Basic Management Security
Before delving into specifics regarding how routers should be configured to help avoid attacks, the differences between internal and external devices must be explored. For purposes of this chapter, the authors use the word external as in external interface, meaning that the interface is directly connected to an untrusted entity. This can be the Internet, another company, or even a subsidiary of your own company. An internal interface is one that connects directly to a fully trusted network.
Many factors determine whether an entity is trusted. If there is doubt that the connected entity can be trusted, the authors recommend that the administrator not trust that entity. The initial reaction of many administrators will be to question why a wholly owned subsidiary should not be trusted. Consider the following example: Company A has a connection to the Internet. The administrator has done everything reasonable to ensure that the network is safe. Company B is a wholly owned subsidiary that has its own connection to the Internet. The administrators of these companies have sent a few e-mails to each other and talked on the phone a number of times to establish connection procedures and procedures for maintaining connections. However, Company A's administrator has no authority, either explicit or implied, over Company B's administrator. Upper management has decided that all subsidiaries will be entirely responsible for their own networks. If Company B's administrator is not careful, Company A may become a target of attack through Company B's network. Figure 2-1 illustrates this scenario.
Figure 2-1. Company A Is Exposed Through Company B
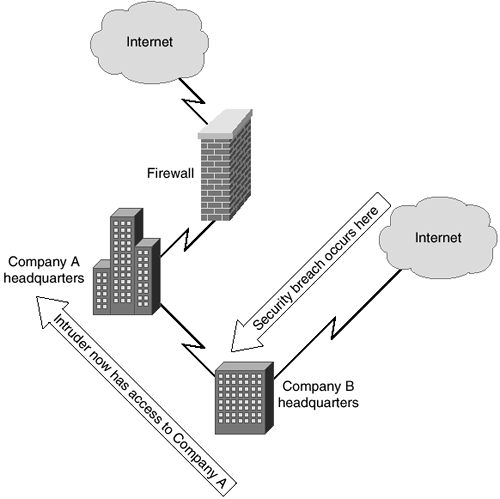
This situation becomes more complicated when a company acquires several hundred subsidiaries. In a multinational company, one cannot possibly assume that each of the subsidiaries will always observe good security practices. Therefore, administrators should assume that any subsidiary of which they do not directly have control is easily breached. Likewise, the subsidiaries should assume that the main office is easily breached. Unless the administrator at the subsidiary personally knows all of the security steps taken within the main office, security should be implemented. Additionally, even if all offices provide adequate security, the only drawback to increased security will be a slight increase in latency and additional CPU requirements on the interface routers—both of which are very reasonable trade-offs for increased security.
In any case, a connection to another company that is not owned by your own company should be treated as a possible threat and considered an external interface. The reasoning behind this is the same as that for a subsidiary. Unless the administrator is able to constantly verify the security on any connection, it must be assumed to be a threat.
Now that the basic differences between internal and external connections have been explored, the chapter will move on to cover some specific settings on routers to discourage the most common forms of attack.
