Dial-In Security
The need to support dial-in users might prove to be the security administrator's largest challenge. This is especially true if users are allowed to dial in directly to their workstations or servers, bypassing all other security methods.
Dial-in access can be through either the plain old telephone service (POTS) or through an ISDN connection. Because ISDN connections are expensive, there are generally fewer individuals who have an ISDN connection at their desk. However, the price of telephone connections is so low that it is reasonable for individuals to have dedicated connections at their desktop. The remainder of this section deals with connections using the POTS.
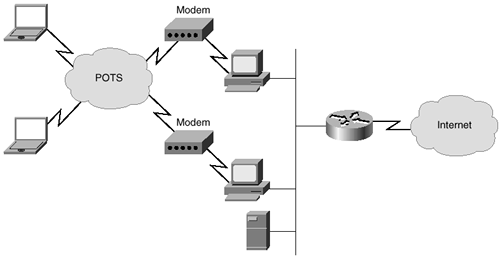
Within some organizations, there are groups and individuals that insist that the normal security precautions need to be bypassed because of special circumstances. Sometimes those insisting on bypassing the security precautions are developers, sometimes they are managers, and sometimes they are network engineers. In most cases, the arguments as to why the security must be bypassed seem logical on the surface. For example, the argument can be made that direct access of the hardware is required for debugging purposes. Another common argument is that a connection must be made for testing purposes without interference or delays imposed by security methods. This scenario can be differentiated from one where there is a central device on the network for dial-in access (such as a Cisco access server or a single Windows NT RAS server) by the fact that there are multiple entries into the network. A company with multiple dial-in connections is shown in Figure 10-1.
Figure 10-1. Multiple Dial-In Entry Point
Once the network starts to become open to remote access without proper authorization, it can be very difficult for the administrator to regain control. Although it is much easier to maintain control than to regain control, it is still possible to move from an unsecured dial-in network to a fully secured dial-in network.
Assume for a moment that you are the newly hired administrator for a 600-host Windows NT network. You discover that there are approximately 50 users who connect a modem to their desktop PC and routinely call into the network through this connection for access to e-mail, network programs, and shared files. What, exactly, is the problem with this scenario? Several things can be improved in this scenario:
If the phone lines can be eliminated through consolidation, recurring expenses in the form of unnecessary phone lines can be eliminated. Some phone systems require that modems use a dedicated line. In this case, a separate line must be purchased for use on each modem. Because all lines are not in use at exactly the same time, the company needs to purchase more lines than are ever used at one time. Building a modem pool allows the administrator to eliminate some of these lines. The authors of this book were faced with exactly this scenario and were able to remove a total of 24 dedicated lines by building a modem pool, saving the company a good deal of money over the first year.
Allowing users to access their computers directly through an uncontrolled dial-up connection decentralizes security. It can become a nearly impossible task to ensure any semblance of security when individual users are setting up their own connections into the network. The user might set up the connection not to require a password or might make the password so obvious that it is useless. A single administrator would have an extremely difficult task of checking every single connection on a regular basis for configuration issues such as encryption and dial-back services.
In this example, the company relies solely on the built-in security methods within the operating system of the desktop. Many operating systems were not built with security as a primary concern. Even those operating systems that claim to have strong security policies might be vulnerable, simply because they are well known. There are also usually no built-in methods within the operating system that allows the administrator to be notified if repeated attempts to break into the network occur.
Unless the administrator has control over dial-in connections, the administrator is unable to limit the areas of the network that a dial-in user can access. Some companies might wish, for example, not to allow any confidential information to be accessed through a dial-in connection. With a large number of operating systems, a user dialing into a workstation has the same rights as that workstation. There might not be provisions made to differentiate the authority levels between a dial-in account and a local user. This means that there is no way to enforce the company's wish that sensitive information be available only through the local network.
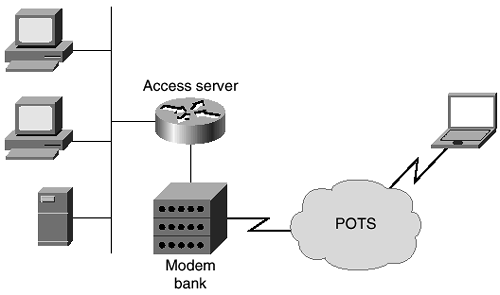
For these reasons, the administrator is strongly urged to move toward a centralized dial-in point where appropriate controls can be used. The fact that all users enter at a single point simplifies all administrative efforts, including security. A diagram of a network using a single point of access through an access server and modem bank is shown in Figure 10-2.
Figure 10-2. Single Dial-In Entry Point