Dynamic Access Lists
Dynamic access lists permit dynamic entries to be made into standard or extended access lists by users after authentication. This authentication comes through the use of a Telnet session to the router initiated by the user. Once the user successfully initiates a Telnet session to the router, the Telnet session is ended by the router and a dynamic entry is added to the access list. The user can then use the newly created opening through the router. Using dynamic access lists requires that usernames and passwords are entered into the router, and that the access list has a statement reflecting the username that is mapped to a permission statement. There are four steps required to use a dynamic access list:
-
The extended access list must be created.
-
The access list must be assigned to an interface.
-
The user must be authenticated through TACACS+, RADIUS, or through a username and password on the router.
-
The user must be able to Telnet to the virtual terminal.
The following is an example of a dynamic access list. Note that the use of an exclamation mark (!) at the beginning of a line indicates that the line is a comment.
access-list 109 permit telnet any host 172.31.10.2 eq telnet access-list 109 dynamic testdynamic timeout 10 permit ip any any deny any any !Set up the access list with a dynamic entry called "testdynamic." !This is the same name as is used in the Telnet session. !The timeout is set to 10 minutes. !The dynamic list entry permits ip traffic from and to any host. !As with any extended access list, you could allow only certain protocols or !ports to be available through this access list entry. interface serial 1 ip address 172.30.1.1 255.255.255.0 ip access-group 109 in !Assigns the access list number 109 to the interface. Username testdynamic password iwanttotelnet !This sets up the user with a password. line vty 0 4 login local !Use the local login. auto-command access-enable host timeout 5 !This is the line that tells user to create the dynamic entry. password mypassword rotary 1 !You need a way for the administrator to access the router. !Using "rotary 1" says that admin Telnets should occur on port 3001. !"rotary 2" would mean port 3002. And so on.
Three show access-list commands follow. The first one is from before the user Telnets to the router. The second one is from during the timeout period that the new opening exists. The last one is from after the opening has closed.
Before the user Telnets to the router:
routera:#show access-list
Extended IP access-list 109
permit telnet any host 172.31.10.2 eq telnet
dynamic testdynamic timeout 10 permit ip any any
During the timeout period:
routera#show access-list
Extended access-list 109
permit telnet any host 172.31.10.2 eq telnet
dynamic testdynamic timeout 10 permit ip any any
permit ip host 192.168.1.2 any idle-time 5 min.
After the opening has closed:
routera:#show access-list
Extended IP access-list 109
permit telnet any host 172.31.10.2 eq telnet
dynamic testdynamic timeout 10 permit ip any any
In the preceding examples, the user at host 192.168.1.2 created the dynamic permit statement in the access list by Telnetting to the router. In response, the dynamic access list opened all traffic to that host from the outside. This opening will remain for as long as data is traveling to and from the local host. When activity ceases for the amount of time specified within the dynamic statement, 5 minutes in this example, packets destined for 192.168.1.2 will again be denied.
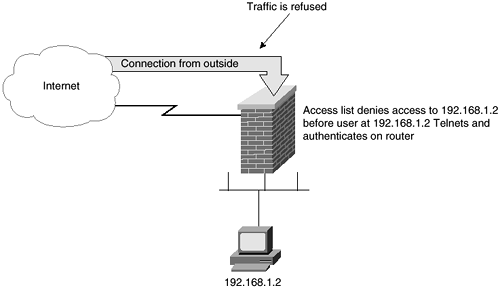
Figure 5-1 shows how under normal circumstances access from the outside to the host at 192.168.1.2 is prevented.
Figure 5-1. Before User Authenticates with Router
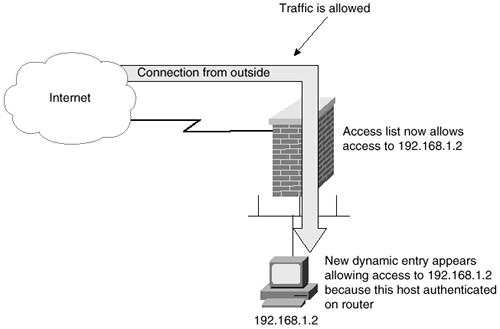
Once the user at host 192.168.1.2 is authenticated by the router, a new entry opens in the router, allowing access to host 192.168.1.2. This is illustrated in Figure 5-2.
Figure 5-2. After User Authenticates with Router
This is not an ideal situation because you do not necessarily want all traffic to be able to enter; you only want the traffic that is directly related to the type of connection the user wishes to establish. Although you could limit the type of traffic available through this opening by adjusting the dynamic statement, this presupposes that you know exactly what type of traffic a user will want. CBAC was designed for this purpose and is covered later in this chapter, in the section “How Context-Based Access Control (CBAC) Works.”
