Chapter 13. The Educational Aspect of Security
Sukamol Srikwan and Markus Jakobsson
13.1 Why Education?
While good user education can hardly secure a system, many believe that poor user education can put it at serious risk. The current problem of online fraud is exacerbated by the fact that most users make security decisions, such as whether to install a given piece of software, based on a very rudimentary understanding of risk. To highlight the complexities of user education, we describe a case study in which a cartoon-based approach is used to improve the understanding of risk among typical Internet users, as it relates both to phishing and to crimeware. This educational approach is based on four guiding principles:
A research-driven content selection, according to which we select educational messages based on user studies
Accessibility of the material, to reach and maintain a large readership
User immersion in the material, based on repetitions on a theme
Adaptability to a changing threat
13.1.1 The Role of Education
Online fraud is threatening organizations and individuals alike, and many fear that it might turn into a weapon of electronic warfare within the not-so-distant future. There is a strong consensus that we, as a society, need to improve our resilience against this threat. This goal can be reached using at least three principal approaches: software-based security initiatives, legal and regulatory efforts, and educational approaches. While the approaches are complementary, they are not entirely independent. For example, legal and regulatory efforts are limited by technological issues related to detection and enforcement. Likewise, the impact of client-side software initiatives is affected by educational efforts related to how to use the technology and how to maintain the integrity of deployed software. In turn, regulatory efforts fuel software development and deployment, and recent FFEIC guidance [119] encourages financial institutions to educate their clients.
While technical efforts to fight the problem are proliferating, and legal and regulatory approaches are rapidly catching up, we argue that the development of educational efforts has been left behind. Consumers are faced with a bewildering array of advice about how to stay safe against identity thieves, but we are not certain that any of the efforts manage to communicate a basic understanding of what to do and why. Current advice comes in many forms, from the terse online resources of financial institutions to in-depth self-help books describing how to obtain access to credit reports. Consumers are advised to buy and use paper shredders; they are likewise told to look for icons indicating that sites are hacker safe, use encryption, and are members of the Better Business Bureau. At the same time, the typical Internet user does not know how to identify a phishing email [366], but often relies on checking spelling and identifying known deceit techniques [425]. Many consumers do not realize how easy it is to clone an existing site (e.g., using a tool such as WebWhacker [471]), but rather interpret convincing web site layout as a sign of legitimacy. Similarly, many typical computer users are not well aware of how they may be infected by crimeware and what to do to minimize the risks. It is not surprising that the average consumer has a rudimentary understanding of these threats, both due to the fact that he or she does not understand the intricacies of the Internet, and due to the difficulties of communicating complex notions to users who would rather not be involved at all. To make matters worse, phishing and crimeware have components of both technology and psychology [202, 367], and there is ample evidence (see, e.g., [260]) supporting the contention that most people want to trust what they see.
Security education is not easy, especially when it is targeted at general computer users who may not want to take the time to learn. In this chapter, we explain pitfalls and difficulties of this education and describe how a detailed understanding of these—and of typical user behavior—can help guide efforts. While such improved education efforts can be expressed using a variety of available media, we describe only one particular approach in detail: a cartoon format. This format was selected because it is accessible to a large portion of the population and allows the use of stories to illustrate complex processes.
13.1.2 Why Security Education Is Difficult
We believe that the educational aspect of security has not been given the attention it deserves, and that many skeptics have prematurely concluded that any involvement of the end user is doomed to fail. We hope that an improved understanding of the issues surrounding both online fraud and the ways in which people relate to potential threats may help develop educational approaches with better impact, and that at least some risky online behavior can be significantly curbed. However, the task of achieving this goal is far from trivial, owing to the complexity of phishing, crimeware, and associated threats. The problem is neither entirely technical nor entirely social in its nature, but rather a combination of the two, and numerous security vulnerabilities are associated with this combination.
Current educational efforts aimed at encouraging safe online behavior have limited efficacy. We argue that many educational efforts expect too much of the audience. Namely, many educational efforts aim at a rather technically knowledgeable reader and, therefore, do not reach the typical Internet user. For example, the Federal Trade Commission (FTC) advises people [132] to forward suspect emails with full headers, but without explaining what a full header is or how to view or forward it. Even though everyone with a networked computer has access to information that would allow them to learn how to view full headers, many users may be insufficiently motivated to find and read such information. As another example, APWG [17] advises users that unless an email is digitally signed, one cannot be sure it was not forged or spoofed. However, recent studies [141] have shown that typical users do not know how to benefit from the security guarantees offered by digitally signed email; moreover, most banks are reluctant to deploy technology to sign outgoing messages given their concern that doing so may drastically increase the number of calls made by recipients who are not familiar with signed email. Handling these calls would incur a cost that is believed to dwarf the savings obtained from the increased security. Thus signed emails are not as common as technologists believed they would be; their lack of popularity is also an outcome of the failure to deploy a public key infrastructure on a large scale.
At the same time as many educational efforts may expect users to be savvier than they are, many other efforts over-simplify the message in an effort to make it digestable to a general audience. For example, financial institutions often warn users not to follow hyperlinks in email messages. As of mid-2007, phishers had started to adapt to users being wary of clicking on links, instead suggesting to targeted individuals that they copy and paste URLs into the address bar. Given that no large-scale effort has warned against this particular attack, the new twist may very well be rather successful. The use of this trick by phishers also illustrates the need to teach people not only simplistic rules but instead to explain why one should or should not do a particular thing. Having a true understanding of the threat will help people adapt to changes. Thus, to create a lasting impact of the educational efforts, it is crucial not to teach people to recognize known phishing attempts, but instead to recognize the patterns behind them. This allows people to generalize and truly understand, but takes an even greater effort—on behalf of both the educator and the user.
Some overly simplified educational messages may elevate the risks to which compliant users expose themselves. As an example, consider the suggestion “you should communicate information such as credit card numbers or account information only via a secure web site or the telephone” [17]. While this advice would reduce the vulnerability to many attacks that are commonplace at the time of this writing, it may also increase people’s vulnerability to vishing (or voice phishing) attacks, and to phishing/vishing hybrid attacks in which the user is sent an email that advises him or her to call the impersonated service provider using a number supplied in the email. This type of attack may become more common if takedown efforts become increasingly effective.
This example shows that some advice may cause problems if users follow it without much critical thought, which in turn suggests that simple rules may not be suitable for education if an attacker might potentially try to leverage the approaches used by the educational campaign. Thus phishing education may be harder to implement than other types of education, because it requires users to act against a threat that in itself is molded by what users understand. While software can be constantly patched to harden it against an evolving threat, it is more challenging to reeducate users to counter such changes.
Coming back to the conflicts between too demanding education and overly simplified education, we see that at the heart of the dilemma is the fact that simple rules do not capture the problem well, whereas complex rules do not captivate the audience. It is not easy to explain complex problems to users who often will not be highly motivated to learn until they have already suffered a bad experience. In addition, most people think they are being reasonably careful, and we all like to think that bad things happen to others only. As a result, current mainstream efforts do not attempt to cover advanced topics, recognizing that the typical user would be unlikely to spend enough time to understand anything but the basics.
For example, while research [200, 425] has identified a common inability to distinguish legitimate domain names from those used in cousin-name attacks or subdomain attacks, these topics are rarely addressed in educational efforts targeting typical Internet users. Examples of deceptive URLs of these types are www.citibank-secure-commection.com and www.chase.pin-reset.com, both of which have been shown to inspire confidence among typical users [425]. The same study showed that short URLs inspire more confidence than longer alternatives. There are plenty of examples of unnecessarily long URLs, and we do not even have to go beyond our bibliography to find such examples [51].
Another example of a neglected topic with high security relevance is malware. While almost all educational efforts indicate the importance of having up-to-date antivirus software installed, typical service providers fail to explain the complexity of malware to their clients or suggest ways to defend themselves against the threat. As an example, most people do not fully appreciate that software they opted to install—maybe because a friend suggested to do so—could, in fact, be malware. This is a serious security concern: A recent study [388] demonstrated a yield of more than 50% for one particular type of socially propagated malware attack.
A problem that exasperates those who focus on educating users about security is that it is not sufficient to explain the problems to the target audience; instead, users must also change their behavior. An oft-ignored point is that there is a tremendous discrepancy between what typical users know and what they practice. An example of this is illustrated by the recent studies involving eyeball tracking [477], in which it was concluded that most users rarely look for SSL indicators, much less choose to interact with them. Even so, most people understand that there is an association between security and the presence of an SSL lock. To make matters worse, many phishing attacks use SSL [387], so teaching users to look for an SSL lock may not be the best approach. Security education has to highlight the need for behavioral changes. We believe this is best achieved by illustrating the causality between behavior and security outcome, a task for which the cartoon format is well suited.
Many educational efforts—and in particular those employed by financial institutions—offer highly concentrated advice, often in an itemized format. While the material is correct and almost always constructive, it explains what to do as opposed to what and why. As such, it may be a better resource for users who already understand the problem than for the larger masses who do not. We think of this type of resource as a dictionary. Whereas no one would attempt to learn a new language from a dictionary alone, dictionaries fill an important role for people with a reasonable background and understanding.
Most existing techniques are best suited to deal with a static threat, which phishing arguably is not. There are several reasons for this preference. For instance, while it is easy to patch software frequently, it is not easy to convince people to educate and reeducate themselves on an ongoing basis. As a consequence, educational efforts must be able to deal with a changing threat (which may adapt to the educational message itself) without relying on constant updates of the material. Such updates are unlikely to be absorbed by the target audience in a timely manner. (While financial institutions, for example, could provide their clients with updated advice as often as they wish, such a move could backfire by breeding fear and prompting people to withdraw from online banking.) Game-based approaches, while being desirable to a large group of users, suffer from a high development cost associated with structural changes that may be necessary to address new topics and changing threats. In comparison, cartoons are lightweight enough to permit integration of new material at a low cost. Both games and cartoons can be designed to avoid the intimidation factor from which lists of abstract “dos and don’ts” typically seem to suffer.
While it is commonly agreed that typical Internet users do not fully understand how to stay safe against phishing, it has also been shown that available training material is surprisingly effective when used [223]. A reasonable conclusion one can draw from this finding is that typical consumers do not make sufficient use of available material. To entice the typical banking client to spend hours instead of seconds learning about security, it is necessary to make the educational message both accessible and enjoyable. This chapter describes a cartoon-based effort [386] aimed at reaching this goal as well as the campaign’s underlying design principles. These relate to the manner in which material is selected, how the material is made accessible to a typical reader, and how repetition on a theme is used to create an immersion approach.
13.1.3 Some Existing Approaches
A growing body of literature has focused on trying to educate typical users of threats. Consumers are offered a range of books (e.g., [2, 18, 61, 129]) explaining identity theft, ways to stay safe, and means to recover from this kind of attack. These books often focus on a taxonomy of the common scams—for example, what happens in a 419 scam and why one must secure wireless networks. The exposition requires a fair amount of dedication from consumers for them to make substantial progress.
A variety of online resources are aimed at improving the public’s understanding of risk. Banks (e.g., [51, 54]) and companies such as eBay [92], Microsoft [255], and PayPal [304] also supply their own pages to warn users about the dangers of phishing and steps to avoid falling prey to these ruses. Pages such as eBay’s Spoof Email Tutorial [93] teach basics about email spoofing as well as technical details regarding URLs and domain names, but with a very clear emphasis on recognizing spoofs on eBay and with a focus on commonly existing psychological twists only. PayPal [303] allows users to take a five-question test that is intended to identify risky behavior, but it is likely that a large portion of users get the highest score. This is not only due to the simplicity of the questions, but is also the result of the subject-expectancy effect—the cognitive bias that occurs when a subject expects a given result and, therefore, unconsciously manipulates an experiment or reports the expected result. There is a risk that users taking the test come away feeling overly confident of their abilities, rather than slightly humbled and intrigued to learn more.
Most financial institutions maintain a list of recommendations, typically in bullet format and fitting on one page. The advice is useful, but seldom communicates any understanding of why it is useful. It has been criticized as not being a helpful educational tool [70]. As such, the advice may often be ignored or forgotten, especially under duress, which is a commonly used approach of phishers. Apart from banks, many nonfinancial service providers also provide guidance. AT&T maintains sites [21, 22, 23] that stand out for having a larger degree of interactivity than most, which is believed to promote learning.
A recent academic effort [373] attempted to teach phishing awareness to a general audience using a computer-game–based approach; this approach shares the third design value (accessibility) with our approach, but achieves this goal in a different way, and using true user interaction. We believe that the game-based approach may have many benefits, but that it may fall short in that it may reach a somewhat limited demographic at this point. In related efforts, AT&T [21] and NetSmartzKids [273] use games to teach Internet security to children, and Hector’s World [168] uses animation to reach the same goal.
Another approach that relies on user interaction to assess risks is the phishing IQ test [244], which scores the user’s ability to recognize phishing instances. This approach, which can be thought of as an indirect educational approach, has been criticized for not measuring the ability of the test taker as much as his or her fears of phishing [8]. Embedded education [222] teaches people about phishing during their normal use of email.
Several movie-based efforts have sought to teach security awareness (see, e.g., [264, 460]). These particular examples are highly technical and are accessible only to expert audiences. Other movies [265] are easier to access but relatively brief and, therefore, communicate only a rather limited understanding of the threats and associated countermeasures. The prospect of the extensive effort required to use a movie format to communicate threats appears to offer this approach’s significant benefits.
Some educational efforts [372] cover slightly irrelevant educational messages, such as encryption over wireless networks. While encryption is helpful to avoid eavesdropping, it is not a form of access control and does not secure the access points that use it. It is not clear that the educator always has a clear understanding of the threats. This is a pity, given the recent wealth of insights into the nature of the problem of phishing. In particular, there have been several recent advances toward understanding how typical users react to deceit [87, 125, 126, 202, 425, 481].
In this chapter, we describe how cartoons can be used as the main medium of communication. Graphical representations have unique advantages, given that words have context only in the culture of the speakers. That is certainly true when it comes to communication of technology-related messages. Scientists are lost in their own subculture-based vocabulary. In contrast, the concept that “A picture speaks a thousand words” has been used in numerous settings to communicate educational messages of importance. Historical, political, and social issues have all been expressed via editorial cartoons in newspapers and magazines for more than 150 years [286]. Very few people, regardless of their culture and nationality, would not recognize a picture of a soldier and a tank and the associated concept of war. Such images inspire alertness and worry to most people, young or old, a fact that highlights the notion that humans are visual by nature. Our minds cannot avoid making associations between images and experiences. Cartoons can be drawn to enhance specific messages while suppressing others, which provides an excellent tool for communicating complex concepts. A simple cartoon is a form of amplification through simplification [246].
HIV/AIDS education using cartoons was done in the New York subway system for a long period of time, in a way that was very clearly targeted to teenage readers. Copyright law is taught using a cartoon approach [15]. Teaching security, however, is slightly different from teaching other topics since—given the adversarial setting—one must assume that the adversary has access to the same educational material and will do his or her best to find ways of taking advantage of the way material is (or is not) taught. This must be a consideration when designing the educational effort: The effort may, in itself, change the nature of the topic associated with the education.
Some material intended to help the public better understand the threats associated with identify theft focuses on server-side issues and does not make recommendations to the reader [5]. While there may be no direct modification of behavior as a result of this kind of campaign, it may help bring the problem to the attention of the general public, which may in turn facilitate legislative efforts. This is another important role of education.
13.1.4 Some Problems with Practiced Approaches
Following the principle that we learn from our mistakes, we review some common drawbacks associated with mainstream educational techniques. We classify these disadvantages into general categories, and give examples to help make these categories concrete.
A sidebar from a phishing education effort in the Reader’s Digest [372] provides tips for “Beating the Thieves”:
• Install security software and stay current with the latest patches.
• Always be suspicious of unsolicited e-mail.
• Monitor the volume and origin of pop-up ads. A change may signal something sinister.
• Visit the FBI’s new website lookstoogoodtobetrue.gov, for tips.
• Use debit cards like credit cards, i.e., with a signature, not a PIN code.
• If you live in one of the 20 states where it’s possible, place a freeze on credit reports. This stops any credit activity in your name unless you specifically initiate it.
• Keep an eye out for “skimmers” lurking in places where you use cards.
• Enable encryption on wireless routers immediately upon setting up a home network.
• Shop only on secure websites (look for the padlock or “https” in the address bar); use credit, not debit, cards; don’t store financial info in an “account” on the website.
However, a user who is nervous about software security patches, and who does not have a solid understanding of what a patch is and what it is not, may be tricked into installing undesirable software that claims to be a patch. In this case, it might instead be better for users to learn how to configure their computers to perform automated patching. Or perhaps it would have been more useful for the Reader’s Digest list to explain the more complex picture of malware.
Similarly, while it is good to be wary of unsolicited email, the typical user receives contradictory advice in the form or large quantities of legitimate but unsolicited mail—sometimes even from the same institution that asked the user to be suspicious in the first place.
The third listed piece of advice (above) is well-meaning but hard to follow for the typical user. How does one monitor pop-up ads, and what should be done if there is a drastic change? Later, the user is encouraged to enable encryption on his or her router, but much more important advice would be to set a strong password.
Advice That Is Hard to Follow. Many current educational efforts suffer from giving advice that is hard to follow and that may, as a result, become entirely redundant at some point. An example of this type is the common piece of advice, “Do not click on links.” Almost all companies with an Internet presence send email with hyperlinks. Many send unsolicited emails, and a large number of them send such emails to users who have not signed up for their services. The advice not to click on links is helpful to security in some instances, but following it would hamper the web browsing experience for many users.
Similarly, consumers are often advised to disable JavaScript. This, too, is advice that is hard to follow, given that web 2.0 applications rely on it being enabled. Consequently, more than 95% of all Internet users have JavaScript enabled.
Another example of advice that is hard to follow, taken from [368], suggests to the user to “Disable JavaScript or do not visit untrusted and trusted web sites at the same time.” Whereas many users would be able to identify a clearly trusted site (say, their bank) as well as many clearly untrusted sites, few would be able to correctly identify randomly chosen sites. Almost no one can determine whether a site is trustworthy before actually having visited it.
Valid but Not Very Important Advice. Some advice is valid, but not very central to the security of the user. If we believe that there is an abundance of important advice to be given, and that the typical user can retain only a given amount of information, then this type of advice would amount to a lost opportunity. An example of this kind of advice is given in Reader’s Digest [372]: “Enable encryption on wireless routers immediately upon setting up a home network.” While this step protects against theft of service, it has little impact on the greater problem of phishing and is probably entirely overshadowed in terms of importance by a piece of advice that is not given: “Select a good password for your router immediately upon setting up a home network. Never use the factory-set password, as strangers on the Internet can easily look this up and access the security settings of your router.” Typical Internet users are unaware of this threat and do not know that if their router becomes corrupted, it can steal passwords, mount pharming attacks [425], and block access to antivirus software updates [389]. Most users do not realize the ease with which a router can be infected [389, 425, 426].
Potentially Dangerous Education. Some advice may be both valid and important, but still pose a potential risk to users. In Reader’s Digest [372], the reader gets the following advice: “Install security software and stay current with the latest patches.” However, the reader is not told how to practically follow the advice and may become more vulnerable to an email that tells the user to install a given security patch. If such an email is spoofed to appear to come from the system administrator, then it may appear fully reasonable to many users to quickly install the required “patch.” To make sure that the advice does not pose a risk to the user, it may sometimes be important to qualify exactly how to follow the advice and what not to do. This is particularly important given that phishers are likely to try to take advantage of habits that their intended victims have been trained to acquire. Another example of this type is to ask users to look for an SSL lock, implicitly equating its presence with security. This is a problem given the ease with which phishers can also use SSL [387].
If we see the creation of habits as a form of education, then another example of potentially dangerous education is a technique that financial institutions commonly use to authenticate themselves to their clients. Namely, many financial institutions authenticate themselves to clients by including “Email intended for your account ending in: XXXX” or a similar text in email communication. As has been shown elsewhere [425], most Internet users do not find a statement such as “Email intended for your account beginning with: XXXX” less trustworthy than a statement such as “Email intended for your account ending in: XXXX” in spite of the fact that the four first digits are possible to infer from the identity of the issuer (a fact that will not be lost on the phisher). Therefore, training users to accept the “last four” as a form of authentication makes them vulnerable to an attack in which the “first four” is used—at least in the absence of a carefully crafted educational campaign aimed at addressing this potential problem.
Advice That Is Not Absorbed. The most significant problem of many current approaches, though, might be that they do not entice the intended readership to spend considerable time and effort understanding the messages. A recent study [223] found that existing phishing education succeeds in communicating important security information, if accessed. The last point is the gist of the problem: Typical user education is not accessed by the typical consumer or is, at the very least, not given hours of attention and afterthought. We argue that many currently used approaches for teaching Internet security to typical consumers are analogous to a ski lesson in which there is no practice or feedback, but where the lesson consists of a single message: “Don’t fall.”
13.1.5 Educational Goals
The educational mission can be formulated, quite simply, as “Help typical users improve their security against online threats.” This is not quite as straightforward as it may seem, but can be broken down into four partial goals.
Goal 1: Know Your Audience. It is important to understand what the typical user’s limitations are—in terms of both what he or she knows and what he or she can reasonably be taught. As we have argued, it is a common mistake to expect too much from the user or to expect so little that the resulting educational message is reduced to sound bites.
It is tempting for security specialists to guess which problems typical users may have based on which problems they themselves perceive. This, however, is a fallacy, and one that led many to believe that the existence of SSL would lead to the failure of phishing as soon as awareness of the problem rose. User experiments, while often challenging to perform [121], provide a better understanding of the likely vulnerabilities.
Goal 2: Know Your Enemy. It is equally important to recognize what the threats are and what they may become. Namely, it is not helpful to secure users against only current threats, given the proven malleability of the threats. To understand the threats and their likely development, it is crucial to recognize that they have both a technological component and a human factor. The educational effort, too, must take both of these aspects into consideration.
Knowing how typical users relate to both user interfaces and deceit helps to anticipate potential trends in phishing. This can also be done by formulating technological hypotheses, from which one may infer the likely resulting threats. See [198] for an example of this approach.
Goal 3: Know How to Tell the Story. A third goal is to enable communication of insights. To make this possible, the material to be taught needs to be accessible. Many researchers agree that security is not a primary goal of the typical user (see, e.g., [257]). The educational technique must take this factor into consideration by making the material accessible to the target audience. This is closely related to the admonition to know one’s audience.
Goal 4: Know How People Learn. A fourth and final goal is to facilitate learning. It is not sufficient for the educational material to be appropriately selected and communicated, because learning is not an instantaneous process. To maximize the benefit of the material, repeated exposure is necessary, and the material must be designed with this consideration in mind.
13.2 Case Study: A Cartoon Approach
The approach we describe here is exemplified in Figures 13.1 to 13.4, and is based on the four core principles presented above.
Figure 13.1. This cartoon is intended to increase the understanding of URLs, which is a difficult topic to teach. Typical computer users do not understand the difference between domains and subdomains and are easily fooled by cousin-name attacks, as supported by [200]. None of the large financial institutions attempts to teach its clients about URLs, despite this subject being an important topic for people to master to stay safe. One reason might be that URLs are complex, and an exhaustive set of rules describing their nature would be daunting for the typical consumer. The strip shows four Chase web pages in a line-up. Readers are asked who robbed them, forcing them to start comparing web pages. The only real differences between the web pages are the URLs. This cartoon is intended to reinforce the notion that copying logos is a functionality that is not beyond the reach for phishers, and to force readers to start comparing the URLs.

Figure 13.2. This cartoon strip shows how easily readers can be updated about recently occurring threats. This strip was developed in response to a wave of malware attacks that occurred in the late spring of 2007, where the recipient of the email was enticed to download content on the premises that it was a postcard from a friend. As described in [39], the attack vector involved both technical and human vulnerabilities in some instances, making this a rather sophisticated attack. Many educational efforts do not warn users against this type of threat, as they often warn users about emails sent from strangers—an email like this one is interpreted by many users as being sent (or at least initiated) by a friend. This is also an example of how attackers are likely to design attacks based on the contents of current educational efforts.
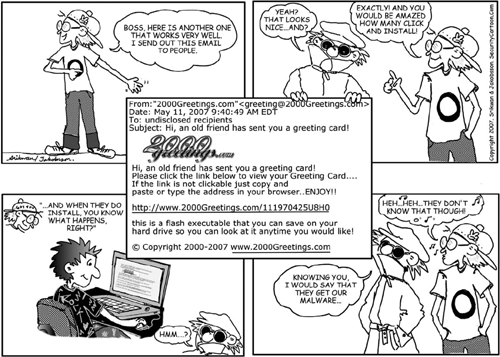
Figure 13.3. Most people are not willing to change their behavior unless they are given a good reason. Therefore, it is not enough to warn people about threats and say what they should and should not do. It is also important to explain what happens if they do not. This strip shows what happens to a victim of a keylogger (identified by the tentacled creature sticking out from his keyboard) and is a continuation on a sequence of strips in which keyloggers are introduced and the victim is infected by one.

Figure 13.4. Many educational efforts focus on what to do and what not to do, but neglect to describe why. As a result, people draw their own conclusions, which sometimes leads to a degraded security awareness. This strip attempts to highlight one of these issues in the context of the configuration of home routers. Research [426] shows that less than 50% of consumer routers have been configured correctly, corresponding to a notable practical security vulnerability in the context of potential attacks such as the drive-by pharming attack described in Chapter 6 or the trawler phishing attack described in Chapter 5.

Research-Driven Content Selection. The educational material is tailored based on an understanding of actual user behavior, as observed in a collection of studies. For example, it has been shown that average users know that an IP address (instead of a regular domain name) signals danger, but do not have any understanding of the risks of cousin-name or subdomain attacks [200]. Similarly, another study showed a success rate of more than 50% for a simulated attack in which victims received an email from a friend in which they were told to run a program with a self-signed certificate [388]. This suggests that typical users do not distinguish well between trusting their friend’s taste and trusting their friend’s ability to identify a threat. Correspondingly, our approach describes both user-propagated threats and the risks of user-installed programs having malicious content.
Accessibility. It is important to design the educational message in a way that does not alienate or bore the intended readership. Combining warnings with explanations and a “role playing” of consequences allows the reader to gain an intuitive understanding of why to follow given advice. We believe that this knowledge is important for a long-term adherence to the educational message. We let our educational message be framed as a cartoon, to avoid a compact “textbook” feeling, and to help the user identify with the characters in the story. We must remember that phishing education—and the exposure to it—is voluntary. Unless a given reader is highly motivated (which is not common), then the educational medium must make it easy to keep reading.
Immersion. To reach the desired results, we believe that the same message—framed in slightly different ways—needs to be repeatedly communicated to the reader. It is not enough to understand a concept once; the reader needs to practice acting in accordance with the message as well. This requires insight and understanding. This type of learning cannot be achieved simply by repeated use of one and the same message; instead, minor variations are necessary to retain the reader’s interest. This principle is fully aligned with how other material is taught and learned: Addition and subtraction, for example, are learned by practice. Knowing the theory alone would not allow many people to obtain the skills needed to do arithmetic.
Adaptability. To help defend against a changing threat, it is important to be able to reflect changes rapidly and to communicate recent trends in a manner that allows for quick adoption of new practices. Cartoons permit this to be done, given their relatively low production costs. Furthermore, based on the accessibility and immersion principles, new advice will reach the target audience relatively quickly.
Conclusion
Existing educational approaches to improve secure behavior or the Internet may not be designed with the intended audience in mind. We have put forward a collection of techniques we believe may be useful in improving security education, and given a cartoon-based example of an approach embodying these suggested techniques.
