Group Setup
Network Configuration
System Configuration
Interface Configuration
Administration Control
External User Databases
Reports and Activity
Online Documentation
Sample configurations also can be seen from here. The sample configurations give you numerous scenarios and the required configuration for both the ACS Server and ACS client.
The following sections look at each of the configuration options listed.
User and Group Setup
The User and Group Setup configuration options can both be reached from the main ACS Admin page.
The User Setup configuration option displays all users who have ever authenticated against the ACS server. For example, Figure 9-3 shows the details for the user chriswhite.
Figure 9-3. User Setup Screen
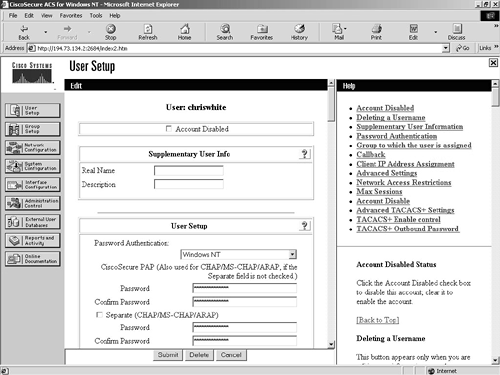
From this initial screen, you can see the user details for chriswhite. You can see that this user has been authenticated against the Windows NT database. This means that this user was first authenticated from an ACS client against the user's Windows NT username and password.
You can change a number of other settings here, such as the advanced settings and the advanced TACACS+ settings. The advanced TACACS+ settings can be seen in Figure 9-4.
Figure 9-4. User Setup Screen—Advanced TACACS+ Settings
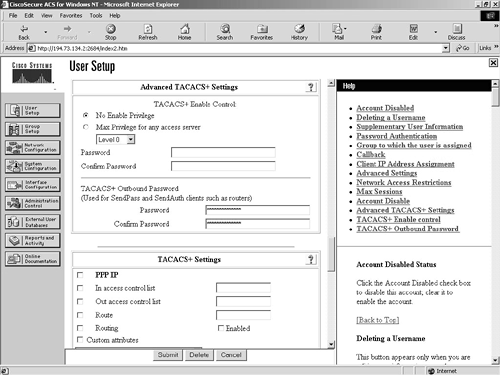
One other important point here is the group membership. Users can be members of groups and have the permissions and settings applied to the group instead of to each individual user. This eases the implementation of changes across groups of users. The groups can be either configured or mapped externally. As you can see in Figure 9-5, the user chriswhite is a member of groups that are mapped by an external authenticator. This means that the Windows NT groups that Chris is a member of are mapped to the Cisco Secure ACS groups. This is explained later in this chapter, in the section “External User Databases.”
Figure 9-5. User Setup Screen—Group Settings

You can also add a new user from the User Setup screen. When you add a new user, by default you add it to the Cisco Secure internal database.
The Group Setup screen is similar to the User Setup screen, except that it deals with groups instead of users. From the main screen, you can view users in a group, edit settings, or rename the group. Figure 9-6 shows you the users in the default group.
Figure 9-6. Group Setup Screen—Users in a Group
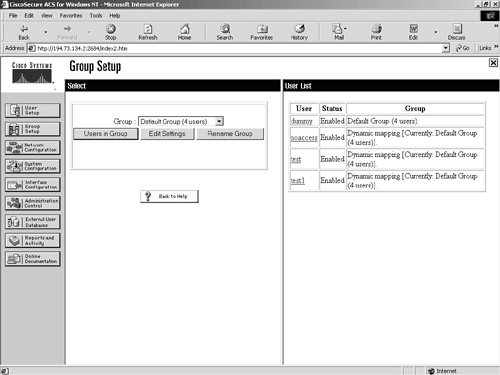
In the right pane of the window, you can see the four users who are members of the Default Group. Clicking the individual user will take you to the User Setup screen for that individual user.
Network Configuration
The Network Configuration screen is where you configure the network information for the ACS server.
From this screen, you enter the network access server information that will configure the ACS server to begin processing requests from that NAS. You can also add, remove, and edit AAA servers to the administrative console.
Figure 9-7 shows the standard screen displayed for Network Configuration.
Figure 9-7. Network Configuration Screen
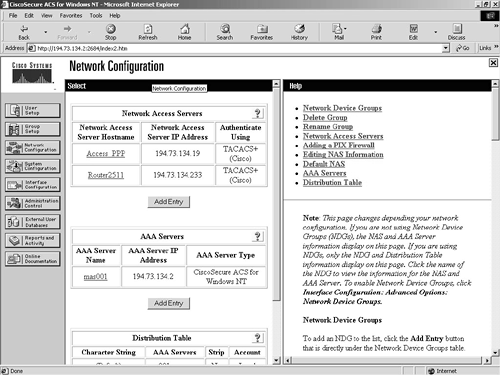
You can see from this screen that there are two network access servers and one AAA server. The two access servers are Access_PPP and Router2511. The AAA server is called mas001.
Clicking any of these items will take you to the individual configuration screen for that item.
To add a new NAS, click the Add Entry button below the Network Access Servers header. The following screen, shown in Figure 9-8, is the Add Access Server screen.
Figure 9-8. Network Configuration Screen—Adding a New NAS
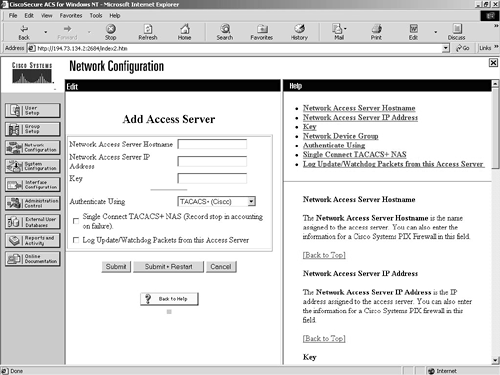
To add a new access server, you have to enter the network access server hostname, IP address, and key. The key is a shared security key that has to be the same on both the ACS server and the ACS client. You can then choose the authentication method. This obviously has to match the authentication type implemented on the ACS client or NAS. If you have configured TACACS+ on the NAS, select the default, TACACS+, on the ACS server. The other options are the different flavors of RADIUS. There is RADIUS (CISCO) for use with Cisco devices, RADIUS (IETF) for use with standards-based (RFC 2058 and RFC 2059) devices, RADIUS (ASCEND) for Ascend internetworking devices, and RADIUS (RedCreek) for Red Creek internetworking devices.
Clicking Submit configures the ACS server to start processing requests for AAA services for the newly configured network access server.
To add a new AAA server, click the Add Entry button below the AAA Servers header. The following screen, shown in Figure 9-9, is the Add AAA Server screen.
Figure 9-9. Network Configuration Screen—Adding a New AAA Server
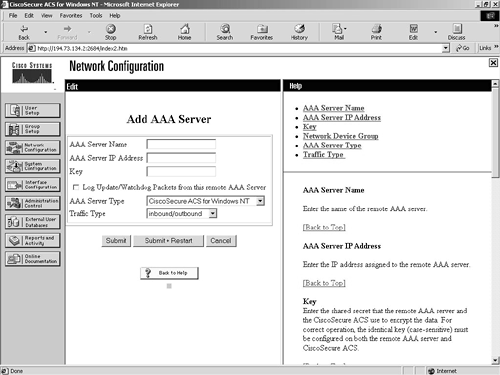
To add a new AAA server, you have to enter the AAA server name, IP address, and key. You then specify whether the server is a RADIUS, TACACS+, or Cisco Secure ACS server. Even though Cisco Secure ACS is both a RADIUS and TACACS+ server, it is important to select the Cisco Secure ACS option if the new AAA server is running the Cisco Secure ACS server software.
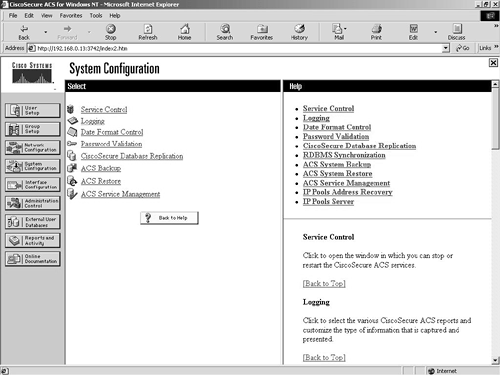
System Configuration
The next configuration option is the System Configuration. This option leads to seven other configuration options that are all related to the configuration of the Cisco Secure ACS system. These options are:
Service Control
Logging
Password Validation
Cisco Secure Database Replication
ACS Backup
ACS Restore
ACS Service Management
The System Configuration screen can be seen in Figure 9-10.
Figure 9-10. System Configuration Screen
Service Control
The Service Control option reports information and lets you stop and start the Windows NT services that relate to the Cisco Secure ACS server.
Logging
The Logging option lets you configure what events and targets you wish to log. These logs are stored on the ACS server in comma separated value (.CSV) format.
Password Validation
The Password Validation option lets you force a minimum and maximum password length for the internal Cisco Secure ACS database. You can also specify further password options, such as deciding that the password and username cannot be the same.
Cisco Secure Database Replication
The Cisco Secure Database Replication option allows you to configure and schedule replication of the Cisco Secure ACS database to other installed Cisco Secure ACS servers. These servers have to be added under the Network Configuration option covered previously.
ACS Backup
The ACS Backup option allows you to back up the Cisco Secure ACS database, including the user, group, and configuration settings. This backup can be to a local or remote shared drive.
ACS Restore
The ACS Restore option performs a restore of the Cisco Secure ACS database, including the user, group, and configuration settings.
ACS Service Management
The ACS Service Management option allows you to specify system-monitoring and event-logging parameters. The system-monitoring option uses a dummy user to test authentication for a predetermined period. The event-logging option sets all events to be sent to the built-in Windows NT event log. These can also be configured to be e-mailed through an SMTP server to any valid e-mail account.
Interface Configuration
The Interface Configuration screen is where you can configure the Cisco Secure HTML interface. There are four further options within the interface configuration:
User Data Configuration
TACACS+ (Cisco IOS)
RADIUS (Microsoft)
RADIUS (Cisco VPN 3000)
RADIUS (IETF)
Advanced Options
Figure 9-11 shows these options on the Interface Configuration screen.
Figure 9-11. Interface Configuration Screen
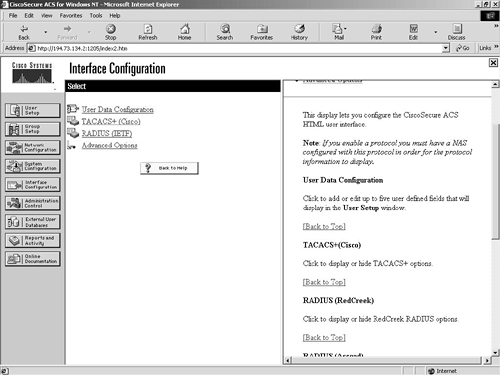
User Data Configuration
In the User Data Configuration screen, you can enter up to five user-defined fields that will be displayed in the User Setup configuration option.
TACACS+ (Cisco IOS)
The TACACS+ (Cisco) option allows you to change the TACACS+ services that you want to appear as configurable items in the User Setup and Group Setup screens.
RADIUS (Microsoft)
The RADIUS (Microsoft) option allows you to change the RADIUS services specific for Microsoft protocols that you want to appear as configurable items in the User Setup and Group Setup windows.
RADIUS (Cisco VPN 3000)
This option allows you to enable the RADIUS Vendor-Specific Attribute (VSA) number 26 for the Cisco VPN 3000 concentrator.
RADIUS (IETF)
The RADIUS (IETF) option allows you to change the RADIUS services that you want to appear as configurable items in the User Setup and Group Setup screens.
Advanced Options
The advanced options are a set of options that are only enabled as configurable if set here. These options are displayed in Figure 9-12.
Figure 9-12. Interface Configuration Advanced Options Screen
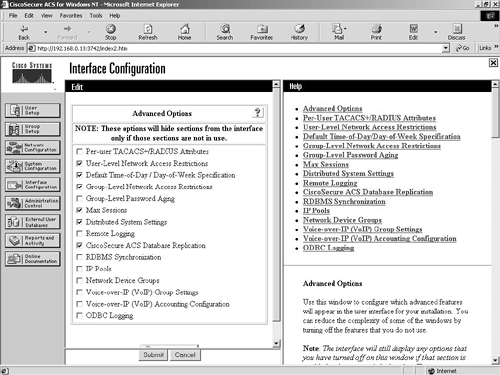
Administration Control
The Administration Control screen is where you can generate and configure users that are classified as administrators of the Cisco Secure ACS system. When you create these administrative users, you can also specify to which groups and functions they have access. This allows you to create tiered levels of administrators. There are three other options available from this configuration page:
Access Policy
Session Policy
Audit Policy
Figure 9-13 shows the main Administration Control screen.
Figure 9-13. Administration Control Screen
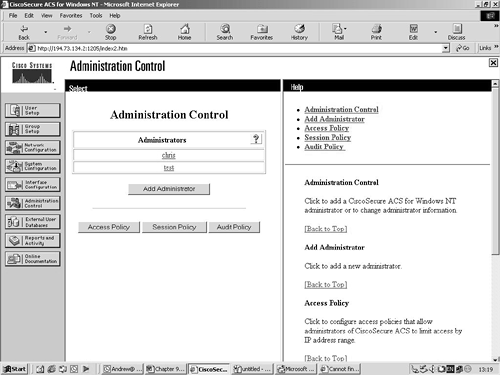
You can see from Figure 9-13 that this ACS server has two configured administrators, chris and test.
Access Policy
The Access Policy is used to restrict access to the administrative functions on the Cisco Secure ACS server. You can enter 10 ranges of IP addresses that can be either allowed or disallowed. The default setting is to let all IP addresses connect to the administrative console. This acts in a similar way to access lists on Cisco routers.
Session Policy
The Session Policy is concerned with the connected session. You can set the idle timeout for the session. This is set at 60 minutes by default, but it might be a good idea to lower this value to 10 minutes or even less. If somebody remains logged in and leaves the machine unattended, anybody with physical access to the machine can use the logged-in administrative rights on the ACS system. You can also set a login failure limit before the administrative account is locked out. This deters brute force and dictionary attacks. Another important setting here is the Allow automatic local login setting. By default, this is checked, which means that anybody with the sufficient privileges to log on locally to the server will be able to run the ACS Admin application without any further authentication. This is not very secure for obvious reasons, and it is a good idea to disable this and control access through administrative accounts for specific administrators.
Audit Policy
The Audit Policy sets the frequency of the audit log generation. The default setting is to create a new log for every day of the week. This can be changed to weekly, monthly, or when the log size reaches a specific value.
External User Databases
The External User Databases configuration screen is where you configure Cisco Secure ACS to authenticate users against external databases. You are presented with three options from the main page:
Unknown User Policy
Database Group Mappings
Database Configuration
This screen is shown in Figure 9-14.
Figure 9-14. External User Databases Screen
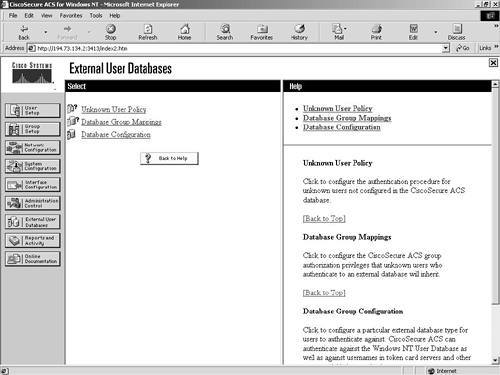
Unknown User Policy
The unknown user policy instructs the ACS server what to do if the user is not found in the built-in ACS database. This is a very important function if you wish to use a different authentication database than the built-in Cisco Secure ACS database.
The default setting is for the ACS to fail the authentication attempt. The only other setting is to use a configured external database. Figure 9-15 shows you the unknown user policy configuration screen.
Figure 9-15. External User Databases Screen—Unknown User Policy Configuration
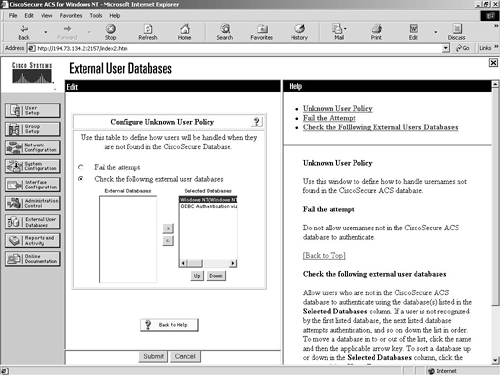
You can see in Figure 9-15 that this ACS server is set to try the internal ACS database, and failing that, it attempts authentication against two external databases, a Windows NT domain and an ODBC source. The Windows NT domain database will be checked first, followed by the configured ODBC data source. Both the Windows NT domain database and the ODBC data source have to be configured in the Database Configuration screen, which is covered in the section “Database Configuration.”
Database Group Mappings
The Database Group Mappings configuration screen allows you to map a preconfigured built-in group within the Cisco Secure ACS database to a group configured on the external database. For example, if you have a Windows NT group called Accounts, you can also have a Cisco Secure ACS group called Accounts and create a mapping between these two groups. Then all members of the Windows group Accounts will be made members of the ACS group Accounts. This group can be configured from the Group Setup configuration screen that was explained earlier in the section “User and Group Setup.”
Figure 9-16 shows some mappings between a Windows NT database and the Cisco Secure ACS database.
Figure 9-16. External User Databases Screen—Database Group Mappings
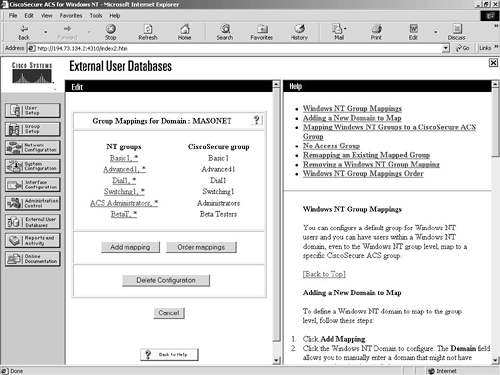
In Figure 9-16, you can clearly see the mappings in relation to the Windows NT database and the Cisco Secure ACS database.
Database Configuration
The External User Database Configuration screen is where you configure Cisco Secure ACS to use an external data source. Figure 9-17 shows the available options.
Figure 9-17. External User Databases Screen—Database Configuration
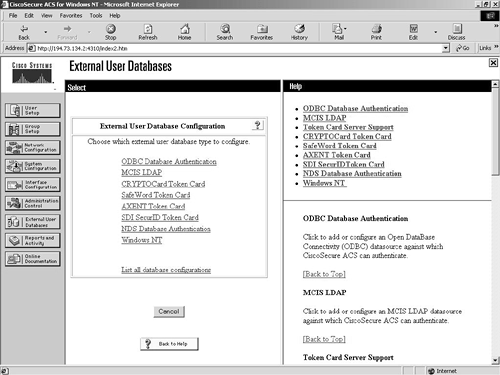
From the screen in Figure 9-17, you can see the external databases available from within Cisco Secure ACS. Each database has its own configuration settings associated with it.
Reports and Activity
The Reports and Activity configuration screen is where you can view the reports created by the Cisco Secure ACS server software. The prebuilt reports include:
TACACS+ Accounting
TACACS+ Administration
RADIUS Accounting
VoIP Accounting
Passed Authentications
Failed Attempts
Logged-In Users
Disabled Accounts
ACS Backup and Restore
RDBMS Synchronization
Database Replication
Administrative Audit
ACS Service Monitoring
TACACS+ Accounting
The TACACS+ Accounting report provides information about the TACACS+ accounting. This report is gathered from information sent from TACACS+ clients that are configured to use TACACS+ for accounting. You can see a sample TACACS+ accounting report in Figure 9-18.
Figure 9-18. Reports and Activity Screen—TACACS+ Accounting Report
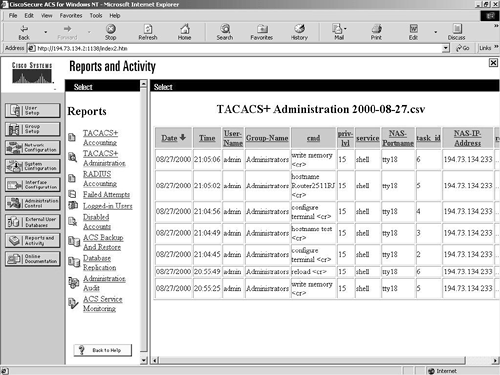
You can see in Figure 9-18 that commands have been executed at privilege level 15. The first command that was entered was write memory, and the last command entered was also write memory.
TACACS+ Administration
The TACACS+ Administration report contains details about the commands that were executed against the devices configured for TACACS+ accounting. This normally refers to Cisco routers that have been configured for TACACS+ accounting to track all commands entered against the router.
RADIUS Accounting
The RADIUS Accounting report provides information about the RADIUS accounting. This report is gathered from information sent from RADIUS clients that are configured to use RADIUS for accounting. This report is very similar to the TACACS+ accounting report.
VoIP Accounting
The VoIP Accounting report provides information about the VoIP RADIUS Accounting. This report is gathered from accounting information sent from RADIUS clients that are configured to use VoIP RADIUS for accounting.
Passed Authentications
This report lists successful authentications during the period covered by the report. By default, this report is disabled.
Failed Attempts
The Failed Attempts report is a list of failed authentication and authorization attempts. The reason for failure is also included, which can include expired accounts, disabled accounts, and exceeding the allowed authentication attempts count.
Logged-In Users
The Logged-In Users report displays a list of current users who are logged in to each network access server on the network. The data in the report contains the date, time, username, group, and IP address.
Disabled Accounts
The Disabled Accounts report is a list of accounts that have been disabled. These accounts might have been disabled manually or automatically by date expiration on the account. No .CSV file is created for this report, and it is only visible from the ACS Admin application.
ACS Backup and Restore
The ACS Backup and Restore report provides information about the ACS backup and restore operations. The date, time, and location of each operation are recorded, along with the administrator's username that started the process.
RDBMS Synchronization
This report contains the times the RDBMS database was synchronized and the cause of the synchronization: manual or scheduled.
Database Replication
The Database Replication report contains the date and time that the ACS database was successfully replicated to the backup server. The cause of the replication, either manual or automatic, is also recorded.
Administrative Audit
The Administrative Audit report contains a list of the Cisco Secure ACS administrators who accessed the ACS system on the specified date. All actions that the administrator carried out are logged, along with the date and time of the action. This report is similar to the TACACS+ accounting feature on Cisco internetworking devices, where all administrator duties are monitored and logged.
ACS Service Monitoring
The ACS Service Monitoring report provides details about the monitored Cisco Secure ACS-related Windows NT services. This information can also be viewed in the Windows NT event log.
These reports are all stored in .CSV files and are stored in the Program FilesCisco Secure ACS v2.3Logs directory on the ACS server. These raw .CSV files can be imported into leading database and spreadsheet applications for further analysis and recording over and above the reports generated by the Cisco Secure ACS server.
Online Documentation
As you would expect, the Online Documentation screen is a collection of the related documents for Cisco Secure ACS server. These documents include the full documents for every feature supported on Cisco Secure ACS, in addition to sample configurations and example commands that are required to be entered on the network access servers. Updated documentation can always be found at the Cisco Connection Online web site at www.cisco.com.
