Access Lists
Access lists are created to deny certain packets the ability to traverse a router interface. By default, a router will allow all packets to travel through an interface. The router may not know where to forward a particular packet but will still allow that packet to cross the interface. An access list is a list of packets that is consulted before allowing or disallowing a packet to travel forward toward its ultimate destination.
Although this text assumes that you have at least an understanding of access lists, this section contains a brief review of the basic forms of IP access lists before moving onto the more complex reflexive and context-based access lists. The examples within this chapter will focus on IP access lists. A wide variety of protocols are available, all of which might have access lists applied to restrict access. A listing of the available access list numbers and their associated protocols can be found in Table 2-1.
| List Range | Protocol | Notes |
|---|---|---|
| 1–99 | IP | Standard IP access list |
| 1–100 | Vines | Standard Vines access list |
| 100–199 | IP | Extended IP access list |
| 101–200 | Vines | Extended Vines access list |
| 200–299 | Type Code | Ethernet Type Code, transparent bridging Type Code, or source–route bridging Type Code access list |
| 201–300 | Vines | Simple Vines access list |
| 300–399 | DECnet | DECnet and Extended DECnet access list |
| 400–499 | XNS | XNS access list |
| 500–599 | XNS | Extended XNS access list |
| 600–699 | AppleTalk | AppleTalk access list |
| 700–799 | Vendor Code | Source-route bridging Vendor Code access list |
| 800–899 | IPX | Standard IPX access list |
| 900–999 | IPX | Extended IPX access list |
| 1000–1099 | IPX | IPX Service Access Protocol[1] access list |
[1] SAP=Service Access Protocol
Any interface on a router may have up to two access lists assigned: one will control inbound traffic, and the other will control outbound traffic. All access lists, regardless of protocol or interface, operate based on six principles:
Access lists usually deny that which is not specifically permitted, because traffic is generally allowed by default.
Access lists control traffic in one direction (inbound or outbound) on an interface.
Every packet traversing the interface is examined against an applied access list in the direction of that packet.
Packets are compared to the access list starting at the top of the access list and continuing until a match is found. The implied deny statement at the end of an access list is considered a match.
Outbound packets are routed to the appropriate interface before the access list is applied.
Inbound packets are compared to the access list and, if permitted, are routed to the appropriate interface.
Any interface may have a maximum of one access list applied to the inbound traffic and a maximum of one access list applied to the outbound traffic.
Access lists are made in one of several forms; the most common are standard and extended. Because standard access lists are simpler by nature, they will be examined first.
Standard Access Lists
Standard access lists deny or permit packets traversing a router interface based solely on the source address of the packet. Numbered 1 through 99 for IP, standard access lists must be defined before they can be used. Figure 2-2 shows that a router, by default, allows all traffic through to the intended destination.
Figure 2-2. By Default, a Router Allows All Traffic Through

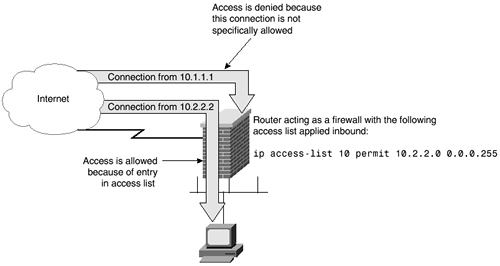
Applying an access list, however, will change this behavior. When an access list is applied, a router acts as a firewall. The function of a firewall is to restrict traffic traveling through itself. As shown in Figure 2-3, adding an access list changes the behavior of the router. When an access list is applied, only traffic that has specifically been allowed will be able to travel through the router. In the example shown in Figure 2-3, traffic from the 10.2.2.0/24 network is allowed to traverse the router. Because no other traffic has been allowed, traffic originating from the host 10.1.1.1 will not be allowed through.
Figure 2-3. Access List Limits Which Packets Travel Through a Router
The syntax for creating a standard IP access list is as follows:
access-list access-list-number {deny | permit} source [source-wildcard]
With this syntax, access-list-number is any number from 1 through 99 that defines the access list number. The parameter permit or deny specifies whether to allow or disallow the packets. The parameter source is the IP address of the host sending the packets to be denied, and source-wildcard is the wildcard mask for the host or hosts sending the packets.
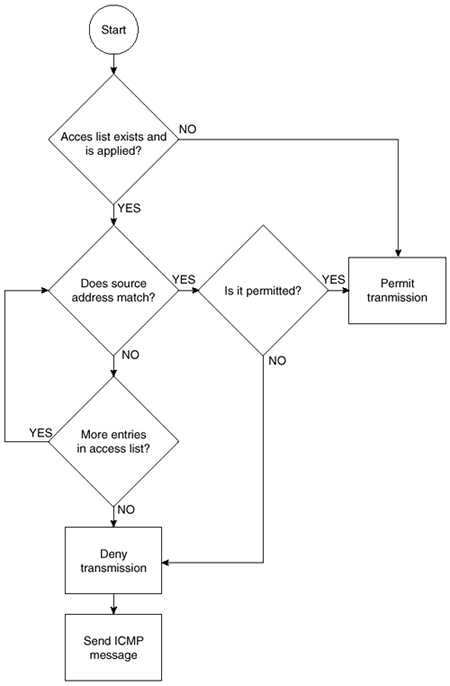
The logical flow for a standard access list is shown in Figure 2-4. Notice that if the source address is either not found or found but not permitted, the packet is denied.
Figure 2-4. Logical Flow of Standard Access List
An example of a standard access list follows. Although this access list will reveal some inconsistencies, it is useful for the purposes of discussion. Each line of this access list will be discussed. For the purposes of this discussion, each line is labeled with a line number:
1)access-list 3 permit 172.30.1.0 0.0.0.255 2)access-list 3 permit 10.1.1.0 0.0.15.255 3)access-list 3 deny 10.1.1.2 0.0.0.0 4)access-list 3 permit 192.168.10.0 0.0.0.7 5)access-list 3 deny 172.31.1.0 0.0.0.255 6)access-list 3 deny any
Line 1 accomplishes a number of objectives. The keyword access-list is used to define that this line is used to specify an access list. The number 3 assigns the following permit or deny statement to access list number 3. The word permit tells the router to allow the following combination of IP address and mask through the interface. Using the keyword deny would tell the router to deny the packets.
Notice that all of the lines have an IP network address and what looks like a reversed subnet mask. The reversed subnet mask is called a wildcard mask and works very much like a subnet mask, only in reverse. In line 1, 172.30.1.0 0.0.0.255 describes the source address of packets to permit through the interface. This means that all packets with the source address of 172.30.1.0 through 172.30.1.255 will be permitted through an interface with this access list applied.
Line 2 looks similar to line 1 and allows all packets between 10.1.0.0 and 10.1.15.255 through an interface to which this access list is applied. At this point, you might be questioning exactly how that conclusion was reached. This is explained in the following sidebar, “Wildcard Masks.”
Line 3 is incorrect. Because an access list is read from the top to the bottom, any packet meeting this deny would have already been permitted by line 2. To correct this problem, line 3 should have been entered before line 2.
Line 4 is simply another permit statement that allows packets with a source IP address from 192.168.10.0 through 192.168.10.7 to traverse the interface. The following shows a recalculation just to be sure this is correct:
255.255.255.255 = 11111111.11111111.11111111.11111111
0.0.0.7 = 00000000.00000000.00000000.00000111
255.255.255.255 - 0.0.0.7 = 255.255.255.248
255.255.255.248 = 11111111.11111111.11111111.11111000
The subnet mask of 255.255.255.248 applied to the IP address of 192.168.10.0 provides for a range of 192.168.10.0 through 192.168.10.7.
Line 5 will deny packets with the source address of 172.31.1.0 through 172.31.1.255.
Finally, line 6 includes a technically unnecessary deny statement that will deny all sources. This is unnecessary because it is implied on an access list. However, the author recommends that it is specifically stated for clarity. Since consistency promotes understanding, the author usually adds a specific deny any to every access list. This is also an important point when working with reflexive access lists. Additionally, when using extended access lists, it is possible to log matches. Logging of access lists will be explored in the later section, “Extended Access Lists.”
Applying Access Lists
Once an access list is created, it must be applied to an interface. To apply an access list to an interface, use the ip access-group or ip access-class command. The ip access-class command is used on virtual terminal interfaces, while the ip access-group command is used on all other interfaces. The access list is applied to either the inbound or outbound packets of the interface. The keywords in and out determine whether the access list is to be applied on the interface to deny inbound or outbound packets. The following is the command for applying access list number 3 to an interface to deny inbound packets. Note that you must first be in configuration mode and within the interface configuration to apply an access list.
ip access-group 3 in
The access list could alternatively be applied to the interface to deny outbound packets with the following:
ip access-group 3 out
To apply an inbound access list to a virtual terminal, the following command is used. The only difference in applying an access list between a virtual terminal and any other terminal is that the virtual terminal uses access-class instead of access-group. Again, the user must first be in configuration mode on that particular interface before applying an access list.
ip access-class 3 in
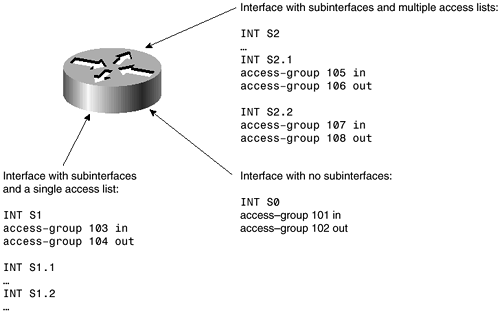
Any interface can have a single access list inbound and another single access list outbound. Only one access list should be applied in any given direction. In other words, one and only one access list should be applied inbound on an interface, and one and only one access list should be applied outbound on an interface. If an interface is using subinterfaces, such as on a serial interface connecting in a point-to-point method to remote sites, each subinterface is considered a separate interface. Each subinterface can have separate access lists. In this case, however, the root interface cannot have a separate access list. Figure 2-5 shows acceptable settings for access lists on interfaces with and without subinterfaces.
Figure 2-5. Access Lists Applied to Interfaces
Extended Access Lists
Standard access lists are limited because they make no distinctions between the ports being used. A standard access list will allow or deny packets based solely on the source IP address and are able to log only those packets that have not passed through the access list. Extended access lists overcome these limitations and form the basis for context-based and reflexive access lists, which are discussed in Chapter 5, “Cisco IOS Firewall.”
As with a standard access list, that which is not specifically permitted is denied. Because extended access lists can look at the source address, the destination address, and ports, any one item might cause a packet to be refused traversing the router. Extreme care should be taken when working on extended access lists to ensure that exactly those packets that should be traversing the router, and only those, do, in fact, traverse the router.
The following example is an extended access list with one of the simple forms available. In the example, a number of differing services are allowed to travel through the interface. A number of protocols are also prevented. Study the following list before moving on to the detailed discussion:
1) ip access-list 101 permit tcp any host 10.1.1.2 established log 2) ip access-list 101 permit tcp any host 172.30.1.3 eq www log 3) ip access-list 101 deny tcp any host 172.30.1.4 eq ftp log 4) ip access-list 101 permit tcp any host 172.30.1.4 log 5) ip access-list 101 deny any any
In the preceding example, line 1 allows access through the TCP protocol to host 10.1.1.2, if a connection has already been established from 10.1.1.2 to that remote host. This line will not permit any packets to traverse the interface unless the session was initiated from the inside of the corporate network.
Line 2 allows any host to connect to 172.30.1.3 for WWW services (HTTP). All other types of connection to this host will be denied because of the implied (and in this case specified) deny any any at the end of the access list.
Line 3 denies access to host 172.30.1.4 if the remote host is trying to connect using FTP services. Line 4 allows all other types of connections to 172.30.1.4.
Notice that each of these lines has the word log added at the end of the line. This causes the router to log all attempts at connection. A standard access list using the log option will only log those packets that have been denied.
Named Access Lists
Named access lists, first introduced in IOS Version 11.0, allow the administrator to use a character string instead of an access list number. One benefit is that the limitations of 99 standard access lists (1–99) and 100 extended access lists (100–199) no longer apply. The administrator can also name an access list something meaningful. For example, an access list named “from-internet” could be created to limit access into the corporate network from the Internet. Naming access lists in a meaningful way tends to make troubleshooting easier.
Another advantage to named access lists is that entries can be removed. However, new entries are still added to the bottom of the access list, which is usually not what is intended.
Reflexive access lists, discussed in Chapter 5, require a named access list, and access lists dealing with packet filters and route filters cannot use named access lists. A standard and an extended access list cannot both have the same name.
