The Internet of Things (IoT) is a network of processing devices with unique identities that can connect to and transfer data over a network without requiring direct human interaction (see Figure 1-1). In many cases this makes the devices themselves autonomous or semiautonomous. They can be controlled, managed, and programmed to follow specific rules of engagement.
Health and Fitness Monitoring
Manufacturing Systems
Energy Metering
Hospital and Patient Care
Smart Appliances and Lighting
Enhanced Surveillance Systems
Entertainment
Home Automation and Security
Multifunction Wearable Technologies
Automotive
Tracking Systems
Personal Communications
Along with new categories emerging every day

IoT interconnected
Note
The focus of this book and the accompanying source code is to observe, learn, model, and detect aberrant behavior of IoT devices using the Raspberry Pi as a sensor.
Why Is IoT Vulnerable?
When considering vulnerabilities of IoT devices and networks, we must first define the overall attack surface. If you believe Gartner’s prediction (Gartner Research, 2017) that 25.1 billion IoT endpoints will exist by the year 20211, then this would certainly define a large attack surface. Many of these devices are also interconnected and operating across boundaries of consumers, business, industry, and government, without geographic restrictions.

Device-to-device communication model
Device-to-Device Communication
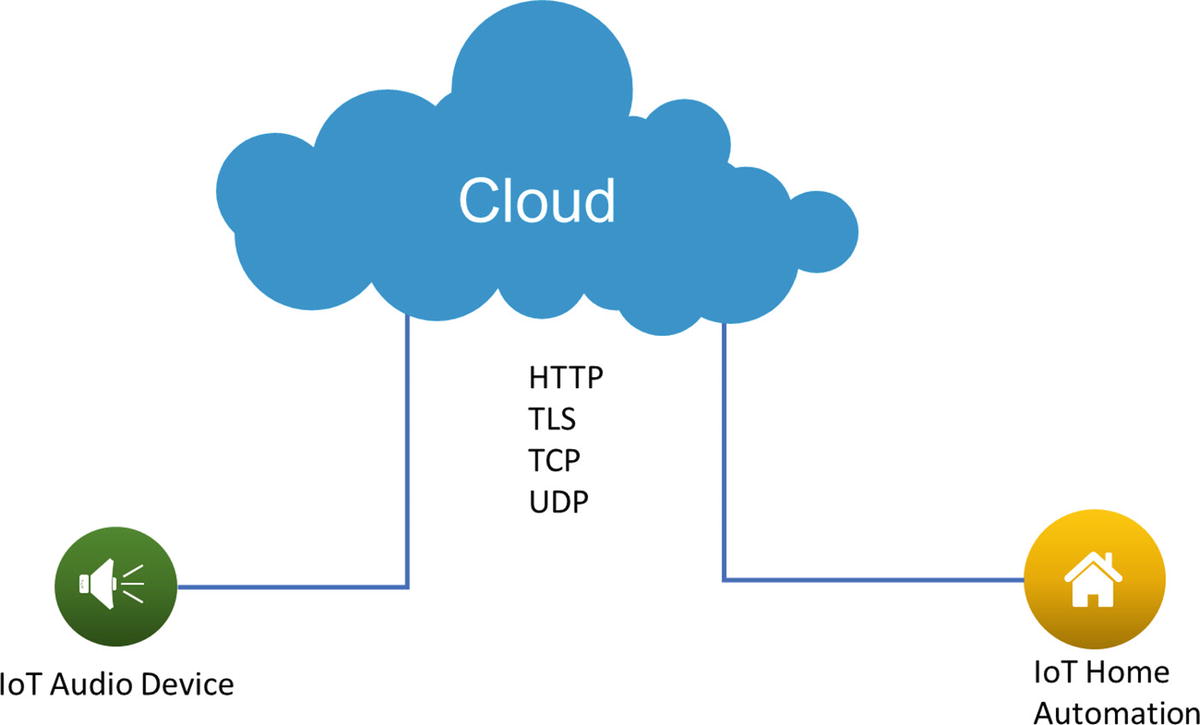
Device-to-cloud communication
Device-to-Cloud Communications
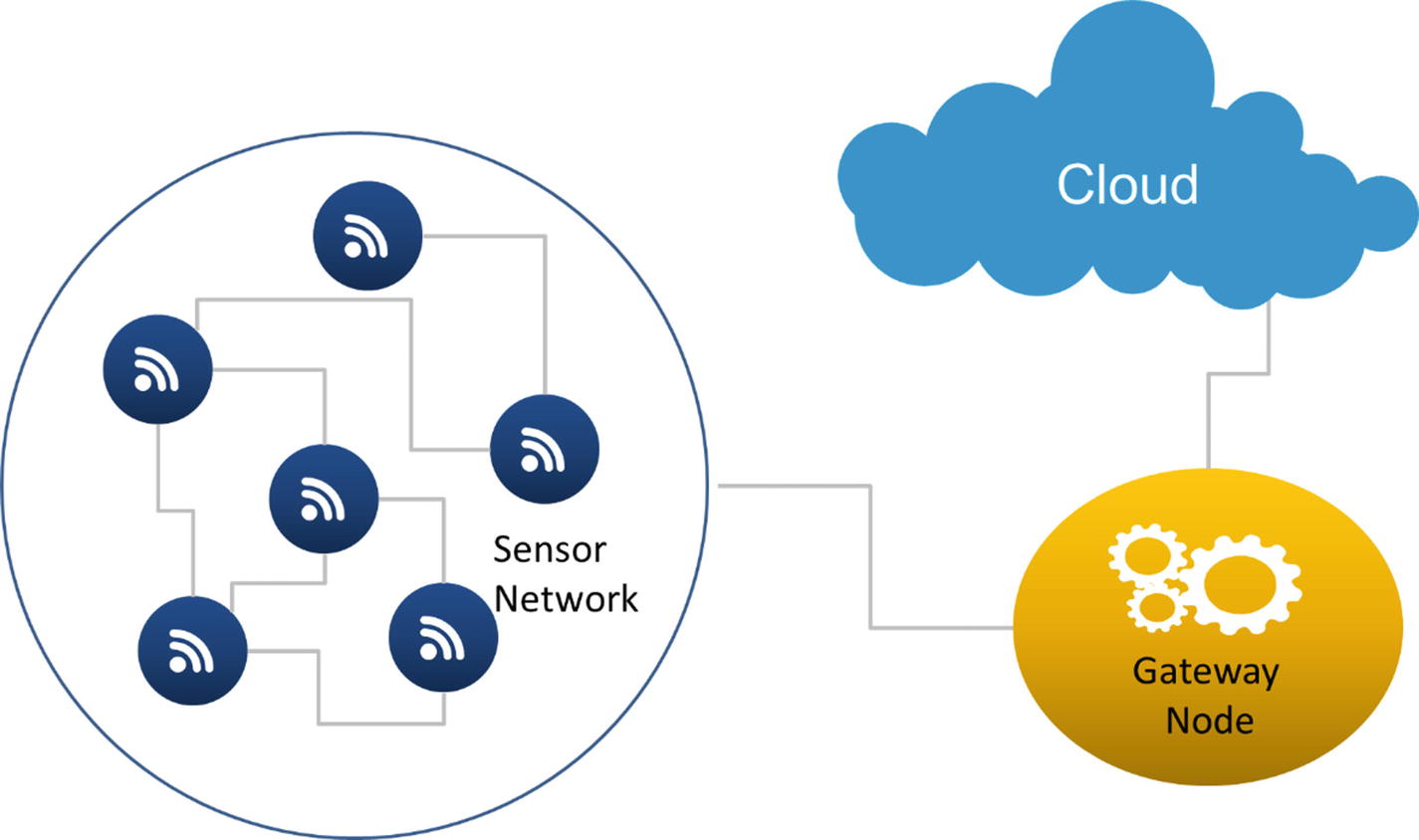
Device-to-gateway framework
Device-to-Gateway Sensor Network Communications
Utilizing this method, sensors discover and communicate with other sensors and coordinate information through gateways. The gateway, in turn, communicates information with other sensor networks and typically with the cloud.

CIA triad
Class 0: Compromise of data would cause little or no impact.
Class 1: Compromise of data would cause limited impact.
Class 2: Devices must be resilient to attack on availability that would have significant impact.
Class 3: Devices must both be resilient to attack and protect sensitive data.
Class 4: Devices must be resilient to attack, preserve integrity of operation, and protect sensitive data. Any resulting breach would cause serious impact and potentially cause injury.
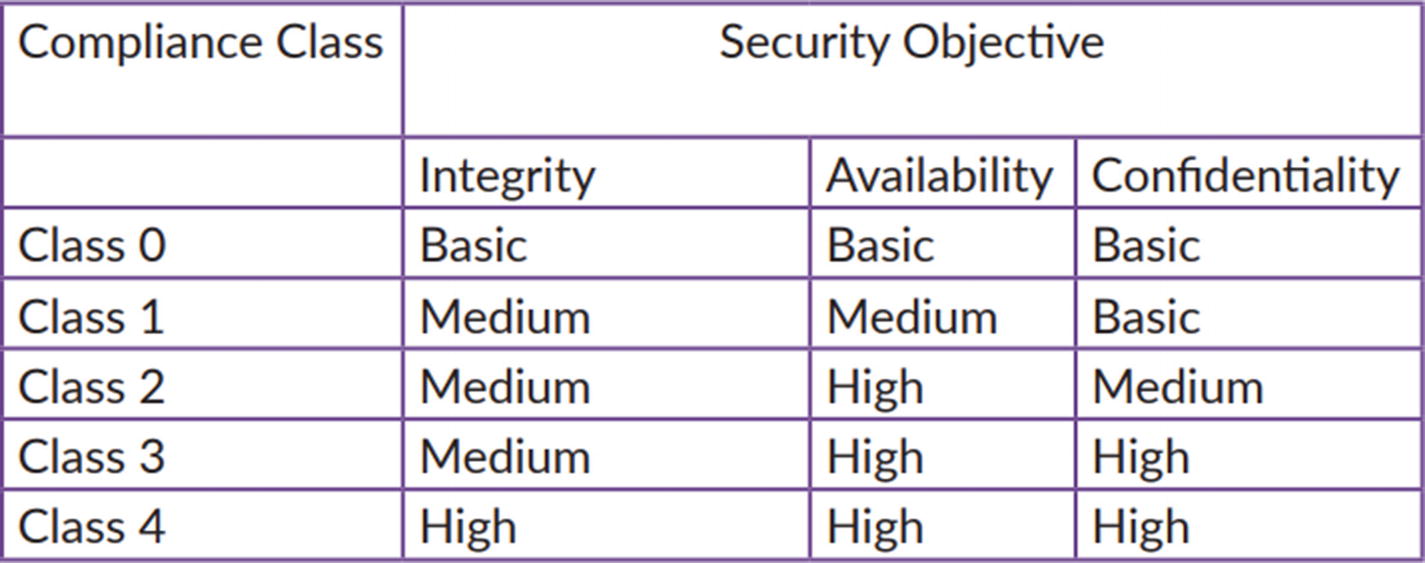
Compliance classification security objectives
Interpreting the Security Levels
Category | Level | Requirements |
|---|---|---|
Integrity | Basic | IoT devices resist low-level threat sources that have very little capability |
Medium | IoT devices resist medium-level threat sources that have minimal focused capability | |
High | IoT devices must resist substantial-level threat sources | |
Confidentiality | Basic | IoT devices processing public information |
Medium | IoT devices protect against disclosure of low-value personally identifiable information | |
High | IoT devices process very sensitive information and must protect against any disclosure | |
Availability | Basic | IoT device lack of availability would cause only minor disruption |
Medium | IoT devices should possess some availability defenses against the most common attacks | |
High | IoT devices must anticipate determined availability attacks and take significant measures to overcome them |
Moving Beyond the Basics
Now that we have set the stage of what we are up against, let’s take a deeper look at what is different about IoT devices and their potential security challenges. What makes IoT devices and their accompanying protocols unique?
Low-Power Sensors - These devices may have limited processing and memory capabilities that limit the amount of traditional defensive technologies that can be integrated into them. In addition, they may only be able to communicate using low-power protocols such as Bluetooth, ZigBee, or Z-Wave, thus obscuring their behavior on either the local area network (LAN) or WIFI network.
Single Board Computers and Embedded Operating Systems - To reduce cost and power requirements, many IoT devices use small inexpensive hardware platforms such as Raspberry Pi, WeMO, Arduino, Intel Edison, and Quark. These devices are capable of running embedded operating systems such as Raspbian, Snappy Ubuntu, FreeBSD, Kali Linux, and Windows 10 IoT Core along with other lesser-known open source and proprietary systems such as RTOS IoT, Nano-RK, TinyOS, Mantis, and Mbed. As you might have already guessed, some of these operating systems have NOT been thoroughly vetted for security vulnerabilities. Furthermore, since some of the most popular are open source, the ability for adversaries to identify and then exploit design and/or coding flaws is a potential threat.
Address allocation without the need of a DHCP (Dynamic Host Configuration Protocol) server
Name translation without access to a predefined Domain Name Service
Ability to discover other devices that are nearby or located on the same subnet, WIFI network, or other low-power wireless network
Dynamic Discovery Protocols - Protocols such as uPnP, Simple Service Discovery Protocol (SSDP), and Network Basic Input/Output System (NETBIOS) with Server Message Block are just a few of the examples that are commonly used. Typically, IoT devices need to discover services available to them. NETBIOS with Server Message Block allows devices to advertise services and then determine their status.
Use of Multicast Communication - Protocols such as Web Services Dynamic Discovery can identify services available on the LAN. Web Services Dynamic Discovery can communicate on top of SOAP (Simple Object Access Protocol) , which in turn can run on top of HTTP, SMTP, TCP, UDP, and even the Java Message Service (JMS).
All of these communication and discovery protocols make it difficult to track behavior, control access, ensure security, and even continuously monitor these dynamic behaviors.
What Unique Vulnerabilities Lurk Within IoT Devices?
Hardware platforms and embedded operating systems built for low cost and low power potentially contain a wide variety of untapped vulnerabilities versus traditional desktop and mobile devices.
Direct discovery and connection between local IoT devices has the potential of enabling self-replicating malware threats once a single device or manufacturer has been compromised.
Direct connection of IoT devices to the Internet and cloud-based services can circumvent traditional proven security mechanisms and frameworks.
Lightweight protocols with limited built-in strong authentication, data privacy, or denial of service defenses capabilities are targets for those wishing to obtain access, leak information, or disrupt operation of target IoT devices and sensor networks.
What Are the Common IoT Attack Vectors?
Device Backdoors
Lack of Encryption
Poor Key Management and Key Protection
Plain Text Passwords
Buffer Overflows
Command Injection Exploits
SQL (Structured Query Language) Injections
SmartTV Data Leaks (Samsung and LG)
Alexa and Google Home can be hacked to monitoring everything you watch and say. These systems control lights, fans, switches, thermostats, garage doors, sprinklers, door locks provided from numerous vendors such as: WeMo, Philips Hue, Samsung SmartThings, Nest, and ecobee
This represents just a glimpse at the attack surface related to IoT devices to give you a flavor of the threats and risks associated with IoT devices, protocols, and platforms.
How Do the Raspberry Pi and Python Fit In?
As the book title Defending IoT Infrastructures with the Raspberry Pi implies, we will be developing a Raspberry Pi sensor written in Python. The Pi will be used to model, monitor, analyze, and report aberrant behavior emanating from IoT devices along with targeted attacks perpetrated against those devices.
Raspberry Pi Brief Introduction
There are literally hundreds of books, videos, tutorials, and online resources that provide a thorough background on the Raspberry Pi. Thus, this quick introduction assumes that the reader have familiarity with the Raspberry Pi. However, I want to provide a focused definition of how I plan to use the Pi as an IoT sensor. It turns out that many IoT devices based on the Raspberry Pi already exist. In addition, the Windows IoT core now runs on a Raspberry Pi offering developers both Linux (Raspbian and other flavors) along with Windows as a choice for development.
Raspberry Pi Hardware

Raspberry Pi 3 Model B
CPU: 1.2 GHZ quad-core ARM Cortex A53 (ARMv8 Instruction Set): Leveraging each core for specific functions will be critical in capturing and identifying IoT device behaviors.
Memory: 1 GB LPDDR2-900 SDRAM: Utilizing the expanded memory of Pi 3, will help to reduce I/O to the slower SD device.
Network: 10/100 MBPS Ethernet, 802.11n Wireless LAN, Bluetooth 4.0: The built-in networking option allows for the use of core functions of the Pi for the main network monitoring interfaces whether they be wired ethernet, WIFI, or Bluetooth devices.
USB ports: 4: Provides the needed expansion opportunities to support other wireless technologies such as ZigBee.
All of this comes in a package that costs under $40.00 for the single board device. Adding in the cost of a fast 32-GB SD Card and a computer kit keeps the cost under $100.
Raspbian OS
In addition to the Pi itself, we will be using the Raspbian Operating System on the Pi. Specifically, I will be using Raspbian GNU/Linux 8 (Jessie). As we move into later chapters I will provide details of the OS configuration and security measures.
Python
Python is the language of choice for all the software components being developed. We will be using Python 2.7.9, which is the latest 2.7.x version available for the Pi as of this writing. With minor modification, the code will run on Python 3.x as well. With a couple of exceptions, I will be only be using the Python Standard Library modules, thus eliminating the need to install or most importantly understand the underpinning, performance, and risks associated with third-party libraries. This is mainly a performance and security decision that will keep the Pi as minimal and safe as possible. The book is not designed to teach you Python, as there are many resources that can help you with that. However, all my Python code is extensively documented and the rationale for the methods and approaches chosen are detailed throughout the book to hopefully extend your knowledge.
Note
There are many outstanding third-party Python libraries and modules out there for you to experiment with as well.
Summary
This chapter provided a very brief introduction to the IoT landscape present and future. In addition, it examined some of the basic differences between IoT devices and more traditional computing devices. We examined several classes of vulnerabilities and exploits of IoT devices to get a flavor for the diversity we face today and in the future. Finally, we provide a brief introduction to the Raspberry Pi, the Raspbian operating system, and the Python programming language that will be utilized throughout this book.
In Chapter 2, we will examine possible methods to model IoT environments for passively monitoring their behavior and ultimately discover aberrant behaviors.
