Chapter 10
Troubleshooting Nexus Route-Maps
This chapter covers the following topics:
Conditional matching with ACLs, Prefix Lists, and Regular Expression
Troubleshooting RPM
Redistribution
Nexus Operating System (NX-OS) route-maps provide the capability to filter routes and modify route attributes and routing behavior. These technologies use conditional match criteria to allow actions to occur based upon route characteristics.
Before route-maps are explained, the concepts involved with conditional matching using access control lists (ACL), prefix lists, and conditional matching of BGP communities must be explained.
Conditional Matching
Route-maps typically use some form of conditional matching so that only certain prefixes are blocked, accepted, or modified. Network prefixes are conditionally matched by a variety of routing protocol attributes, but the following sections explain the most common techniques for conditionally matching a prefix.
Access Control Lists
Originally, access control lists (ACL) were intended to provide filtering of packets flowing into or out of a network interface, similar to the functionality of a basic firewall. Today, ACLs provide a method of identifying networks within routing protocols. ACLs are also useful to isolate the direction of the problem or identify where the packet is getting dropped while troubleshooting a complex network environment.
ACLs in NX-OS are generic expressions for filtering traffic based on Layer 2, Layer 3, or Layer 4 information. ACLs are composed of access control entries (ACE), which are entries in the ACL that identify the action to be taken (permit or deny) and the relevant packet classification. Packet classification starts at the top (lowest sequence) and proceeds down (higher sequence) until a matching pattern is identified. After a match is found, the appropriate action (permit or deny) is taken and processing stops. At the end of every ACL is an implicit deny ACE, which denies all packets that did not match earlier in the ACL.
ACLs are classified into two categories:
Standard ACLs: Define the packets based solely on the source network.
Extended ACLs: Define the packet based upon source, destination, protocol, port or combination of other packet attributes. Standard ACLs use the numbered entry 1–99, 1300–1999, or a named ACL. Extended ACLs use the numbered entry 100–199, 2000–2699, or a named ACL. Named ACLs provide relevance to the functionality of the ACL, are used with standard or extended ACLs, and are generally preferred.
The behavior for selecting a network prefix with an extended ACL varies depending on whether the protocol is an IGP such as Enhanced Interior Gateway Protocol (EIGRP), Open Shortest Path First (OSPF), Intermediate System-to-Intermediate System (IS-IS) or Border Gateway Protocol (BGP).
ACLs and ACL Manager Component
In NX-OS, ACLs are managed by a component named ACL Manager (ACLMGR). The ACLMGR is a platform-independent module that serves as a central location for managing ACL definitions for IP, IPv6, and MAC ACLs, as well as for policy objects. The ACLMGR is responsible for processing the configuration received from the user and associating the security ACLs and the enabled interfaces.
Using ACLMGR, the following functionalities are available with ACL:
Object-Groups (Matching IP Addresses, TCP or UDP ports)
Time ranges
IPv6 wildcard matching
Packet length based matching
Stateful restarts
Per-entry statistics
Along with applying ACLs on the interface or using ACLs along with route-maps, which is then used by routing protocols for route filtering purposes, ACLs have the following applications:
Control Plane Policing (CoPP)
Dynamic Host Configuration Protocol (DHCP)
Policy-Based Routing (PBR)
Web Cache Communication Protocol (WCCP)
NX-OS supports the following ACL formats:
IPv4/IPv6 ACLs
Media access control (MAC) ACL
Address resolution protocol (ARP) ACL
Virtual LAN (VLAN) access-map
In NX-OS, when an ACL is applied to a target, a policy is created. NX-OS supports the following types of ACL policies:
Router ACL (RACL)
Port ACL (PACL)
VLAN ACL (VACL)
Virtual terminal line (VTY) ACL
Note
PACL can be applied only on ingress packets for L2/L3 physical Ethernet interfaces (including L2 port-channel interfaces).
Example 10-1 illustrates the various ACL configurations supported on NX-OS. In the following example, the command statistics per-entry is configured to enable the statistics for the ACEs configured under the ACLs. If the command statistics per-entry is not configured, the command show ip access-list does not display any statistics for the packets hitting a particular ACE.
NX-1(config)# ip access-list TEST
NX-1(config-acl)# permit ip host 192.168.33.33 host 192.168.3.3
NX-1(config-acl)# permit ip any any
NX-1(config-acl)# statistics per-entry
NX-1(config)# ipv6 access-list TESTv6
NX-1(config-ipv6-acl)# permit icmp host 2001::33 host 2001::3
NX-1(config-ipv6-acl)# permit ipv6 any any
NX-1(config-ipv6-acl)# statistics per-entry
NX-1(config)# mac access-list TEST-MAC
NX-1(config-mac-acl)# permit 00c0.cf00.0000 0000.00ff.ffff any
NX-1(config-mac-acl)# permit any any
NX-1(config-mac-acl)# statistics per-entry
NX-1(config)# arp access-list TEST-ARP
NX-1(config-arp-acl)# deny ip host 192.168.10.11 mac 00c0.cf00.0000 ffff.ff00.0000
NX-1(config-arp-acl)# permit ip any mac any
NX-1(config)# vlan access-map TEST-VLAN-MAP
NX-1(config-access-map)# match ip address TEST
NX-1(config-access-map)# action drop
NX-1(config-access-map)# statistics per-entry
Note
Validate the ACL-related configuration using the command show run aclmgr. This command displays both the ACL configuration and the ACL attach points.
Example 10-2 illustrates the difference between the output of the show ip access-list command when the statistics per-entry command is configured, compared to when it is not configured. In the following example, the ACL configuration that has the statistics per-entry command configured displays the statistics for the confirmed hits.
NX-1# show ip access-list TEST
IP access list TEST
statistics per-entry
10 permit ip 192.168.33.33/32 192.168.3.3/32 [match=5]
20 permit ip any any [match=1]
NX-1# show ip access-list TEST
IP access list TEST
10 permit ip 192.168.33.33/32 192.168.3.3/32
20 permit ip any any
When an ACL is attached to an interface or any other component, the ACL gets programmed in the ternary content addressable memory (TCAM). The TCAM programming for the access-list is verified using the command show system internal access-list interface interface-id input statistics [module slot]. This command displays under which bank the ACL is programmed and what kind of policy is created when the ACL is attached to an attach point. Along with this, the command displays the statistics of each ACE entry in the ACL.
If the statistics per-entry command is not configured, the counters in the TCAM increment only for the entry for all traffic; that is, permit ip 0.0.0.0/0 0.0.0.0/0. Example 10-3 demonstrates the ACL entry on TCAM and the TCAM statistics when statistics per-entry command is not configured.
Example 10-3 Verifying Access-List Counters in TCAM
NX-1# show system internal access-list interface e4/2 input statistics module 4
INSTANCE 0x0
---------------
Tcam 1 resource usage:
----------------------
Label_b = 0x2
Bank 0
------
IPv4 Class
Policies: RACL(TEST)
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[0018:14242:0004] prec 1 permit-routed ip 192.168.33.33/32 192.168.3.3/32 [5]
[0019:14c42:0005] prec 1 permit-routed ip 0.0.0.0/0 0.0.0.0/0 [2]
[001a:15442:0006] prec 1 deny-routed ip 0.0.0.0/0 0.0.0.0/0 [0]
NX-1# show system internal access-list interface e4/2 input statistics module 4
INSTANCE 0x0
---------------
Tcam 1 resource usage:
---------------------- Label_b = 0x3
Bank 0
------
IPv4 Class
Policies: RACL(TEST) [Merged]
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[001b:15262:0007] prec 1 permit-routed ip 0.0.0.0/0 0.0.0.0/0 [33]
! Output after 5 packets are sent between the host 192.168.3.3 and 192.168.33.33
NX-1# show system internal access-list interface e4/2 input statistics module 4
INSTANCE 0x0
---------------
Tcam 1 resource usage:
----------------------
Label_b = 0x3
Bank 0
------
IPv4 Class
Policies: RACL(TEST) [Merged]
Netflow profile: 0
Netflow deny profile: 0
Entries:
[Index] Entry [Stats]
---------------------
[001b:15262:0007] prec 1 permit-routed ip 0.0.0.0/0 0.0.0.0/0 [38]
As stated before, the ACLMGR takes care of creating the policies when an ACL is attached to an attach point. The policies created by the ACLMGR are verified using the command show system internal aclmgr access-lists policies interface interface-id. This command displays the policy type and interface index, which points to the interface where the ACL is attached, as shown in Example 10-4.
Example 10-4 Verifying Access-List Counters in Hardware
{
0x11498cfc
type = SC_TYPE_PORT; mode = SC_MODE_L3;
flags =
ifindex = 0x1a181000 (Ethernet4/2); vdc = 0; vlan = 0;
no links
}
Policy node 0x04400282, name TEST, policy type 0x00400004
Destination: vdc = 1; vlan = 0; ifindex = 0x1a181000;
Effective destinations: no-destination
Ifelse node 0x04400265
TRUE action node 0x04400266, action type 0x00200002
FALSE action node 0x04400267, action type 0x00200001
NOMATCH action node 0x04400267, action type 0x00200001
Policy node 0x04400283, name TEST, policy type 0x00400010
Destination: vdc = 1; vlan = 0; ifindex = 0x1a181000;
Effective destinations: no-destination
Ifelse node 0x04400265
TRUE action node 0x04400266, action type 0x00200002
FALSE action node 0x04400267, action type 0x00200001
NOMATCH action node 0x04400267, action type 0x00200001
NX-OS has a packet processing filter (PPF) API, which is used to filter the security rules received and processed by the ACLMGR to the relevant clients. The clients can be an interface, a port-channel, a VLAN manager, VSH, and so on. It is important to remember that the ACLMGR stores all the data in the form of a PPF database, where each element is a node. Based on the node ID received from the previous command, more details about the policy can be verified by performing a lookup in the PPF database on that node.
Example 10-5 illustrates the use of the command show system internal aclmgr ppf node node-id to perform a lookup on the PPF database of the ACLMGR for the policy node created when the policy is attached to an attach point. This command is useful when troubleshooting ACL/filtering-related issues, such as ACL not filtering the traffic properly or not matching the ACL entry at all on NX-OS platform.
Example 10-5 Verifying the PPF Database
ACLMGR PRIVATE DATA VERSION IN USE : 1
========= PPF Node: 0x4400283 ========
.nlinks = 1
0x4400265
.noptlinks = 0
.nrefs = 0
.id = 0x4400283
.group = 0x0
.flags = 0x0
.priv_data_size = 0
.type = Policy Instance
.dest.vdc = 1
.dest.vrf = 0
.dest.vlan = 0
.dest.ifindex = 0x1a181000
.dir = IN
.u.pinst.type = 0x400010 (racl_ipv4)
.u.pinst.policy.head = 0x4400265
.u.pinst.policy.tail = 0x0
.u.pinst.policy.size = 0x0
.u.pinst.policy.el_field = 0
.u.pinst.policy.el_field = 0
Note
When troubleshooting any ACL related issues, it is recommended that you collect the command show tech aclmgr [detail] or show tech aclqos [detail] during a problem. The ACLQOS component on the line card provides statistics for ACLs on a per-line card basis and are important when you are troubleshooting ACL-related issues.
Interior Gateway Protocol (IGP) Network Selection
When ACLs are used for the IGP network selection during redistribution, the source fields of the ACL are used to identify the network, and the destination fields identify the smallest prefix length allowed in the network range. Table 10-1 provides sample ACL entries from within the ACL configuration mode and specifies the networks that match with the extended ACL. Notice that the subtle difference for the destination wildcard for the 172.16.0.0 network affects the actual network ranges that are permitted in the second and third rows of the table.
Table 10-1 Extended ACL for IGP Route Selection
ACE Entry |
Networks |
permit ip any any |
Permits all networks |
permit ip host 172.16.0.0 host 255.240.0.0 |
Permits all networks in the 172.16.0.0/12 range |
permit ip host 172.16.0.0 host 255.255.0.0 |
Permits all networks in the 172.16.0.0/16 range |
permit host 192.168.1.1 |
Permits only the 192.168.1.1/32 network |
Note
Extended ACLs that are used for distribute-list use the source fields to identify the source of the network advertisement, and the destination fields identify the network prefix.
BGP Network Selection
Extended ACLs react differently when matching BGP routes than when matching IGP routes. The source fields match against the network portion of the route, and the destination fields match against the network mask, as shown in Figure 10-1. Extended ACLs were originally the only match criteria used by IOS with BGP before the introduction of prefix-lists.
Figure 10-1 BGP Extended ACL Matches
Table 10-2 demonstrates the concept of the wildcard for the network and subnet mask.
Table 10-2 Extended ACL for BGP Route Selection
Extended ACL |
Matches These Networks |
permit ip 10.0.0.0 0.0.0.0 255.255.0.0 0.0.0.0 |
Permits only the 10.0.0.0/16 network |
permit ip 10.0.0.0 0.0.255.0 255.255.255.0 0.0.0.0 |
Permits any 10.0.x.0 network with a /24 prefix length |
permit ip 172.16.0.0 0.0.255.255 255.255.255.0 0.0.0.255 |
Permits any 172.16.x.x network with a /24 to /32 prefix length |
permit ip 172.16.0.0 0.0.255.255 255.255.255.128 0.0.0.127 |
Permits any 172.16.x.x network with a /25 to /32 prefix length |
Prefix Matching and Prefix-Lists
Prefix lists provide another method of identifying networks in a routing protocol. They identify a specific IP address, network, or network range, and allow for the selection of multiple networks with a variety of prefix lengths (subnet masks) by using a prefix match specification. This technique is preferred over the ACL’s network selection method because most network engineers find it easier to understand.
Prefix Matching
The structure for a prefix match specification contains two parts: high-order bit pattern and high-order bit count, which determine the high-order bits in the bit pattern that are to be matched. Some documentation refers to the high-order bit pattern as the address or network, and the high-order bit count as length or mask length.
In Figure 10-2, the prefix match specification has the high-order bit pattern of 192.168.0.0 and a high-order bit count of 16. The high-order bit pattern has been converted to binary to demonstrate where the high-order bit count lays. Because no additional matching length parameters are included, the high-order bit count is an exact match.
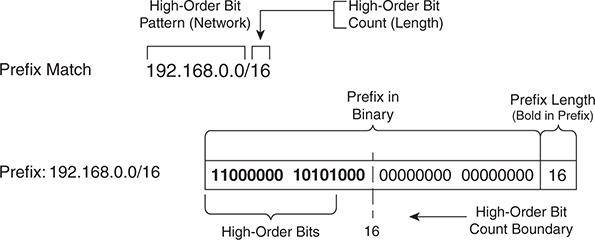
Figure 10-2 Basic Prefix Match Pattern
The prefix match specification logic might look identical to the functionality of an access-list. The true power and flexibility comes by using matching length parameters to identify multiple networks with specific prefix lengths with one statement. The matching length parameter options are as follows:
le (less than or equal to <=)
ge (greater than or equal to >=), or both.
Figure 10-3 demonstrates the prefix match specification with a high-order bit pattern of 10.168.0.0, high-order bit count of 13, and the matching length of the prefix must be greater than or equal to 24.
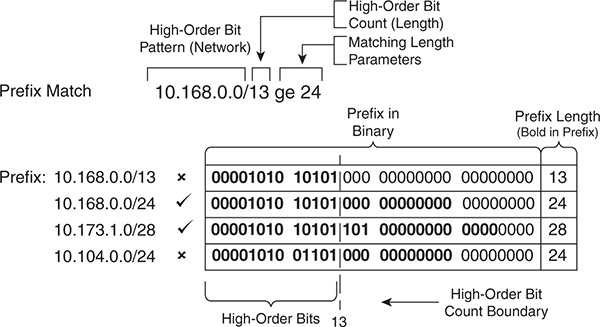
Figure 10-3 Prefix Match Pattern with Matching Length Parameters
The 10.168.0.0/13 prefix does not qualify because the prefix length is less than the minimum of 24 bits, whereas the 10.168.0.0/24 prefix does meet the matching length parameter. The 10.173.1.0/28 prefix qualifies because the first 13 bits match the high-order bit pattern, and the prefix length is within the matching length parameter. The 10.104.0.0/24 prefix does not qualify because the high-order bit-pattern does not match within the high-order bit count.
Figure 10-4 demonstrates a prefix match specification with a high-order bit pattern of 10.0.0.0, high-order bit count of 8, and the matching length must be between 22 and 26.
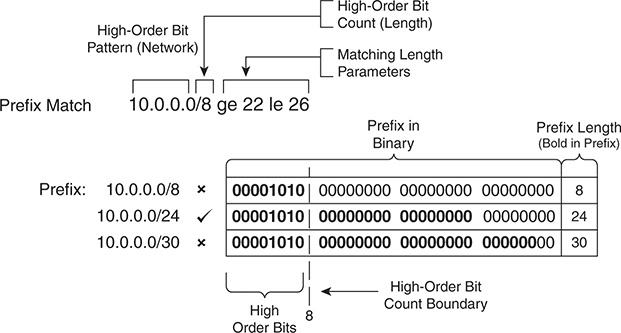
Figure 10-4 Prefix Match with Ineligible Matched Prefixes
The 10.0.0.0/8 prefix does not match because the prefix length is too short. The 10.0.0.0/24 qualifies because the bit pattern matches and the prefix length is between 22 and 26. The 10.0.0.0/30 prefix does not match because the bit pattern is too long. Any prefix that starts with 10 in the first octet and has a prefix length between 22 and 26 will match the prefix match specification.
Prefix Lists
Prefix lists contain multiple prefix matching specification entries that contain a permit or deny action. Prefix lists process in sequential order in a top-down fashion, and the first prefix match processes with the appropriate permit or deny action.
NX-OS prefix lists are configured with the global configuration command ip prefix-list prefix-list-name [seq sequence-number] {permit | deny} high-order-bit-pattern/high-order-bit-count [{eq match-length-value | le le-value | ge ge-value [le le-value]}].
If a sequence is not provided, the sequence number auto-increments by 5 based off the highest sequence number. The first entry is 5. Sequencing allows the deletion of a specific entry. Because prefix lists cannot be resequenced, it is advisable to leave enough space for insertion of sequence numbers at a later time.
Example 10-6 provides a sample prefix list named RFC 1918 for all the networks in the RFC 1918 address range. The prefix list only allows /32 prefixes to exist in the 192.168.0.0 network range and not exist in any other network range in the prefix list.
Example 10-6 Sample Prefix List
NX-1(config)# ip prefix-list RFC1918 seq 10 deny 0.0.0.0/0 ge 32
NX-1(config)# ip prefix-list RFC1918 seq 15 permit 10.0.0.0/7 ge 8
NX-1(config)# ip prefix-list RFC1918 seq 20 permit 172.16.0.0/11 ge 12
NX-1(config)# ip prefix-list RFC1918 seq 25 permit 192.168.0.0/15 ge 16
Notice that sequence 5 permits all /32 prefixes in the 192.168.0.0/13 bit pattern, then sequence 10 denies all /32 prefixes in any bit pattern, and then sequence 15, 20, 25 permit routes in the appropriate network ranges. The sequence order is important for the first two entries to ensure that only /32 prefixes exist in the 192.168.0.0 in the prefix list.
The command show ip prefix-list prefix-list-name high-order-bit-pattern/high-order-bit-count first-match provides the capability for a specific network prefix to be checked against a prefix-list to identify the matching sequence, if any.
Example 10-7 displays the command being executed against three network prefix patterns based upon the RFC1918 prefix-list created earlier. The first command uses a high-order bit count of 32, which matches against sequence 5, whereas the second command uses a high-order bit count of 16, which matches against sequence 25. The last command matches against sequence 10, which has a deny action.
Example 10-7 Identification of Matching Sequence for a Specific Prefix Pattern
seq 5 permit 192.168.0.0/13 ge 32
seq 25 permit 192.168.0.0/15 ge 16
seq 10 deny 0.0.0.0/0 ge 32
Note
This command demonstrated in Example 10-7 is useful for verifying that the network prefix matches the intended sequence in a prefix-list.
Route-Maps
Route-maps provide many features to a variety of routing protocols. At the simplest level, route-maps filter networks similar to an ACL, but also provide additional capability by adding or modifying a network attribute. Route-maps must be referenced within a routing-protocol to influence it. Route-maps are a critical to BGP because it is the main component of modifying a unique routing policy on a neighbor-by-neighbor basis.
Route-maps are composed of four components:
Sequence Number: Dictates the processing order of the route-map.
Conditional Matching Criteria: Identifies prefix characteristics (network, BGP path attribute, next-hop, and so on) for a specific sequence.
Processing Action: Permits or denies the prefix.
Optional Action: Allows for manipulations dependent upon how the route-map is referenced on the router. Actions include modification, addition, or removal of route characteristics.
Route-maps use the following command syntax route-map route-map-name [permit | deny] [sequence-number]. The following rules apply to route-map statements:
If a processing action is not provided, the default value of permit is used.
If a sequence number is not provided, the sequence number defaults to 10.
If a conditional matching statement is not included, an implied all prefixes is associated to the statement.
Processing within a route-map stops after all optional actions have processed (if configured) after matching a conditional matching criteria.
If a route is not conditionally matched, there is an implicit deny for that route.
Example 10-8 provides a sample route-map to demonstrate the four components of a route-map shown earlier. The conditional matching criteria is based upon network ranges specified in an ACL. Comments have been added to explain the behavior of the route-map in each sequence.
match ip address ACL-ONE
route-map EXAMPLE deny 20
match ip address ACL-TWO
route-map EXAMPLE permit 30
match ip address ACL-THREE
set metric 20
route-map EXAMPLE permit 40
Note
When deleting a specific route-map statement, include the sequence number to prevent deleting the entire route-map.
Conditional Matching
Now that the components and processing order of a route-map were explained, this section expands upon the aspect of how to match a route. Example 10-9 shows the various options available within NX-OS.
NX-1(config-route-map)# match ?
as-number Match BGP peer AS number
as-path Match BGP AS path list
community Match BGP community list
extcommunity Match BGP community list
interface Match first hop interface of route
ip Configure IP features
ipv6 Configure IPv6 features
length Packet length
mac-list Match entries of mac-lists
metric Match metric of route
route-type Match route-type of route
source-protocol Match source protocol
tag Match tag of route
vlan Vlan ID
As you can see, a number of conditional matching options are available. Some of the options, like vlan and mac-list, are applicable only for policy-based routing. Table 10-3 provides the command syntax for the most common methods for matching prefixes and describes their usage.
Table 10-3 Conditional Match Options
Match Command |
Description |
match as-number { number [, number ...] | as-path-access- list name acl-name } |
Matches routes that come from peers with the matching ASNs |
match as-path acl-number |
Selects prefixes based on regex query to isolate the ASN in the BGP path attribute (PA) AS-Path *Allows for multiple match variables |
match community community- list-name |
Selects prefixes based on BGP communities *Allows for multiple match variables |
match extcommunity extcommunity-list-name |
Selects prefixes based on extended BGP communities |
match interface interface-id |
Select prefixes based on the interface that they are associated to *Allows for multiple match variables |
match ip address {acl-number | acl-name} |
Selects prefixes based on network selection criteria defined in the ACL *Allows for multiple match variables |
match ip address prefix-list prefix-list-name |
Selects prefixes based on prefix selection criteria *Allows for multiple match variables |
match ip route-source prefix-list prefix-list-name |
Selects prefixes based on prefix selection criteria *Allows for multiple match variables |
match local-preference |
Selects prefixes based on the BGP attribute Local Preference *Allows for multiple match variables |
match metric {1-4294967295 | external 1-4294967295} [+- deviation] |
Selects prefixes based on the metric that can be exact, a range, or within acceptable deviation |
match route-type protocol- specific-flag |
Selects prefixes based on the source protocol or subclassification of routes in the source routing protocol. *Allows for multiple match variables |
match tag tag-value |
Selects prefixes based on a numeric tag (0-4294967295) which was set by another router *Allows for multiple match variables |
Multiple Conditional Match Conditions
If there are multiple variables (ACLs, prefix-lists, tags, and the like) of the same type configured for a specific route-map sequence, only one variable must match for the prefix to qualify. The Boolean logic uses an or operator for this configuration.
In Example 10-10, sequence 10 requires that a prefix pass ACL-ONE or ACL-TWO. Notice that sequence 20 does not have a match statement, so all prefixes that are not passed in sequence 10 qualify and are denied.
Example 10-10 Multiple Match Variables Example Route-Map
match ip address ACL-ONE ACL-TWO
!
route-map EXAMPLE deny 20
Note
Sequence 20 is redundant because of the implicit deny for any prefixes that are not matched in sequence 10. However it provides clarity for junior network engineers.
If multiple match options are configured for a specific route-map sequence, both match options must be met for the prefix to qualify for that sequence. The Boolean logic uses an and operator for this configuration.
In Example 10-11, sequence 10 requires that the prefix match ACL ACL-ONE and that the metric be a value between 500 and 600. If the prefix does not qualify for both match options, the prefix does not qualify for sequence 10 and is denied because another sequence does not exist with a permit action.
Example 10-11 Multiple Match Options Example Route-Map
match ip address ACL-ONE
match metric 550 +- 50
Complex Matching
Some network engineers find route-maps too complex if the conditional matching criteria uses an ACL, AS-Path ACL, or prefix list that contains a deny statement in it. Example 10-12 demonstrates a configuration where the ACL uses a deny statement for the 172.16.1.0/24 network range.
Example 10-12 Complex Matching Route-Maps
deny 172.16.1.0 0.0.0.255
permit 172.16.0.0 0.0.255.255
!
route-map EXAMPLE permit 10
match ip address ACL-ONE
!
route-map EXAMPLE deny 20
match ip address ACL-ONE
!
route-map EXAMPLE permit 30
set metric 20
Reading configurations like this must follow the sequence order first, conditional matching criteria second, and only after a match occurs should the processing action and optional action be used. Matching a deny statement in the conditional match criteria excludes the route from that sequence in the route-map.
The prefix 172.16.1.0/24 is denied by ACL-ONE, so that infers that there is not a match in sequence 10 and 20; therefore, the processing action (permit or deny) is not needed. Sequence 30 does not contain a match clause, so any remaining routes are permitted, The prefix 172.16.1.0/24 passes on sequence 30 with the metric set to 20. The prefix 172.16.2.0/24 matches ACL-ONE and passes in sequence 10.
Note
Route-maps process in the order of evaluation of the sequence, conditional match criteria, processing action, and optional action, in that order. Any deny statements in the match component are isolated from the route-map sequence action.
Optional Actions
In addition to permitting the prefix to pass, route-maps modify route attributes. Table 10-4 provides a brief overview of the most popular attribute modifications.
Table 10-4 Route-Map Set Actions
Set Action |
Description |
set as-path prepend {as-number- pattern | last-as 1-10} |
Prepends the AS-Path for the network prefix with the pattern specified, or from multiple iterations from neighboring AS. |
set ip next-hop { ip-address | peer-address | self } |
Sets the next-hop IP address for any matching prefix. BGP dynamic manipulation uses the peer-address or self keywords. |
set local-preference 0-4294967295 |
Sets the BGP PA Local Preference. |
set metric {+value | -value | value} *Value parameters are 0-4294967295 |
Modifies the existing metric or sets the metric for a route. |
set origin {igp | incomplete} |
Sets the BGP PA Origin. |
set tag tag-value |
Sets a numeric tag (0-4294967295) for identification of networks by other routers. |
set weight 0-65535 |
Sets the BGP path attribute Weight. |
Incomplete Configuration of Routing Policies
Another common issue with route policies is the partial configuration of route-maps— specifically, the conditional matching that refers to an ACL, prefix-list, AS-Path ACL, BGP community list, and so on, and that entity is not defined. In some instances, all paths are accepted, and in other instances, no paths are accepted. This problem exists regardless of whether the route-map is used directly with a BGP neighbor, or during route redistribution.
Verifying that all components of a route-map are defined is a vital component of troubleshooting.
Diagnosing Route Policy Manger
NX-OS includes a process called Route Policy Manager (RPM) that provides the route-map functionality with the following properties:
Operates as a stateful, restartable, and multithreaded process
Maintains state in a database that exists in private memory
Supports IPv4 and IPv6 address families
Provides API interaction for other processes like BGP or OSPF
Interacts with the unicast RIB (URIB), ARP table
NX-OS’s RPM provides additional methods to verify route-map interaction on a Nexus switch. Figure 10-5 provides a sample topology where NX-2 is redistributing OSPF learned routes into EIGRP.
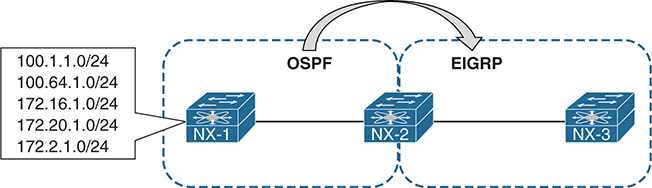
Figure 10-5 Sample Topology Displaying Redistribution
Example 10-13 displays the relevant EIGRP configuration that redistributes OSPF and directly connected routes into EIGRP. The route-map is selective with the routes that are being redistributed into EIGRP.
Example 10-13 NX-2 Redistribution Configuration
ip prefix-list PRE1 seq 5 permit 100.1.1.0/24
ip prefix-list PRE2 seq 5 permit 100.64.1.0/24
!
route-map REDIST-CONNECTED-2-EIGRP permit 10
match interface Vlan10
route-map REDIST-OSPF-2-EIGRP permit 10
match ip address prefix-list PRE1 PRE2
set metric 10000 1 255 1 1500
!
router eigrp NXOS
router-id 192.168.2.2
address-family ipv4 unicast
autonomous-system 100
redistribute direct route-map REDIST-CONNECTED-2-EIGRP
redistribute ospf NXOS route-map REDIST-OSPF-2-EIGRP
When routes are not installed in EIGRP as anticipated, the first step is to check to make sure that any relevant policies were bound to the destination routing protocol. The command show system internal rpm event-history rsw displays low-level events that are handled by RPM.
Example 10-14 displays the command. Notice that two different route-maps were applied to EIGRP: one was for OSPF and the other for directly connected interfaces as the source redistribution protocols.
Example 10-14 Viewing RPM Event-History
Routing software interaction logs of RPM
1) Event:E_DEBUG, length:98, at 211881 usecs after 02:01:35 [120] [4933]:
Bind ack sent - client eigrp-NXOS uuid 0x41000130 for policy
REDIST-CONNECTED-2-EIGRP
2) Event:E_DEBUG, length:93, at 211857 usecs after 02:01:35 [120] [4933]:
Bind request - client eigrp-NXOS uuid 0x41000130 policy
REDIST-CONNECTED-2-EIGRP
3) Event:E_DEBUG, length:114, at 17980 usecs after 02:01:21 [120] [4933]:
Notify of clients aborted for policy REDIST-CONNECTED-2-EIGRP - change
status: 0 - config refcount: 0
4) Event:E_DEBUG, length:85, at 95007 usecs after 02:01:06 [120] [4933]:
Trying to notify for policy REDIST-CONNECTED-2-EIGRP – config refcount 1
5) Event:E_DEBUG, length:85, at 815063 usecs after 02:01:02 [120] [4933]:
Trying to notify for policy REDIST-CONNECTED-2-EIGRP – config refcount 1
6) Event:E_DEBUG, length:93, at 381829 usecs after 01:59:30 [120] [4933]:
Bind ack sent - client eigrp-NXOS uuid 0x41000130 for policy
REDIST-OSPF-2-EIGRP
7) Event:E_DEBUG, length:88, at 381614 usecs after 01:59:30 [120] [4933]:
Bind request - client eigrp-NXOS uuid 0x41000130 policy REDIST-OSPF-2-EIGRP
It might be simpler to get a count of the number of RPM processes that have attached to a protocol using the command show system internal rpm clients, as demonstrated in Example 10-15. If the Bind-count did not match the anticipated number of route-maps used by that protocol, viewing the RPM event-history will indicate the error.
Example 10-15 Viewing the Number of RPM Clients per Protocol
PBR: policy based routing RF/RD: route filtering/redistribution
Client Bind-count Client-name [VRF-name/Status/Id]
RF/RD 0 bgp-100
RF/RD 0 icmpv6
RF/RD 0 igmp
RF/RD 0 u6rib
RF/RD 0 tcp
RF/RD 0 urib
In addition to viewing the accuracy of a prefix-list as shown in Example 10-2, the capability to view the internal programming for a prefix-list is beneficial. The command show system internal rpm ip-prefix-list displays all the prefix-lists configured on the Nexus switch for the route-map from Example 10-13. Notice that the clients show you the route-map referencing the prefix list. In addition, each prefix-list entry displays the number of sequences and version history for that prefix-list. Example 10-16 displays the use of the show system internal rpm ip-prefix-list command for NX-2.
Example 10-16 Viewing Prefix-Lists from RPM Perspective
Policy name: PRE1 Type: ip prefix-list
Version: 2 State: Ready
Ref. count: 1 PBR refcount: 0
Stmt count: 1 Last stmt seq: 5 Set nhop cmd count: 0 Set vrf cmd count: 0
Set intf cmd count: 0 Flags: 0x00000003
PPF nodeid: 0x00000000 Config refcount: 0
PBR Stats: No
Clients:
REDIST-OSPF-2-EIGRP (internal - route-map)
Policy name: PRE2 Type: ip prefix-list
Version: 2 State: Ready
Ref. count: 1 PBR refcount: 0
Stmt count: 1 Last stmt seq: 5 Set nhop cmd count: 0 Set vrf cmd count: 0
Set intf cmd count: 0 Flags: 0x00000003
PPF nodeid: 0x00000000 Config refcount: 0
PBR Stats: No
Clients:
REDIST-OSPF-2-EIGRP (internal - route-map)
The last method is to view relevant changes from a debug perspective. Traditionally, the route-map option needs to be enabled from the destination protocol. Example 10-17 displays the debugs for the route-maps associated to the redistribution into EIGRP.
Example 10-17 Viewing Debug Information for Redistribution
NX-2# config t
NX-2(config)# router eigrp NXOS
NX-2(config-router)# address-family ipv4 unicast
NX-2(config-router-af)# redistribute ospf NXOS route-map REDIST-OSPF-2-EIGRP
referer handle 0x820d5e4 referee_plcy 0x5f835614
02:59:50.071917 eigrp: librpm NXOS [9600] rpm_build_prefix_trie_pfl() - List:
PRE1, No. of entries: 1
02:59:50.071954 eigrp: librpm NXOS [9600] rpm_create_prefix_in_trie()
- ip addr: 100.1.1.0 mask_len: 24
02:59:50.071973 eigrp: librpm NXOS [9600] Successfully cloned the policy PRE1
with version 2 rules_flag 0x00000001
02:59:50.071987 eigrp: librpm NXOS [9600] Stats AVL initialized with keysize 12
and offset 16
02:59:50.072001 eigrp: librpm NXOS [9600] Setting up referee policy PRE2 –
referer handle 0x820d5e4 referee_plcy 0x5f83556c
02:59:50.072016 eigrp: librpm NXOS [9600] rpm_build_prefix_trie_pfl() - List:
PRE2, No. of entries: 1
02:59:50.072030 eigrp: librpm NXOS [9600] rpm_create_prefix_in_trie() - ip addr:
100.64.1.0 mask_len: 24
02:59:50.072043 eigrp: librpm NXOS [9600] Successfully cloned the policy PRE2
with version 2 rules_flag 0x00000001
02:59:50.072055 eigrp: librpm NXOS [9600] Stats AVL initialized with keysize 12
and offset 16
02:59:50.072070 eigrp: librpm NXOS [9600] Successfully cloned the policy
REDIST-OSPF-2-EIGRP with version 5 rules_flag 0x00000409
02:59:50.072086 eigrp: librpm NXOS [9600] Stats AVL initialized with keysize 12
and offset 16
02:59:50.072099 eigrp: librpm NXOS [9600] Stats successfully init for policy
REDIST-OSPF-2-EIGRP and context 0x0820d894
02:59:50.072125 eigrp: librpm NXOS [9600] rpm_bind request sent with uuid
0x41000130 client name eigrp-NXOS policy <REDIST-OSPF-2-EIGRP> type <route-map>
02:59:50.072688 eigrp: librpm NXOS [9600] Recvd msg-type <BIND_ACK> pname
<REDIST-OSPF-2-EIGRP> ptype <route-map> pversion <0> data <0x0820d894>
02:59:50.076902 eigrp: librpm NXOS [9600] ========== RPM Evaluation starting for
policy REDIST-OSPF-2-EIGRP ==========
..
Policy-Based Routing
A router makes forwarding decisions based upon the destination address of the IP packet. Some scenarios accommodate other factors, such as packet length or source address, when deciding where the router should forward a packet.
Policy-based routing (PBR) allows for conditional forwarding of packets based on the following packet characteristics:
Routing by protocol type (Internet Control Message Protocol [ICMP], Transmission Control Protocol [TCP], User Datagram Protocol [UDP] and so on)
Routing by source IP address, destination IP address, or both
Manually assigning different network paths to the same destination based upon tolerance for latency, link-speed, or utilization for specific transient traffic
Packets are examined for PBR processing as they are received on the router interface. PBR verifies the existence of the next-hop IP address and then forwards packets using the specified next-hop address. Additional next-hop addresses are configured so that in the event that the first next-hop address is not in the RIB, the secondary next-hop addresses are used. If none of the specified next-hop addresses exist in the routing table, the packets are not conditionally forwarded.
Note
PBR policies do not modify the RIB because the policies are not universal for all packets. This often complicates troubleshooting because the routing table displays the next-hop address learned from the routing protocol, but does not accommodate for a different next-hop address for the conditional traffic.
NX-OS PBR configuration use a route-map with match and set statements that are then attached to the inbound interface. The following steps are used:
Step 1. Enable the PBR feature. The PBR feature is enabled with the global configuration command feature pbr.
Step 2. Define a route-map. The route-map is configured with the global configuration command route-map route-map-name [permit | deny] [sequence- number].
Step 3. Identify the conditional match criteria. The conditional match criteria is based upon packet length with the command match length minimum-length maximum-length, or by using the packet ip address fields with an ACL using the command match ip address {access-list-number | acl-name}.
Step 4. Specify the next-hop. The route-map configuration command set ip [default] next-hop ip-address [... ip-address] is used to specify one or more next-hops for packets that match the criteria. The optional default keyword changes the behavior so that the next-hop address specified by the route-map is used only if the destination address does not exist in the RIB. If a viable route exists in the RIB, that is the next-hop address that is used for forwarding the packet.
Step 5. Apply the route-map to the inbound interface. The route-map is applied with the interface parameter command ip policy route-map route-map-name.
Step 6. Enable PBR statistics (optional). Statistics of PBR forwarding are enabled with the command route-map route-map-name pbr-statistics.
Figure 10-6 displays a topology to demonstrate how PBR operates. The default path between NX-1 and NX-6 is NX-1 → NX-2 → NX-3 → NX-5 → NX-6 because the link cost of 10.23.1.0/24 is lower than 10.24.1.0/24 link. However, specific traffic sourced from NX-1’s Loopback 0 (192.168.1.1) to NX-6’s Loopback 0 (192.168.6.6) must not forward through NX-3. These packets must forward through NX-4 even though it has a higher path cost.
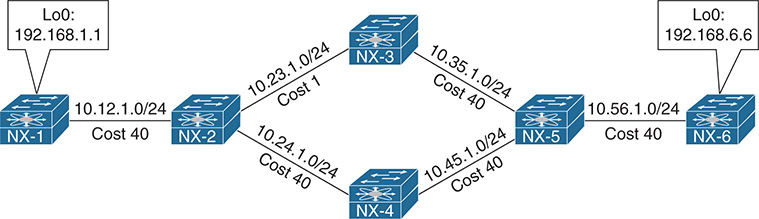
Figure 10-6 Policy-Based Routing Topology
Example 10-18 displays NX-2’s PBR configuration.
Example 10-18 NX-2’s PBR Configuration
feature pbr
!
ip access-list R1-TO-R6
10 permit ip 192.168.1.1/32 192.168.6.6/32
!
route-map PBR pbr-statistics
route-map PBR permit 10
match ip address R1-TO-R6
set ip next-hop 10.24.1.4
!
interface Ethernet2/1
description to NX-1
ip address 10.12.1.2/24
ip router ospf NXOS area 0.0.0.0
ip policy route-map PBR
Example 10-19 displays a traceroute from NX-1, which displays traffic flowing through NX-3. A source interface was not specificed, so traffic is sourced from the 10.12.1.1 IP address. This is confirmed based upon the routing table on NX-2 for the 192.168.6.6 network prefix.
Example 10-19 Normal Traffic Flow to NX-6’s Loopback 0 Interface
traceroute to 192.168.6.6 (192.168.6.6), 30 hops max, 40 byte packets
1 10.12.1.2 (10.12.1.2) 2.016 ms 1.382 ms 1.251 ms
2 10.23.1.3 (10.23.1.3) 3.24 ms 3.372 ms 3.364 ms
3 10.35.1.5 (10.35.1.5) 5.819 ms 5.497 ms 3.844 ms
4 10.56.1.6 (10.56.1.6) 5.577 ms * 5.359 ms
192.168.6.6/32, ubest/mbest: 1/0
*via 10.23.1.3, Eth2/2, [110/82], 3d01h, ospf-NXOS, intra
Example 10-20 displays a traceroute from NX-1’s Loopback 0 interface to be redirected on NX-2 toward NX-4. The traceroute displays that PBR is working as intended.
Example 10-20 Verification of PBR-Based Traffic
traceroute to 192.168.6.6 (192.168.6.6) from 192.168.1.1 (192.168.1.1), 30 hops max, 40 byte packets
1 10.12.1.2 (10.12.1.2) 1.33 ms 1.199 ms 1.064 ms
2 10.24.1.4 (10.24.1.4) 3.354 ms 2.978 ms 2.825 ms
3 10.45.1.5 (10.45.1.5) 3.818 ms 3.707 ms 3.487 ms
4 10.56.1.6 (10.56.1.6) 4.542 ms * 4.907 ms
PBR statistics were enabled on NX-2 that allows for network engineers to see how much traffic was forwarded by PBR. Example 10-21 displays output for PBR statistics before and after traffic was conditionally forwarded.
Example 10-21 Sample Output of PBR Statistics
NX-2# show route-map PBR pbr-statistics
route-map PBR, permit, sequence 10
Policy routing matches: 0 packets
Default routing: 12 packets
NX-2# show route-map PBR pbr-statistics
route-map PBR, permit, sequence 10
Policy routing matches: 12 packets
Default routing: 12 packets
Note
The PBR configuration shown is for transient traffic. For PBR on locally generated traffic, use the command ip local policy route-map route-map-name.
Summary
This chapter covered several important building block features that are necessary for understanding the conditional matching process used within NX-OS route-maps:
Access control lists provide a method of identifying networks. Extended ACLS provide the capability to select the network and advertising router for IGP protocols and provide the capability to use wildcards for the network and subnet mask for BGP routes.
Prefix lists identify networks based upon the high-order bit pattern, high-order bit count, and required prefix length requirements.
Regular expressions (regex) provide a method of parsing output in a systematic way. Regex is commonly used for BGP filtering, but it is also used in the CLI for parsing output, too.
Route-maps filter routes similar to an ACL and provide the capability to modify route attributes. Route-maps are composed of sequence numbers, matching criteria, processing action, and optional modifying actions. They use the following logic:
If matching criteria is not specified, all routes qualify for that route-map sequence.
Multiple conditional matching requirements of the same type are a Boolean or, and multiple conditional matching requirements of different type are a Boolean and.
NX-OS uses RPM that operate as a separate process and memory space from the actual protocols. This provides an additional method for diagnosing unintentional behaviors in a protocol.
The default packet-forwarding decisions bypass routing protocols altogether through the use of policy-based routing to place specific network traffic onto a different path that was selected by the routing protocol.
References
Edgeworth, Brad, Aaron Foss, and Ramiro Garza Rios. IP Routing on Cisco IOS, IOS XE and IOS XR. Indianapolis: Cisco Press, 2014.
Cisco. Cisco NX-OS Software Configuration Guides, www.cisco.com.
