Chapter 15
Physical Security and Risk
THE FOLLOWING COMPTIA NETWORK+ EXAM OBJECTIVES ARE COVERED IN THIS CHAPTER:
- 1.1 Explain the functions and applications of various network devices
- IDS/IPS
- 2.4 Explain the importance of implementing network segmentation
- Honeypot/honeynet
- 3.1 Compare and contrast risk-related concepts
- Disaster recovery
- Business continuity
- Battery backups/UPS
- First responders
- Data breach
- End user awareness and training
- Single point of failure
- Critical nodes
- Critical assets
- Redundancy
- Adherence to standards and policies
- Vulnerability scanning
- Penetration testing
- 3.4 Compare and contrast physical security controls
- 3.5 Given a scenario, install and configure a basic firewall
- Types of firewalls
- Host-based
- Network-based
- Software vs hardware
- Application aware/context aware
- Small office/home office firewall
- Stateful vs stateless inspection
- UTM
- Settings/techniques
- ACL
- Virtual wire vs routed
- DMZ
- Implicit deny
- Block/allow
- Outbound traffic
- Inbound traffic
- Firewall placement
- Internal/external
- Types of firewalls
Finding a corporate network that isn't connected to the Internet would be pretty tough these days. Being connected allows for a huge increase in productivity, and not having an online presence is akin to sheer oblivion in today's business environment. But as is often the case, advantages, even big ones, have a downside to them, and being hooked up to the Internet is no exception. Connecting our private networks to a huge public one exposes us to some really major security risks, so we absolutely have to protect our networks from the very real threats of intrusion, corporate espionage, data and identity theft, and exploitation in general. To succeed, we need to make sure our networks have one or more security devices to control any traffic coming into and flowing out from them. We need things like firewalls and intrusion detection and/or prevention systems as much as we need any other form of security in our businesses and daily lives today—period.
These vital security methods are going to be the focus of this chapter. In it, I'll be covering the ins and outs of the protective networking measures and devices designed to shield and secure our network traffic, zooming in on the all-important firewalls because they're a ubiquitous and critical line of defense against the exploits of the all-too-common hackers who seek to compromise our corporate and personal network security.
I'll end this important chapter by going over the specific issues that can and do affect device security on your network. I'll discuss things you can do physically and logically to implement tight security, right down to choosing the best protocols to use for safe communication to the outside world.

To find up-to-the-minute updates for this chapter, please see www.lammle.com/networkplus or the book's website at www.sybextestbanks.wiley.com.
Using Hardware and Software Security Devices
This heading may be a little misleading because it makes it sound like I'm going to discuss the differences between hardware and software security devices. But I'm not, because even though many firewalls and routers that contain proxy and/or firewall services brand themselves as hardware or software solutions, the fact is, most of these devices are really a combination of the two. For instance, there's software embedded within a hardware ROM chip to make the software harder to attack, but it still actually functions as software. So instead of focusing on the type of device, it makes a lot more sense to delve into exactly what it is that a device does and how it does it.
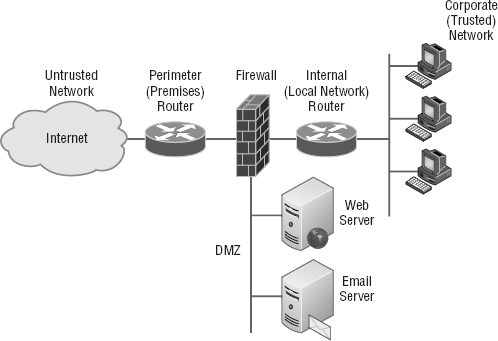
In medium to large enterprise networks, strategies for security usually include some combination of internal and perimeter routers plus firewall devices. Internal routers provide added security by screening traffic to the more vulnerable parts of a corporate network through a wide array of strategic access lists. You can see where each of these devices is found within a typical network in Figure 15.1.
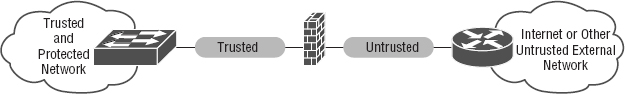
I'll use the terms trusted network and untrusted network throughout this chapter, so it's important that you can see where they are found in a typical secured network. The demilitarized zone (DMZ) can be global (real) Internet addresses or private addresses, depending on how you configure your firewall, but this is typically where you'll find the HTTP, Domain Name Service (DNS), email, and other Internet-type corporate servers. The DMZ is used to create a security zone that allows public traffic but the traffic is isolated from the company private network.
Instead of having routers, we can also use virtual local area networks (VLANs) with switches on the inside trusted network. Multilayer switches containing their own security features can sometimes replace internal (LAN) routers to provide higher performance in VLAN architectures.
Next, I'll show you how these devices go about directing traffic between your private network that only authorized users have access to and the public network part of the network that everyone connects to.
Defining Firewalls
Firewalls are usually a combination of hardware and software. The hardware part is usually a router, but it can also be a computer or a dedicated piece of hardware called a black box that has two Network Interface Cards (NICs) in it. One of the NICs connects to the public side, and the other one connects to the private side. The software part is configured to control how the firewall actually works to protect your network by scrutinizing each incoming and outgoing packet and rejecting any suspicious ones.
Firewalls generally allow only packets that pass specific security restrictions to get through; they can also permit, deny, encrypt, decrypt, and proxy all traffic that flows through, either between the public and private parts of a network or between different security domains, or zones, on a private network. The system administrator decides on and sets up the rules a firewall follows when deciding to forward data packets or reject them.

Just so you know, a Network+ certified system administrator rarely has the sophisticated knowledge required to design, install, and manage a firewall. The information I'm imparting to you here will give you the tools you need to understand the basic ways firewalls work and to help you to work effectively in an environment where a firewall is already installed.
Firewalls can be placed on top of an existing operating system or be self-contained. Conversely, black-box systems are proprietary and have external controls that aren't controlled by the operating system itself. If you opt to use a general-purpose server operating system to run your firewall, you can do that with Unix and Windows because both support third-party firewall products.

For networks with multiple Windows-based computers, firewalls should be installed on a router that connects the private network to the Internet or to a Windows server like Windows Server 2008 or newer rather than on clients like Windows 7 or 8.
Clearly, if your firewalls aren't configured properly, they're not going to do you much good. Most of them are configured as default-deny, meaning that the only network connections allowed are the ones that have been specified to be permitted. A proficient system administrator has to do this, and trust me, with the multitude of applications and ports involved in internal-external network communication, it's not all that easy! To make life easier, some people resort to trusting the default-allow option, where all traffic is allowed to pass through unless it's been specifically blocked. But doing this isn't exactly tight because it makes inadvertent network connections and security breaches much more likely to happen. Even though it might ease a little administrative pain, I don't recommend going with this method—ever.
Network-Based Firewalls
A network-based firewall is what companies use to protect their private network from public networks. The defining characteristic of this type of firewall is that it's designed to protect an entire network of computers instead of just one system, and it's usually a combination of hardware and software.
As you can imagine, protecting an entire network of computers from malicious attacks is quite the challenge. Most of the firewall features that I'm going to cover in this chapter are designed with this goal in mind, although the technology is certainly applicable to host-based firewalls too.

In many small office, home office (SOHO) networks, a firewall with somewhat less sophistication may be used. While not providing all of the functionality of an enterprise firewall, these devices, may be easier to configure and can still be deployed safely.
Host-Based Firewalls
In contrast to a network-based firewall, a host-based firewall is implemented on a single machine, so it protects only that one machine. This type of firewall is usually a software implementation because you don't need any additional hardware in your personal computer to run it. All current Windows client operating systems come with Windows Firewall, which is a great example of a host-based solution.
If you hear someone say that host-based software solutions just aren't as secure as a separate hardware-based solution, they're pretty much right. This is because if you're running a dedicated black-box firewall and someone manages to hack in and disable it, your best-case scenario is a blown black box and a ruined firewall. Believe it or not, even if that happens, all the data on your internal network may still be safe if the bad guy wasn't able to get past everything. But if they were able to get all the way in, you could have some ugly consequences to deal with; if the hacker makes it through the often relatively flimsy software firewall running on your local computer, they could not only view and/or nick your files but also trash your entire system—yikes!
Still, it all comes down to how much security you really require. Unless you're the director of the CIA or something, you probably don't need to go the extra mile and shell out for a dedicated black box if all you want to do is protect your personal computer from someone who's trying to hack their way in through your high-speed Internet connection.
Firewall Technologies
There's a whole bunch of firewall technologies, and they all differ in the way that they restrict information flow. Things like access control lists and dynamic packet filtering are often used as firewalls in their own right, or they can be implemented along with proxies, DMZs, and other firewall technologies to build a serious, formidable system fortress.
Access Control Lists
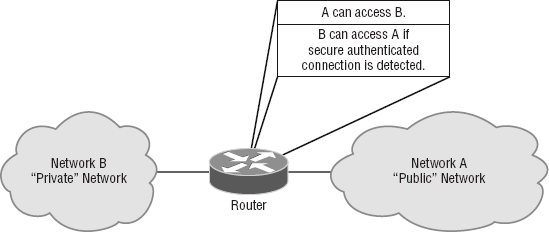
The first line of defense for any network that's connected to the Internet is what we call access control lists (ACLs). These reside on your routers and determine by IP addresses which machines are allowed to use those routers and in what direction. ACLs have been around for decades and have some other really cool uses apart from being used as firewalls. Figure 15.2 gives you a great demonstration of how ACLs can work to prevent users on Network B from accessing Network A. Network A, however, hosts from Network B and can access Network A if a secure authenticated connection is used.
An important thing to note here is that data from users in Network A can still pass through the router into Network B. This means that a hacker executing an IP spoofing attack that makes it appear as though they're an IP address originating from inside the firewall can still gain access to Network B by pretending to be a valid user in Network A.
ACLs are essentially lists of conditions that categorize packets, so you can imagine how helpful they can be in helping you gain control over the network's traffic. One of the most common and easiest-to-understand ways that ACLs are used is for filtering unwanted packets when you're implementing security policies. You can set up the ACLs to make very specific decisions about regulating traffic patterns so that they'll allow only certain hosts to access web resources on the Internet while restricting others. With a solid combination of ACLs, network managers can arm themselves like Rambo and powerfully enforce pretty much any security policy they need to.
Chapter 14 discussed some of the security threats that ACLs can help mitigate:
- IP address spoofing, inbound
- IP address spoofing, outbound
- Denial of service (DoS) TCP SYN attacks
- DoS Smurf attacks
The following techniques can be used to mitigate these security threats:
- Using TCP intercept to address DoS TCP SYN attacks
- Filtering ICMP messages, inbound
- Filtering ICMP messages, outbound
- Filtering Traceroute
You can even employ ACLs for situations that don't necessarily involve blocking packets—like using them to control which networks will or won't be advertised by dynamic routing protocols. The way you configure your ACL to do that is the same; you just apply it to a routing protocol instead of an interface. The only other difference here is that an ACL applied to a protocol is referred to as a distribution list, and it doesn't stop routing advertisements, it just controls their content. You can also use ACLs to categorize and queue packets for applications that require quality of service (QoS) and for controlling the types of traffic that can activate a pricey backup link.
So, how do you go about creating an ACL? Well, it's really a lot like programming a series of if-then statements: If a given condition is met, then a specific action happens; but if that explicit condition isn't met, nothing happens except that the next statement in the list is evaluated. Access-list statements are basically packet filters that packets are compared against, categorized by, and then acted on accordingly as directed. Once your list is built, it can be applied to either inbound or outbound traffic on any interface, causing the router to analyze every packet crossing that interface in the specified direction and take the appropriate action.
There are a few important rules by which packets are processed when being compared with an ACL:
- They're always compared with each line of the ACL in sequential order, always beginning with the first line, then proceeding to line 2, then line 3, and so on.
- They'll be compared with subsequent lines of the list until a match is made. Once the packet matches the condition on a line of the ACL, the packet is acted upon and no further comparisons take place.
- There is an implicit “deny” at the end of each ACL that says that if a packet doesn't match the condition on any of the lines in the ACL, it will be discarded.
Each of these rules has some powerful implications for filtering IP packets with ACLs, which is why creating effective ACLs truly takes some practice!
There are two main types of ACLs:
Standard ACLs These use only the source IP address in an IP packet as the condition test, so all decisions regarding a packet will be based on the source IP address. This means that standard ACLs basically permit or deny an entire suite of protocols without distinguishing between any of the myriad types of IP traffic like web, Telnet, UDP, and so on.
Extended ACLs Extended ACLs go the distance and evaluate lots of the other fields in the Layer 3 and 4 headers of an IP packet. They can evaluate source and destination IP addresses, the protocol field in the Network layer header, and the port number at the Transport layer header. This gives extended ACLs the ability to enforce highly specific network traffic control conditions.
Once you create an ACL, it doesn't do much of anything until you apply it. Yes, it's there on the router, but it's inactive until you tell that router what to do with it. To use an ACL as a packet filter, you've got to apply it to the interface on the router exactly where you want the traffic filtered, and you've also got to specify the traffic's direction—inbound or outbound. This is because you probably want different controls in place for traffic leaving your network that's destined for the Internet than you want for traffic coming into your network from the Internet. Here's the difference:
Inbound ACLs When an ACL is applied to inbound packets on an interface, those packets are processed through the ACL before being routed to the outbound interface. Any packets that are denied won't be routed because they'll be discarded before the routing process is completed.
Outbound ACLs When an ACL is applied to outbound packets on an interface, those packets are routed to the outbound interface and then processed through the ACL before being queued.
Creating ACLs is great, but don't forget to apply them to an interface or they're not going to filter traffic. With that in mind, here's a list of rules to live by when configuring ACLs on interfaces from the Internet into your production network:
- Deny any addresses from your internal networks.
- Deny any local host addresses (127.0.0.0/8).
- Deny any reserved private addresses.
- Deny any addresses in the IP multicast address range (224.0.0.0/4).
These addresses should never, ever be allowed to enter your internetwork.
Port Security
While firewalls can be used to protect access to the network at Layer 3 (IP addresses), there are cases where security needs to be maintained between users within the network. This can be done by implementing port security on the switches in the network. When you do this, you are enforcing security at Layer 2 (MAC addresses).
This can be used in several ways. First, you can use port security to define a set of MAC addresses that are allowed to access a port where a sensitive device is located. Another use is to set unused ports to only be available to a preconfigured set of MAC addresses. The second example could help to prevent unauthorized persons from plugging into a wall outlet (connected to a secured switch port) and accessing the network.
Demilitarized Zone
Most firewalls in use today implement something called a demilitarized zone (DMZ), which, as its name implies, is a network segment that isn't public or local but halfway between the two. People outside your network primarily access your web servers, File Transfer Protocol (FTP) servers, and mail relay servers, and because bad guys tend to go after these servers first, it's a good idea to place them in the DMZ.
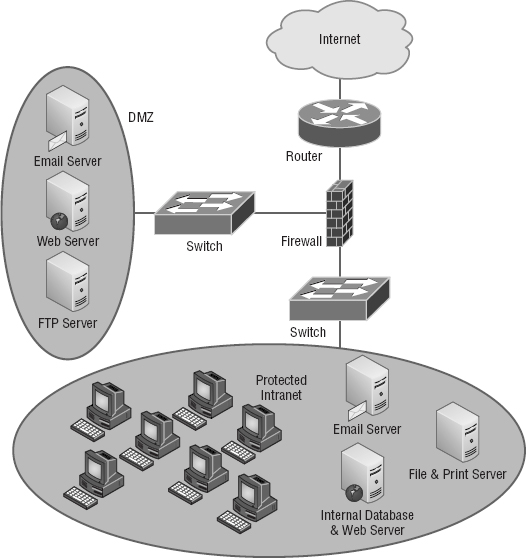
A standard DMZ setup typically (but not always) has two or three network cards in the firewall computer. The first goes to the Internet, the second one goes to the network segment where the commonly targeted servers exist (the servers I recommended be placed in the DMZ), and the third connects to your intranet. As you can see in Figure 15.3, the email server, the FTP server, and web server are all in the DMZ, so all critical servers live inside the firewall.
Understand that it is very possible to have a DMZ outside the firewall. Figure 15.3 shows an example of having the DMZ inside the firewall. Both options are available when building your intranets.
If you set things up like this, hackers who break into servers in the DMZ will only get to see public information—meaning your entire corporate network won't be compromised. Understand that email messages are still fairly vulnerable, but only the relay server can be accessed because all messages are stored and viewed on email servers inside the network.
It is important to understand and remember that you need to administer your DMZ. This is not a device you buy at the store and just connect, turn on, and forget—you need to permit and deny the ports you want. If your company uses custom port numbers, you need to verify that the DMZ is allowing these ports through your server. This is easy to do by telnetting to the DMZ server using the custom port number. If the server responds, you're good!
Protocol Switching
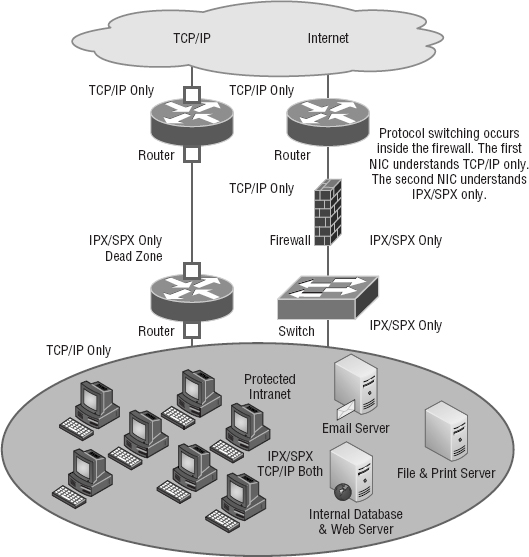
Protocol switching protects data on the inside of a firewall, and because Transmission Control Protocol/Internet Protocol (TCP/IP) is what the Internet runs on, most external attacks take direct aim at this protocol stack. In days gone by, protocol switching used to be pretty popular, but not so much anymore due to the greatly intensified power of firewall technology and the fact that TCP/IP is now the protocol of choice for all network communications. But if you did want to implement protocol switching, here are the two best ways to do it:
- Use a protocol other than TCP/IP on the internal network inside the firewall. IP-based attacks aimed at your development server just can't work if you use Internetwork Packet Exchange (IPX) on the internal-network side of a router, which gives you an automatic firewall.
- Use TCP/IP on the internal network and use a different protocol like IPX in a dead zone between the internal network and the Internet. Basically, you'll have things set up to switch from IP to IPX in that dead zone and switch back to IP again once inside your network (IPv6 would work in this example as well, but IPX is a good example because no one would expect it).
![]()
Applying Your Knowledge
Your new role with ABB Tech Inc. requires you to manage the firewall leading into the Sales department. Your predecessor configured the following rule set on the firewall.
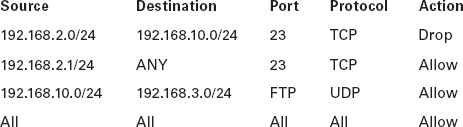
The following issues have been identified with the functioning of the firewall.
- Joe Smith, an IT tech with an IP address of 192.168.2.1, should be able to use Telnet to any devices in the network, but he cannot use it with any devices.
- All users in the Marketing department, which uses the 192.168.10.0 subnet, should be able to use FTP to upload images to a server at 192.168.3.10 but cannot do so.
Your assignment is to correct the rule list. The corrected list is at the end of the chapter.
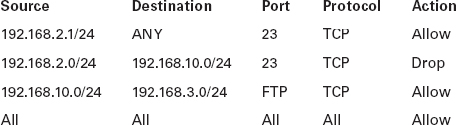
Note: The rule designed to allow Joe at 192.168.2.1 should be moved to the top of the list. As it is now positioned, the first rule will match his address as well and prevent him from using Telnet to any devices. The rule designed to allow users in the Marketing department, which uses the 192.168.10.0 subnet, to use FTP to upload images to a server at 192.168.3.10 is set with an incorrect protocol type. FTP uses TCP and not UDP, so changing that in the rule set will solve that issue.
Figure 15.4 demonstrates both of these strategies. Focus on the dead zone between two of the routers, and also notice that the only protocol on the inside of either router is IPX. This means that any TCP/IP packets coming in from the Internet can't pass through into the local network because of the difference in protocols used by each network.

Both of these methods protect only the Internal network. You still need a firewall to guard against attacks on your network's access point and protocol-switching device.
Dynamic Packet Filtering
Packet filtering refers to the ability of a router or a firewall to discard packets that don't meet the right criteria. Firewalls use dynamic packet filtering to ensure that the packets they forward match sessions initiated on their private side by something called a dynamic state list or state table, which keeps track of all communication sessions between stations from inside and outside the firewall. This list changes dynamically as sessions are added and deleted.
So with dynamic packet filtering, only packets for valid and current sessions are allowed to pass. Anyone trying to play back a communication session—for instance, a login to gain access—won't be able to do that if your firewall is using dynamic packet filtering with a dynamic state list because the data they send isn't part of a currently valid session. The firewall will respond to an event like this by dropping all packets that don't correspond to a current session via the information in the dynamic state list. Let me clarify this: Say a computer in Network A requests a Telnet session with a server in Network B. The firewall in between the two keeps a log of the communication packets that are sent each way, and only packets that belong to the current session will be allowed back into Network A through that firewall.
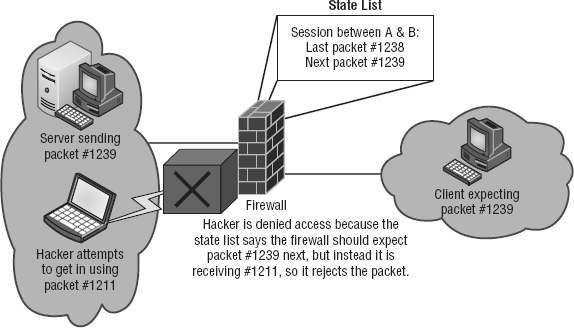
Figure 15.5 depicts a failed attempt to infiltrate a network protected with a dynamic state list. Can you see that the hacker attempts to insert a packet into the communication stream but can't because they don't have the correct packet number? This is because the firewall was waiting for a specific order of packets and the hacker's packet is out of sequence.
Proxy Services
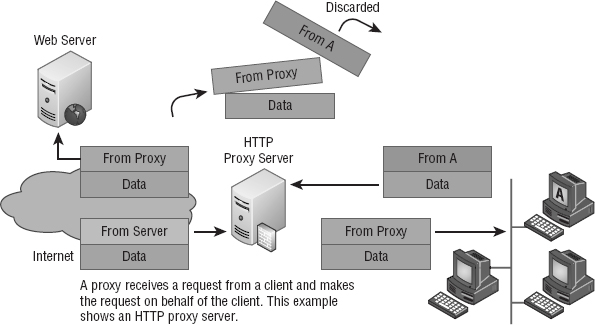
Firewalls can also implement something called proxy services, which actually makes them proxy servers, or proxies for short. Proxies act on behalf of the whole network to completely separate packets from internal hosts and external hosts. Let's say an internal client sends a request to an external host on the Internet. That request will get to the proxy server first, where it will be examined, broken down, and handled by an application that will create a new packet requesting information from the external server. Figure 15.6 demonstrates this process. Make a note to self that this exchange occurs between applications at the Application layer of the OSI model.
Proxies make good firewalls because they dissect the entire packet so that each section of it can be scrutinized for invalid data at each and every layer of the OSI model; proxies look at everything from information in the packet header to the actual contents of the message. They can even examine attachments for viruses. As if all that isn't cool enough, proxies can also search messages for keywords that can indicate the source of a packet. That last little goodie is vital because you can use this type of searching to prevent sensitive information from escaping your organization along with the outbound data stream. If your sensitive documents contain a header or footer that includes something like MyCompanyName Confidential, you can set up your proxy server software to search for it. The only downside is that all that analysis will definitely degrade overall performance because it requires a lot more time than just checking state lists.
There are many types of proxy servers:
IP Proxy An IP proxy hides the IP addresses of all the devices on the internal network by exchanging its IP address for the address of any requesting station. This is good because you definitely don't want a hacker to know any IP addresses specific to your internal network, right? Even Internet web servers won't be able to determine the specific IP address from which they receive a request because any and all communications appear to have originated from the proxy server—nice! These proxies are sometimes called Network Address Translation (NAT) proxies.
Web (HTTP) Proxy Web proxies, also called HTTP proxies, handle HTTP requests on behalf of the sending workstation. When these are implemented correctly, a client's web browser asks a web server on the Internet for a web page using an HTTP request. Because the browser is configured to make HTTP requests using an HTTP proxy, the browser sends the request to the proxy server. The proxy server changes the From address of the HTTP request to its own network address and sends it to the Internet web server. The response to the HTTP request goes directly to the proxy (because it replaced the sender's address with its own). The proxy server then replaces its address with the address of the original sender, and the response is delivered to the original sender.
The most popular implementation of a web proxy is a proxy cache server. This server receives an HTTP request from a web browser and then makes the request on behalf of the sending workstation. When the requested page is returned, the proxy server caches a copy of the page locally. The next time someone requests the same web page or Internet information, the page can be delivered from the local cache instead of the proxy server having to formulate a new request to the web server on the Internet. This speeds up web surfing for commonly accessed pages. Web proxies can also increase network security by filtering out content that is considered insecure, such as executables, scripts, or viruses.
FTP Proxy FTP proxies handle the uploading and downloading of files from a server on behalf of a workstation. An FTP proxy operates in a fashion similar to a web proxy. As with web proxies, FTP proxies can filter out undesirable content (viruses and the like).
SMTP proxy SMTP proxies handle Internet email. Here, the actual contents of the packet and mail can be automatically searched. Any packets or messages that contain material that is not considered secure can be blocked. Many SMTP proxies allow network virus protection software to scan inbound mail.

Not every firewall falls into a simple category. Although firewalls are used to typically work in one arena, today's firewalls offer multiple solutions within one box or software program. Firewalls that perform more than one type of filtering service are sometimes referred to as hybrid firewalls.
Firewalls at the Application Layer vs the Network Layer
By now, you know all about the OSI model and that the Application layer is at the top of the heap and the Network layer is third up from the bottom. And as a rule of thumb, the higher you get in the OSI model, the more complex the interactions become. This rule holds true for discussions of firewalls that work at the Application layer versus those that work at the Network layer.
The first firewalls that were developed functioned solely at the Network layer, and the earliest of these were known as packet-filter firewalls. I covered packet filtering a bit earlier in this chapter; as a refresher, all it means is that the firewall looks at an incoming packet and applies it against the set of rules in the ACL(s). If the packet passes, it gets sent on. If not, the packet is dropped.
This type of filtering is pretty basic because all the firewall considers is the individual packet. All that matters are the source and destination addresses, protocol, and port number. The firewall doesn't care whether that packet is stand-alone or part of another data stream. This process works fairly well for common protocols such as TCP and User Datagram Protocol (UDP), which communicate on predefined port numbers. People generally refer to two types of Network layer firewalls: stateful and stateless.
Stateful vs Stateless Network Layer Firewalls
As I said in the last section, a basic packet filter doesn't care about whether the packet it is examining is stand-alone or part of a bigger message stream. That type of packet filter is said to be stateless, in that it does not monitor the status of the connections passing through it. Again, these work pretty well, but the firewall has no idea whether a packet is legitimate or possibly a rogue packet trying to sneak by. These types of firewalls tended to be susceptible to various DoS attacks and IP spoofing.
The one big advantage that a stateless firewall has over its stateful counterparts is that it uses less memory. Today, stateless firewalls are best used on an internal network where security threats are lower and there are few restrictions.
In contrast to a stateless firewall, a stateful firewall is one that keeps track of the various data streams passing through it. If a packet that is a part of an established connection hits the firewall, it's passed through. New packets are subjected to the rules as specified in the ACL. These types of firewalls are better at preventing network attacks that look to exploit existing connections, or DoS attacks.
A stateful firewall works by using the TCP three-way handshake. First, the client sends a packet with the SYN bit set to the firewall. The firewall interprets this as a new connection and passes the request to the appropriate service provider on the internal network. Next, the service responds with a packet that has both the SYN and ACK bits set. Finally, the client responds with a packet with only the ACK bit set. At that point, the connection is considered established and the firewall will only allow packets in that have the same connection identification. The established connection is logged in the state table.
If there is no data on the connection for a specified period of time, the connection will time out in the state table. Any new communication will need to be reestablished based on the ACL rules.
Stateful firewalls tend to be a bit slower at establishing connections than stateless ones because there is more to do. After the connection is established, though, stateful firewalls are usually faster because they just have to check the state table for the connection instead of comparing the packet against all the relevant ACLs. This is done via stateful packet inspection. Most stateful firewalls can also keep track of connections using connectionless protocols such as UDP.

In a common DoS attack, the SYN flood, the attacker attempts to overload a firewall by spamming it with inordinate numbers of SYN requests. The firewall by default will keep sending SYN/ACKs back, thereby preventing it from responding to legitimate connection requests. An additional problem for the firewall is that it maintains memory space for every SYN/ACK it sends out and the attacker never answers with a final ACK, so memory gets used up. Many of today's firewalls can circumvent this problem by not responding to multiple SYN requests from the same host.
![]()
Firewall Challenges
You were just given a firewall for your network and that firewall was appropriated from a different part of your company. You want to make sure hackers can't get in through that firewall on random ports. Fortunately for you, the firewall is default deny, so you don't have too many worries. You open up the ports for legitimate traffic, such as 80 for HTTP, 161 for Simple Network Management Protocol (SNMP), 21 for FTP, and so on. But users complain that they are unable to download files from the extranet using FTP. What happened?
FTP does work on port 21, but it also establishes connections on arbitrary high-number ports to complete its work. If those ports are not opened, FTP won't work. This is where a stateful firewall is handy. When FTP goes to open the new port number, the firewall will see that the data intended for the new port is part of the existing FTP connection and let the data pass through. Yet another reason why stateful firewalls are so much better than stateless ones!
Application Layer Firewalls
Although stateful firewalls are more powerful and secure than stateless ones, Application layer firewalls are even better. They work by inspecting more than just data in the IP header: They read data at the Application layer. In other words, they will know whether a packet is FTP, SNMP, HTTP, or whatever Application layer protocol it is. The one major drawback is speed. Because these devices have to read more information than their Network layer counterparts, they do tend to be a bit slower. It's generally not enough that you'll notice, though, unless you have the reaction time of Superman.
One nice feature of Application layer firewalls is that they let you set proxy rules for multiple applications on the same firewall. As a proxy, the firewall processes all data between the two endpoints and drops all packets that are suspicious. In theory, a rogue packet will never reach the system on your internal network. Application layer firewalls also handle complex protocols such as H.323, which is used for Voice over IP (VoIP), much better than their Network layer counterparts.
Scanning Services and Other Firewall Features
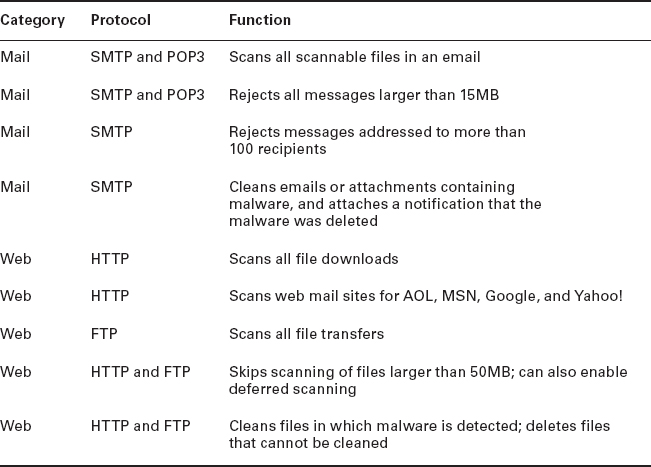
Most firewalls are capable of performing scanning services, which means that they scan different types of incoming traffic in an effort to detect problems. For example, firewalls can scan incoming HTTP traffic to look for viruses or spyware, or they can scan email looking for spam. You can often set scanning rules that will prevent users from downloading files over a certain size. On Cisco routers, scanning is administered by the Content Security and Control Security Services Module (CSC-SSM). Two categories of content are typically scanned: mail and web.
Table 15.1 shows some key default scanning settings within CSC-SSM.
The defaults give you a pretty good level of protection, but there may be instances where you want to change settings. For example, if you are concerned about bandwidth, then you can limit the size of files transferred via FTP or HTTP. If mail storage is an issue, then you can set the firewall to reject mail larger than 10MB.
Keep in mind, though, that by changing some settings, you are increasing your security risk. If you offer deferred scanning for large files, it will allow you to begin viewing the data without a prolonged wait while the entire body of information is scanned. However, the unscanned portion of information can introduce a security risk.

If you are having problems with large file transfers timing out on your network, it's possible that it's partially caused by the firewall scanning the files immediately. Offering deferred scanning can help fix the problem, but you also need to weigh the additional security risk.
Content Filtering
Content filtering is very closely related to scanning services, and on Cisco routers it's also provided by the CSC-SSM. Specifically, content filtering means blocking data based on the content of the data rather than the source of the data. Most commonly, this is used to filter email and website access.
The reasons for using content filtering seem pretty obvious. Most companies have a zero-tolerance policy against hateful material or pornography. If a user on a company network uses that network to spread hate mail or porn, the company could be liable for damages in a lawsuit if they didn't take measures to prevent such actions. It's not only a moral issue, it's a legal issue, too.
Content filtering is also important in places like schools. It's doubtful that parents want their kids to be able to stumble upon a porn site in the school library while researching a school project. Content filtering can block that site from being accessed so the problem never occurs. You can also find several parental-control software packages for home use that employ content filtering.
There are several ways to filter content; here are some of the more common categories used:
- Attachment (blocking attachments of a certain type, such as EXE files)
- Bayesian
- Content-encoding
- Email headers
- Language
- Phrases
- Proximity of words to each other
- URLs
Nearly all filtering methods use a combination of filters to protect users from improper content.
Signature Identification
Firewalls can also stop attacks and problems through a process called signature identification. Viruses that are known will have a signature, which is a particular pattern of data, within them. Firewalls (and antivirus programs) can use signatures to identify a virus and remove it. The same holds true for other software bugs, such as worms and spyware.
Numerous network attacks have signatures as well. For example, if your router starts getting hit by large numbers of SYN requests, you may be at the beginning of a SYN flood attack. The inundation of SYN traffic is a signature of a SYN flood.
Context Awareness
A firewall that is “context aware” is one that can take into consideration the context in which traffic is arriving at the firewall. It can detect different applications, users, and devices—not just IP addresses. Because of this more sophisticated approach, it lets administrators track how applications are used across a range of devices. For example, it may track and/or prevent the posting or sharing of videos on Facebook using an iPhone, PC, or other device. It also enables companies to enforce policies, like not allowing a specific group of employees to access games on iPads.
Virtual Wire vs Routed
Firewalls can control communications between segments by controlling traffic between Layer 3 segments (routed approach) or by a process called virtual wire. In this approach, the firewall is connected between a trusted and untrusted section of a network, as shown in Figure 15.7. To the devices connected to the firewall (in this figure a switch and router) it appears that only a single “wire” is connected between them.
Virtual wire firewall interfaces do not need IP addresses. Security zones are defined on the physical interfaces of the virtual wire pair. Virtual wire does neither routing nor switching; it examines the traffic flow to perform deep packet inspection and enforces the firewall policy.
Zones
A zone is an individual area of the network that has been configured with a specific trust level. Firewalls are ideal devices to regulate the flow of traffic between zones. If you look back at Figure 15.3, this provides a good example of how zone levels could work. The Internet would be a zone with no trust or a low level of trust. The DMZ, located between the Internet and the internal network, could have a medium level of trust. The computers on the intranet would all be within a high trust zone. The higher the trust level, the less scrutiny you place on data coming from a computer in that zone.
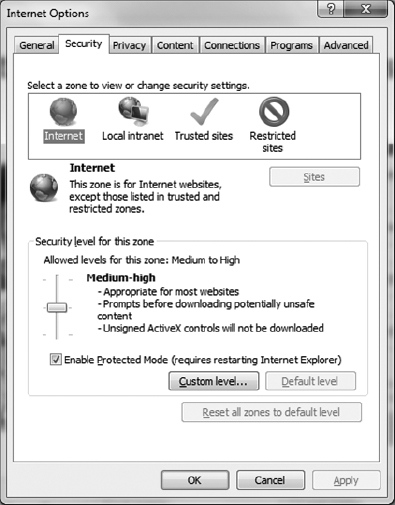
Another way to look at zones is to understand how Internet Explorer deals with them. Figure 15.8 shows you what the Internet Options Security tab looks like. On this tab, you can see that there are four zones for which you can configure security levels: Internet, Local Intranet, Trusted Sites, and Restricted Sites. There are three default security levels for the Internet: High, Medium, and Low. Don't get this confused with the trust levels I talked about in the previous paragraph—they are basically opposites. If the security level is set to High, it means you have low trust.
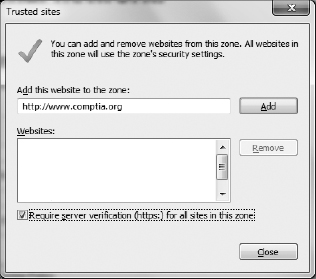
A good way to ensure some security through your browser is to set the security level to Medium-High or High and leave it there. If there are sites that you download from frequently and that you trust, then you can put those sites into the Trusted Sites zone. Click Trusted Sites and then click the Sites button to get to the screen shown in Figure 15.9.
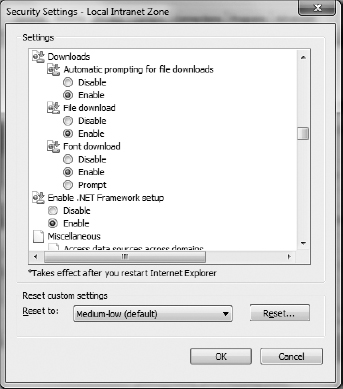
Finally, you can customize the security level of any of the zones by clicking the Custom Level button near the bottom of the Internet Options window. This will take you to a screen similar to the one shown in Figure 15.10.
Within the custom settings, you can specify behavior for .NET framework components, ActiveX controls and plug-ins, downloads, scripting, user authentication, and several other options. Most of the options have choices to disable, enable, or prompt you if you want to continue with the operation.

Although Internet Explorer security options can help protect your computer, do not think of them as a replacement for a firewall. The best security systems are multifaceted. You should have a firewall solution in place and then augment that with solid security measures on your local computer as well.
Intrusion Detection and Prevention Systems
If someone has broken into your network, how would you know? I mean, it's not like you're going to find broken windows or the door left wide open, right? Although it's true that you won't be dusting for prints, bad guys who break into networks still leave clues behind that can help you sleuth out their identities as well as how they gained access. A great tool for doing network detective work is known as an intrusion detection system (IDS).
Firewalls are designed to block nasty traffic from entering your network, but an IDS is more of an auditing tool: It keeps track of all activity on your network so you can see if someone has been trespassing. Because the technology behind IDSs is fairly new, people are busy developing ways to combine IDS technology with existing firewalls.

An intrusion detection system does not replace a firewall on your network!
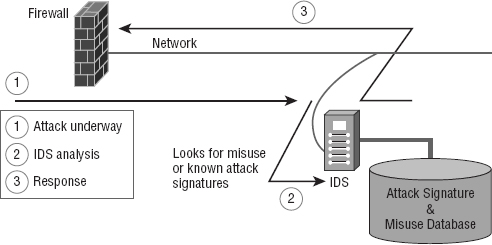
There are two ways IDSs can detect attacks or intrusions. The first is based on the signature of an intrusion, often referred to as a misuse-detection IDS (MD-IDS), and it works by looking for fingerprints. That's right—I said fingerprints, which in this case means strange or abusive use of the network. The IDS sends up an alarm only if it recognizes the fingerprints typical of attackers. The second approach looks for anomalies in network activity, or an anomaly-detection IDS (AD-IDS). An AD-IDS basically watches for anything out of the ordinary; if it discovers fingerprints where there shouldn't be any, it will send out an alert. And a really cool feature is that it's known as a smart system because it learns on the go by keeping track of and building a history of network activity for norms to which you can compare unusual activity. Most IDSs today are a combination of two types of detection systems. Figure 15.11 shows an MD-IDS in action.

An intrusion detection system cannot detect attacks within encrypted traffic.
An IDS is a system made up of several components, including one or more sensors to detect events, a console to control and configure the sensors and monitor events, and a database that records the events. These three elements can all be on the same device, or they can be implemented on multiple devices.
The two most common types of IDS implementations are network based and host based.
Network-Based IDS
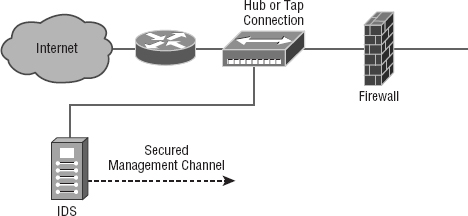
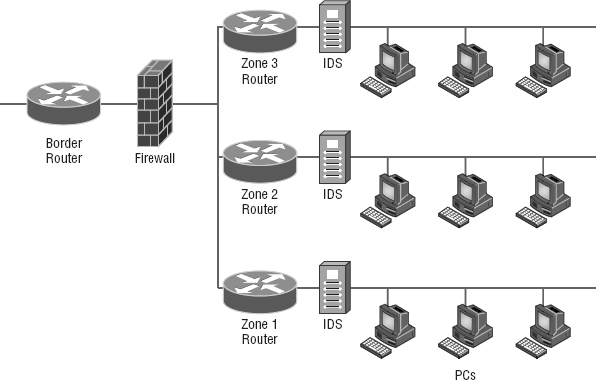
By far the most common implementation of a detection system is a network-based IDS (NIDS), where the IDS is a separate device attached to the network via a machine like a switch or directly via a tap. Some IDSs are even capable of attaching to the network both outside and inside the firewall; this gives you the best security because you can see what is happening out in the wild and really nail exactly what's getting through your defenses. Figure 15.12 gives you an example of a typical IDS setup can look like.
When your IDS detects an intrusion, it will respond to it either passively or actively. Passive responses are the easiest to configure and include the following:
Logging All activity to the intrusion is logged. The information gathered can be used to foil future attacks of the same type. Intrusions should always be logged.
Notification When an attack occurs, an IDS can send an alert to one or more administrators.
Shunning I'm not kidding about this one—you can sometimes just ignore the attack because it's possible it won't affect your network. For instance, if someone launches an attack designed to cripple a Microsoft Exchange email server at a network that's running Lotus Notes, you're all good, so why waste time doing anything about it? I would recommend recording the event though.
Active responses mean taking immediate action. When an IDS moves to prevent an attack, it's often called a reactive system or an intrusion protection system (IPS). Here are three common active responses:
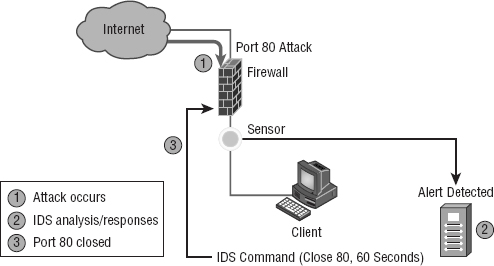
Changing Network Configuration Let's say an attack comes in on port 21. Your IDS can close the port either temporarily or permanently. The downside is that if the IDS closes ports, legitimate traffic can't get through either, but it will definitely stop the attack. Figure 15.13 shows an example of closing port 80 (HTTP) for 60 seconds.
Terminating Sessions When the IDS detects an attack, it can force all sessions to close and restart, which will affect and delay legitimate traffic, too, but not for long.
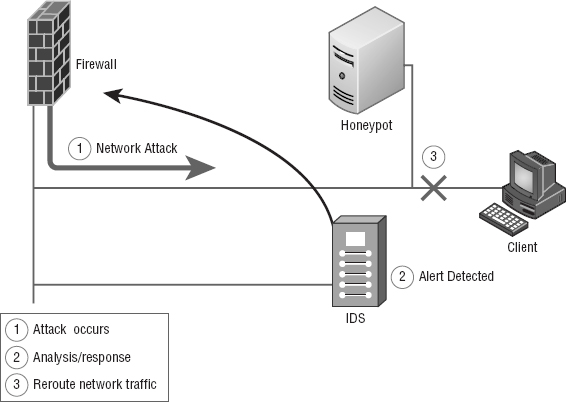
Deceiving the Attacker This one's the most fun because it tricks the bad guy into thinking their attack is really working when it's not. The system logs information, trying to pinpoint who's behind the attack and which methods they're using. This response requires something called a honeypot, typically a server or group of servers (called honeynets) or maybe even access points, to which the hacker is directed; it's intended to keep their interest long enough to gather enough information to identify them and their attack method so you can prevent another attack in the future. Figure 15.14 demonstrates this.
Host-Based IDS
In a host-based IDS (HIDS), software runs on one computer to detect abnormalities on that system alone by monitoring applications, system logs, and event logs—not by directly monitoring network traffic.
Systems like these are typically implemented on servers because they're a bear to manage if spread across several client computers on a network. Plus, if the IDS database is on the local computer and its data becomes compromised by an attack, the IDS data could be corrupted too.

Other types of IDSs are protocol based (PIDS), which monitor traffic for one protocol on one server; application protocol based (APIDS), which monitor traffic for a group of servers running the same application (such as SQL); and hybrid IDS, which combine one or more IDS technologies.
Vulnerability Scanners
One of the most effective ways to determine if security holes exist in the network is to think like an attacker and attack your own network. In that case, why not use the same tools that the hacker might use to identify your weaknesses? For example, if I wanted to verify the proper application of some ACls to a firewall, I could do so with scanning services supplied by a vulnerability scanner. In the following sections, I'll cover two of the most widely known and effective programs that can be used for this purpose.
Nessus
Nessus is a propriety vulnerability scanning program that requires a license to use commercially yet is the single most popular scanning program in use. It normally is executed from the command line because it can thus be included in batch files that can automate its operation on a schedule. Its output can be reported in a variety of formats, including plain text, HTML, and XML.
It operates by performing a port scan and then follows up with more specific tests and scans based on the ports open. It can identify a wide array of weaknesses, including the following:
- Unsecured access to sensitive data on a system
- Misconfigurations like open mail relay and missing patches
- Password issues such as the use of default passwords, common passwords, and blank passwords on system accounts
It can also perform an active attack such as denial of service or a dictionary attack.
NMAP
Network Mapper (NMAP) was originally intended to simply identify devices on the network for the purpose of creating a network diagram. Its functionality has evolved, however, and now it can also do the following:
- Perform port scanning
- Identify versions of network services in operation on the network
- Identify operating systems
It can be used from the command line as with Nessus, but it also can be used with web-based interfaces to be controlled remotely.
Unified Threat Management (UTM)
Unified threat management (UTM) devices perform multiple security functions within the same appliance:
- Network firewalling
- Network intrusion prevention
- Gateway antivirus
- Gateway anti-spam
- VPN
- Content filtering
- Load balancing
- Data leak prevention
- On-appliance reporting
While the advantage of unified security lies in the fact that administering multiple systems is no longer necessary, some feel that a single point of failure is created and creating multiple layers of devices is a more secure approach.
VPN Concentrators
A VPN concentrator is a device that creates remote access for virtual private networks (VPNs) either for users logging in remotely or for a large site-to-site VPN. In contrast to standard remote-access connections, remote-access VPNs often allow higher data throughput and provide encryption. Cisco produces VPN concentrators that support anywhere from 100 users up to 10,000 simultaneous remote-access connections.
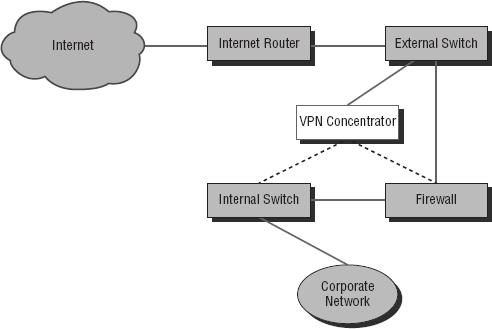
Encryption for a remote-access VPN through a concentrator is usually handled by Internet Protocol Security (IPSec) or by Secure Sockets Layer (SSL), and user authentication can be achieved via Microsoft's Active Directory; Kerberos; Remote Authentication Dial In User Service (RADIUS); Rivest, Shamir, and Adleman (RSA); and digital certificates. Many VPN concentrators also have a built-in authentication server and allow ACLs to be implemented through them. In Figure 15.15, you can see where VPN concentrators are usually placed within a network setup.
The dotted line indicates that you can opt to run your remote-access clients through the firewall before they're granted internal access, or you can just let the concentrator handle the security.
Understanding Problems Affecting Device Security
Throughout this whole chapter, I've been going on and on about the myriad devices we use to secure traffic coming into our networks and devices and the things we depend on to detect and prevent attacks on them. It's an important subject and one that you must solidly understand in order to be effective in networking. Knowing how to implement a tight security program requires working knowledge of these devices, but it doesn't end there because there's always more you can know.
There happen to be a few more really significant and valuable concepts you should have a good grasp of when setting up and managing the security on your network. So that's the direction in which we're going to head for the remainder of this chapter—we'll cover key issues you need to be aware of, including physical security and corresponding logical security structures, restricting access, and the types of protocols you should and should not use on your network.
Physical Security
Over the years, I've visited lots of different companies, large and small, public and private, and analyzed, advised, troubleshot, designed, and implemented their networks. Without fail, the system administrators I've met along the way have been really eager to tell me all about the security systems they have in place. “Look at this awesome firewall setup!” “Check out the cool Group Policy structure we have!” “Watch how quickly our fault tolerance springs into action!” They're very proud, and rightly so, of what they've worked so hard to set up, because doing that isn't easy.
But interestingly, one of the things few people brag about is physical security—like it's some kind of afterthought. Maybe the server room has a locked door, maybe it doesn't. Maybe the badges that open that door are owned by the right people, or maybe they aren't. I guess that on a subconscious level, we tend to inherently trust the people working within the walls and focus our fears, suspicions, and ammo on mysterious outside forces that we're sure are incessantly trying to break in, steal data, or totally murder our networks. Some of the sharpest, most talented, and savvy system administrators I've ever met still have a tendency to neglect inside security and fail to reasonably monitor things going on within the building.
And there are some seriously vital things to nail down on the inside. For instance, does it really matter if your network has a secured subnet for the servers, with its own dedicated internal firewall? Definitely—I've actually found servers in racks like sitting ducks in a hallway right across from the lunch room. When I pointed out the fact that this was not so good, I was assured that it was only temporary until the server room construction was complete. I don't know about you, but for some reason, that didn't cut it and didn't make me feel anywhere near okay with the situation. At another company, I found the door to the server room propped open because otherwise “it got too hot in there.” Because that toasty server room didn't exactly have a guard posted, anyone could just walk in and do whatever; the backup tapes were clearly marked and sitting there on a shelf—yikes! And don't even get me started about the heat. The bottom line is that if your system is not physically secured, you're basically sending out an open invitation to a Pandora's box of problems without even realizing it.
![]()
Beware the Big Gulp
Several years ago when I was teaching a networking class, one of my best students issued me a challenge. He was proud of the security configuration on his server computer in the classroom and went so far as to tell me there was no way I could get to or damage any files on his system. He was really sure about that. Well, it just so happens I like a good challenge.
The students went off to lunch, and I stayed behind to work on a few things. While they were gone, I got out my handy Partition Magic diskette (I said this was a while ago) and popped it into his system. One reset button push later, I was in business. I wiped out the partitions on his hard drive and shut down the system.
When he came back from lunch, he looked a bit confused. He clearly remembered leaving his computer on, and upon booting up and playing around for a minute, he realized that his hard drive was gone. At first, he was more than a little angry at me for doing that, but then I asked him to give me a chance to prove a point—an important one. That is, when someone has access to your computer, they can do whatever they want. Yes, they might not be able to read your files (although I could have done that too), but they can still do a lot of damage. My tool of destruction was a partitioning program, but going back to that “servers out in the open across from the lunch room” situation, all it would take is a spilled soft drink to cause mass destruction. In any case, the data clearly was not safe, so physical security needs to be a top priority.
Physical Barriers
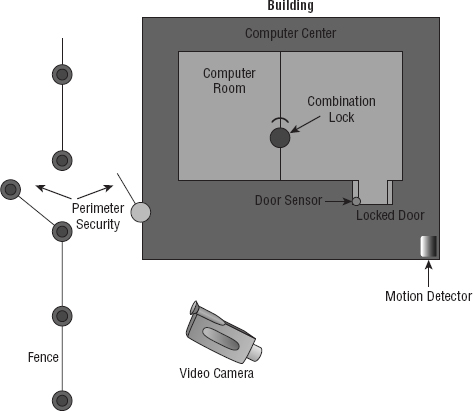
Your first objective is to keep people from physically getting to your equipment. Clearly, end users need to be able to get to their workstations, but only authorized personnel should be anywhere near your servers. The best way to do this is to have a dedicated, two-stage, air-conditioned server room with really secure doors and locks. Even better, your data center should have more than one form of physical security—preferably three. We call that a multiple barrier system. For instance, you could have a perimeter security system controlling access to the building as your first line of defense. The second would be a secured door to the computer room, and the third would be another security door to the server room itself. This is illustrated in Figure 15.16.
Security Zones
Your network probably has different security zones. Let's say your servers are in one zone and the clients are in another. Maybe your engineering department has its own zone. So why not have the same zones for physical access to the computers? Many companies today use RFID badges to control where employees are allowed to go inside the building. You may need a safety clearance and/or certification before you can go in the room where the pilot production machine lives. People should be cleared and certified before they're allowed in the server room as well.
Mantraps
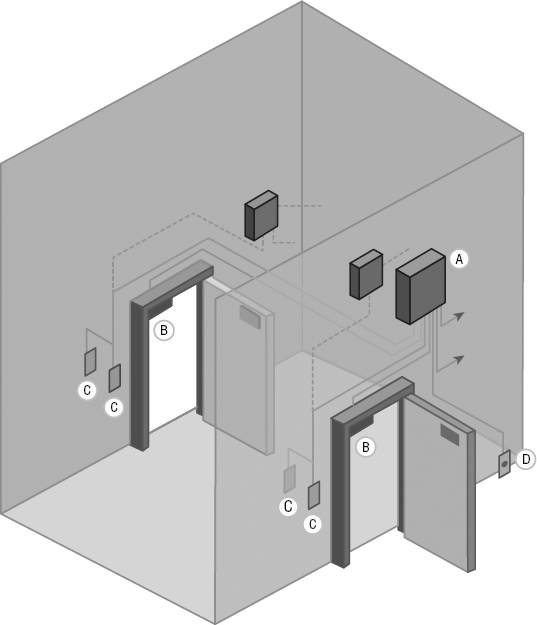
A mantrap is a series of two doors with a small room between them. The user is authenticated at the first door and then allowed into the room. At that point, additional verification will occur (such as a guard visually identifying the person) and then they are allowed through the second door. These doors are typically used only in very high-security situations. They can help prevent tailgating. A mantrap design is shown in Figure 15.17.
Network Closets
While much of the network equipment should be locked securely in the server room, there are frequently cases where it is also stored in a smaller location or closets. If that is the case, these locations should be locked as securely as the server room, and access to them should be controlled through mechanisms such as cipher doors or proximity locks.
Video Monitoring
In many high-security scenarios it may be advisable to visually monitor the area 24 hours a day. When this is the case, it will make sense to deploy video monitoring. We'll look at two options, IP cameras and CCTV systems.
IP Cameras IP video systems are a good example of the benefits of networking applications. These systems can be used for both surveillance of the facility and for facilitating collaboration.
CCTVs While an IP camera is a type of digital video camera commonly employed for surveillance, analog closed circuit television (CCTV) cameras are unable to send their images across IP networks. CCTV cameras record directly to a medium such as video tape or hard drive. It is possible to convert the signal to digital in cases where you need to send it across an IP network.
Door Access Controls
While mantraps may justify their cost in some high-security scenarios, not all situations require them. Door controls should be used to prevent physical access to important infrastructure devices such as routers, switches, firewalls, and servers. Door control systems are covered in the following sections.
Proximity Readers/Key Fob
Proximity readers are door controls that read a card from a short distance and are used to control access to sensitive rooms. These devices can also provide a log of all entries and exits. Usually, a card contains the user information required to authenticate and authorize the user to enter the room.
A key fob, on the other hand, is a type of security token: a small hardware device with built-in authentication mechanisms. The mechanisms in the key fob control access to network services and information. An advantage of a key fob is that it can support multifactor authentication.
For example, a user may have a personal identification number (PIN), which authenticates them as a device's owner; after the user correctly enters their PIN, the device displays a number that allows them to log on to the network
Biometrics
Biometric systems are designed to operate using characteristic and behavioral factors. While knowledge factors (password, PIN) are the most common authentication factors used, characteristic factors represent something that you are (fingerprint, iris scan) while behavioral factors represent something that you do (signature analysis).
Multifactor authentication is achieved by combining authentication factors. When two knowledge factors are combined, such as a retina scan (characteristic factor) and a password (knowledge factor), dual-factor authentication is required. When three factors are combined, such as a retina scan (characteristic factor), a password (knowledge factor), and signature analysis (behavioral factor), then multifactor authentication is in effect.
One of the issues with biometrics is the occurrence of false positives and false negatives. A false positive is when a user that should not be allowed access is indeed allowed access. A false negative, on the other hand, is when an authorized individual is denied passage by mistake.
Keypad/Cypher Locks
Cypher locks that use a keypad require a user to know the key code. This devices can also come with additional security features. The lock can be combined with a set time for opening the door as well as a battery standby system. Three types of alarm systems are available. A burglar alarm interface is available to indicate when the door is breached. An error alarm can reveal someone who tries to guess the code. Finally, a hostage alarm can be triggered to indicate that entry was made under duress.
Security Guard
In cases where judgment may be required to control entry, a security guard may be advisable. While the cost is generally higher than with an automated system, there are advantages to this. This offers the most flexibility in reacting to whatever occurs. One of the keys to success when using guards is to ensure that they are trained with a response to every conceivable eventuality. Finally, the biggest advantage is that guards can use discriminating judgment in a situation, which an automated system cannot.
Logical Security Configurations
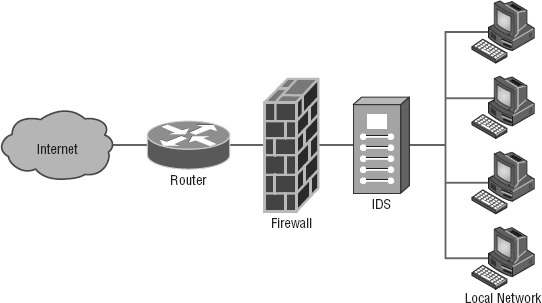
Now that you have your physical network locked down tight, it's time to review the security configuration of your network. The same concepts that apply to physical security apply here, too. First, you want to ensure that your network has an outside barrier and/or a perimeter defense. This is usually achieved by having a solid firewall, and it's best to have an IDS or IPS of some sort as well. Figure 15.18 shows what this might look like.
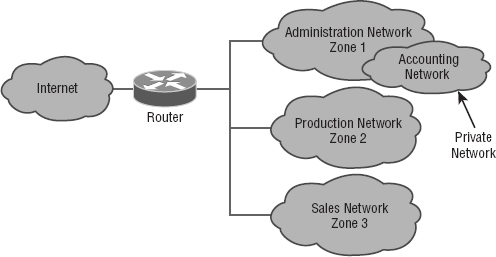
That may be enough for your network, but maybe not. Let's say that your network serves several distinct departments at your company. The admin, production, and sales groups all have their own unique needs. What you can now do is divide up your internal network into smaller administrative zones by creating VLANs and using a DMZ. Maybe your network would logically look like the one shown in Figure 15.19.
Finally, your network might be similar to the one shown in Figure 15.19 but just larger. Maybe traffic is heavy and you need to break up physical segments. Perhaps different groups are in different buildings or on different floors of a building and you want to effectively segment them. There could be any number of reasons for you to “physically” separate your network into different groups, effectively partitioning your network by using multiple routers, as shown in Figure 15.20.
Risk-Related Concepts
All organizations should identify and analyze the risks they face. This is called risk management. In the following sections, you'll find a survey of topics that all relate in some way to identifying risks and mitigating them.
Disaster Recovery
A disaster is an emergency that goes beyond the normal response of resources. The causes of disasters are categorized into three main areas according to origin:
- Technological disasters (device failures)
- Manmade disasters (arson, terrorism, sabotage)
- Natural disasters (hurricanes, floods, earthquakes)
The severity of financial and reputational damage to an organization is largely determined by the amount of time it takes the organization to recover from the disaster. A properly designed disaster recovery plan (DRP) minimizes the effect of a disaster. The DRP is implemented when the emergency occurs and includes the steps to restore functions and systems so the organization can resume normal operations. The goal of DRP is to minimize or prevent property damage and prevent loss of life.
Business Continuity
One of the parts of a DRP is a plan to keep the business operational while the organization recovers from the disaster, known as a business continuity plan (BCP). Continuity planning deals with identifying the impact of any disaster and ensuring that a viable recovery plan for each function and system is implemented. By prioritizing each process and its supporting technologies, the company can ensure that mission-critical systems are recovered first and systems that are considered luxuries can be recovered as time allows.
One document that should be created to drive this prioritization is the business impact analysis. In this document, the impact each system has on the ability of the organization to stay operational is determined. The results list the critical and necessary business functions, their resource dependencies, and their level of criticality to the overall organization.
Battery Backups/UPS
One risk that all organizations should prepare for is the loss of power. All infrastructure systems should be connected to uninterruptible power supplies (UPSs). These devices can immediately supply power from a battery backup when a loss of power is detected. You should keep in mind, however, that these devices are not designed as a long-term solution. They are designed to provide power long enough for you to either shut the system down gracefully or turn on a power generator. In scenarios where long-term backup power is called for, a gas-powered generator should be installed.
First Responders
A first responder is the first person to discover a data breach or other security incident. First responders are covered in the section “Basic Forensic Concepts” in Chapter 14.
Data Breach
A data breach is a risk that the organization should always be prepared to address. Procedures for responding to data breaches and other security incidents are covered in the section “Incident Response” in Chapter 14.
End User Awareness and Training
One of the issues related to the risk involved in security incidents and disasters over which the company has some control is the amount of preparation spent on training users. Regardless of whether the incident is as small as the mistaken deletion of a key document or as large as a fire destroying the entire building, users should be trained in how to respond to every eventuality.
Moreover, it would be even better if recovery teams were created to address the stages of disaster recovery. The following teams should be assembled and trained before a disaster occurs:
- Damage assessment team
- Legal team
- Media relations team
- Recovery team
- Relocation team
- Restoration team
- Salvage team
- Security team
Each team should rehearse its response to various scenarios. One exercise that seems to work well is called a tabletop exercise. A tabletop exercise is an informal brainstorming session that encourages participation from business leaders and other key employees. In a tabletop exercise, the participants agree to a particular disaster scenario upon which they will focus.
Single Point of Failure
One concept that makes any IT technician nervous is the existence of a single point of failure anywhere in the network. During the process of creating the BCP, all single points of failure should be identified. The process begins as described in the following sections, with the identification of critical assets and nodes, and is followed by providing redundancy where indicated.
Critical Nodes
Critical nodes are individual systems or groups of systems without which the organization cannot operate. The process of identifying these system should begin with prioritization of the business processes that each supports. Once this has been done, it is simple to identify the servers and other systems that are required to allow that process to continue to function. If this investigation reveals a system that is critical and a single point of failure, action should be taken to provide some form of redundancy to the node.
Critical Asset
While critical nodes need to be identified and provided with additional support to prepare for disasters and smaller issues, some critical business processes depend on access to assets such as data that may reside in a database or in connections to vendors and partners. These assets also need to be identified and an action plan developed that recognizes their importance. In almost all cases, the solution is some form of redundancy, as covered in the next section.
Redundancy
Redundancy occurs when an organization has a secondary component, system, or device that takes over when the primary unit fails. Redundancy can be implemented in many forms. The organization should assess any systems that have been identified as critical to determine if it is cost effective to implement redundant systems. Redundant systems include redundant servers, redundant routers, redundant internal hardware, and even redundant backbones.
One form of fault tolerance that can be provided to a system is Redundant Array of Independent Disks (RAID). This technology allows for automatic recovery from a hard drive failure (within certain limits based on the exact form of RAID) in a system. The major forms of RAID are as follows:
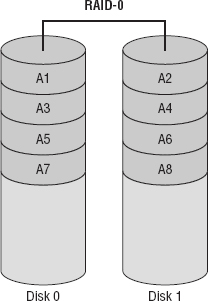
RAID-0 Also called disk striping, this method writes the data across multiple drives. While it improves performance, it does not provide fault tolerance. RAID-0 is depicted in Figure 15.21.
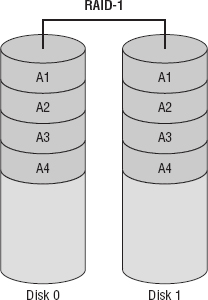
RAID-1 Also called disk mirroring, RAID-1 uses two disks and writes a copy of the data to both disks, providing fault tolerance in the case of a single drive failure. RAID-1 is depicted in Figure 15.22.
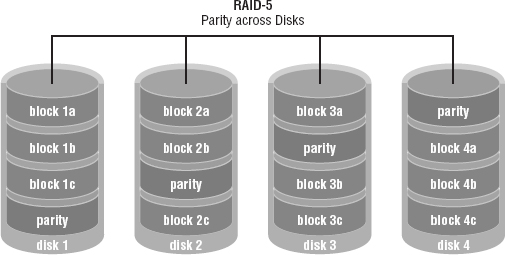
RAID-5 Requiring at least three drives, this method writes the data across all drives like striping, and then parity information is also written across all drives. With hardware RAID-5, the spare drives that replace the failed drives are usually hot swappable, meaning they can be replaced on the server while it is running. RAID-5 is depicted in Figure 15.23
Adherence to Standards and Policies
Policies and standard are created to communicate to employees the behavior expected from them in various situations. This includes polices related to business continuity and disaster recovery. Security policies and procedures are covered in detail in Chapter 14.
Vulnerability Scanning
Part of the security policy of an organization should address the type and frequency of vulnerability scans. These scans are designed to identify any security vulnerabilities that exist.
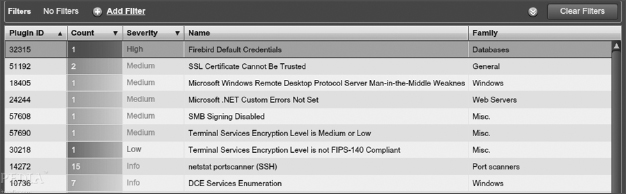
A vulnerability scanner can probe for a variety of security weaknesses, including misconfigurations, out-of-date software, missing patches, and open ports. One of the most widely used is Nessus, a proprietary vulnerability scanner developed by Tenable Network Security. A partial screenshot is shown in Figure 15.24. In the output, the issues found on a host are rated, and issues with the highest severity are at the top by default.
Penetration Testing
A penetration test is designed to simulate an attack on a system, network, or application. Its value lies in its potential to discover security holes that may have gone unnoticed. It differs from vulnerability testing in that it attempts to exploit vulnerabilities rather than simply identify them.
Strategies for penetration testing are based on the testing objectives as defined by the organization:
Blind Test The testing team is provided with limited knowledge of the network systems and devices using publicly available information. The organization's security team knows that an attack is coming. This test requires more effort by the testing team.
Double-Blind Test This test is like a blind test except the organization's security team does not know that an attack is coming. This test usually requires equal effort for both the testing team and the organization's security team.
Target Test Both the testing team and the organization's security team are given maximum information about the network and the type of test that will occur. This is the easiest test to complete, but it will not provide a full picture of the organization's security.
Summary
In this chapter, you learned a lot about physical and hardware security. We dove into this increasingly important subject by looking at one of the most useful network protection devices around: firewalls. You found out the differences between network-based and host-based firewalls, and then learned the specific ways that firewalls work to protect our data and networks by using access control lists (ACLs). You also learned about other key firewall topics, like demilitarized zones (DMZs), protocol switching, packet filtering, and proxy services. I talked about how firewalls can operate at the Network layer or the Application layer of the OSI model. For those operating at the Network level, there are stateful firewalls that keep track of the established connections passing through them and stateless firewalls that don't. Firewalls also provide services like scanning, signature identification, content filtering, and breaking your network up into security zones.
We then moved on and discussed two other vital hardware devices: intrusion detection and prevention systems and VPN concentrators. You learned that IDS devices can be network or host based, just like firewalls, but unlike firewalls, which block traffic based on specific rules, IDS and IPS systems allow traffic in and then initiate a reaction if any problems are detected. I also talked about something called an IPS, which is an IDS that can generate an active response when an intrusion is detected. We then covered VPN concentrators, which are specifically designed to allow several hundred—even several thousand—users to remotely access your network either through a secure connection or by setting up a virtual secure network between two locations.
Finally, you discovered some often-overlooked aspects of physical security that can seriously affect your network. You now know that beyond a doubt, if people can get to your hardware, they can do damage to your infrastructure, intentionally or not.
Exam Essentials
Understand and utilize network segmentation. This includes segmentation at Layer 2 and 3, and includes the proper location of devices such as IPS, IDS, honeypots, and honey nets.
Understand the difference between a network-based firewall and a host-based firewall. A network-based firewall is a hardware device on the network or on a router that protects a group of computers. A host-based firewall is software installed on one individual machine, and it protects only that machine.
Compare and contrast risk-related concepts. Understand how to identify and prioritize key systems and business functions. Create standards and policies to ensure the continued operation of these functions to support business continuity and disaster recovery.
Understand how a firewall determines which traffic can pass through it. Firewalls use access control lists (ACLs), which are sets of rules, to determine which traffic is allowed to pass through.
Describe and apply proper physical security controls. This includes door access controls, biometric systems, and the use of cameras and security guards.
Remember where a DMZ can be placed. A demilitarized zone (DMZ) can be located outside a firewall, connected directly to the Internet. However, it can also be placed after the firewall inside your network. You need to remember that it can be placed in either location.
Understand what a proxy server is and what types of proxying are common. A proxy server is a computer that makes and fulfills requests on behalf of another computer. Many firewalls can act as proxies. Common proxy services include IP proxy, web proxy, FTP proxy, and mail (SMTP) proxy.
Know on which levels of the OSI model various security devices operate. Firewalls work at the Application layer or the Network layer. Port security on switches operates at the Data Link layer.
Understand the difference between stateful and stateless firewalls. A stateful firewall keeps track of the established connections passing through it. When another packet is received that's part of an existing connection (part of a current state), the packet is passed without checking the ACLs. A stateless firewall examines each packet individually and does not track existing states. This makes it a bit slower and more susceptible to network attacks.
Know what types of services firewalls can provide. Most firewalls provide scanning services, content filtering, signature identification, and the ability to segregate network segments into separate security zones.
Know the difference between an IDS and an IPS. An intrusion detection system (IDS) monitors network traffic, looking for signs of an intrusion. Intrusions are detected by matching activity versus known signatures within the IDS's database. If an intrusion is detected, a passive response such as logging or notifying a network administrator is executed. An intrusion prevention system (IPS) is like an IDS, but with two key differences. First, it learns what is “normal” on the network and can react to abnormalities even if they're not part of the signature database. Second, it can issue an active response such as shutting down a port, resetting connections, or attempting to lull the attacker into a trap.
Written Lab
In this section, write the answers to the following security questions. You can find the answers in Appendix A.
- Which type of firewall interface does not use IP addresses?
- Which type of firewall keeps track of existing connections passing through it?
- If you wanted to ensure that your firewall could block inflammatory email, which type of service would you look for?
- The main security issue with UTM devices is that they constitute a __________
- If you wanted to allow remote access to 500 users, which type of device is recommended?
- If data from one of your subnets should be restricted from entering another subnet, the subnets should be configured as different __________.
- A series of two doors with a small room between them is called a __________?
- How does an ACL treat any traffic type by default?
- What is a group of servers used to lure attackers called?
- Logging, notification, and shunning are what types of reactions from what type of security device?
Review Questions
You can find the answers to the review questions in Appendix B.
- In general, firewalls work by __________.
- Rejecting all packets regardless of security restrictions
- Forwarding all packets regardless of security restrictions
- Allowing only packets that pass security restrictions to be forwarded
- None of the above
- Which if the following devices can read an entry card from a distance?
- Biometric reader
- Proximity reader
- Mantrap
- Key fob
- What is the main difference between a network-based firewall and a host-based firewall?
- A network-based firewall protects the Internet from attacks.
- A network-based firewall protects a network, not just a single host.
- A network-based firewall protects the network wires.
- A network-based firewall protects a CD from data loss.
- Which of the following minimizes the effect of a disaster and includes the steps necessary to resume normal operation?
- SLA
- BIA
- DRP
- ARP
- Which of the following items cannot be identified by the Nessus program?
- Default password use
- Incorrect IP addresses
- Unsecured data
- Missing security patches
- What is the benefit of using a firewall?
- Protects external users
- Protects external hardware
- Protects LAN resources
- Protects hardware from failure
- IDSs can identify attackers by their __________.
- Port number
- Signature
- Timing
- IV
- Which of the following is also called disk striping?
- RAID-0
- RAID-1
- RAID-3
- RAID-5
- Which is not a type of access control list (ACL)?
- Standard
- Extended
- Referred
- Outbound
- What is it called when the firewall ignores an attack?
- Logging
- Shunning
- Notification
- False negative
- What is the function of a DMZ?
- To separate a security zone for an IPS and IDS server
- To create a security zone for VPN terminations
- To create a security zone that allows public traffic but is isolated from the private inside network
- To create a security zone that allows private traffic but is isolated from the public network
- Which of the following are types of services that firewalls can provide?
- Content filtering
- Segregate network segments
- Signature identification
- Scanning services
- All of the above
- In which type of test is the testing team provided with limited knowledge of the network systems and devices using publicly available information?
- Blind test
- Double-blind test
- Target test
- Open test
- Which of the following is a vulnerability scanner?
- Network Monitor
- Nessus
- Traceroute
- Tripwire
- Which of the following is not a function of NMAP?
- Perform port scanning
- Identify operating systems
- Collect passwords
- Identify versions of network services in operation on the network
- Changing network configurations, terminating sessions, and deceiving the attacker are actions that can be taken from what type of security device?
- Access control list (ACL)
- Content filtering
- Security zones
- Intrusion prevention system (IPS)
- __________ act on behalf of the whole network to completely separate packets from internal hosts and external hosts.
- Honeypots
- IDSs
- IPSs
- Proxies
- Which of the following cannot be identified by Nessus?
- Unsecured access to sensitive data on a system
- IP address conflicts
- Misconfigurations like open mail relay
- Password issues
- A __________ firewall keeps track of the established connections passing through it.
- Hardware
- Software
- Stateful
- Network
- A(n) __________ learns what is “normal” on the network and can react to abnormalities even if they're not part of the signature database.
- IDS
- Firewall
- IPS
- VPN concentrator