Chapter 2. Crucial Need for Security: Vulnerabilities and Attacks
A growing desire exists to learn more about security threats and the possible impact they can have on network and computing environments. Awareness levels in organizations both large and small are rising rapidly, as attacks are becoming more virulent and the collateral damage they cause more costly. Learning about those who threaten, and understanding what the threats can entail, is a major step toward counteracting the menace. Gauging investments in security products is not like any other; it ignites a range of discussion that will continue unabated until concrete numbers can be validated. The menace must be seen, understood, tamed, and nullified. This chapter is focused on seeing and understanding those menaces, and the following chapter concentrates on taming and nullifying them. Return on prevention (ROP) is about acknowledging the grey area that exists by understanding the threats, assessing individual tolerance to those threats, and moving forward accordingly. In keeping with the discussion, this chapter focuses on threats and attacks.
This chapter covers the following topics:
• Recognizing vulnerabilities
• Categories of attacks
• Common attacks
• Wireless intrusions
• Summary of attacks
• Social engineering
• Cisco SAFE axioms
Recognizing Vulnerabilities
It is inevitable that threats will exist. The more one is exposed to any type of interaction, be it computer networks or any aspect of everyday life, the more vulnerable one is to risk. Organizations are becoming increasingly more dependent on the Internet for their daily operations. From just-in-time manufacturing to customer service and accounts receivables, the growing reliance on the Internet results in a heightened vulnerability that needs to be continually managed. Human nature suggests there will always be an element in society that hunts for a vulnerability to exploit. Threats are external to organizations, and these threats can appear as poisoned arrows, continually airborne, searching for weak armor, or network vulnerabilities, to pierce. The best defense is stronger armor, coupled with a keen awareness of potential cracks.
Most attack vulnerabilities fall into one of the following categories:
• Design issues
• Human issues
• Implementation issues
Design Vulnerabilities Issues
Design issues encompass all network equipment, including both hardware and software. This discussion centers on the following topics:
• Operating systems
• Applications
Operating Systems
Operating system weaknesses have been known to wreak havoc within a network. In a rush to market, operating systems (OSs) have been promoted and installed, only to reveal later that flaws within the software enabled hackers to penetrate systems with ease. A well-known flaw in an OS caused the OS to lack so much security that it allowed hackers to install malicious software and then access it remotely, with all the flexibility of a legitimate administrator.
Applications
Issues can exist in both hardware and software, but it is typically the latter that is responsible for a higher frequency of cracks within a system. While it does not occur as often with newer software, it was not uncommon for applications to be devoid of security mechanisms; a newly installed workstation on a network, for example, might not have required authentication for it to operate. Today, while most network-ready products arrive with built-in authentication, key steps need to be followed to ensure that proper verification procedures are enabled.
Protocol Weakness
A protocol is a set of rules that devices follow when communicating with one another. When network protocols were originally developed, security was not a large issue. Even today, ISPs rarely require e-mail traffic routed from a user to be authenticated. In addition, exchanges between the user’s home workstation and the provider’s server are usually done in clear text, enabling anyone eavesdropping on the communication to clearly see the messages.
Human Vulnerability Issues
Human issues delve into administrator and user errors, with the discussion focused on the following topics:
• Unsecured user accounts
• Unsecured devices
• Hardening devices
Unsecured User Accounts
It is not uncommon for users within an organization to be assigned network passwords when they are issued equipment. While some organizations force the user to create a new password when he first accesses the system, many companies still do not. Too often, the default password on a new system is the assignee’s surname, or the company name, leaving it easy prey for a hacker. Informing a user that it is imperative to change her password might not be enough; a prompt forcing her to do so should be required. Even adept PC users can be unsure of the process to change passwords, and they might be reticent to speak up for fear of embarrassment.
Equally damaging are those users who utilize the same password for every function or, lacking a good memory, write their passwords on a piece of paper and tape it underneath their keyboard.
Unsecured Devices
Hackers are well aware that many new devices, from firewalls to routers and everything in between, often leave the factory with both the username and password preset to admin or another similar word. Because a tremendous amount of work is involved in just installing the new devices, the network administrator might not prioritize the resetting of the factory default passwords. But prior to the unit going live, changing the passwords can help to mitigate a vulnerability scanned for by most hackers.
Hardening Devices
Devices, operating systems, and applications often arrive set to behave in an open and trusting manner. It is the responsibility of the systems administrator to harden a device; this is the process of ensuring that all possible leaks get plugged. For example, some routers, by default, broadcast pertinent configuration information such as their network addresses, and host name. While publicizing that information internally might be expedient for the network administrator, broadcasting that same data on the Internet connection would only aid the hacker in his reconnaissance. By immediately deactivating the discovery protocol, unnecessary broadcasts are curtailed. At minimum, the interface, which faces the Internet, must stop such broadcasts.
Implementation Vulnerability Issues
Implementation issues deal with policy creation, configuration, and enforcement. This discussion focuses on the following topics:
• Password policy
• Access integrity
• Extrapolating policy intent
• Policy enforcement challenges
• Peer group communication
The proceeding discussion on security policy is presented as it relates to attacks. A greater analysis of policy and procedures can be found in Chapter 10, "Essential Elements of Security Policy Development.”
Password Policy
Password integrity and password expiration are vital to security, and it is critical that users understand what is expected of them. If the system accepts alphanumeric passwords or requires a concocted password derived from a combination of numbers and characters, it is incumbent upon the corporation to consistently relay that information to its users. While it might be noted in a security policy, continually reminding users can only aid in overall adherence to the program.
Access Integrity
To effectively maintain a secure border, communication with employees is essential. Certain seemingly innocuous actions could represent a breach of security and, unless otherwise advised, might continue to occur. A user should be cognizant, for example, that under no circumstance is it permissible to disconnect a fax machine and borrow its analog telephone line to connect his laptop to the Internet. Although a user might want to do this when the network is down, utilizing an analog line could open a back door into the network once it is live again.
Extrapolating Policy Intent
Technology often precedes formal policy, requiring employees to understand the intent of company guidelines and ensure that they conduct themselves within the spirit of the guidelines. Even if a situation is not explicitly mentioned, or there is a lack of formal written policy, an employee should be able to discern between acceptable and unacceptable behavior.
For example, wireless hubs are relatively inexpensive, and an employee might decide to purchase his own for office use so that he can still be connected while freely moving about the department. He might justify his actions by concluding that the personal expenditure has increased his productivity, so the company shouldn’t have an issue. But inexpensive wireless hubs typically ship from the manufacturer with the encryption option not yet activated, and the employee’s actions could place the corporation in a highly vulnerable position.
Organizations do not customarily allow unauthorized devices to be installed on their internal networks. Even if it was not specifically detailed in a policy, an employee should have been able to draw that inference.
Policy Enforcement Challenges
An organization faces many challenges, not the least of which is the consistent implementation of its policies. When the corporation is experiencing high employee turnover or has numerous varied-sized remote offices, periodical challenges to policy enforcement might exist. Even where formal policy is not lacking, various departments, or remote offices, could have differing interpretations of the same rules.
Equally important as a written policy is the policy’s consistent implementation throughout an organization.
Security policies are explored in detail in Chapter 10.
Peer Group Communication
Organizations continually stress the need for open lines of communication between departments but, in some instances, open dialogue within departments can be even more critical. A large enterprise acts as an example when it separates its IT department by responsibility. A typical IT group could be divided in the following manner, spreading responsibility, for example, over four distinct parties:
• Workstations group—Includes all in-house and remote users
• Network infrastructure group—Includes, but not limited to, routers and Ethernet switches
• Network security group—Typically includes firewalls and security policy
• Network communications group—Includes WAN (wide-area network), head office–to–branch office communication
While each group bears an enormous responsibility, they all are, at their core, intricately interrelated. A policy that encourages communication and strives for consistent implementation will be better prepared to deal with the unknown.
Categories of Attacks
Preparing for known attacks is relatively straightforward: Equipment can be put in place, logs can be monitored, and IT personnel can be trained and placed at the ready. Dealing with new attacks can be more problematic, but history shows that these attacks seem to take their cue from the past. Acknowledging historical trends can go a long way in preparing for the unknown.
This section first covers the human component and then covers the following categories of attacks:
• Reconnaissance attacks
• Access attacks
• Denial of service attacks
The Human Component in Attacks
Try as hackers might, it is generally difficult for them to completely cover their tracks. They can be successful in somewhat obscuring their trail, but analysis performed after an attack has enabled targeted organizations to see how, where, and possibly why they were attacked, allowing these companies to take necessary measures to plug leaks and ward off similar future attacks. In an effort to expose unlawful activity, many organizations have proactively taken the lead in advising security interest groups. Organizations such as CERT Coordination Center routinely publish wrongdoing, enabling systems administrators to perform preemptive measures that could better secure their networks.
But human nature will continue to play a major role in most organizations: Systems to protect the perimeter are purchased and associated equipment which protects the interior are installed, and until an attack occurs, an organization can begin to feel a comfort level that it is doing everything possible to fortify itself against intrusions. Typically, it is right at that point where human nature begins to assume a greater role.
The most comprehensive equipment can’t help secure an organization if someone goes home at night leaving a back door open. Complacency typically creates exposure, and an organization’s weakest link might be the execution of standard security practices in each of its departments. Human nature dictates that until a breach occurs, until perceived exposure exists, complacency can be masked by thoughts that one is doing the right thing.
By reconstructing an event, network forensic specialists illustrate how reconnaissance attacks, access attacks, and denial of service attacks were carried out on a targeted organization. Through this process, these specialists can act as an enabler, helping the organization to move forward.
Figure 2-1 depicts a generic corporate network, as well as the possible network devices and systems that it uses against attacks. Devices that typically perform targeted tasks are also referred to as appliances. These include, but are not limited to, routers, switches, VPN concentrators, remote access servers, and intrusion-detection sensors. These devices are discussed further in Chapter 3, "Security Technology and Related Equipment.”
Reconnaissance Attacks
Reconnaissance is the observing, gathering, and analyzing of information about a specific area or device. It is often associated with wartime, when participants in a conflict would collect intelligence on their enemy in an attempt to capitalize on the enemy’s vulnerabilities. In IT, reconnaissance invariably precedes a structured attack; the hacker rarely skips this intelligence-gathering step when planning to break into a network.
Through reconnaissance, the hacker collects as much data as possible about the network and hosts that he wants to break in to. As an example, the hacker can do the following things:
• Search for network addresses of possible targets
• Determine the operating system
• Drill down to the version of the operating system
• Determine the applications that are running on the possible targets
The wily hacker has access to a wide array of readily available tools that can aid in determining both the live network hosts and their respective network addresses, also known as IP addresses. IP is the underlying communication protocol used on the Internet and by most organizations (see the following Tech Tip regarding IP addresses). A great deal of effort, and many steps, are required to unearth such data, but when the data is in hand, the hacker is in a position to identify diverse information, from the vendor of the operating system to the version that is installed on a workstation. Proceeding to the manufacturer’s or CERT website, the hacker will search for information concerning significant flaws pertaining to the equipment. It is generally accepted that equipment will experience issues from time to time, and manufacturers post solutions, or patches, to the issues on their websites.
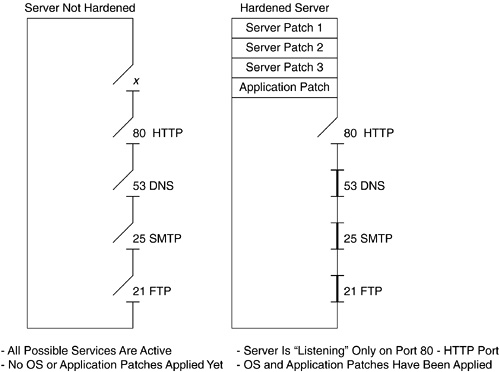
Even the most ardent network administrators have their hands full running their networks, and they don’t necessarily apply patches that would immediately address system known issues. Relying on human nature, the hacker assumes that at least one patch is yet to be installed, so he attempts to determine on which ports the host is listening. A port, which makes a service accessible, is similar to a door, and certain ports are always open so that traffic can flow easily. For example, an outgoing mail server usually receives e-mail messages on its port 25, a file transfer server usually listens on its port 21, and a web server usually welcomes browser requests on its port 80.
The server should only be listening to ports that are relevant to it, and ports that are not needed should be turned off. This is part of hardening a device, as described earlier in this chapter and as shown in Figure 2-3. Active ports that are not required can be an invitation to hackers. Ultimately, the more ports the server leaves open, the more its exposure is increased. This is important to note, because many servers arrive with multiple ports open, by factory default. If a network only requires a handful of ports for its e-mails, file sharing, and web surfing, but doesn’t close the remainder, the organization is more vulnerable than it needs to be. It would be equivalent to the shopkeeper who opens his front door for customers but also leaves every door and window open in the back.
Mapping the Topology
The hacker’s goal during a reconnaissance attack is to do one or more of the following things:
• Discover all hosts on the network
• Discover services (ports) on those hosts
• Determine the OS and the versions of software running on the identified hosts
If the hacker can drill that far into the network, he might eventually be able to plan his assault from multiple fronts.
Network reconnaissance is a fundamental part of information gathering. Similar to the potential criminal who wanders into the same bank branch every other day for two weeks studying the movement of guards and staff in the hopes of exposing vulnerability, he is signaling his intent. Discovering a pattern of harmless intrusions on your network might be a telltale sign of intent to cause damage. Chapter 3 discusses tools that can alert a systems administrator to possible intent.
Access Attacks
An access attack is a breach, widely considered to be a major assault on a network. Using data collected from a reconnaissance, an access attack puts knowledge into motion and executes on specific vulnerabilities.
Capitalizing on Protocol Vulnerabilities
A hacker might decide, for example, to capitalize on a protocol vulnerability by sending the following items:
• A specially crafted packet bearing the same source IP address as the destination IP address
• The same source port number as the destination port number
The workstation to which the packet was addressed, becomes stuck in a loop when trying to reply to the source address—because the source address is also itself—and the result is full CPU consumption.
Packets are further expanded upon in Appendix C, "Quick Guides to Security Technologies.”
Access Stratagems
Conversely, a hacker might use a Trojan horse (a program that purports to do one thing, but is actually doing something malevolent in the background). Inadvertently activating the malicious code concealed in an e-mail, for example, a pop-up window presents an enticing tag line: Click here to see cute puppies. When the code is activated, puppies instantly appear on top of what was already on the screen. In the short time the user is enjoying the dancing puppies, a program is diligently running in the background, accessing the user’s e-mail address book and sending it back to the originator, typically a spammer, an individual or organization that sends unsolicited commercial messages. With multiple new address entries in its customer contact database, the program goes on to send the same Trojan horse to an ever-expanding list of victims. The concept of a Trojan horse is expanded on later in this chapter.
Access attacks are unmitigated acts of trespassing, the hacker’s equivalent of unlawful entry into secured sites.
Denial of Service Attacks
Unlike a typical attack, where a hacker wants to gain control of a system to use it for specific purposes, a hacker attempting to conduct a denial of service (DoS) attack does not necessarily need to gain access to the targeted system to wreak havoc. He merely needs to overload a system or network so that it cannot provide service any longer. DoS attacks can have different targets, ranging from the simple, bandwidth consumption, to the more complex, resource starvation. Some of the classifications for DoS attacks are application DoS, network-based DoS, and distributed denial of service (DDoS).
Denial of service encompasses a range of exploits, any of which are capable of stymieing normal network activities. Its goal is to effectively quash network resources including, but not limited to, processors, memory, storage drives, and bandwidth. It can also include instances where Internet URL directories are purposely corrupted, resulting in Internet traffic being diverted to a third-party website, as evidenced in Figure 2-4, when a user requests the web page www.stropsekin.com, but is unwillingly directed to www.environment.org. Domain name hijacking is discussed later in this chapter. In essence, denial of service (DoS) represents those acts that prevent the use of a network or cause a system to be inaccessible. Similar to other kinds of attacks, they are not necessarily carried out by an external party, nor are they necessarily done intentionally.
Buffer Overflow and Bandwidth Consumption
In an attempt to create a chaotic situation, a hacker might fire off very large data strings in his effort to overwhelm a targeted server, performing an action known as buffer overflow. The hacker is aware that the server has a finite amount of memory and processing power and, as an example, sending an illegally large payload in a ping request could result in a buffer overflow. That particular buffer overflow attack is called Ping of Death, ping being a tool that determines whether a network device is online, as shown in Figure 2-5. Similar to naval sonar, a signal is sent and the return of the signal bouncing off an object is used to gain information.
Specifically, to effectively transmit a very large ping, the ping typically needs to be broken into smaller chunks; upon reaching the destination, the server reassembles the chunks. But the size of the reassembled ping, or chunks, is so far beyond the processing capacity of the Internet Protocol that the buffer, in this example, overflows and effectively shuts down the targeted system. Even those servers with seemingly endless processing power and equally ample memory resources can be stymied if the buffer becomes overloaded.
Mail Bomb
A mail bomb, another DoS attack, is an attempt to direct enormous numbers of e-mails to a single user or system with the goal of overwhelming and derailing the targeted system.
Though typically intentional, a mail storm can be an inadvertent DoS initiated by an internal party. Preparing to be absent from the office for jury duty, an employee might, for example, want to advise those contacting him that he will be unreachable for a number of days. Activating the out of office and reply to all options in his e-mail program, he also activates auto-confirmation, because he wants to ensure that the original sender opened his reply e-mail and understood the response would be delayed.
While these tools are useful when users check their e-mails regularly, they can tax a system if not monitored closely. It is not uncommon for large organizations to e-mail company-wide memos, and when both reply to all and auto-confirmation are activated on a recipient’s e-mail, the result can be overwhelming. If a corporation has 4000 users, the auto-reply feature will, in this case, send out the recipient’s jury duty note to all 4000 users on the network. Worse yet, an auto-confirmation will be sent back to the original recipient, after each of the 4000 users opens his or her e-mail. When the auto-confirmation is received, it sends an auto-reply in response. If any of the 4000 users are similarly out of the office and have their e-mail set up in a comparable fashion, the domino effect can be devastating to a network, grinding it to a halt from the fantastic flurry of e-mail activity. While checks and balances are typically in place to expose unusual activity, significant damage can still be inflicted in the interim.
Domain Name Hijacking
Domain name hijacking has become prevalent, and while fixes have been published, the allure of hijacking a domain name can be too great a magnet for many a hacker; the resourceful ones will likely root out new avenues to keep redirecting traffic. A famous case involved traffic destined for a sportswear manufacturer that was redirected to an environmental website. An odd twist on DoS—because the prospective visitor had seemingly reached the intended site—it would take repeated attempts before realizing that the diversion had been deliberate and done without the visitor’s consent.
Distributed Denial of Service
While a DoS attack is straightforward for even a novice to initiate, a distributed denial of service (DDoS) requires barely more expertise. Where a DoS attacks from a single point, a DDoS recruits other computers across numerous networks, resulting in an attack from multiple fronts.
A hacker initiates his plan by searching for a network he can compromise. Performing reconnaissance and pinpointed access attacks, he locates a vulnerable system and loads specific hacking software onto it. The attacker activates the newly loaded program to work in stealth mode, so a systems administrator performing a routine examination of the network wouldn’t necessarily notice the malicious application. As shown in Figure 2-6, the newly recruited handler, also known as master, searches its network for peer workstations that can be compromised and plants malicious software to turn the workstations into agents. The hacker continues his search for additional vulnerable networks until he has successfully breached, for example, eight networks. If each of the 8 workstations he compromised is able to find 99 others, he will have amassed an army of 800 workstations spread over 8 different networks from which to launch his attack.
Typically choosing a famous website as his target, the hacker adds a twist to his plan. He sends a request to the website, knowing that its reply will always be sent to the originator’s network address. The hacker’s twist is that he involves an unaware third party, typically another well-known website, and modifies that source, or originator network address, in his requests.
With 800 workstations, from various networks, preprogrammed to send 1000 header-modified requests simultaneously (an information-carrying ping that appears more legitimate to the about-to-be-breached server) to the target, www.skoobnozama.com is not only overwhelmed, but the server’s automatic response to the requests is also returned to the falsified address—www.mitciv.com—as shown in Figure 2-7. The hacker will have successfully used 8 unwilling networks, and 800 of its workstations, to send 800,000 requests to the www.skoobnozama.com website and worse, force the breached website to unwittingly attack another website, www.mitciv.com, with the mandatory 800,000 replies.
In summary, forensic analysis allows organizations to understand how and why they were attacked, typically resulting in higher walls being erected after a breach. Certain organizations can be reticent to react in such a manner because, some might surmise, the movement of hackers is so quick that the game is perpetually being ratcheted up a notch, and hackers will be looking forward to their next complicated attack rather than looking to the past. But history tends to repeat itself, as hackers seem to look to the past to figure out how they are going to attack in the future. Whether social engineering is the old conman’s game or reconnaissance is similar to the petty criminal scouting a sleeping neighborhood searching for unlocked doors, human nature suggests that people tend to pull from their store of knowledge when they chart a path for the future. Organizations would be wise to do the same.
Additional Common Attacks
The list of possible attacks is endless, with new ones surfacing each week and older ones being resurrected, richly peppered with unique twists to make them more explosive in their reincarnated state. Hackers typically drive new attacks, pushing the envelope at every turn, because their main preoccupation is to wreak havoc. While an exhaustive analysis of attacks could fill its own book, the goal of this section is to provide a basic overview of some common attacks, understanding that many newer ones are often subsets or combinations, of what already exists. The discussion includes the following topics:
• Footprinting
• Scanning and system detailing
• Eavesdropping
• Password attacks
• Impersonating
• Trust exploitation
• Software and protocol exploitation
• Worms
• Viruses
• Trojan horses
• Attack trends
Footprinting
Performed during the reconnaissance stage, footprinting is the process of identifying a network and determining its security posture. The hacker attempts to create a layout of the IT operation, by mapping out the following items:
• Geographical location of corporate IT assets
• Related companies—extranet—to find weakest links
• Phone numbers assigned to corporate analog
• Names of employees, usernames, and e-mail addresses
Individually, each parcel of information could be deemed somewhat innocuous. By combining these pieces, the hacker is able to draw a map that can roughly determine the architecture of the overall system and its security infrastructure.
Scanning and System Detailing
Scanning and system detailing, part of the reconnaissance stage, is the process of probing for live servers, determining which ports are active, and drilling down further to discover details regarding applications and versions running on the system.
The hacker, for example, might be running a reconnaissance overnight, as shown in Figure 2-8. By using port-scanning software, a report can tell her which stations are live and what ports the stations are listening on. If the report states that the system is listening on ports 21, 25, and 80, all well-known ports, she can surmise that the equipment is most likely a server. By drilling down further and determining the operating system, she can confirm her suspicion. Utilizing that information, she can then search for known vulnerabilities inherent in the operating system, as well as the particular version of the OS.
Eavesdropping
Eavesdropping is a traffic-analysis program that sniffs (monitors), records, and analyzes network traffic. As shown in Figure 2-9, the hacker uses software that does the following things:
• Listens to all communication on a network
• Captures each bit of every transmission
• Uses a protocol analyzer to reassemble packets of information, allowing it to read e-mails, for example
Eavesdropping can quickly reveal usernames and passwords, enabling the hacker to eventually impersonate a user to gain entry into the network.
Password Attacks
A password attack is a process the hacker employs to learn user passwords.
Discovering a legitimate username within a network is only valuable if the hacker can also determine the user’s password. Depending on how well the hacker knows the user, he might first go through the obvious list: given name, company name, birth date, maiden name, and family names. Many systems use a three-strike access rule, whereby the system locks out the user after his third failed authenticating attempt. If the hacker were unable to establish the passwords, he might favor an attack known as a brute-force attack, which uses a process that tries seemingly endless combinations of letters, numbers, and symbols in an attempt to determine a user password. This technique works particularly well when the three-strike rule has not been implemented.
Conversely, if the hacker is an insider, he might opt to walk by a workstation and see whether the user wrote her password on a slip of paper and taped it to her keyboard. Alternatively, an insider could also be aware of certain tools that provide access to encrypted password lists on a network, such as password decryption tools, which can take advantage of weak encryption algorithms.
Impersonating
Impersonating describes the person or persons who unlawfully assume a legitimate user’s credentials for the purposes of deceiving a computer network.
The hacker might sniff on a network (monitor its traffic) in an attempt to uncover a username and its accompanying password.
Conversely, the hacker might opt to steal a purse, wallet, or personal digital assistant (PDA) that belongs to a network administrator, knowing that many people keep pertinent access information close at hand.
With this sensitive data, the hacker would be able to access the targeted network with the full authority to run it. After the attack has been carried out, the hacker has minimal fear of being caught, because analysis after the fact will attribute the breach to the impersonated user. However, exhaustive forensics could ultimately reveal the true hacker.
Trust Exploitation
A trust relationship exists when two systems, possibly operating within the same organization or, as an example, two separate organizations that connect for just-in-time processes, grant certain two-way access privileges to each other. A user authorized on server X would be provided with privileges on server Y, with both systems openly allowing the other in. The premise is that if a user is precleared on one system, that gives her automatic right, or trust, to access the other system. Trust exploitation, as shown in Figure 2-10, can occur when a hacker, who might have been unsuccessful in his attempts to break into server X, discovers he is able to penetrate server Y and, exploiting the trust that is inherent between the two systems, successfully works his way back to server X and inflicts damage.
Software and Protocol Exploitation
It is not uncommon for flaws to exist in software and operating systems. While vendors are thorough in their research and development, the possibility exists that product containing flaws could be shipped to an end user. Similar to most other industries, software manufacturers are quick to respond, issuing patches for the flawed software. The wily hacker, aware that his targeted organization uses the affected software, relies on human nature when he surmises that most network administrators are very busy and might not install the needed patch the moment it is published. Taking advantage of that window, the hacker attempts to break into the system, exploiting the flaw in the software.
When major software revisions are initially made available, organizations can decide to delay implementation until the inevitable quirks, or issues, have been determined and a less problematic version of the software revision is available.
Another type of exploiting occurs when a tool is used for something other than its original purpose. Pinging, for example, was created to aid network administrators in determining whether equipment was live on their networks. While they could have walked around the facility and seen for themselves, it was not only faster to send a signal and see whether the appliance responded, but networks were also quickly becoming geographically larger, and walking around to check on equipment was becoming a poor option. Hackers seized the checking tool and used it for their own nefarious purposes.
Worms
A worm is a program that potentially contains malicious code that continually replicates itself as it works its way through networks. Although worms self-propagate, unlike viruses, worms are not designed to impose harm on their host systems.
The primary goal of a worm program is to replicate itself on as many networks as possible, sometimes gathering data, possibly e-mail address books, from each of the breached systems.
Worms can quickly create a DoS attack by bottlenecking networks. The Melissa worm in 1999 wreaked havoc and stymied systems as it literally wormed its way through networks, duplicating itself whenever it came into contact with a target. It would worm its way into the targeted user’s e-mail address book and then forward itself to the first 50 addresses it found. The worm would arrive at each new victim’s computer disguised as e-mail from someone the victim seemingly knew. Not surprisingly, the unsuspecting user would open the e-mail and the worm would perform the same act: Each worm found 50 new addresses, reattached itself, and 2500 new victims were attacked. Those 2500 victims each found 50 more to infect and, quite rapidly, the aberrant e-mail propagated throughout the Internet on the backs of address books, leaving bottlenecked systems in its wake.
Viruses
A virus is a software program that strives to generate great harm by corrupting files or functionality on a system. Early-generation viruses required the help of an unwitting accomplice, typically a system user, to propagate itself. But viruses have matured and now often include worm-like characteristics that enable self-generating replication. Code Red was a prime example of this type of hybrid. It acted like a virus by dynamically generating new web pages on infected web servers that made the claim Hacked by Chinese. In its sister role as a worm, it also self-propagated and spread itself to other networks, continually seeking new web server victims in its path of infection.
Trojan Horses
A Trojan horse is a malicious program that masquerades as a legitimate one, purporting to do one thing in the foreground while it is doing something malevolent in the background. A Trojan horse is a popular means of disguising a virus or worm, as described in the puppy example in the section "Access Stratagems,” earlier in this chapter.
Attack Trends
Combination malicious attacks, known as combo-malware, are becoming more prevalent. By combining the most destructive elements from past attacks with the most effective tools available today, hackers are able to combine worms and viruses that replicate faster, cause greater damage in shorter periods of time, and leave fewer clues for forensic analysts.
While the industry should anticipate attacks to become more sophisticated, most hackers themselves likely will not. Regrettably, the tools available, along with easily obtainable elementary instruction guides, make attacks a pastime in which too many could effortlessly engage. The tools that carry out malicious activities are more powerful with each new iteration, as illustrated in Figure 2-11. Hackers’ technical abilities need not be as advanced as in the past, because their tools are now so automated and powerful that they can carry out the attacks.

Figure 2-11. Inverse Relationship Between Hacker Knowledge and Hacking Tools (Source: "Cisco Networking Simplified,” 1-58720-074-0, Cisco Press)
But a small minority remains that relishes the cerebral challenge that a breach poses. The reality for organizations is that they must contend with this element and use mitigation tools to deal with those who perpetually strive to unearth innovative ways to breach even the most sophisticated intrusion-prevention systems. A basic key for most organizations is to first acknowledge their weakest links and then implement procedures to fortify them, ensuring that any future programs are built on terra firma.
Wireless Intrusions
Wireless networks have simplified daily rituals for many people, from the remote user whose laptop is configured to borrow any wireless signal it can detect regardless where he might be to the office-bound professional who can shift to multiple locations within a building and always maintain his wireless connection. While much has changed in the new office realm, attacks perpetrated against wireless systems have not. Notably, some of the so-called traditional attacks can still be used against wireless systems and, of more concern, these attacks are also less complicated to stage. In many of the following examples, wireless access points (WAPs) are deployed throughout an office. A WAP is a wireless hub, layer 1 device that provides physical connectivity—in this case, through radio frequencies instead of unshielded twisted-pair cable. Some common types of wireless intrusions are as follows:
• Wireless eavesdropping
• Man-in-the-middle wireless attacks
• Walk-by hacking
• Drive-by spamming
• Wireless denial of service
• Frequency jamming
• The hapless road warrior
Wireless Eavesdropping
A hacker attempting to eavesdrop in a wired environment must be physically connected to her target’s network infrastructure, as opposed to being in a wireless situation, where she need only be in the vicinity. Yet she would still face issues, such as contending with possible broadcast interference and the uncertainties inherent in sending signals around concrete walls.
An activity known as war driving could easily be referred to as drive-by eavesdropping, because it typically involves an individual driving an automobile, attempting to log on to wireless networks, as shown in Figure 2-12. It’s not an illegal act, because radio frequencies used by LANs (local-area networks) are unlicensed public frequencies. Unless an organization could prove that a war driver was acting with intent, compiling information for an attack, it could prove difficult to bring such a hacker down.
Man-in-the-Middle Wireless Attacks
A typical wireless office has wireless access points scattered about its building, and with so many signals available, equipment is generally configured to attract the strongest signal each time it boots up. Hackers have been known to position their own wireless access point just outside an office window, resulting in a workstation being more attracted to the hacker’s hub than an office antenna, which could be farther away. Called a man-in-the-middle attack, the rogue access point can reveal invaluable information—for example, usernames, associated passwords, the network’s authentication request mechanism, and so on—while the unsuspecting user attempts to connect to his supposed network.
Walk-By Hacking
In his article "Walk-by Hacking" in The New York Times Magazine (July 13, 2003), Eric Sherman relayed the story of his short stroll along The Avenue of Americas in Manhattan. Armed with his laptop and a $40 network interface card, he connected to 13 different networks along a 45-foot stretch of sidewalk. Of those 13 networks, only one-third were using encryption. While connecting shouldn’t necessarily be equated with breaking in, the hacker can still engage in disruptive activity, namely, bandwidth hogging. Borrowing a network’s bandwidth for the hacker’s own, possibly innocuous, activities can slow the network’s pace in its own office.
Drive-By Spamming
A person who engages in sending spam e-mail could be a prime candidate for stealing bandwidth. Possibly reticent to initiate mass mailings through his own outgoing mail server, or simply lacking enough bandwidth himself, the hacker parks his vehicle in close proximity to the targeted network, connects to his wireless signal, and sends e-mails. He not only minimizes his own costs, but he also reduces the likelihood of getting caught, because the sender will technically be the breached network. Similarly, spammers can also spoof the receiver address so that it is the same as the sender address. As a result, the victim receives messages that appear to have been sent by himself.
Wireless Denial of Service
To carry out a DoS in a wired environment, a remote hacker must crack through an organization’s firewall. In a wireless environment, the hacker need only position himself in close proximity to the building to initiate network contact and begin his acts of intrusion. His job is even easier to execute if the corporation has not yet activated encryption on its wireless network devices.
Frequency Jamming
An attack that is more prone to a wireless environment is frequency jamming. The hacker attempts to overload every frequency over which the network is broadcasting, bringing all internal activity to a standstill.
The Hapless Road Warrior
Many laptop users spend a certain amount of time away from their office but still have the need to connect with their organizations while on the road. To ensure ease of use, wireless network cards installed on laptops are configured to search and capture every available signal they can locate. Similarly configured is e-mail software, which immediately begins to synchronize the moment its network card makes a connection.
While convenient, problem situations can arise. For example, a CEO of a medium-sized public company was working on his laptop during a drive through a high-end residential neighborhood when he noticed his e-mail begin to synchronize. When the car drove through an intersection, it suddenly stopped synchronizing. A block later, his e-mail started to synchronize again and, as the car drove along, it stopped again. On its third attempt to connect, the reason became clear: The e-mail program was designed to synchronize as soon as its network card found a wireless signal to borrow. Driving through the neighborhood, the CEO’s laptop kept locating signals emanating from the wireless LANs installed in neighborhood homes. Because the vehicle was moving, it lost signals as quickly as it picked them up. Had the car been stationed in front of a wireless home, he could have sent e-mails all afternoon, provided that the network was not protected with an encryption option.
Social Engineering
An individual who purports to be someone he is not, or who assumes a persona and proceeds to engage insiders in verbal and written conversation for the express purpose of infiltrating their organization, is understood to be engaging in social engineering. These individuals possess persuasive communication powers, ably convincing their targets to reveal confidential network information. The social engineer rarely employs technology in the pursuit of information. The tool of choice is similar to that of the old-time conman: fast-talking conversation.
Social engineering is not a new phenomenon. Kevin Mitnick, a self-proclaimed social engineer, has publicly stated that he rarely used his technical expertise to garner information. He simply employed an endless range of communication tactics.
Examples of Social Engineering Tactics
The conman initiates telephone contact with an organization’s IT department, claiming to be an official with the company’s service provider. He speaks with authority, stating that he was delayed by an off-site project and couldn’t return to his office in time to perform a required diagnostic analysis of the network. And therefore, he doesn’t have the network passwords with him. Requesting the help desk agent’s assistance, he asks for a favor: Could she provide the current network password so that the analysis could be done remotely? The help desk agent succumbs to the tired and weary technician, and she supplies the requested information.
Conversely, the conman can pose as the network administrator and contact a user in a remote office. He informs the branch employee that due to system maintenance performed overnight, his account needs to be reset right away. Peppering the conversation with technical jargon, he gives the employee every reason to trust him. When he inevitably asks for the password, the user doesn’t hesitate to supply the requested information.
The conman has also been known to employ aggressive telephone tactics. Posing as a senior manager, she will intimidate a help desk agent, forcing the agent to divulge proprietary access information. Try as the agent might, when a senior manager is threatening him, the inclination is to provide the demanded passwords.
With millions of customers using personal identification numbers (PINs) daily to carry out financial transactions, the banking community was confronted with vulnerability in its ATM network. While the community fortresses had high walls, conmen focused on the bankers’ weakest link: their customers. Assuming that the consumer wouldn’t suspect an official request for information, the social engineer wily conned individuals into providing the keys to their personal safes. Posing as bank officials, the conmen made telephone contact with consumers and convinced them to expose their PINs. Swiftly responding to the attacks, the banking community informed their customers that under no circumstance would a bank representative ever telephone them and request that they reveal their PIN. But the damage had been done.
Social engineers have been quick to capitalize on the growing trend to outsource nonkey functions. A typical small- to medium-sized business (SMB) in cost-reduction mode might decide to maintain an in-house IT department for its key infrastructure needs, but to outsource such perceived minor functions as its help desk. Handling calls from a branch office whose network is down, or a remote user who can’t access her e-mail, the help desk is seen as a quick-fix department, which is best handled by a third-party provider specializing in the field.
Depending on the service provider the SMB engages, the technicians fielding calls might be the weakest link in the chain. Possibly overwhelmed on a particular day, needing to get users off the telephone and get back online, they skip in-depth identification probes and unwittingly release proprietary network access information to an intimidating, angry, senior-sounding voice on the telephone. It is important to note that this scenario could exist even if the department remained in-house. Third-party services can impose authentication processes that are more stringent than those an organization might initiate, or enforce, in-house.
Using third-party relationships can be quite safe, assuming that the company has a verifiable track record and that rigid rules tie back to an enforceable security policy that doesn’t tolerate shortcuts.
The conman has many faces, changing his identity and calling card as the situation warrants. The best protection is a specific and enforced security policy that dictates what, if any, information can be handed out. Most importantly, the document should detail how someone must present himself or herself to be in a position to even seek information. With all parties aware of the policy, the help desk representative can have the necessary strength to stand tall against the belligerent senior manager.
Summary of Attacks
Table 2-1 provides a summary of common attacks and their characteristics.
Most attacks share some common components, not the least of which is patience on the part of the hacker, because many attacks require intricate planning. A DDoS attack, for example, is generally preceded by a reconnaissance attack and an access attack, as shown in Figure 2-13.
Cisco SAFE Axioms
Cisco’s SAFE blueprint, a best practices guide for designing and implementing secure networks, enables organizations to determine the type and level of security that should be implemented throughout their networks. The SAFE blueprint addresses the enterprise as a whole and identifies and examines each major facet of a security-conscious network. The SAFE blueprint aids organizations in realizing a security environment that can accurately reflect their desired security posture.
It would be foolhardy to look at the infrastructure of a network and categorically declare that certain facets were either out of a hacker’s reach or simply held no interest for him. The dismal reality is that every aspect of a network is a target. Whether it’s an appliance, a server, a link, or the network itself, every element and component is potentially in a hacker’s gun sights. Regrettably, nothing is immune from attack.
Using Cisco’s SAFE blueprint, this section considers the following targets:
• Routers
• Switches
• Hosts
• Networks
• Applications
Routers Are Targets
A router, at its core, is an interface between networks. Routers are intelligent devices, widely used from small network environments to large Internet service providers. By using routing protocols to share information with neighboring routers, they keep data circulating on corporate networks and the Internet. They forward data or packets within networks on a hop-by-hop basis, with each router along a route determining the next hop to send the data.
Routers not only maintain a table of available network routes, but they are also able to distinguish between an organization’s large network and all of its subnetworks. Using their knowledge, routers determine the most efficient route to use when sending data between senders and receivers.
Routers’ support of multiple protocols and their ability to interconnect networks, coupled with their continual broadcasting or multicasting to that effect (they are commonly stationed at the edge of complex data networks), make them highly susceptible to attack.
Protecting routers is a critical element in security deployment, requiring those responsible for routers to be acutely aware of their inherent vulnerabilities. By keeping abreast of the latest threats and most pertinent router protection information, security professionals work diligently to safeguard their systems.
Switches Are Targets
Switches help to control congestion in a system by breaking traffic into smaller, logical, and more manageable units. Most users within large organizations typically direct the vast majority of their network traffic to destinations within their own workgroups. For example, switches can contain traffic within a finance department by linking its workstations to printers and other equipment that service only its department. When workgroups are segmented, system speed and efficiency are optimized, because the number of users sharing the same equipment has been limited.
While departmental switches are interconnected to allow the flow of information between workgroups, the switches never do so unless requested. The goal of a switch is to ease overall congestion and to optimize system performance by compartmentalizing as much data as possible.
Switches create the physical backbone for a LAN and would be a target for hackers desiring to disrupt a network. It is highly recommended that network administrators take measures to protect switches from potential hackers. The following list covers switch security basics, but it is not meant to be an exhaustive representation:
• It is best to avoid configuring switches using a network connection, particularly if the communication is in clear text. Use encryption for in-band configuration or configure the switch as out-of-band, as described in the sidebar "Out-of-Band and In-Band Management.”
• Ensure that access to configuring switches is restricted to system administrators.
• Unless required, deactivate discovery broadcast.
Hosts Are Targets
Hosts are intelligent devices that comprise, but are not limited to, servers, mainframes, and computers that make services available to other computers on a network. They often provide services such as www, e-mail, and file download capabilities. Unfortunately for hosts, they are easy targets.
Generally accepted practice for hardware and software vendors is their issuance of patches and fixes for their installed base of product, whenever it has been determined that issues have arisen. Failure to subscribe to an automated notification service means that a network administrator never knows when alerts will be published, and he therefore must always be on the lookout for patches that are relevant to his equipment. Just as importantly, he must be prepared to install the patches as soon as he is made aware of an issue.
Network administrators are faced with the following fundamental issues:
• Security notices are issued haphazardly, and it’s critical that most be addressed urgently.
• A wide array of equipment is typically under their control, and most appliances need to be handled separately.
• Equipment is usually purchased from a multitude of sources, resulting in diverse hardware with different operating systems and applications. Patch alerts arrive from a vast array of suppliers, with little or no uniformity to them.
Hosts provide services, such as www, to other computers on a network and, as a result, become highly visible to hackers. While other components continue to be targets, they are not generally as vulnerable. The job of a router, for example, is to move data from one host to another host. The end result is that the destination, and not the path taken, becomes the more vulnerable device and, ultimately, the more obvious target.
Networks Are Targets
Networks bring diverse components together and allow them to communicate and share information in an efficient manner. Networks connect computers with printers and connect servers with innumerable communication devices, while at the same time allowing users and resources to exchange information and perform tasks.
A planned DDoS can have certain appliances in its gun sights as it executes an attack on a network, but it doesn’t necessarily view the network itself as a target. But as evidenced in Figure 2-15, a well-executed DDoS can have as great an impact on an overall network as it could have on individual appliances. A hacker launches a DDoS attack through the master, along with 100 recruited agents.
A DDoS disrupts regular network traffic and, by the time the administrator is notified that traffic is crawling, the damage will have been done, as follows:
1. The outbound traffic, on a mission to cause more harm, not only disrupts internal network traffic but also probably uses most of the network’s Internet bandwidth, stymieing all potential incoming traffic that might be headed for the company website.
2. When the attack reaches its destination, the DDoS and its onslaught of data consume any available bandwidth. The server runs the risk of crashing because of resource starvation.
Some of the most frustrating attacks are those that cannot be predicted or stopped. The effects of a DDoS could be muted somewhat by effective coordination within an organization’s ISP.
Applications Are Targets
An application, or software, is a program that both servers and computers use to perform tasks.
Programs are highly complex, and software manufacturers have, at times, found it challenging to produce them without flaws. Commonly referred to as bugs, these flaws have run the gamut from innocuous errors to potential disasters. A well-known bug allowed hackers to remotely access servers; hackers were recognized as administrators and granted full network privileges, including configuration.
CERT and similar agencies regularly post security advisories. Because potential hackers routinely check the same sites, or even get automated notification detailing the latest flaws, it is advisable to follow the guidelines in the reports, which typically suggest applying patches immediately.
Summary
Threats will inevitably exist. Regardless of a hacker’s motivation, recognizing that systems are inherently vulnerable is a fundamental first step in deciding what an organization is prepared to tolerate. This chapter focused on the following topics:
• Recognizing vulnerabilities
• Understanding attack types
• Understanding attack processes
• Acknowledging power-of-persuasion attacks
• Recognizing that every part of a network is a potential target
Making the business case for security investment involves many components, not the least of which is determining an organization’s real cost of vulnerability. In today’s climate, it is not yet possible to rule out threats, but the desired level of mitigating them can potentially limit any impact they could possibly inflict. The following chapter advances the discussion by addressing threats directly and detailing how an organization can protect itself.