The diamond model of intrusion analysis is a methodology to describe the process for differentiating APT threats and their specific attributes. The diamond is comprised of four components: Adversary, Infrastructure, Capabilities, and Victim.
The model attempts to determine the interplay between each of these four groups.
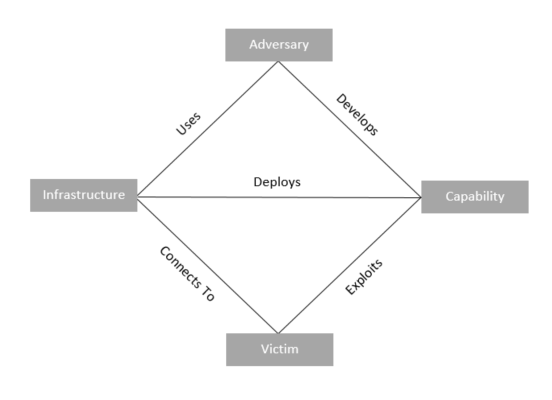
For example, take a simple malware attack. The Adversary is going to use a custom piece of malware. They develop the malware which feeds into their Capability. The Adversary then utilizes their capability to deploy the malware via a compromised web server or infrastructure. This connects to the Victim where the capability exploits a social engineering vulnerability.
This simple example highlights just a small sliver of how the diamond model can be utilized to categorize attacks. Therefore, it is recommended that a deeper exploration be undertaken by reviewing the diamond model paper, which can be downloaded at http://www.dtic.mil/dtic/tr/fulltext/u2/a586960.pdf. By integrating this model, an organization can have a better understanding of the threats they face and how those threats interact during an attack against their infrastructure. From here, they will be able to align their threat intelligence requirements to better fit their unique challenges.
