As the world goes digital, the use of computerized systems to provide services and store information becomes prevalent in both the public and private sectors. Individuals also use computing devices heavily in their daily lives; it is rare to see a person who is not dependent on some form of computing device to organize his or her digital data or to communicate with others.
The threat of cybersecurity is unquestionably growing more serious over time. A recent estimate shows that by 2021, cybercrime damages will cost the world $6 trillion annually,1 while the spending on information security products and services will grow to $93 billion in 2018, according to the latest forecast from Gartner, Inc.2 Cybersecurity Ventures expects the damage caused by ransomware attacks will increase to $11.5 billion in 20193; at that time, a ransomware attack will target businesses every 14 seconds. This dollar amount does not include the costs of attacks against individuals, which are expected to exceed even this number!
The increase in cybercrimes, terrorist threats, and security concerns in addition to the increased awareness of the importance of data on the part of authorities and business corporations has encouraged them to act and develop different digital forensics tools and methodologies to counter such threats. Nowadays, anything related to the examination, interpretation, or reconstruction of digital artifacts in a computing environment is considered within the discipline of digital forensics.
Digital forensics can be used in different contexts like government, the private sector, financial institutions, and legal; many organizations already use it as a part of their disaster recovery planning. In this introductory chapter, we will define the term “digital forensics”; describe its objectives, usage, main users, and professional certifications; look at the governmental and institutional organizations that promote its methodologies and best practices; learn about its different types; and describe its core element, which is the digital evidence.
Note!
During this book we will use the term “computing device” to refer to a digital device in the form of a smartphone, laptop, personal digital assistant (PDA), tablet, thumb drive, or any other electronic device that can store digital information.
What Is Digital Forensics?
Digital forensics is a branch of forensic science that uses scientific knowledge for collecting, analyzing, documenting, and presenting digital evidence related to computer crime for using it in a court of law. The ultimate goal is knowing what was done, when it was done, and who did it.
The term “digital forensics” is widely used as a synonym for computer forensics (also known as cyberforensics) but has expanded to cover investigating all devices that are capable of storing digital data, like networking devices, mobile phones, tablets, digital cameras, Internet of Things (IoT) devices, digital home appliances, and other digital storage media like CD/DVD, USB drives, SD cards, external drives, and backup tapes.
Under this wider definition, digital forensics is also responsible for investigating nearly all cyberattacks against computerized systems like ransomware, phishing, SQL injunction attacks, distributed denial-of-service (DDoS) attacks, data breach, cyberespionage, compromised accounts, unauthorized access to network infrastructure, and other related cyberattacks that can cause commercial or reputation loss.
Conducting computer forensic investigation requires implementing rigorous standards to stand up to cross-examination in court. This includes acquiring data (both static and volatile) in a forensically sound manner, analyzing data using court-accepted forensics tools, searching in the collected data to find evidence, and finally presenting findings to court in an official report. If these procedures are incorrectly implemented, we risk damaging or destroying digital evidence, making it inadmissible in a court of law.
Digital forensics is considered a relatively new branch in the cybersecurity domain that is becoming increasingly important with the proliferation of crimes and illegal activities in cyberspace. Compared with traditional forensic science (DNA profiling, blood tests, and fingerprinting), digital forensics is not a mature science; the fact that this science deals with fast-paced changes in the computing environment, in addition to its span over many disciplines (like the legal system, law enforcement, business management, information technology, and the borderless nature of the Internet) makes it a very challenging field that requires continual development of its methodologies, tools, and laws to counter the ever newly emerging variations of cybercrime.
Note!
“Forensically sound” is a term used in the digital forensics community to describe the process of acquiring digital evidence while preserving its integrity to be admissible in a court of law.
Digital Forensics Goals
- 1.
Finding legal evidence in computing devices and preserving its integrity in a way that is deemed admissible in a court of law.
- 2.
Preserving and recovering evidence following court-accepted technical procedures.
- 3.
Attributing an action to its initiator.
- 4.
Identifying data leaks within an organization.
- 5.
Accessing possible damage occurring during a data breach.
- 6.
Presenting the results in a formal report suitable to be presented in court.
- 7.
Providing a guide for expert testimony in court.
Cybercrime
In a nutshell, cybercrime includes any illegal activity committed using a type of computing device or computer networks such as the Internet. The US Department of Justice (DOJ) defines cybercrime as “any criminal offense committed against or with the use of a computer or computer network.” The major motivation behind cybercrime is financial gain (example: spreading malware to steal access codes to bank accounts). However, a good portion of cybercrime has different motivations, like interrupting service (for example, DDoS attacks to stop services offered by the target organization), stealing confidential data (example: consumer data, medical information), exchanging copyrighted materials in an unlawful way, and cyberespionage (corporate trade and military secrets).
Cybercrime Attack Mode
Insider attacks: This is the most dangerous cyberrisk facing organizations today, as it can last for a long time without them knowing about it; such attacks come when there is a breach of trust from employees—or other people like former employees, third-party contractors, or business associates—working within the target organization who have legitimate access to its computing systems and/or information about its cybersecurity practices and defenses. Economic espionage falls under this category.
External attacks: This kind of attack originates from outside the target organization, usually coming from skilled hackers. Such attacks constitute the largest attacks against organizations around the world. A black hat hacker can try to penetrate the target organization’s computing networks from another country to gain unauthorized access. Sometimes external attackers gain intelligence from an insider (disgruntled employee) in the target company who has information about its security systems to facilitate their illegal access.
How Are Computers Used in Cybercrimes?
- 1.
A computing device is used as a weapon to commit a crime. Example: Launching denial-of-service (DoS) attacks or sending ransomware.
- 2.
A computing device is the target of a crime. Example: Gaining unauthorized access to a target computer.
- 3.
A computing device is used as a facilitator of a crime. Example: Using a computer to store incriminating data or to make online communications with other criminals.
Example of Cybercrime
Different types of computer threats are associated with varied types of damaging effects. For example, some threats may damage or corrupt your installed operating system and force you to reinstall it. Another type may steal your credentials and saved passwords. Still other threats may not bring any harm to your PC; instead, they will track your online activities and invade your privacy.
Today, criminals are smarter than ever before, and malicious programs are more sophisticated. Modern malware can infect a target computing device and remain undetected for a long time. The motive behind the majority of cyberattacks nowadays is not to damage your machine, but instead to steal your money, to access your private information, or to acquire your logon credentials.
Similar to traditional crime, cybercrime can be grouped into various categories according to the malicious actor’s objective for applying it. The following are the most common forms of cybercrime.
Malware Distribution
Malware is short for “malicious software” and is any software employed to bring damage to computing devices (computers, smartphones, etc.) or the stored content (data or applications). Malware corruption can manifest in different ways, such as formatting your hard disk, deleting or corrupting files, stealing saved login information, gathering sensitive information (your files and private photos), or simply displaying unwanted advertisements on your screen. Many malware variants are stealthy and operate silently without the user’s knowledge or awareness. Malware is a term used to refer to many types of malicious software such as computer viruses, worms, Trojan horses, spyware, ransomware, rootkit, scareware, and adware.
Ransomware Distribution
Ransomware is computer malware that installs silently on the user’s machine. Its objective is to deny access to user files, sometimes encrypting the entire hard drive (HD) and even all the attached external drives and connected cloud storage accounts. It then demands that the user pay a ransom to get the malware creator to remove the restriction so the user can regain access to the system and stored assets.
CryptoJacking
This is a piece of code, usually written in JavaScript, that infects your computer silently via web browser to mine cryptocurrencies. As the cryptocurrency wave is on the rise, more cybercriminals are using such techniques for commercial gain using other peoples’ computers without their knowledge. This attack consumes much of the target computer’s CPU speed.
Hacking
Hacking is the process of invading your privacy by gaining unauthorized access to your computing device or internal network. Hackers usually scan your machines for vulnerabilities (such as unpatched Windows updates) and gain access through them. After gaining access, they may install a keylogger or a Trojan horse to maintain their access, to begin stealing information, or to spy on user activities.
SQL Injections
This is a hacking technique that allows hackers to attack the security vulnerabilities of the database that runs a web site. An attacker enters SQL code into target web site web forms and executes it to force the back-end database of the web site to release confidential information to the attacker.
Note!
Modifying computer program code to steal money in small amounts is also a crime committed by evil programmers or anyone who has access to the financial software source code.
Pharming
This is a cyberattack intended to redirect users from a legitimate web site to a fraudulent site without their knowledge. The end goal is usually to infect the target computer with a malware.
Phishing
Phishing messages come in different shapes, such as SMS messages, e-mails, and web site links (URLs), all of which are designed to look genuine and use the same format as the legitimate company they pretend to be. Phishing aims to collect user-sensitive details (such as banking information, login credentials, and credit card info) by tricking the end user into handing the information to the attacker.
Note!
The United States Computer Emergency Readiness Team (US-CERT) defines phishing as follows: “…an attempt by an individual or group to solicit personal information from unsuspecting users by employing social engineering techniques. Phishing e-mails are crafted to appear as if they have been sent from a legitimate organization or known individual. These e-mails often attempt to entice users to click a link that will take the user to a fraudulent web site that appears legitimate. The user then may be asked to provide personal information, such as account usernames and passwords, that can further expose them to future compromises. Additionally, these fraudulent web sites may contain malicious code.”4
E-mail Bombing and Spamming
E-mail bombing occurs when an intruder, or a group of intruders, sends a large volume of e-mails to a target server or target e-mail account, making it crash. Spam is unsolicited e-mail that usually sent to a large number of users for commercial purposes (showing ads or promotions); however, many spam e-mails contain disguised links that can lead the victim to phishing web sites or to malicious web sites hosting malware to further infect the user’s machine.
Identity Theft
Identity theft is stealing personal information about people and using it in an illegal context.
Cyberstalking
This is an invasion of the user’s privacy; it works when an intruder follows a target person’s online activity and tries to harass/threaten him or her using verbal intimidation via e-mail, chat services, and social media. The wide reach of social media sites and the vast amount of personal details available publicly make cyberstalking a major problem in today’s digital age.
Using Internet Network Illegally
Spreading illegal contents and selling illegal services and products. Example include spreading hate and inciting terrorism, distributing child pornography online, and selling drugs and weapons (especially in the darknet market).
DDoS Attacks
A DDoS attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. Attackers build networks of infected computers, which could be millions of machines, known as botnets, by spreading malicious software through e-mails, web sites, and social media. Once infected, these machines can be controlled remotely by a bot master, without their owners’ knowledge, and used like an army to launch an attack against any target.
Social Engineering
Social engineering is a kind of attack that uses psychological tricks (social tricks) over the phone or uses a computing device to convince someone to hand over sensitive information about himself or herself or about an organization and its computer systems.
Software Piracy
This is the unauthorized use, downloading, and distribution of pirated material like movies, games, software, songs, books, and other intellectual property products.
Cybercrimes could be conducted by either one person or a group of organized criminals; the latter is more dangerous as it has the resources to conduct and develop sophisticated attacks against target organizations and individuals.
Digital Forensics Categories
Digital forensics can be grouped according to the source of the acquired digital evidence.
Note!
“Digital evidence” is a term that refers to the sum of digital artifacts found on the target computing device that can be used as evidence in a court of law. Digital evidence is covered thoroughly later on in this chapter.
Computer Forensics
This is the oldest type of digital forensics; it is concerned with investigating digital evidence found on desktop computers, on laptops, on digital storage devices (like external hard drives, thumb drives, and SD cards), and in random access memory (RAM), in addition to operating systems and installed application traces and their associated logs. The main activity of this type is recovering deleted data from the target device’s storage and analyzing it for incriminating or exonerating evidence.
Mobile Forensics
Mobile forensics is a type of digital forensics concerned with acquiring digital evidence from mobile devices. Mobile devices include any computing device (such as phones, smartphones, tablets, and wearable devices such as smart watches) able to make phone calls using standard communication networks like GSM, 3G, 4G, and so on. Such a device is usually location aware, meaning that it has a built-in GPS or similar satellite positioning system. The proliferation of mobile technology among users globally will soon make mobile forensics the most used branch among other digital forensics types.
Network Forensics
This type of digital forensics is concerned with monitoring and analyzing traffic flow in computer networks to extract incriminating evidence (e.g., discovering the source of security attacks) or to detect intrusions. Data flow through networks can be captured as a mass in real time and stored for later analysis or analyzed in real time with an option to save only segments of interesting events for further offline analysis (this option require less storage space). Network forensics deals with volatile (live) data only, unlike other digital forensics types.
Database Forensics
Database forensics is concerned with the analysis of data and metadata existing within a database such as Microsoft SQL Server, Oracle, MySQL, and others. Database forensics looks for who accesses a database and what actions are performed to help uncover malicious activities conducted therein.
Forensics Data Analysis
This branch deals with analyzing corporate structured data to prevent and discover fraud activities resulting from financial crime. It looks at meaningful patterns within corporate data assets and compares it with historical results to detect and prevent any misuse of corporate resources.
There are also other specific types of digital forensics like e-mail forensics, cloud storage forensics, forensics for specific application (e.g., Web browser forensics), file system forensics (NTFS, FAT, EXT), hardware device forensics, multimedia forensics (text, audio, video, and images), and memory forensics (RAM [volatile memory]); however, all these are small subbranches that fall within the main types already mentioned.
Digital Forensics Users
Digital forensics can be used in different contexts in virtually all sectors and businesses. The widespread usage of computing technology and Internet communications makes this science integrated across different domains.
Law Enforcement
Digital forensics was originally developed to aid law enforcement agencies in applying the law and to protect society and businesses from crime. Law enforcement officials use digital forensics in different contexts to detect offenses and associate illegal actions with the people responsible for them. Indeed, using digital forensics is not limited to cybercrimes, as most traditional crimes may require collecting digital evidence from the crime scene (e.g., a mobile phone found at a murder scene will certainly require investigation, and the same applies to a laptop and/or thumb drives found in a drug dealer’s home).
For the law enforcement computer forensics specialist, a predefined digital forensics methodology should be followed strictly when collecting, preserving, analyzing, and presenting digital evidence. The investigation procedures will largely depend on the jurisdiction responsible for investigating the subject crime. A search warrant is usually needed, where applicable, before the law enforcement officer can seize the hardware (computing device) involved in the crime.
Civil Ligation
Using digital forensicsin civil ligation has become big business these days. Business corporations use digital forensics techniques and methodologies as part of their electronic discovery process to find incriminating digital data that can be used as evidence in a civil or criminal legal case. E-discovery is considered an integral part of the justice system, although the implemented digital forensics procedures in civil ligation are somehow different from the one applied in criminal cases in terms of the procedures used to acquire digital evidence, investigatory scope, and the legal consequences of the case.
Most cases in business corporations are motivated by financial gain. Example include violations of the company’s policy, financial theft, intellectual property theft, fraud, bribery, tax evasion, misuse of company resources, industrial espionage, embezzlement, and commercial dispute. Other known corporate digital-related crimes includes e-mail harassment, gender and age discrimination, and sabotage. Companies utilize digital forensics techniques as a part of their e-discovery process to discover and retrieve digital evidence in order to know the source, entity, or person responsible for such violations. The outcome of such investigations may lead to terminating the offending employee, giving a warning (if the violation is limited and unimportant), or prosecuting him/her if the case is to be taken to a court of law.
Using digital forensics in civil ligation is not limited to the business world; personal cases like family problems and divorce also fall under this category.
Legal Tip!
You can find the Federal Rules of Evidence that govern the introduction of evidence at civil and criminal trials in US federal trial courts at www.rulesofevidence.org .
Intelligence and Counterintelligence
Intelligence agencies use digital forensics techniques and tools to fight terrorist activities, human trafficking, organized crime, and drug dealing, among other dangerous criminal activities. Digital forensics tools can help officers uncover important information about criminal organizations through investigating a criminal’s digital devices, monitoring networks, or acquiring information from publicly available sources such as social media sites—known as open source intelligence (OSINT)—about the person/entity of interest.
Note!
OSINT refers to all information that is publicly available. OSINT sources are distinguished from other forms of intelligence in that they must be legally accessible by the public without breaching any copyright or privacy laws. Chapter 10 will discuss OSINT in some detail .
Digital Forensics Investigation Types
- 1.
Public investigations
- 2.
Private (corporate) sector investigations
General public sector criminal investigation flow
Private investigations are usually conducted by enterprises to investigate policy violations, litigation dispute, wrongful termination, or leaking of enterprise secrets (e.g., industrial espionage). There are no specific rules (or laws) for conducting such investigations as it depends on each enterprise’s own rule; however, many organizations are now following strict procedures for investigating digital crimes internally. These procedures are similar to public investigations when investigating crime, as some cases can be transferred later to court and becomes official criminal cases.
Enterprises can reduce ligation related to computer crime by setting a clear policy that can be easily read and understood by their employees. Such policy can also make digital forensics investigation (once needed) easier to conduct with minimal downtime of the running business. The most important policy that should be signed by all enterprise employees is computer usage policy. This policy defines how employees can use company IT equipment like computers and networks and promises them that there will be legal consequences if they violate these terms.
Note!
Always treat a private investigation as if it will end up in court. This will force you to follow strict investigatory procedures when building your case and thus protect your organization’s private assets if the case ends up in court.
Forensics Readiness
Forensics readiness is about the ability of a particular organization to collect, preserve, protect, and analyze digital evidence in a forensically sound manner. The process should proceed without disrupting current operations to minimize investigation cost.
The Importance of Forensic Readiness for Organizations
High response to incidents with digital evidence. When an incident (e.g., data breach or information leakage) that requires the collection of digital evidence occurs, the existence of a clear e-discovery process in place will help organizations act promptly and acquire digital evidence in a forensically sound manner.
Compliance with government-applied regulations. Since 2015, US Federal Rules of Civil Procedure5 have imposed a set of requirements on parties involved in a legal dispute on how to collect and preserve digital evidence in order to be acceptable in a court of law. Forensic readiness will reduce the cost of acquiring digital evidence and will certainly lead to faster resolution if the case is taken to court.
Strengthening organizational security defense. Utilizing forensic readiness will make an organization well prepared to handle internal and external security incidents and able to identify an attack quickly before it dives deeply into its IT infrastructure (e.g., monitoring usage on endpoint computers may uncover dangerous malware, such as ransomware, before the infection spreads to the entire organization’s network).
Minimizing internal attacks. As we already said, internal threats (e.g., originating from a disgruntled employee) are more dangerous than external attacks; the existence of a forensic readiness plan in an organization will make malicious insiders fear being caught if they carry out any illegal activities.
Increasing an organization’s security posture. Forensic readiness planning will make an organization stand out as an entity with great defense against cyberthreats. Customers will be more willing to deal with this organization as their confidential transactions will be protected and secure. Investors will also be assured that their investment is protected and there is a limited possibility of launching successful attacks against this organization and consequently damaging their investment.
Electronic Discovery Reference Model (EDRM)
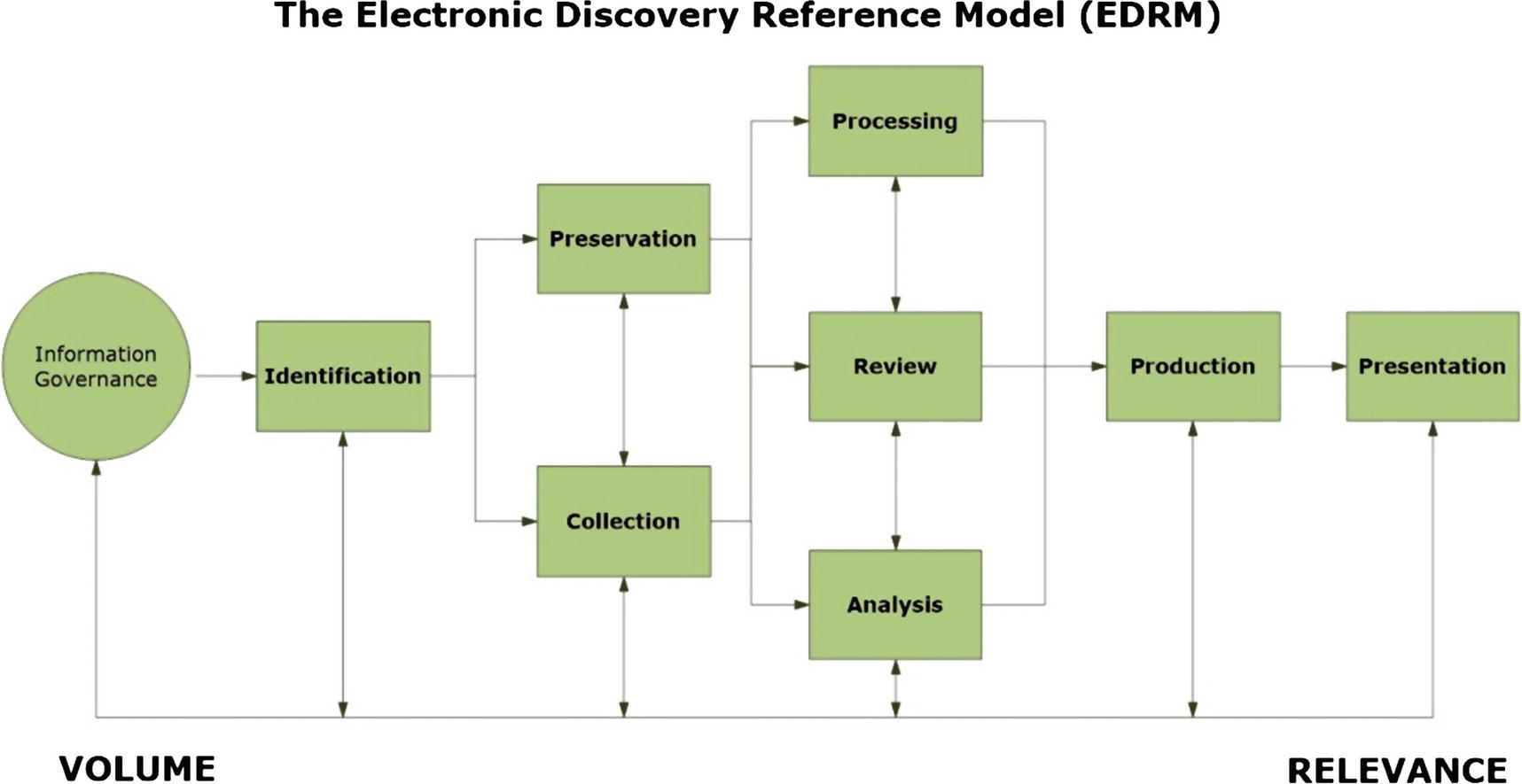
EDRM reference model
Developing a forensic readiness plan has become a must for any organization or corporation that wants to survive in today’s digital age.
Digital Evidence
According to the a Universe study report,6 the amount of digital data produced by humans and machines (e.g., IoT devices) will exceed 44 zettabytes by the year 2020 (1 zettabyte = 1 billion terabytes). People are increasingly accessing the Internet and using it on a daily basis to socialize, send e-mails, and browse the Internet; most of these activities will produce traces and remain present on users’ computing devices for many years to come. Most computer users are not tech savvy; they might think that the deletion of a file erases it completely and forever from their hard drive, but this is quite wrong. Data stored on storage units can be restored even after formatting the drive many times; although certain tools can be used to further wipe hard drive space to make it irrecoverable (this is discussed in Chapter 9), even these advanced tools can still leave traces, allowing computer forensic investigators to obtain essential evidence to help them solve criminal cases and prevent other crimes using computer forensic techniques.
Note!
The ability to restore deleted data from storage units depends on its type and the installed operating system, as we are going to see later in this book.
Computer forensics involves acquiring digital evidence-sometimes known as electronically stored information (ESI)-from a computer hard drive, a mobile phone, a tablet or PDA, or other storage media (like CD/DVD, USB thumb drive) among other places, in a systematic way; this ESI is to be used in court during trials.
Digital Evidence Types
- 1.
We can differentiate between two main types of digital artifacts according to who has created them:
- 2.
User-created data
- 3.
User-created data includes anything created by a user (human) using a digital device. It includes the following and more:
- 4.
Text files (e.g. MS Office documents, IM chat, bookmarks), spreadsheets, database, and any text stored in digital format,
- 5.
Audio and video files,
- 6.
Digital images,
- 7.
Webcam recordings (digital photos and videos),
- 8.
Address book and calendar,
- 9.
Hidden and encrypted files (including zipped folders) created by the computer user,
- 10.
Previous backups (including both cloud storage backups and offline backups like CD/DVDs and tapes),
- 11.
Account details (username, picture, password),
- 12.
E-mail messages and attachments (both online and client e-mails as Outlook),
- 13.
Web pages, social media accounts, cloud storage, and any online accounts created by the user.
Files created by a computer user also contain metadata; the metadata could be either produced on purpose by the computer user (e.g., author name and e-mail) or generated automatically by the software used to create it (e.g., GPS coordination of a specific photo, captured camera type, and resolution). As we insist in Chapter 2, metadata should also be investigated thoroughly during any investigation, as it may contain substantial evidence about the case in hand.
Warning!
In Windows OS, you can view any file metadata be right-clicking over it and selecting “Properties.” However, keep in mind that whenever you access a file under Windows, you are changing some system-created metadata (last access date) about it, which should be taken into account during investigation.
Machine/Network-Created Data
- 1.
Computer logs. These include the following logs under Windows OS: Application, Security, Setup, System, Forward Events, Applications, and Services Logs,
- 2.
Router logs, including third-party service provider (e.g., Internet service providers (ISPs) commonly store users’ account web browsing history logs),
- 3.
Configuration files and audit trails,
- 4.
Browser data (browser history, cookies, download history),
- 5.
Instant messenger history and buddy list (Skype, WhatsApp),
- 6.
GPS tracking info history (from devices with GPS capability),
- 7.
Device Internet protocol (IP) and MAC addresses in addition to the IP addresses associated with a LAN network and the broadcast settings,
- 8.
Applications history (e.g., recently opened file on MS Office) and Windows history,
- 9.
Restore points under Windows machines,
- 10.
Temporary files,
- 11.
E-mail header information,
- 12.
Registry files in Windows OS,
- 13.
System files (both hidden and ordinary),
- 14.
Printer spooler files,
- 15.
Hidden partition and slack space (can also contain hidden user information),
- 16.
Bad cluster,
- 17.
Paging and hibernation files,
- 18.
Memory dump files,
- 19.
Virtual machines,
- 20.
Surveillance video recordings.
We can summarize “digital evidence” as any kind of file or data/metadata that is presented in digital format (binary format) and could be used during a trial.
Locations of Electronic Evidence
- 1.
Desktops
- 2.
Laptops
- 3.
Tablets
- 4.
Servers and RAIDs
- 5.
Network devices like hubs, switches, modems, routers, and wireless access points
- 6.
Internet-enabled devices used in home automation (e.g., AC and smart refrigerator)
- 7.
IoT devices
- 8.
DVRs and surveillance systems
- 9.
MP3 players
- 10.
GPS devices
- 11.
Smartphones
- 12.
PDA
- 13.
Game stations (Xbox, PlayStation, etc.)
- 14.
Digital cameras
- 15.
Smart cards
- 16.
Pagers
- 17.
Digital voice recorders
- 18.
External hard drives
- 19.
Flash/thumb drives
- 20.
Printers
- 21.
Scanners
- 22.
Fax machines (e.g., incoming and outgoing fax numbers)
- 23.
Copiers (e.g., recently copied files)
- 24.
Fixed telephony and cordless phones (e.g., calls made, received, and answered, voice messages and favorite numbers)
- 25.
Answering machines
- 26.
Backup tapes
Note!
There are different sources of digital evidence, and each one requires a different method/tool to acquire it. The focus of this book will be on acquiring digital evidence from computers running Windows OS in addition to thumb drives and external hard drives.
Tip!
Digital devices can contain other sources of evidence like fingerprints, DNA, and other identifiers that should not overlooked during investigation.
Challenge of Acquiring Digital Evidence
- 1.
Locked computer with a password, access card, or dongle.
- 2.
Digital steganography techniques to conceal incriminating data in images, videos, audio files, file systems, and in plain sight (e.g., within MS Word document).
- 3.
Encryption techniques to obscure data, making it unreadable without the password.
- 4.
Full disk encryption (FDE) including system partition (e.g., BitLocker drive encryption).
- 5.
Strong passwords to protect system/volume; cracking them is very time consuming and expensive.
- 6.
File renaming and changing their extensions (e.g., changing DOCX into DLL, which is a known Windows system file type).
- 7.
Attempts to destroy evidence through wiping the hard drive securely using various software tools and techniques.
- 8.
Removing history from the web browser upon exit and disabling system/application logging where available.
- 9.
Physically damaged digital media; for example, we cannot retrieve deleted files from a failed HDD before repairing it.
- 10.
Sensitivity of digital evidence; if not handled carefully it might be destroyed. Heat, cold, moisture, magnetic fields, and even just dropping the media device can destroy it.
- 11.
Easy alteration of digital evidence; for instance, if a computer is ON, you must leave it ON and acquire its volatile memory (if possible), but if the computer is OFF, leave it OFF to avoid changing any data.
- 12.
Laws governing the collection of digital evidence and device seizure, which differ from one state to another (and between one country and another). Cybercrimes can cross boarders easily through the Internet, making the lack of cyberlaw standardization a major issue in this domain.
- 13.
The issue of data ownership; for example, if investigators captured a USB thumb drive that belongs to a suspect, but the data inside it is fully encrypted and protected with a password, the suspect can deny its ownership of this thumb, making the decryption process very difficult to achieve without the correct password/key file.
Note!
You might think physical damage to media devices will render them useless and prevent any recovery of data from it. This is completely wrong. Advanced digital forensics labs have the ability to restore data from heavily damaged devices like burned, smashed, and sunken devices. So always take the device to an expert digital forensic examiner to analyze it.
The techniques mentioned briefly herein to frustrate computer investigators will be described in some detail in Chapter 9; however, keep in mind that the majority of criminals are not tech savvy. Those people will not employ advanced methods to cover their tracks. Even though some of them may use different privacy techniques to cover their files and activities on the computer, the majority will not implement them 100% correctly, and this will leave a door open for examiners to do their job and break in to acquire valuable information from the suspect computing device.
Who Should Collect Digital Evidence?
Analytical thinking: This includes the ability to make correlations between different events/facts when investigating a crime.
Solid background in IT knowledge: This includes wide knowledge about different IT technologies, hardware devices, operating systems, and applications. This does not mean that an investigator should know how each technology works in detail, but he should have a general understanding of how each technology operates.
Hacking skills: To solve a crime, you should think like a hacker. Knowing attack techniques and cybersecurity concepts is essential for a successful investigation.
Communication and organizational skills: An investigator should have documentation skills to organize his/her findings and present them to other members of the team and to attorneys and judges.
Understanding of legal issues concerning digital crime investigations.
Excellent knowledge of technical skills related to digital forensics like data recovery and acquisition and writing technical reports.
Online searching skills and ability to gather information from publicly available sources (i.e., OSINT).
THE ROLE OF EXPERT WITNESS
Sometimes, a digital forensics professional will play the role of expert witness in a court of law, but what differentiates an expert witness from a nonexpert witness or conventional witness?
The typical witness will testify on what he saw or heard, while the expert witness will have the opportunity to give his/her opinion to the court. Judges and jury are not always familiar with the technical details associated with digital crimes, so an expert witness should help them to assimilate and understand these technical details.
An expert witness does not have to hold an advanced academic degree to testify, however. He needs to show a proven technical ability that clearly demonstrates he fully understands the subject he is going to testify about. To make expert witness testimony effective in court, it is recommended that this expert have the ability to convey complicated technical details for something easy to assimilate by nontechnical people like judges and jury members. Often, such people work in the teaching field and authors can play this role very well.
Chain of Custody
Chain of custody is an integral part of any digital forensic investigation process. Proper chain of custody must declare clearly how digital evidence was discovered, acquired, transported, investigated (analyzed), preserved, and handled between different parties involved in the investigation. The ultimate goal is to ensure the integrity of digital evidence through knowing all persons who were in contact with this evidence from its acquisition to its presentation in a court. If we fail to understand who was in contact with the evidence during any phase of investigation, the chain of custody will be jeopardized and the acquired evidence will become useless in a court of law.
- 1.
What is the digital evidence? (E.g., describe the acquired digital evidence.)
- 2.
Where was the digital evidence found? (E.g., computer, tablet, cell phone, etc.; also to be included is the state of the computing device upon acquiring the digital evidence–ON or OFF?)
- 3.
How was the digital evidence acquired? (E.g., tools used; you also need to mention the steps taken to preserve the integrity of evidence during the acquisition phase.)
- 4.
How was the digital evidence transported, preserved, and handled?
- 5.
How was the digital evidence examined? (E.g., any tools and techniques used.)
- 6.
When was the digital evidence accessed, by whom and for what reason?
- 7.
How was the digital evidence used during the investigation?
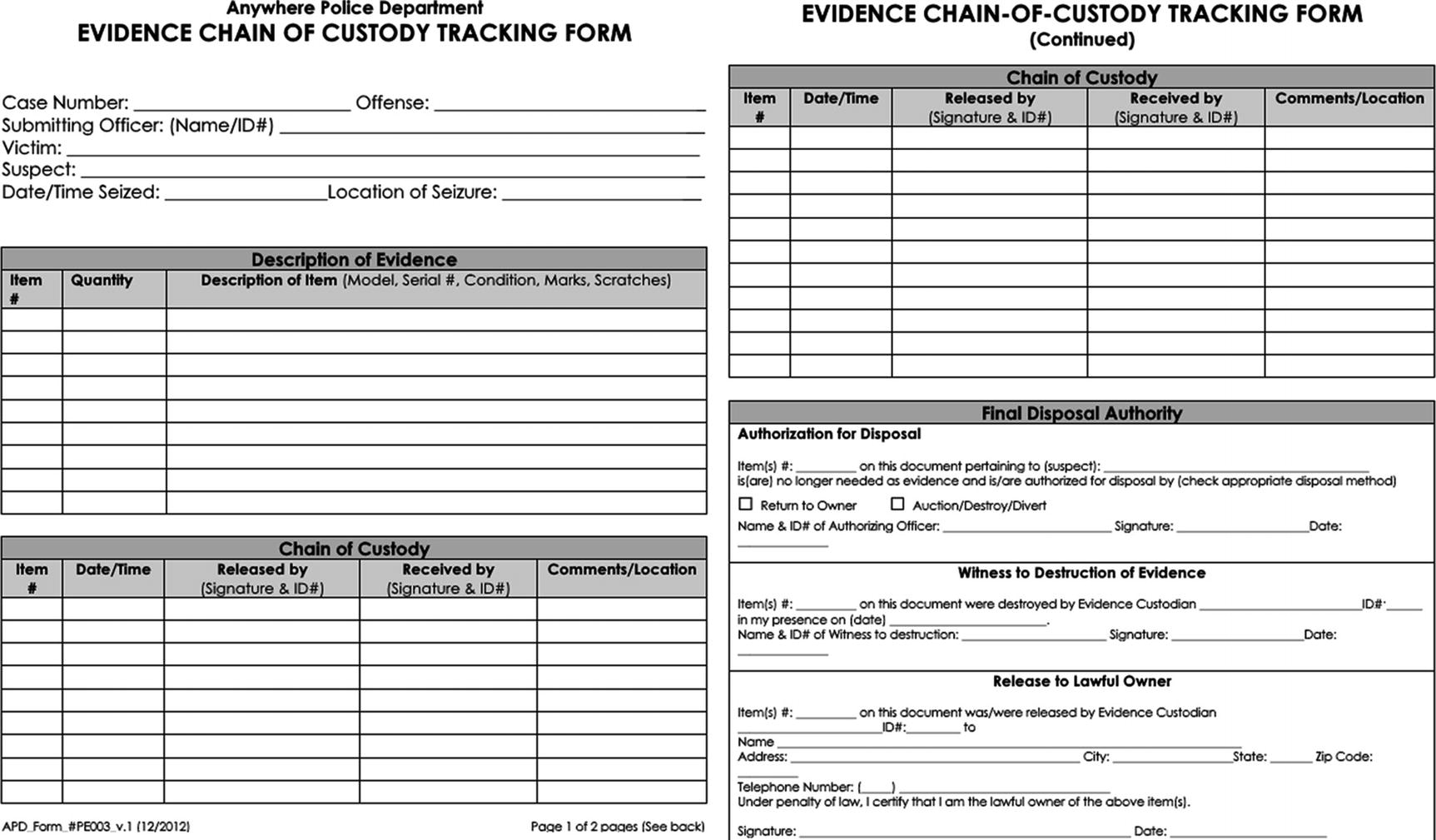
Sample chain of custody form (template) suggested by the National Institute of Standards and Technology (NIST) to track digital evidence during legal investigations. Source: www.nist.gov/document/sample-chain-custody-formdocx .
A predefined investigation methodology should be followed when acquiring, preserving, and analyzing digital evidence, and this what we are going to cover next.
Digital Forensics Examination Process
- 1.
Seizure
- 2.
Acquisition
- 3.
Analysis
- 4.
Reporting

Common phases of digital forensics
Warning!
No matter what your chosen forensic process has been, it is crucial to apply a process with sound forensics practice that conforms to the current jurisdiction laws.
Seizure
In this phase, the physical evidence (digital device) will be seized and transferred safely to the forensic lab. This evidence can be any computing device type such as laptop, tablet, mobile phone, external hard drive, USB flash drive, wearable device (e.g., digital watch), or even a desktop PC. Remember, you need to have a permission from the proper authority (e.g., court warrant) to seize the suspect’s machine.
Upon arriving to the crime scene, the suspect digital device should be examined by a well-trained technician to ensure the digital evidence is acquired/preserved in a forensically sound manner. If the suspect computer was still running, then we should consider acquiring its volatile memory (RAM) if possible. The old-school practice was to unplug the computer and then seize it in a special antistatic case. However, modern forensic practices appreciate the great importance of acquiring volatile memory while the PC is still running. RAM memory can contain a wealth of information like cryptographic keys, IM chat logs, unencrypted contents, clipboard contents, and process information, among other things. Acquiring RAM memory should be documented along with the tool used in the final investigative report, as the tool used to extract RAM content will bring minor changes to the target operating system files, RAM memory, and hard drive.
Acquisition
This phase deals with the computing secondary storage device (e.g., HDD, solid state drive [SSD], thumb drive, tape drive) and with the volatile memory (RAM) if the computer was still running. In this phase, a computer forensic examiner will conduct a duplication of the suspect hard drive (this is also known as a bit-to-bit image) to create a complete image of the seized hard drive. Analysis will be performed on the digital copy later. Examiners usually use hardware duplicators or software imaging tools like the DD command in Linux to duplicate drives. Remember that the suspect hard drive should be write-protected when conducting the duplication process to avoid tampering with the original evidence. If the suspect machine was still running, RAM memory should be acquired considering the different scenarios, as we are going to see in Chapter 4.
Note!
It is very important to have more than one copy (image) of the acquired suspect hard drive. The forensics analysis will be conducted on a copy of the digital evidence, so that original media will remain intact and can be verified at a later stage for accuracy.
Analysis
In this phase, the contents of the acquired forensic image file are investigated using a set of tools to search for interesting leads within the acquired image. Hidden, deleted, and encrypted files in addition to IM chat logs, Internet browsing history, and deleted e-mails can all be recovered using specialized tools like EnCase, Sleuth Kit, Volatility, and Forensic Toolkit (FTK) from AccessData, to name a few.
During this phase, hash signature analysis is used (as we are going to see in the next chapter) by the forensic tool to identify notable files or to exclude known ones. Acquired image file contents are hashed and compared to precompiled lists such as the Reference Data Set (RDS) from the National Software Reference Library, which tries to collect software from various sources and incorporate file profiles computed from this software into an RDS of information. The RDS can be used to review files on the seized computers by matching file profiles in the RDS. This will help alleviate much of the effort involved in determining which files are important as evidence on computers or system files that have been seized as part of criminal investigations. You can download a single 7GB ISO image containing all data from www.nsrl.nist.gov/Downloads.htm .
Forensic tools can also perform searches within the acquired image file using keyword search terms or phrases. This will effectively speed up the investigation and help investigators to find relevant information quickly.
Incriminating evidence will be recovered and analyzed to reach conclusions related to the case at hand. All these facts will be presented later in a formal report, as we will see in the next stage.
Note!
If you do not know what is meant by hash, check the “Hash Analysis” section in the next chapter. For now, consider hashing as a digital fingerprint (a set of unique strings) of any digital data. It is used to compare the original evidence (e.g., the sum of data existing on a hard drive) to the acquired forensic image of the same hard drive. When the two hash values match, this means that the two files are 100% identical.
Reporting
In this phase, the examiner produces a structured report about his/her findings. Such a report is usually prepared for nontechnical people (like attorneys, judges, and juries). Writing style, terminology, and the way facts are presented should be taken into consideration when writing the report. Evidence should be presented along with the report, mostly in digital format.
Summary of key findings.
Description of tools (both hardware and software) used during the investigation process and the function of each in addition to the version of the software tools.
Method used to acquire the digital evidence.
Description of the digital evidence (image content) and the interesting artifacts found within it (e.g., Internet browsing history, e-mail history, USB registry analysis, deleted files found). It is preferable to use screen captures where applicable to describe to the reader steps undertaken to analyze digital evidence.
Explanation of technical terms used like “unallocated disk space,” “Host Protected Area,” and the like so nontechnical people can understand the technical terms mentioned in the report.
Conclusion of the investigation.
The original suspect hard drive and digital copies of it (images) should be presented along with the report to the court.
Digital Forensics Process Official Guides
NIST published a guide titled “Guide to Integrating Forensic Techniques into Incident Response” ( http://csrc.nist.gov/publications/nistpubs/800-86/SP800-86.pdf ) that addresses most issues related to handling computer security incidents in addition to making general recommendations for performing a digital forensic process and how to conduct it on four different groups of data sources: files, operating system, network traffic, and applications.
US DOJ published a guide titled “Forensic Examination of Digital Evidence: A Guide for Law Enforcement” ( www.ncjrs.gov/pdffiles1/nij/199408.pdf ) that describes procedures and best practices for the examination of digital evidence. Other guides from the same source are “Electronic Crime Scene Investigation: A Guide for First Responders,” which can be found at www.ncjrs.gov/pdffiles1/nij/187736.pdf , AND “Digital Evidence in the Courtroom: A Guide for Law Enforcement and Prosecutors,” which can be found at www.ncjrs.gov/pdffiles1/nij/211314.pdf .
The Association of Chief Police Officers, which leads the development of policing practices in the United Kingdom, has also published a guidance called “ACPO Good Practice Guide for Digital Evidence” to ensure the authenticity and integrity of evidence during computer forensic investigations. Currently, the last updated version of the guide is version 5, you can find it at www.acpo.police.uk/documents/crime/2011/201110-cba-digital-evidence-v5.pdf .
There are many bodies interested in developing digital forensics standards in collaboration with different actors like government bodies, digital forensics investigators, and academia; one of these is the Digital Forensic Research Workshop ( www.dfrws.org ).
Digital Forensics Certifications
- 1.
Computer Hacking Forensic Investigator (CHFI) ( www.eccouncil.org/programs/computer-hacking-forensic-investigator-chfi/ ) offered by EC-Council. The exam covers forensics tools, analytical techniques, and steps involved in acquiring, maintaining, and presenting digital forensic evidence in a court of law. You can attempt the CHFI exam without attending an official training; however, you need to pay a nonrefundable $100 eligibility application fee. You must renew this certification every three years (various options are available to renew EC-Council certifications).
- 2.
Certified Forensic Computer Examiner (CFCE) ( www.iacis.com/certifications/cfce ) offered by the International Association of Computer Investigative Specialists (IACIS). This certificate requires candidates to register for an official course to be eligible to register for its exam. Without the official training, candidates need to pay for registration fee and pass a background check to enroll in the CFCE program and sit for the exam. This certification has high value and excellent recognition among other digital forensics certificates.
- 3.
GIAC Certified Forensic Examiner (GCFE) and GIAC Certified Forensic Analyst (GCFA) ( www.giac.org ). Both certifications are offered by GIAC, focus on computer forensics investigation and incident response, and cover collecting digital evidence from both Windows and/or Linux computer systems. Certification is valid for four years and a maintenance fee of $429 must be paid every four years. You need to take official training before attempting these exams.
- 4.
Certified Computer Crime Investigator (types: basic and advanced) ( www.htcn.org/site/certification-requirements.html ) offered by the High Tech Crime Network. To sit for this exam you need to have three or five years’ experience (three for basic and five for the Advanced level) directly related to the investigation of technical incidents or technical crimes in either law enforcement or corporate. You also need to have followed a training related to cybercrime offered by an approved center or organization, and finally you have to write a narrative report describing some criminal cases you have already solved.
- 5.
AccessData Certified Examiner (ACE) ( http://accessdata.com/training/computer-forensics-certification ) offered by AccessData the vendor of FTK. Obviously, this certification measures a candidate’s ability to use the latest version of this tool in investigations. There is no formal training required before attempting this exam. Exam recertification is required every two years. Current exam fees $100.
- 6.
EnCase Certified Examiner (EnCe) ( www2.guidancesoftware.com/training/Pages/ence-certification-program.aspx ) offered by OpenText. This certification measures a candidate’s ability to use Guidance Software’s EnCase computer forensic software. No formal training is required in order to attempt this exam. EnCe certifications are valid for three years from the date obtained and the cost of renewal is $75.
Digital Forensics vs. Other Computing Domain
Digital forensics is considered a standalone domain, although it has some overlap with other computing domains such as computer security (also known as cybersecurity), data recovery, and disaster recovery. The ultimate aim of digital forensics is to acquire, preserve, and analyze digital artifacts in a forensically sound manner to be used in a court of law.
Computer security aims to protect systems and data according to specific security policy set by individuals or organizations, whereas digital forensics tries to explain how a security policy came to be violated. One of the aims of computer security is to protect user data and ensure his/her privacy by using encryption, access controls, and steganographic techniques, while digital forensic tries to recover passwords, access encrypted files, discover hidden data, investigate violation of access controls, and recover deleted files and wiped disks for evidence.
Computer data recovery involves recovering data from computers that was deleted by a mistake or lost because of power failure or hardware crash. Many data recovery cases involve fixing hardware damage to hard drives or other digital storage units. In data recovery, the user usually knows what he is looking for; however, in digital forensics, an investigator is searching for hidden data and intentionally deleted files to use as evidence during a trial.
Disaster recovery has many things in common with digital forensics, as it uses many of its techniques to restore data that has been lost; the main difference between these two is the final outcome of the process and the way to achieve it. The ultimate goal of digital forensics is still acquiring data following strict procedures so that it can be admissible in a court of law.
Finally, e-discovery is concerned with searching within a large volume of digital data sets (e.g., backup tapes, storage servers) for interesting evidence that can be presented in a court of law as a part of corporate private investigations. E-discovery does not deal with damaged hardware as is the case with data recovery. When used in US courts, e-discovery processes are usually conducted under the Federal Rules of Civil Procedure (“FRCP”) guidelines.
Chapter Summary
In this chapter, we introduced the term “digital forensics” and differentiated between it and other kind of cybersecurity domains. We briefly covered the concept of digital evidence, its types, and where we can find it in electronic devices. There is no formal global process for conducting digital forensics investigations; however, we introduced the general phases of any digital investigation process and what tasks are required as a part of each phase.
There have been many attempts made to standardize digital forensics standards and process through published guides by some recognized official bodies; the most important ones are those published in the United States and the United Kingdom.
Digital forensics experts are needed in virtually all industries and sectors, from nonprofit organizations to government entities to private corporations and enterprises. As more companies are shifting most of their work digitally, we can expect to see a tremendous growth in demand for digital forensics experts in coming years.
In the next chapter, we will cover the main technical concepts that any digital forensics-or cybersecurity-expert needs to understand before beginning his/her investigation.
