Chapter 2
Network Implementations
- Which of the following technologies associated with the Internet of Things (IoT) is often used to identify pets using embedded chips?
- Z-wave
- Bluetooth
- NFC
- RFID
- Which of the following is typically not an example of the Internet of Things (IoT)?
- A key fob that unlocks your car
- A smartphone home automation app
- A remotely monitored cardiac pacemaker
- A seismic early warning system
- A Wireless Access Point (WAP) enables computers equipped with wireless network interface adapters to function in which of the following topologies?
- Star
- Ad hoc
- Bus
- Infrastructure
- Ralph has been hired by a company to redesign its Local Area Network (LAN). Right now, it has a single 100 Mbps Ethernet LAN with 40 users and 2 shared servers, all connected through 3 hubs. The users on the network must be able to share files with one another and also access the shared servers. The users are complaining that the network is too slow. Management states that cost is a factor that must be considered. Which of the following upgrade scenarios should Ralph recommend in this situation?
- Split the network into smaller segments with dedicated hubs as opposed to shared hubs.
- Split the network into two routed LANs with 20 users each.
- Replace the hubs with switches to define separate collision domains and filter unnecessary traffic from each segment.
- Replace the hubs with a layer 3 switch and define two Virtual LANs (VLANs) with 20 users each.
- Which of the following devices can split a single network into two collision domains while maintaining a single broadcast domain?
- Hub
- Bridge
- Switch
- Router
- Repeater
- Which two of the following functions is the multifunction device on a home or small office network known as a broadband router least likely to provide? (Choose two.)
- Wireless Access Point (WAP)
- Switch
- Proxy server
- DHCP server
- VPN headend
- Which of the following devices run exclusively at the physical layer of the Open Systems Interconnection (OSI) model? (Choose all that apply.)
- Routers
- Hubs
- Repeaters
- Switches
- Which of the following is the true definition of the term modem?
- A device that connects a computer to the Public Switched Telephone Network (PSTN)
- A device that connects a Local Area Network (LAN) to the Internet
- A device that converts analog signals to digital signals and back again
- A device that connects a Local Area Network (LAN) to a Wide Area Network (WAN)
- Which of the following devices is used to physically connect computers in the same Virtual Local Area Network (VLAN)?
- A bridge
- A hub
- A switch
- A router
- Which of the following best describes the function of a firewall?
- A device located between two networks that enables administrators to restrict incoming and outgoing traffic
- A device that connects two networks together, forwarding traffic between them as needed
- A device that enables Internet network clients with private IP addresses to access the Internet
- A device that caches Internet data for subsequent use by internal network clients
- Which of the following terms is used to describe the method by which a firewall examines the port numbers in transport layer protocol headers?
- IP address filtering
- Service-dependent filtering
- Deep Packet Inspection (DPI)
- Next-Generation Firewall (NGFW)
- Which of the following devices can also be described as a multiport repeater?
- Hub
- Bridge
- Switch
- Router
- Which of the following bridging types has never been used on Ethernet Local Area Networks (LANs)?
- Store and forward
- Transparent
- Source route
- Multiport
- Which of the following physical network devices can conceivably be implemented as software in a computer's operating system? (Choose all that apply.)
- Hub
- Switch
- Router
- Firewall
- Which of the following criteria does a firewall capable of service-dependent filtering use to block traffic?
- Hardware addresses
- Protocol identifiers
- IP addresses
- Port numbers
- Ralph is a freelance network consultant installing a three-node small business network. The computers are all in the same room and use wired Ethernet to connect to the switched ports of a multifunction device. The device also functions as a Network Address Translation (NAT) router for a cable modem connection to the Internet. NAT provides a measure of security, but Ralph wants to be sure that the network is protected from unauthorized Internet traffic and attacks against open ports. Which of the following solutions would enable Ralph to accomplish this goal with the minimum cost to the client?
- Install a hardware firewall between the multifunction device and the cable modem.
- Install an Intrusion Prevention System (IPS) between the multifunction device and the cable modem.
- Install a personal firewall on each of the computers.
- Connect an Intrusion Detection System (IDS) to one of the switched ports in the multifunction device.
- Use a port scanner to monitor the traffic entering the open ports on the computers.
- Which of the following statements about hubs and switches are true? (Choose all that apply.)
- Hubs operate at the physical layer, whereas switches operate at the network layer.
- All of the devices connected to a hub are part of a single collision domain, whereas each device connected to a switch has its own collision domain.
- There are switches available with network layer functionality, but there are no hubs with that capability.
- Switches create a separate broadcast domain for each connected device, whereas hubs create a single broadcast domain for all of the connected devices.
- Which of the following problems is the Spanning Tree Protocol (STP) intended to prevent? (Choose all that apply.)
- Broadcast storms
- Late collisions
- Bridging loops
- Crosstalk
- Which of the following devices perform essentially the same function? (Choose two.)
- Hubs
- Bridges
- Switches
- Routers
- Which of the following is not one of the five functional levels associated with a distributed control system such as Supervisory Control and Data Acquisition (SCADA) systems?
- Field level
- Remote access
- Direct control
- Plant supervisory
- Production control
- Production scheduling
- Which of the following switch types immediately forwards frames after looking at only the destination address?
- Cut-through
- Source route
- Store-and-forward
- Destination
- Which of the following does a switch use to forward incoming packets out through the correct ports?
- IP addresses
- MAC addresses
- DNS names
- MTU values
- Which of the following statements about the Spanning Tree Protocol (STP) is not true?
- STP operates at the data link layer of the OSI model.
- STP is implemented in switches.
- STP prevents traffic from circulating endlessly around a network.
- STP compiles a database containing the IP addresses of connected devices.
- Small Office Home Office (SOHO) networks typically use a multifunction connectivity device that can perform all but which one of the following functions?
- DHCP
- DNS
- Switch
- Router
- Hub
- NAT router
- Access Point (AP)
- Which of the following is the correct term for the process by which the Spanning Tree Protocol (STP) on a switch evaluates the paths through the network and places each port in the forwarding or blocking state?
- Assimilation
- Convergence
- Tree-building
- Listening
- A multilayer switch typically functions at which layers of the OSI reference model? (Choose two.)
- Data link
- Network
- Transport
- Application
- Which of the following is something that only a firewall capable of stateful packet inspection can do?
- Filter traffic-based port numbers
- Block traffic destined for specific IP addresses
- Scan transport layer header fields for evidence of SYN floods
- Block all TCP traffic from entering a network
- In local area networking, which of the following is not a type of bridge?
- Store and forward
- Routing
- Transparent
- Multiport
- Which of the following are methods typically used by Intrusion Detection Systems (IDSs) to analyze incoming network traffic? (Choose all that apply.)
- Anomaly-based detection
- Behavior-based detection
- Signature-based detection
- Statistic-based detection
- Virtual Local Area Networks (VLANs) create the administrative boundaries on a switched network that are otherwise provided by which of the following devices?
- Hubs
- Routers
- Firewalls
- Bridges
- Which of the following devices can you use to connect two multimode fiber-optic Ethernet networks in different buildings 2000 meters apart using a single-mode fiber-optic cable segment running at the same speed, while maintaining a single collision domain?
- Bridge
- Switch
- Router
- Media converter
- Which of the following is another term for a multiport bridge?
- Router
- Switch
- Hub
- Gateway
- Which of the following devices enables two computers to communicate when they are using different protocols at each layer of the Open Systems Interconnection (OSI) reference model?
- A router
- A switch
- A hub
- A gateway
- Review the following figure. How many collision domains and broadcast domains exist in the network diagram?
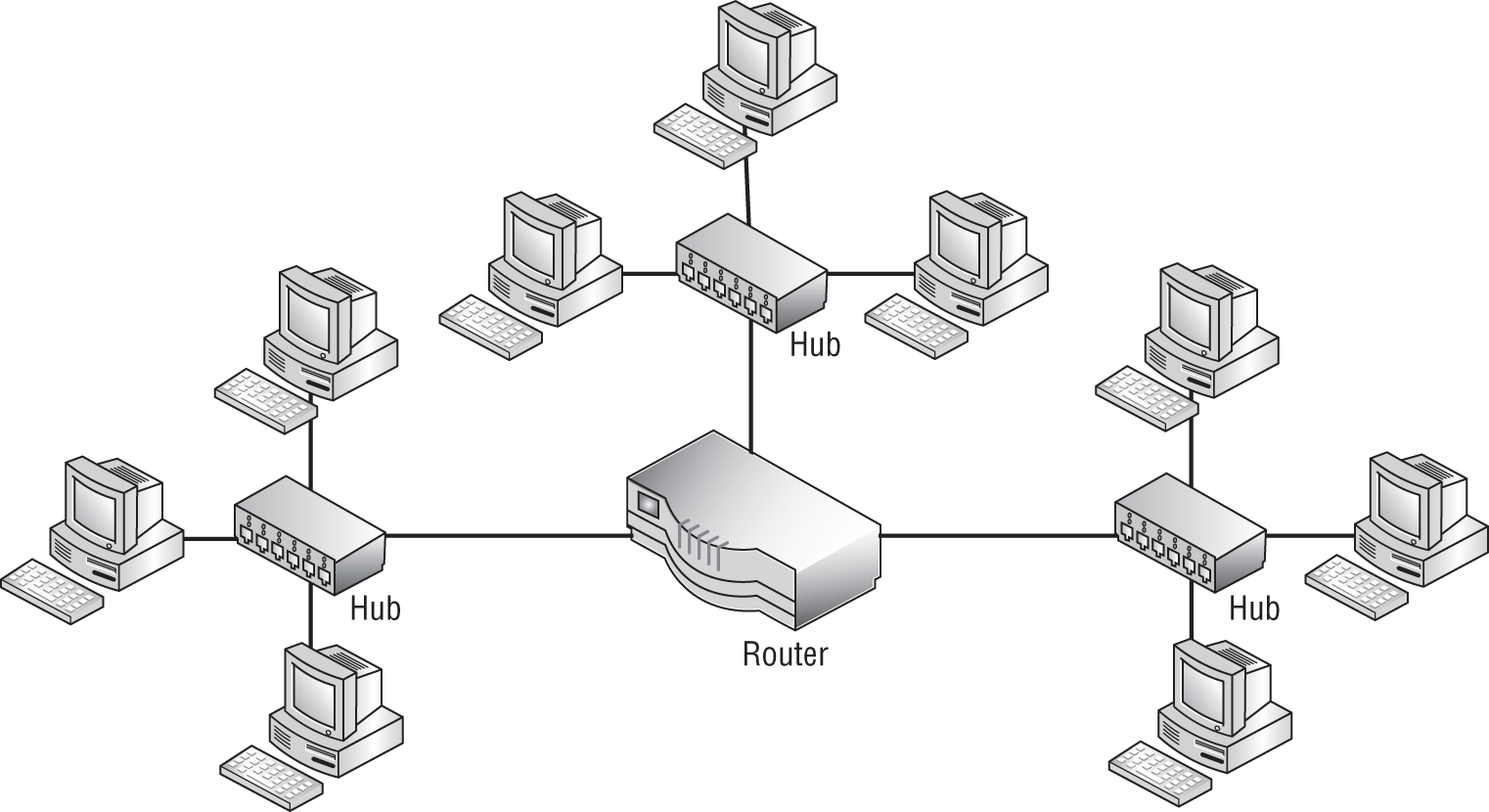
- There are three collision domains and three broadcast domains.
- There is one collision domain and three broadcast domains.
- There is one broadcast domain and three collision domains.
- There are no collision domains and only one broadcast domain.
- There are nine collision domains and three broadcast domains.
- Which of the following statements about switches and routers are true? (Choose all that apply.)
- Routers operate at the network layer, whereas switches operate at the data link layer.
- All of the devices connected to a switch are part of a single broadcast domain, whereas the networks connected to a router form separate broadcast domains.
- Routers can communicate with each other and share information, but switches cannot.
- Switches forward packets based on their hardware addresses, whereas routers forward packets based on their IP addresses.
- Ralph is installing an Ethernet Local Area Network (LAN) for a small business with two offices on opposite sides of a courtyard. Ralph plans to run a multimode fiber-optic cable across the courtyard, but the budget is limited, and he cannot use fiber for the whole network. Therefore, he installs Unshielded Twisted Pair (UTP) cable in the two offices, which have 10 and 12 workstations, respectively. Which of the following devices should Ralph use to join the two UTP installations together into one LAN using the fiber-optic run across the courtyard, while keeping the cost to a minimum?
- Media converters
- Hubs
- Switches
- Routers
- Five computers are connected to the same switch, but only four are able to communicate with each other. Assuming that all of the hardware is functioning properly, which of the following could be a reason for the fifth computer's communication problem?
- The switch has the fifth computer connected to a Virtual Local Area Network (VLAN) that's different from that of the other four.
- The network is experiencing a switching loop.
- The fifth computer is experiencing an MTU black hole, whereas the other four computers are not.
- There is a virtual router between the fifth computer and the other four.
- Which of the following types of systems are frequently used to collect information from Intrusion Detection Systems (IDSs)?
- SIEM
- NGFW
- RADIUS
- VoIP
- Which of the following network devices are “dumb”—that is, purely electrical devices with no electronic intelligence?
- Hubs
- Switches
- Routers
- Bridges
- Which of the following explains why splitting a large, switched Ethernet LAN into two LANs by adding a router can help to alleviate traffic congestion and improve performance? (Choose all that apply.)
- Adding a router reduces the amount of broadcast traffic on each of the two LANs.
- Adding a router reduces the amount of unicast traffic on each of the two LANs.
- Adding a router diverts traffic to an alternate path through the network.
- Adding a router prevents computers on one LAN from communicating with computers on another LAN.
- A small business office currently has a 100Base-TX Ethernet network with a single 8-port hub. All of the hub ports are populated, and the business owner wants to expand the network further. However, the hub does not have an uplink port. The owner has purchased a new hub, also with eight ports, which does have an uplink port, but he does not know how to connect them together. What must the owner do to install the new hub on the network?
- Use a standard patch cable to connect a standard port on the existing hub to a standard port on the new hub.
- Use a standard patch cable to connect a standard port on the existing hub to the uplink port on the new hub.
- Purchase a crossover cable and use it to connect a standard port on the existing hub to the uplink port on the new hub.
- Purchase a second new hub with an uplink port to replace the old one and use a standard patch cable to connect the two uplink ports together.
- Which of the following tasks can you perform to split a large, switched Local Area Network (LAN) into multiple broadcast domains? (Choose all that apply.)
- Replace one or more switches with hubs.
- Install a firewall to filter broadcast traffic.
- Enable the Spanning Tree Protocol (STP) on the switches.
- Create Virtual Local Area Networks (VLANs) in the switches.
- Install routers on the network.
- Which of the following statements about bridges and switches is true?
- Bridges and switches are network layer devices that use logical addressing to forward frames.
- Bridges and switches are data link layer devices that use Media Access Control (MAC) addresses to forward frames.
- Bridges and switches build their internal tables based on destination addresses and forward packets based on source addresses.
- Bridges and switches must support the network layer protocol implemented on the Local Area Network (LAN).
- Each port on a bridge or switch defines a separate broadcast domain.
- Which of the following is a correct term describing the function of a switch?
- Layer 2 router
- Ethernet hub
- Multiport bridge
- Layer 3 repeater
- Which of the following are available as Internet of Things (IoT) devices?
- Refrigerators
- Doorbells
- Thermostats
- Speakers
- All of the above
- Which of the following is the primary reason why replacing hubs with switches on an Ethernet Local Area Network (LAN) improves its performance?
- Switches forward packets faster than hubs.
- Switches do not forward broadcast transmissions.
- Switches reduce the number of collisions on the network.
- Switches read the IP addresses of packets, not the hardware addresses.
- Which of the following is a correct definition of a collision domain?
- A group of Local Area Networks (LANs), connected by routers, that enables any node to transmit to any other node
- A group of computers connected so that a broadcast transmission by any one device reaches all of the other devices
- A group of devices connected by cable segments that are longer than the maximum length stated in the physical layer specification
- A group of devices connected so that when two devices transmit at exactly the same time, a data collision occurs
- Which of the following terms are used to describe the device used to place calls on a Voice over Internet Protocol (VoIP) installation? (Choose all that apply.)
- Terminal
- Gateway
- Endpoint
- PBX
- Which of the following statements about hubs is not true?
- Hubs are data link layer devices that connect network devices in a star or ring topology.
- Hubs amplify and repeat signals received through one port out all other ports regardless of the destination.
- Hubs are physical layer devices that connect network devices in a star topology.
- Hubs provide internal crossover circuits and use uplink ports to form a hierarchical star.
- Which of the following statements about routers are true? (Choose all that apply.)
- Routers are network layer devices that use IP addresses to forward frames.
- Routers are data link layer devices that use Media Access Control (MAC) addresses to forward frames.
- Routers build their internal tables based on destination MAC addresses and forward frames based on source MAC addresses.
- Routers must support the network layer protocol implemented on the Local Area Network (LAN).
- Each port on a router defines a separate broadcast domain.
- Which of the following hub types are supported by the 100Base-TX physical layer specification? (Choose all that apply.)
- Class I
- Class II
- Class III
- Class IV
- Which of the following statements about routers is not true?
- Routers can connect two or more networks with dissimilar data link layer protocols and media.
- Routers can connect two or more networks with the same data link layer protocols and media.
- Routers store and maintain route information in a local text file.
- Servers with multiple network interfaces can be configured to function as software routers.
- Routers can learn and populate their routing tables through static and dynamic routing.
- The network administrator for a small business is installing a computer to function as a firewall protecting their internetwork from Internet intrusion. At which of the following locations should the administrator install the firewall system?
- Anywhere on the private internetwork, as long as the Internet is accessible
- Between the Internet access router and the Internet Service Provider's (ISP's) network
- At the ISP's network site
- Between the Internet access router and the rest of the private internetwork
- What must you do to configure a firewall to admit File Transfer Protocol (FTP) traffic to the internal network using its default port settings? (Choose all that apply.)
- Open port 20
- Open port 21
- Open port 22
- Open port 23
- Open port 24
- Proxy servers operate at which layer of the OSI reference model?
- Data link
- Network
- Transport
- Application
- Which of the following is a feature that is not found in a traditional firewall product, but which might be found in a Next-Generation Firewall (NGFW)?
- Stateful packet inspection
- Deep Packet Inspection (DPI)
- Network Address Translation (NAT)
- Virtual Private Network (VPN) support
- Which of the following statements about content filtering in firewalls is true?
- Content filters examine the source IP addresses of packets to locate potential threats.
- Content filters enable switches to direct packets out through the correct port.
- Content filters examine the data carried within packets for potentially objectionable materials.
- Content filters use frequently updated signatures to locate packets containing malware.
- Which of the following is not one of the criteria typically used by load balancers to direct incoming traffic to one of a group of servers?
- Which server has the lightest load
- Which server has the fastest response time
- Which server is next in an even rotation
- Which server has the fastest processor
- Which of the following devices enables you to use a standard analog telephone to place calls using the Internet instead of the Public Switched Telephone Network (PSTN)?
- Proxy server
- VPN headend
- VoIP gateway
- UTM appliance
- Which of the following devices enable users on private networks to access the Internet by substituting a registered IP address for their private addresses? (Choose all that apply.)
- NAT router
- RADIUS server
- Proxy server
- UTM appliance
- HVAC systems can use the Internet of Things (IoT) to monitor which of the following? (Choose all that apply.)
- Temperature
- Pressure
- Humidity
- Printers
- Occupancy
- Cameras
- Door locks
- A VPN headend is an advanced type of which of the following devices?
- Switch
- Router
- Gateway
- Bridge
- Which of the following technologies is typically associated with virtual PBX services?
- Quality of Service (QoS)
- Voice over IP
- CARP
- Round-robin DNS
- Ralph, the administrator of a 500-node private internetwork, is devising a plan to connect the network to the Internet. The primary objective of the project is to provide all of the network users with access to web and email services while keeping the client computers safe from unauthorized users on the Internet. The secondary objectives of the project are to avoid having to manually configure IP addresses on each one of the client computers individually and to provide a means of monitoring and regulating the users’ access to the Internet. Ralph submits a proposal calling for the use of private IP addresses on the client computers and a series of proxy servers with public, registered IP addresses, connected to the Internet using multiple T-1 lines. Which of the following statements about Ralph's proposed Internet access solution is true?
- The proposal fails to satisfy both the primary and secondary objectives.
- The proposal satisfies the primary objective but neither of the secondary objectives.
- The proposal satisfies the primary objective and one of the secondary objectives.
- The proposal satisfies the primary objective and both of the secondary objectives.
- Which of the following protocols can be used by wireless controllers to communicate with the Access Points (APs) on a Wireless Local Area Network (WLAN)? Choose all that apply.
- CAPWAP
- LWAPP
- LDAP
- PPTP
- Which of the following devices enables administrators of enterprise wireless networks to manage multiple Access Points (APs) from a central location?
- Hypervisor
- Wireless controller
- Wireless endpoint
- Demarcation point
- Which of the following devices can administrators use to create multiple Virtual Local Area Networks (VLANs) and forward traffic between them?
- Multilayer switch
- Virtual router
- Load balancer
- Broadband router
- Which of the following is not a mechanism for distributing incoming network traffic among multiple servers?
- Load balancer
- Round-robin DNS
- NLB cluster
- VPN headend
- A load balancer is a type of which of the following devices?
- Switch
- Router
- Gateway
- Firewall
- Which of the following devices expands on the capabilities of the traditional firewall by adding features like Deep Packet Inspection (DPI) and an Intrusion Prevention System (IPS)?
- RADIUS server
- CSU/DSU
- NGFW
- Proxy server
- Which of the following is a device that switches calls between endpoints on the local IP network and provides access to external Internet lines?
- VoIP PBX
- VoIP gateway
- VoIP endpoint
- Multilayer switch
- Which of the following statements about Internet access through a proxy server accounts for the security against outside intrusion that a proxy provides?
- The proxy server uses a public IP address, and the client computers use private addresses.
- The proxy server uses a private IP address, and the client computers use public addresses.
- Both the proxy server and the client computers use private IP addresses.
- Both the proxy server and the client computers use public IP addresses.
- Which of the following statements about proxy servers and NAT servers are true? (Choose all that apply.)
- NAT servers and proxy servers can both provide Internet access to clients running any application.
- NAT servers and proxy servers both use public IP addresses.
- NAT servers and proxy servers both access Internet servers and relay the responses to network clients.
- Both NAT servers and proxy servers cache web data for later use.
- A multilayer switch can operate at which layers of the Open Systems Interconnection (OSI) model? (Choose all that apply.)
- Physical
- Data link
- Network
- Transport
- Session
- Presentation
- Application
- Which of the following devices can an administrator use to monitor a network for abnormal or malicious traffic?
- IDS
- UPS
- RADIUS
- DoS
- RAS
- Which of the following is not a function that is typically provided by a unified threat management (UTM) appliance?
- Virtual private networking
- Network firewall
- Packet forwarding
- Antivirus protection
- Which of the following features enables an Intrusion Detection System (IDS) to monitor all of the traffic on a switched network?
- Stateful packet inspection
- Port mirroring
- Trunking
- Service-dependent filtering
- Which of the following network devices does not employ Access Control Lists (ACLs) to restrict access?
- Routers
- Hubs
- Switches
- Wireless Access Points (WAPs)
- Which of the following TCP/IP parameters, configured on an end system, specifies the Internet Protocol (IP) address of a router on the local network that provides access to other networks?
- WINS Server Addresses
- Default Gateway
- DNS Server Addresses
- Subnet Gateway
- Which of the following routing protocols uses the packet format shown in the figure?

- RIPv1
- RIPv2
- OSPF
- EIGRP
- BGP
- Which of the following statements about the Enhanced Interior Gateway Routing Protocol (EIGRP) is not true?
- EIGRP does not support classless IPv4 addresses.
- EIGRP is a hybrid routing protocol.
- EIGRP can only transmit incremental routing table updates.
- EIGRP shares routes within an autonomous system.
- Which of the following are techniques used in traffic shaping to prevent networks from being overwhelmed by data transmissions? (Choose all that apply.)
- Bandwidth throttling
- Rate limiting
- Broadcast storming
- Network Address Translation (NAT)
- Which of the following terms refers to methods by which network traffic is prioritized to prevent applications from suffering faults due to network congestion?
- Port forwarding
- Dynamic routing
- VLANs
- QoS
- Which of the following statements about Routing Information Protocol version 1 (RIPv1) is true? (Choose all that apply.)
- RIPv1 broadcasts the entire contents of the routing table every 30 seconds.
- RIPv1 advertises the subnet mask along with the destination network.
- RIPv1 broadcasts only the elements in the routing table that have changed every 60 seconds.
- RIPv1 does not include the subnet mask in its network advertisements.
- Which of the following mechanisms for prioritizing network traffic uses a 6-bit classification identifier in the Internet Protocol (IP) header?
- Diffserv
- CoS
- Traffic shaping
- QoS
- Administrative distance
- Which of the following statements about static routing are true? (Choose all that apply.)
- Static routes are manually configured routes that administrators must add, modify, or delete when a change in the network occurs.
- Static routes are automatically added to the routing table by routing protocols when a new network path becomes available.
- Static routes adapt to changes in the network infrastructure automatically.
- Static routes are a recommended solution for large internetworks with redundant paths to each destination network.
- Static routes are a recommended solution for small internetworks with a single path to each destination network.
- Which of the following TCP/IP routing protocols does not include the subnet mask within its route update messages, preventing it from supporting subnetting?
- Routing Information Protocol, version 1 (RIPv1)
- Routing Information Protocol, version 2 (RIPv2)
- Border Gateway Protocol (BGP)
- Open Shortest Path First (OSPF)
- Which of the following terms refers to a routing protocol that does not rely on hop counts to measure the efficiency of routes?
- Interior gateway protocol
- Edge gateway protocol
- Distance vector protocol
- Link state protocol
- What is the maximum number of routes that can be included in a single RIP broadcast packet?
- 20
- 25
- 32
- Unlimited
- Which of the following routing protocols can you use on a TCP/IP internetwork with segments running at different speeds, making hop counts an inaccurate measure of route efficiency? (Choose all that apply.)
- Enhanced Interior Gateway Routing Protocol (EIGRP)
- Routing Information Protocol (RIP)
- Open Shortest Path First (OSPF)
- Border Gateway Protocol (BGP)
- Which of the following statements about the Open Shortest Path First (OSPF) routing protocol are true? (Choose all that apply.)
- OSPF is an interior gateway protocol.
- OSPF is a link state routing protocol.
- OSPF does not support Classless Inter-Domain Routing (CIDR).
- OSPF shares routes within an autonomous system.
- What is the term for the process by which dynamic routing protocols update other routers with routing table information?
- Convergence
- Distance vectoring
- Redistribution
- Dissemination
- Which of the following TCP/IP routing protocols measures the efficiency of routes by the number of hops between the source and the destination?
- Routing Internet Protocol (RIP)
- Open Shortest Path First (OSPF)
- Border Gateway Protocol (BGP)
- Intermediate System to Intermediate System (IS-IS)
- Which of the following types of routing protocols route datagrams between autonomous systems?
- EGP
- RIP
- IGP
- OSPF
- Which of the following prevents packets on a TCP/IP internetwork from being transmitted endlessly from router to router?
- Open Shortest Path First (OSPF)
- Maximum Transmission Unit (MTU)
- Administrative distance
- Time to Live (TTL)
- Which of the following command-line tools can you use to create and modify static routes on a Unix or Linux system? (Choose all that apply.)
routeifconfigtracerouteip
- Routers that use the Open Shortest Path First (OSPF) routing protocol calculate the relative costs of routes through the network by exchanging which of the following specifications for each interface with other routers?
- Transmission speed
- Data link layer protocol
- Network medium
- IP address
- Which of the following statements about the Border Gateway Protocol (BGP) is not true?
- BGP is an exterior gateway protocol.
- BGP is a link state routing protocol.
- BGP supports Classless Inter-Domain Routing (CIDR).
- BGP shares routes among autonomous systems.
- In an IPv4 routing table, what is the network destination address for the host system's default route?
- 0.0.0.0
- 127.0.0.0
- 127.255.255.255
- 255.255.255.255
- Which of the following routing protocols uses the packet format shown in the figure?
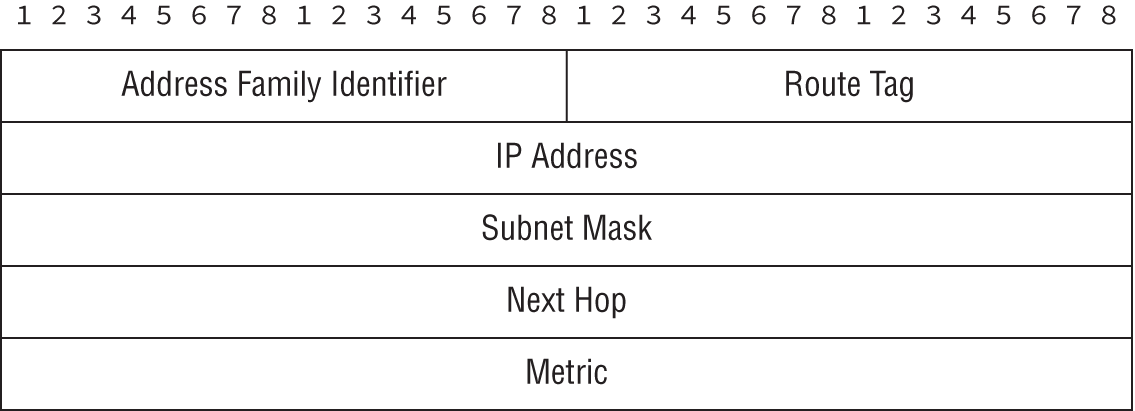
- RIPv1
- RIPv2
- OSPF
- EIGRP
- BGP
- Which of the following routing protocols has both interior and exterior designations, based on whether it is used for routing within an autonomous system or on the Internet?
- RIP
- OSPF
- EIGRP
- BGP
- Which of the following network layer protocols includes a Time to Live (TTL) field? (Choose all that apply.)
- IPv4
- IPv6
- ICMP
- IGMP
- Which of the following is not a method of traffic shaping?
- Rate limiting
- WAN optimization
- Bandwidth throttling
- Self-limiting
- An enterprise network has been designed with individual departmental switches because, in most cases, the devices in a specific department exchange network traffic with other devices in the same department. Each of the departmental switches is also connected to a host switch, which enables devices to communicate with other departments. Which of the following terms describes this switching architecture?
- Distributed switching
- Port forwarding
- Traffic shaping
- Neighbor discovery
- Flow control
- Review the following figure. Note that each store-and-forward switch has three connected node ports and one port for switch-to-switch connections. All node ports and links are configured for half-duplex communication. The switch-to-switch links are configured for full-duplex communication. Which of the following statements about the switched network is true?

- There are nine collision domains, one for each half-duplex connection.
- There are 12 collision domains, one for each switch connection.
- There are three collision domains, one for each switch-to-switch connection.
- There is one collision domain for this network.
- Which of the following could be a valid MAC address for a network interface adapter?
- 10.124.25.43
- FF:FF:FF:FF:FF:FF
- 00:1A:6B:31:9A:4E
- 03:AE:16:3H:5B:11
- fe80::89a5:9e4d:a9d0:9ed7
- Which of the following protocols prevents network switching loops from occurring by shutting down redundant links until they are needed?
- RIP
- STP
- VLAN
- NAT
- ARP
- Which of the following cable types can be used to connect an MDI port on a workstation to an Auto-MDI-X port on an Ethernet switch? (Choose all that apply.)
- A crossover twisted pair cable
- A straight-through twisted pair cable
- A coaxial cable
- A single-mode fiber optic cable
- A multimode fiber optic cable
- Which of the following is a network layer protocol that uses ICMPv6 messages to locate routers, DNS servers, and other nodes on an IPv6 network?
- BGP
- NDP
- OSPF
- PoE
- Which of the following is a protocol that identifies VLANs by inserting a 32-bit field in the Ethernet frame?
- IEEE 802.1P
- IEEE 802.1Q
- IEEE 802.1X
- IEEE 802.1AB
- IEEE 802.1AX
- Each of the following Carrier-Sense Multiple Access with Collision Detection (CSMA/CD) events occurs on an Ethernet network when two stations transmit simultaneously, although not in the order listed. Which of the following events occurs immediately after the collision?
- The two stations observe a random backoff interval.
- The two stations transmit a jam signal.
- The two stations stop transmitting.
- The two stations listen to see if the channel is idle.
- The two stations begin retransmitting their frames.
- For the Carrier-Sense Multiple Access with Collision Detection (CSMA/CD) mechanism to function properly on an Ethernet network, host systems must be able to detect when a collision occurs, so they can react to it. Which of the following cabling errors can prevent the collision detection process from functioning properly?
- Excessively long cable segments
- Incorrect wiring pinouts
- Too many systems on a single network
- An excessive number of collisions
- When a packet collision between two systems occurs on an Ethernet network, Carrier-Sense Multiple Access with Collision Detection (CSMA/CD) causes the two systems to stop transmitting and generate a jam signal. After sending the jam signal, why do the two systems wait for a randomized backoff interval before retransmitting their packets?
- They need time to reassemble the packets.
- To prevent another collision from occurring.
- They need to rebuffer the packet.
- To recalculate the packets’ checksum values.
- Which of the following devices is used to physically connect computers in the same VLAN?
- A bridge
- A hub
- A switch
- A router
- Which of the following statements is true about an Ethernet network that uses CSMA/CD?
- Collisions are a normal occurrence.
- Collisions never occur unless there is a network fault.
- Collisions cause data to be irretrievably lost.
- Collisions are the result of duplicate IP addresses.
- Which of the following is an abnormal occurrence on an Ethernet network?
- Packet retransmissions
- Collision detection
- Jam signals
- Late collisions
- VLANs create the administrative boundaries on a switched network that are otherwise provided by which of the following devices?
- Hubs
- Routers
- Domains
- Bridges
- Which of the following statements about VLANs are true? (Choose all that apply.)
- All of the devices in a particular VLAN must be physically connected to the same switch.
- A VLAN creates a limited broadcast domain on a switched network.
- You must have VLANs on a switched network for communication between computers on different cable segments to occur.
- A router is required for communication between VLANs.
- Which of the following elements can be used to identify the devices in a particular VLAN? (Choose all that apply.)
- Hardware addresses
- IP addresses
- DNS names
- Switch port numbers
- Alice has a network that consists of three Virtual LANs (VLANs) defined on all of the network's switches. VLAN 10 is the Sales VLAN, VLAN 20 is the Marketing VLAN, and VLAN 30 is the Accounting VLAN. Users are reporting that they cannot communicate with anyone outside of their own VLANs. What is the problem, and what must Alice do?
- The problem is a faulty VLAN configuration on one of the switches. Alice needs to re-create the VLANs and configure each VLAN for routing.
- One of the VLANs is configured to filter all other VLAN traffic for security purposes. Alice needs to change the filter on this VLAN.
- VLANs are limited to data link layer communication only. To allow communication between VLANs, Alice must add a router or a layer 3 switch to the network and configure it to route traffic between the VLANs.
- The VLANs are using different data link layer protocols. VLANs must use the same data link layer protocol in order to communicate.
- The jumbo frame capability is associated with which layer of the Open Systems Interconnection (OSI) model?
- Application
- Transport
- Network
- Data link
- Which of the following technologies would you be less likely to find on the average home or small office network? (Choose all that apply.)
- NAT
- DHCP
- 10GBase-T
- VLAN
- Which of the following modifications occur when you configure the native Virtual Local Area Network (VLAN) on your network switches to use 802.1q tagging? (Choose all that apply.)
- Double-tagged packets are prevented.
- BPDU guards are applied.
- Root guards are applied.
- Trunk traffic is routed, not switched.
- Which of the following protocols is responsible for inserting the tags into frames that enable switches to forward them to the appropriate Virtual Local Area Network (VLAN)?
- IEEE 802.3x
- IEEE 802.1X
- IEEE 802.1q
- IEEE 802.11ac
- Which of the following best explains how tagging the native Virtual Local Area Network (VLAN) traffic can improve in-band switch management security?
- By renaming the default VLAN
- By preventing double-tagged packets
- By encrypting in-band management traffic
- By moving in-band management traffic off the native VLAN
- A switch with auto-medium-dependent interface crossover (MDI-X) ports eliminates the need for which of the following?
- 8P8C connectors
- Switch-to-switch connections
- Straight-through cables
- Crossover cables
- Which of the following cable types is needed to connect an MDI port on a workstation to an MDI-X port on an Ethernet switch?
- A crossover twisted pair cable
- A straight-through twisted pair cable
- A coaxial cable
- A single-mode fiber optic cable
- A multimode fiber optic cable
- Port security on an Ethernet switch is implemented through the use of which of the following methods?
- Blacklisted MAC addresses
- Whitelisted MAC addresses
- Port-by-port MAC address filtering
- Spoofed MAC addresses
- Which of the following best explains why networks using Voice over IP (VoIP) often have separate voice and data Virtual Local Area Networks (VLANs)?
- To prevent voice and data packet conflicts
- To encrypt voice traffic
- To encrypt data traffic
- To prioritize voice traffic
- Which of the following protocols uses a form of flow control called the sliding window technique?
- UDP
- HTTP
- TCP
- DNS
- Which of the following Power over Ethernet (PoE) specifications supplies power to devices using the spare wire pair on a 10Base-T or 100Base-TX twisted pair network?
- Alternative A
- Alternative B
- 4PPoE
- All of the above
- Which of the following best describes the process of whitelisting on a wireless network?
- Using an Access Control List (ACL) to specify the IP addresses that are permitted to access a wireless network
- Using port protection to specify the well-known port numbers of applications that users are permitted to run over a wireless network
- Using MAC filtering to create a list of devices that are permitted to access a wireless network
- Using an AAA server to create a list of users that are permitted to access a wireless network
- Which of the following features helps to protect network switches from attacks related to the Spanning Tree Protocol (STP)? (Choose all that apply.)
- BPDU guard
- Root guard
- DHCP snooping
- Geofencing
- Which of the following IEEE standards calls for the use of the Carrier-Sense Multiple Access with Collision Avoidance (CSMA/CA) Media Access Control (MAC) mechanism?
- 802.11ac
- 802.1X
- 802.3
- All of the above
- Which of the following topologies enables wireless devices to access resources on a wired network?
- Ad hoc
- Star
- Infrastructure
- Bus
- Which of the following components are required for two computers to communicate using an IEEE 802.11 wireless LAN in an ad hoc topology?
- A router connected to the Internet
- A Wireless Access Point (WAP)
- An external antenna
- None of the above
- Which of the following wireless networking technologies will never experience interference from a 2.4 GHz wireless telephone? (Choose all that apply.)
- IEEE 802.11a
- IEEE 802.11b
- IEEE 802.11g
- IEEE 802.11n
- IEEE 802.11ac
- IEEE 802.11ax
- Which of the following wireless networking standards is capable of supporting speeds of 54 Mbps and is also backward compatible with IEEE 802.11b?
- IEEE 802.11a
- IEEE 802.11g
- IEEE 802.11n
- Bluetooth
- IEEE 802.11
- Which of the following wireless LAN standards include the ability to use Multiple Input, Multiple Output (MIMO) antennae? (Choose all that apply.)
- IEEE 802.11a
- IEEE 802.11b/g
- IEEE 802.11n
- IEEE 802.11ac
- IEEE 802.11ax
- Which of the following is a cellular communication technology that is virtually obsolete in the United States?
- GSM
- CDMA
- TDMA
- LTE
- Which of the following IEEE wireless LAN standards uses the Direct Sequence Spread Spectrum (DSSS) signal modulation technique?
- 802.11a
- 802.11b
- 802.11g
- 802.11n
- 802.11ac
- When designing a wireless LAN installation, which of the following are valid reasons to install a unidirectional antenna in an Access Point (AP), rather than an omnidirectional one? (Choose all that apply.)
- The AP will be located against an outside wall.
- There are many interior walls between the AP and the most distant workstation.
- A unidirectional antenna can be focused to a specific signal pattern width.
- All of the above
- How do wireless networking devices conforming to the IEEE 802.11n and 802.11ac standards achieve transmission speeds greater than 72.2 Mbps?
- By using direct sequence spread spectrum (DSSS) modulation
- By using multiple antennae to transmit several data streams simultaneously
- By using frequencies in the 5 GHz band
- By sacrificing transmission range for speed
- Which of the following are possible reasons why the 5 GHz frequency tends to perform better than the 2.4 GHz frequency on a wireless LAN? (Choose all that apply.)
- The 5 GHz frequency has more channels than the 2.4 GHz frequency.
- The 5 GHz frequency supports longer ranges than the 2.4 GHz frequency.
- The 5 GHz frequency conflicts with fewer common household devices than the 2.4 GHz frequency.
- The 5 GHz frequency transmits at faster speeds than the 2.4 GHz frequency.
- Alice is attempting to deploy an IEEE 802.11b/g wireless LAN on the fifth floor of a 10-story office building that is surrounded on all sides by other office buildings, all of which seem to be running many wireless LANs. Scanning the 2.4 GHz band, she sees literally dozens of networks, spread across all of the available channels. As a result, her wireless devices have trouble connecting to their Access Point (AP), and when they do, they achieve only low speeds. Which of the following tasks should Alice perform to enable the wireless clients to connect to the network more reliably? (Choose two.)
- Upgrade all of the wireless network devices to IEEE 802.11n.
- Configure all of the network devices to use WPA2 encryption with AES.
- Configure the wireless devices to use the 5 GHz band.
- Configure the AP to suppress SSID broadcasts.
- Upgrade all of the network devices to the latest firmware.
- Which of the following is the fastest speed achievable by a wireless LAN using the currently ratified IEEE 802.11 standards?
- 54 Mbps
- 600 Mbps
- 1.3 Gbps
- 2.6 Gbps
- What is the term for the technology implemented in the IEEE 802.11ac standard that enables a wireless device to transmit multiple frames to multiple clients simultaneously?
- MIMO
- Channel bonding
- CSMA/CA
- MU-MIMO
- On an IEEE 802.11b/g/n wireless network running at 2.4 GHz with multiple Access Points (APs), the traditional best practice is to use channels 1, 6, and 11, with no two adjacent APs configured to use the same channel. Which of the following is the real reason why this is a good plan?
- Channels 1, 6, and 11 are the only channels with frequencies that do not overlap.
- Channels 1, 6, and 11 have more bandwidth than the other channels.
- Channels 1, 6, and 11 have greater ranges than the other channels.
- Channels 1, 6, and 11 are the default settings on most wireless devices.
- Ralph is planning a wireless LAN installation for a warehouse with two offices at either end of the building, approximately 300 feet apart. If he installs a single Access Point (AP) in the center of the warehouse, equidistant from the two offices, which of the following standards should he look for when purchasing hardware so that workstations in both offices will be able to connect to the network at the best possible speed?
- IEEE 802.11a
- IEEE 802.11g
- IEEE 802.11n
- IEEE 802.11ac
- Which of the following terms defines a wireless LAN transmission technique in which devices use multiple antennae to increase transmission speeds?
- MIMO
- TDMA
- PAN
- Ant+
- What is the maximum channel width possible using wireless networking equipment based on the ratified IEEE 802.11 regulatory standards?
- 20 MHz
- 40 MHz
- 80 MHz
- 160 MHz
- Which of the following wireless networking standards are capable of using only the 5 GHz frequency? (Choose all that apply.)
- IEEE 802.11a
- IEEE 802.11b
- IEEE 802.11g
- IEEE 802.11n
- IEEE 802.11ac
- Which of the following IEEE wireless LAN standards provides the greatest possible throughput?
- 802.11a
- 802.11ac
- 802.11b
- 802.11g
- 802.11n
- Which of the following IEEE 802.11 wireless LAN standards are capable of supporting both the 2.4 GHz and 5 GHz frequencies?
- 802.11a
- 802.11b
- 802.11g
- 802.11n
- 802.11ac
- What is the maximum number of transmit and receive antennae supported by the currently ratified IEEE 802.11 wireless LAN standards?
- 2
- 4
- 8
- 16
- Which of the following is the term for the network name that you use to connect a client device to an Access Point (AP) on a wireless LAN?
- BSS
- ESS
- SSID
- BSSID
- Which of the following IEEE wireless LAN standards define devices with a maximum aggregate channel width of 20 MHz? (Choose all that apply.)
- 802.11a
- 802.11g
- 802.11n
- 802.11ac
- At which layer of the Open Systems Interconnection (OSI) model do wireless range extenders operate?
- Physical
- Data link
- Network
- Transport
- Session
- Presentation
- Application
- Which of the following wireless security protocols provides the greatest degree of network device hardening?
- WEP
- WPA
- WPA2
- EAP
- Which of the following encryption protocols was introduced in the WiFi Protected Access (WPA) wireless security standard?
- CCMP-AES
- TKIP-RC4
- EAP-TLS
- TACACS+
- TKIP-RC4 is an encryption protocol used with which of the following wireless network security standards?
- WEP
- WPA
- WPA2
- EAP
- Which of the following protocols provides wireless networks with the strongest encryption?
- AES
- TKIP
- EAP
- 802.1X
- When the WiFi Protected Access (WPA) wireless security protocol was released to replace Wired Equivalent Privacy (WEP), it included the Temporal Key Integrity Protocol (TKIP) for encryption. Which of the following is not one of the improvements that WPA and TKIP provide over WEP?
- TKIP enlarges the WEP encryption key.
- TKIP modifies the encryption key for every packet.
- WPA does not require a hardware upgrade for WEP devices.
- TKIP eliminates the use of Pre-Shared Keys (PSKs).
- To connect a wireless client to a Wireless Access Point (WAP) using the WiFi Protected Access II (WPA2) security protocol with a Pre-Shared Key (PSK), which of the following must you supply on both devices?
- Base key
- Passphrase
- Serial number
- MAC address
- Upgrading a wireless network from the Wired Equivalent Privacy (WEP) security protocol to WiFi Protected Access (WPA) enables it to use the Temporal Key Integrity Protocol (TKIP) for encryption, which generates a unique key for each packet. Which of the following types of attacks does this capability prevent?
- Denial-of-Service (DoS) attacks
- Brute-force attacks
- Replay attacks
- Deauthentication attacks
- Which of the following wireless security protocols uses CCMP-AES for encryption?
- WEP
- WPA
- WPA2
- TKIP
- Which of the following was the first wireless LAN security protocol to come into common usage?
- WEP
- WPA
- WPA2
- TKIP
- Which of the following did the second version of the WiFi Protected Access (WPA) protocol add to the standard?
- CCMP-AES
- MIMO
- WEP
- TKIP
- You are setting up a wireless LAN in a friend's home, using devices that conform to the IEEE 802.11g standard. You have installed and successfully tested the devices on an open network, and now you are ready to add security. Which of the following protocols should you choose to provide maximum security for the wireless network?
- WEP
- WPA2
- IPsec
- TLS
- L2TP
- CCMP-AES is an encryption protocol used with which of the following wireless network security standards?
- WEP
- WPA
- WPA2
- EAP
- Which of the following encryption protocols was introduced in the WiFi Protected Access II (WPA2) wireless security standard?
- CCMP-AES
- TKIP-RC4
- EAP-TLS
- TACACS+
- Which of the following wireless security protocols can enable network users to authenticate using smartcards?
- WEP
- WPA2
- EAP
- AES
- Which of the following forms of the WiFi Protected Access (WPA) and WPA2 protocols require a RADIUS server? (Choose all that apply.)
- WPA-Personal
- WPA-PSK
- WPA-Enterprise
- WPA-802.1X
- Which of the following forms of the WiFi Protected Access (WPA) and WPA2 protocols call for the use of a Pre-Shared Key (PSK)?
- WPA-Personal
- WPA-Enterprise
- WPA-EAP
- WPA-802.1X
- Which of the following stream ciphers does the Temporal Key Integrity Protocol (TKIP) use for encryption on a wireless network?
- RC4
- AES
- CCMP
- SHA
- Which of the following wireless security protocols uses CCMP for encryption?
- WEP
- WPA
- WPA2
- 802.1X
- CCMP is based on which of the following encryption standards?
- TKIP
- RC4
- AES
- 802.1X
- You have installed a new Wireless Access Point (WAP) on your network and configured it to use an SSID that is not broadcasted and WPA2 for security. Which of the following describes what you must do to configure your wireless clients?
- Select the SSID from a list and allow the client to automatically detect the security protocol.
- Select the SSID from a list and then select WPA2 from the security protocol options provided.
- Type the SSID manually and allow the client to automatically detect the security protocol.
- Type the SSID manually and then select WPA2 from the security protocol options provided.
- Which of the following wireless LAN security protocols was rendered obsolete after it was found to be extremely easy to penetrate?
- WEP
- WPA
- WPA2
- EAP
- Which of the following protocols does the WiFi Protected Access (WPA) security protocol use for encryption?
- AES
- TKIP
- MD5
- SHA
- Which of the following wireless network security protocols provides open and shared key authentication options?
- WPA
- WEP
- WPA2
- EAP
- Which of the following wireless security protocols uses TKIP for encryption?
- WEP
- WPA
- WPA2
- AES
- Which of the following is not a factor that weakens the security of the Wired Equivalent Privacy (WEP) protocol used on early IEEE 802.11 wireless LANs?
- 40-bit encryption keys
- 24-bit initialization vectors
- Static shared secrets
- Open System Authentication
- Which of the following encryption ciphers was replaced by CCMP-AES when the WPA2 wireless security protocol was introduced?
- EAP
- WEP
- TKIP
- CCMP
- Which of the following wireless security protocols was substantially weakened by its initialization vector?
- WPA
- WEP
- WPA2
- PEAP
- Ralph is installing a wireless LAN that includes three Access Points (APs) to provide coverage for a large building. Which of the following must Ralph do to ensure that users are able to roam without interruption from one AP to another using their portable devices? (Choose all that apply.)
- Configure each AP with the same IP address.
- Configure each AP with the same security passphrase.
- Configure each AP to use the same security protocol.
- Configure each AP with the same SSID.
- Which of the following is the maximum theoretical download speed for a 5G cellular network?
- 42 megabits per second
- 150 megabits per second
- 1 gigabit per second
- 10 gigabits per second
- 100 gigabits per second
- Which of the following statements about 5G cellular networks are true? (Choose all that apply.)
- 5G networks can operate on three frequency bands.
- 5G networks with the highest speeds also have a more limited range.
- 4G devices can connect to 5G networks at reduced speeds.
- On a 5G network, the lower frequency bands provide the highest speeds.
- Which of the following IEEE standards describes an implementation of port-based access control for wireless networks?
- 802.11ac
- 802.11n
- 802.1X
- 802.3x
- Unauthorized users are connecting to your Wireless Access Point (WAP) and gaining access to the network. Which of the following are steps you can take to prevent this from happening? (Choose all that apply.)
- Disable SSID broadcasting.
- Use Kerberos for authentication.
- Place the Access Point (AP) in a DMZ.
- Implement MAC address filtering.
- On a Wireless Access Point (WAP) that uses an Access Control List (ACL) to specify which devices are permitted to connect to the network, which of the following is used to identify the authorized devices?
- Usernames
- IP addresses
- Device names
- MAC addresses
- On a network carrying both voice and data traffic, separate Virtual Local Area Networks (VLANs) enable the voice traffic to be assigned a higher priority than the data traffic. Which of the following are methods for identifying the packets carrying voice traffic, so the switches can assign them to the voice VLAN? (Choose all that apply.)
- MAC addresses
- VLAN tags
- IP addresses
- DNS names
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
