Chapter 9. AMP Threat Grid: Malware Analysis and Threat Intelligence
This chapter covers the following topics:
![]() Cisco AMP Threat Grid cloud
Cisco AMP Threat Grid cloud
![]() On-premises Cisco AMP Threat Grid appliance
On-premises Cisco AMP Threat Grid appliance
This chapter introduces the cloud and on-premises Cisco AMP Threat Grid deployment options. These two types of deployments present different options, including the Cisco AMP, Email Security Appliance (ESA), and Web Security Appliance (WSA).
Threat Grid is a deep threat analysis solution that leverages many identification techniques, including sandboxing. It can be architected as a cloud or on-premises solution. It does deep analysis of file samples that are submitted to the AMP Threat Grid cloud or appliance. Cisco AMP Threat Grid analyzes files based on behavioral indicators and malware knowledge information and provides accurate and context-rich malware analytics. The analysis results can be used for updating file disposition in the cloud that is used by other cloud deployments.
Cisco AMP Threat Grid
Cisco AMP Threat Grid is a cloud and on-premises malware analysis solution that was first introduced in FirePOWER v6.0.
Note
Cisco customers can deploy an on-premises Cisco Threat Grid appliance if they do not wish to send any file information to the Cisco cloud or if they are worried about bandwidth utilization.
With either an on-premises or cloud installation, security engineers can use Cisco AMP Threat Grid to quickly correlate a single malware sample or hundreds of observed activities and characteristics against millions of samples in order to study malware behavior in a historical context. This helps them defend against targeted attacks and threats from advanced malware. Cisco AMP Threat Grid also can generate detailed reports, including important behavioral indicators and threat scores that allow security analysts to quickly prioritize and recover from advanced attacks.
Cisco AMP Threat Grid is not a single tool. It is a malware analysis and threat intelligence solution. It crowdsources malware from a closed community and analyzes all samples, using highly secure proprietary techniques including static and dynamic analysis. It performs automated analysis with adjustable runtimes while not exposing any indicators that malware could use to detect that it is being observed and analyzed. That way, Cisco AMP Threat Grid can still operate and analyze malware that changes behavior to avoid analysis in sandbox environments.
Many think that the Cisco AMP Threat Grid offering is just a sandboxing solution, but it is much more than just that. Sandboxing is a piece of the solution, and its sandbox functions are performed in a way that evades detection by malware. AMP Threat Grid uses an outside-in approach and has no presence in the virtual machine. The sandboxing’s dynamic analysis includes an external kernel monitor, dynamic disk analysis that illuminates any modifications to the physical disk (such as the master boot record [MBR]), monitoring of user interaction, video capture and playback, and monitoring of process information, artifacts, and network traffic. The following are some of the object types Cisco AMP Threat Grid supports:
![]() Executable files (.EXE) and libraries (.DLL)
Executable files (.EXE) and libraries (.DLL)
![]() Java archives (.JAR)
Java archives (.JAR)
![]() Portable document format (.PDF)
Portable document format (.PDF)
![]() Office documents (.RTF, .DOC, .DOCX, .XLS, .XLSX, .PPT, .PPTX)
Office documents (.RTF, .DOC, .DOCX, .XLS, .XLSX, .PPT, .PPTX)
![]() ZIP containers (.ZIP)
ZIP containers (.ZIP)
![]() Quarantine containers
Quarantine containers
![]() URLs
URLs
![]() HTML documents
HTML documents
![]() Flash
Flash
Among its outputs, Cisco AMP Threat Grid provides video playback, the Glovebox feature for malware interaction and troubleshooting, a process graph for visual representation of process lineage, and a threat score with behavior indicators of malware. The Glovebox feature helps analysts dissect and interact with the malware in real time by recording all activity for future playback and reporting. It correlates sample malware data elements against billions of sample artifacts historically collected and analyzed in order to match well-known malicious behaviors. The threat score provided for analyzed malware is based on severity and confidence. In addition, the more than 450 behavioral indicators, sourced from around the globe, can show an analyst if a piece of malware is malicious, suspicious, or benign—and why—which eliminates guesswork and helps an analyst make better decisions more quickly.
Cisco AMP Threat Grid is integrated with Cisco security technologies that span from the network edge to the endpoint, including Cisco AMP for Networks, Cisco ASA with FirePOWER Services, Cisco Firepower Threat Defense, Cisco Email Security Appliance, Cisco Web Security Appliance, and Cisco AMP for Endpoints. In combination, these tools give organizations more visibility than ever before. Information across many platforms can be correlated and synthesized so organizations can make faster, better decisions to more quickly eliminate threats and reduce the harm caused by malware.
Cisco AMP Threat Grid also provides highly accurate, easy-to-integrate security content feeds that help organizations generate context-rich threat intelligence that is both actionable and specific. The feeds are available in a number of standardized formats:
![]() JavaScript Object Notation (JSON)
JavaScript Object Notation (JSON)
![]() Cyber Observable Expression (CybOX)
Cyber Observable Expression (CybOX)
![]() Structured Threat Information Expression (STIX)
Structured Threat Information Expression (STIX)
![]() Comma-separated values (CSV)
Comma-separated values (CSV)
![]() Snort rules
Snort rules
Customized feed formats are also available for particular security products. Using the powerful application programming interface (API), you can import threat information into your security technologies, including security information and event management (SIEM) solutions, graphical visualization tools, and more to automate detection and response to even the most sophisticated threats. Cisco AMP Threat Grid’s threat intelligence allows administrators to look into markets and industries of interest. An analyst can understand the relevancy of the executable sample as it pertains to the environment and look at specific threat information for specific types of data and take proactive, preventive action.
Among the security personnel who can benefit from Cisco AMP Threat Grid are incident response and security operation team members and information security executives. Incident response teams use Cisco AMP Threat Grid to analyze malware submissions; search for malicious files, registry keys, and URLs; and run malicious code in Glovebox. Security operation teams generate threat scores, prioritize malware cleanup and remediation, and submit suspicious code for analysis. Threat Grid empowers a security team to act faster on malware, offers a more complete security solution by integrating with existing technologies, and accelerates detection of advanced attacks.
The rest of this chapter presents specifics of the cloud and appliance deployment options for Cisco AMP Threat Grid and briefly presents details on how to configure them.
Cisco AMP Threat Grid Cloud Solution
The Cisco AMP cloud includes multiple analytics engines constantly correlating data. Threat Grid is one of them. The analysis results generated by AMP engines are used to update the AMP signatures. Other machine-learning engines are used to refine signatures and reevaluate detections of indicators that have already been caught. AMP does not serve as a static signature repository. Decision making and intelligent operations take place in real time, evolving constantly based on the data that is received.
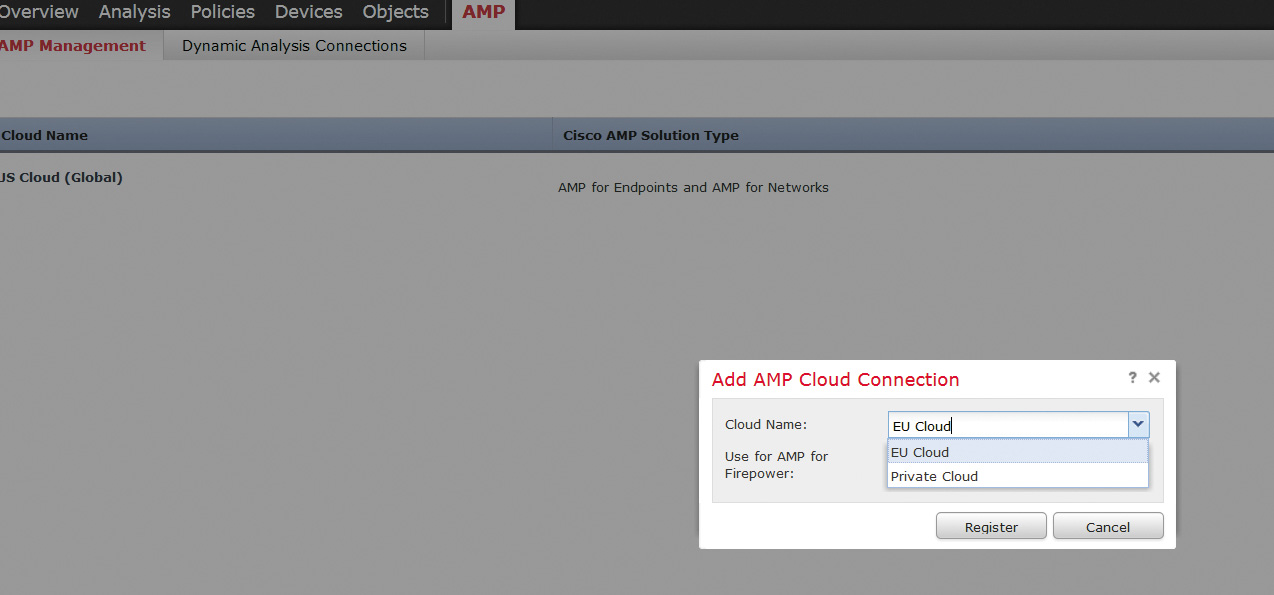
As mentioned previously, AMP Threat Grid’s cloud solution allows users to submit malware samples to the cloud for analysis and receive detailed reports that identify important malware behavioral indicators and assign threat scores. Security teams can then rapidly prioritize and recover from advanced attacks. Figure 9-1 shows the Firepower Management Center (FMC) with the AMP cloud located in U.S. and EU data centers. An AMP private cloud option is also available for organizations that do not want malware information shared in the cloud.
Cisco AMP Threat Grid can be accessed via a portal page. Files can be submitted for analysis using the browser. All the results can be easily retrieved from the web page. Malware samples can also be compared with other samples and searched for. In addition, with Cisco AMP Threat Grid cloud, you can define the malware runtime from 5 to 30 minutes.
Threat Grid exposes an API that integrates with existing security solutions and can create custom threat intelligence feeds. It can automatically receive submissions from other products and pull the results in the environment. Cisco AMP Threat Grid’s analysis, threat intelligence correlation, and feeds retrieval can be automated and integrated with existing security solutions using the API. Security tools can also access and integrate with it by using the Threat Grid API.
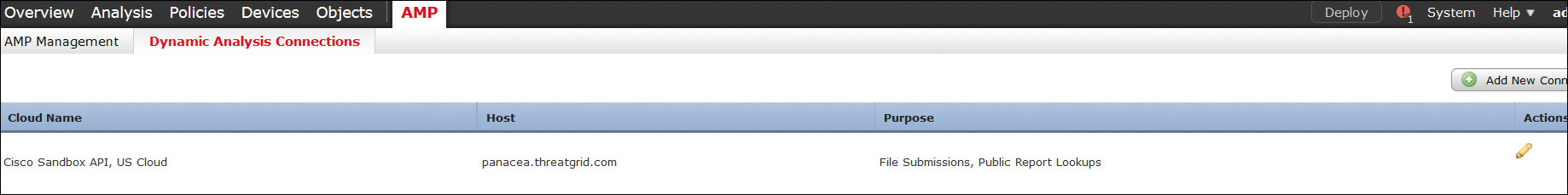
Administrators can navigate to AMP > Dynamic Analysis Connections in FMC (see Figure 9-2) to configure cloud HTTPS connections that the Cisco ASA with FirePOWER Services or Cisco Firepower Threat Defense will be using to get attribute and dynamic analysis updates to verify whether malware samples are malicious. Cisco ESA and WSA also integrate with Cisco Threat Grid cloud, leveraging a similar outbound HTTPS connection configured in the File Reputation Filtering and File Analysis page.
Cisco AMP Threat Grid On-Premises Appliance
Even though the Cisco AMP Threat Grid cloud-based solution can serve many organizations well, others might require no outbound connections to the cloud transferring information externally. Organizations with such compliance and policy restrictions can submit malware samples to the AMP Threat Grid on-premises appliance for local analysis and ensure policy enforcement and compliance. The appliance also has the capability to manually update its knowledge base while complying with corporate or regulatory policies to keep all information within logical boundaries and not transfer it externally.
The Cisco AMP Threat Grid appliances (TG5000 and TG5500) are hosted in a Cisco UCS C220 hardware server. They can analyze 1500 and 5000 samples per day, respectively.
Similarly to the cloud, with the Cisco AMP Threat Grid appliance, malware samples are analyzed using static and dynamic analysis techniques, and the results are correlated against millions of analyzed malware artifacts; however, in the case of the on-premises appliance, information is not sent out of an organization’s logical boundaries. Security teams can quickly correlate a single malware sample’s activity and characteristics against other samples to analyze its behaviors in historical and global contexts to defend against targeted attacks or general threats from advanced malware.
As shown in Figure 9-2, in FMC administrators can navigate to AMP > Dynamic Analysis Connections to create new connections to the Cisco AMP Threat Grid appliance rather than using the public cloud to analyze files traversing an ASA with FirePOWER Services or Cisco Firepower Threat Defense (FTD). These connections allow the firewall to connect the Threat Grid appliance to get files analyzed and find their posture. The Cisco ESA and Cisco WSA offer similar integration with Threat Grid. If the system is configured to connect to an on-premises appliance, it can use the default public cloud connection for public report retrieval. If the appliance cannot generate a dynamic analysis report about a file, it queries the Cisco AMP cloud. In an on-premises appliance deployment, public cloud reports returned to the system by the cloud are scrubbed and returned with limited data.
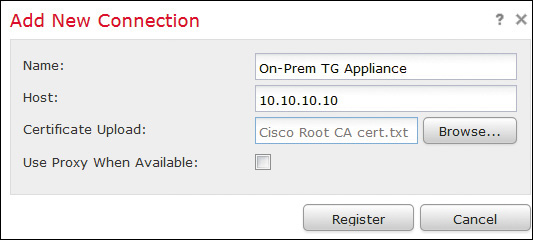
The initial configuration of a device (Cisco ASA with FirePOWER Services, Cisco FTD, Cisco ESA, or Cisco WSA) consists of configuring Secure Sockets Layer (SSL) certificates so the appliance can communicate, registering the device in the appliance, creating a user, and configuring the device to connect to the appliance, as demonstrated in Figure 9-3. In the Cisco ESA and Cisco WSA, Cisco AMP Threat Grid dynamic file analysis is enabled in the File Reputation Filtering and File Analysis page.
The appliance itself has an administrator interface, a clean interface that connects to the trusted inside network, and a dirty interface for the untrusted network. Access to the appliance is from the administrator interface, using the graphical user interface in a browser. The web interface allows for file submission for analysis, report generation about malware activities and network traffic, result retrieval, sample searches, and comparison.
To analyze malware, an administrator has the opportunity to run and interact with it in Glovebox for 5 to 30 minutes to observe its behaviors. Malware analysis, threat intelligence correlation, and feeds retrieval are other features the web interface offers. These can also be automated and integrated with existing security solutions using the API. A powerful representational state transfer (REST) API allows organizations to integrate the appliance with existing security infrastructure, such as gateways, proxies, and SIEM platforms. The API can also be used to automatically consume submissions from third-party endpoint agents, deep-packet-inspection platforms, and investigation tools. Numerous partner solution integrations showcase that functionality. Finally, the user interface offers customizable workflows that are designed for security operations center (SOC) malware analysts and forensic investigators to perform their day-to-day operations.
Default Users
The default Cisco AMP Threat Grid portal administrator username is admin, and the password is changeme.
The default Cisco AMP Threat Grid OpAdmin administrator’s password is “threatgrid,” which is the same as the Threat Grid portal user password, and it is maintained in the OpAdmin interface.
As previously mentioned, the Cisco AMP Threat Grid appliance is a Cisco UCS server. It also comes with the Cisco Integrated Management Controller (CIMC) for low-level server administration. The default username for the CIMC is admin, and the default password is password.
Tip
It is highly recommended that you change the device password and that you use strong passwords to increase the security posture of the device and to reduce its attack surface.
Once the user accounts are set up, the administrators or other users can log in and begin submitting malware samples for analysis.
Network Segment Configuration
As mentioned previously, the Cisco AMP Threat Grid appliance has three required networks:
![]() Administrative (admin) network: This network must be configured in order to configure the appliance.
Administrative (admin) network: This network must be configured in order to configure the appliance.
![]() Clean network: This network is used for inbound trusted traffic (requests) to the appliance, including traffic from other integrated systems (for example, Cisco ESA, Cisco WSA).
Clean network: This network is used for inbound trusted traffic (requests) to the appliance, including traffic from other integrated systems (for example, Cisco ESA, Cisco WSA).
![]() Dirty network: This network is used for outbound traffic, including malware traffic.
Dirty network: This network is used for outbound traffic, including malware traffic.
Tip
A best practice is to configure a dedicated external IP address for the appliance that is different from your corporate IP address in order to protect your internal network.
Summary
This chapter provides an overview of the Cisco AMP Threat Grid solution, which offers an efficient and granular file analysis and context-rich and accurate malware analytics. This chapter also explains how Cisco AMP Threat Grid can be used in conjunction with Cisco AMP to offer a complete malware protection and analysis solution that operates throughout the attack continuum—before, during, and after a malware compromise—and helps organizations understand what malware is attempting to do, the threats it poses, and how to defend against it. The cloud-based AMP Threat Grid solution offers flexibility of deployment and off-the-shelf analytics from the Cisco AMP cloud. On-premises AMP Threat Grid deployments, on the other hand, serve organizations that want to use Cisco AMP Threat Grid’s granular analysis without transferring information to the cloud.