Chapter 6. The Application and Use of Cryptography
Terms you’ll need to understand:
![]() Symmetric encryption
Symmetric encryption
![]() Asymmetric encryption
Asymmetric encryption
![]() Algorithm
Algorithm
![]() Key
Key
![]() Encrypt
Encrypt
![]() Decrypt
Decrypt
![]() One-time pad
One-time pad
![]() Hashing
Hashing
![]() Message digests
Message digests
![]() Public key infrastructure (PKI)
Public key infrastructure (PKI)
![]() Zero knowledge proof
Zero knowledge proof
![]() Steganography
Steganography
![]() IPSec
IPSec
![]() Link encryption
Link encryption
![]() End-to-end encryption
End-to-end encryption
Topics you’ll need to master:
![]() Identify cryptographic attacks
Identify cryptographic attacks
![]() Describe the advantages and disadvantages of symmetric and asymmetric systems
Describe the advantages and disadvantages of symmetric and asymmetric systems
![]() Define the structure of public key infrastructure
Define the structure of public key infrastructure
![]() Detail the components of IPSec
Detail the components of IPSec
![]() Define the concept of nonrepudiation
Define the concept of nonrepudiation
![]() Know the importance of key security
Know the importance of key security
![]() Be able to define the different modes of DES
Be able to define the different modes of DES
![]() Know the Advanced Encryption Standard (AES)
Know the Advanced Encryption Standard (AES)
![]() Determine the difference between block and stream ciphers
Determine the difference between block and stream ciphers
Introduction
To make things easier, the cryptographic topics covered in the Security Engineering, Asset Security, and Communications and Network Security domains are all in this one chapter. Before you start to sweat at the thought of learning how to create and decipher complex cryptographic systems, just keep in mind that the CISSP exam is a mile wide and an inch deep. CISSP test candidates won’t need to know the complete inner workings of every cryptographic system ever designed.
The exam expects you to understand the application of cryptographic systems, their functions, and their strengths and weaknesses. The CISSP candidate is expected to know basic information about cryptographic systems such as symmetric algorithms, asymmetric algorithms, public key infrastructure, message digests, key management techniques, and alternatives to traditional cryptography, such as steganography.
Test candidates will need to know that cryptography is the science and study of secret writing. Cryptography is concerned with the ways in which information can be encoded or encrypted to prevent disclosure. It is tied closely to three basic pillars of security: integrity, nonrepudiation, and confidentiality. Cryptography offers its users the capability to protect the confidentiality of information in spite of eavesdropping or other interception techniques. Cryptography protects integrity by ensuring that only the individuals who have been authenticated and authorized can access and view the data. Cryptography provides integrity services by detecting the modification to, addition to, or deletion of data while in transit or in storage. Cryptography offers assurance that the true source of information can be determined and that nonrepudiation can be insured.
Cryptographic Basics
Cryptography is the process of transforming data so that it appears to be gibberish, except to those who know the key. Today, cryptographic systems are mandatory to protect email, corporate data, personal information, and electronic transactions.
To have a good understanding of cryptography, you should review how it relates to the foundations of security: privacy, authentication, integrity, and nonrepudiation.
One easy way to remember these foundations is to think of their initials: “PAIN.” Not pain in the physical sense but “PAIN” in the sense of the four primary goals of cryptography: privacy, authentication, integrity, and nonrepudiation.
Confidentiality, or privacy, is the ability to guarantee that private information stays private. Cryptography provides confidentiality by transforming data. This transformation is called encryption. Encryption can protect confidentiality of information in storage or in transit. Just think about the CEO’s laptop. If it is lost or stolen, what is really worth more: the laptop or information regarding next year’s hot new product line? Information assets can be worth much more than the equipment on which they are stored. Hard disk encryption offers an easy way to protect information should equipment be lost, stolen, or accessed by unauthorized individuals.
Authentication has several roles. First, authentication is usually associated with message encryption. Authentication provides a way to ensure that data or programs have not been modified and really come from the source that you believe it to have come from. Authentication is also used to confirm a user’s identity, and is part of the identification and authentication process. The most common implementation of identification and authentication is username and password. Most passwords are encrypted, but they do not have to be. Without encryption, the authentication process is very weak. FTP and Telnet are examples of weak authentication. With these protocols, usernames and passwords are passed in unencrypted or in the clear, and anyone with access to the communication stream can intercept and capture these cleartext passwords. VPNs (virtual private networks) also use authentication, but instead of a cleartext username and password, they normally use digital certificates and digital signatures to more accurately identify the user, and to protect the authentication process from spoofing.
Integrity is the assurance that information remains unaltered from the point it was created until it is received. If you’re selling widgets on the Internet for $100 each, you will likely go broke if a criminal can change the posted price to $1 at checkout. Integrity is critical for the exchange of information, be it engaging in e-commerce, maintaining trade secrets, or supplying accurate military communications.
Nonrepudiation is the capability to verify proof of identity. Nonrepudiation is used to ensure that a sender of data is provided with proof of delivery, and that the recipient is assured of the sender’s identity. Neither party should be able to deny having sent or received the data at a later date. In the days of face-to-face transactions, nonrepudiation was not as hard to prove. Today, the Internet makes many transactions faceless. You might never see the people that you deal with; therefore, nonrepudiation becomes all the more critical. Nonrepudiation is achieved through digital signatures, digital certificates, and message authentication codes (MACs).
To help make this chapter a little easier to digest, review the following basic terms that will be used throughout this chapter:
![]() Plaintext / cleartext—Text that is directly readable.
Plaintext / cleartext—Text that is directly readable.
![]() Encryption—The transformation of cleartext into ciphertext
Encryption—The transformation of cleartext into ciphertext
![]() Ciphertext—Text that has been rendered unreadable by encryption.
Ciphertext—Text that has been rendered unreadable by encryption.
![]() Cryptographic algorithm—A set of mathematical procedures used to encrypt and decrypt data in a cryptographic system. As an example, a simple algorithm like Caesar’s cipher might simply shift characters forward or backward three characters in the alphabet.
Cryptographic algorithm—A set of mathematical procedures used to encrypt and decrypt data in a cryptographic system. As an example, a simple algorithm like Caesar’s cipher might simply shift characters forward or backward three characters in the alphabet.
![]() Cryptographic key—A piece of information, also called a cryptovariable, that controls how a cryptographic algorithm functions. It can be used to control the transformation of plaintext to ciphertext, or ciphertext to plaintext. As an example, an algorithm that shifts characters might use a key of “+3” to shift characters forward by three positions. The word “cat” would be encrypted as “fdw” using this algorithm and key.
Cryptographic key—A piece of information, also called a cryptovariable, that controls how a cryptographic algorithm functions. It can be used to control the transformation of plaintext to ciphertext, or ciphertext to plaintext. As an example, an algorithm that shifts characters might use a key of “+3” to shift characters forward by three positions. The word “cat” would be encrypted as “fdw” using this algorithm and key.
![]() Symmetric cryptography—Cryptography that uses a single key for both encryption and decryption.
Symmetric cryptography—Cryptography that uses a single key for both encryption and decryption.
![]() Asymmetric cryptography—Cryptography that uses a public key for encryption and a separate, private key for decryption. What the public key does, the private key can undo.
Asymmetric cryptography—Cryptography that uses a public key for encryption and a separate, private key for decryption. What the public key does, the private key can undo.
![]() Cryptanalysis—the art and science of breaking a cryptography system or obtaining the plaintext from ciphertext without a cryptographic key. It is used by governments, the military, enterprises, and malicious hackers to find weaknesses and crack cryptographic systems.
Cryptanalysis—the art and science of breaking a cryptography system or obtaining the plaintext from ciphertext without a cryptographic key. It is used by governments, the military, enterprises, and malicious hackers to find weaknesses and crack cryptographic systems.
![]() Message digest or Hash—A fixed-length hex string used to uniquely identify a variable anount of data.
Message digest or Hash—A fixed-length hex string used to uniquely identify a variable anount of data.
![]() Digital signature—A hash value that is encrypted with a sender’s private key. It is used for authentication and integrity.
Digital signature—A hash value that is encrypted with a sender’s private key. It is used for authentication and integrity.
When symmetric encryption is used to convert plaintext into ciphertext, the transformation can be accomplished in two ways:
![]() Block ciphers—Ciphers that separate the message into blocks for encryption and decryption.
Block ciphers—Ciphers that separate the message into blocks for encryption and decryption.
![]() Stream ciphers—Ciphers that divide the message into bits for encryption and decryption.
Stream ciphers—Ciphers that divide the message into bits for encryption and decryption.
History of Encryption
Encryption dates back through the ages. The truth is that as long as there have been people, there have been secrets. One early system that was used by the ancient Greeks and the Spartans is called scytale. This system functioned by wrapping a strip of papyrus around a rod of fixed diameter on which a message was written. The recipient used a rod of the same diameter on which he wrapped the paper to read the message. If anyone intercepted the paper, it appeared as a meaningless letters.
Even Julius Caesar encrypted messages sent between himself and his trusted advisors. Although many might not consider it a robust method of encryption, Caesar’s cipher worked by means of a simple substitution cipher. In Caesar’s cipher, there was a plaintext alphabet and a ciphertext alphabet. The alphabets were arranged as shown in Figure 6.1.
When Caesar was ready to send a message, it was encrypted by moving the text forward according to the key. If the key was 3 characters, for example, then the word “cat” would encrypt to “fdw”. You can try this yourself by referring to Figure 6.1. Just look up each of the message’s letters in the top row and write down the corresponding letter from the bottom row. Caesar’s cipher is also known as a rotation cipher, and a key of three is called ROT3.
Ancient Hebrews used a similar cryptographic system called ATBASH that worked by replacing each letter used with another letter the same distance away from the end of the alphabet; A was sent as a Z, and B was sent as a Y, as illustrated in Figure 6.2.
More complicated substitution ciphers were developed through the Middle Ages as individuals became better at breaking simple encryption systems. In the ninth century, Abu al-Kindi published what is considered to be the first paper that discusses how to break cryptographic systems titled, “A Manuscript on Deciphering Cryptographic Messages.” It deals with using frequency analysis to break cryptographic codes. Frequency analysis is the study of how frequent letters or groups of letters appear in ciphertext. Uncovered patterns can aid individuals in determining patterns and breaking the ciphertext.
As these early ciphers all had weaknesses, people worked to improve them. A polyalphabetic cipher makes use of more than one arrangement of the alphabet. The alphabetic cipher, also known as the Vigenère cipher, uses a single encryption/decryption chart shown here:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
The chart is simply the alphabet written repeatedly for a total of 26 times. Each new line shifts the alphabet by one letter. You need a key to use the Vigenère system. Table 6.1 shows an example of a plaintext, key, and ciphertext using this method of encryption.
How does Vigenère encryption work? Note that the first letter of the plaintext is “C”, and the first letter of the key is “Q”. Compare the natural alphabet to the alphabet arrangement above that begins with “Q”:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
You can see that a plaintext “C” correlates to a ciphertext “S”. Next, encrypt the second plaintext letter, “R”, according to the alphabet that starts with the second letter of the key, “U”:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
Plaintext “R” becomes ciphertext “L”. This process continues until the entire plaintext is encrypted. If the key is shorter than the plaintext (as it usually is), you start at the beginning of the key again.
Note that using a different key with the same algorithm would result in a completely different ciphertext.
The Caesar, ATBASH, and Vigenère ciphers are considered symmetric substitution ciphers that operate by replacing bits, bytes, or characters with alternative bits, bytes, or characters. Substitution ciphers are vulnerable to frequency analysis and are not considered secure.
Substitution ciphers use an encryption method to replace each character or bit of the plaintext message with a different character. The Caesar cipher is a basic example of a substitution cipher. Ciphers can also use transposition, which was the basis of the scytale cipher. Transposition ciphers use algorithms to rearrange the letters of a plaintext message. The result is a ciphertext message. The process of decryption reverses the encryption process to retrieve the original message. The transposition cipher is different in that the letters of the original message remain the same, but their positions are scrambled in an ordered way.
An example of this can be demonstrated in a simple column array transposition. The letters of the message are written in a rectangular array by rows and then read out by columns. Our message is CRYPTO IS MY FAVORITE SUBJECT. The message is written here in a 5 × 5 array as follows:
C R Y P T
O I S M Y
F A V O R
I T E S U
B J E C T
To encrypt the message, each column is processed:
COFIB RIATJ YSVEE PMOSC TYRUT
The result is the ciphertext. Although it appears complex, a transposition cipher can easily be broken given enough time and resources.
Tip
Modern cryptographic systems no longer use simple substitutions or transpositions. However, these substitutions and transpositions are mixed together with other Boolean math operations to create sophisticated algorithms that result in the block and stream ciphers we use today. A block cipher such as Data Encryption Standard (DES) operates on fixed-length groups of bits. A stream cipher inputs and encrypts one bit at a time.
History offers many other examples of systems developed to act as codes and ciphers. One such example is the concealment cipher, which hides the message inside another message. One concealment cipher works by burying the intended message a word at a time inside an innocuous message. The intended message might be found as every third word in a sentence. An example can be seen in the letter received by Sir John Trevanion in the 1600s. Sir John was awaiting execution during the English civil war and was eager to escape his captors. The letter stated:
Worthie Sir John: Hope, that is ye beste comfort of ye afflicted, cannot much, I fear me, help you now. That I would saye to you, is this only: if ever I may be able to requite that I do owe you, stand not upon asking me. ‘Tis not much that I can do: but what I can do, bee ye verie sure I wille. I knowe that, if dethe comes, if ordinary men fear it, it frights not you, accounting it for a high honor, to have such a rewarde of your loyalty. Pray yet that you may be spared this soe bitter, cup. I fear not that you will grudge any sufferings; only if bie submission you can turn them away, ‘tis the part of a wise man. Tell me, an if you can, to do for you anythinge that you wolde have done. The general goes back on Wednesday. Restinge your servant to command. —R.T.
When the message is divided up and every third letter after a punctuation mark is read, it says:
Panel at east end of chapel slides
A somewhat similar technique is a book or running key cipher that uses references to pages, paragraphs, or works in a book. The running key cipher is a form of symmetric substitution cipher in which a text, typically from a book, is used to provide a very long key stream. Usually, the book or text would need to be agreed to ahead of time. These ciphers don’t actually encrypt the message using modern mathematical operations, or even scramble the message with yesterday’s techniques; however, they do hide the message from the unintended recipient. (A variation of this used to be seen in some computer games. To start the game, you had to input a certain word from a specific page of the game’s printed manual. Without the manual, the game could not be started.)
Are any ciphers or codes unbreakable? The only known system unbreakable by brute force is a one-time pad called a Vernam cipher. (Think of a brute force attack as an exhaustive search of all possible keys that could be used in an algorithm, in an attempt to decrypt the message.) The one-time pad was created in 1917 while Gilbert Vernam was investigating methods to potentially improve the polyalphabetic cipher. The one-time pad is a plaintext combined with a random key. This cryptographic system relies on several mechanisms to work correctly. These include:
![]() The message and the key must be stored securely, and the key must be the same length or longer than the message.
The message and the key must be stored securely, and the key must be the same length or longer than the message.
![]() The key can only be used once.
The key can only be used once.
![]() The key must be random.
The key must be random.
![]() The key must be distributed by an out-of-band mechanism. Out-of-band means that communications are outside a previously established method of communication.
The key must be distributed by an out-of-band mechanism. Out-of-band means that communications are outside a previously established method of communication.
Tip
Another cryptographic advancement of the 20th century is the Feistel Network. A German-born cryptographer, Horst Feistel, is the creator of this cryptofunction, and it is the foundation of many symmetric key block ciphers, including DES, 3DES, CAST, and Skipjack. A key feature of the Feistel Network is that it uses the well-known round function.
The early twentieth century was dominated by mechanical encryption devices. Some examples include the German Enigma machine, which used a series of internal rotors to perform the encryption, and the Japanese Purple Machine. Such devices were developed in an attempt to counter the weaknesses of early substitution ciphers. Both systems were eventually broken. Today, the military, government, industry, and individuals use cryptographic systems. Cryptography is used by the movie industry for DVD and Blu-ray encryption, by Pretty Good Privacy (PGP) for email and file security, by Internet Protocol Security (IPSec) for data transfers, and so on.
In the United States, the National Security Agency (NSA) is responsible for cryptology and the creation and breaking of codes. Cryptography continues to advance; today new implementations are being created that are based on light. This is known as quantum cryptography. Quantum cryptography operates by securing optic communications by properties and phenomena of quantum physics.
Steganography
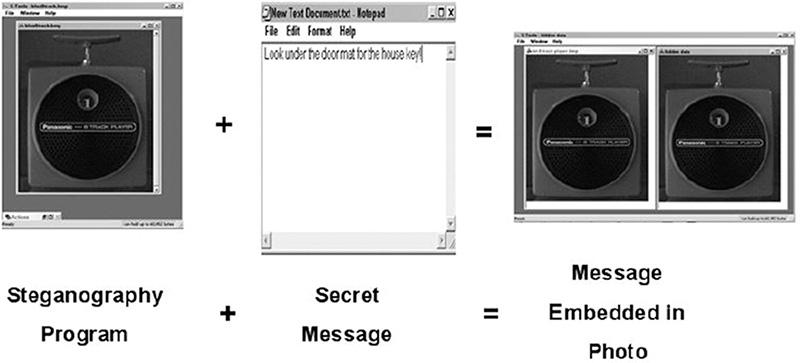
Steganography is an art of secret writing that dates back to the time of ancient Greece; the word derives from the Greek words for “covered” and “writing”. The mechanism of modern steganography is to hide information by embedding it in a carrier file. Steganography took a big leap forward with the invention of computers, which made it possible for many different types of media to be used to hide information. The carrier file can be a graphic, an audio file, a document, or even a video.
Computer graphics such as bitmaps or image files are commonly used. To the viewer of the image, the picture remains the same, but in reality, information has been hidden in it. The hidden information can be plaintext, ciphertext, or other types of data.
Note
Hackers, terrorists, and others use steganography to move information from one location to another without detection. USA Today reported after 9/11 that governmental agencies believed that Al Qaeda operatives used steganography to hide illicit communications.
With steganography, someone could be looking right at some type of covert message and never even realize it! And if the data is encrypted, this dual level of protection vastly increases the security of the hidden object; even if someone discovers the existence of the hidden message, the encryption method to view the contents must be overcome. An example of steganography can be seen in Figure 6.3. I have used an image of one of my prized 8-track players to demonstrate the concept.
Steganography Operation
There are three basic components used in steganography.
![]() The payload—The data or information that is to be hidden and transmitted.
The payload—The data or information that is to be hidden and transmitted.
![]() The carrier or cover—The file or container, such as an image, audio file, document, or video file, that is to contain the hidden payload.
The carrier or cover—The file or container, such as an image, audio file, document, or video file, that is to contain the hidden payload.
![]() The stegomedium—The final file that contains the hidden payload.
The stegomedium—The final file that contains the hidden payload.
To hide information in an image using steganography you will need to alter the image only slightly. Computer-based images are composed of many dots, called pixels. Each pixel has a color encoded as a set of three brightness values: one for red light, one for green, and one for blue. These brightness values can range from a minimum of 0 to a maximum of 255. These values can be altered slightly to hold information in a way that is undetectable to humans.
As an example, let’s say an image has a pixel with brightness values of 38, 74, 130. These correspond to binary values as shown:
To hide the decimal value 7 (binary 111) here, you could simply change the least significant bit of each byte to equal the binary digits 111:

Could a viewer recognize the difference? Most likely not because the actual image file has changed very little. Most monitors offer at least 32-bit color, which equals about four billion color shades. The human eye is not capable of detecting tiny changes from one shade to the next. The size of the payload that can be successfully hidden depends on the size of the carrier.
Steganography in a sound file works in a similar fashion because sound is also represented digitally.
In reality, steganography algorithms can be much more complex, and to further protect the hidden content, you could encrypt the data before encoding it into an image file. Such a technique could be used to make it much harder for a third party to uncover the encrypted data.
Digital Watermark
The most common commercial application of steganography is the use of digital watermark. A digital watermark acts as a type of digital fingerprint and can verify proof of source. It’s a way to identify the copyright owner, the creator of the work, authorized consumers, and so on. Steganography is perfectly suited for this purpose because a digital watermark should be invisible and permanently embedded into digital data for copyright protection. The importance of digital watermarks cannot be overstated because the Internet makes it so easy for someone to steal and reproduce protected assets; violations occur at an alarming rate. Proprietary information is copied, recopied, and duplicated with amazing speed.
Digital watermarks can be used in cases of intellectual property theft to show proof of ownership. Adobe Photoshop actually includes the capability to add a watermark. Its technology is called Digimarc. It is designed to help artists determine whether their art was stolen. Other applications include marking files such as music when they are prereleased. This allows the identification of the individuals that violate their nondisclosure agreements by releasing the work, using peer-to-peer networks, or other unauthorized sources.
For a good example of watermarking, look no further than the Academy Awards. Individuals that vote on movies for the awards are sent high-quality Blu-ray/DVDs as a convenience so that voters can watch the required movies at home before filling out their ballots. In recent years, screeners have been issued with watermarks to track which screeners release films or provide illegal copies to others. www.afterdawn.com/news/archive/8757.cfm.
Algorithms
An algorithm is a set of rules used to encrypt and decrypt data. It’s the set of instructions that will be used with the cryptographic key to encrypt plaintext data. Plaintext data encrypted with different keys or with dissimilar algorithms will produce different ciphertext.
Not all cryptosystems are of the same strength. For example, Caesar might have thought his system of encryption was quite strong, but it would be seen as insecure today. How strong should an encryption be? The strength of a cryptosystem relies on the strength of the algorithm itself because a flawed algorithm can be broken.
But the strength of the encryption also rests on the size and complexity of the key. As an example, imagine that you’re contemplating buying a combination lock. One lock has three digits, whereas the other has four. Which would you choose? Consider that there are 1,000 possible combinations for the three-digit lock, but 10,000 possible combinations for the four-digit lock. As you can see, just a one-digit increase can create a significant difference. The more possible keys or combinations there are, the longer it takes an attacker to guess the right key.
The size of the key, be it four possible numbers, seven possible numbers, or even sixty-four possible numbers, is known as the key space. In the world of cryptography, key spaces are defined by the number of bits. So, a 64-bit key has a key space of 2 to the power of 64, or 18,446,744,073,709,551,616.
Keys must remain secret. You could buy a seven-digit combination lock, but it would do you little good if everyone knew the combination was your phone number.
Note
DES uses a 64-bit key with every 8th bit being a parity bit. With all three keys being different, 3DES (also called Triple-DES) has a key strength of 168 bits and is the last official version.
The final consideration in the choice of a cryptosystem is the value of the data. Highly valued data requires more protection than data that has little value. Therefore, more valuable information needs stronger algorithms, larger keys, and more frequent key exchange to protect against attacks.
Cryptographic systems might make use of a nonce. A nonce is a number generated as randomly as possible and used once. These pseudorandom numbers are different each time one is generated. An initialization vector (IV) is an example of a nonce. An IV can be added to a key and used to force creation of unique ciphertext even when encrypting the same message with the same cipher and the same key.
Modern cryptographic systems use two types of algorithms for encrypting and decrypting data:
![]() Symmetric algorithms use the same key to encrypt and decrypt data.
Symmetric algorithms use the same key to encrypt and decrypt data.
![]() Asymmetric algorithms use different keys, one for encryption and the other for decryption.
Asymmetric algorithms use different keys, one for encryption and the other for decryption.
Before examining each of these in more detail, review Table 6.2, which highlights some of the key advantages and disadvantages of each style of algorithm.
ExamAlert
Make sure you know the differences between symmetric and asymmetric encryption for the exam.
Cipher Types and Methods
Symmetric encryption methods includes block and stream ciphers. Block ciphers operate on blocks or fixed-size chunks of data. The transposition cipher previously discussed is an example of a block cipher. The data was written into a column and then divided into five-character blocks. Most modern encryption algorithms implement some type of block cipher and 64-bit blocks are a commonly used size. Block ciphers are widely used in software products. During the encryption and decryption process, the message is divided into blocks of bits. These blocks are then put through Boolean mathematical functions resulting in the following:
![]() Confusion—Occurs from substitution type operations that create a complicated relationship between the plain text and the key so that an attacker can’t alter the ciphertext to determine the key.
Confusion—Occurs from substitution type operations that create a complicated relationship between the plain text and the key so that an attacker can’t alter the ciphertext to determine the key.
![]() Diffusion—Occurs from transposition type operations that shift pieces of the plain text multiple times. The result is that changes are spread throughout the ciphertext.
Diffusion—Occurs from transposition type operations that shift pieces of the plain text multiple times. The result is that changes are spread throughout the ciphertext.
The substitution box (s-box) performs a series of substitutions, transpositions, and exclusive-or (XOR) operations to obscure the relationship between the plaintext and the ciphertext. When properly implemented, s-boxes are designed to defeat cryptanalysis. An s-box takes a number of input bits (m) and transforms them into some number of output bits (n). S-boxes are implemented as a type of lookup table and used with symmetric encryption systems such as Data Encryption Standard (DES).
A stream cipher encrypts a stream of data one bit at a time. To accomplish this, a one-time pad is created from the encryption engine. This one-time pad is a key-stream, and it is XORed with the plaintext data stream (one bit at a time) to result in ciphertext. Stream ciphers differ from each other in the engine they use to create the one-time pad; the engine receives the symmetric key as input to cause the creation of a unique key stream. The XOR operation is a Boolean math function that says when two bits are combined, if either one or the other is a value of one, a one will result; but if both of the bits are the same, a zero will result. Refer to Table 6.3 for a list of commonly used Boolean operators:
Stream ciphers operate at a higher speed than block ciphers and, in theory, are well suited for hardware implementation.
Symmetric Encryption
In symmetric encryption, a single shared secret key is used for both the encryption and the decryption, as shown in Figure 6.4. The key is referred to as a dual-use key because it is used to lock and unlock data. Symmetric encryption is the oldest form of encryption; scytale and Caesar’s cipher are examples of it. Symmetric encryption provides confidentiality by keeping individuals who do not have the key from knowing the true contents of the message.
The simple diagram in Figure 6.4 shows the symmetric encryption process. Plaintext is encrypted with the single shared key resulting in ciphertext; the ciphertext is then transmitted to the message’s recipient, who reverses the process to decrypt the message. Symmetric encryption and decryption are fast, and symmetric encryption is very hard to break if a large key is used. However, it has three significant disadvantages:
![]() Distribution of the symmetric key
Distribution of the symmetric key
![]() Key management
Key management
![]() Provides only for confidentiality
Provides only for confidentiality
Distribution of the symmetric key is the most serious deficiency with symmetric encryption. For symmetric encryption to be effective, there must be a secure method in which to transfer keys. In our modern world, there needs to be some type of out-of-band transmission. Just think about it: If Bob wants to send Alice a secret message but is afraid that Eavesdropper Eve can monitor their communication, how can he send the message? If the key is sent in cleartext, Eve can intercept it. Bob could deliver the key in person, mail it, or even send a courier. All these methods are highly impractical in our world of e-commerce and electronic communication.
In addition to the problem of key exchange, there is also a key management problem. If, for example, you had 10 people who all needed to communicate with each other in complete confidentiality, you would require 45 keys for them. That’s right, 45 keys! The formula used to calculate the number of keys needed in symmetric encryption is:
N(N–1)/2 = 10(10–1)/2 = 45 keys
Table 6.4 shows how the number of keys climbs as users increase.
The third and final problem with symmetric encryption is that it provides only for confidentiality. The ultimate goal within cryptography is to supply confidentiality, integrity, authenticity, and nonrepudiation.
You might be thinking that I have offered you nothing but bad news about symmetric encryption, but recall, it does have excellent features that make it the perfect choice for providing confidentiality. SP800-131A specifies encryption key lengths. Some examples of symmetric algorithms include:
![]() DES—Data Encryption Standard was once the most commonly used symmetric algorithm. It has been officially retired by NIST. 3DES is still allowed for use while all other DES implementations are no longer allowed.
DES—Data Encryption Standard was once the most commonly used symmetric algorithm. It has been officially retired by NIST. 3DES is still allowed for use while all other DES implementations are no longer allowed.
![]() Blowfish—A general-purpose symmetric algorithm intended as a replacement for DES. Blowfish has a variable block size and a key size of 32 bits up to 448 bits.
Blowfish—A general-purpose symmetric algorithm intended as a replacement for DES. Blowfish has a variable block size and a key size of 32 bits up to 448 bits.
![]() Twofish—A block cipher that operates on 128-bit blocks of data and is capable of using cryptographic keys up to 256 bits in length.
Twofish—A block cipher that operates on 128-bit blocks of data and is capable of using cryptographic keys up to 256 bits in length.
![]() IDEA—International Data Encryption Algorithm is a block cipher that uses a 128-bit key to encrypt 64-bit blocks of plaintext. It is patented, but free for noncommercial use, and is used by PGP.
IDEA—International Data Encryption Algorithm is a block cipher that uses a 128-bit key to encrypt 64-bit blocks of plaintext. It is patented, but free for noncommercial use, and is used by PGP.
![]() Rijndael—This is a block cipher adopted as the Advanced Encryption Standard (AES) by the United States government to replace DES. Although Rijndael supports multiple block sizes, as AES, the block size is fixed at 128 bits. There are three approved key lengths—128, 192, and 256.
Rijndael—This is a block cipher adopted as the Advanced Encryption Standard (AES) by the United States government to replace DES. Although Rijndael supports multiple block sizes, as AES, the block size is fixed at 128 bits. There are three approved key lengths—128, 192, and 256.
![]() RC4—Rivest Cipher 4 is a stream-based cipher. Stream ciphers treat the data as a stream of bits.
RC4—Rivest Cipher 4 is a stream-based cipher. Stream ciphers treat the data as a stream of bits.
![]() RC5—RC5, or Rivest Cipher 5, is a fast block cipher. It is different from other symmetric algorithms in that it supports a variable block size, a variable key size, and a variable number of rounds. Allowable choices for the block size are 32, 64, and 128 bits. The number of rounds can range from 0 to 255 and the key can range up to 2,040 bits.
RC5—RC5, or Rivest Cipher 5, is a fast block cipher. It is different from other symmetric algorithms in that it supports a variable block size, a variable key size, and a variable number of rounds. Allowable choices for the block size are 32, 64, and 128 bits. The number of rounds can range from 0 to 255 and the key can range up to 2,040 bits.
![]() SAFER—Secure and Fast Encryption Routine is a block-based cipher that processes data in blocks of 64 and 128 bits.
SAFER—Secure and Fast Encryption Routine is a block-based cipher that processes data in blocks of 64 and 128 bits.
![]() MARS—A candidate for AES that was developed by IBM. MARS is a block cipher that has a 128-bit block size and a key length between 128 and 448 bits.
MARS—A candidate for AES that was developed by IBM. MARS is a block cipher that has a 128-bit block size and a key length between 128 and 448 bits.
![]() CAST—Carlisle Adams/Stafford Tavares is a 128- or 256-bit block cipher that was a candidate for AES.
CAST—Carlisle Adams/Stafford Tavares is a 128- or 256-bit block cipher that was a candidate for AES.
![]() Skipjack—Promoted by the NSA. Skipjack uses an 80-bit key, supports the same four modes of operation as DES, and operates on 64-bit blocks of text. Skipjack faced public opposition because it was developed so that the government could maintain information enabling legal authorities (with a search warrant or approval of the court) to reconstruct a Skipjack access key and decrypt private communications between affected parties.
Skipjack—Promoted by the NSA. Skipjack uses an 80-bit key, supports the same four modes of operation as DES, and operates on 64-bit blocks of text. Skipjack faced public opposition because it was developed so that the government could maintain information enabling legal authorities (with a search warrant or approval of the court) to reconstruct a Skipjack access key and decrypt private communications between affected parties.
ExamAlert
Be sure to take your time to review the various encryption types, block sizes, and key lengths; you can expect to see these items on the exam. You will be expected to know some of these algorithms that are discussed in detail in the following section. Others may simply be used as distractors on the exam.
To provide authentication from cryptography, you must turn to asymmetric encryption. But, before discussing asymmetric encryption, the sections that follow complete the discussion of DES and a couple of other popular symmetric encryption methods.
Data Encryption Standard
DES grew out of an early 1970s project originally developed by IBM. IBM and NIST modified IBM’s original encryption standard, known as Lucifer, to use a 56-bit key. This revised standard was endorsed by the NSA, named DES, and published in 1977. It was released as an American National Standards Institute (ANSI) standard in 1981.
DES uses a 64-bit block to process 64 bits of plaintext at a time, and outputs 64-bit blocks of ciphertext. As mentioned, DES uses a 64-bit key (with every 8th bit being ignored) and has the following modes of operation:
![]() Electronic Codebook (ECB) mode
Electronic Codebook (ECB) mode
![]() Cipher Block Chaining (CBC) mode
Cipher Block Chaining (CBC) mode
![]() Cipher Feedback (CFB) mode
Cipher Feedback (CFB) mode
![]() Output Feedback (OFB) mode
Output Feedback (OFB) mode
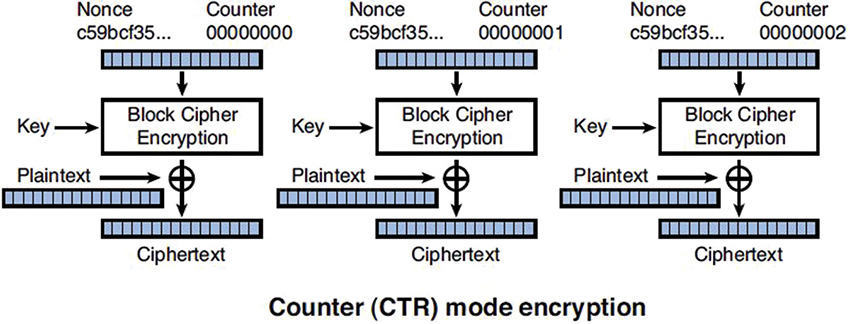
![]() Counter (CTR) mode
Counter (CTR) mode
ExamAlert
These modes of operation can be applied to any symmetric key block cipher, such as DES, 3DES, and AES. You will need to know these for the exam.
The written standard reports the DES key to be 64 bits, but 8 bits are actually used for parity to ensure the integrity of the remaining 56 bits. Therefore, in terms of encryption strength, the key is really only 56 bits long. Each 64-bit plaintext block is separated into two 32-bit blocks, and then processed by this 56-bit key. The processing submits the plaintext to 16 rounds of transpositions and substitutions.
ExamAlert
Keep in mind that while DES operates on 64-bit blocks, the key has an effective length of only 56 bits.
Electronic Codebook Mode
ECB is the native encryption mode of DES. As with all modes, if the last block is not full, padding is added to make the cleartext a full block. Although ECB produces the highest throughput, it is also the easiest form of DES encryption to break. If used with large amounts of data, it can be easily attacked because identical plaintext, when encrypted with the same key, will always produce the same ciphertext. ECB mode is appropriate only when used on small amounts of data. Figure 6.5 illustrates an example of ECB.
Tip
When using ECB, a given block of plaintext encrypted with a given key will always give the same ciphertext. ECB is the weakest form of DES.
Cipher Block Chaining Mode
The CBC mode of DES is widely used and is similar to ECB. CBC processes 64-bit blocks of data but inserts some of the ciphertext created from each block into the next block. This process is called chaining, and is accomplished by using the XOR operation. This mode of DES makes the ciphertext more secure and less susceptible to cracking. CBC mode will experience a slight risk of propagating transmission errors upon reception. Any error experienced will be propagated into the decryption of the subsequent block of receipt. This can make it impossible to decrypt that block and the following blocks as well.
Cipher Feedback Mode
CFB is implemented using a small block size (of one bit to one byte) so that streaming data can be encrypted without waiting for 64 bits to accrue. The resulting effect is that CFB behaves as a stream cipher. It is similar to CBC in that previously generated ciphertext is added to subsequent blocks. And, as with CBC, errors and corruption during transmission can propagate through the decryption process on the receiving side.
Output Feedback Mode
OFB also emulates a stream cipher. Unlike CFB, however, OFB feeds the plaintext of the data stream back into the next block to be encrypted. Therefore, transmission errors do not propagate throughout the decryption process. An initialization vector is used to create the seed value for the first encrypted block. DES XORs the plaintext with a seed value to be applied with subsequent data.
There is a derivative mode of OFB known as counter mode. Counter mode implements DES as a stream cipher and produces a ciphertext that does not repeat for long periods. Figure 6.6 illustrates an example of DES OFB encryption.
Tip
Although DES remained secure for many years, in 1998 the Electronic Frontier Foundation (EFF) was able to crack DES by brute force in about 23 hours. When DES was officially retired, it was recommended that Triple-DES (3DES) be used to ensure security. Triple-DES has since been replaced by AES.
Counter Mode
Counter mode also implements a block cipher into a stream cipher and adds a counter to the process. The counter is a function which produces a sequence which will not repeat for a long time. The counter value gets combined with an initialization vector to produce the input into the symmetric key block cipher. This value is then encrypted through the block cipher using the symmetric key. Counter mode is designed for operation on a multi-processor machine where blocks can be encrypted in parallel, as shown in Figure 6.7.
Triple-DES
Before jumping into the details of Triple-DES, some of you must be wondering why Triple-DES was even invented. DES was adopted with a five-year certification, and needed to be recertified every five years. While initially passing without any problems, DES begin to encounter problems during the 1987 recertification. By 1993, NIST stated that DES was beginning to outlive its usefulness and began looking for candidates to replace it. The new standard was to be referred to as the Advanced Encryption Standard (AES). Why the change? Well, DES had become the victim of increased computing power. Just as Moore’s Law had predicted, the number of transistors per square inch doubled every 18 to 24 months, and so did processing power. The result of this is that an encryption standard that originally required years to brute force was becoming dramatically easier to attack. The final demise of DES came in 1998, when the Electronic Frontier Foundation (EFF) was able to crack DES by brute force in about 23 hours. The actual attack used distributed computing involving over 100,000 computers. Although DES had been resistant to cracking for many years, the EFF project demonstrated the need for stronger algorithms.
Although AES was to be the long-term replacement, the government had not chosen a cipher to put behind the label of AES. Another temporary solution was needed to fill the gap before AES could be deployed. Some thought that Double-DES might be used. After all, Double-DES could have a 112-bit key! However, cryptanalysis proved that Double-DES was no more secure than DES; it requires the same work factor to crack as DES. Double-DES is also susceptible to a meet-in-the-middle attack.
But a geometric increase in performance was provided by using Triple-DES. Therefore, to extend the usefulness of the DES encryption standard, Triple-DES was seen as a stopgap solution. Triple-DES (3DES) can make use of two or three keys to encrypt data, depending on how it is implemented; therefore, it has either an effective key length of 112 bits or 168 bits. Triple-DES performs 48 rounds of transpositions and substitutions. Although it is much more secure, it is approximately three times as slow as 56-bit DES. 3DES can be implemented in several ways:
![]() DES EEE2 uses two keys—The first key is reused during the third round of encryption. The encryption process is performed three times (encrypt, encrypt, encrypt).
DES EEE2 uses two keys—The first key is reused during the third round of encryption. The encryption process is performed three times (encrypt, encrypt, encrypt).
![]() DES EDE2 uses two keys—Again, the first key is reused during the third round of encryption. Unlike DES EEE2, DES EDE2 encrypts, decrypts, and then encrypts.
DES EDE2 uses two keys—Again, the first key is reused during the third round of encryption. Unlike DES EEE2, DES EDE2 encrypts, decrypts, and then encrypts.
![]() DES EEE3 uses three keys and performs the encryption process three times, each time encrypting—Sometimes, you might see the specifics of these ciphers mathematically summarized. For example, when discussing DES-EEE3 using E(K,P), where E refers to the encryption of plaintext P with key K, the process is summarized as E(K3,E(K2,E(K1,P))).
DES EEE3 uses three keys and performs the encryption process three times, each time encrypting—Sometimes, you might see the specifics of these ciphers mathematically summarized. For example, when discussing DES-EEE3 using E(K,P), where E refers to the encryption of plaintext P with key K, the process is summarized as E(K3,E(K2,E(K1,P))).
![]() DES EDE3 uses three keys but operates by encrypting, decrypting, and then encrypting the data—Figure 6.8 illustrates an example of EDE3.
DES EDE3 uses three keys but operates by encrypting, decrypting, and then encrypting the data—Figure 6.8 illustrates an example of EDE3.
Advanced Encryption Standard (AES)
In 2002, NIST decided on the replacement for DES, to be known as AES. Several algorithms were examined. Rijndael (which sounds like “rain doll”) was the chosen algorithm. Its name derives from its two developers: Vincent Rijmen and Joan Daemen. It is considered a fast, simple, robust encryption mechanism. AES is likely the most important symmetric encryption standard today. It is widely used and commonly found in wireless access points and other products. Rijndael is also known to stand up well to various types of attacks. The Rijndael algorithm uses three layers of transformations to encrypt/decrypt blocks of message text:
![]() Linear mix transform
Linear mix transform
![]() Nonlinear transform
Nonlinear transform
![]() Key addition transform
Key addition transform
It also uses a four-step, parallel series of rounds. The steps performed during each round are
![]() Byte sub—Each byte is replaced by an S-box substitution.
Byte sub—Each byte is replaced by an S-box substitution.
![]() Shift row—Bytes are arranged in a rectangular matrix and shifted.
Shift row—Bytes are arranged in a rectangular matrix and shifted.
![]() Mix column—Matrix multiplication is performed based on the arranged rectangle.
Mix column—Matrix multiplication is performed based on the arranged rectangle.
![]() Add round key—Each byte of the state is combined with the round key.
Add round key—Each byte of the state is combined with the round key.
On the last round, the fourth step is bypassed and the first is repeated.
Rijndael is an iterated block cipher, and as developed, it supports variable key and block lengths of 128, 192, or 256 bits. If both key and block size are
![]() 128-bit, there are 10 rounds.
128-bit, there are 10 rounds.
![]() 192-bit, there are 12 rounds.
192-bit, there are 12 rounds.
![]() 256-bit, there are 14 rounds.
256-bit, there are 14 rounds.
As specified in the standard for becoming AES, Rijndael is now fixed in block size of 128 but can still deploy multiple key lengths.
International Data Encryption Algorithm
IDEA is a 64-bit block cipher that uses a 128-bit key. Although it has been patented by a Swiss company, it is freely available for noncommercial use. It is considered a secure encryption standard and there have been no known attacks against it. It operates in four distinct modes similar to DES. At one time, it was thought that IDEA would replace DES, but patent fees prevented that from happening.
Rivest Cipher Algorithms
Rivest cipher is a general term for the family of ciphers all designed by Ron Rivest. These include RC2, RC4, RC5, and RC6. Ron Rivest is one of the creators of RSA. RC1 was never released, and RC3 was broken by cryptanalysis before its release.
RC2 is an early algorithm in the series. It features a variable key-size, 64-bit block cipher that can be used as a drop-in substitute for DES.
RC4 is a fast stream cipher, faster than block mode ciphers, and was widely used. It was especially suitable for low power devices. The 40-bit version is used in Wi-Fi’s Wired Equivalent Privacy (WEP). Although only 40-bit keys (together with a 24-bit IV, creating 64-bit WEP) were specified by the 802.11 standard, many vendors tried to strengthen the encryption by a de facto deployment of a 104-bit key (with the 24-bit IV, making 128-bit WEP).
RC5 is a block-based cipher in which the number of rounds can range from 0 to 255 and the key can range from 0 bits to 2,048 bits. RC6 is similar; it uses a variable key size and key rounds. RC6 added two features (integer multiplication and four 4-bit working registers) not found in RC5.
Asymmetric Encryption
Asymmetric encryption, known as public or private key cryptography, is unlike symmetric encryption in that it uses two unique keys, as shown in Figure 6.9. What one key encrypts requires the other key to decrypt. One of the greatest benefits offered by asymmetric encryption is that it overcomes one of the big barriers of symmetric encryption: key distribution.
FIGURE 6.9 Asymmetric encryption.
Here’s how asymmetric encryptions functions: Imagine that you want to send a client a message. You use your client’s public key to encrypt the message. When your client receives the message, he uses his private key to decrypt it. The important concepts here are that if the message is encrypted with the public key, only the matching private key will decrypt it. The private key, by definition, is generally kept secret, whereas the public key can be given to anyone. If properly designed, it should not be possible for someone to easily deduce a key pair’s private key from the public key.
Cryptographic systems can also make use of zero knowledge proof. This concept allows you to prove your knowledge without revealing the fact to a third party. For example, if someone encrypts with the private key it can be decrypted with the public key. This would permit a perfect check of authenticity. Asymmetric encryption provided the mechanism for accomplishing this concept. It is possible for the holder of a private key to prove they hold that key without ever disclosing the contents to anyone. Dr. W. Diffie and Dr. M. E. Hellman (discussed next) used this concept to permit creation of a trusted session key while communicating across an untrusted communication path. And, presto, key distribution was solved.
Public key cryptography is made possible by the use of one-way functions. A one-way function, known as a trap door, is a mathematical calculation that is easy to compute in one direction, yet next to impossible to compute in the other. Depending on the type of asymmetric encryption used, this calculation involves one of the following:
![]() Manipulating discrete logarithms
Manipulating discrete logarithms
![]() Factoring large composite numbers into their original prime factors
Factoring large composite numbers into their original prime factors
As an example of the trap door function, consider an implementation that uses factoring. If you are given two large prime numbers such as 387 and 283, it is easy to multiply them together and get 109,521. However, if you are given only the product 109,521, it will take a while to find the factors.
As you can see, anyone that knows the trap door can perform the function easily in both directions, but anyone lacking the trap door can perform the function in only one direction. Trap door functions are used in their forward direction when someone is using the public key function; the forward direction is used for encryption, verification of digital signatures, and receipt of symmetric keys. Trap door functions are used in the inverse direction when someone is using the private key function; the inverse direction is used for decryption, generation of digital signatures, and transmission of symmetric keys. Properly implemented, anyone with a private key can generate its public pair, but no one with a public key can easily derive its private pair. We have Dr. W. Diffie and Dr. M. E. Hellman to thank for helping develop public key encryption; they released the first key-exchange protocol in 1976.
Diffie-Hellman
Diffie-Hellman was the first public key-exchange algorithm. It was developed only for key exchange, not for data encryption, or digital signatures. The Diffie-Hellman protocol allows two users to exchange a secret key over an insecure medium without any prior secrets.
Although in-depth knowledge of Diffie-Hellman’s operation is not necessary for the CISSP exam, its operation is classic and worth review for anyone interested in the working of cryptographic systems. Diffie-Hellman has two system parameters: p and g. Both parameters are public and can be used by all the system’s users. Parameter p is a prime number and parameter g, which is usually called a generator, is an integer less than p that has the following property: For every number n between 1 and p–1 inclusive, there is a power k of g such that gk = n mod p. For example, when given the following public parameters:
p = Prime number
g = Generator
These values are used to generate the function y = gx mod p. With this function, Alice and Bob can securely exchange a previously unshared secret (symmetric) key as follows:
Alice can use a private value a, which only she holds, to calculate
ya = ga mod p
Bob can use a private value b, which only he holds, to calculate
yb = gb mod p
Alice can now send ya (as Alice’s nonce, or A-nonce) to Bob, and Bob can send yb (as Bob’s nonce, or B-nonce) to Alice. Again, starting with Alice, she can again use her private value A on the B-nonce. Her result will be (yb)a or
gba mod p
Similarly, with his private value, b, Bob can calculate (ya)b from the received A-nonce:
gab mod p
But guess what: Mathematically, gba mod p and gab mod p are equivalent. So, in fact, Bob and Alice have just, securely, exchanged a new secret key.
Diffie-Hellman is vulnerable to man-in-the-middle attacks because the key exchange does not authenticate the participants. To prove authenticity, digital signatures and digital certificates by accepting someone’s public key in advance, sometimes within a PKI, should be used. Diffie-Hellman is used in conjunction with several authentication methods including the Internet Key Exchange (IKE) component of IPSec. The following list provides some information you should know about Diffie-Hellman:
![]() First asymmetric algorithm
First asymmetric algorithm
![]() Provides key exchange services
Provides key exchange services
![]() Considered a key agreement protocol
Considered a key agreement protocol
![]() Operates by means of discrete logarithms
Operates by means of discrete logarithms
RSA
RSA was developed in 1977 by Ron Rivest, Adi Shamir, and Len Adleman at MIT. The cipher’s name is based on their initials. Although RSA is much slower than symmetric encryption cryptosystems, it offers symmetric key exchange and is considered very secure. RSA is based on factoring prime numbers, but to be secure, has to use prime numbers whose product is much larger that 129 digits. Decimal numbers less than 130 digits have been factored using a number field sieve algorithm. RSA public and private key generation will also not be required knowledge for the CISSP exam.
Typically, the plaintext will be broken into equal-length blocks, each with fewer digits than n, and each block will be encrypted and decrypted. Cryptanalysts or anyone attempting to crack RSA would be left with the difficult challenge of factoring a large integer into its two factors. Cracking the key would require an extraordinary amount of computer processing power and time. RSA supports a key size up to 2,048 bits.
The RSA algorithm has become the de facto standard for industrial-strength encryption, especially since the patent expired in 2000. It has been built into many protocols, firmware, and software products such as Microsoft’s Internet Explorer, Edge, Google Chrome, and Mozilla’s Firefox.
Note
LUC is an alternative to RSA. Although not widely used, it was invented in 1991 and uses Lucas functions.
Note
XTR is a public key cryptosystem developed by Arjen Lenstra and Eric Verheul that is also based on finite fields and discrete logs, and is seen as a generic superset function for all discrete log functions.
El Gamal
El Gamal is an extension of the Diffie-Hellman key exchange. It can be used for digital signatures, key exchange, and encryption. El Gamal consists of three discrete components including a key generator, an encryption algorithm, and a decryption algorithm. It was released in 1985 and its security rests in part on the difficulty of solving the discrete logarithm problems.
Elliptical Curve Cryptosystem
ECC is considered more secure because elliptic curve systems are harder to crack than those based on discrete log problems. Elliptic curves are usually defined over finite fields such as real and rational numbers and implemented analogously to the discrete logarithm problem. An elliptic curve is defined by the following equation:
y2 = x3 + ax + b, along with a single point O, the point at infinity
The space of the elliptic curve has properties where
![]() Addition is the counterpart of modular multiplication.
Addition is the counterpart of modular multiplication.
![]() Multiplication is the counterpart of modular exponentiation.
Multiplication is the counterpart of modular exponentiation.
Thus, given two points, P and R, on an elliptic curve where P = KR, finding K is known as the elliptic curve discrete logarithm problem. ECC is fast. According to RFC 4492, a 163-bit key used in ECC has similar cryptographic strength to a 1,024-bit key used in the RSA algorithm and, as such, is being implemented in smaller, less-powerful devices such as smart phones, tablets, smartcards, and other handheld devices.
Merkle-Hellman Knapsack
Merkle-Hellman Knapsack (Knapsack) is an asymmetric algorithm based on fixed weights. Although this system was popular for a while, it has fallen from favor because it was broken in 1982.
ExamAlert
Before attempting the exam, it is prudent that you know which categories each of the asymmetric algorithms discussed fit into. Take some time to review the differences. The following shows how each functions:
![]() Functions by using a discrete logarithm in a finite field: Diffie-Hellman; El Gamal
Functions by using a discrete logarithm in a finite field: Diffie-Hellman; El Gamal
![]() Functions by the product of large prime numbers: RSA
Functions by the product of large prime numbers: RSA
![]() Functions by means of fixed weights: Merkle-Hellman Knapsack
Functions by means of fixed weights: Merkle-Hellman Knapsack
![]() Functions by means of elliptic curve: Elliptic curve cryptosystem
Functions by means of elliptic curve: Elliptic curve cryptosystem
Review of Symmetric and Asymmetric Cryptographic Systems
To help ensure your success on the CISSP exam, symmetric and asymmetric cryptographic systems are compared in Table 6.5.
Hybrid Encryption
Up to this point, we have discussed symmetric and asymmetric ciphers individually, and as noted in Table 6.2 each has advantages and disadvantages. Although symmetric is fast, key distribution is a problem. Asymmetric offers easy key distribution but is not suited for large amounts of data. Hybrid encryption uses the advantages of each approach and combines them together into a truly powerful system. The public-key cryptosystem is used as a key encapsulation scheme and the private key cryptosystem is used as a data encapsulation scheme.
The system works as follows. If Michael wants to send a message to his editor, Betsy, the following would occur, as illustrated in Figure 6.10.
1. Michael generates a random private key for the data encapsulation scheme. We will call this the session key.
2. Michael encrypts the message with the data encapsulation scheme using the session key that was generated in step 1.
3. Michael encrypts the session key using Betsy’s public key.
4. Michael sends both of these items, the encrypted message and the encrypted key, to Betsy.
5. Betsy uses her private key to decrypt the session key and then uses the session key to decrypt the message.
Nearly all modern cryptosystems work this way because you get the speed of secret key cryptosystems and the “key-exchange-ability” of public key cryptosystems. Hybrid cryptographic systems include IPSec, PGP, SSH, SET, SSL, WPA2-Enterprise, and TLS. Each of these systems will be discussed in detail later in the chapter.
Integrity and Authentication
As mentioned previously, one of the things cryptography offers to its users is the capability to verify integrity and authentication. Integrity assures a recipient that the information remained unchanged and is in its true original form. Authentication provides the capability to ensure that messages are sent from who you believed sent them, and that messages are received by the intended recipient. To help ensure your success on the CISSP exam, review the integrity methods listed in Table 6.6
Hashing and Message Digests
Hashing algorithms function by taking a variable amount of data and compressing it into a fixed length value referred to as a hash value. Hashing provides a fingerprint or message digest of the data. Strong hashing algorithms are hard to break and will not produce the same hash value for two or more messages. Hashing can be used to meet the goals of integrity and/or nonrepudiation depending on how the algorithms are used. Hashes can help verify that information has remained unchanged. Figure 6.11 gives an overview of the hashing process.
Hashing algorithms are not intended to be reversed to reproduce the data. The purpose of the message digest is to verify the integrity of data and messages. In a well-designed message digest if there is even a slight change in an input string the output hash value should change drastically. This is known as the avalanche effect. As an example, Knoppix STD version 0.1 (s-t-d.org/md5.html) has an MD5 hash value of de03204ea5777d0e5fd6eb97b43034cb. This means if you were to download the distribution, or get it from a friend, the file you receive should produce this saved hash value if you recalculate the MD5 hash. Any other value would indicate the file has been altered or corrupted. Programs such as Tripwire, MD5sum, and Windows System File Verification all rely on hashing. Some common hashing algorithms include:
![]() Message DIGEST Algorithm (MD5) series
Message DIGEST Algorithm (MD5) series
![]() Secure Hash Algorithm (SHA) series
Secure Hash Algorithm (SHA) series
![]() HAVAL
HAVAL
![]() RIPEMD
RIPEMD
![]() Whirlpool
Whirlpool
![]() Tiger
Tiger
Note
While there are many hashing algorithms, two of the most common are SHA and the MD series.
The biggest problem for hashing is the possibility of collisions. Collisions result when two or more different inputs create the same output. Collisions can be reduced by moving to an algorithm that produces a larger hash.
Note
When considering hash values, remember that close does not count! If the hashes being compared differ in any way, even by just a single bit, the data being digested is not the same.
MD Series
All of the MD algorithms were developed by Ron Rivest. They have progressed through a series of versions over the years as technology has advanced. The original was MD2, which was optimized for 8-bit computers and is somewhat outdated. It has also fallen out of favor because MD2 has been found to suffer from collisions. MD4 was the next algorithm to be developed. The message is processed in 512-bit blocks plus a 64-bit binary representation of the original length of the message, which is concatenated to the message. As with MD2, MD4 was found to be vulnerable to possible attacks. This is why MD5 was developed; it could be considered as an MD4 with additional safety mechanisms. MD5 processes a variable-size input and produces a fixed 128-bit output. As with MD4, it processes the data in blocks of 512 bits.
Collisions occur when two different messages are passed through a hash and produce the same message digest value. This is undesirable because it can mask the fact that someone might have changed the contents of a file or message. MD5 and SHA-0 have been shown to be vulnerable to forced collisions.
SHA-1/2
SHA-1 is a secure hashing algorithm (SHA) that is similar to MD5. It is considered the successor to MD5 and produces a 160-bit message digest. SHA-1 processes messages in 512-bit blocks and adds padding, if needed, to get the data to add up to the right number of bits. Out of the 160 bits, SHA-1 has only 111-bit effectiveness. SHA-1 is one of a series of SHA algorithms including SHA-0, SHA-1, and SHA-2. SHA-0 is no longer considered secure and SHA-1 is no longer recommended. SHA-2 is actually a family of functions and is a safe replacement for SHA-1. The SHA-2 family includes SHA-224, SHA-256, SHA-386, and SHA-512.
SHA-3
SHA-3 is the newest family of hashing algorithms and was designed to replace SHA-1 and SHA-2.
HAVAL
HAVAL is another one-way hashing algorithm that is similar to MD5. Unlike MD5, HAVAL is not tied to a fixed message-digest value. HAVAL-3-128 makes three passes and produces a 128-bit fingerprint and HAVAL-4-256 makes four passes and produces a 256-bit fingerprint.
Message Authentication Code
A MAC is like a poor man’s version of a digital signature and is somewhat similar to a digital signature except that it uses symmetric encryption. MACs are created and verified with the same secret (symmetric) key. Four types of MACs exist: unconditionally secure, hash function-based, stream cipher-based, and block cipher-based.
HMAC
The Hashed Message Authentication Code (HMAC) was designed to be immune to the multi-collision attack. This immunity was added by including a shared secret key. In simple terms, HMAC functions by using a hashing algorithm such as MD5 or SHA-1 and altering the initial state of the file to be processed by adding a password. Even if someone can intercept and modify the data, it’s of little use if that person does not possess the secret key. There is no easy way for the person to re-create the hashed value without it. For HMACS to be used successfully, the recipient would have to have acquired a copy of the symmetric key through some secure out-of-band mechanism.
CBC-Message Authentication Code
A cipher block chaining MAC uses the CBC mode of a symmetric algorithm such as DES to create a MAC. CBC-MACs differ from HMACs in that CBC-MACs use one algorithm, whereas HMACs use two. These two components include a hashing algorithm and a symmetric block cipher. The last block of the message is used as the MAC authentication portion and is appended to the actual message.
Cipher-Based Message Authentication (CMAC)
CMAC addresses some of the security deficiencies of CBC-MACs. CMACs have more complex logic and use mathematical functions that make use of AES for increased security. You can use a CMAC to verify both the integrity and authenticity of a message.
Digital Signatures
Digital signatures are based on public key cryptography and are used to verify the authenticity and integrity of a message. Digital signatures are created by passing a message’s contents through a hashing algorithm and encrypting it with a sender’s private key once the message is received, the recipient decrypts the encrypted hash and then recalculates the received message’s hash. These values should match to ensure the validity of the message and to prove that the message was sent by the party believed to have sent it (because only that party has access to the private key). Let’s break this process out step by step with an example to help detail the operation:
1. Bill produces a message digest by passing a message through a hashing algorithm.
2. The message digest is then encrypted using Bill’s private key.
3. The message is forwarded to the recipient, Alice.
4. Alice creates a message digest from the message with the same hashing algorithm that Bill used. Alice then decrypts Bill’s signature digest by using his public key.
5. Finally, Alice compares the two message digests, the one originally created by Bill and the other that she created. If the two values match, Alice can rest assured that the message is unaltered.
Figure 6.12 illustrates this process and demonstrates how the hashing function ensures integrity, and the signing of the hash value provides authentication and nonrepudiation.
Digital Signature Algorithm
Things are much easier when we have standards and that is what the DSA was designed for. The DSA standards were proposed by NIST in 1991 to standardize Digital Signature Standards (DSS). The DSA digital signature algorithm involves key generation, signature generation, and signature verification. It uses SHA-1 in conjunction with public key encryption to create a 160-bit hash. Signing speeds are equivalent to RSA signing, but signature verification is much slower. The DSA digital signature is a pair of large numbers represented as binary digits.
Cryptographic System Review
As a recap and to help ensure your success on the CISSP exam, well-known cryptographic systems are reviewed in Table 6.7.
Public Key Infrastructure
Dealing with bricks-and-mortar businesses gives us plenty of opportunity to develop trust with a vendor. We can see the store, talk to the employees, and get a good look at how they do business. Internet transactions are far less transparent. We can’t see who we are dealing with, don’t know what type of operation they really run, and might not be sure we can trust them. The public key infrastructure (PKI) was made to address these concerns and bring trust, integrity, and security to electronic transactions.
PKI is a framework that consists of hardware, software, and policies that exist to manage, create, store, and distribute keys and digital certificates. The components of this framework include the following:
![]() The Certificate Authority (CA)
The Certificate Authority (CA)
![]() The Registration Authority (RA)
The Registration Authority (RA)
![]() The Certificate Revocation List (CRL)
The Certificate Revocation List (CRL)
![]() Digital certificates
Digital certificates
![]() A certificate distribution system
A certificate distribution system
Certificate Authority
A good analogy of a CA is that of the Department of Motor Vehicles (DMV). This is the state entity that is responsible for issuing a driver’s license, the known standard for physical identification. If you cash a check, go to a night club, or catch a plane, your driver’s license is one document that is widely accepted at these locations to prove your identity. CAs are like DMVs: They vouch for your identity in a digital world. VeriSign, Thawte, and Entrust are some of the companies that perform public CA services.
A CA doesn’t have to be an external third party; many companies decide to tackle these responsibilities by themselves. Regardless of who performs the services, the following steps must be performed:
1. The CA verifies the request for certificate with the help of the RA.
2. The individual’s identification is validated.
3. A certificate is created by the CA, which certifies that the person matches the public key that is being offered.
Registration Authority
The RA is like a middleman: it’s positioned between the client and the CA. Although the RA cannot generate a certificate, it can accept requests, verify a person’s identity, and pass along the information to the CA for certificate generation.
RAs play a key role when certificate services expand to cover large geographic areas. One central CA can delegate its responsibilities to regional RAs around the world.
ExamAlert
Expect to see exam questions that deal with the workings of PKI. It’s important to understand that the RA cannot issue certificates.
Certificate Revocation List
Just as with driver’s licenses, digital certificates might not always remain valid. (I had a great aunt that drove with an expired license for years. In her case, she was afraid that at 95 years old, she might not pass the eye exam.) In corporate life, certificates might become invalid because someone leaves the company, information might change, or a private key might become compromised. For these reasons, the CRL must be maintained.
The CRL is maintained by the CA, which signs the list to maintain its accuracy. Whenever problems are reported with digital certificates, they are considered invalid and the CA has the serial number added to the CRL. Anyone requesting a digital certificate can check the CRL to verify the certificate’s integrity. The replacement for CRLs is the Online Certificate Status Protocol (OCSP); it has a client–server design that scales better. When a user requests access to a server, OCSP sends a request for certificate status information. The server sends back a response of current, expired, or unknown. Regardless of which method is used, problems with certificates are nothing new; Dell had such a problem in 2015. You can read more about it at www.infoworld.com/article/3008422/security/what-you-need-to-know-about-dells-root-certificate-security-debacle.html.
Digital Certificates
Digital certificates are at the heart of the PKI system. A digital certificate serves two roles:
![]() It ensures the integrity of the public key and makes sure that the key remains unchanged and in a valid state.
It ensures the integrity of the public key and makes sure that the key remains unchanged and in a valid state.
![]() It validates that the public key is tied to the stated owner and that all associated information is true and correct.
It validates that the public key is tied to the stated owner and that all associated information is true and correct.
The information needed to accomplish these goals is added into the digital certificate. Digital certificates are formatted to the X.509 standard. The most current version of X.509 is version 3. One of the key developments in version 3 was the addition of extensions. Version 3 includes the flexibility to support other topologies. It can operate as a web of trust much like PGP. An X.509 certificate includes the following elements, and examples showing some of these elements are displayed in Figure 6.13:
![]() Version
Version
![]() Serial number
Serial number
![]() Algorithm ID
Algorithm ID
![]() Issuer
Issuer
![]() Validity
Validity
![]() Not Before (a specified date)
Not Before (a specified date)
![]() Not After (a specified date)
Not After (a specified date)
![]() Subject public key information
Subject public key information
![]() Public key algorithm
Public key algorithm
![]() Subject public key
Subject public key
![]() Issuer-unique identifier (optional)
Issuer-unique identifier (optional)
![]() Subject-unique identifier (optional)
Subject-unique identifier (optional)
![]() Extensions (optional)
Extensions (optional)
Digital certificates play a vital role in the chain of trust. Public key encryption works well when we are dealing with people we know because it’s easy for us to send each other a public key. But what about communicating with people we don’t know?
Note
Digital certificates are used to prove your identity when performing electronic transactions.
Although you might want to use an external certificate authority, it is not mandatory. You could decide to have your own organization act as a certificate authority. Regardless of whether you have a third party handle certificate duties or you perform them yourself, digital certificates will typically contain the following critical pieces of information:
![]() Identification information that includes username, serial number, and validity dates of the certificates.
Identification information that includes username, serial number, and validity dates of the certificates.
![]() The public key of the certificate holder.
The public key of the certificate holder.
![]() The digital signature of the signature authority. This piece is critical because it certifies and validates the integrity of the entire package.
The digital signature of the signature authority. This piece is critical because it certifies and validates the integrity of the entire package.
The Client’s Role in PKI
It might seem that up to this point, all the work falls on the shoulders of the CAs; this is not entirely true. Clients are responsible for requesting digital certificates and for maintaining the security of their private keys. Loss or compromise of the private key would be devastating; it would mean that communications were no longer be secure. If you are dealing with credit card numbers or other pieces of user identity, this type of loss of security could lead to identity theft.
Protecting the private key is an important issue because it’s easier for an attacker to target the key than to try to crack the certificate service. Organizations should concern themselves with seven key management issues:
![]() Generation
Generation
![]() Distribution
Distribution
![]() Installation
Installation
![]() Storage
Storage
![]() Key control
Key control
![]() Key disposal
Key disposal
Key recovery and control is an important issue that must be addressed. One basic recovery and control method is the M of N Control method of access. This method is designed to ensure that no one person can have total control and is closely related to dual control. Therefore, if N number of administrators have the ability to perform a process, M number of those administrators must authenticate for access to occur. M of N Control should require physical presence for access. Here is an example: Suppose that a typical M of N Control method requires that four people have access to the archive server and at least two of them must be present to accomplish access. In this situation, M = 2 and N = 4. This would ensure that no one person could compromise the security system or gain access.
Note
Many organizations use Hardware Security Modules (HSM) to securely store and securely retrieve these escrowed keys. These HSM systems protect keys and can detect and prevent tampering by destroying the key material if unauthorized access is detected.
Email Protection Mechanisms
Secure email solutions are important because email is one of the most widely used Internet applications. Email is susceptible to several threats including spoofing, spamming, forging, and so on. Standard email uses the Simple Mail Transfer Protocol (SMTP) TCP port 25 to accept messages from clients, and Internet Message Access Protocol (IMAP4) TCP port 143 or Post Office Protocol (POP3) version 3 TCP port 110 to retrieve email from server-based inboxes. Sending an email is much like sending a postcard through the postal service: Anyone along the way can easily read the note you wrote to your mom while visiting Niagara Falls. Fortunately, several digital services enable you to seal your mail in an envelope. Several applications and protocols are available to help secure email.
Pretty Good Privacy
PGP was developed in 1991 by Phil Zimmermann to provide privacy and authentication. Over time, it evolved into an open standard known as OpenPGP, but now can be purchased for enterprise use by Symantec’s for endpoint, file and folder and email encryption as well. PGP is unlike PKI in that there is no CA. PGP builds a web of trust that develops as users sign and issue their own keys. Users must determine what level of trust they are willing to place in other parties. The goal of PGP was for it to become the “everyman’s encryption.” No longer would encryption be available only to companies and corporations. Popular programs and providers such as Hushmail and Veridis are based on PGP.
Other Email Security Applications
PGP is not the only game in town for those looking to secure email. Other options include S/MIME, PEM, MSP, and MOSS. Each is discussed now.
![]() Secure Multipurpose Internet Mail Extensions (S/MIME)—By default, MIME does not provide any protection. To overcome this problem, S/MIME was developed by RSA. S/MIME has been built into virtually every email system to encrypt and digitally sign the attachments of protected email messages. S/MIME adds two valuable components to standard email: digital signatures and public key encryption. S/MIME supports X.509 digital certificates and RSA encryption.
Secure Multipurpose Internet Mail Extensions (S/MIME)—By default, MIME does not provide any protection. To overcome this problem, S/MIME was developed by RSA. S/MIME has been built into virtually every email system to encrypt and digitally sign the attachments of protected email messages. S/MIME adds two valuable components to standard email: digital signatures and public key encryption. S/MIME supports X.509 digital certificates and RSA encryption.
![]() Privacy Enhanced Mail (PEM)—PEM is an older standard that has not been widely implemented but was developed to provide authentication and confidentiality. PEM public key management is hierarchical. PEM uses MD2/MD5 and RSA for integrity and authentication.
Privacy Enhanced Mail (PEM)—PEM is an older standard that has not been widely implemented but was developed to provide authentication and confidentiality. PEM public key management is hierarchical. PEM uses MD2/MD5 and RSA for integrity and authentication.
![]() Message Security Protocol (MSP)—MSP is the military’s answer to PEM. Because it was developed by the NSA, it has not been open to public scrutiny and is not widely used. It is part of the DoD’s Defense Messaging System and provides authentication, integrity, and nonrepudiation. The military has its own security network referred to as SIPERNET.
Message Security Protocol (MSP)—MSP is the military’s answer to PEM. Because it was developed by the NSA, it has not been open to public scrutiny and is not widely used. It is part of the DoD’s Defense Messaging System and provides authentication, integrity, and nonrepudiation. The military has its own security network referred to as SIPERNET.
![]() MIME Object Security Services (MOSS)—MOSS extended the functionality of PEM and is not widely used. MOSS was eclipsed by S/MIME and by PGP. MOSS is the only email standard that gives users an out-of-the-box mechanism for signing the recipient-list.
MIME Object Security Services (MOSS)—MOSS extended the functionality of PEM and is not widely used. MOSS was eclipsed by S/MIME and by PGP. MOSS is the only email standard that gives users an out-of-the-box mechanism for signing the recipient-list.
Securing TCP/IP with Cryptographic Solutions
Did you ever really consider that security is like a cake? Although it might not taste as good as a cake, it is best to have the option of security in all the layers. Cryptography can be layered to help build a true defense in depth. This is not to say that cryptographic controls should be applied at every layer, just that defense in depth should be the target. Just as too much cake might not be good for you, too many layers of cryptography will slow down a system or process. Users might look for ways to bypass some of these controls. Many types of cryptographic solutions are available from the application layer all the way down to the physical frame. Your job as a CISSP is to understand these potential solutions and be able to determine which should be used to meet the goals of the organization.
Because security wasn’t one of the driving forces when the TCP/IP protocols were developed, the cryptographic solutions discussed here can go a long way toward protecting the security of an organization. Although in reality encryption at any layer is accomplished on the payload of the next higher layer, most CISSP questions will focus on basic knowledge of encryption processes and the layer at which they are found. Figure 6.14 shows some common cryptographic solutions and their corresponding layers. Chapter 7, “Communications and Network Security,” discusses many of these protocols in greater depth. Let’s start at the top of the stack and work down through the layers.
Application/Process Layer Controls
The following application-layer protocols can be used to add confidentiality, integrity, or nonrepudiation:
![]() Secure Shell (SSH)—SSH is an Internet application that provides secure remote access. It is considered a replacement for FTP, Telnet, and the Berkley “r” utilities. SSH defaults to TCP port 22. SSH version 1 has been found to contain vulnerabilities, so it is advisable to use SSH V2.
Secure Shell (SSH)—SSH is an Internet application that provides secure remote access. It is considered a replacement for FTP, Telnet, and the Berkley “r” utilities. SSH defaults to TCP port 22. SSH version 1 has been found to contain vulnerabilities, so it is advisable to use SSH V2.
![]() Secure FTP (SFTP)—SFTP uses an SSH connection, and then tunnels the FTP protocol through the secure shell. The latest version of SSH is v2.0 and typically runs on TCP port 22. The FTP client software must support the SFTP protocol.
Secure FTP (SFTP)—SFTP uses an SSH connection, and then tunnels the FTP protocol through the secure shell. The latest version of SSH is v2.0 and typically runs on TCP port 22. The FTP client software must support the SFTP protocol.
![]() FTP Secure (FTPS)—FTPS establishes an SSL secure channel, and then runs the FTP session through SSL. IANA assigned ports 989 (data) and 990 (control) for FTPS, but vendors are free to use custom port numbers and often do.
FTP Secure (FTPS)—FTPS establishes an SSL secure channel, and then runs the FTP session through SSL. IANA assigned ports 989 (data) and 990 (control) for FTPS, but vendors are free to use custom port numbers and often do.
![]() Secure Hypertext Transfer Protocol (S-HTTP)—S-HTTP is a superset of HTTP that was developed to provide secure communication with a web server. S-HTTP is a connectionless protocol designed to send individual messages securely.
Secure Hypertext Transfer Protocol (S-HTTP)—S-HTTP is a superset of HTTP that was developed to provide secure communication with a web server. S-HTTP is a connectionless protocol designed to send individual messages securely.
![]() Secure Electronic Transaction (SET)—Visa and MasterCard wanted to alleviate fears of using credit cards over the Internet, so they developed SET. This specification uses a combination of digital certificates and digital signatures among the buyer, merchant, and the bank so that privacy and confidentiality are ensured. While this sounds like a great idea, one of the problems with SET was that the banks wanted to charge for this service, and required hardware and software changes. Many vendors fought these fees and so SET is not widely used. Out of the ashes of SET came the Payment Card Industry Data Security Standard (PCI-DSS). This requires all vendors who accept credit cards to meet and guarantee specific information system security standards designed to protect the credit card data.
Secure Electronic Transaction (SET)—Visa and MasterCard wanted to alleviate fears of using credit cards over the Internet, so they developed SET. This specification uses a combination of digital certificates and digital signatures among the buyer, merchant, and the bank so that privacy and confidentiality are ensured. While this sounds like a great idea, one of the problems with SET was that the banks wanted to charge for this service, and required hardware and software changes. Many vendors fought these fees and so SET is not widely used. Out of the ashes of SET came the Payment Card Industry Data Security Standard (PCI-DSS). This requires all vendors who accept credit cards to meet and guarantee specific information system security standards designed to protect the credit card data.
Host to Host Layer Controls
The host to host layer of the TCP/IP stack can also be used to add cryptographic solutions to data communications. Some common examples follow:
![]() Secure Sockets Layer (SSL)—SSL was developed by Netscape for transmitting private documents over the Internet. Unlike S-HTTP, SSL is application-independent. One of the advantages of SSL is its cryptographic independence. The protocol itself is merely a framework for communicating certificates, encrypted keys, and data. The most current version of SSL is SSLv3, which provides for mutual authentication and compression. Figure 6.15 illustrates the transactions in an SSL session. As of 2014 SSLv3 is considered insecure and is vulnerable to the POODLE exploit. If attackers successfully exploit this vulnerability, they only need to make about 256 SSL 3.0 requests to break the encryption. TLS 1.2 is the current standard for HTTP encryption.
Secure Sockets Layer (SSL)—SSL was developed by Netscape for transmitting private documents over the Internet. Unlike S-HTTP, SSL is application-independent. One of the advantages of SSL is its cryptographic independence. The protocol itself is merely a framework for communicating certificates, encrypted keys, and data. The most current version of SSL is SSLv3, which provides for mutual authentication and compression. Figure 6.15 illustrates the transactions in an SSL session. As of 2014 SSLv3 is considered insecure and is vulnerable to the POODLE exploit. If attackers successfully exploit this vulnerability, they only need to make about 256 SSL 3.0 requests to break the encryption. TLS 1.2 is the current standard for HTTP encryption.
![]() Transport Layer Security (TLS)—TLS encrypts the communication between a host and a client. TLS typically makes use of an X.509 digital certificate for server authentication. This mechanism provides strong authentication of the server to the client, so the client can trust that it is connected to the correct remote system. TLS consists of two layers: the TLS Record Protocol and the TLS Handshake Protocol. One of the most common implementations of TLS is HTTPS, which is simply HTTP over TLS.
Transport Layer Security (TLS)—TLS encrypts the communication between a host and a client. TLS typically makes use of an X.509 digital certificate for server authentication. This mechanism provides strong authentication of the server to the client, so the client can trust that it is connected to the correct remote system. TLS consists of two layers: the TLS Record Protocol and the TLS Handshake Protocol. One of the most common implementations of TLS is HTTPS, which is simply HTTP over TLS.
![]() Secure Socket Tunneling Protocol (SSTP)—SSTP is a form of VPN tunnel that was released in 2008 and provides a mechanism to transport PPP or L2TP traffic through an SSL 3.0 connection. SSTP requires a digital certificate on the server side and establishes an SSL tunnel that encrypts all traffic over TCP port 443. Because it uses the same port used by HTTPS, this facilitates its use through corporate firewalls.
Secure Socket Tunneling Protocol (SSTP)—SSTP is a form of VPN tunnel that was released in 2008 and provides a mechanism to transport PPP or L2TP traffic through an SSL 3.0 connection. SSTP requires a digital certificate on the server side and establishes an SSL tunnel that encrypts all traffic over TCP port 443. Because it uses the same port used by HTTPS, this facilitates its use through corporate firewalls.
![]() Wireless Transport Layer Security (WTLS)—WTLS is a security protocol developed for cellular technology. In an attempt to minimize upper-layer support code, the cellular industry developed its own Wireless Access Protocol (WAP) stack. WTLS encrypts the communication between the cellular wireless client and the ISP tower that the cell phone is connecting to. At the tower, the WTLS packet is decrypted, then re-encrypted with standard TLS and routed on to the Internet. This means that for a moment, customer data exists unencrypted. This is a security vulnerability that has become known as the gap in WAP. The cellular industry has since released WAPv2, which incorporates industry standard TLS (minimized as possible), so that decryption is no longer necessary.
Wireless Transport Layer Security (WTLS)—WTLS is a security protocol developed for cellular technology. In an attempt to minimize upper-layer support code, the cellular industry developed its own Wireless Access Protocol (WAP) stack. WTLS encrypts the communication between the cellular wireless client and the ISP tower that the cell phone is connecting to. At the tower, the WTLS packet is decrypted, then re-encrypted with standard TLS and routed on to the Internet. This means that for a moment, customer data exists unencrypted. This is a security vulnerability that has become known as the gap in WAP. The cellular industry has since released WAPv2, which incorporates industry standard TLS (minimized as possible), so that decryption is no longer necessary.
Internet Layer Controls
Internet Protocol Security (IPSec) resides at the Internet layer and is a well-known cryptographic solution. IPSec is an end-to-end security technology that allows two devices to communicate securely. IPSec was developed to address the shortcomings of IPv4. Although it is an add-on for IPv4, it was created for, and is built into, IPv6. IPSec can be used to protect just the data or the data and the original IP header. This level of protection can be for integrity and/or encryption. The components of IPSec include:
![]() Encapsulated secure payload (ESP)—ESP provides confidentiality by encrypting the data packet. The encrypted data is hidden from prying eyes, so its confidentiality is ensured.
Encapsulated secure payload (ESP)—ESP provides confidentiality by encrypting the data packet. The encrypted data is hidden from prying eyes, so its confidentiality is ensured.
![]() Authentication header (AH)—The AH provides integrity and authentication. The AH uses a hashing algorithm and symmetric key to calculate a message authentication code. This message-authentication code is known as the integrity check value (ICV). When the AH is received, an ICV value is calculated and checked against the received value to verify integrity.
Authentication header (AH)—The AH provides integrity and authentication. The AH uses a hashing algorithm and symmetric key to calculate a message authentication code. This message-authentication code is known as the integrity check value (ICV). When the AH is received, an ICV value is calculated and checked against the received value to verify integrity.
![]() Security Association (SA)—For AH and ESP to work, there must be some negotiations regarding the rules of conduct for exchanging information between the client and server. These negotiations include the type of symmetric and asymmetric algorithms that will be used, as well as state-specific information in support of the secure channel. The results of these negotiations are stored in an SA. The SA identifies the details of each one-way connection. Two-way communication channels will have two SAs; each distinguished by its Security Parameter Index (SPI). If both AH and ESP are used, four SAs are required. IPSec uses a symmetric shared key to encrypt bulk communications. The Diffie-Hellman algorithm is used to generate this shared key.
Security Association (SA)—For AH and ESP to work, there must be some negotiations regarding the rules of conduct for exchanging information between the client and server. These negotiations include the type of symmetric and asymmetric algorithms that will be used, as well as state-specific information in support of the secure channel. The results of these negotiations are stored in an SA. The SA identifies the details of each one-way connection. Two-way communication channels will have two SAs; each distinguished by its Security Parameter Index (SPI). If both AH and ESP are used, four SAs are required. IPSec uses a symmetric shared key to encrypt bulk communications. The Diffie-Hellman algorithm is used to generate this shared key.
![]() IPSec Internet Key Exchange (IKE)—IPSec must have a procedure to exchange key information between clients, and the Internet Key Exchange (IKE) is the default standard. IKE is responsible for creating IPSec’s SA and is considered a hybrid protocol because it combines the functions of two other protocols: the Internet Association and Key Management Protocol (ISAKMP) and the OAKLEY protocol.
IPSec Internet Key Exchange (IKE)—IPSec must have a procedure to exchange key information between clients, and the Internet Key Exchange (IKE) is the default standard. IKE is responsible for creating IPSec’s SA and is considered a hybrid protocol because it combines the functions of two other protocols: the Internet Association and Key Management Protocol (ISAKMP) and the OAKLEY protocol.
![]() The Internet Association and Key Management Protocol (ISAKMP)—This subset of IKE sets up the framework for performing the negotiations during the client/server handshake process. This could include items such as algorithm types and key sizes.
The Internet Association and Key Management Protocol (ISAKMP)—This subset of IKE sets up the framework for performing the negotiations during the client/server handshake process. This could include items such as algorithm types and key sizes.
![]() OAKLEY Protocol—This portion of the IKE is responsible for carrying out the negotiations. This protocol is like the errand guy!
OAKLEY Protocol—This portion of the IKE is responsible for carrying out the negotiations. This protocol is like the errand guy!
![]() Transport and tunnel modes—AH and ESP can work in one of two modes: transport mode or tunnel mode. These modes define how the encryption or integrity functions will be applied to the data stream. Transport mode encrypts the payload received from the host-to-host layer. Tunnel mode encapsulates the payload received from the host-to-host layer and the original IP header that was to encapsulate that payload. A new IPv4 header is added for routing between the tunnel endpoints. Tunnel mode is designed to be used by VPNs.
Transport and tunnel modes—AH and ESP can work in one of two modes: transport mode or tunnel mode. These modes define how the encryption or integrity functions will be applied to the data stream. Transport mode encrypts the payload received from the host-to-host layer. Tunnel mode encapsulates the payload received from the host-to-host layer and the original IP header that was to encapsulate that payload. A new IPv4 header is added for routing between the tunnel endpoints. Tunnel mode is designed to be used by VPNs.
Other lesser-known cryptographic solutions found at the Internet layer include:
![]() Simple Key Management for Internet Protocol (SKIP)—SKIP was developed by the IETF. SKIP is rarely used and requires no prior communication; it is similar to SSL. SKIP was evaluated as a key exchange mechanism for IPsec before the adoption of IKE in 1998.
Simple Key Management for Internet Protocol (SKIP)—SKIP was developed by the IETF. SKIP is rarely used and requires no prior communication; it is similar to SSL. SKIP was evaluated as a key exchange mechanism for IPsec before the adoption of IKE in 1998.
![]() Software IP Encryption (SwIPe)—SwIPe was an early attempt to develop an open standard for VPNs. Although freely available, it was available only for SunOS and is not widely used.
Software IP Encryption (SwIPe)—SwIPe was an early attempt to develop an open standard for VPNs. Although freely available, it was available only for SunOS and is not widely used.
Network Access Layer Controls
At the TCP/IP network access layer or OSI Layer 2, we find several cryptographic solutions:
![]() Point-to-Point Tunneling Protocol (PPTP)—PPTP was developed by a group of vendors. It consists of two components: the transport, which maintains the virtual connection, and the encryption, which ensures confidentiality. It can operate at a 40-bit or 128-bit key length.
Point-to-Point Tunneling Protocol (PPTP)—PPTP was developed by a group of vendors. It consists of two components: the transport, which maintains the virtual connection, and the encryption, which ensures confidentiality. It can operate at a 40-bit or 128-bit key length.
![]() Layer 2 Tunneling Protocol (L2TP)—L2TP was created by Cisco and Microsoft to replace L2F and PPTP. L2TP merged the capabilities of both L2F and PPTP into one tunneling protocol. By itself, it provides no encryption; but it is deployed with IPSec as a VPN solution.
Layer 2 Tunneling Protocol (L2TP)—L2TP was created by Cisco and Microsoft to replace L2F and PPTP. L2TP merged the capabilities of both L2F and PPTP into one tunneling protocol. By itself, it provides no encryption; but it is deployed with IPSec as a VPN solution.
Note
L2F does not provide encryption or confidentiality by itself; it relies on the protocol being tunneled to provide privacy
![]() WPA2-Enterprise—This is a Wi-Fi Alliance certification that identifies equipment capable of establishing a secure channel of communication at TCP/IP layer 1 / OSI Layer 2 using EAP for authentication, and AES-CTR-CBC-MAC for encryption. Cisco LEAP can be used with WPA and WPA2 networks.
WPA2-Enterprise—This is a Wi-Fi Alliance certification that identifies equipment capable of establishing a secure channel of communication at TCP/IP layer 1 / OSI Layer 2 using EAP for authentication, and AES-CTR-CBC-MAC for encryption. Cisco LEAP can be used with WPA and WPA2 networks.
Note
Extensible Authentication Protocol (EAP) is an authentication protocol that is widely used in point-to-point and wireless connections. It is discussed in detail in Chapter 7, “Communications and Network Security.”
Link and End-to-End Encryption
As the various protocols have shown, there are many ways to encrypt and secure data. One final decision that must be considered is how information is to be moved between clients. In reality, encryption can happen at any one of many different layers. The question the CISSP must ask is, what is actually getting encrypted? The layer you choose to encrypt at forces encryption of all layers above your chosen layer.
End-to-end encryption encrypts the message and the data packet. Header information, IP addresses, and routing data are left in cleartext. Although this means that a malicious individual can intercept packets and learn the source and target destination, the data itself is secure. The advantage of this type of encryption is speed. No time or processing power is needed to decode address information at any intermediate points. The disadvantage is that even with the data encrypted, an attacker might be able to make an inference attack.
Sending information by means of end-to-end encryption prevents the attacker from sniffing host-to-host or application data, but it does not mean the attacker cannot understand something about the actual communication. This is known as inference.
Inference can occur any time an attacker notices a change in activity at a client. As an example, some news agencies allegedly monitor the White House for pizza deliveries. The belief is that a spike in pizza deliveries indicates that officials are working overtime and that there is a pending event of importance. A similar spike in encrypted email traffic could allow similar inferences.
Traffic padding can be used to defeat an inference attack. As an example, a military agency could have a connection between the United States and Afghanistan. Although third parties might be able to see that traffic is flowing, the amount transmitted stays at a constant flow and thereby prevents attackers from performing an inference attack.
Your choice for encryption at the physical layer is link-to-link encryption. Link-to-link encryption encrypts all the data sent from a specific communication device to another specific device. This includes the headers, addresses, and routing information. Its primary strength is that it provides added protection against sniffers and eavesdropping. Its disadvantage is that all intermediate devices must have the necessary keys, software, and algorithms to encrypt and decrypt the encrypted packets at each hop along the trip. This adds complexity, consumes time, and requires additional processing power.
Cryptographic Attacks
Attacks on cryptographic systems are nothing new. Whenever someone has information to hide, there is usually someone who would like to reveal it. The name for such activities is cryptanalysis. Cryptanalysis is the study of analyzing cryptography and can best be defined by the root meaning of the word, crypt = secret, hidden and analysis = loosen, dissolve. The ultimate goal of cryptanalysis is to determine the key value, and these types of activities go on every day at organizations like the NSA and at locations where hackers and security specialists are working. Depending on which key is cracked, an attacker could gain access to confidential information or pretend to be someone else and attempt some sort of masquerade attack.
Because cryptography can be such a powerful tool and the ability to break many algorithms is limited, the Coordinating Committee for Multilateral Export Controls (CoCOM) was established to deal with the control of cryptographic systems. CoCOM ended in 1994 and was replaced by the Wassenaar Arrangement on Export Controls for Conventional Arms and Dual-Use Goods and Technologies. The Wassenaar Arrangement had wide support; that more than 30 countries have come together to control the export of cryptography.
One issue to consider before launching a cryptographic attack is what is known about the algorithm. Is it public or private? Auguste Kerckhoff is credited with creating, in the nineteenth century, Kerckhoff’s Principle, which states that a cryptographic system should not require secrecy. Everything should be public except the key. An example of this debate can be seen in the development and crack of Content Scrambling System (CSS). This method of encryption was developed by the DVD Copy Control Association (DVD CCA). Because the algorithm was proprietary, it was not made public. CSS was designed to allow only authorized DVD players to decode scrambled content stored on the original DVD discs. This was until Jon Lech Johansen and others got together and cracked CSS, posting a utility called DeCSS to the Internet in late October 1999. So, whereas some argue that algorithms should be secret, others continue to believe that open standards and systems allow for more robust, secure systems.
When attempting a cryptographic attack, the work factor is something that must be considered. The work factor can be measured as the time and effort needed to perform a brute-force attack against an encryption system. As an example, the CSS algorithm reduced the effective key length to only around 16 bits. This small key size meant the work factor was low and that CSS could be brute-forced by a 1GHz processor in less than a minute. An example of a distributed cryptographic attack can be seen with www.distributed.net. The program functions by downloading a client utility. Anyone can join in as long as they do not mind sharing some of the local system’s CPU cycles. This project was started in 1997 and, on July 14, 2002, was able to crack the RSA Labs 64-bit secret-key for one message.
With the basic concepts of cryptanalysis completed, let’s review some common attacks that might target a cryptographic system:
![]() Known plaintext attack—This attack requires the attacker to have the plaintext and ciphertext of one or more messages. Encrypted file archives such as ZIP are prone to this attack.
Known plaintext attack—This attack requires the attacker to have the plaintext and ciphertext of one or more messages. Encrypted file archives such as ZIP are prone to this attack.
![]() Ciphertext-only attack—This attack requires the attacker to obtain several encrypted messages that have been encrypted using the same encryption algorithm. The attacker does not have the associated plaintext; he attempts to crack the code by looking for patterns and using statistical analysis.
Ciphertext-only attack—This attack requires the attacker to obtain several encrypted messages that have been encrypted using the same encryption algorithm. The attacker does not have the associated plaintext; he attempts to crack the code by looking for patterns and using statistical analysis.
![]() Chosen ciphertext—If the attacker can decrypt portions of the ciphertext message, the decrypted portion can then be used to discover the key.
Chosen ciphertext—If the attacker can decrypt portions of the ciphertext message, the decrypted portion can then be used to discover the key.
![]() Chosen plaintext—The attacker has the plaintext messages encrypted and then can analyze the ciphertext output.
Chosen plaintext—The attacker has the plaintext messages encrypted and then can analyze the ciphertext output.
![]() Differential cryptanalysis—Generally used to target block ciphers, it works by looking for the difference between related plaintexts that are encrypted, and the difference between their resultant ciphertexts.
Differential cryptanalysis—Generally used to target block ciphers, it works by looking for the difference between related plaintexts that are encrypted, and the difference between their resultant ciphertexts.
![]() Linear cryptanalysis—Along with differential cryptanalysis, one of the two most widely used attacks on block ciphers. Linear cryptanalysis uses functions to identify the highest probability a specific key was used during the encryption process. The key pairs are then studied to derive information about the key used to create them.
Linear cryptanalysis—Along with differential cryptanalysis, one of the two most widely used attacks on block ciphers. Linear cryptanalysis uses functions to identify the highest probability a specific key was used during the encryption process. The key pairs are then studied to derive information about the key used to create them.
![]() Birthday attack—The birthday attack gets its name from the birthday paradox, which states that within a group of people, the chances that two or more will share birthdays is unexpectedly high. This same logic is applied to calculate collisions in hash functions. A message digest can be susceptible to birthday attacks if the output of the hash function is not large enough to avoid collisions.
Birthday attack—The birthday attack gets its name from the birthday paradox, which states that within a group of people, the chances that two or more will share birthdays is unexpectedly high. This same logic is applied to calculate collisions in hash functions. A message digest can be susceptible to birthday attacks if the output of the hash function is not large enough to avoid collisions.
![]() Key clustering—This is a vulnerability that can occur when two different keys produce the same ciphertext from the same message. This can sometimes be the result of having a small key space or might be a characteristic of some cryptosystems. Key clustering is a real problem as it means that two or more different keys could also decrypt the secure content. A strong cryptosystem should have a low frequency of key clustering occurrences. If not, this is yet another way that a cryptosystem might be targeted for attack.
Key clustering—This is a vulnerability that can occur when two different keys produce the same ciphertext from the same message. This can sometimes be the result of having a small key space or might be a characteristic of some cryptosystems. Key clustering is a real problem as it means that two or more different keys could also decrypt the secure content. A strong cryptosystem should have a low frequency of key clustering occurrences. If not, this is yet another way that a cryptosystem might be targeted for attack.
![]() Replay attack—This method of attack occurs when the attacker can intercept cryptographic keys and reuse them later to either encrypt or decrypt messages.
Replay attack—This method of attack occurs when the attacker can intercept cryptographic keys and reuse them later to either encrypt or decrypt messages.
![]() Man-in-the middle attack—This attack is carried out when attackers place themselves in the communications path between two users. From this position, the possibility exists that they can intercept and modify communications.
Man-in-the middle attack—This attack is carried out when attackers place themselves in the communications path between two users. From this position, the possibility exists that they can intercept and modify communications.
![]() Side channel attack—These attacks are based on side channel information such as timing, sound, or electromagnetic leaks. Here is a link that provides a good example of side channel attack by analyzing the power consumption of the CPU: en.wikipedia.org/wiki/Side-channel_attack
Side channel attack—These attacks are based on side channel information such as timing, sound, or electromagnetic leaks. Here is a link that provides a good example of side channel attack by analyzing the power consumption of the CPU: en.wikipedia.org/wiki/Side-channel_attack
ExamAlert
When comparing cryptographic algorithms, it is important to keep in mind that the larger the work factor, the stronger the cryptosystem. Cryptographers develop systems with high work factors to withstand attacks, not to be foolproof. All systems can be cracked with enough time and a determined hacker. Sometimes attackers simply look for vulnerabilities that have yet to be publicly discovered. These are known as zero-day vulnerabilities.
![]() Rubber hose attack—When all else fails, this method might be used to extract a key value or other information. This type of attack might include threats, violence, extortion, or blackmail, because humans are the biggest weakness, not the cryptosystem.
Rubber hose attack—When all else fails, this method might be used to extract a key value or other information. This type of attack might include threats, violence, extortion, or blackmail, because humans are the biggest weakness, not the cryptosystem.
ExamAlert
On the exam, be careful to distinguish a meet-in-the-middle attack from a man-in-the-middle attack. Although the names are similar, they are completely different.
Exam Prep Questions
1. You are security manager for a bank that has 100 employees. They are all required to encrypt data before they send it. While they examined both symmetric and asymmetric encryption, management has decided to use DES encryption. How many keys will they require for all employees??
![]() A. 4950
A. 4950
![]() B. 49.5
B. 49.5
![]() C. 99
C. 99
![]() D. 4900
D. 4900
2. Which of the following best describes obtaining plaintext from ciphertext without a key?
![]() A. Frequency analysis
A. Frequency analysis
![]() B. Cryptanalysis
B. Cryptanalysis
![]() C. Decryption
C. Decryption
![]() D. Hacking
D. Hacking
3. Which of the following attacks occurs when an attacker can intercept session keys and reuse them at a later date?
![]() A. Known plaintext attack
A. Known plaintext attack
![]() B. Ciphertext-only attack
B. Ciphertext-only attack
![]() C. Man-in-the-middle attack
C. Man-in-the-middle attack
![]() D. Replay attack
D. Replay attack
4. Which of the following is a disadvantage of symmetric encryption?
![]() A. Key size
A. Key size
![]() B. Speed
B. Speed
![]() C. Key management
C. Key management
![]() D. Key strength
D. Key strength
5. Which of the following is not an example of a symmetric algorithm?
![]() A. DES
A. DES
![]() B. RC5
B. RC5
![]() C. AES
C. AES
![]() D. RSA
D. RSA
6. Which of the following forms of DES is considered the most vulnerable to attack?
![]() A. CBC
A. CBC
![]() B. ECB
B. ECB
![]() C. CFB
C. CFB
![]() D. OFB
D. OFB
7. DES uses which of the following for a key size?
![]() A. 56 bits
A. 56 bits
![]() B. 64 bits
B. 64 bits
![]() C. 96 bits
C. 96 bits
![]() D. 128 bits
D. 128 bits
8. Which implementation of Triple-DES uses the same key for the first and third iterations?
![]() A. DES-EEE3
A. DES-EEE3
![]() B. HAVAL
B. HAVAL
![]() C. DES-EEE2
C. DES-EEE2
![]() D. DES-X
D. DES-X
9. Which of the following algorithms is used for key distribution, not encryption or digital signatures?
![]() A. El Gamal
A. El Gamal
![]() B. HAVAL
B. HAVAL
![]() C. Diffie-Hellman
C. Diffie-Hellman
![]() D. ECC
D. ECC
10. Which hashing algorithm produces a 160-bit output?
![]() A. MD2
A. MD2
![]() B. MD4
B. MD4
![]() C. SHA-1
C. SHA-1
![]() D. El Gamal
D. El Gamal
11. What is another name for a one-time pad?
![]() A. ATBASH cipher
A. ATBASH cipher
![]() B. Vigenère cipher
B. Vigenère cipher
![]() C. Caesar cipher
C. Caesar cipher
![]() D. Vernam cipher
D. Vernam cipher
12. Which of the following is also known as a ROT3 cipher?
![]() A. ATBASH cipher
A. ATBASH cipher
![]() B. Vigenère cipher
B. Vigenère cipher
![]() C. Caesar cipher
C. Caesar cipher
![]() D. Vernam cipher
D. Vernam cipher
13. Which of the following did the Wassenaar Arrangement replace?
![]() A. IETF
A. IETF
![]() B. ComCo
B. ComCo
![]() C. The group of five
C. The group of five
![]() D. CoCom
D. CoCom
14. Which of the following is not a hashing algorithm?
![]() A. Whirlpool
A. Whirlpool
![]() B. RipeMD
B. RipeMD
![]() C. Tiger
C. Tiger
![]() D. Mars
D. Mars
15. While working with a file integrity program, Tripwire, you have been asked to review some recent issues with a cryptographic program. What is it called when two different keys generate the same ciphertext for the same message?
![]() A. Hashing
A. Hashing
![]() B. A collision
B. A collision
![]() C. Key clustering
C. Key clustering
![]() D. Output verification
D. Output verification
Answers to Exam Prep Questions
1. A. The formula for computing the number of keys in symmetric cryptography is n(n–1)/2. In this question n = 100, so the answer is 100(100–1)/2 = 4950. B, C, and D are all incorrect.
2. B. Cryptanalysis is the study and act of breaking encryption systems. Although it can mean obtaining the plaintext from the ciphertext without a key, it can also mean that the cryptosystem was cracked because someone found a weakness in the cryptosystem’s implementation. Such was the case with wired equivalent privacy (WEP). Answer A is incorrect because although the cryptanalyst can use frequency analysis to aid in cracking, it is not a valid answer. Answer C is incorrect because decryption is the act of unencrypting data. Answer D is incorrect because hacking is a term used to describe the actions of criminal hackers.
3. D. A reply attack occurs when the attacker can intercept session keys and reuse them at a later date. Answer A is incorrect because a known plaintext attack requires the attacker to have the plaintext and ciphertext of one or more messages. Answer B is incorrect because a ciphertext-only attack requires the attacker to obtain several messages encrypted using the same encryption algorithm. Answer C is incorrect because a man-in-the middle attack is carried out when attackers place themselves in the communications path between two users.
4. C. Key management is a primary disadvantage of symmetric encryption. Answers A, B, and D are incorrect because encryption speed, key size, and key strength are not disadvantages of symmetric encryption.
5. D. RSA is an asymmetric algorithm. Answers A, B, and C are incorrect because DES, RC5, and AES are examples of symmetric algorithms.
6. B. Electronic Code Book is susceptible to known plaintext attacks because the same cleartext always produces the same ciphertext. Answers A, C, and D are incorrect. Because CBC, CFB, and OFB all use some form of feedback, which helps randomize the encrypted data, they do not suffer from this deficiency and are considered more secure.
7. A. Each 64-bit plaintext block is separated into two 32-bit blocks and then processed by the 56-bit key. Total key size is 64 bits but 8 bits are used for parity, thereby making 64, 96, and 128 bits incorrect.
8. C. DES-EEE2 performs the first and third encryption passes using the same key. Answers A, B, and D are incorrect: DES-EEE3 uses three different keys for encryption; HAVAL is used for hashing and DES does not use it; DES-X is a variant of DES with only a 56-bit key size, which was designed for DES, not 3DES.
9. C. Diffie-Hellman is used for key distribution, but not encryption or digital signatures. Answer A is incorrect because El Gamal is used for digital signatures, data encryption, and key exchange. Answer B is incorrect because HAVAL is used for hashing. Answer D is incorrect because ECC is used for digital signatures, data encryption, and key exchange.
10. C. SHA-1 produces a 160-bit message digest. Answers A, B, and D are incorrect because MD2 and MD4 both create a 128-bit message digest and El Gamal is not a hashing algorithm.
11. D. Gilbert Vernam is the creator of the one-time pad. A one-time pad (key) is a keystream that can be used only once and is considered unbreakable if properly implemented. The one-time pad (Vernam cipher) consists of a pad of the same length as the message to which it’s applied. The one-time pad is very effective for short messages and is typically implemented as stream ciphers. Therefore, answers A, B, and C are incorrect.
12. C. Caesar’s cipher is also known as a ROT3 cipher as each character is rotated by three spaces. ATBASH used two separate alphabets that were reversed. The Vigenère cipher is an example of a polyalphabetic cipher, and Gilbert Vernam is the creator of the one-time pad.
13. D. CoCom is an acronym for Coordinating Committee for Multilateral Export Controls and was established by Western block powers after the end of World War II. The Wassenaar Arrangement replaced it. Answers A, B, and C are therefore incorrect.
14. D. Mars is an example of a symmetric encryption algorithm, whereas Whirlpool, RipeMD, and Tiger are all examples of hashing algorithms.
15. C. Key clustering is said to occur when two different keys produce the same ciphertext for the same message. A good algorithm, using different keys on the same plaintext, should generate a different ciphertext. Answers A, B, and D are incorrect: hashing is used for integrity verification; a collision occurs when two different messages are hashed and output the same message digest; and output verification is simply a distractor.
Need to Know More?
History of cryptography: en.wikipedia.org/wiki/History_of_cryptography
IETF PKI Working Group: datatracker.ietf.org/wg/pkix/charter/
Possible Backdoor to ECC: blog.cloudflare.com/how-the-nsa-may-have-put-a-backdoor-in-rsas-cryptography-a-technical-primer/
Concealment ciphers: math.ucdenver.edu/~wcherowi/courses/m5410/m5410cc.html
Historical ciphers: www.cs.trincoll.edu/~crypto/historical/
RFC 3280 information on PKI: www.ietf.org/rfc/rfc3280.txt
Steganography in real life: threatpost.com/attackers-embracing-steganography-to-hide-communication/115394/
Enigma: www.codesandciphers.org.uk/enigma/index.htm
Digital signature algorithm: www.rfc-base.org/rfc-5485.html
Steganography: www.garykessler.net/library/steganography.html
Password hashing: phpsec.org/articles/2005/password-hashing.html