As with most hardware solutions, they are never finished until they are no longer relevant. This chapter adds a couple of final touches to this version of the Pi sensor. As this book proceeds to print, I’m sure more changes, updates, and enhancements will continue. Not to worry, the updates and source code for the latest changes will be available via git-hub. Go to www.apress.com/9781484236994 .
Raspberry Pi Latest Version

Raspberry Pi 3 Model B+
The 3B+ upgrade offers a faster processor (200MHz increase in CPU clock frequency), better thermal management, three times the wired and wireless network throughput, and Gigabit Ethernet. These improvements add value to our sensor solution by delivering additional speed to process packets faster without overheating the Pi.

Raspberry Pi in ruggedized Smraza case
As of this writing, the multilayer Smraza case is available from Amazon, among other places. The case includes an on/off switch cable, a fan, and heat sinks.
Sensor Software Updates
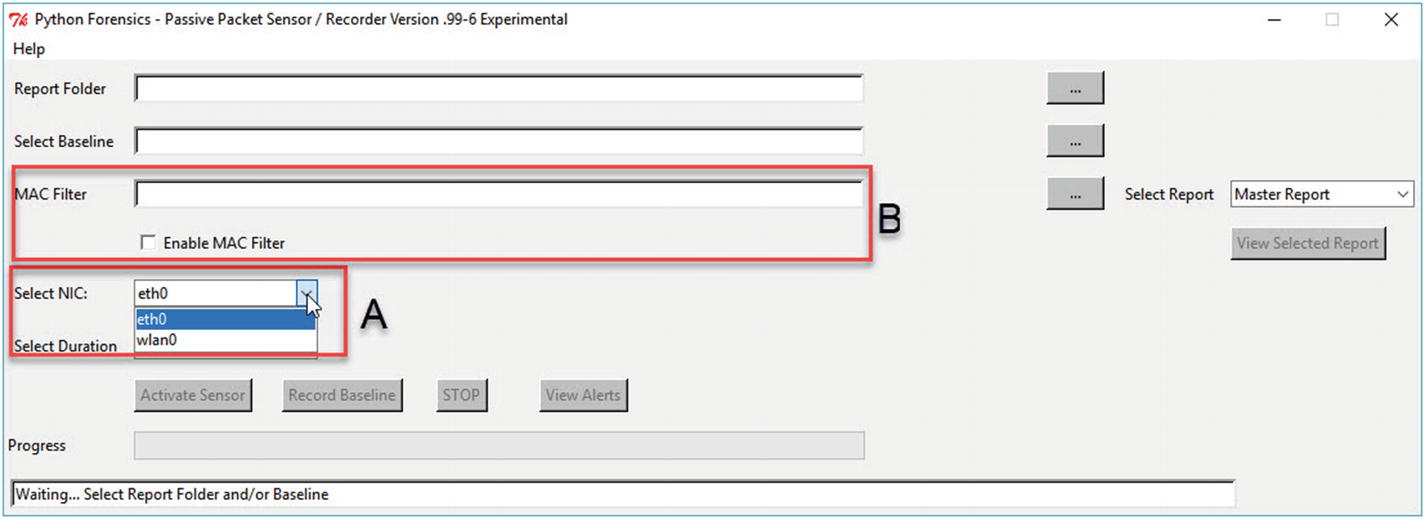
Sensor updates: (A) NIC selection; (B) MAC address filtering
(A) NIC Selection
Determining the available interfaces on the Raspberry Pi is quite straightforward. The directory /sys/class/net holds the names of the available interfaces. For our purposes, this allows us to provide a drop-down list of possible interfaces and most importantly allows the selection of the wireless interface in addition to the standard Ethernet port. As mentioned in the preceding, both interfaces have been significantly improved on the Raspberry Pi 3 Model B+.
To build a list and the GUI drop-down menu, see Listing 6-1.
Targeting Specific Devices to Monitor
Raspberry Pi wireless selection
(B) MAC Address Filtering

Selection of the MAC filtering list
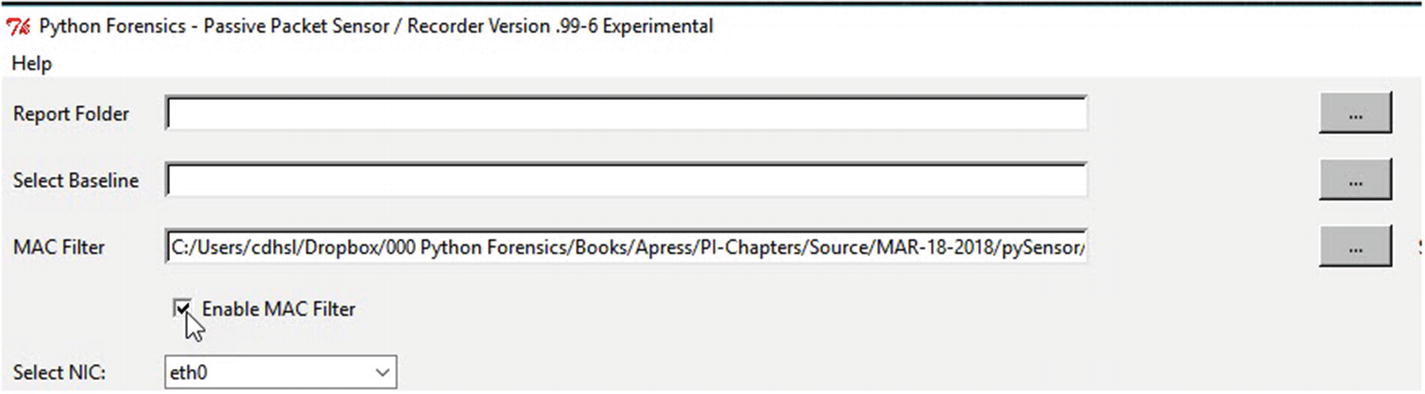
Enabling the MAC filter

Sample MAC-LIST text file
You might be questioning why we chose to use a MAC address for filtering instead of the IP address. IP addresses for devices are dynamically assigned by DHCP unless they are statically defined. Therefore, using MAC addresses (which can be manipulated as well, but require targeted action to do so) provides better filtering options. When the sensor is operated, only packets with source or destination MAC addresses provided in the list will be recorded. This allows for easier analysis of the reports such as port usage and country, allowing you to verify the inbound and outbound traffic from specific devices.
The MAC address filtering is handled in just a few lines of code. First, we create a list of MACs to filter when a MAC filtering file is provided, and MAC filtering is enabled (see Listing 6-2).
Honoring User Filter Selections
This method provides easy filtering of MAC addresses during packet extraction (see Listing 6-3).
Filtering Out Other Device Packets
Summary
This chapter added some finishing touches to the Raspberry Pi sensor, specifically, the ability to monitor any network interface that is available on the Pi. This provides a wider view of activity on the network in question.
In addition, the capability to target specific MAC addresses detected during recording or sensor activation further refines the applications of the Pi sensor.
In Chapter 7, we will discuss future capabilities that are planned for the Pi sensor, and how you can participate in the project.
