The evolution of the telephone reveals one consistent evolving design principle: People do not want to be tied down to a particular location when using the phone. The first phones were attached to the wall, and people leaned down or stood on their toes to speak into the horn and listen to the response. Then the mouthpiece and listening device were combined into a single handset and connected to the phone by a chord; the phone still hung on the wall, but a person could rest the handset against his head and talk to the other person comfortably.
Finally, the phone was liberated from the wall. A cable attached to the phone itself allowed the caller to comfortably move the phone around the room. The caller was still restricted by the length of the phone cable, but at least she could lay on the couch while talking to a friend.
Then came wireless phones. Throw away the cable; the caller could be anywhere in the house, or even in the garden outside, and still comfortably speak with friends and family. This change was revolutionary in the independence it provided.
This principle of independence applies to wireless LANs. Notebook computers and personal digital assistants (PDAs) are commonplace in corporations; people take their computers with them to meetings, customer sites, airports, and hotels. Until recently, this mobility meant dragging a cable and being restricted to sitting somewhere near the wall where the cable plugged into the network.
With wireless networking, the computing user can easily access the network wherever he is as long as a wireless access point is nearby. Breaking the dependence on a cable and a wall jack is quite liberating.
Some benefits realized with the introduction of wireless networking include the following:
Computer users can access the corporate network and Internet anywhere on campus. This offers unprecedented convenience and flexibility.
Temporary networks are easier to set up when making moves, adds, and changes or when setting up war rooms or temporary workspaces.
It is easier to collaborate on the spot. Users can exchange files or handle requests for information when in meetings, for example.
Users can exchange data with servers directly rather than wait to download it from a wired connection. This flexibility is important in warehouse and manufacturing, for example.
Recently, with the addition of LEAP and other security and encryption-related protocols, wireless LANs are as secure as wired LANs. Before the development of these protocols, hackers could easily join a wireless network and access corporate or personal data.
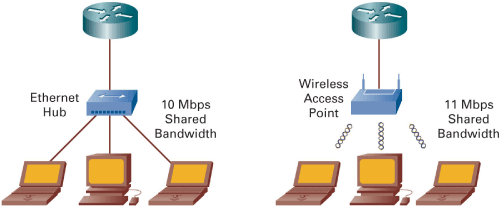
Wireless LANs are meant to complement existing wired networks. Wireless access points (similar to a traditional Ethernet hub) provide access to devices that have wireless network interface cards. The access points connect to an Ethernet switch and are typically configured on their own VLAN. Wireless bridges can provide wireless connectivity as well. This setup allows for longer distance connectivity between buildings, for example. The current wireless standards include 802.1a, 802.1b, and 802.1g.
In general, wireless LANs cannot achieve speeds as fast as wired networks. The size of the antenna and the transmission power setting of the interface card determine the distance, speed, and area between the transmitter and receiver. If you must achieve greater distance must be achieved, you can reduce the data rate. Tradeoffs occur between greater distance and faster transmission speeds.
As a user moves from one part of a building to another, the network must be able to switch which access point is associated with the user. This roaming happens automatically, invisibly to the user.
Security is a significant concern with wireless networking. Anyone with a wireless card can walk by a company building and possibly gain access to the corporate network. For example, a teleworker might be running a virtual private network (VPN) from her house to the corporate network and running wireless. Someone could easily access the corporate network with a wireless card from outside that person’s house.
Wireless security consists of authentication and privacy. Authentication ensures that only authorized persons can access the wireless LAN. Privacy provides a means to securely encrypt the traffic on the wireless LAN so that it cannot be intercepted. These means are effective in preventing unauthorized access to the wireless network.