Chapter 7
Practice Exam 2
- Which of the following are technologies typically used for Personal Area Networks (PANs)? (Choose all that apply.)
- RFID
- Z-Wave
- ISDN
- NFC
- Bluetooth
- Review the following figure. How many collision domains and broadcast domains are there in the network diagram?
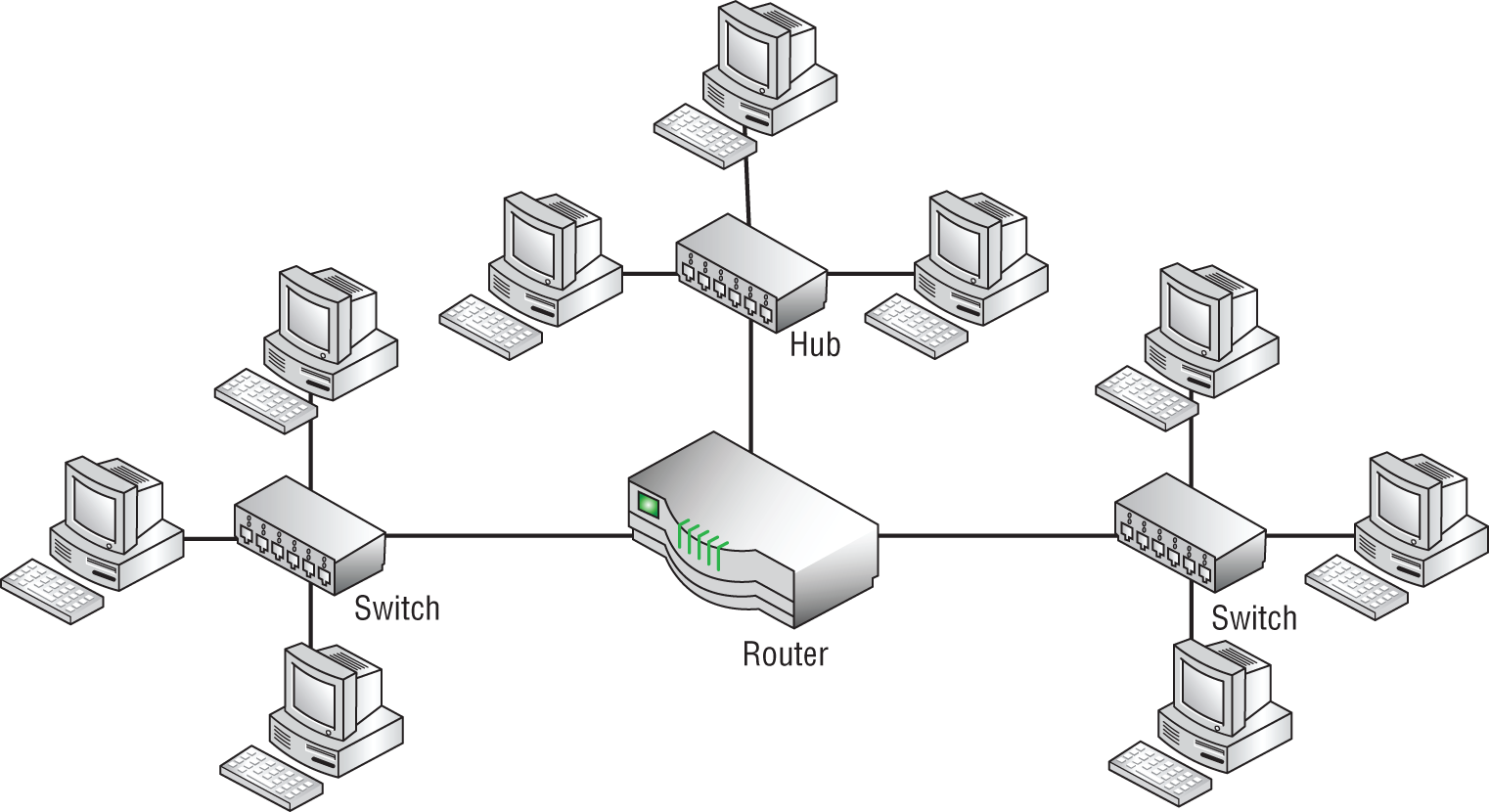
- There are three collision domains and one broadcast domain.
- There is one collision domain and one broadcast domain.
- There are three collision domains and three broadcast domains.
- There are seven collision domains and three broadcast domains.
- There are nine collision domains and three broadcast domains.
- Which of the following types of network devices can provide authentication services for multiple remote access servers using the device's own account database?
- NAS
- IDS
- NGFW
- RADIUS
- You are designing the network for your company's new branch office, and you need a device on which administrators can create Virtual Local Area Networks (VLANs) and that will forward traffic between them. Which of the following types of devices can do this?
- Virtual router
- Multilayer switch
- Broadband router
- Load balancer
- You are setting up a new network for which you have been given the IPv4 network address 10.61.0.0/19. You want to calculate the number of hosts you can create on each subnet. How many bits are allocated to the host identifier in an IPv4 address on this network?
- 5
- 8
- 13
- 21
- The protocols that are responsible for the delivery of data packets to their final destinations on an internetwork operate at which layer of the Open Systems Interconnection (OSI) reference model?
- Application
- Session
- Transport
- Network
- Data link
- Originally, Storage Area Networks (SANs) were dedicated solely to storage-based traffic. A Local Area Network (LAN) was also required for other types of traffic. Today, however, it is possible for SAN and LAN traffic to coexist on a single network medium. Which of the following SAN protocols are capable of sharing a network medium with standard LAN traffic? (Choose all that apply.)
- InfiniBand
- Fibre Channel
- iSCSI
- FCoE
- Which of the following application layer protocols do not include a program that enables a user to log on to a remote network device and execute commands using a character-based interface? (Choose all that apply.)
- Telnet
- Simple Mail Transfer Protocol (SMTP)
- File Transfer Protocol (FTP)
- Domain Name System (DNS)
- Many network diagrams use Cisco symbols to illustrate the locations of and relationships between network components. Cisco symbols are standardized pictographs that illustrate the basic function of a network component. In a network diagram that uses Cisco symbols, what component does the symbol in the figure represent?
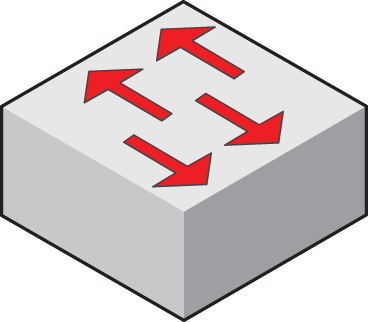
- A hub
- A switch
- A router
- A gateway
- You are planning an automated operating system deployment for 100 new Windows workstations your company has received. You intend to configure the workstations to boot using Preboot Execution Environment (PXE), during which time the system will obtain an IP address from a Dynamic Host Configuration Protocol (DHCP) server and then download a boot image file from a Trivial File Transfer Protocol (TFTP) server. Which of the following well-known ports must you open on the firewall separating the workstations from the servers? (Choose all that apply.)
- 64
- 65
- 66
- 67
- 68
- 69
- Your department is experiencing frequent delays as users wait for images to render using their outdated graphics software package. As a result, you submitted a change request for a new software product at the monthly meeting of the company's change management team. Now that the change request has been approved, it is time to implement the change. Which of the following administrative tasks will most likely be the change management team's responsibility during the implementation process? (Choose all that apply.)
- Notifying users
- Documenting all modifications made
- Authorizing downtime
- Designating a maintenance window
- You are installing a new server that is equipped with two power supplies. The server's firmware enables you to set the mode in which the power supplies will be used. In which of the following modes must the dual power supplies be running for the system to be fault tolerant?
- Individual mode
- Combined mode
- Redundant mode
- Hot backup mode
- The Domain Name System (DNS) defines a hierarchical name space, locations in which are reflected in fully qualified domain names (FQDNs). Which of the words in the FQDN
www.paris.mydomain.orgrepresents the bottommost layer in the DNS namespace's domain hierarchy?wwwparismydomainorg
- The term datagram is typically used by protocols offering connectionless delivery service. Which of the following protocols use(s) the term datagram to describe the data transfer unit it creates? (Choose all that apply.)
- TCP
- IP
- UDP
- Ethernet
- After using a tape backup solution for years, you have recently started backing up your server to an external hard disk drive. Your backup schedule calls for weekly full backups and daily incremental backups. In the past, performing a restore required multiple jobs, but now only a single job is needed. Why does performing incremental backups to a hard drive, rather than a tape drive, make it possible to restore a server with a single job, rather than multiple jobs?
- Because hard drives use a different block size than tape drives
- Because hard drives can transfer data faster than tape drives
- Because hard drives hold more data than tape drives
- Because hard drives are random access devices and tape drives are not
- You have just received notification of a new software release for an application you are running on your servers. The release is intended to address a newly discovered security vulnerability. Which of the following is the correct term for a software release containing a fix designed to address one specific issue?
- An upgrade
- A patch
- A service pack
- An update
- Twisted-pair cables consist of multiple pairs of wires within a sheath, with each pair of wires twisted together separately. Which of the following statements best explains the reason for the twists in twisted-pair cabling? (Choose all that apply.)
- The twists help to prevent crosstalk in adjacent wire pairs.
- The twists make it easier for installers to attach connectors to the cable ends.
- The twists extend the cable's bend radius allowance, making it easier to install.
- The twists limit the effects of electromagnetic interference (EMI) on the signals carried over the cable.
- The twists help to prevent data collisions from occurring.
- The figure shown here lists the processes currently running on a Linux workstation. Which of the following performance monitoring tools, provided in Linux and Unix operating systems, enables you to display information about processes that are currently running on a system?
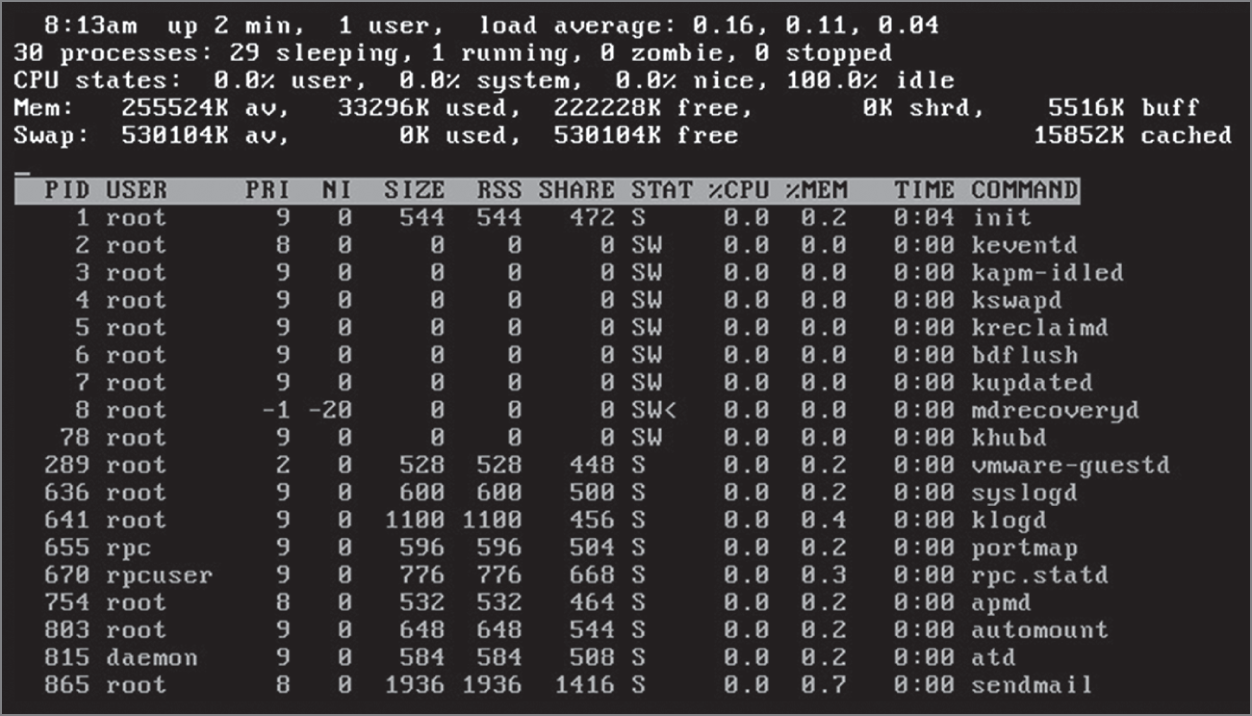
netstatdigperfmontop
- You are contracting with a provider to obtain email services for the clients on your network, using their existing email servers in the public cloud. You do not need anything from the provider other than email. Which of the following service models will you be using?
- PaaS
- SaaS
- IaaS
- All of the above
- Security Information and Event Management (SIEM) is a combination tool that uses information gathered from logs and network devices to provide a real-time analysis of the network's security condition. Which of the following SIEM processes performs searches for specific criteria, during specific time frames, in logs located on different computers?
- Correlation
- Retention
- Data aggregation
- Forensic analysis
- When you start Dynamic Host Configuration Protocol (DHCP) client, it transmits DHCPDISCOVER messages to locate and initiate contact with DHCP servers. Which of the following types of transmissions does the client use for this purpose?
- Broadcast
- Multicast
- Anycast
- Unicast
- Virtual Private Networks (VPNs) use a technique called tunneling to secure traffic as it passes over a public network, such as the Internet. In some cases, the traffic within the VPN tunnel is also encrypted. Which of the following VPN protocols does not provide encryption within the tunnel?
- L2TP
- IPsec
- PPTP
- SSL
- You are installing a wireless network in a site that has a great many 2.4 GHz wireless telephones. Which of the following wireless networking technologies can you use, which will never experience interference from the telephones? (Choose all that apply.)
- IEEE 802.11b
- IEEE 802.11g
- IEEE 802.11ac
- IEEE 802.11a
- IEEE 802.11n
- Which of the following is another term for a switch?
- Multicast hub
- Multiport repeater
- Multiport bridge
- Multihomed router
- You are working at a client site with a managed router that includes a console port for administrative access, which you can use to connect a laptop and run a terminal program to access the device's interface. Which of the following is the best term for this type of access to the device?
- Client-to-site
- In-band
- BYOD
- Out-of-band
- After some incidents of security breaches, you have been asked to draft a revised password policy for the company's users. Which of the following are typical elements of a corporate password policy? (Choose all that apply.)
- Frequent password changes
- Use of special characters
- Minimum password length
- Unique passwords
- You have a laptop that requires you to hold your finger on a scanner pad before you can use it. A device equipped with a fingerprint scanner that authenticates the user is using which of the following types of technology?
- Tamper detection
- Biometrics
- Hand geometry
- Pattern recognition
- You have been asked to locate the computers on a network which the previous consultant has configured with incorrect IPv6 addresses. Which of the following are not correctly formatted IPv6 addresses? (Choose all that apply.)
- fe00::c955:c944:acdd:3fcb
- fe00::b491:cf79:p493:23ff
- 2001:0:44ef68:23eb:99fe:72bec6:ea5f
- 2001:0:49e6:39ff:8cf5:6812:ef56
- During a security evaluation by an outside contractor, you are asked whether your company uses a fail open or fail closed policy for the datacenter. You do not know what the contractor means. Which of the following physical security mechanisms can either fail closed or fail open?
- Door locks
- Motion detectors
- Honeypots
- Video cameras
- Your company is concerned about the possibility of insider threats. Which of the following security measures can you use to monitor the specific activities of authorized individuals within sensitive areas?
- Identification badges
- Motion detection
- Video surveillance
- Key fobs
- Ralph is troubleshooting a Windows server, and while doing so, he runs the following command:
ping 127.0.0.1. The command completes successfully. What has Ralph proven by doing this?- That the computer's network adapter is functioning properly
- That the computer's IP address is correct for the network
- That the computer's TCP/IP networking stack is loaded and functioning
- Nothing
- Which of the following are not examples of multifactor authentication? (Choose all that apply.)
- A system that requires a smart card and a PIN for authentication
- A system that uses an external RADIUS server for authentication
- A system that requires two passwords for authentication
- A system that requires a password and a retinal scan for authentication
- A user calls Ed at the help desk to report that he cannot access the Internet. He can access systems on the local network, however. Ed examines the routing table on the user's workstation and sees the following listing. Which statement explains why the user cannot access the Internet?
IPv4 Route Table==========================================================================Active Routes:Network Destination Netmask Gateway Interface Metric127.0.0.0 255.0.0.0 On-link 127.0.0.1 331127.0.0.1 255.255.255.255 On-link 127.0.0.1 331127.255.255.255 255.255.255.255 On-link 127.0.0.1 331192.168.2.0 255.255.255.0 On-link 192.168.2.37 281192.168.2.37 255.255.255.255 On-link 192.168.2.37 281192.168.2.255 255.255.255.255 On-link 192.168.2.37 281224.0.0.0 240.0.0.0 On-link 127.0.0.1 331224.0.0.0 240.0.0.0 On-link 192.168.2.37 281255.255.255.255 255.255.255.255 On-link 127.0.0.1 331255.255.255.255 255.255.255.255 On-link 192.168.2.37 281==========================================================================Persistent Routes:None- The routing table does not specify a loopback address.
- The routing table does not specify a DNS server address.
- The routing table does not specify a default gateway address.
- The routing table contains two different routes to the 224.0.0.0 network.
- Which of the following statements about single-mode fiber-optic cable are true? (Choose all that apply.)
- Multimode cables use an LED light source, while single-mode cables use a laser.
- Multimode cables can span longer distances than single-mode cables.
- Multimode cables have a smaller core filament than single-mode cables.
- Multimode cables have a smaller bend radius than single-mode, making them easier to install.
- Multimode fiber-optic cables require a ground, whereas single-mode cables do not.
- A user swipes a smartcard through the reader connected to a laptop and then types a password to log on to the system. Which of the following actions is the user performing?
- Auditing
- Accounting
- Authorization
- Authentication
- Which of the following cabling topologies have never been used by standard Ethernet networks? (Choose all that apply.)
- Bus
- Ring
- Star
- Mesh
- Pulling into your company parking lot at lunchtime, you notice a person without a company parking sticker on his car working at a laptop. You have seen this more than once, and you begin to suspect that unauthorized users are connecting to the company's Wireless Access Point (WAP) and gaining access to the network. Which of the following are steps you can take to prevent this from happening in the future? (Choose all that apply.)
- Use Kerberos for authentication
- Place the access point in a screened subnet
- Disable SSID broadcasting
- Implement MAC address filtering
- Traffic shaping is a series of techniques that optimize the allocation of network bandwidth. Which of the following are techniques used in traffic shaping to prevent networks from being overwhelmed by data transmissions? (Choose all that apply.)
- Broadcast storming
- Bandwidth throttling
- Network Address Translation (NAT)
- Rate limiting
- Multiprotocol switches are devices that perform functions associated with two different layers of the Open Systems Interconnection (OSI) reference model. Which two of the following layers are often associated with network switching? (Choose all that apply.)
- Application
- Presentation
- Session
- Transport
- Network
- Data link
- Physical
- You are attempting to connect your new laptop to your company's wireless network. The Wireless Access Point (WAP) on the network has a Service Set Identifier (SSID) that is not broadcasted and uses WiFi Protected Access II (WPA2) for security. Which of the following describes what you must do to connect your laptop to the network?
- Select the SSID from a list and allow the client to automatically detect the security protocol.
- Type the SSID manually and then select WPA2 from the security protocol options provided.
- Type the SSID manually and allow the client to automatically detect the security protocol.
- Select the SSID from a list and then select WPA2 from the security protocol options provided.
- Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is a Media Access Control (MAC) mechanism designed to prevent two systems using the same network medium from transmitting at the same time. Which of the following IEEE standards calls for the use of CSMA/CA?
- 802.3
- 802.1X
- 802.11ac
- All of the above
- A large enterprise network will—at a minimum—have demarcation points for telephone services and a connection to an Internet Service Provider's (ISP's) network. In many cases, these services will enter the building in the same equipment room that houses the backbone switch. Which of the following is the term used to describe this wiring nexus?
- MTBF
- IDF
- RDP
- MDF
- You have configured your company's wireless network to enable clients to authenticate only when the signal strength of their connections exceeds a specified level. Which of the following terms best describes the security mechanism provided by this configuration?
- Geofencing
- Local authentication
- Motion detection
- Port security
- Social engineering has become an increasingly serious problem on your company network. Which of the following is an effective method for preventing sensitive data from being compromised through social engineering?
- Install a firewall between the internal network and the Internet.
- Install an antivirus software product on all user workstations.
- Implement a program of user education and corporate policies.
- Use IPSec to encrypt all network traffic.
- You have been given a Class B network IP address with which to configure the new network you are designing. Which of the following is the default subnet mask you should use for an IPv4 Class B network?
- 255.255.255.255
- 255.255.255.0
- 255.255.0.0
- 255.0.0.0
- Alice's company has just started working with sensitive government data. To enhance the security of the datacenter, she has implemented some additional security measures. All of the servers now have crimped metal tags holding the cases closed. All of the hardware racks are locked in clear-fronted cabinets. All of the cable runs are installed in transparent conduits. These are all examples of which of the following physical security measures?
- Geofencing
- Tamper detection
- Port security
- Asset tracking
- You have just installed a web server for your company, which is configured to host a public Internet site using the registered domain name
adatum.com. The server's hostname in the Domain Name System (DNS) iswww. The web server also has an administrative site, which you want to be able to access remotely. You have configured the administrative site to be encrypted and to use the port number 12354. Which of the following URLs must you use to access the administrative website from the Internet? - To prevent outside users from accessing your wireless network, you configure the access point not to broadcast the network's Service Set Identifier (SSID). However, you later discover that outsiders are still accessing the network. For which of the following reasons is disabling SSID broadcasts a relatively weak method of device hardening?
- Every access point's SSID is printed on a label on the back of the device.
- Attackers have software that can easily guess a network's SSID
- Attackers can capture packets transmitted over the network and read the SSID from them.
- Attackers have ways of connecting to the network without the SSID.
- You are installing a web server farm in your corporate headquarters, which will be used to host websites for the corporation's subsidiaries, located all around the world. In which of the following cloud models does a single organization function as both the provider and the consumer of all cloud services?
- Private cloud
- Public cloud
- Ad hoc cloud
- Hybrid cloud
- Your supervisor has recently begun using the terms on-boarding and off-boarding. With which of the following types of policies are these terms typically associated?
- Incident response
- Identity management
- Inventory management
- Data loss prevention
- Virtual Private Networks (VPNs) use a data transmission technique called tunneling, which encapsulates a data packet within another packet for transmission over a network connection, typically using the Internet. The system also encrypts the entire encapsulated data packet for protection. Split tunneling is a variation of this method that provides which of the following advantages? (Choose all that apply.)
- Additional data integrity protection
- Access to local network devices while connected to the VPN
- Faster data transmission through multiplexing
- Conservation of VPN bandwidth
- Your supervisor wants you to disable all of the ports on the network's switches that are not in use. You tell her that this is not necessary, and she wants to know why you think so. Which of the following are valid reasons not to disable unused switch ports? (Choose all that apply.)
- The unused ports are not patched in to wall jacks.
- The datacenter is already secured from unauthorized access.
- The switch is configured to use a MAC-based ACL.
- Leaving some ports enabled facilitates the on-boarding of new users.
- Despite having imposed password policies on your network that compel users to change their passwords frequently, create passwords of a specific length, and use complex passwords, you have still had several reports of account penetrations. After investigating the incidents, you determine that the victims had all apparently shared a “tip” suggesting that users cycle through the names of their children, nephews, nieces, and other relatives when forced to create new passwords, changing letters to numbers as needed. Which of the following actions can you take to remedy the situation without creating a larger problem?
- Modify the password policies to force users to change passwords more frequently.
- Change the minimum password age policy to a larger value.
- Distribute a list of common passwords that are insecure, such as those based on names, birth dates, etc.
- Assign the users long passwords consisting of random-generated characters and change them often.
- Which of the following network devices can employ Access Control Lists (ACLs) to restrict access? (Choose all that apply.)
- Routers
- Servers
- Switches
- Hubs
- Wireless Access Points
- Which of the following terms is used to describe the threat mitigation technique of deploying individual applications and services on separate virtual servers so that no more than one is endangered at any one time, rather than deploying multiple applications on a single server?
- Network segmentation
- Geofencing
- VLAN hopping
- Role separation
- Which of the following statements about Dynamic Host Configuration Protocol (DHCP) snooping are true? (Choose all that apply.)
- DHCP snooping is implemented in network switches.
- DHCP snooping prevents DNS cache poisoning.
- DHCP snooping detects rogue DHCP servers.
- DHCP snooping drops DHCP messages arriving over the incorrect port.
- A user reports that she cannot connect to a server on her network. You want to identify the scope of the problem, so you try to reproduce the problem on the user's computer. The problem persists. No other users are reporting the same problem. What is the next logical step that you should perform to identify the affected area?
- Examine the server's configuration for the correct settings.
- Verify that the local router is forwarding traffic.
- Confirm that the switch the client is connected to is functioning.
- Perform the same task on another computer connected to the same segment.
- On a wireless network, which of the following best describes an example of a captive portal?
- A web page stating that the data on a user's computer has been locked and will only be unlocked after payment of a fee
- A series of two doors with an intervening airlock through which people must pass before they can enter a secured space
- A dedicated switch port used to connect to other switches
- A web page with which a user must interact before being granted access to a wireless network
- In the standard troubleshooting methodology, you begin by taking steps to identify the problem. After you have done this, which of the following steps should you perform next?
- Verify full system functionality
- Establish a theory of probable cause
- Establish a plan of action
- Implement the solution
- The secured version of the Hypertext Transfer Protocol (HTTPS) uses a different well-known port from the unsecured version (HTTP). Which of the following ports are used by HTTP and HTTPS by default? (Choose all that apply.)
- 25
- 80
- 110
- 443
- Which of the following are criteria typically used by load balancers to direct incoming traffic to one server out of a group of servers? (Choose all that apply.)
- Fastest response time
- Fastest processor
- Lightest load
- The next in an even rotation
- You are responsible for a network that has a Domain Name System (DNS) server, a proxy server, and an Internet router. A user is reporting that she cannot connect to hosts on her own Local Area Network (LAN) or other internal LANs, and she also cannot access hosts on the Internet. No one else has reported a problem. What is the likeliest location of the issue preventing the user's access to the network?
- The router
- The DNS server
- The proxy server
- The user's computer configuration
- Virtual Local Area Network (VLAN) hopping is a type of attack directed at network switches. Which of the following best describes how VLAN hopping is a potential threat?
- VLAN hopping enables an attacker to access different VLANs using 802.1q spoofing.
- VLAN hopping enables an attacker to scramble a switch's patch panel connections.
- VLAN hopping enables an attacker to change the native VLAN on a switch.
- VLAN hopping enables an attacker to rename the default VLAN on a switch.
- You are a first-tier support technician working the IT help desk at your company. In your first hour of duty, you receive four trouble calls. Your job is to prioritize the calls based on their severity. Which of the following should be the problem that receives the lowest priority?
- A fatal error that causes a single computer to fail
- A problem with a mission-critical backbone router that affects an entire network
- A problem with an application server that affects a single Local Area Network (LAN)
- A problem with an order entry or customer service call center resource that affects an entire department, with multiple LANs
- You are attempting to access a Domain Name System (DNS) server located on the other side of a router, but your attempt fails with an error stating that the destination port UDP 53 is unreachable. Your first step in troubleshooting the problem is to try using the
nslookuputility to access that specific DNS server. This attempt also fails. Next, you use thepingutility with the DNS server's IP address. Thepingtest is successful, indicating that the server is up and running. Which of the following are possible causes of the problem? (Choose all that apply.)- The TCP/IP host settings on your computer are improperly configured.
- The router connecting the networks is not running DNS and will not forward this type of datagram.
- There is a firewall blocking the DNS server's UDP port 53.
- The DNS process on the remote server is not running.
- The TCP/IP host settings on the DNS server are improperly configured.
- Which of the following types of switches performs a Cyclic Redundancy Check (CRC) on an entire frame's contents prior to forwarding it out a port leading to the destination system?
- Packet filtering
- Cut-through
- Source route
- Store-and-forward
- Which of the following attack types is not specifically targeted at wireless network clients?
- Logic bomb
- Deauthentication
- Evil twin
- War driving
- You are having trouble installing a Wireless Local Area Network (WLAN) using IEEE 802.11b/g equipment in a new office complex. The wireless devices have trouble connecting to the access point, and when they do, they achieve only low speeds. When you use a WiFi analyzer to scan the 2.4 GHz frequency band, you see literally dozens of other networks in the area, spread across all of the available channels. Choose the tasks from the following list that you should perform to enable your wireless devices to connect to the network reliably and at their best possible speeds. (Choose all that apply.)
- Configure the access point to suppress SSID broadcasts.
- Configure all of the wireless network devices to use the 5 GHz band.
- Upgrade all of the network devices to the latest firmware.
- Configure all of the network devices to use WPA2 encryption with AES.
- Upgrade the access point and all of the wireless client devices to IEEE 802.11n.
- Which Windows command-line utility produced the output shown here?
Interface: 192.168.2.24 --- 0x2Internet Address Physical Address Type192.168.2.2 d4-ae-52-bf-c3-2d dynamic192.168.2.20 00-26-c7-7e-00-e0 dynamic192.168.2.22 00-90-a9-a2-43-8f dynamic192.168.2.27 1c-c1-de-ca-1f-12 dynamic192.168.2.28 30-f7-72-38-e9-1d dynamic192.168.2.255 ff-ff-ff-ff-ff-ff static224.0.0.22 01-00-5e-00-00-16 static224.0.0.251 01-00-5e-00-00-fb static224.0.0.252 01-00-5e-00-00-fc static224.0.0.253 01-00-5e-00-00-fd static239.255.255.250 01-00-5e-7f-ff-fa static255.255.255.255 ff-ff-ff-ff-ff-ff staticarppingtracertnetstat
- Your boss is working in the crawlspace under the floor of the datacenter, and he asks you to hand him the pliers. You hand him the tool shown in the following figure, and he throws it back at you. What is the real function of the tool shown in the figure?

Reprinted from CompTIA Network+ Study Guide: Exam N10-006, Third Edition by Todd Lammle (Wiley, 2015)
- When you connect the tool to pins in a punchdown block, you can access telephone circuits in order to test them or place telephone calls.
- When you attach the tool to one end of a wire, it generates a tone that can be detected at the other end.
- To attach a bulk cable end to an RJ45 connector, you use the tool to squeeze the connector closed, forcing the wire ends to contact the connector's pins.
- When you attach the tool to a copper cable, you can detect and measure the electrical current flowing through it.
- You are starting work for a contractor that performs telecommunications cable installations. One of the tools in the kit you have been given is in the following figure. What is the name of the tool shown?

Reprinted from CompTIA Network+ Study Guide: Exam N10-006, Third Edition by Todd Lammle (Wiley, 2015)
- Crimper
- Punchdown tool
- Butt set
- Tone generator and locator
- You are seeking to upgrade your company's IEEE 802.11b access point to one that provides faster transmission speeds for your newer workstations. Which of the following wireless networking standards are capable of supporting speeds faster than the 11 Mbps of 802.11b but that are still backward compatible with your existing IEEE 802.11b workstations? (Choose all that apply.)
- IEEE 802.11
- Bluetooth
- IEEE 802.11g
- IEEE 802.11a
- IEEE 802.11n
- You are working on your company's screened subnet (also known as a perimeter network), which has five Linux web servers, a Cisco router, a CSU/DSU providing a leased line connection, and a Windows-based firewall on it. While trying to troubleshoot a network communications failure, you type the following command on one of the systems:
tracerouteadatum.com. Which of the following systems might you be working on? (Choose all that apply.)- The Cisco router
- One of the Linux web servers
- The CSU/DSU console
- The Windows-based firewall
- Which of the following are network topologies used by IEEE 802.11 Wireless Local Area Networks (WLANs)? (Choose all that apply.)
- Bus
- Mesh
- Ad hoc
- Star
- Infrastructure
- You have recently started a new job that enables you to telecommute from home, and you need a Wide Area Network (WAN) connection to the Internet. You will need to access the company network using a Virtual Private Network (VPN) connection to obtain client information, transfer files, and send email through the company servers. Your home is over 30 years old. The existing telephone wiring was not run through a conduit, and it seems to be deteriorating. You have cable television service, and your home is approximately 20,000 feet from the nearest telephone central office. You want to implement the fastest possible remote connection service, but cost is still a factor in the decision. Which WAN technology should you implement?
- A standard modem-to-modem connection
- A DSL (Digital Subscriber Line) connection
- A broadband cable television (CATV) connection
- A dedicated leased line (fractional T-1)
- You are working the help desk at a local computer store, and you receive a call from a customer trying to set up a home network using computers running Windows 10 and wired Ethernet equipment. The customer reports that she cannot access the other two computers in the house from her workstation, nor can she access the Internet. You ask her to run the
ipconfig /allcommand and read the results to you. She says that her IP address is 192.168.0.2, her subnet mask is 255.255.255.0, and her default gateway is 192.168.0.1. Which of the following is the most likely cause of the customer's problem?- The customer's network address cannot include a zero.
- The customer has an incorrect subnet mask.
- The customer's network cable is damaged or unplugged.
- The customer has an incorrect default gateway address.
- Some networks are designed with a switching fabric that contains redundant paths, for fault tolerance purposes. However, in this type of design, it is possible for packets to circulate endlessly around the network, which is called a switching loop. Which of the following protocols prevents network switching loops from occurring by shutting down redundant links until they are needed?
- NAT
- RIP
- VLAN
- STP
- You are responsible for an internetwork that consists of four internal Local Area Networks (LANs) with 50 users each. Each internal LAN uses twisted-pair Gigabit Ethernet links that connect the users to a switch. Each of the four switches is connected to a separate router. All four routers connect to the same backbone network, which has a single additional router to connect the company's network to the Internet, using a T-1 Wide Area Network (WAN) link. Today, users on one of the four internal LANs are reporting that when they came in this morning, they could not access the Internet or resources on the other three internal LANs. However, they could access resources on their own LAN with no problems. Which network component is the likeliest source of the problem in this scenario?
- The switch on the problem LAN
- The Internet router
- The router connecting the problem LAN to the backbone
- The cable on the backbone network
- You are negotiating an agreement with a provider for your company's email service. You have been told to require a 99.99 percent guaranteed rate of service reliability, but the provider is only willing to guarantee 99 percent. Eventually, you and the provider agree on a compromise of 99.9 percent. Which of the following documents will include the negotiated language on this particular point?
- AUP
- SLA
- BYOD
- NDA
- Which of the following types of networking devices can split a single network into multiple collision domains while maintaining a single broadcast domain? (Choose all that apply.)
- Switch
- Bridge
- Router
- Hub
- You have just finished installing a web server farm on your company's network, along with a router to create a screened subnet (perimeter network) on which the web servers are located. However, you now cannot access the web servers from your workstation on the internal network. Which of the following is not one of the tasks you will have to complete before you can access the screened subnet from the internal network?
- Change MAC addresses
- Change IP addresses
- Update the DNS records
- Change default gateway addresses
- You are testing a twisted-pair cable run using a tone generator and locator. When you apply the tone generator to a particular pin at one end of the cable, you detect a tone on two pins at the other end. Which of the following faults have you discovered?
- Split pair
- Open
- Short
- Crosstalk
- Your network has been experiencing intermittent service slowdowns and outages ever since the company moved into their new building. You have tried every troubleshooting modality you can think of, but you have not been able to determine the cause. One particular user, perhaps hoping to be the squeaky wheel that gets the grease, has taken to calling you every time he experiences a problem. One day, as you are working in the datacenter, you notice that the user calls every time you hear an additional humming noise. After examining the doors in the hallway, you realize that the racks containing the network switches are located right next to the elevator machinery room. Which of the following conditions is probably causing this intermittent network communication problem?
- Bottleneck
- EMI
- Latency
- Crosstalk
- Ralph is installing a pair of redundant servers and must choose whether to run them in an active-active or active-passive configuration. Running the servers in an active-active configuration provides which of the following advantages that the same servers in an active-passive configuration do not? (Choose all that apply.)
- Fault tolerance
- Load balancing
- Data encapsulation
- Increased performance
- You are starting work at a new company, and on your first day, you ask about wireless access for your laptop. You are given a Service Set Identifier (SSID) and a WiFi Protected Access II (WPA2) passphrase. Later, in the lunchroom, when you try to connect your laptop to the network, you cannot see the SSID you were given in the list of available networks, although you can see other networks. What should you do next to try to resolve the problem?
- Move closer to the Wireless Access Point (WAP).
- Move away from the microwave in the lunchroom.
- Type in the WPA2 passphrase.
- Type the SSID in manually.
- You are responsible for a Wireless Local Area Network (WLAN) that consists of an 802.11n 2x2 access point and laptop computers with a variety of network adapters. Some of the laptops support 802.11n, most support 802.11g, and a few older models have 802.11b adapters. The WLAN is located in a large office building with many other wireless networks, and you are having trouble finding a channel on the 2.4 GHz band that is not congested with traffic. Scanning the 5 GHz band, you find relatively little traffic, so you reconfigure the access point to use a 5 GHz channel. The result is that some of the laptops are able to connect to the network, whereas others are not. What is the most likely reason for the connection failures, and what must you do to enable all the laptops to connect to the wireless network?
- The 802.11b standard does not support communication using the 5 GHz band. You must replace the network adapters in those laptops with newer models for them to connect successfully.
- The 5 GHz band does not support automatic channel selection. You must configure each laptop to use the same channel as the access point for all the laptops to connect successfully.
- The 5 GHz band does not support Multiple Input, Multiple Output (MIMO) communications, so the 802.11n laptops are unable to connect to the network. You must replace the access point with an 802.11g unit for all the laptops to connect successfully.
- The 802.11g and 802.11b standards do not support communication using the 5 GHz band. You must configure the access point to support 2.4 GHz for all the laptops to connect successfully.
- In the Domain Name System (DNS), a zone is a contiguous area of the DNS namespace for which authority is delegated to one or more DNS servers. Which of the following DNS resource record types specifies the IP addresses of the authoritative DNS servers for a particular zone?
- PTR
- SRV
- MX
- NS
- You are experiencing poor performance on your home 802.11n wireless network. You live in a large apartment complex, and when you run a WiFi analyzer, you see many other nearby networks using the often-recommended channels 1, 6, and 11 on the 2.4 GHz frequency. Using the 5 GHz frequency is not an option for your equipment. What should you do to improve the network's performance?
- Configure your equipment to use channel 10.
- Configure your equipment to use channel 9.
- Configure your equipment to use channel 5.
- Configure your equipment to use channel 2.
- Your company's office building is having a fire inspection, and you are the only person on duty in the datacenter. The inspector from the fire department asks you where they can find documentation about all chemicals and equipment used in the company's datacenter. You lead the inspector to the director's office, but you are not sure what the documents he needs are called. Which of the following document types contains this information?
- MSDS
- NDA
- BYOD
- ESD
- Which of the following Power over Ethernet (PoE) specifications supplies power to devices using the spare wire pair on a 10Base-T or 100Base-TX twisted-pair network?
- 4PPoE
- Alternative A
- Alternative B
- All of the above
- The iSCSI storage area networking protocol uses clients called initiators and servers called targets. However, on many Storage Area Networks (SANs), there needs to be a way for the initiators to locate the targets. Which of the following technologies do iSCSI initiators use to locate iSCSI targets on the network?
- ICMP
- DNS
- iDNS
- iSNS
- You are deploying an 802.11n wireless network for a client that is asking for the best possible security you can provide without deploying additional servers. When setting up the Wireless Access Point (WAP), you disable Service Set Identifier (SSID) broadcasts, select WiFi Protected Access with Pre-Shared Keys (WPA-PSKs), and configure Media Access Control (MAC) address filtering. Which of the following statements about the security of this arrangement is true?
- You should not disable SSID broadcasts since this prevents users from connecting to the network.
- The configuration is as secure as you can make it with the specified equipment.
- You should use WiFi Protected Access II (WPA2) instead of WPA, since it is more resistant to certain types of attacks.
- You should not use MAC address filtering since it exposes MAC addresses to possible attacks.
- Which of the following connector types are used with fiber-optic cables? (Choose all that apply.)
- DB-9
- SC
- BNC
- ST
- MTRJ
- RJ11
- Which of the following are available as Internet of Things (IoT) devices?
- Refrigerators
- Doorbells
- Thermostats
- Speakers
- All of the above
- You are designing an Ethernet network for your company's newest branch office. Your current task is to decide which Ethernet specification to use for the network, a decision that you know will determine what type of cabling you need to purchase and the topology with which the cable will be installed. Which layers of the Open Systems Interconnection (OSI) reference model apply to the cabling and topology elements of a network?
- The application and transport layers
- The transport and network layers
- The network and data link layers
- The data link and physical layers
- You are troubleshooting a workstation that cannot access the network. The workstation is plugged into a wall plate that should provide it with access to a DHCP-equipped network using the 192.168.4.0/24 network address. No one else on that network is reporting a problem. You check that the patch cable is properly plugged into the workstation and the wall plate, which they are, and then run
ipconfig /allon the workstation and examine the output. Which of the statements could be the explanation for the workstation's problem, based on the followingipconfigresults?Windows IP ConfigurationHost Name . . . . . . . . . . . . : Client12Primary Dns Suffix . . . . . . . :Node Type . . . . . . . . . . . . : HybridIP Routing Enabled. . . . . . . . : NoWINS Proxy Enabled. . . . . . . . : NoEthernet adapter Local Area Connection:Connection-specific DNS Suffix . :Description . . . . . . . . . . . : PCIe Family ControllerPhysical Address. . . . . . . . . : 60-EB-69-93-5E-E5DHCP Enabled. . . . . . . . . . . : YesAutoconfiguration Enabled . . . . : YesLink-local IPv6 Address . . . . . : fe80::c955:c944:acdd:3fcb%2IPv4 Address. . . . . . . . . . . : 169.254.203.42Subnet Mask . . . . . . . . . . . : 255.255.0.0Lease Obtained. . . . . . . . . . : Monday, October 23, 2017 6:23:47 PMLease Expires . . . . . . . . . . : Saturday, November 18, 2017 9:49:24 PMDefault Gateway . . . . . . . . . :DHCPv6 IAID . . . . . . . . . . . : 241232745DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-18-10-22-0D-60-EB-69-93-5E-E5DNS Servers . . . . . . . . . . . : fec0:0:0:ffff::1%1fec0:0:0:ffff::2%1fec0:0:0:ffff::3%1NetBIOS over Tcpip. . . . . . . . : Enabled- The DNS server addresses are incorrect.
- The Default Gateway address is missing.
- The Subnet Mask value is incorrect.
- The DHCP scope is exhausted.
- A user calls you at the IT help desk and reports that she is having intermittent problems accessing both local servers and internet websites. Which of the following potential problems can you rule out immediately?
- Malfunctioning Domain Name System (DNS) server
- Duplicate Media Access Control (MAC) addresses
- Duplicate IP addresses
- Malfunctioning router
- You have recently discovered a rogue Dynamic Host Configuration Protocol (DHCP) server on your network. After disabling the rogue server, you now need to terminate all of the rogue IP address leases currently held by DHCP clients on the network and then have them request new leases from the authorized DHCP server. Which of the following commands must you run on each client to do this? (Choose all that apply.)
ipconfig /dumpipconfig /leaseipconfig /releaseipconfig /renewipconfig /discard
- Ralph is reading an article about datacenter design, and he is puzzled by references to east-west and north-south traffic. Which of the following statements best describes the difference between east-west and north-south traffic in a datacenter?
- East-west is switch-to-switch traffic, while north-south is switch-to-router traffic.
- East-west describes traffic between devices at the same layer of the Open Systems Interconnection (OSI) reference model, while north-south describes traffic between OSI model layers.
- East-west traffic stays within the datacenter, while north-south traffic does not.
- East-west is backbone traffic among switches and routers, while north-south is traffic to end systems, such as servers.
- Which of the following attack types involves the modification of a legitimate software product?
- War driving
- Logic bomb
- Evil twin
- Social engineering
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
