Chapter 4. System Infrastructure Control
This chapter helps you prepare for the Certified Information Systems Auditor (CISA) exam by covering the following ISACA objectives, which include understanding the importance of system infrastructure and control.
Tasks
Perform post-implementation review of systems and/or infrastructure to ensure that they meet the organization’s objectives and are subject to effective internal control.
Evaluate the processes by which systems and/or infrastructure are developed/acquired and tested to ensure that the deliverables meet the organization’s objectives.
Perform periodic reviews of systems and/or infrastructure to ensure that they continue to meet the organization’s objectives and are subject to effective internal control.
Knowledge Statements
Knowledge of risk management practices applied to projects
Knowledge of control objectives and techniques that ensure the completeness, accuracy, validity, and authorization of transactions and data within IT systems applications
Knowledge of enterprise architecture related to data, applications, and technology (e.g., distributed applications, web-based applications, web services, n-tier applications)
Programmed and Manual Application Controls
Auditing Systems Development, Acquisition, and Maintenance
This chapter addresses system infrastructure control. As such, this chapter discusses application controls and how these controls can be audited to verify their functionality. This chapter also examines business application systems and looks at the risks with such items as electronic funds transfer and electronic banking. A CISA candidate should review the following primary topics for the exam:
![]() Application controls for input, output, and processing
Application controls for input, output, and processing
![]() Data integrity auditing and verification of the accuracy of controls
Data integrity auditing and verification of the accuracy of controls
![]() Electronic commerce and electronic data interchange
Electronic commerce and electronic data interchange
![]() Security issues surrounding email
Security issues surrounding email
![]() How decision support systems are used for efficiency and effectiveness
How decision support systems are used for efficiency and effectiveness
Introduction
Before an IS auditor can begin an audit of infrastructure or application systems, the auditor must understand the environment. Modern application processes can be highly complex. As an example, consider a few steps in a simple e-commerce transaction:
1. The customer must browse the merchant’s online store.
2. The customer must complete an order form and store their personal information and credit card number.
3. The customer must review and approve the form.
4. The merchant must send a notice to the customer that the order was received and being processed. About the same time, the credit card information should be making its way through the bank’s payment system.
5. The bank must verify the credit card and send payment to the merchant.
6. The order is shipped.
This is a high-level overview of the steps. This level of complexity means that an auditor must understand many controls in relation to the business. This process can be highly complex. Issues such as when the order was processed, where the customer’s data is stored, where the product is shipped from, and how the financial transaction occurs are all relevant isssues. Without this knowledge, the auditor cannot verify that proper security measures have been implemented.
Programmed and Manual Application Controls
Knowledge Statement
![]() Knowledge of control objectives and techniques that ensure the completeness, accuracy, validity, and authorization of transactions and data within IT systems applications
Knowledge of control objectives and techniques that ensure the completeness, accuracy, validity, and authorization of transactions and data within IT systems applications
This section discusses programmed and manual application controls as they relate to input, output, and processed information. These controls can be either manually or automatically programmed. Automated controls include validation and edit checks, programmed logic functions, and controls. Manual controls are those that auditors or staff manually verify, such as the review of reconciliation reports, and exception reports. The purpose of both automated and manual controls is to verify the following:
![]() The validity of data processed is ensured.
The validity of data processed is ensured.
![]() The accuracy of data processed is ensured.
The accuracy of data processed is ensured.
![]() The data is stored so that controls maintain the security of the data so that accuracy, validity, confidentiality, and integrity of the data is maintained.
The data is stored so that controls maintain the security of the data so that accuracy, validity, confidentiality, and integrity of the data is maintained.
![]() Processed data is valid and meets expectations.
Processed data is valid and meets expectations.
Auditors can perform control checks by doing the following:
![]() Discovering and identifying application components so that transaction flow can be analyzed.
Discovering and identifying application components so that transaction flow can be analyzed.
![]() Determining the appropriate audit procedures to perform tests to evaluate strengths and weaknesses of the application.
Determining the appropriate audit procedures to perform tests to evaluate strengths and weaknesses of the application.
![]() Analyzing test results.
Analyzing test results.
![]() Validating the results and reporting on the application’s effectiveness and efficiency. The results should also be measured against good programming standards and compared against management’s objectives for the application.
Validating the results and reporting on the application’s effectiveness and efficiency. The results should also be measured against good programming standards and compared against management’s objectives for the application.
Note
Setting the Scope of the Review The audit engagement letter should set out clearly the types of matters that will be reviewed during the audit and the scope of such review.
Business Process Controls
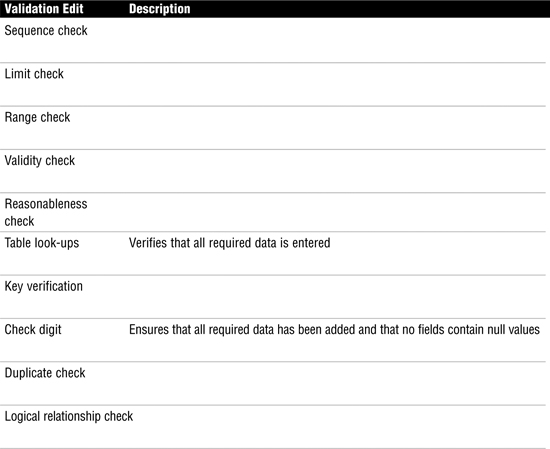
Before controls can be examined, an auditor must understand the business strategy and the business process. To understand business objectives and strategy, start with the company’s business plan. Next, review the long- and short-term goals. Long-term goals are considered strategic and focus on activities planned for the next three to five years. Short-term goals are tactical and address immediate concerns that are no more than 18 months into the future. Finally, review the organization’s goals. After reviewing this background information, examine process flow charts. Next, review application controls, data integrity controls, and controls for business systems. Table 4.1 provides an overview of input, processing, and output controls.
Table 4.1 Business Process Controls
The following sections look at each category of control in more detail, beginning with input controls, moving on to processing controls, and finally covering output controls.
Input Controls
When reviewing input controls, the auditor must ensure that all transactions have been entered correctly. Whatever controls are used, they should be capable of checking that input is valid. This becomes important because in many automated systems, the output of one system is the input of another. In such situations, data should be checked to verify the information from both the sending and receiving applications.
Controls can be either automated authorization or manual authorization. As an example, consider the last time you were at your local discount store and, at checkout, a sales item did not ring up at the advertised price. Most likely, you had to wait for the clerk to signal a supervisor to advise of the error in the sales price. The supervisor then had to enter a second-level password to authorize the price change. This is a manual authorization control. Other types of authorization controls include these:
![]() Signatures on forms or documents approving a change.
Signatures on forms or documents approving a change.
![]() Password controls that are required to process a change.
Password controls that are required to process a change.
![]() Client identification controls that allow only certain clients to authorize the change. As an example, the clerk at the local market cannot authorize a price override, yet the manager can by using their access login.
Client identification controls that allow only certain clients to authorize the change. As an example, the clerk at the local market cannot authorize a price override, yet the manager can by using their access login.
A batch control is a second type of input control. Batch controls combine transactions into a group. This group then has a value assigned. The total of this transaction can be based on dollar amounts, total counts, total document numbers, or hash totals. Figure 4.1 illustrates an example of a batch control. Notice that the billing system has a count of 312. This number should match the count in the receivables system.
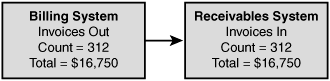
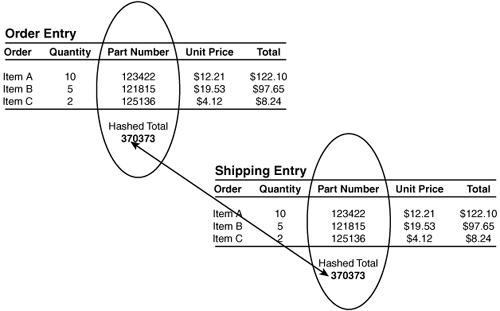
Total dollar amounts verify that each item totals up to the correct batched total amount. Total item counts verify the total counts match. As an example, if 312 items were ordered, 312 items should have been processed and shipped. Total document numbers verify that the total number of documents in the batch equals the total number of documents processed. Documents could be invoices generated, orders, or any document count that is used to track accuracy. Hash totals are generated by choosing a selected number of fields in a series of transactions. These values are computed again later to see if the numbers match. An incorrect value indicates that something has been lost, entered incorrectly, or corrupted somehow. As an example of hashing, consider that the totaling of part numbers on an order normally provides no usable value, but the total can be compared to the shipping order to verify accuracy, as illustrated in Figure 4.2. Notice how both the order and shipping entry are equal at 370373.
Note
Hash Totals The use of hash totals is similar to how cryptographic hashing algrothims such as MD5 or SHA1 are used to verify integrity.
Exam Alert
Batch Controls Be aware that the CISA exam might ask questions about what is considered a valid batch control. Test candidates should understand each type and know that batch controls are used to detect loss, duplication, or corruption of data.
Batch controls must be combined with the proper follow-up procedures. For example, if rejected items are resubmitted, controls must be in place to detect this anomaly. Additionally, procedures must be in place to follow up on any discrepancies found when batch controls are performed. Batch balancing is used to verify that the batch was processed correctly. This can be accomplished by comparing computer-generated batch quantities to manual batch counts. Control accounts can also be used. Control accounts write an initial batch value to a data file. After processing, the processed value is compared to the initially stored value. An example of this can be seen in batch registers. Batch registers allow for the manual recording of batch totals. These are saved and then compared to totals that are generated by the system. If they do not agree, the batch can be rejected.
Processing Controls
Processing controls are used to ensure the accuracy, completeness, and timeliness of data during online or batch processing. Controls should be in place to verify that data is processed only through authorized routines. Processing controls should be designed to detect problems and initiate corrective action. If procedures are in place to override these controls, their use should be logged. Individuals who have the ability to override these controls should not be the same ones responsible for reviewing the log. Edit controls can be used after the data has been entered into the system but before it has been processed. Edit controls can be considered a type of preventive control. Table 4.2 describes edit controls, and Figure 4.3 shows an example of existence and completion checks.
Table 4.2 Processing Edit Controls
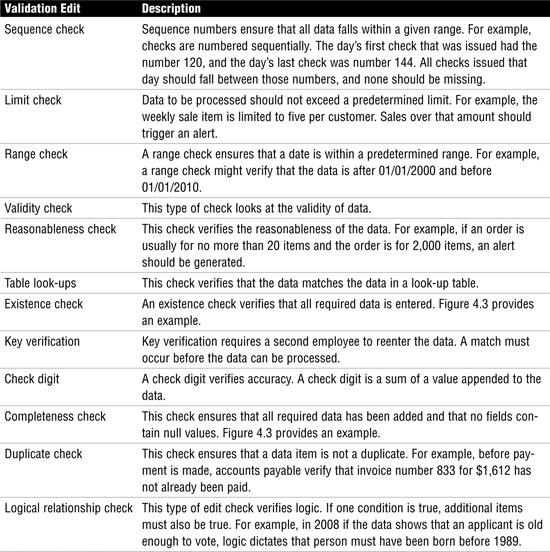
Figure 4.3 Existence and completeness check.
Exam Alert
Validation Edit Controls CISA exam candidates must understand that validation edit controls are applied before processing and are therefore considered a type of preventive control.
Now that you understand edit controls, turn your attention to processing controls used to ensure that the data remains unchanged until processed by an authorized process. Table 4.3 outlines the control techniques used to protect the integrity of the data.
Table 4.3 Processing Control Techniques

Exam Alert
Run-to-Run Totals The CISA exam might ask about specific process-control techniques. For example, run-to-run totals enable you to ensure the validity of data through various stages of processing.
Data File Controls
Data files or database tables can be one of four types:
![]() System-control parameters control values such as how much money can be transferred in a single transaction with approval.
System-control parameters control values such as how much money can be transferred in a single transaction with approval.
![]() Standing data refers to information that is somewhat static. An example of standing data is a customer’s name, address, and phone number. Because these values do not frequently change, an alteration should be controlled and should require authorization.
Standing data refers to information that is somewhat static. An example of standing data is a customer’s name, address, and phone number. Because these values do not frequently change, an alteration should be controlled and should require authorization.
![]() Balance data refers to various values and totals that might be held temporarily during processing. These values should be strictly controlled; any manual alteration of these values should require authorization and be logged.
Balance data refers to various values and totals that might be held temporarily during processing. These values should be strictly controlled; any manual alteration of these values should require authorization and be logged.
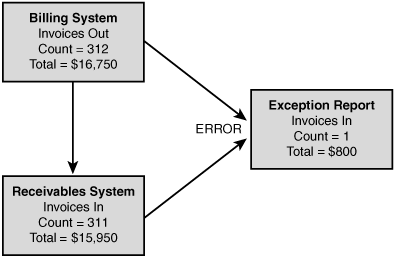
![]() Transaction files deal with the transmission of information between two systems or applications. Transaction files should be managed with exception reports or validation checks. Figure 4.4 shows an example of this in which the billing and receivables do not match. This, in turn, generates an exception report that notes the problem.
Transaction files deal with the transmission of information between two systems or applications. Transaction files should be managed with exception reports or validation checks. Figure 4.4 shows an example of this in which the billing and receivables do not match. This, in turn, generates an exception report that notes the problem.
The four data file types can have various controls applied to them:
![]() Before-and-after image reports—By taking a snapshot of computer data before and after a transaction, you can determine what changes have been made to data.
Before-and-after image reports—By taking a snapshot of computer data before and after a transaction, you can determine what changes have been made to data.
![]() Maintenance error reporting—Procedures should be established to verify that any errors or exceptions are rectified and reconciled. The employee who generated the transaction should not have the authorization to clear the error.
Maintenance error reporting—Procedures should be established to verify that any errors or exceptions are rectified and reconciled. The employee who generated the transaction should not have the authorization to clear the error.
![]() Internal and external labeling—Internal labeling ensures that proper data files are used and that all information is present. External labeling applies to removable media.
Internal and external labeling—Internal labeling ensures that proper data files are used and that all information is present. External labeling applies to removable media.
![]() Data file security—This control should ensure that individuals who process data cannot bypass validity checks, clear logs, or alter stored data.
Data file security—This control should ensure that individuals who process data cannot bypass validity checks, clear logs, or alter stored data.
![]() One-to-one checking—Documents entered for processing should match processed totals.
One-to-one checking—Documents entered for processing should match processed totals.
![]() Transaction logs—Transactional information such as date, time, terminal, user ID, and so on should be recorded to create a usable audit trail.
Transaction logs—Transactional information such as date, time, terminal, user ID, and so on should be recorded to create a usable audit trail.
![]() Parity checking—Data integrity should be verified in the event of a transmission error.
Parity checking—Data integrity should be verified in the event of a transmission error.
Output Controls
Output controls are designed to provide assurance in data that has completed processing. Output data must be delivered accurately in a timely manner so that it is useful in the decision-making process. Output controls should be designed to ensure that the data is distributed and stored in a secure manner. Sensitive data should have sufficient controls to monitor usage and control who has access to it. These controls will vary, depending on whether the information is centrally stored or distributed to end-user workstations.
Note
Output Printer Controls Auditors should be aware that one way to control distribution is to place controls on data that limit what information is to be printed and to whose printer it should be directed. For example, some reports might be configured so that they are printed only to the supervisor’s printer. Software printing controls are another example of this. Products such as Adobe PDF and others can be used to limit printing or embed password controls for viewing or printing.
Per ISACA, output controls should address the following:
![]() Logging and storage of sensitive negotiable and critical forms
Logging and storage of sensitive negotiable and critical forms
![]() Negotiable instruments, forms, and signatures that are computer generated
Negotiable instruments, forms, and signatures that are computer generated
![]() Distribution control
Distribution control
![]() Balancing and reconciliation of control totals
Balancing and reconciliation of control totals
![]() Output errors that should be logged and reviewed
Output errors that should be logged and reviewed
![]() Retention records that specify how long output data should be stored or maintained
Retention records that specify how long output data should be stored or maintained
Auditing Application Controls
Tasks
![]() Perform periodic reviews of systems and/or infrastructure to ensure that they continue to meet the organization’s objectives and are subject to effective internal control.
Perform periodic reviews of systems and/or infrastructure to ensure that they continue to meet the organization’s objectives and are subject to effective internal control.
![]() Evaluate the processes by which systems and/or infrastructure are developed/acquired and tested to ensure that the deliverables meet the organization’s objectives.
Evaluate the processes by which systems and/or infrastructure are developed/acquired and tested to ensure that the deliverables meet the organization’s objectives.
Application software is the engine behind automated business transactions. These systems might process payroll, manage inventory, or even invoice and bill customers. Most users see only the application interface, but what does the application really do? The auditor should be most concerned about the limits, controls, and rules that define how the application interacts with the organization’s data.
Understanding the Application
One of the first questions the auditor should ask is, what does the application do? How this question is answered will vary from organization to organization and from case to case. The auditor can start by asking for documentation. If the application was developed in-house, system-development methodology documents might be available. These documents will provide the auditor with insight into what the user requirements were and what cost-benefit analysis was done to justify development of the application. Functional design specifications should also be reviewed. These specifications are a great resource because they detail how the application is designed and what it was developed to achieve. If the application has been in use for a while, program-change documents that list any changes or updates also might exist. Checking outstanding bugs and issues in release note documentation and software build information also can provide good information. After reviewing these documents, the auditor can develop an application flowchart to accomplish the following:
![]() Validate every input to the system against the applicable criteria
Validate every input to the system against the applicable criteria
![]() Review logical access controls and authorization controls
Review logical access controls and authorization controls
![]() Evaluate exception handling and logging
Evaluate exception handling and logging
![]() Examine data flow to find control weaknesses
Examine data flow to find control weaknesses
With an understanding of the application and knowledge of how transactions flow through the application, the auditor can move to the next step: observing and testing.
Observation and Testing
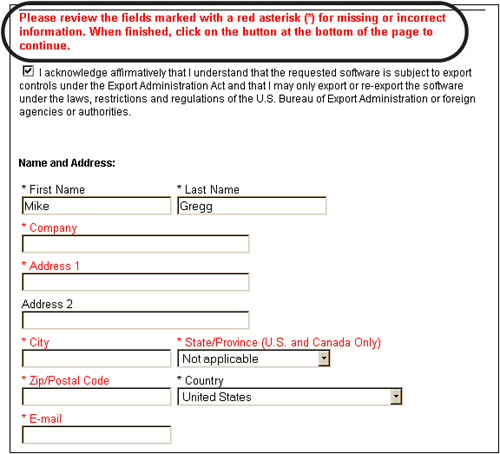
A big part of an auditor’s job involves observation. Auditors are tasked with observing how users interact with the application. Auditors should also test the limits of the application. Buffer overflows are one concern. Buffer overflows can occur when attackers try to stuff more than the total number of characters allowed in a field. The design specification might state that the application does not accept negative numbers, but is that actually the case? If you enter a negative number or a negative quantity in a field, will the application actually accept it? It shouldn’t. Figure 4.5 presents an example of a poorly constructed application entry form. Notice the grand total of –$2,450.99.
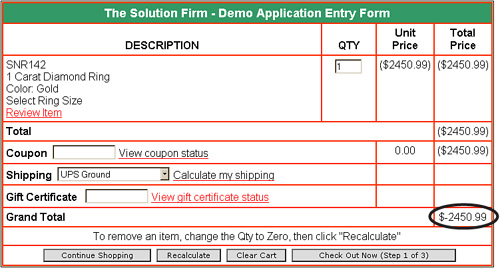
Even if the application was to accept an invalid entry as shown in Figure 4.5, activity reports should track the IP address or terminal number used to complete the entry. Logging should also track the date and time of activity. In addition, invalid entries should be logged so that violation reports can be created.
Caution
Tracking Violators Tracking violators can be a real challenge in the distributed world of the Internet. Proxy servers, anonomizers, and network address translation (NAT) make the prospect of identifying an individual user much harder.
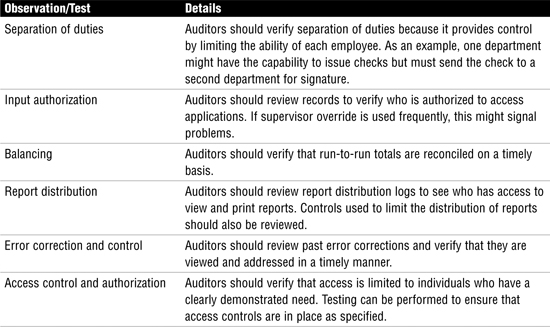
When working with applications, auditors should observe and test the items listed in Table 4.5.
Table 4.5 Observation and Test
Data Integrity Controls
Data integrity testing is performed to ensure the accuracy, completeness, consistency, and authorization of data. Integrity testing is considered a substitutive test. Data can be stored in files or in databases.
Note
Data Integrity Testing Data integrity testing is the best method of examining the accuracy, completeness, consistency, and authorization of data. Data integrity testing can be used to find failures in input and processing controls.
Data stored in databases has unique requirements because it differs from data stored or processed by an application. Database integrity testing can be performed through several methods. Referential integrity guarantees that all foreign keys reference existing primary keys, as demonstrated in Figure 4.6.
Figure 4.6 Referential integrity.
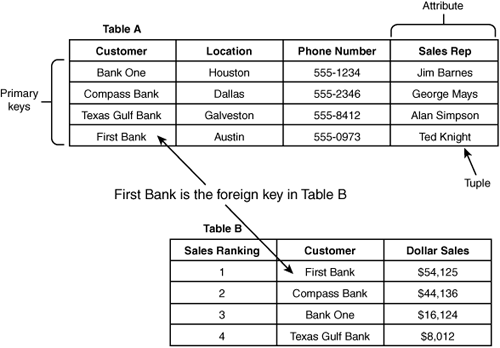
Controls in most databases should prevent the primary key from being deleted when it is linked to existing foreign keys. Relational integrity ensures that validation routines test data before it is entered into a database and that any modification can be detected. A third integrity control is entity integrity. As an example, in Figure 4.6, the primary keys are names of banks; entity integrity ensures that each tuple contains a primary key. Without the capability to associate each primary key with a bank, entity integrity cannot be maintained and the database is not intact.
Online data integrity has somewhat different concerns because online databases most likely are distributed or clustered for performance and fault tolerance. Online databases work in real time. This might mean that several databases must be updated simultaneously. These complexities mean that the ACID test should be applied:
![]() Atomicity, to divide work so that the results are either all or nothing
Atomicity, to divide work so that the results are either all or nothing
![]() Consistency, to ensure that transactions are processed only if they meet system defined integrity constraints
Consistency, to ensure that transactions are processed only if they meet system defined integrity constraints
![]() Isolation, to ensure that each transaction is isolated from all others until complete
Isolation, to ensure that each transaction is isolated from all others until complete
![]() Durability, to ensure that when a transaction is processed, the transaction cannot be rolled back and is accurate
Durability, to ensure that when a transaction is processed, the transaction cannot be rolled back and is accurate
Application System Testing
Application testing is a critical part of the audit process. Testing enables the auditor to evaluate the program, review its controls, and monitor the transaction process. The primary methods used for application testing are as follows:
![]() Snapshots—These are used to monitor and record the flow of data through an application. Although snapshots require an in-depth knowledge about the application, they are useful in verifying logic.
Snapshots—These are used to monitor and record the flow of data through an application. Although snapshots require an in-depth knowledge about the application, they are useful in verifying logic.
![]() Mapping—Unlike snapshots, mapping verifies program logic that might not have been performed or tested. This is useful because it might detect undiscovered problems.
Mapping—Unlike snapshots, mapping verifies program logic that might not have been performed or tested. This is useful because it might detect undiscovered problems.
![]() Tracing and tagging—Tagging is used to mark selected transactions. Tracing enables these tagged transactions to be monitored.
Tracing and tagging—Tagging is used to mark selected transactions. Tracing enables these tagged transactions to be monitored.
![]() Using test data—This type of test uses test data to verify program operation. This technique requires little knowledge of the environment and does not require the review of the source code.
Using test data—This type of test uses test data to verify program operation. This technique requires little knowledge of the environment and does not require the review of the source code.
![]() Base case system evaluation—This compressive test uses test data that was developed to thoroughly test the environment. This method is useful because it requires great effort and close cooperation among various internal groups.
Base case system evaluation—This compressive test uses test data that was developed to thoroughly test the environment. This method is useful because it requires great effort and close cooperation among various internal groups.
![]() Parallel operation—Both old and new systems process data so that the results can be compared.
Parallel operation—Both old and new systems process data so that the results can be compared.
![]() Integrated test facility—This test method creates a fictitious entity in a database to process sample test transactions at the same time live input is being processed.
Integrated test facility—This test method creates a fictitious entity in a database to process sample test transactions at the same time live input is being processed.
![]() Parallel simulation—Another useful audit tool uses computer programs to simulate program logic.
Parallel simulation—Another useful audit tool uses computer programs to simulate program logic.
![]() Transaction selection—This method of testing uses audit software to determine what transactions should be processed.
Transaction selection—This method of testing uses audit software to determine what transactions should be processed.
Note
Base case system evaluation Using test data that was developed in a comprehensive manner is known as base case system evaluation.
Continuous Online Auditing
Testing a system once before rollout might provide a baseline of information, but it offers no ongoing feedback on the operation of the application. Continuous online auditing gives auditors the tools needed to perform ongoing monitoring. Continuous online auditing produces audit results either at real-time intervals or after a short period of time. This method actually can reduce costs because the need for conventional audits might be reduced or eliminated. In a conventional audit, the auditor has a limited amount of time to design tests and examine data. Continuous online auditing greatly increases the quantity and scope of data available to the auditor. With continuous auditing, the auditor can evaluate data on an ongoing schedule and alert management to problems as needed. Paperwork is reduced and the auditor can electronically examine application data and report problems directly as needed.
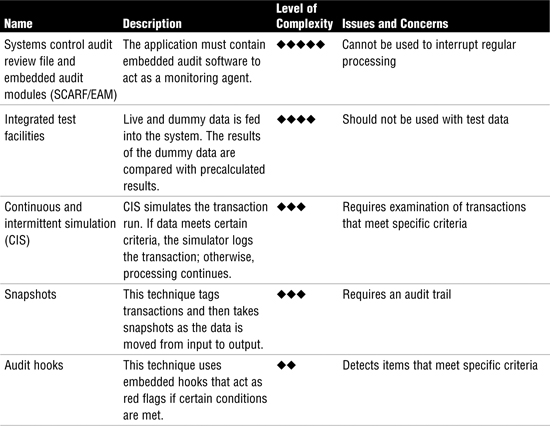
Continuous online auditing also increases security. Consider a bank that allows online access to customer accounts and funds. Although such systems are convenient for users, they present additional risk for the bank. Continuous online auditing allows the bank to monitor transactions as they occur. If some type of misuse occurs, the time between the misuse and discovery is greatly reduced. If additional controls are needed, they can be deployed in a shortened time frame. Overall, five continuous audit techniques exist, as described in Table 4.6.
Table 4.6 Continuous Audit Techniques
Exam Alert
Continuous Audit Techniques The CISA exam might ask you to describe the unique attributes of each continuous audit technique. As an example, you should understand that snapshots require an audit trail.
Review Break
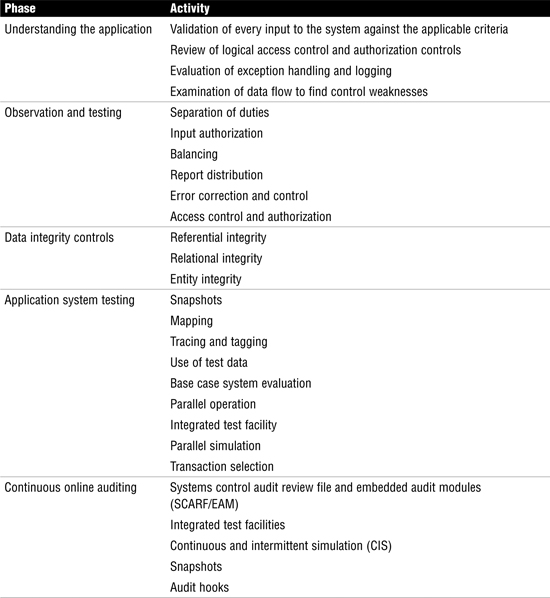
Auditing application controls is a big piece of system infrastructure. Table 4.7 describes the four major steps and activities performed during each phase of application auditing.
Table 4.7 Review Break: Auditing Applications
Auditing Systems Development, Acquisition, and Maintenance
Task
![]() Perform post-implementation review of systems and/or infrastructure to ensure that they meet the organization’s objectives and are subject to effective internal control.
Perform post-implementation review of systems and/or infrastructure to ensure that they meet the organization’s objectives and are subject to effective internal control.
Knowledge Statement
![]() Knowledge of risk management practices applied to projects
Knowledge of risk management practices applied to projects
In the past, software development consisted of one lone programmer writing code to meet the needs of a small group or department. Today’s systems are much more complex, in that systems might be used by different branches located in different areas of the world or accessed by users through the Internet. Many more legal regulations and requirements, such as Safe Harbor or Sarbanes-Oxley, also must be satisfied. This means that coding must be performed by teams of programmers with the help of architects, analysts, testers, auditors, and end users that must all work together. To manage such a large endeavor, the system development lifecycle was created.
The auditor role in this process is to work with the development team to ensure that the final product meets user requirements while possessing adequate controls. Throughout the system development lifecycle, the auditor should work with the development team to minimize risks and exposures. The following list provides the general steps an auditor should follow during the development process.
4.1 Auditing Systems Development
1. Determine the objectives and user requirements of the project.
2. Perform a risk assessment that identifies threats, risks, and exposures.
3. Assess existing controls to determine whether they will adequately reduce risk to acceptable levels. Discuss any needed changes with the development team.
4. Monitor the development process and evaluate controls as they are designed and created.
5. Evaluate the system during rollout, and review audit mechanisms to ensure that they function as designed.
6. Take part in any post-implementation reviews.
7. Verify system-maintenance procedures.
8. Review production library control to ensure the needed level of security.
Project Management
Implementing good application controls is just part of the task. Organizations must also use good project-management techniques. The auditor should be involved throughout the development process to minimize risk and ensure that adequate controls are in place. An auditor must evaluate the level of oversight that a project committee has over the process. Other issues, such as reporting, change control, and stakeholder involvement, are also important. Table 4.8 lists additional issues that the auditor should perform per ISACA recommendations. Although this is not a complete list, it should give you an overall idea of how important it is for the auditor to play a proactive role in the process.
Table 4.8 Audit Controls and Quality-Assurance Checks
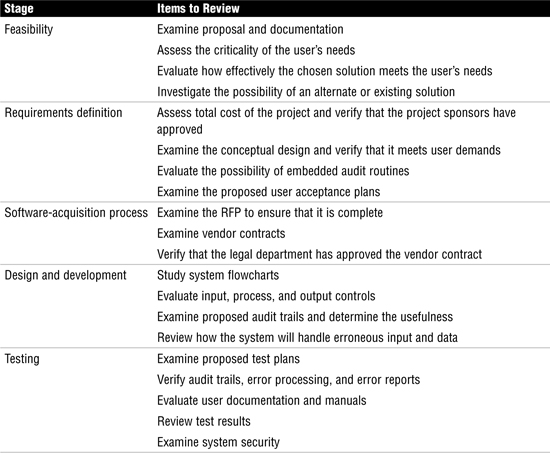

Exam Alert
Project Management Audit Activities The CISA exam expects candidates to understand what activities occur at each stage of the project-management process. As an example, user-acceptance test plans are reviewed at the requirements definition stage.
Business Application Systems
Knowledge Statement
![]() Knowledge of enterprise architecture related to data, applications, and technology e.g., distributed applications, web-based applications, web services, n-tier applications)
Knowledge of enterprise architecture related to data, applications, and technology e.g., distributed applications, web-based applications, web services, n-tier applications)
Audit programs require an understanding of the application being reviewed. One good place to start is reviewing application system flowcharts. Business applications can be categorized according to where they are used or by their functionality. Business application programs are used for accounting, payroll, inventory, sales, and so on. These systems can be used in e-commerce systems, for web-based applications, in electronic banking, and even for electronic payment systems. The following sections describe each of these systems in greater detail.
Tip
Flowcharts Flowcharts are one of the first things an auditor should examine when evaluating business application systems.
E-Commerce
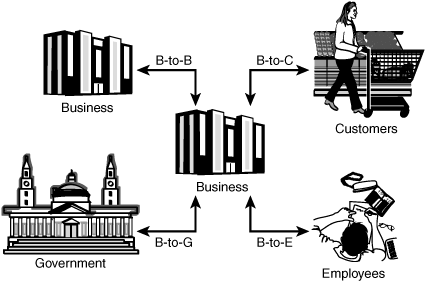
Electronic commerce, or e-commerce, is about the buying, selling, and servicing of goods via the Internet. The process usually begins with a company advertising its goods on a website. When a buyer finds the goods he or she is looking for, the buyer adds them to a shopping cart. Upon checkout, the buyer is redirected to a secure web page so that credit card and shipping information can be entered. E-commerce saw tremendous growth in the 1990s because it enabled businesses to offer better prices than in brick-and-mortar stores. E-commerce has none of the overhead of these traditional models. Although that model has somewhat held, many companies have moved to a bricks-and-clicks model that supports both online and offline presences. E-commerce models can be broken down into four basic categories (see Figure 4.7):
![]() Business to business (B-to-B)—Transactions between two or more businesses, such as a business and its suppliers.
Business to business (B-to-B)—Transactions between two or more businesses, such as a business and its suppliers.
![]() Business to consumer (B-to-C)—Transactions between businesses and consumers. This area is one of the greatest growth areas for e-commerce. For companies that don’t sell products directly to their customer, there are brokers that can act as middlemen to sell products for them.
Business to consumer (B-to-C)—Transactions between businesses and consumers. This area is one of the greatest growth areas for e-commerce. For companies that don’t sell products directly to their customer, there are brokers that can act as middlemen to sell products for them.
![]() Business to government (B-to-G)—Transactions between business and government, such as the online filling of legal documents and reports.
Business to government (B-to-G)—Transactions between business and government, such as the online filling of legal documents and reports.
![]() Business to employee (B-to-E)—Transactions between business and employees. This model can be seen when organizations set up internal websites and portals for employee services such as health care, job benefits, and payroll.
Business to employee (B-to-E)—Transactions between business and employees. This model can be seen when organizations set up internal websites and portals for employee services such as health care, job benefits, and payroll.
E-commerce adds an additional level of challenge to the organization because data and applications must now protect availability, integrity, and confidentiality 24 hours a day, seven days a week. Companies must also be careful in handling customers’ personal information and payment information such as credit cards. Authentication and nonrepudiation are important aspects of this because customers need to know that they are really dealing with the company, not an impostor.
Note
B-to-C Business-to-consumer e-commerce offers the greatest capability to reshape business models.
Electronic Data Interchange
Electronic data interchange (EDI) is a technology designed to facilitate the exchange of data between computer systems. It was designed to bridge the gap between dissimilar systems. EDI is used to exchange invoices, shipping notices, inventory updates, and so on in a format that both the sending and receiving systems can understand. ANSI X12 is the most common of the formats used. EDI offers real benefits for organizations: It reduces paperwork and results in fewer errors because all information is transmitted electronically. Traditional EDI consists of the following components:
![]() Communications handler—The method used to transmit and receive electronic documents. Much of this activity occurs via the Internet.
Communications handler—The method used to transmit and receive electronic documents. Much of this activity occurs via the Internet.
![]() EDI interface—The EDI interface handles data as it is being passed between the two organizations’ applications. Security controls are usually placed here. The EDI interface is comprised of the EDI translator and the application interface.
EDI interface—The EDI interface handles data as it is being passed between the two organizations’ applications. Security controls are usually placed here. The EDI interface is comprised of the EDI translator and the application interface.
![]() Application system—The application system is the program responsible for processing documents that have been sent or received. Additional controls are usually not placed here.
Application system—The application system is the program responsible for processing documents that have been sent or received. Additional controls are usually not placed here.
Note
Value-added network (VAN) Before the rise of the Internet, VANs, which are private networks, were the primary communications handlers. The Internet disrupted the VAN’s business because many companies found it cheaper to move data via the Internet.
EDI adds a new level of concern to organizations because documents are processed electronically. One big concern with EDI is authorization. This means that EDI process should have an additional layer of application control. These controls can be used to address the issue of authorization, as well as lost or duplicate transactions and issues of confidentiality and invalid distribution. Some common controls include these:
![]() Transmission controls to validate sender and receiver
Transmission controls to validate sender and receiver
![]() Manipulation controls to prevent unauthorized changes to data
Manipulation controls to prevent unauthorized changes to data
![]() Authorization controls to authenticate communication partners
Authorization controls to authenticate communication partners
![]() Encryption controls to protect the confidentiality of information
Encryption controls to protect the confidentiality of information
Auditors should seek to verify that these common controls have been implemented. Other controls include the deployment of audit monitors, which are devices used to capture EDI activity as it is sent or received. The auditor should also review systems that process inbound transactions to make sure that each transaction is properly logged, as well as use transaction totals to verify that totals agree with those collected by trading partners.
Caution
EDI and Internal Controls The impact of EDI on internal controls means fewer opportunities for review and authorization.
Email enables individuals to communicate electronically through the Internet or a data communications network. Although email is the most used Internet application, it raises some security concerns. Specifically, email is usually clear text, which means anyone can easily read it. Email can be spoofed to mask the true identity of the sender. Email also is a major conduit for spam, phishing, and viruses. Users need to be made aware of these problems. Email carries a number of legal and regulatory requirements which are expected to grow in the coming years. Email actually uses two underlying services—Simple Mail Transfer Protocol (SMTP) and Post Office Protocol (POP). The following steps describe basic email operation.
4.2 Basic Email Operation
1. The user opens an email program such as Outlook to create an email message.
2. After the email is created and addressed to the recipient, the user sends the email.
3. The email is forwarded to an SMTP server, which provides a message transfer agent (MTA). Just as the postal service sorts mail using a zip code, email messages are sorted by domain. As an example, in an email addressed to [email protected], the domain is thesolutionfirm. This domain identifies where the message is to be forwarded.
4. The MTA forwards the email toward its final destination.
5. The email is delivered to the destination mail server, where it waits until the recipient user retrieves it.
6. The email is retrieved using Post Office Protocol version 3 (POP3) and is displayed via Outlook on the recipient’s computer.
Users must be educated that sensitive information (such as social security numbers) should not be sent by clear-text email. If an organization has policies that allow email to be used for sensitive information, encryption should be used. This requires an evaluation of the business needs. If only some information is to be encrypted, Pretty Good Privacy (PGP) might be the best option. However, if full-time encryption is needed, the company might want to use link encryption or standards such as Secure Multipurpose Internet Mail Extensions (S/MIME) or Privacy Enhanced Mail (PEM).
Business Intelligence
The objective of business intelligence is to reduce decision-making time and increase the value of the decision. Business intelligence is much like having a crystal ball because the organization can make better decisions in a shorter period of time. Thus, the organization can compare itself to its competitors. Business intelligence is also useful in helping understand customer needs as well as the capabilities of the firm. In addition, business intelligence is useful in risk management; it can help the business spot unusual trends, odd transactions, and statistics on loss and exposure. To properly implement an infrastructure to support business intelligence, the business must design and develop a data architecture, such as the one shown in Figure 4.8.
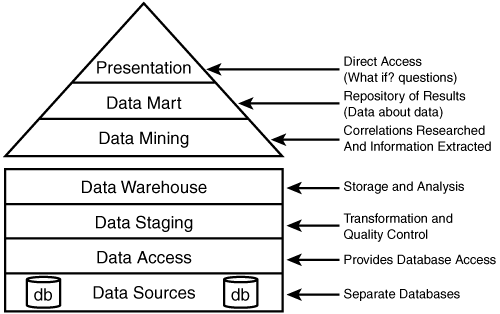
These components encompass the data architecture:
![]() Data sources—The actual data sources reside here. As an example, a grocery store might have customer reward card scanners at each checkout, so that customers using the card have each item recorded on their account.
Data sources—The actual data sources reside here. As an example, a grocery store might have customer reward card scanners at each checkout, so that customers using the card have each item recorded on their account.
![]() Data access—This layer is responsible for connecting the data sources with the data staging layer. As an example, the grocery store might process sales to customers with reward cards to a local database.
Data access—This layer is responsible for connecting the data sources with the data staging layer. As an example, the grocery store might process sales to customers with reward cards to a local database.
![]() Data staging—This layer is responsible for copying and formatting data into a standard format for the data warehouse layer.
Data staging—This layer is responsible for copying and formatting data into a standard format for the data warehouse layer.
![]() Data warehouse—Data is captured by many databases and organized into subject-oriented usable groupings. As an example, the grocery store collects all the data from various stores across the country into this one centeralized database. This allows them to drill up or drill down and obtain information by region or by item.
Data warehouse—Data is captured by many databases and organized into subject-oriented usable groupings. As an example, the grocery store collects all the data from various stores across the country into this one centeralized database. This allows them to drill up or drill down and obtain information by region or by item.
![]() Data mining—Large volumes of data are searched for specific patterns. For example, if a grocery store examines paper plate sales, does it see that the same customers purchase plastic cutlery?
Data mining—Large volumes of data are searched for specific patterns. For example, if a grocery store examines paper plate sales, does it see that the same customers purchase plastic cutlery?
![]() Data mart—At this layer resides some type of relational database that enables the user to move the data around to extract specific components that they are looking for. At this point, the user can extract data about data.
Data mart—At this layer resides some type of relational database that enables the user to move the data around to extract specific components that they are looking for. At this point, the user can extract data about data.
![]() Presentation layer—This is the top of the model, the point at which users interact with the system. This layer can include such applications as Microsoft Access and Excel.
Presentation layer—This is the top of the model, the point at which users interact with the system. This layer can include such applications as Microsoft Access and Excel.
Exam Alert
Data warehouse Exam candidates are expected to know that data warehouses are subject oriented.
Together these components provide the structure for a business intelligence system. Once developed, this system can be used in different ways, including scorecarding, customer relationship management, decision support systems, document warehouses, data mining, and supply chain management.
Note
Data warehouse accuracy The quality of data in the data warehouse is dependent upon the accuracy of the source data.
Decision Support System
A decision support system (DSS) helps managers solve problems. DSS uses models and mathematical techniques, and usually is designed with fourth-generation programming (4GL) tools. This makes the systems flexible and adaptable, yet not always as efficient as lower-level programming tools might deliver. DSS models include the following:
![]() Model-driven DSS—Uses models based on statistics, finance, or simulation. These are designed to help users make a decision. An example of this can be seen in the dicodess project at http://dicodess.sourceforge.net/.
Model-driven DSS—Uses models based on statistics, finance, or simulation. These are designed to help users make a decision. An example of this can be seen in the dicodess project at http://dicodess.sourceforge.net/.
![]() Communication-driven DSS—Designed to facilitate sharing so that more than one person can work on a task. Lotus Notes is an example of a communication-driven DSS. Lotus Notes was used for just such a purpose after 9/11 when it served as a DSS to help rebuild an emergency operation center.
Communication-driven DSS—Designed to facilitate sharing so that more than one person can work on a task. Lotus Notes is an example of a communication-driven DSS. Lotus Notes was used for just such a purpose after 9/11 when it served as a DSS to help rebuild an emergency operation center.
![]() Data-driven DSS—Can access a variety of internal and external data to analyze outcomes. Companies such as Oracle, IBM, and Microsoft are some of the leaders in this field as they build products that support data warehousing.
Data-driven DSS—Can access a variety of internal and external data to analyze outcomes. Companies such as Oracle, IBM, and Microsoft are some of the leaders in this field as they build products that support data warehousing.
![]() Document-driven DSS—Manipulates and manages unstructured information. eRoom is an example of a document-driven DSS.
Document-driven DSS—Manipulates and manages unstructured information. eRoom is an example of a document-driven DSS.
![]() Knowledge-driven DSS—Based on rules, facts, and knowledge. It is used for problem solving and to provide answers.
Knowledge-driven DSS—Based on rules, facts, and knowledge. It is used for problem solving and to provide answers.
DSS models share these common characteristics:
![]() Used for decision making
Used for decision making
![]() Used for goal seeking
Used for goal seeking
![]() Perform simulation
Perform simulation
![]() Linkable
Linkable
![]() Perform “what if” modeling
Perform “what if” modeling
![]() Provide time series analysis
Provide time series analysis
In the end, the true test of a DSS is in its capability to help the user make a better decision.
Note
Communication-driven DSS Microsoft Netmeeting is an example of a communication–driven DSS.
Artificial Intelligence and Expert Systems
Auditors should understand artificial intelligence and expert systems, and know that these systems are used to solve complex problems. An expert system is a computer program that contains the knowledge base and set of rules needed to extrapolate new facts from existing knowledge and inputted data. The Prolog and LISP programming languages, used most in developing such systems, are both considered 5GL languages. At the heart of these systems is the knowledge base.
As an example, imagine the knowledge that an auditor can obtain after 20 years on the job. Now consider the possibility of entering this knowledge into a knowledge base, enabling the expert to enter information into the program without a software engineer or programmer. Expert systems are typically designed for a specific purpose. For example, a hospital might have one designed with various types of medical information entered so that if a doctor enters the symptoms of headache, sore jaw, and trouble swallowing, the knowledge base can scan existing data to determine that the patient is suffering from tetanus. The challenge with these systems is in ensuring that accurate data is entered into the system, that access controls are in place, that the proper level of expertise was used in developing the system, and that the knowledge base is secure.
Customer Relationship Management
Customer relationship management (CRM) refers to the tools, techniques, and software companies use to manage their relationship with customers. CRM solutions are designed to track and record everything you need to know about your customers. This includes items such as buying history, budget, timeline, areas of interest, and future planned purchases. Products designed as CRM solutions range from simple off-the-shelf contact-management applications to high-end interactive systems that combine marketing, sales, and executive information. CRM typically involves three areas:
![]() Sales automation—Automation of sales force management tasks
Sales automation—Automation of sales force management tasks
![]() Customer service—Automation of customer service processes such as requests, comments, complaints, and returns
Customer service—Automation of customer service processes such as requests, comments, complaints, and returns
![]() Enterprise marketing—Automation of business enterprise information such as trends, forecasts, business environment, and competition
Enterprise marketing—Automation of business enterprise information such as trends, forecasts, business environment, and competition
Supply Chain Management
Supply chain management (SCM) is the science of matching buyers to sellers to improve the way businesses can acquire the raw materials they need to make the products or services they sell to customers. SCM begins with raw materials and ends with finished goods that have been delivered to the customer. SCM involves five basic components:
![]() Plan—Definition of the strategy used for managing resources and monitoring the supply chain
Plan—Definition of the strategy used for managing resources and monitoring the supply chain
![]() Source—The process of choosing suppliers
Source—The process of choosing suppliers
![]() Make—The manufacturing process
Make—The manufacturing process
![]() Deliver—The logistics of moving goods and services to the customer
Deliver—The logistics of moving goods and services to the customer
![]() Return—The systems developed to return non-compliant products back to the manufacturer
Return—The systems developed to return non-compliant products back to the manufacturer
SCM has become more popular as companies move to a global economy with increased competition. The opportunities SCM offers focus on key items in the supply chain process. First is the focus on keeping transportation costs as low as possible while also keeping enough raw material on hand—but no more than needed. With these two items handled properly, production improves as parts and raw materials are available as needed. This helps ensure that products are available to meet customer demand, thereby preventing loss of sales due to product shortages. The key to the SCM process is cooperation between companies in the supply chain and the business. Applying these principles can reduce inventory, increase the transaction speed by exchanging data in real time, and produce higher revenue.
Chapter Summary
Audit applications, systems, and electronic processes are important considerations for the CISA and require an understanding of process. Looking at flowcharts to learn the application is a good place to start. Next, the CISA must examine input, process, and output controls. The CISA can test and validate these controls in a variety of ways, including snapshots, mapping, and tracing and tagging. After all, application testing is a critical part of the process. Testing enables the auditor to evaluate the program and see if it really operates as specified.
The CISA must also be concerned with e-commerce. Although e-commerce provides the capability to be connected to vendors, customers, and others 24¥7, it presents a new level of risk: Individuals outside the company can access payment systems and purchase accounting systems. With so much more at risk today and so many more critical decisions to be made, many companies turn to expert systems, data mining, and decision support systems to help solve problems.
Key Terms
![]() Audit monitors
Audit monitors
![]() Balance data
Balance data
![]() Entity integrity
Entity integrity
![]() Hash totals
Hash totals
![]() Manual authorization control
Manual authorization control
![]() Referential integrity
Referential integrity
![]() Relational integrity
Relational integrity
![]() Standing data
Standing data
![]() System-control parameters
System-control parameters
![]() Total document numbers
Total document numbers
![]() Total dollar amounts
Total dollar amounts
![]() Total item counts
Total item counts
![]() Transaction files
Transaction files
Apply Your Knowledge
This chapter demonstrated the importance of various application controls. Although the ISACA does not test knowledge on the use of any type of application, Exam Prep titles are designed to provide a deeper understanding of the material. Testing application systems, performing integrity testing, and examining application code are all important concerns for the auditor. For this exercise, you will perform some software-auditing activities.
Exercises
4.1 Software Application Audit
In this exercise, you perform a basic audit of a sample of source code.
Estimated Time: 60 minutes
1. Pick an open-source software application to perform a security audit on. You can use standard Linux utilities or download a simple C program from http://www.cis.temple.edu/~ingargio/cis71/code/. After you choose a program, download it and save the source code on your local computer.
2. Determine the lines of source code. You might remember from Chapter 3, “Lifecycle Management,” that this is done in two common ways: though lines of source code or function point analysis. Count the lines of code manually and record your result here:
_________________________________________________________________
_________________________________________________________________
_________________________________________________________________
3. Next, use a tool that automatically counts the lines of code for you. For instance, you can use a tool called K-LOC, which is available for download from http://www.analogx.com/contents/download/program/kloc.htm. After downloading, install the program and enter the name and path of the source code you are auditing. Enter the lines of code that K-LOC calculates here:
_________________________________________________________________
_________________________________________________________________
_________________________________________________________________
Do the numbers entered here agree with those calculated in step 2?
4. Spend some time looking at the source code you downloaded. Look for anything that might be a problem or that you do not understand. Document any findings here:
_________________________________________________________________
_________________________________________________________________
_________________________________________________________________
5. Although a manual audit of a small program is possible, the task becomes much more difficult on larger programs. To ease that task, some programs automatically look at the code. One such tool is Rough Auditing Tool for Security (RATS), which you can download from http://www.securesoftware.com/resources/download_rats.html. After you download the program, install it on your computer.
6. RATS is a source code–scanning tool that enables an auditor to search for program trouble spots and can suggest remedies. Although it might not find every problem, it can detect potential buffer overflows, race conditions, and other common problems. When you execute RATS, it inspects each segment of code and signals an alert for each problem it finds. Spend some time using RATS to look through the application code you previously loaded.
7. Did RATS find any security holes or potential vulnerabilities? If so, describe them here:
_________________________________________________________________
_________________________________________________________________
_________________________________________________________________
This exercise demonstrated how manual methods of an audit, such as counting lines of code or examining code for potential errors, can be supplemented by automated tools that aid in the process.
Exam Questions
1. Which one of the following is not an application system testing methodology?
![]() A. Snapshots
A. Snapshots
![]() B. Entity integrity
B. Entity integrity
![]() C. Mapping
C. Mapping
![]() D. Base case system evaluation
D. Base case system evaluation
2. Which continuous auditing technique detects items that meet specific criteria?
![]() A. Audit hooks
A. Audit hooks
![]() B. Snapshots
B. Snapshots
![]() C. Integrated test facilities
C. Integrated test facilities
![]() D. Continuous and intermittent simulation
D. Continuous and intermittent simulation
3. Which of the following best defines how a decision support system should be used?
![]() A. It uses structured models to solve complex problems.
A. It uses structured models to solve complex problems.
![]() B. It is designed to support nontraditional support activities.
B. It is designed to support nontraditional support activities.
![]() C. It is designed to answer structured problems.
C. It is designed to answer structured problems.
![]() D. It is designed to answer less structured problems.
D. It is designed to answer less structured problems.
4. You have been asked to recommend a control that can detect the following: “An order is normally for no more than 20 items, yet this order is for 2,000.” Which control works best to detect this?
![]() A. Validity check
A. Validity check
![]() B. Range check
B. Range check
![]() C. Reasonableness check
C. Reasonableness check
![]() D. Limit check
D. Limit check
5. Decision support systems are usually developed with which of the following types of programming languages?
![]() A. 2GL
A. 2GL
![]() B. 3GL
B. 3GL
![]() C. 4GL
C. 4GL
![]() D. 5GL
D. 5GL
6. Referential integrity is best defined as which of the following?
![]() A. Referential integrity ensures that validation routines exist to test data before it is entered into a database and that any modification can be detected.
A. Referential integrity ensures that validation routines exist to test data before it is entered into a database and that any modification can be detected.
![]() B. Referential integrity ensures that each tuple contains a primary key.
B. Referential integrity ensures that each tuple contains a primary key.
![]() C. Referential integrity guarantees that all foreign keys reference existing primary keys.
C. Referential integrity guarantees that all foreign keys reference existing primary keys.
![]() D. Referential integrity is used to divide work so that the results are either all or nothing.
D. Referential integrity is used to divide work so that the results are either all or nothing.
7. Which of the following is most correct about electronic data interchange (EDI)?
![]() A. EDI has no impact on internal or external controls.
A. EDI has no impact on internal or external controls.
![]() B. EDI reduces internal controls.
B. EDI reduces internal controls.
![]() C. EDI increases internal controls.
C. EDI increases internal controls.
![]() D. EDI has no impact on internal controls.
D. EDI has no impact on internal controls.
8. Which of the following specifies a control that is used after data has been entered into a system but before it has been processed?
![]() A. Editing
A. Editing
![]() B. Sequence check
B. Sequence check
![]() C. Balancing
C. Balancing
![]() D. Input authorization
D. Input authorization
9. You have been asked to recommend a continuous audit technique. Which of the following would be considered the least complex?
![]() A. Audit hooks
A. Audit hooks
![]() B. Systems control audit review file and embedded audit modules
B. Systems control audit review file and embedded audit modules
![]() C. Snapshots
C. Snapshots
![]() D. Continuous and intermittent simulation
D. Continuous and intermittent simulation
10. During the project-management process at the design and development phase, which of the following is not a required activity?
![]() A. Study system flowcharts
A. Study system flowcharts
![]() B. Examine proposed test plans
B. Examine proposed test plans
![]() C. Evaluate output controls
C. Evaluate output controls
![]() D. Examine proposed audit trails
D. Examine proposed audit trails
Answers to Exam Questions
1. B. Valid application-testing methodologies include snapshots, mapping, tracing and tagging, using test data, and base case system evaluation. Answer B is an example of a data integrity control.
2. A. Audit hooks detect items that meet specific criteria. Answer B is incorrect because snapshots require an audit trail. Answer C is incorrect because integrated test facilities should not be used with test data. Answer D is incorrect because continuous and intermittent simulation requires examination of transactions that meet specified criteria.
3. D. Decision support systems (DSS) are software-based applications that help analyze data to answer less structured problems. DSS typically uses knowledge databases, models, and analytical techniques to make decisions. Answer A is incorrect because DSS does not use structured models to solve complex problems. Answer B is incorrect because DSS is designed to support traditional decision-making activities. Answer C is incorrect because DSS is designed to support unstructured problems.
4. C. A reasonableness check verifies the reasonableness of the data. Answer A is incorrect because a validity check is usually used with dates. Answer B is incorrect because range checks are typically used to verify that data is within a specified range. Answer D is incorrect because a limit check is used to verify that sales do not exceed a specified limit—as an example, limit one per customer.
5. C. Decision support systems are typically developed with 4GL programming languages. Answers A, B, and D are incorrect.
6. C. Referential integrity guarantees that all foreign keys reference existing primary keys. Answer A is incorrect because it describes relational integrity; it ensures that validation routines exist to test data before it is entered into a database and that any modification can be detected. Answer B is incorrect because it describes entity integrity; it ensures that each tuple contains a primary key. Answer D is incorrect because it defines ACID: atomicity, consistency, isolation, and durability. Atomicity is used to divide work so that the results are either all or nothing.
7. B. The impact of EDI on internal controls is that there are fewer opportunities for review and authorization. Answers A, C, and D are, therefore, incorrect.
8. B. An edit control is used with data that has been entered but not yet processed. A sequence check is an example of an edit control. Answers A, C, and D are incorrect because they are all examples of processing controls, which ensure that data remains unchanged until processed by an authorized process.
9. A. Audit hooks are considered the least complex because they use embedded hooks that act as red flags if certain conditions are met. Answer B is incorrect because using systems control audit review file and embedded audit modules requires embedded audit software and is considered one of the most complex. Answer C is incorrect because snapshots are considered moderately complex. Answer D is incorrect because continuous and intermittent simulation is also considered moderately complex; it simulates the transaction run.
10. B. The examination of proposed test plans is part of the testing phase. Items to be addressed during the design and development phase include studying flowcharts; evaluating input, output, and process controls; examining proposed audit trails; and reviewing how the system will deal with erroneous input.
Need to Know More?
![]() The Need for Audit of the SDLC: http://www.asosai.org/journal2002/articles_1.htm
The Need for Audit of the SDLC: http://www.asosai.org/journal2002/articles_1.htm
![]() Is Your Internal Audit Effective?: http://www.gebbusinesssolutions.co.uk/documents/IAEffectivenessArticle.pdf
Is Your Internal Audit Effective?: http://www.gebbusinesssolutions.co.uk/documents/IAEffectivenessArticle.pdf
![]() ACID Compliance: http://www.fredosaurus.com/notes-db/transactions/acid.html
ACID Compliance: http://www.fredosaurus.com/notes-db/transactions/acid.html
![]() The Evolution of Continuous Online Auditing: http://raw.rutgers.edu/continuousauditing/continuousonlineauditing-p1.html
The Evolution of Continuous Online Auditing: http://raw.rutgers.edu/continuousauditing/continuousonlineauditing-p1.html
![]() What Is a Decision Support System?: http://dssresources.com/papers/whatisadss/
What Is a Decision Support System?: http://dssresources.com/papers/whatisadss/
![]() Project Management Basics: http://www.managementhelp.org/plan_dec/project/project.htm
Project Management Basics: http://www.managementhelp.org/plan_dec/project/project.htm
![]() Data Mining: http://www.anderson.ucla.edu/faculty/jason.frand/teacher/technologies/palace/datamining.htm
Data Mining: http://www.anderson.ucla.edu/faculty/jason.frand/teacher/technologies/palace/datamining.htm
![]() Supply Chain Management: http://www.scmr.com/
Supply Chain Management: http://www.scmr.com/