This chapter explains remote access scenarios that are possible with Office Communications Server 2007. Remote access gives users the flexibility to communicate whether they are on the enterprise network or on external networks such as the Internet. The scenarios that will be discussed involve users who are working from an external network outside the enterprise (such as the Internet). There are three primary remote access scenarios and two extended scenarios:
Primary Remote Access Scenarios
Basic Remote Access (for instant messaging [IM] and presence)
Involves remotely using Office Communicator to log in to the enterprise network
Requires that the Access Edge Server role is deployed by the enterprise
Web Conferencing Remote Access
Involves using the Live Meeting 2007 client remotely to connect to a data conference
Requires that the Access Edge Server and Web Conferencing Edge Server roles are deployed by the enterprise
A/V Remote Access
Involves using Office Communicator remotely for an audio/video conference
Requires that the Access Edge Server and A/V Edge Server roles are deployed by the enterprise
Extended Remote Access Scenarios
For almost all remote access scenarios, the Access Edge Server role needs to be deployed. The only exception is the use of Office Communicator Web Access 2007, which involves a Web interface to the Office Communicator client. (See the Enabling Office Communicator Web Access 2007 section later in this chapter.) The Access Edge Server provides the core functionality for collaboration between internal users and users outside the enterprise firewall. This is true whether the outside users are using Office Communicator, Office Communicator Mobile, or the Office Live Meeting 2007 client. The Access Edge Server provides a single, trusted connection point for both inbound and outbound Session Initiation Protocol (SIP) traffic. Practically all Office Communications Server 2007 components use SIP to provide the basic connectivity and communications channel.
The Web Conferencing Edge Server enables external users using the Live Meeting 2007 client to join enterprise meetings. If the Web Conferencing Edge Server is deployed, enterprise users (whether local or remote) can join meetings, as can users from federated partners or anonymous users (other users who have connectivity to the Web Conferencing Edge Server who don't have accounts defined by the local enterprise Active Directory). Remote access users are authenticated using their domain credentials; federated users are authenticated based on certificate credentials from their organization's Access Edge Server; and anonymous users are authorized by their use of per-meeting conference keys, which are provided to them along with the conference invitation.
The Office Communications Server 2007 A/V Edge Server enables media traversal of firewalls. Users who log in remotely using Office Communicator 2007 require use of the A/V Edge Server for both individual calls and conference calls. The A/V Edge Server is responsible for opening media ports and bridging the external and internal networks safely to allow audio and video sessions for remote users.
Office Communicator Web Access requires its own Web server published through an HTTP reverse proxy independent of the other edge server roles. The other edge server roles can be deployed on separate physical servers within the enterprise edge network (also known as a perimeter network or screened subnet), or they can all be hosted on the same physical server.
This chapter identifies the basic remote access topologies and then explains each of the primary and extended remote access scenarios. An overview of each remote access scenario is shown from the user's perspective, and then the technical details that make the scenario possible are presented.
Before examining different remote access scenarios, many examples of the basic remote access topologies are presented to help you see the underlying infrastructure. The extended remote access scenario topologies are presented along with the scenarios themselves in later sections. In a production environment, there are many topology variations that might be useful for an organization to deploy based on its connectivity, collaboration, and availability needs.
The simplest installation involves minimizing the hardware required to provide access by consolidating the installation of the Access, Web Conferencing, and A/V Edge Servers on the same physical server in the edge network. (See Figure 6-1.) Firewalls protect the edge network from the external network and protect the enterprise network from irregular access from the edge network. The consolidated edge server bridges the edge network for valid traffic and connects to the internal servers in the organization, which could be a pool of servers or a single, Standard Edition server. Figure 6-1 shows the topology with the next hop as a Standard Edition Director, which can provide authentication and forward requests to the Enterprise Edition pool.
For a single edge server topology, remote access Office Communicator clients use Transport Layer Security (TLS) to securely connect to the Access Edge Server from the Internet. The enterprise Access Edge Server is discovered by Office Communicator through Domain Name Service service (DNS SRV) records. This interaction is very similar to how internal clients connect. (See Chapter 4 for more details on an internal login and the use of DNS SRV records.) However, to prevent anonymous users and network infrastructure on the client's network from listening in on the communications channel, Transmission Control Protocol (TCP) is not offered for clients connecting from external networks. The Access Edge Server has a certificate issued by a well-known certificate authority (CA) that is trusted by Microsoft Windows. This allows non-domain machines outside the enterprise network to easily connect, validate, and trust the Access Edge Server certificate. This trust is necessary to prevent DNS spoofing attacks that could otherwise allow the connecting Office Communicator client to negotiate authentication and pass communications through an undesired intermediary. The Access Edge Server then uses another certificate (issued by a public or private CA) to connect securely to the Director inside the enterprise network. The Director on the internal network actually works through a SIP-based NTLM authentication handshake with Office Communicator (over these established connections) because it has access to the internal Active Directory infrastructure. Note that the Access Edge Server helps protect the internal servers against network-level attacks, validates the SIP network protocol messages that it receives, validates the domain that the client uses to log in, and then forwards requests to the internal Director.
Note
For more details on how Office Communicator uses DNS SRV records during remote access and local enterprise logins, refer to Chapter 4. The Examining the Technical Details Behind the Login Process section explains which DNS SRV records are queried and how the result is interpreted. For remote access, the sipexternal.<domain> host (A) record and the _sip._tls.<domain> server (SRV) records are of interest.
The recommended single-site edge topology is similar to the single edge server topology except that in single-site edge topology, the A/V Edge Server is installed on a separate physical server. (See Figure 6-2.) Because the A/V Edge Server is more bandwidth-intensive than the other edge servers, greater scalability is provided by having it installed on its own machine, which alleviates load on the server hosting the Access Edge Server and Web Conferencing Edge Server and provides the most processing and network resources for the A/V Edge Server. Both physical servers reside in the edge network and are insulated by firewalls. The firewall rules for each server can be managed independently to prevent intrusions on one server from affecting the capabilities of the other.
If the remote Office Communicator client makes use of audio and video conferencing features, the connection point goes through the separate A/V Edge Server. After Office Communicator uses TLS to authenticate with the Access Edge Server, the client then makes a connection to the A/V Edge Server over the Simple Traversal of User Datagram Protocol (UDP) through Network Address Translators (NATs) protocol. (The simplified protocol name is STUN.)
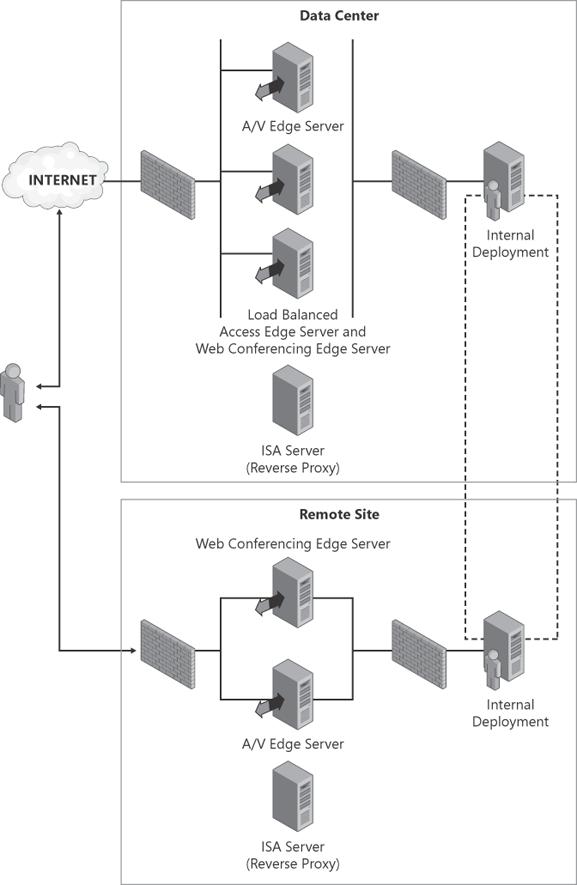
The recommended multisite edge topology is similar to single-site edge topology for the primary site; however, for greater scalability, it has a pair of load-balanced Access and Web Conferencing Edge Servers. The remote site simply has A/V and Web Conferencing Edge Servers installed to prevent introducing media session delays by routing media through the local site. (See Figure 6-3.) Because the domain DNS SRV records publish only the main site (for federation and remote access purposes), the SIP traffic from remote Office Communicator clients always travels through the main site with this topology. Because the SIP traffic is not bandwidth intensive like media traffic, the Access Edge Servers can be centrally managed at the main site.