Common Internet Security Threats
Throughout the short history of the Internet, attacks to the public servers of large corporations have been prevalent. These are usually for financial gain to the perpetrator, financial loss to the victim, or sense of personal achievement and increase in status to the perpetrator among the hacking community. These attacks can be categorized based on the type of attack. Most Internet attacks fall into one of these categories. However, just as the Internet evolves, new categories and new attacks evolve all of the time.
These attacks fall into two general categories. They are trying either to gain unauthorized access into the network or to deny service to the network. These two categories can intermingle such that a network intrusion could lead to the denial of service. Throughout this chapter, the following separate attacks are covered:
Network intrusion
Denial of service
Network Intrusion
Network intrusion is when unauthorized access is gained to a computer system or computer network. This can be achieved in many ways. The following are the two main types of network intrusion with which this book is concerned:
Unauthorized access
Eavesdropping
Unauthorized Access
Unauthorized access generally refers to the gaining of access to a network by using username and password pairs. These passwords can be obtained by the following methods:
Social engineering— Social engineering is where the attacker gets someone of authority to release information, such as username and password pairs. A common social engineering attack could be someone telephoning a network user, pretending to be from the company's network help desk, and asking for the user's username and password. These attacks are very hard to overcome; the only real way is through staff training and fostering a secure office culture.
Dictionary attack— A dictionary attack is a brute-force attack against a password system. The attacker runs a piece of dictionary software to try numerous passwords against the system. The attack gets its name from the fact that the method usually employs a dictionary file, which contains thousands of common and not-so-common words. Each of these words in turn is attempted in the authentication attempt.
Security policy should stipulate the maximum number of wrong passwords that can be entered before the account is locked. This feature is implemented in most mainstream network operating systems today. One way to overcome a majority of these attacks is to make all passwords a random set of alphanumeric characters with mixed case. For example, the password “dfgWJdHu75G4fo” would be a lot harder for a dictionary attack to break than the password “miamidolphins.”
Exploitation of services— In addition to password attacks, which encompass the previous two methods, there is the exploitation of the network services. For example, a bug with the UNIX sendmail service allowed a user to send a series of commands to the service that would gain the user administrative access to the host machine.
Be sure to keep abreast of all the latest security vulnerabilities and ensure that all network services have the latest security patch.
Eavesdropping
Eavesdropping is where an attacker uses a network analyzer or sniffer to listen and decode the frames on the network medium. This type of attack is physically hard to achieve, because it has to be done either at the same location as the network or at the office of a service provider to that network. The traffic that the attacker can capture is limited by the location of the attacker. For example, if the sniff or trace is run on the corporate LAN, an attacker probably will not see WAN routing traffic because that traffic will not be local or contained to the LAN. A common use of sniffing is to obtain the username and password pairs of either users or network services.
Sniffing can also lead to session replay attacks and session hijacking:
Session replay attacks— With most network analyzers available today, you can capture the data into a buffer. This buffer can then be replayed on the network. An attacker can capture a user logging into a system and running commands. By replaying the captured session, the attacker can recreate the initial user's actions and use it for personal benefit. The common method is for the attacker to change the source IP address of the capture so that the session initiates with another host. Even with encryption, session replays are very hard to spot and prevent.
Session hijacking— Session hijacking is where the attacker inserts falsified IP data packets after the initial session has been established. This can alter the flow of the session and establish communication with a different network host than the one where the session was originally established.
Denial of Service (DoS)
The term denial of service has been heard quite a lot in the Internet community recently. This is partly because of frequent DoS attacks that have been carried out against leading e-commerce vendors, such as eBay.com and Amazon.com.
A DoS attack is the saturation of network resources targeted against a single host or range of hosts with the intent to stop that host from furnishing further network requests. This has the same effect as a server that is under too much strain and cannot deal with the concentration of requests for its services.
The problem with DoS attacks is that most of the attacks appear to be genuine requests for service. They just come in rather large numbers—large enough to make the server fall over.
Numerous DoS attacks exist, and new ones are found almost on a weekly basis. Web sites run by white hat hackers (hackers benevolently researching security issues) are being misused by black hat hackers (malevolent hackers) and script kiddies. This information is being misused in the form of DoS attacks against Internet hosts.
Attackers can run a DoS attack from anywhere. They target a public service, so they protect and hide their identity, and they can run the attack by a dial-up connection anywhere in the world.
Many DoS attacks are very simple to run, which has led to the increase in what are called script kiddies. A script kiddie is someone with limited knowledge who runs a prebuilt DoS script to attack an Internet host. The authors have even seen UNIX GUI-based applications that mimic numerous DoS attacks and make it extremely easy to use this technology against an unsuspecting host.
This section looks at some common and more famous DoS attacks. There are literally hundreds of these in existence now.
TCP SYN flooding attack— The TCP SYN flood attack exploits the three-way handshake connection mechanism of TCP/IP. The attacker initiates a TCP session with the server by sending a TCP SYN packet to the server. The server responds to this initial packet with a TCP SYN/ACK response. The attacker's machine should then respond to this SYN/ACK by sending its own SYN/ACK back to the server. At this point, the session would be established. What happens in a TCP SYN attack is that the attacker's machine never responds to the TCP SYN/ACK sent by the server. This causes the server to wait for response and for the session to start. This is called a half-open session. Each of these half-open sessions uses resources on the server. The attacker floods the server with thousands of these session initiation packets, causing the server eventually to run out of resources, thus denying service to any other inbound connections.
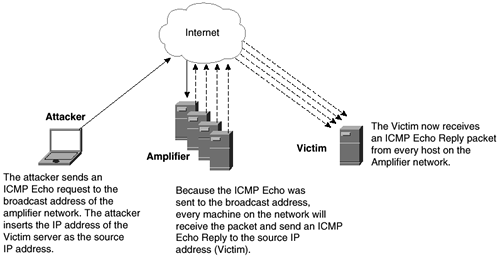
Smurf attack— A smurf attack is when an attacker sends an ICMP Echo Request to a network address rather than a specific host. The important point is that the attacker enters the IP address of the targeted server as the ICMP Echo Request source address.
This has the effect of every host on a network responding and sending an ICMP Echo Reply to the attacker-supplied source address of the ICMP Echo packet. This source address is the address of the server that the attacker wants to attack.
In this case, the attacker uses somebody else's resources and network to attack the victim. This attack works by simply consuming bandwidth to the victim. Once this bandwidth is consumed, all access to the server from other public hosts slowly grinds to a halt. The third party who is amplifying the attack is also affected because it consumes outbound bandwidth from the network.
Figure 11-1 depicts a smurf attack.
Figure 11-1. Smurf Attack
Ping of death— The ping of death is a famous DoS attack that uses the ping ICMP Echo Request and Echo Reply to crash a remote system. It is classified as an elegant one-packet kill.
This attack works by sending a large ICMP Echo Request packet that gets fragmented before sending. The receiving host, which is also the victim, reconstructs the fragmented packet. Because the packet size is above the maximum allowed packet size, it can cause system crashes, reboots, kernel dumps, and buffer overflows, thus rendering the system unusable.
This attack, although still in existence, is well protected against with all recent operating systems.
Teardrop— The teardrop attack is a classic DoS attack that normally causes memory problems on the server that is being attacked. Teardrop attacks use fragmentation and malformed packets to cause the victim host to miscalculate and perform illegal memory functions. These illegal memory functions can interact with other applications running on the server and result in crashing the server.
Because this is a fragmentation attack, it can bypass some traditional intrusion detection systems (IDSs).
Land— The land attack is where the attacker sends a spoofed packet to a server that has the same source IP address and port as the destination IP address and port. For example, if the server had an IP address of 192.168.0.1, both the source and destination IP addresses of the packet would be 192.168.0.1. The port is identified as being open by a network scan that the attacker runs before sending the packet. The result is that the server, if susceptible, will crash. This attack is also known as the LAND.c attack. The .c refers to the C script in which it is presented.
The preceding list represents only a small percentage of the network intrusions and DoS attacks that exist. White hat hackers who aim to educate security administrators about the new threats and vulnerabilities that emerge almost daily provide helpful web sites; among these sites are www.security-focus.com and www.rootshell.com. These sites should be examined frequently to keep network security up-to-date and as secure as possible.
