Chapter 4. Putting It All Together: Threats and Security Equipment
The discussion to this point has centered on potential threats and the technology and equipment that can be used to guard against attacks. This chapter takes that information and offers a range of security topologies that organizations can implement to reflect their tolerance for risk. Risk tolerance determination is explored in Chapter 5, "Policy, Personnel, and Equipment as Security Enablers,” and Chapter 7, "Engaging the Corporation: Management and Employees.”
This chapter covers the following topics:
• Threats, targets, and trends
• Lowering risk exposure
• Security topologies
Threats, Targets, and Trends
Many types of attacks have been discussed in the previous chapters, and while new ones might be appearing on a regular basis, older ones are not necessarily dying off—they are being reused and reinvented in ever-destructive ways. Table 4-1 lists some of the attacks that have been addressed in earlier chapters and states whether their frequency is on the rise, declining, or holding steady.
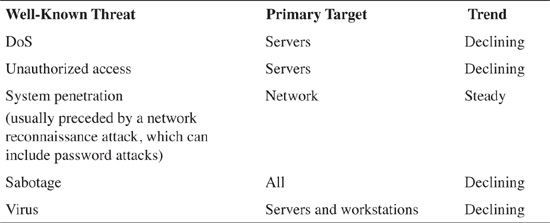
Table 4-1. Threats, Targets, and Trends According to CSI/FBI[*]
[*] "CSI/FBI Computer Crime and Security Survey 2004.” Computer Security Institute and Federal Bureau of Investigation (CSI/FBI). http://i.cmpnet.com/gocsi/db_area/pdfs/fbi/FBI2004.pdf.
It is relevant to note that certain statistical data regarding attack activity can be somewhat contradictory—different sources reveal differing attack trends. For example, the 2004 E-Crime Watch Survey, conducted by CSO Magazine in cooperation with the United States Secret Service and the CERT Coordination Center, reports that attacks are up 46%, whereas other organizations report downward trending.
At first glance, the data appears to be conflicting. But delving further, the data reveals a landscape that is being better protected by tools and equipment such as antivirus (AV) software, IDS, IPS, and so on. If organizations were to scour their logs for all attacks that were attempted against their networks, most would likely discover that while the numbers of attacks were on the rise, the damage that had been inflicted had been substantively decreased because of the equipment that had been put in place.
Organizations that have invested in IT security prevention equipment over the last number of years will have experienced the positive trending that has recently been reported. Sustaining an environment that is focused on preventive measures continues to pose a challenge, as attacks, and attackers, will forever attempt to find vulnerable points that can be penetrated.
There might not always be agreement on attack trends, but following them ensures that an organization is always aware of existing threats. An appropriate infrastructure, aligned with an organization’s tolerance for risk, can be effectively developed to address the bevy of ever-present threats.
Lowering Risk Exposure
Equipment is available to address most risks, and while new and reinvented threats will inevitably continue to abound, implementing fundamental security appliances and practices throughout the system can aid organizations in their attempts to mitigate such threats.
Additional measures can also be taken to reduce the risk of attack and to ensure that hackers cannot clandestinely use an organization’s network. Refer to the sidebar “Tech Tip: Being a Good Netizen.”
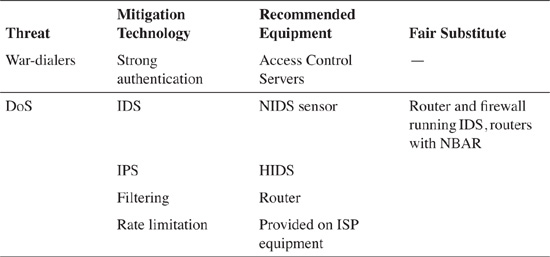
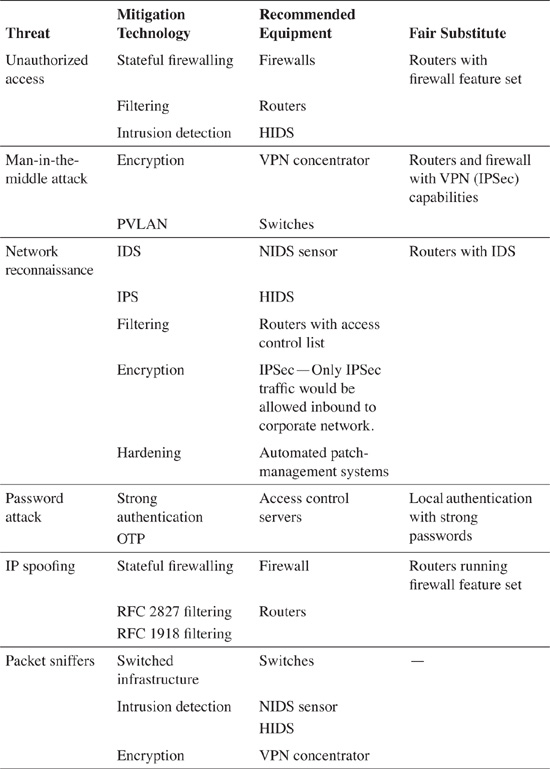
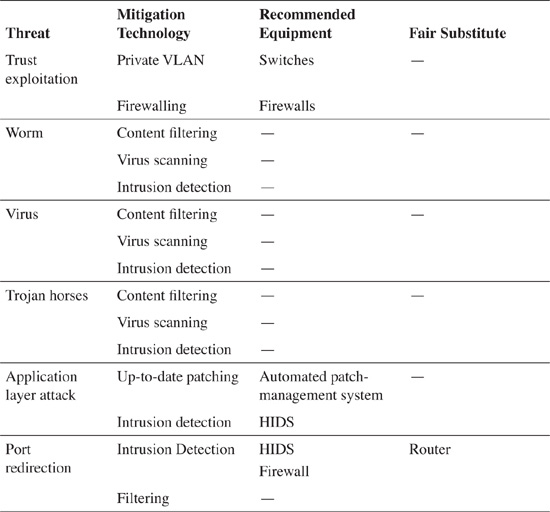
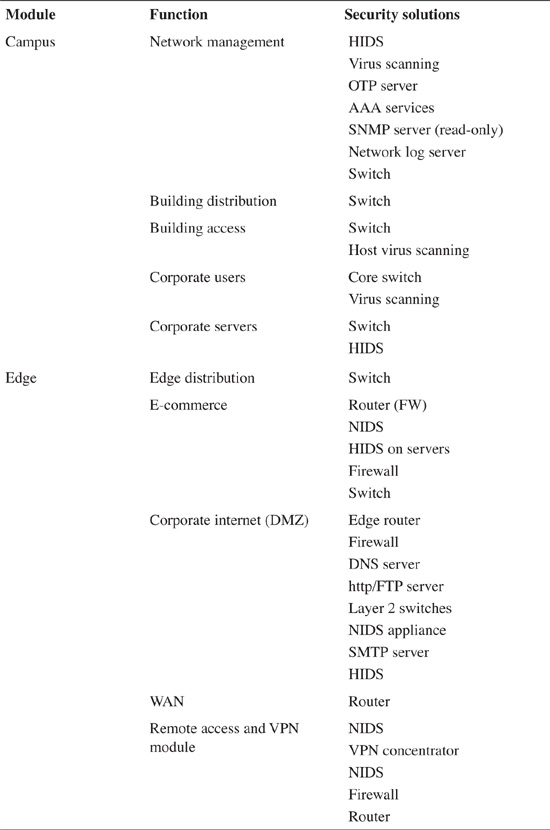
Table 4-2 borrows threats from Table 4-1 and provides an appropriate type of technology that can effectively mitigate a particular type of attack. It lists the equipment in which the mitigating technology is primarily found, along with a fair substitute—other equipment that can be effectively used to also provide similar mitigation, albeit invariably to a lesser degree.
Security Topologies
Cisco has developed a best-practices guide, called SAFE, for designing and implementing secure networks. The guide addresses different-sized organizations, from small- and medium-sized businesses (SMBs) to large enterprises. Cisco also addresses specific situations, or issues, of functionality, in an attempt to aid organizations in determining the type and level of security that should be implemented throughout a network.
The SAFE series of best-practices can assist the reader in joining the vulnerabilities that were discussed in Chapter 2, "Crucial Need for Security: Vulnerabilities and Attacks,” and the network security mechanisms that were discussed in Chapter 3, "Security Technology and Related Equipment.” Using the network models presented in the SAFE series, readers can learn how to combat security threats originating from both inside and outside the organization. Through the use of a modular design, they can create a scalable, corporate-wide security solution.
This section considers the following topics:
• SAFE blueprints
• SAFE architecture
• Using SAFE
SAFE Blueprints
The Cisco website (http://www.cisco.com/go/safe) provides a multitude of readily available SAFE blueprints, including the following:
• SAFE: A Security Blueprint for Enterprise Networks (SAFE: Enterprise)—Provides information on designing and implementing secure networks for large organizations.
• SAFE: Extending the Security Blueprint to Small, Midsize, and Remote-User Networks (SAFE: SMR)—Provides information on designing and implementing secure networks for small organizations or networks, which can include branches of larger organizations, or stand-alone operations. It also provides information on remote-user networks, such as those for mobile workers and teleworkers.
• SAFE: VPN IPSec Virtual Private Networks in Depth (SAFE: VPN)—Provides information for designing and implementing enterprise IP security (IPSec) Virtual Private Networks (VPNs).
• SAFE: Wireless LAN Security in Depth (SAFE: Wireless)—Provides information for designing and implementing wireless LAN (WLAN) security in networks.
• SAFE: IDS Deployment, Tuning, and Logging in Depth (SAFE: IDS)—Builds on the information in high-level design guidance for NIDS sensor placement, host-based IPS implementation, and secure syslog messaging by discussing in detail other IDS and logging design considerations and best practices.
• SAFE: Worm Mitigation (SAFE: Worm)—Describes best practices for containment and mitigation techniques and technologies that can be used against worms.
• SAFE: IP Telephony Security in Depth (SAFE: IP Telephony)—Provides information for designing and implementing secure IP telephony networks.
SAFE Architecture
Many SAFE blueprints are available, and while all hold great value, this book focuses on SAFE: Enterprise and SAFE: SMR.
This section explores the following topics:
• SAFE: A security blueprint for enterprise networks
• SAFE: Extending the security blueprint to small, mid-size, and remote-user networks
SAFE: A Security Blueprint for Enterprise Networks
The blueprint for enterprise networks emulates, as closely as possible, the functional structure and requirements of enterprise-sized networks and allows scalability and redundancy.
Scalability ensures that components can be added without needing to dismantle the current SAFE architecture that is in place on a network. Redundancy recognizes that certain appliances on a network could be considered mission-critical and that the security topology must have room to meet the demands of those types of requirements by doubling-up equipment.
SAFE uses a modular architecture that allows designers to address individual blocks of a network module-by-module, rather than requiring designers to contend with the entire enterprise every time security is addressed.
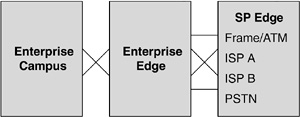
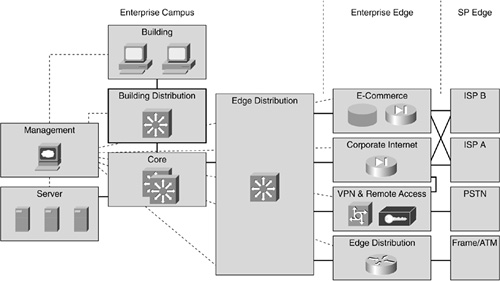
In Figure 4-1, the first layer of modularity is illustrated, with each block representing a functional area of the enterprise. As a side note, because the Internet service provider (ISP) module is not implemented by an organization, it is not discussed here.
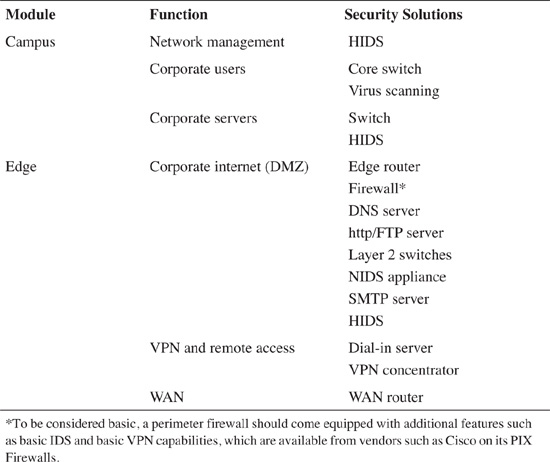
Networks found in large organizations today typically consist of two fundamental functional areas: campus and edge, as shown in Figure 4-2. Because both areas are significant in size and complexity, the Cisco SAFE blueprint addresses each of their issues by subdividing them into specific modules that address each functional area. For example, the campus functional area typically includes a server module, a management module, a building distribution module, and similar modules. This modular approach helps to ensure that undivided attention is delivered to one vital aspect of the network at a time.
The primary role of SAFE blueprints is to ensure that mitigating functions are specific to the particular threat that a network module addresses.
SAFE: Extending the Security Blueprint to Small, Mid-Size, and Remote-User Networks
The SAFE blueprint for small- and medium-sized businesses and remote-user networks (SMRs) is similar to that available for enterprise networks, except that it is sized for smaller networks. SMRs can include branches of large enterprises or stand-alone small- to medium-sized security installations.
The SAFE document also provides pertinent information on remote-user networks.
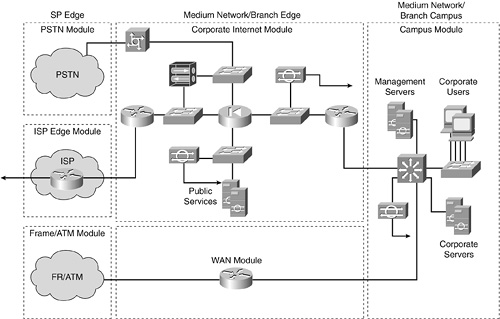
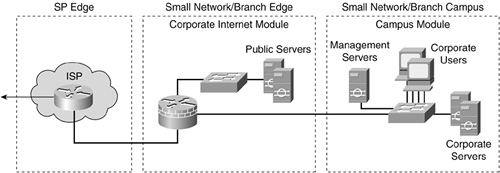
The SAFE enterprise model represents the most comprehensive security blueprint. Figures 4-3 and 4-4 illustrate how the smaller models take their lead from the enterprise offering.
Using SAFE
Every organization has an operating and network structure that is somewhat unique, and it might not always be possible to slot requirements into one particular model, as described earlier in this chapter. The SAFE enterprise modular approach provides an effective solution to that issue by allowing security functions to be implemented modularly across a network. Network security topology models that address three general levels of risk aversion (basic, modest, and comprehensive), are presented in this section with risk tolerance itself being further explored in Chapters 5 and 7.
This section considers the following three network security topology models that organizations can use in their search for the most appropriate fit:
• Basic network security topology
• Modest network security topology
• Comprehensive network security topology
Basic Network Security Topology
Two organizations will likely have different definitions of what might constitute a basic network security topology model, particularly if they operate in different industries. Each of the three models presented in this section can be used as guides when developing security models in-house, but they are not meant to represent definitive solutions. For example, one organization might consider a straightforward firewall as constituting basic protection, whereas another might assume that a firewall would need to incorporate NIDS, among other offerings, to be called basic.
At a minimum, it is expected that workstations—be they stand-alone, networked, corporately owned, or situated in users’ homes—are equipped with virus-protection software. The same is true for servers, regardless of whether they are connected to the Internet. Any server that is used for finance, engineering, general administration, or any operational function should be equipped with a host-intrusion prevention system.
All organizations that connect to the Internet, regardless of their size, should install a firewall. Stateful firewalls, as discussed in Chapter 3, cost as little as a few hundred dollars for a basic unit.
Modest Network Security Topology
Modest network security topologies are different for large enterprises and SMBs, resulting in the shopping lists for each being presented in separate tables.
Table 4-3 presents a modest security model for an enterprise network. It corresponds with Figure 4-2.
Table 4-4 presents a modest security topology for an SMB. Table 4-4 corresponds with Figures 4-3 and 4-4.
Comprehensive Network Security Topology
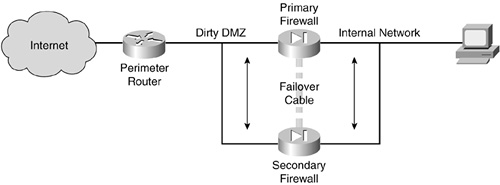
One of the main attributes of a comprehensive topology structure is redundancy. A resiliency that is a fundamental part of the operation is built in so that if anything should occur that would cause a system to fail—for example, poor configuration or physical failure—backup equipment would immediately take over operations. For example, Figure 4-5 illustrates a network redundancy situation, where a primary firewall is backed up by a standby firewall. Known as stateful failover, the job of the standby firewall is to continually check on the status of the primary firewall. The moment the standby firewall notices an issue with the operation of the primary firewall, the standby immediately takes over all functioning from the primary unit.
While the topology of a comprehensive security network could resemble that of a modest topology—with the main difference being equipment redundancy built into the plan—every organization has its own unique set of requirements. The possible list of equipment that could be found on a comprehensive security topology is potentially endless. The list is wholly dependent on the amount of redundancy and resiliency an organization might require.
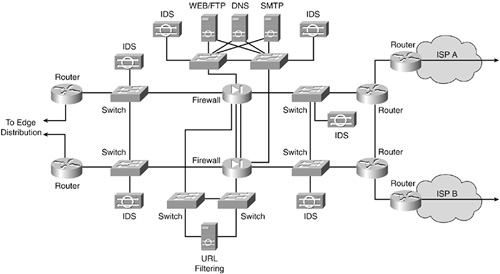
In essence, a comprehensive security topology is the ultimate of alternates. Every relevant appliance and component is backed up, and additional componentry can also be included, as shown in Figure 4-6.
Summary
It is inevitable that threats will continue to exist. Understanding the magnitude of threats, the equipment that is typically targeted, and whether a particular threat is on the decline or the increase can aid organizations in determining the appropriate equipment to install on their networks.
Cisco publishes SAFE blueprints that organizations can use to proactively develop security systems to suit individual requirements. The SAFE blueprints are modular in their approach, allowing organizations to implement corporate-wide security solutions that are highly scalable.
This chapter explored the following topics:
• The issues inherent in threats, targets, and trends
• The equipment that can lower risk exposure
• The various security topologies that organizations can use as effective guides
Every organization is built differently, both in physical characteristics and ability to tolerate risk. The discussion in Chapters 2 and 3 centered on potential attacks and equipment that can help mitigate them. While this chapter provides security topologies and specific modeling that organizations can implement across their networks, it is vital to note that security policy development and enforcement are equal partners in the fight against potential attacks. The security policy development and enforcement topics are discussed throughout the rest of the book, primarily in Chapter 5, "Policy, Personnel, and Equipment as Security Enablers,” Chapter 6, "A Matter of Governance: Taking Security to the Board,” and Chapter 10, "Essential Elements of Security Policy Development.”
Creating an effective business case for network security uses all this information, along with return-on-investment (ROI) modeling that is found in Chapter 9, "Return on Prevention: Investing in Capital Assets,” to develop a proposal that is comprehensive in nature and financially sound in structure.