3
Cyber Crime Tools You Won’t Believe
In Chapter 1, “Cyber Stalking,” we showed you how a GPS (Global Positioning System) can be used for tracking people, but there are many other techniques and devices that can aid an avid stalker.
Wi-Fi Tracking
Would it surprise you to know that your own computer could provide a means of tracking you? Most newer computers, especially laptops, are Wi-Fi (wireless) enabled, meaning you do not need any cables to connect to the Internet. If someone has had access to your computer and knows your computer’s name (“Mary Smith’s Laptop,” for example), they can easily listen for your broadcast signal within a few hundred meters to ascertain your whereabouts.
Packet Sniffers
Beyond locating you via your computer, someone with a program such as a packet sniffer can actually grab the data you type and read it if it is unencrypted, within proximity. When you type on a wireless Internet connection, the computer sends the information through the air in small groups of data, called “packets”.
A packet sniffer program sniffs the air much like a dog lifts its snout to find a scent. Such programs are readily available on the Internet, often for free. Packet sniffers can be fine-tuned to listen for keywords such as “login” and “password” to gain access to account information. In fact, packet sniffers have become quite specialized and can be used for sniffing specific types of traffic, such as MSN messages and live chats (see Figure 3.1).
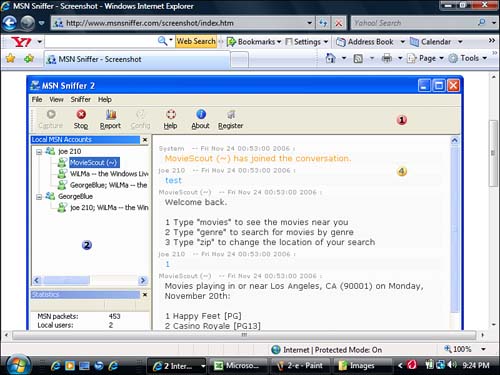
It should be noted that packet sniffers have a legitimate use in information technology—to determine network traffic—but too often they are used for illegitimate purposes. They can also be used on a hard-wired network to sniff out data. (Read more about wireless networks in Chapter 16, “Your Online Safety Checkup.”)
Bluetooth Locating
Bluetooth is another means of connecting devices wirelessly. Your cell phone and laptop may be “Bluetooth enabled”. Bluetooth differs from Wi-Fi in that it broadcasts a stronger signal covering greater distances and is more expensive. Most Bluetooth applications have default security settings. If someone knows your device name, they can sniff for your device location to within 50 to 100 meters.
What Is an IP Address?
Given the millions of computers in use and online at any given moment, how does your computer know to deliver your email to Aunt Mary, who lives in Massachusetts?
There are probably hundreds, if not thousands of computers called “Mary’s Computer” online at any given point in time. So how do things get routed and tracked on the Internet? Think about the last time you sent or received a package from UPS. Do you remember the driver using a scanning gun to scan the package’s barcode? Barcodes are symbols that represent information such as the street number and name where the package is to be delivered. This barcode system allows UPS to track millions of packages around the world each day in real time via a quick scan, rather than having to manually reenter the destination address or the originating location each time.
Along those same lines, computers also use a numbering system to ensure that messages get routed to the appropriate place. That number is called an IP address (or Internet Protocol address).
Every time your computer connects to the Internet, it takes on an IP address. An IP address is temporarily assigned to a computer as it connects to the Internet by your Internet service provider (ISP). You usually don’t see this address and probably don’t know it’s there, but it is. The entire Internet uses this same numbering scheme, so when you type in www.nasa.gov to visit the NASA website, the computer thinks 72.246.51.15, which is the actual IP address of the NASA site. Obviously, www.nasa.gov is much easier to remember. All of this translation of IP addresses happens in the background and is transparent to the user.
When you send an email to Aunt Mary, it gets routed correctly because it knows Aunt Mary is actually [email protected], and Yahoo! has a preset list of IP addresses, which are like ZIP Codes in a sense. Yahoo! also knows which account holder is “best auntie” and makes the delivery accordingly. All of this routing and IP address information is contained in a part of the email called the “headers,” which most people usually don’t see. In order to see them, you must enable “full headers” on your incoming email.
Here’s how a cyber stalker might use the information gained in the email headers to further his or her efforts:
I now have the internet addresses of your computer and your Internet Service Provider (ISP). This minimally gives me something else to key a web search on, where no matter what email aliases you were using, I can find emails or other postings originating from your home system. And of course more information for more next steps. I would also take all the IP addresses and decode them at a website like http://www.dnsstuff.com/ or http://remote.12dt.com/rns/ to see what it tells me about the service provider you’re using.
It’s frightening to think that someone with a little savvy can gain so much information about you just by reviewing the headers of your email. However, the reality is that it is possible, and this is something you need to be aware of prior to clicking the Send button.
Anonymizers and Anonymous Remailers
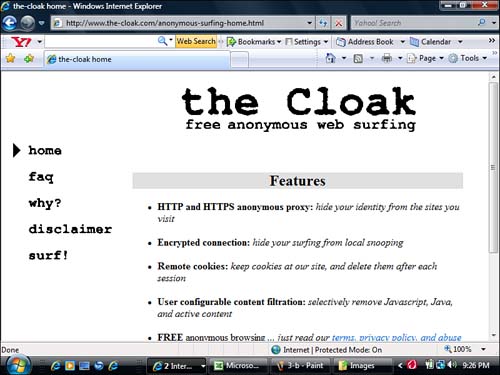
Anonymizers are programs, often available on the Internet for free, that claim to protect the privacy of someone surfing online or sending email (see Figure 3.2). They can also be used for more nefarious deeds, such as sending offensive emails and avoiding being traced.
Figure 3.2 The front page of an anonymizer site called “The Cloak”. Many variants of this site are available on the Internet.
Whereas the main function of anonymizers is to cloak Internet usage, anonymous remailers are programs that are specifically meant to strip the header information away from email and replace it with information that is untraceable.
Closely related to anonymizers and anonymous remailers are online websites that provide temporary email addresses that virtually disappear in as little as 15 minutes, leaving little trace of their existence behind (see Figure 3.3).
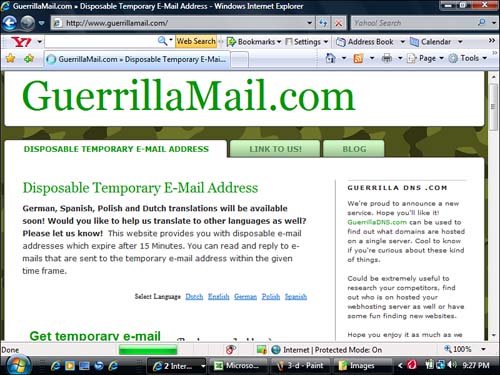
An important point to understand here is that nothing is really ever truly “anonymous” when you are on the Internet. At some point, there is a trail that, to some degree, can be traced back to you. Let’s say, for example, someone uses one of these anonymizer programs to visit a site containing sexually explicit images of children, which they then proceed to download.
First of all, a connection to the Internet must be established. If that person is sitting in the comfort of his home, he has an account with some company to connect to the Internet. Even if he is on a public Wi-Fi account, connection information is still being recorded somewhere. We will talk a lot more about the horrors of child sexual exploitation later on, but bear in mind that whenever you download something to your computer—an image, a file, or a program—it is very likely to be retrievable even if you delete it.
Second, even though many anonymizer sites claim not to keep records, there are logs that, if the site is based in a country subject to warrant searches, may be produced.
Finally, if any site raises suspicions as a target for potential illegal activity, it’s an anonymizer site. Don’t think for one second that local law enforcement hasn’t already figured that out and that it wouldn’t raise suspicions to see that someone went to an anonymizer site (because a trail of the actual site visit would still be there).
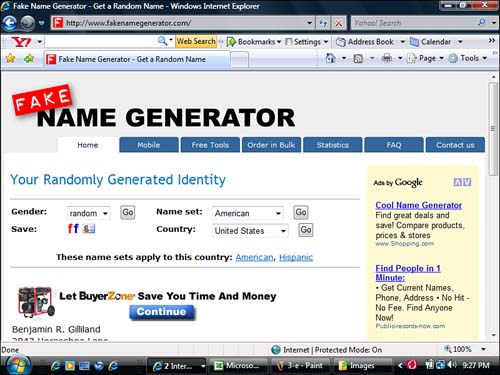
Fake Name Generators
The site shown in Figure 3.4 not only provides fake names, but fake addresses, social security numbers, credit card accounts, and so forth. Although this information is false, someone could use the site to very quickly come up with a false ID if they knew that the information wouldn’t be checked immediately. The site has been touted by writers who are looking to make up character names and identities, but law enforcement deals with too many people giving false identification. This site makes it a lot easier.
Figure 3.4 Screenshot from www.fakenamegenerator.com. According to the website, up to 100 fake names are generated a minute.
Fake Caller ID
Another type of software allows Caller ID to be faked or “spoofed”. Most people think if their Caller ID reads “XYZ Bank” that, in fact, the call is legitimate. This is not necessarily true. Caller ID spoofing is purported to be a “fun way to fake out your friends,” but clearly the opportunity it presents for criminal activities is rampant. In fact, it’s become key to attempts at defrauding people via their cell phones. This type of fraud is known as “vishing.” (See Chapter 11, “Phishing, Pharming, Spam, and Scams.”)
Felicia had an unusual, and not so pleasant experience, as a result of this type of program.
The ability to change Caller ID has led to an extremely dangerous new prank called “swatting”. The term is derived from police SWAT (Special Weapons and Tactics) teams. The goal of swatters is to falsely report an emergency to a police department to cause a SWAT team response to a physical address. Caller ID spoofing just makes it that much easier for someone to claim she is someone else and that a dangerous person is inside her house with a weapon. This dangerous prank not only puts innocent people, the people at the actual address, in extreme danger, it puts law enforcement in danger as well because they have no idea what they are facing.
Think swatting sounds like fun? Just ask Jason R. Trowbridge of Houston, Texas, and Chad A. Ward of Syracuse, New York, who each just recently entered guilty pleas to “conspiracy to commit access device fraud” and “computer intrusions in furtherance of harassing and swatting telephone calls”. They each face a maximum statutory sentence of 5 years in prison, a $250,000 fine, and restitution.