We have already established the irrefutable importance of security in application design and development. It should be quite clear that security is a primary engineering tenet within application development. Microsoft embraced this belief as part of the larger Trustworthy Computing (TWC) initiative, which began in 2002, and has subsequently created a security-focused culture within the company. Although the TWC initiative is broader than just security, several great security processes and practices have emerged from TWC and are incorporated across the company today. Let’s review the security principles outlined by the TWC initiative that developers should incorporate within the application development life cycle to avoid introducing security bugs into their software.
Embracing a culture of security within your company is an important first step in designing and building secure applications. This requires that all disciplines, including program management, development, and test, incorporate security-focused principles into their respective work streams. From application feature conception to design and testing, security should always be top of mind when building software. Let’s review the specific tactics that application development teams should incorporate into their existing processes to help foster a security-focused culture.
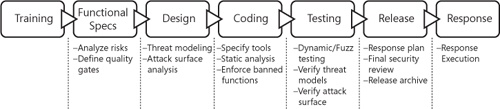
Most application development organizations already have a well-defined process established for building applications. Augmenting that process to include security-related objectives and tasks will ensure that application development teams spend less time fixing security bugs toward the end of the release cycle and ultimately release a more secure product. Simply stated, the applications that your team builds can only be secure if there is a security process interwoven into the application development process. At Microsoft, the security process that is incorporated into product release cycles is called the Microsoft Security Development Lifecycle (SDL). The SDL represents a holistic approach to application security and privacy that includes milestone-based goals and objectives ranging from individual team member security training to specific design, implementation, and testing tactics. It is important that application development teams incorporate a process that will ensure repeatable and reliable delivery of secure applications. The SDL is an example of such a process. A visual representation of the SDL and its milestone-based goals has been provided in 6-1.
Note
Implementing an SDL within your company is a commitment that may seem like a large amount of work. However, the benefit to your application’s users in terms of increasing security quality is undeniable. For more information on each step of the Microsoft Security Development Lifecycle, I recommend reading more at http://msdn.microsoft.com/en-us/library/84aed186-1d75-4366-8e61-8d258746bopq.aspx.
Application development teams should augment their existing software development processes to include a holistic focus on security. This will ensure that a culture of security is encouraged across the company, which will ultimately lead to the construction and delivery of more secure software. Despite the criticism from Microsoft’s rivals about the company’s historical approach to security, the SDL outlined by the TWC initiative is an example that other software development organizations should definitely learn from. Microsoft now finds itself with a much better reputation since the TWC initiative began.
In addition to establishing a security process within your organization, it is also important to apply specific strategies to ensure secure application designs. Defense-in-depth is a technique that has been proven to reduce the exposure of vulnerabilities in application designs. Defense-in-depth is actually a military strategy that intends to delay the advances of an attacker rather than actually prevent it. It is based on the idea that an attacker loses momentum over a period of time, or as the attacker is required to cover a broader attack surface. In software development, this technique is used to apply multiple layers of security around the application, so that if the outer layer were to be penetrated, the inner layers would continue to secure the application, thus preventing the application from immediate compromise. By applying defense-in-depth, even a series of imperfect attack mitigations can stop a potential exploit. Developers should apply this strategy when designing application architectures to ensure that critical infrastructure and applications are protected by multiple layers of security.
As a means to help developers apply the defense-in-depth technique, Microsoft created a strategy that is referred to as the SD3+C. This acronym stands for secure by design, secure by default, and secure in deployment and communication. This strategy establishes four major security tenets, each of which contains a set of best practices for securing applications. It is recommended that application developers adhere to these tenets during the design and implementation of their application code to ensure that security best practices are properly incorporated. Let’s review these tenets and best practices in greater detail.