How to mislead digital forensics investigations
As we mentioned before, digital forensics, also known as cyber or computer forensics, is a branch of forensic science that uses scientific knowledge, methodology, and rigor to aid the solving of crimes and incidents by collecting, analyzing, and presenting digital evidence to use in remedial action or a court of law. The primary goal of digital forensics is to perform a structured investigation of digital evidence and prepare this evidence for presentation in a court of law. Digital forensic investigators use different forensic tools to collect, preserve, and interpret digital evidence. Based on their findings, they will draw conclusions and present these conclusions to those who will act on them.
Attempts to negatively affect the existence, amount and/or quality of evidence from a crime scene, or make the analysis and examination of evidence difficult or impossible to conduct. 1
In this chapter, we are going to describe the nature of digital antiforensics techniques and explain how these techniques may be used to mislead the forensic investigation process, thereby making it very difficult to carry out a digital investigation or even gather enough evidence to debate during a trial.
Users of Antiforensics Techniques
Military professionals
Law enforcement
Politicians and diplomats
Security researchers
Journalists and whistleblowers
Business corporations
Casual Internet users seeking privacy
From a digital forensics perspective, it’s necessary for digital forensics examiners to know about such techniques and how they work, so they have a better understanding of what they should do if they encounter it during their investigations.
Classification of Antiforensics Techniques
- 1.
Data hiding techniques (known as steganography)
- 2.
Data destruction techniques (antirecovery)
- 3.
Encryption techniques
- 4.
Cryptographic anonymity techniques
- 5.
Direct attacks against computer forensics tools
Digital Steganography
Steganography is the science of concealing a secret message within an ordinary honest file, thus maintaining its secrecy during delivery. Steganographic techniques have been used since ancient times; they have been used to convey secret messages during battles and to deliver secret espionage information from spies.
Old steganographic techniques were mainly dependent on physical objects (e.g., paper, eggs, invisible ink, and even human skin) as the medium to conceal the secret message, However, with the advance of computing technology and Internet communications, modern techniques become largely based on exploiting digital files (whether images, videos, audio, or even a file system like Windows NTFS) and IPs to convey secret messages between communicating parties.
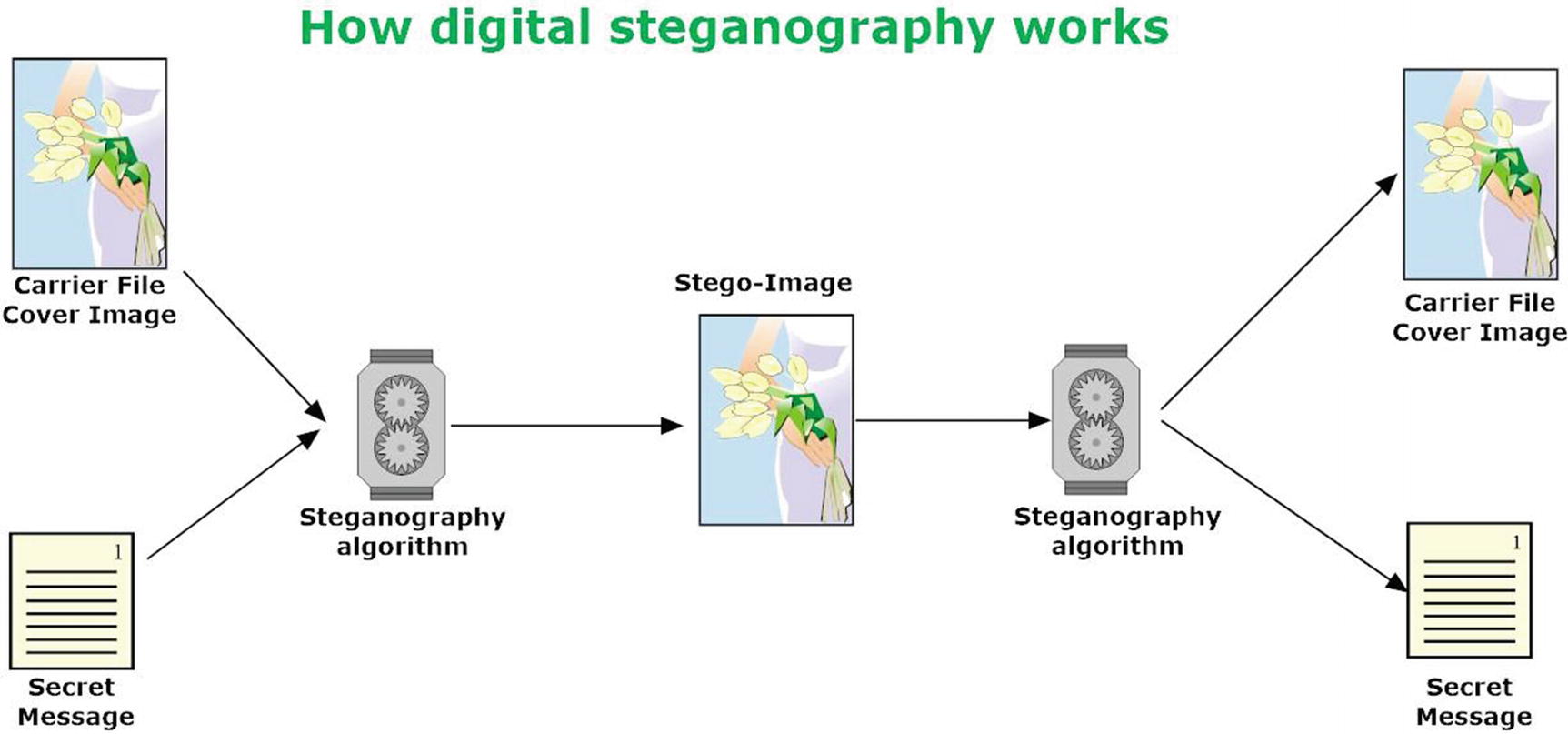
How digital steganography works
Digital Steganography Techniques
- 1.
Injunction: Using this method, we embedded a secret message in a trivial, nonreadable location of the overt file. An example of this technique is embedding a secret message after the end-of-file marker (EOF). Hiding with this method will not have an effect on overt file quality or appearance.
- 2.
Substitution: Using this method, we are replacing insignificant bits that belong to the overt file with the one that belongs to the secret message. This method is more secure than the previous one, as the overt file size will not get increased because we are just replacing bits without adding anything new.
- 3.
Generation: This is the most secure method to achieve digital steganography; with this type, we are creating a new file that holds the secret message within it.
Digital Steganography Types According to Carrier File Type
Steganographic techniques may be classified according to carrier file (overt file) type used to conceal the secret message.
Text Steganography
This type uses text to conceal secret data within it. Some examples include inserting spaces between words and/or inserting one or two spaces at the end of each line to store hidden bits, reducing the text size to 1 pixel and using the hidden text feature in MS Word to conceal data. Watermarking is also considered a type of text steganography where secret data are embedded in the overt file (image or audio) and can be extracted only by the owner using a secret key.
The main disadvantage of this type is the small amounts of secret data that can be embedded in text compared with other digital file types.
A simple way to achieve text steganography is by changing a text’s spelling while preserving its visual appearance. This method is used in some countries to fool surveillance systems used by their governments to filter/block Internet traffic; by changing the spelling of important words, we can avoid getting caught by the monitoring machines.
Changing Spelling to Fool Surveillance Systems and to Conceal Data in Plain Sight
Original Text | Misspelled Text Variation | ||
|---|---|---|---|
Attack | Αtтack | Aтtack | Attack |
Train | Τгαɪn | Tгain | Train |
London | London | Loϖdon | Londoϖ |
Plane | РΙaɳe | Pɭane | PІaɳe |
Note!
A secret message can be concealed within Twitter tweets in plain sight. http://holloway.co.nz/steg/ is a web site that offers such a service.
Other areas to consider when investigating for hidden data is searching in MS Office files (the modern versions beginning from version 2007, as these versions are based on the XML- file structure called OOXML [Office Open XML]). The OOXML structure opens various possibilities to embed different types of digital files (text, image, audio, and video files) inside the MS Office file structure.
Image Steganography
This is the most used file type to conceal secret messages. As we all know, in today’s digital age, it is common for people to exchange and post images online (e.g., to social media sites); the large volume of exchanged digital images daily make this file type less suspicious to outside observers. In image steganography, a user embeds a secret message within an image file using a specific steganographic algorithm; the result, called a stego-image, is then sent to the receiver, who will use a similar algorithm to extract the secret message from the overt file.
Let us demonstrate an experiment on how a suspect can employ image steganography to conceal secret information using a simple tool called Steghide .
- 1.
Download the tool from http://steghide.sourceforge.net/index.php ; in my case I downloaded the Windows version and unzipped the contents of the zip file into my working directory, which is c:work.
- 2.
Since this is a command-line tool, launch a command prompt and navigate (using the CD command) to where you have extracted the tool; type the command shown in Figure 9-2.
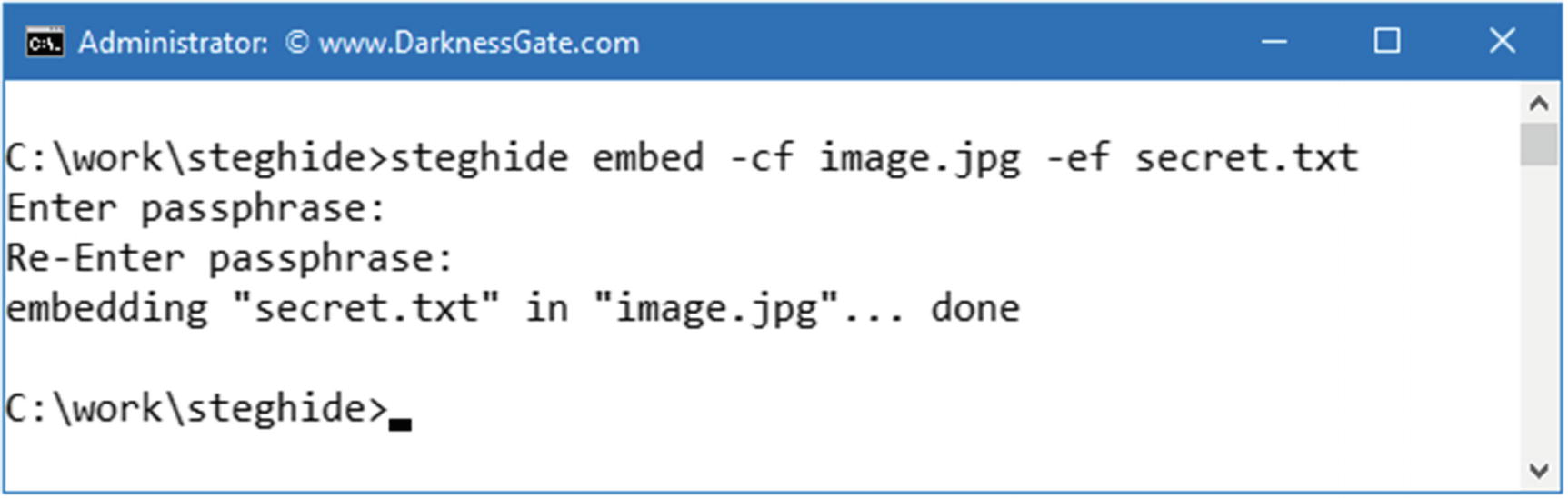
Using Steghide tool to conceal a secret text file in an image file
From Figure 9-2, this command will embed the text file named “secret.txt” in the overt file image.jpg. Please note that when you type the passphrase after executing the command, it will not appear on the screen, so do not worry about this issue.

On the left is the image with the hidden message (hence, a secret text file) embedded inside it. On the right is the original image. No difference appears visually between both images.
Data concealed in digital images have some limitations. For instance, for many implementations of an image’s steganographic algorithms, if you update the image (resize it, change the format, edit it, or crop it), the secret message within it will get destroyed, so you should always work with a copy of acquired digital evidence—as we have insisted before many times—to avoid destroying the evidence accidentally.
Audio-Video Steganography
In a nutshell, audio steganography conceals secret data in digital audio files. The most popular audio steganography tool is MP3stego, which conceals secret data in the most used audio file format, MP3. You can find it at www.petitcolas.net/steganography/mp3stego .
Techniques used to conceal secret data in images and audio files can be utilized to conceal secret data in video files. Video files are composed of a series of audio and image files, thus allowing for a huge capacity of secret data without affecting the quality of the original file (overt file).
Network Steganography
Experiments show that we can exploit networking protocols like the TCP/IP suite to embed secret messages. The design features of many networking protocols allow for this possibility. An example of a program to conceal data within networking protocols (TCP/IP header) is called covert_tcp; you can find it at http://firstmonday.org/ojs/index.php/fm/article/view/528/449 .
Digital Steganography Tools
Popular Digital Steganography Tools
Program | Supported Overt Files | Support Encryption | URL |
|---|---|---|---|
Crypture | Bmp | YES | |
OpenStego | Different media files | YES | |
Gifshuffle | GIF | YES | |
wbStego4open | Bmp , text files, HTML, pdf | YES | |
SilentEye | JPEG , BMP , WAVE | YES | |
Steghide UI | Different media files | YES | |
Camouflage | Different media files | YES | |
DeepSound | Audio files | YES | http://download.cnet.com/DeepSound/3000-2092_4-75758214.html |
Data Destruction and Antirecovery Techniques
Physical destruction: In this type, digital storage media (like hard drives, memory sticks, magnetic tapes, CDs, DVDs and Blu-ray discs, credit cards) are destroyed physically to avoid recovery. The equipment used in this case is called “hard drive shredders” or “destroyers.”
Degaussing technique: This technique works by exposing the magnetic storage devices such as HDD or the magnetic tape to the powerful magnetic field of a degausser to eliminate magnetically stored data. This method is valid only to destroy data stored on magnetic devices, and cannot destroy data stored on SSD and USB thumb drives.
Logical destruction (sanitizing): This is the most commonly used technique to destroy data. It uses a wiping tool to destroy data without affecting the hardware that holds this data. Please note that although this technique offers a high level of secure erasure, it still cannot guarantee 100% removal of data from some type of storage media (especially the magnetic storage media like HDD and tapes), as some hardware-based techniques can recover data even after it is wiped with disk sanitization tools.
Algorithms Used to Wipe Data on Hard Drives
Erasing Technique | Security Level | Overwriting Passes |
|---|---|---|
RCMP TSSIT OPS-II | High | 7 |
HMG Infosec Standard 5 | High | 3 |
DoD 5220.22-M | High | 3 |
Bruce Schneier’s Algorithm | High | 7 |
German Standard BSI/VSITR | High | 7 |
Tools Used to Securely Wipe Your Hard Drive Data
Program name | URL |
|---|---|
DBAN | |
Secure Erase | |
Eraser | |
CCleaner | |
SDelete | https://technet.microsoft.com/en-us/sysinternals/sdelete.aspx |
Specific Manufacturer Tools Used to Securely Wipe SSD Drives
Tool Name | URL |
|---|---|
Intel SSD Toolbox | |
Corsair SSD Toolbox | |
Samsung Magician | www.samsung.com/semiconductor/minisite/ssd/download/tools.html |
SanDisk SSD | https://kb.sandisk.com/app/answers/detail/a_id/16678/~/secure-erase-and-sanitize |
Kingston SSD Manager | |
Micron’s Storage Executive software | www.micron.com/products/solid-state-storage/storage-executive-software |
Note!
The existence of wiping tools on a suspect machine (even the leftover of such tools existing on the registry or other places like the Prefetch folder) will raise suspicions that the examined PC contained incriminating data or was used to destroy such data on attached storage devices.
Please note that using wiping tools will also leave clear clues about their usage on a hard drive; for instance, wiping tools usually work by repeating a predefined pattern many times over the unallocated space on the hard drive, and this can be easily seen when investigating the target hard drive on the bit level using any Hex editor.
Employing data destruction techniques in the correct way will make recovering data from suspect digital devices impossible.
Files’ Metadata Manipulation
File created: This is the time when the file was “created” on the hard drive.
File accessed: This is the date/time when the file was last accessed. When a user opens or moves the file from one location to another, the access time will get changed. When scanning files, antivirus programs can change their access times.
File modified: This is when the data within a file was modified.
MTF last written: This attribute does not appear in Windows Explorer (when right-clicking the file and selecting Properties); it can be seen by some computer forensic tools like EnCase and AccessData FTK.

Using BulkFileChanger tool to change file’s date/time attributes

Comparison of date/time attribute values after changing them using the BulkFileChanger tool
Changing the date/time stamp of files is still an effective method to fight against computer forensics; however, bear in mind that if a professional examiner suspects that a specific file attribute has been changed in this way, s/he can perform deep analysis of this file’s hidden timestamp attributes located in the MFT. This will clearly uncover that the time attributes of the subject file have been changed manually.
Encryption Techniques
While the aim of steganography is to hide secret data, making it hard to notice, encryption techniques perform a similar job through scrambling the data. Encryption is the practice of concealing information by obscuration, thus making it unreadable for unintended recipients.
Encryption plays a key role in today’s IT systems: both public and private organizations need to encrypt their data at rest and in transit. The wide spread of encryption tools—some with very powerful capabilities—in addition to the ease of using them will certainly lead to making a forensic investigation of encrypted devices difficult, time consuming, and even impossible without the suspect’s cooperation. In many cases, authorities have paid large expenses to decrypt high-value incrementing data when the key/password is not available.
Note!
The FBI paid $900,000 to unlock the San Bernardino iPhone.2
In cryptography, a key is a string of bits used by an algorithm to alter information from the plain text into cipher text and vice versa. This is aimed at scrambling this information scrambled, with it being visible only to people who have the corresponding key to recover the desired information.
Cryptographic Systems
Symmetrical encryption: Also known as secret key cryptography (SKC), in this type, both the sender and the receiver use the same key to encrypt and decrypt the data. Having the key fall into the wrong hands will compromise the entire system.
Asymmetrical encryption: Also known as public key cryptography (PKC), this cryptographic type uses two different keys for encryption and decryption. The two keys are mathematically linked. However, no one can derive the decryption key (private key) from the encryption key (public key).
FDE
FDE uses a cryptographic method (either a symmetric key or an asymmetric key) to encrypt each bit of data that exists on the target drive. This form of encryption is becoming increasingly required by enterprises and individuals willing to protect their private data, especially when using mobile devices like tablets, laptops, and external drives. FDE is now supported by major vendors (Android, Windows, and Apple) for both desktop and mobile devices and can be applied easily with minimal effort.
FDE has become integrated into many operating systems (e.g., BitLocker encryption for Windows and FileVault available in Mac OS X 10.3 and later) to protect private user data; this poses real challenges to computer forensic examiners who will become unable to access suspect private data without knowing the key (password) for decrypting it.
Windows BitLocker
BitLocker drive encryption is a data protection feature offered by newer editions of Windows beginning with Vista. By using BitLocker, a user can encrypt the entire disk drive, including the Windows partition and removable USB drives (using BitLocker To Go), securely.
BitLocker uses the AES encryption algorithm with a 128-bit key size by default; however, you can strengthen the encryption by changing the key length to 256 bits for enhanced security.
Windows 10 Pro, Enterprise, and Education editions
Window 8 and 8.1 Enterprise and Pro editions
Windows Server 2008 R2, all editions
Windows 7 Enterprise and Ultimate editions
Windows Vista Enterprise and Ultimate editions
BitLocker requires a computer with a Trusted Platform Module (TPM). TPM is a small microchip found on the computer motherboard. Most modern Windows-certified devices come equipped with this chip. The main role of the TPM with regard to BitLocker encryption is to store BitLocker encryption keys. It also offers a security mechanism to detect any attempt to change the host OS software or hardware by attackers to decrypt your encrypted drive (e.g., planting a keylogger on the bootloader of the OS). However, if your PC does not contain a TPM chip, you can continue to use BitLocker on your Windows device and unlock the encrypted drive using either a password or a key file stored on a thumb drive.
Decrypting a machine with BitLocker enabled is nearly impossible, so it is very advisable if you come across a running machine with BitLocker enabled to capture its RAM memory immediately and then capture the entire hard drive before powering the machine OFF, as this could be your only chance to get evidence from that computer.
EFS
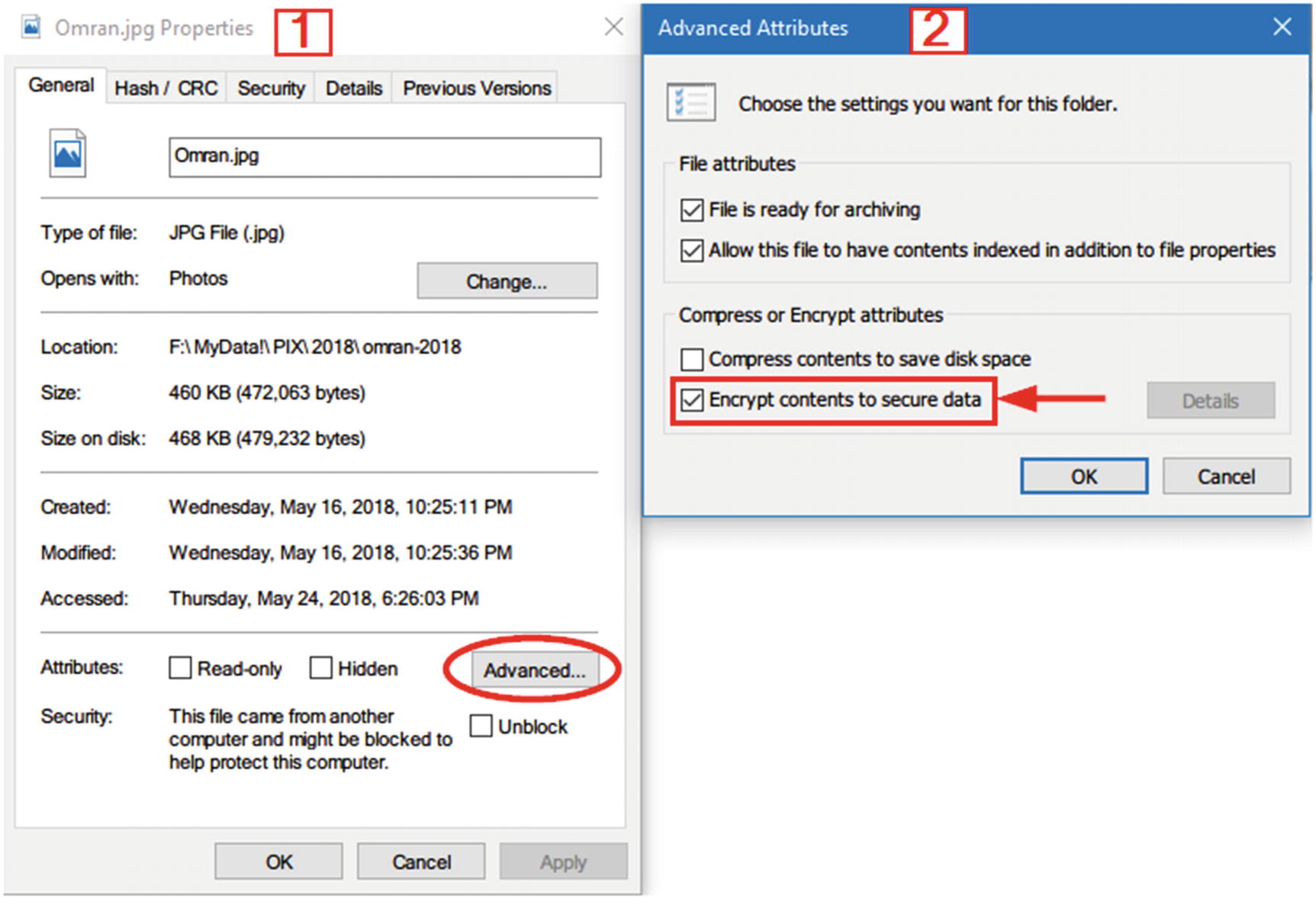
Enable EFS encryption for individual file under Windows NTFS file system
EFS uses a combination of symmetrical and asymmetrical encryption algorithms to encrypt data. To secure encrypted data without entering a password from the user, EFS uses the currently logged-on Windows account (username and password) as a part of the encryption private key.
Disk Encryption Using Open Source Tools
VeraCrypt ( www.veracrypt.fr/en/Home.html ): This is based on TrueCrypt 7.1a. It is a free open source encryption disk supported on Windows, Mac OSX, and Linux. VeraCrypt allows the creation of a hidden volume (this resides within a virtual encrypted disk) and hidden operating system partition in addition to its ability to encrypt the entire hard drive and portable storage devices like USB sticks and external HDD.
CipherShed ( www.ciphershed.org ): This is another fork based on TrueCrypt. It maintains backward compatibility with the previous TrueCrypt container format.
Cracking the encryption of many open source cryptographic programs is impossible if an offender refuses to disclose the encryption key; many legal cases have already been stopped due to the inaccessibility of the encrypted files.
Password Cracking
- 1.
Cain and Abel ( www.oxid.it/ca_um ): A popular tool for cracking encrypted passwords—using brute force, dictionary, and cryptanalysis attack techniques—and sniffing passwords out of network traffic.
- 2.
Ophcrack ( http://ophcrack.sourceforge.net ): This is a free password cracker that utilizes rainbow tables to crack Windows passwords.
- 3.
RainbowCrack ( http://project-rainbowcrack.com/table.htm ): This speeds cracking password hashes from Windows XP, 2000, Vista and 7.
- 4.
John the Ripper ( www.openwall.com/john ): A password cracker for Unix, Windows, DOS, and OpenVMS.
Cryptographic Anonymity Techniques
Digital anonymity works by hiding any traces between the sender and message receiver when communicating through open networks like the Internet. It uses a combination of encryption algorithms to encrypt messages and cryptographic anonymity software to hide your identity during the transmission.
Anonymous networks like the TOR network help users to maintain their online privacy when going online through concealing their true IP address from outside observers, including the ISP. The most famous anonymous network is the TOR network. To access the TOR network, you need to use the TOR Browser, which can be downloaded from www.torproject.org/projects/torbrowser.html.en .
Tracking users through the TOR networks is almost impossible when the user follows strict precautionary security measures. Other anonymous networks include I2P ( https://geti2p.net/en ) and Freenet ( https://freenetproject.org ).
Web Browsers’ Private Modes Do Not Record Users’ Online Activities
Employing antiforensics techniques does not need to be that hard, as some applications used every day—such as web browsers—can be configured in one click to forget a user’s previous activities automatically. For instance, many web browsers have introduced a special configuration known as Private Browsing (Firefox) or Incognito Mode (Google Chrome). Firefox Private Browsing will automatically erase all browsing history, form and search bar entries, download lists, passwords, cookies and cached web content, offline web content, and user data from a user’s machine upon closing the browser; the private mode will also block ads with hidden trackers making following a user across different websites very difficult. You can open a new private Firefox window by going to the right corner of the main Firefox window and clicking New Private Window. Alternatively, you can press the Ctrl+Shift+P button combination to open a new private browsing window.

Google Chrome Incognito Mode window launched
Direct Attacks Against Computer Forensics Tools
Some tech-savvy criminals employ modern techniques to attack forensic tools used to acquire or analyze digital evidence. Such attacks include program packers, anti–reverse engineering techniques, and attacking the integrity of digital evidence acquired during the investigation. If successful, such attacks can hinder the credibility of the acquired evidence during legal trial.
Chapter Summary
This chapter was the reverse of the previous one. Antiforensics techniques are concerned with making digital forensics investigations very difficult to conduct and time consuming; they focus on frustrating digital forensics examiners through destroying digital evidence, hiding incriminating information so examiners cannot notice it, and manipulating evidence files to mislead the investigation and take it in the wrong direction.
As computing advances, more antiforensics tools will be developed. This will impose real challenges for computer forensic investigators to have their skills up to date. The branch of cyberforensics requires its practitioners to continue their education and stay updated with the latest tools/techniques in the industry. Antiforensics capabilities should be integrated into computer forensics suites to automatically discover technical measures implemented by offenders to conceal their incriminating activities.
In the next chapter, we are going to cover a sophisticated topic that has gained extensive coverage lately: the use of OSINT to aid law enforcement officers during their search to solve criminal cases.
