Analysts can also check the loaded DLL files associated with a process. This allows the analyst to determine if a suspect process has accessed these files when it was executed. For example, if an analyst would like to examine the DLL files associated with one of the suspect processes, PID 868, the following command is run:
forensics@ubuntu:~/Documents$ volatility -f stuxnet.vmem --profile=WinXPSP2x86 -p 868 dlllist
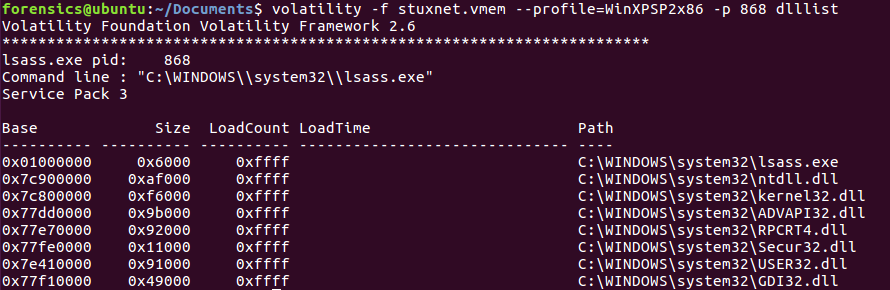
The output indicates that there are several DLL files. Later on in this chapter, these DLL files will be acquired for further examination.
