No matter what computer you use to access the Internet, here are the three most important steps you need to take to ensure protection:
1. Always keep your system up to date with automatic updates and patches to the operating system.
2. Install virus protection and make sure it is updated.
3. Install a spyware and/or malware detection program and run it frequently.
When your system alerts you that updates are available, install them immediately. They often contain important security patches. Every day, software companies such as Microsoft are notified of security vulnerabilities. Depending on the severity of the vulnerability, they generally package all the updates and fixes into one update and release it, usually on what has come to be known in the industry as “Patch Tuesday”. It is imperative that you keep your system and any other software you use up to date on security patches.
If you use a Windows-based computer, you should have Automatic Updates running. If you don’t, go to Control Panel, Security Center and turn on this feature. For nontechnical users, set this feature to automatically update the patches at a time you know your computer will be on. If you’d prefer, you can manually install the patches, but the important point is to make sure you install a patch whenever a new release is available. The 5 minutes or so it takes to install a patch and reboot your computer is time well spent if it shores up a security hole. Remember that cyber criminals are counting on you not staying current with the updates. Malware and viruses can propagate across the Internet in a matter of hours. It takes the same amount of time for malicious code to attempt to access your computer by identifying security vulnerabilities. Keep the system patched!
According to a 2005 study, 81% of home computers lacked “core” protection (source: National Cyber Security Alliance 2005 Online Safety Study). We hope that number has since improved.
Computers are often shipped with a demonstration (30-day free trial) virus protection program. After the 30 days, you need to subscribe to continue receiving the protection. Most of these programs average $30 to $50 a year. This money is well spent to ensure against computer viruses that can completely wipe out your system or make you vulnerable to credit card fraud or identity theft. A single virus that attacks the system can render it useless. It’s not worth the risk when the cost of prevention is relatively inexpensive.
We recommend Symantec AntiVirus (www.symantec.com) or McAfee Antivirus (www.mcafee.com) for baseline protection. These are the industry-standard programs.
If you cannot afford either of these programs, you can install AVG Anti-Virus (www.grisoft.com) for free, but get something on your computer to protect it against basic viruses.
An antivirus program is only effective if its files are kept updated. New viruses are introduced every day that propagate across the Internet rapidly. It’s almost pointless to have a virus protection program installed if you don’t keep it updated. Each virus has a “signature”—a small line of code that identifies it—and that’s what the virus protection program looks for. Make sure your virus program is set to automatically update itself whenever a new release is available.
Two of the most effective tools at combating spyware and malware remain free of charge. We highly recommend you install SpyBot Search & Destroy (http://www.safer-networking.org) and/or Ad-Aware (www.lavasoft.com) and run them regularly. These programs will search for keystroke loggers and malware, remove unnecessary cookies, and alert you to any suspect programs. When running the free versions, we recommend you clear all your cookies first to speed it up (in Internet Explorer select Tools, Internet Options and click Delete Cookies.) Run these programs on a regular basis—weekly if you can.
We recently came across Malware City (www.malwarecity.com), which is a portal on software producer BitDefender’s website (www.bitdefender.com). It looks like a game, but is actually filled with the latest information and news related to malware. We mention it because it is not only entertaining, but rather informative. We’re not advocating software, just suggesting its interesting features could help keep users wanting to learn more. The site is meant to appeal to the young popular gaming culture and offers opportunities to join the site as a contributor to the “wise warriors fighting malware”.
StopBadware.org is a partnership between academic institutions, technology industry leaders, and volunteers that aims to educate and reduce the amount of malware, or what they refer to as “badware”.
A May 2008 report issued by StopBadware.org found that almost half the websites that “push” malware are hosted by just 10 networks. This means that most of this malware is coming from just a few highly organized places. The report also indicated that six of the 10 hosting networks were based in China.
We cannot emphasize enough the importance of using strong passwords, which means at least eight alphanumeric characters (that is, a combination of letters and numbers).
Here’s a list of what you should never use for a password:
• Blank (no password)
• The word password, passcode, admin, or a derivation
• Your name or login name
• The name of your significant other or another person
• Your birthplace or date of birth
• A pet’s name
• A dictionary word in any language
• Your automobile’s license plate number
Programs are freely available on the Internet for download that can be run against a password list and crack a password in a matter of minutes. When doing forensic examinations of computers, we sometimes come up against password-protected files or folders. These programs have a special feature that allows the investigator to build a potential password cracker.
The investigator “feeds” the program with potential passwords, such as birthdates, kids’ names, dog names—whatever can be gleaned during the course of the investigation. The same types of tools are, unfortunately, available to the bad guys as well. So, please, never use a “real” word as a password.
How can you create a secure password? It’s actually much easier than you think.
Think of a phrase you can remember. We’ll use “Mary had a little lamb whose fleece was white as snow” as an example. Now take the first letter of each word—MHALLWFWWAS. That’s 11 characters, which is a good length for a strong password. Note that some passwords are restricted to eight characters, so this would have to be truncated. Using MHALLWFWWAS, substitute some numbers for letters. We’ll use the number 1 for the letter L. Now the phrase reads MHA11WFWWAS. We could also use upper and lowercase letters because many password programs are case-sensitive: mha11wfwWAS. Hum the song in your mind a few times and emphasize the last three words to remind yourself they are uppercase. Do it a few times and you’ll quickly remember which ones are uppercase. That’s a pretty good password, and because you know the original phrase, it’s easy to remember.
It’s not atypical to have half a dozen or more accounts to log into these days. Between professional and personal email, bank accounts, credit card accounts, college accounts—the list is endless. However, you should never use the same password for more than one account!
If your password is inadvertently gleaned in one application, you could be giving data thieves access to all your accounts. It’s always better to use different passwords, but then how do you remember eight different passwords for eight different accounts? That’s easy. Change your base password up. Let’s go back to our final passphrase (remember it?): mha11wfwWAS. If you want to use it for eBay, you could change the first letters to “EB,” so the password would be “EBha11wfwWAS”. If the password is for American Bank, it would be “ABha11wfwWAS”. The important thing is that each password is slightly different. That’s pretty easy if you think about it. Just change up one important keyword in the phrase and you’ll remember to substitute each time.
Table 16.1 is an interesting chart showing examples of passwords and the time it would take to crack them.
Table 16.1. Time to Crack Passwords
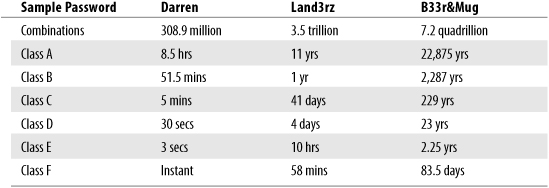
Note that most personal computers these days are fast, with dual processors, and could perform a Class D attack. A more organized group would have Class E capabilities. A supercomputer would be categorized as having the capability to perform a Class F attack.
A number of online tools are available for maintaining your passwords in encrypted form, some of which are free from download sites. We’re not particularly keen on these types of programs, but they’re probably better than using the feature in Internet Explorer called “AutoComplete,” which stores passwords, including those for your bank and credit accounts, so you don’t have to reenter them when you go to their websites. We always shut off this feature on any computer because we do not want anyone who might gain access to the computer, either directly or remotely, to be able to access private account data without being prompted for a password.
When we think of passwords being discerned and people getting unauthorized access, it’s natural to think of potential crimes such as identity theft and credit card fraud, but there are many other instances where access to passwords has led to more “juvenile” crimes.
There have been many cases in which either individual schools or entire school districts have been hacked into by students. In fact, if you visit www.youtube.com and search for “school hacked,” you’ll see several videos documenting this. In Santa Clara County, California, students hacked into their school system to get a sneak peek at their upcoming final examinations. In April of 2008, six students from a San Diego area high school were suspended for hacking into their school’s computers, changing their grades, and obtaining advanced copies of exams. The students allegedly used software downloadable from the Internet (likely a keystroke logger) to obtain passwords from teachers, which then gave them access to restricted files and programs. The files were stored on a flash drive, which was discovered by a teacher when left in one of the computers.
Wireless routers have become quite popular for home use, but they continue to present a security vulnerability if they are not configured properly.
Every day we read cases about people who set up their wireless access point (Wi-Fi router) with the factory-default settings. This is like leaving your doors unlocked at night and allowing someone to come into your house and steal your possessions!
“I don’t mind if my neighbor’s kid borrows my connection to play online games,” you may say. That’s what one neighbor in Delaware County thought until the police showed up at his door, search warrant in hand. What was the offense? Possession of child pornography—a serious offense with even more serious consequences. Little did this neighbor know that a suspect who had been on the run for over a year was “borrowing” his unsecured wireless network to download 100 images of child and adult pornography. The warrant was based on the account holder information of the Internet service provider. If you leave your Wi-Fi connection unsecured, the criminals using it can be long gone but the records will still point back to your account. In apartment complexes or streets where houses are close together, it’s not unusual for an unsecured Wi-Fi signal to be available several houses down—up to 200 feet away on average, depending on building features.
Criminals love to access unprotected Wi-Fi, a practice known as piggybacking. And it’s no different than splitting into your cable line and stealing your cable access. It is still considered theft of services. Many just want the free Internet access without having to pay for it, but some deliberately seek it out to cover their tracks and thwart law enforcement’s efforts to find them.
Many times, we travel with a Wi-Fi-enabled laptop and are amazed at the number of unprotected networks we find. Unless you are offering a public Wi-Fi network, do you really want your neighbor across the street to be able to browse the Internet at your expense or to download kiddie porn on your account?
Unprotected Wi-Fi also means that the neighbor may be hogging a great deal of the bandwidth you’re paying for, which can cause your Internet access to bog down. Interestingly, the United Kingdom takes piggybacking very seriously. Offenders there can face up to 5 years in prison and a fine of about $1,900.
Think it’s hard to detect Wi-Fi connections? Think again. Figure 16.1 shows a $30 t-shirt available from Think Geek (www.thinkgeek.com) that can do just that. The glowing bars on the front of the shirt dynamically change as the surrounding Wi-Fi signal strength fluctuates.
In 1983, the movie War Games was released about a teenager who, thinking he was playing an online game, accidentally hacked into a military computer network and nearly launched World War III. The expression “wardriving” is based on that movie. Wardriving is when someone drives around and attempts to hack into open, wireless networks.
Using readily available and free software such as NetStumbler, people involved in wardriving find open, unsecured networks that are quickly tagged, identified, and mapped on the Internet for others to take advantage of. Many wardrivers use GPS (Global Positioning System) units for quick reference to their location and provide that to others on the Internet.
You’re sitting in a local café sipping your latte and surfing the Internet, knowing that you’re using the café’s free Wi-Fi account. A good idea? Not if you’re careless. It’s possible that the person sitting across the way you’ve witnessed with his head buried in his laptop is actually gathering every single word you type. How is this possible? Through Wi-Fi spoofing, also called evil twin spoofing. Here’s how Wi-Fi spoofing works: You go into a place with a free wireless account and think you’re logging onto their wireless network, when in fact you’re actually connected to BadGuy’s laptop, which is pretending to be the coffee shop’s wireless account.
There are an estimated 68,000 Wi-Fi “hot spots” in the U.S. alone, and that’s a conservative number. Unlike wired network systems that use cables to transport information through the Internet, Wi-Fi uses radio waves, which are inherently more vulnerable because many laptops are configured to automatically connect to the wireless network with the strongest signal. If a hacker is sitting two tables away, he can easily override the local Wi-Fi signal and have you connected to his laptop, where he’ll happily collect your account usernames and passwords, your credit card information, every keystroke you type.
To avoid Wi-Fi spoofing, change the settings under Control Panel, Networks, Wireless to not automatically connect to the strongest signal. Watch for the name of the wireless network. If you’re sitting at Los Angeles Airport and always connect to “LAX-Wi-Fi,” don’t assume that “LAX2-Wi-Fi” is valid. Be aware and leery in public Wi-Fi spots. They may be okay to check the local news or weather, but we would not advise logging into your bank account to check your balance.
Several methods can be used to secure an open Wi-Fi connection. We recommend you do as many as you can and enlist the aid of someone knowledgeable to help you if needed. Note that in order to secure a wireless connection, a password is usually involved, so only give the password to those you trust. Professional technical support people should always be willing to hand over the keyboard for you to enter the password out of their view.
The first part of any wireless setup is establishing the SSID, or Service Set Identifier. This is the name given to the router to be broadcast out to everyone else. Typically, when you take the wireless router out of the box, the default SSID is set to the manufacturer’s name (for example, Linksys or Belkin). If you leave it set up with the manufacturer’s name, hackers are more prone to try and penetrate it because this shows there is minimal security and may even give them a heads up that no password is set. Use something obscure for the SSID, not anything that would identify it as yours. Don’t call it “Smith Family Network” or “Jones Avenue”. The instructions to change the SSID are usually included in the setup software.
All routers use some basic level of encryption, typically either WEP or WPA. Without it, it’s like leaving your front door wide open all day long.
The two wireless encryption standards are WEP (Wireless Equivalency Protocol) and WPA (Wi-Fi Protected Access). Of these two standards, WPA is the more recent and the more secure. These encryption standards usually require either a password or a passphrase to connect a computer to your network. WEP is much less secure and can be quickly hacked in less than 20 minutes using readily available software on the Internet. Once the network is penetrated, the data being passed between the hacked computer and the Internet can be seen in clear text and can even be used to gain access to the computer’s files. When it comes to Wi-Fi equipment, it pays to spend extra money to get the most recent devices because they will employ the newer standards, such as WPA, which is far more secure (but make sure your computer can still connect to the device if it’s brand-new technology). If you’re unsure whether your computer’s network card will run on a newer router, write down the make and model number and take it with you. Most qualified salespeople will be able to assist you with this.
“Administrator” is commonly used as the default username for wireless routers. This means you’re giving a hacker half the work of penetrating your network. If possible, change the username and password under the security settings to something obscure that you can remember.
One common mistake people often make in installing their Internet connection and Wi-Fi equipment is to place it in an area that is not easily accessible, such as the basement. There are several reasons for placing the equipment where you have better access it. First of all, you can easily see the device to ensure it is properly functioning. Many times the wireless router is connected to an integrated modem, where you receive phone, cable television, and Internet service all from the same company. It’s going to be a whole lot easier to troubleshoot everything if you can see which lights are on and which are not. Secondly, there are many times when you will want to shut off the router by pulling its power source to refresh it, as discussed next.
In order to have the most security, consider shutting off your wireless router when not in use. Install it in an easily accessible location and consider unplugging the power chord when you’re not at home. This serves two purposes: It reduces the chance of someone hacking into your network because there is no network for them to hack into, and more importantly, it resets the IP address of the router, making it more difficult to trace. This can enhance your privacy if your Internet service provider is tracking your web access history.
Cell phones are vulnerable to hackers, sometimes also called phreakers. A phreaker can hack into your cell phone and listen in on your calls or steal personal information simply by exploiting a short-range Bluetooth wireless connection. A hacker can do even more damage by stealing a cell phone or finding one lost by its owner.
We highly recommend the following tips for anyone with a cell phone, particularly since, with the newer phones, you can do much more than make a call or send a text. Cell phone Internet and email service make you and your phone even more vulnerable to a hacker.
• Always keep a close watch on your cell phone. Don’t leave it in public unattended, even for a minute!
• Lock your cell phone calling availability by password-protecting it.
• Disable the Bluetooth wireless connection when you’re not using your cell phone.
• Consider using antivirus software to block hackers, and keep it updated.
• Never accept text messages or files from a stranger.
• Notify your cell phone provider immediately if you lose a cell phone or suspect it has been hacked. Discontinue service right away to prevent a thief from running up a bill.
With technology practically changing overnight and the price of computers dropping rapidly, it’s not unusual for people to upgrade their computers. The question is, what do you do with that old system?
Many people, with very good intentions, donate their old systems to nonprofit organizations such as local schools or churches. It sounds like a reasonable, charitable thing to do. Unfortunately, without taking the proper steps, it’s also a very dangerous thing to do.
Just because you’ve deleted all your personal files before you donated a computer doesn’t mean you’ve really deleted them. Deleting a file just means that the index to that particular file is removed. The actual file is likely still residing on the hard drive, and while one may argue that a church isn’t going to actively attempt to recover your deleted files, you really have no say what happens to that computer after you make the donation. It is possible that it could fall into less-than-honest hands.
If you are thinking about donating your computer to a local school, remember that there are some very savvy students who would quickly run one of the many file-recovery programs that exist on the Internet and thus be able to retrieve your data.
Once that computer leaves your possession with your data still on it, you might as well be handing over your checkbook. You run the risk of having the following data exposed and/or compromised:
• Your personal financial information, including your checking account information if you do online banking.
• Your social security number, which could lead to identity theft, if you’ve ever filed taxes online or applied for credit online.
• Your credit card information, including account numbers and/or passwords.
• Your personal medical information, if you’ve ever used the Internet to research a specific medical topic.
• Your email address list and any other personal contact information you stored.
We could go on and on, but the point is that once you hand over a hard drive, even if you think you have deleted the files, you’re taking a huge risk. There are many ways to minimize this risk. One is to simply run a “clean wipe” program on your hard drive before you turn it over.
Go to any of the shareware websites, such as www.download.com or www.tucows.com, and enter the search term “secure wipe”. You’ll find many listings for utility programs (some for free) that will perform a secure wipe of your hard drive. Just remember that a secure wipe is just that—a secure wipe. Whatever you’ve “wiped” is not recoverable, so proceed only when you know you will never need that data again.
When a hard drive is reformatted, the process does not usually securely clean the hard drive—it merely prepares the hard drive for the installation of a new operating system. Felicia assisted on a case a few years ago in which a computer was stolen from a local restaurant. The computer was later recovered, but upon examination had been renamed and appeared to not contain any traceable files.
The perpetrators mistakenly thought that by reformatting the hard drive, they would remove all evidence of the computer’s prior ownership. It only took a few rudimentary tools for Felicia to “undelete” the hard drive. Suddenly, numerous documents, including menus, suppliers, and customer lists, began reappearing.
Note that when you run a secure wipe, the operating system can also be deleted, rendering the computer useless until this is restored. Many charitable organizations will accept computers without the operating system installed because often they will install their own, but check with the organization first. Be especially aware that the place where you donate your computer is not necessarily where the computer will end up.
This is the best rule-of-thumb to use with computers. They are, by nature, “memory machines,” and what they can capture and store is unfathomable. Every chat, email, image viewed, website visited—all of this can potentially be recovered and restored. Use your computer wisely and dispose of it thoughtfully.
Many organizations will now take computers regardless of whether they have the hard drives in them. You can find many of these organizations on the Web. Computer components contain precious metals that have value. Some companies actually melt certain components down and resell them. Don’t think that the hard drive couldn’t be put into some other computer and viewed, because hard drives can easily be swapped from one computer to another for examination. If you go this route, pull the hard drive and smash it with a hammer, shoot it up on the range, or drive over it if your tires are strong, but make sure you have rendered it useless. Otherwise, someone else may find it quite useful for unsavory purposes.
We recently had a case where a laptop was stolen from a business. In this case, the business was relatively small, so they outsourced their IT work to a local technology group. Weren’t we pleasantly surprised to find out that the IT company had installed “locator” software on the laptop, as well as remote access. Within a few hours, they were able to provide us enough detailed information about the laptop’s “new” owner that officers were able to knock on their door in a relatively short amount of time. Charges are forthcoming.
Many different programs are available that, depending on the configuration of your laptop, can either send out its location or at least give remote control access back to the original owner.
One interesting program is Retriever, by Front Door Software. Once the laptop is stolen, this program sends out the message “This computer is reported stolen”. It then prompts for a pass code. If the pass code isn’t entered in a timely manner, the laptop’s location is displayed on a Google map to allow the original owner to locate it.
Dozens of similar programs are available. Just Google “anti-theft laptop” and pick one. It could result in the safe return of your laptop! In the meantime, back up, back up, back up.
And while we’re at it, given the enormous popularity of iPods, we couldn’t help but mention the iPod disguise, available for around $10 from www.iDisguise.com. It looks like a mint container but is actually used to store your iPod.
If disguising your iPod doesn’t work for you, try a special case that comes with a combination lock and a steel cable. The one shown in Figure 16.2 is available for around $50 from www.audiocubes.com.
On a final note: We must say that we are constantly amazed at the staggering number of electronic devices stolen from unlocked vehicles within our jurisdiction. This includes iPods, cell phones, laptop computers, GPS units, and so on. Thieves who steal from cars are usually down-and-out folks who are looking for items they can quickly resell or pawn. The best way to prevent your electronic gear from being stolen is to lock your vehicle. It would shock people to know just how often cars are left unlocked with valuables left inside, often in clear sight. Use common sense.
Consider what you’re giving to thieves the next time you walk away from your unlocked car. Do you really want them to have your entire music library in which you’ve invested thousands of dollars? Do you want them to have your social security number from the taxes you filed last year online on your laptop, your entire email contact list, your resumes, and your bank statements? Do you want them to have your GPS with “Home” already programmed in, or your child’s cell phone number, which is programmed into your cell phone? Probably not. So, please, lock your car.


