Appendix C. Quick Guides to Security Technologies
The intent of the cheat sheets in this appendix is to provide the reader with quick supplemental information and quick reference of concepts that are covered in this book. Refer to Chapter 3, “Security Technology and Related Equipment,” for more detailed technical explanations and the Cisco website (http://www.cisco.com) for more comprehensive information.
This appendix contains cheat sheets for the following topics:
• Cheat Sheet 1: Routers
• Cheat Sheet 2: Hubs and Switches
• Cheat Sheet 3: Perimeter Routers and Firewalls
• Cheat Sheet 4: Intrusion-Detection Systems
• Cheat Sheet 5: Virtual Private Networks and Authentication
• Cheat Sheet 6: Comprehensive Security Topology
Cheat Sheet 1: Routers
Routers perform the following tasks:
• Segment logical networks at the IP layer
• Route IP traffic (IP packets) according to routing information kept in their router tables
• Build routing tables manually or, usually, automatically by using routing protocols that exchange routing information between neighboring routers
• Usually keep only optimal paths in their routing tables
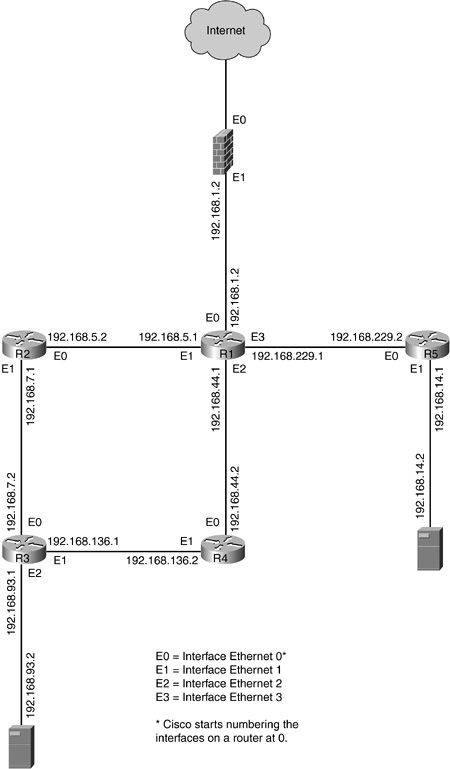
R1 Routing table
Network 192.168.1.0 ![]() directly connected
directly connected![]() out Ethernet 0
out Ethernet 0
Network 192.168.5.0 ![]() directly connected
directly connected![]() out Ethernet 1
out Ethernet 1
Network 192.168.7.0 ![]() via Router 2
via Router 2![]() out Ethernet 1
out Ethernet 1
Network 192.168.14.0 ![]() via Router 5
via Router 5![]() out Ethernet 3
out Ethernet 3
Network 192.168.44.0 ![]() directly connected
directly connected![]() out Ethernet 2
out Ethernet 2
Network 192.168.93.0 ![]() via Router 2
via Router 2![]() out Ethernet 1
out Ethernet 1
![]() via Router 4
via Router 4![]() out Ethernet 2
out Ethernet 2
Network 192.168.136.0 ![]() via Router 4
via Router 4![]() out Ethernet 2
out Ethernet 2
Network 192.168.229.0 ![]() directly connected
directly connected![]() out Ethernet 3
out Ethernet 3
Cheat Sheet 2: Hubs and Switches
For more information regarding hubs and other LAN devices, visit http://www.cisco.com.
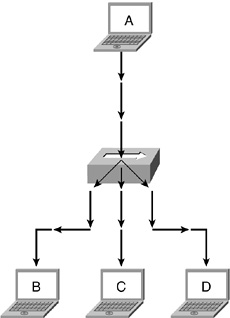
What Is a Hub?
• A hub is a physical layer device that connects multiple user stations, servers, and network equipment.
• Devices connect to the hub through dedicated cable, often referred to as network cable or patch cable (which usually connects to a network drop installed in a wall socket).
• Electrical interconnections are established inside the hub.
• Electrical signals emitted from one station are propagated to all stations connected in the same hub.
• Network bandwidth is shared among all devices connected to the hub.
What Is a Wireless Hub?
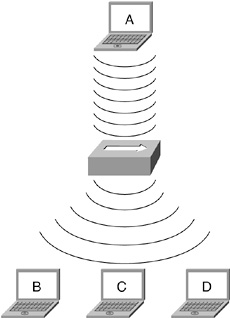
• A wireless hub is also known as a wireless access point.
• A wireless hub operates under the same principle as a wired hub by receiving a signal and propagating it out.
What Is a LAN Switch?
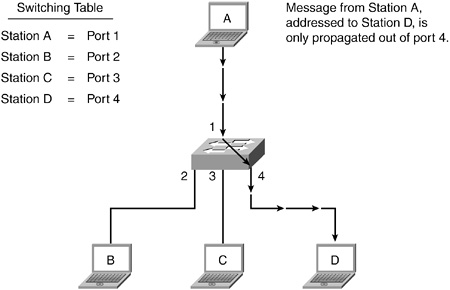
• A LAN switch segments communication between devices of the same physical network, contrary to a hub, which indiscriminately repeats signals to all members of the same physical network.
• For the most part, switches have replaced hubs in wiring closets.
• Network bandwidth is dedicated to each station connected directly to the switch.
• Modern switches are more versatile and accomplish more tasks than the physical segmentation work done by their predecessors.
For more information on LAN switches, visit http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/lanswtch.htm#xtocid2.
Cheat Sheet 3: Perimeter Routers and Firewalls
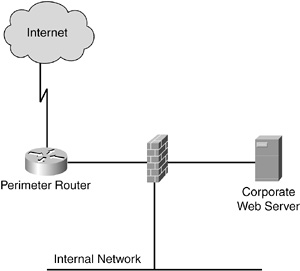
For more information regarding perimeter routers and firewalls, refer to Chapter 3.
What Is a Perimeter Router?
• The first line of defense
• Performs the following basic security checks:
– Validates source and destination IP addresses on incoming and outgoing network traffic
– By default, performs stateless packet filtering and therefore is easier to hack than a stateful firewall
Can a Router be a Firewall?
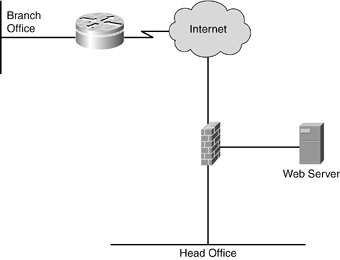
Some perimeter routers can be upgraded to perform as stateful firewalls. Those upgraded routers/firewalls can also terminate VPN tunnels and perform some IDS tasks. Routers with these extra capabilities are often used by branch offices.
What Is a Firewall?
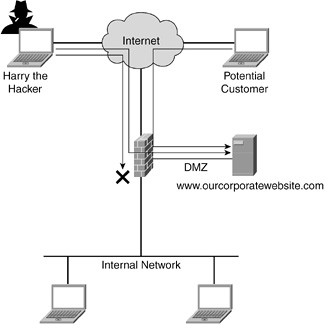
• A firewall is a network appliance dedicated to the meticulous filtering of all network traffic.
• Stateful firewalls meticulously record pertinent information of data streams transiting through it to permit or deny access.
• Default behavior dictates that traffic originating from the outside is denied access.
• Default behavior dictates that traffic originating from the inside is allowed out and that replies are permitted in.
• A firewall can be configured to modify its default behavior, for example, to let incoming outside traffic in, provided that the destination address is the corporate web server and only for the purpose of browsing the corporate web server. However, a hacker’s traffic trying to access the internal network is blocked by the firewall.
• A firewall is commonly configured to perform Network Address Translation (NAT), where inside addresses are never revealed to the outside network.
What Is Network Address Translation?
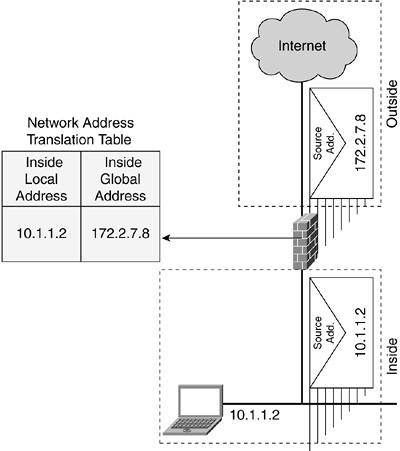
• NAT translates internal addresses (local addresses) to addresses used only when communicating on the Internet (global addresses).
• NAT is commonly configured on firewalls and perimeter routers.
• NAT provides additional security, because the true addresses of devices are not publicly known.
Cheat Sheet 4: Intrusion-Detection Systems
For more information regarding intrusion-detection systems (IDSs) and intrusion-prevention systems (IPSs), refer to Chapter 3.
IDSs
• IDSs analyze data streams in real time to detect attacks and viruses.
• A network-based IDS (NIDS) is located on the net-work and analyzes traffic for malicious activities.
• A host-based IDS (HIDS) is installed on a server or workstation and analyzes incoming data for malicious codes.
Actions Taken by an IDS
Upon discovering suspicious activities, an IDS can do the following:
• Logs an alarm
• Resets the IP (TCP) connection
• Blocks (shuns) further traffic from the suspect
Alarm Severity Levels
• Informational
• Medium
• Low
• High
Traffic Analysis
An IDS analyzes traffic according to the following items:
• Signature—Looks for a match of a data string according to an attack definition database (similar to standard virus-detection software)
• Pattern—Learns what is normal traffic and then analyzes future traffic according to the previously created baseline
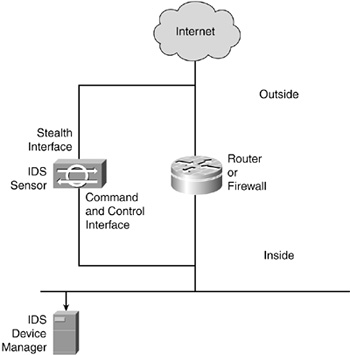
IDS Components
• IDS Device Manager—Configures sensors and is the central repository of alarms
• IDS sensor—Captures and analyzes traffic in real time
Sensor Interface Operating Modes
• Stealth—Captures data without having a logical participation on the network
• Command and control—Announces suspicious activities that were detected as a result of data captured by the stealth interface
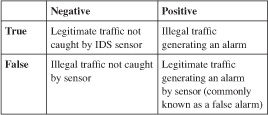
Alarms
Alarms, defined in the following table, are classified as follows:
• True-negative
• False-negative
• True-positive
• False-positive
Cheat Sheet 5: Virtual Private Networks and Authentication
For more information regarding Virtual Private Networks (VPNs) and authentication, refer to Chapter 3.
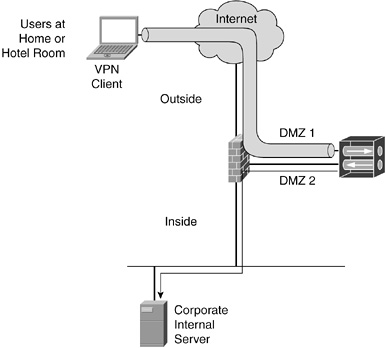
A VPN allows data to be sent securely over public networks, such as the Internet, through secure encrypted tunnels.
VPN tunnels from remote offices and telecommuters commonly terminate on VPN concentrators, which are dedicated appliances optimized for this task.
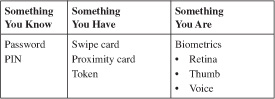
VPN and network security are better served when strong authentication is used.
Money withdrawn from a bank machine requires strong authentication, as follows:
• Something you have: bank card
• Something you know: PIN
IPSec
IPSec is currently the most readily available VPN protocol. It provides the following features:
• Authenticity through authentication
• Confidentiality through encryption
• Integrity through hashing (integrity checking)
Preferred VPN Topology
Ideally, encrypting traffic originating from a remote office or a telecommuter would be permitted access through a firewall, terminating at the VPN concentrator.
Strong authentication refers to a minimum two-factor process, where the two methods must be used jointly.
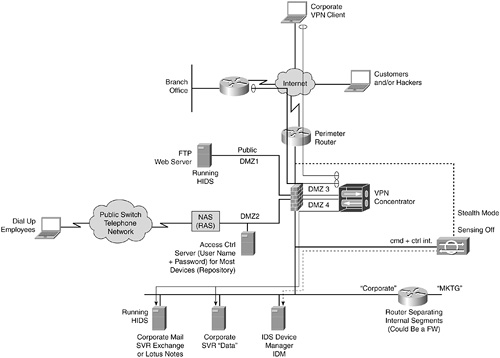
Cheat Sheet 6: Comprehensive Security Topology
For more information regarding the equipment listed in this figure, refer to Chapter 3.