Cisco IDS Configuration
This section looks at the configuration tasks required to configure Cisco intrusion detection on the Cisco router and Cisco PIX Firewall. It does not cover the configuration of the Cisco Secure IDS (NetRanger) Sensor or Director, as these are beyond the scope of this book.
This section concentrates on intrusion detection from an Internet—and specifically, a hosted-solution—point of view. It starts by looking at the Cisco IOS Firewall IDS configuration that is located on a corporate router that provides Internet access to the organization. It then covers the Cisco Secure PIX Firewall IDS that is deployed to protect a corporate web site hosted at an ISP.
Cisco IOS Firewall IDS Configuration
Routers connect networks. The Internet connection point of nearly all companies is through some routing device. In this section, you will look at the configuration of the Cisco IOS Firewall IDS for a router that is acting as the Internet connection point for a large company. This company has other WAN links to other sites. All Internet-bound traffic is routed through the central site. The Internet connection is provided for Internet browsing and e-mail only. There are no Internet servers located at any corporate site. The router has been configured with Context-based Access Control (CBAC) to allow back through the firewall only what was originated from inside on the corporate network. Network Address Translation (NAT) has been used in an overload fashion. This is also known as Port Address Translation (PAT). Theoretically, from the outside, nothing on the inside should be visible.
Because all Internet traffic comes through this connection onto the corporate network, the company has decided to configure intrusion detection on this router to provide a further layer of security against any external threats that exist. Figure 6-10 shows this simple network.
Figure 6-10. Corporate Internet Connection
To configure intrusion detection on the Cisco IOS Firewall, you have to ensure that you are using the correct IOS level. You must be using IOS 12.0(5)T or later with the Cisco IOS Firewall included.
You are going to configure intrusion detection to use syslog logging and to protect the outside interface of the router.
The following configuration lines are all entered in global configuration mode:
ip audit notify log ip audit name ids info action alarm ip audit name ids attack action alarm drop reset
The first line configures the IDS to use syslog logging. With the Cisco IOS Firewall IDS, you have the option of using syslog or the Cisco Secure Intrusion Detection Director. The second and third lines specify the IDS profile called ids. This profile is set to alarm for informational messages and alarm, drop, and reset sessions for attack messages.
Once this IDS profile has been created, you have to apply it to an interface. Enter the following configuration line from the interface configuration mode for the interface to which you wish to apply the policy:
ip audit ids in
This command applies the IDS policy ids to the interface for inbound traffic. This is similar to the ip access-group command that applies access lists, either inbound or outbound, to interfaces.
A few show commands can be used on the router to look at the configuration of IDS.
The show ip audit configuration Command
The show ip audit configuration command displays the global configuration settings for IDS on the router:
Router#show ip audit configuration
Event notification through syslog is enabled
Event notification through Net Director is disabled
Default action(s) for info signatures is alarm
Default action(s) for attack signatures is alarm
Default threshold of recipients for spam signature is 250
PostOffice:HostID:0 OrgID:0 Msg dropped:0
:Curr Event Buf Size:0 Configured:100
Post Office is not enabled - No connections are active
Audit Rule Configuration
Audit name ids
info actions alarm
attack actions alarm drop reset
You can see from the command output that this router is using syslog logging and not the NetRanger (Cisco Secure) Director.
The show ip audit interfaces Command
The show ip audit interfaces command displays interface specific information about IDS for every interface that IDS is configured on:
Router#show ip audit interfaces
Interface Configuration
Interface FastEthernet0/0
Inbound IDS audit rule is ids
info actions alarm
attack actions alarm drop reset
Outgoing IDS audit rule is not set
The output shows that the IDS profile ids is configured inbound on the Fast Ethernet 0/0 interface on the router.
The show ip audit name Command
This command displays the IDS information for the specific IDS profile:
Router#show ip audit name ids
Audit name ids
info actions alarm
attack actions alarm drop reset
The output shows the configuration of the IDS profile called ids that was previously configured for this example.
This concludes the simple configuration of the Cisco IOS Firewall IDS. As you can see, the configuration of IDS on the Cisco IOS Firewall is fairly straightforward. You have to ensure that the router is successfully logging to a syslog server. There are numerous syslog servers available for UNIX. For Windows platforms, there is an excellent syslog server available from www.ccstudy.com.
Cisco Secure PIX Firewall IDS Configuration
It is very common for hosted solutions that are located within an ISP to be behind a firewall. The firewall separates the hosted solution from the main ISP public network and provides NAT and stateful inspection of packets to protect the hosted network from various external attacks. This makes the firewall an ideal place to implement IDS.
IDS technologies operate by passively listening to traffic to ascertain whether the traffic is genuine or matches a known attack signature. This can be a problem in a shared network environment, because you do not want your IDS system to alert all of the time because of traffic destined for other networks. This can be true of a hosted solution from an ISP, because the public Ethernet connection that forms the outside interface of the PIX Firewall can be in the same broadcast domain as numerous other hosted networks. However, all ISPs should use switches to provide Ethernet connectivity. The switch ensures that only the required unicast traffic is delivered to each hosted network. The nature of the static NAT translations causes the outside switches to send unicast traffic for every host behind the firewall to the port where the outside interface of the firewall is physically connected. This removes potential false positives on the IDS from traffic that is directed toward other hosted networks. However, because the switch implements a single broadcast domain throughout the Layer 3 domain, you might still get false positives for broadcast-based attacks.
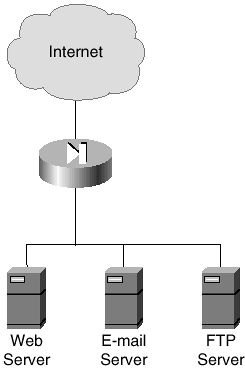
This section looks at a very simple hosted Internet solution and the commands that are required to install IDS on the firewall. Figure 6-11 displays this simple network.
Figure 6-11. Simple Hosted Network
The configuration lines in this section configure IDS on the outside interface of the router. Remember that the outside interface is the Internet-facing interface. There is little use in this scenario to enable IDS on both the inside and outside interfaces.
You can see from the network diagram in Figure 6-11 that this is a simple model, where the hosted firewall's outside interface is connected to the Internet, and the inside interface provides access to the protected network. In this simple network, there is a Web server, an e-mail server, and an FTP server.
To enable IDS on the PIX Firewall, the software on the PIX must be release 5.2 or later.
IDS configuration on the PIX is carried out with one command that has numerous variables associated with it. This command is ip audit. The important point to remember is that the alarm action with both the info and attack signatures uses the currently configured syslog server. This means that syslog has to be configured and working on an inside interface. Syslog is enabled with the logging commands.
These commands are all entered in global configuration mode:
ip audit info action alarm ip audit attack action alarm ip audit name idsattack attack action alarm drop reset ip audit name idsinfo info action alarm ip audit interface outside idsinfo ip audit interface outside idsattack
The first two lines are configured by default and apply to all interfaces. These alarm on info or attack signatures.
The third and fourth lines of the configuration specify an IDS policy with the name of idsattack and idsinfo. The fifth and sixth lines apply these named IDS policies to the outside interface.
A few show commands can be used on the PIX to look at the configuration of IDS.
The show ip audit info Command
The show ip audit info command displays the global info IDS policy on the firewall:
pixfirewall# show ip audit info
ip audit info action alarm
You can see from the output that the global info IDS policy is to alarm.
The show ip audit attack Command
The show ip audit attack command displays the global attack IDS policy on the firewall:
pixfirewall# show ip audit attack
ip audit attack action alarm
You can see from the output that the global attack IDS policy is to alarm.
The show ip audit interface Command
The show ip audit interface command displays the specific IDS policy that has been applied to an interface. From this example, the following is observed:
pixfirewall# show ip audit interface outside
ip audit interface outside idsinfo
ip audit interface outside idsattack
This shows that the named IDS policies idsinfo and idsattack have been applied to the outside interface of the PIX.
The show ip audit name Command
The show ip audit name command displays the IDS policy that has been specified in a named policy. From this example, you can observe that the IDS policy idsinfo is set just to alarm:
pixfirewall# show ip audit name idsinfo
ip audit name idsinfo info action alarm
The following shows that attack signatures are alarmed, dropped, and reset:
pixfirewall# show ip audit name idsattack
ip audit name idsattack attack action alarm drop reset
IDS Monitoring
Once intrusion detection has been configured, you can monitor the syslog information to identify any attempted security issues. The following log data are extracts from an actual Internet-facing PIX Firewall. You can see that the IDS on the PIX has intercepted quite a few items of suspicious activity:
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.2
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.6
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.7
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.20
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.21
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.22
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.23
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.24
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.26
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.25
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.27
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.28
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.30
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.29
on interface outside
%PIX-4-400027: IDS:3041 TCP SYN+FIN flags from 24.15.59.98 to 194.73.134.100
on interface outside
The preceding messages indicate that the IP address 24.15.59.98 is attempting a reconnaissance sweep against the IP addresses on the 194.73.134.0 network. This is classified as an attack, and because of the policy that is in place, these sessions would be logged, dropped, and reset.
The following message could indicate that the IP address 137.39.5.35 is trying to overcome the packet-filtering security policy. This could indicate an attack:
%PIX-4-400011: IDS:2001 ICMP unreachable from 137.39.5.35 to 194.73.134.7
on interface outside
The following message indicates that a successful ICMP echo reply (ping) was sent from the IP address 64.225.249.26. This is an informational message:
%PIX-4-400010: IDS:2000 ICMP echo reply from 64.225.249.26 to 194.73.134.2
on interface outside
This concludes the simple configuration of the Cisco PIX IDS. As you can see, the configuration of IDS on the PIX is fairly straightforward. You have to ensure that the PIX is successfully logging to a syslog server. There are numerous syslog servers available for UNIX. For Windows platforms, there is an excellent syslog server available from www.ccstudy.com.
