Disk Imaging and Validation Tools
After identifying the physical media that they suspect contains evidence, forensic investigators must make sure media is preserved before any further steps are taken. Preserving the media is necessary to provide assurance the evidence acquired is valid.
Chapter 3, “Computer Evidence,” and Chapter 4, “Common Tasks,” both emphasize the importance of copying all media first and then analyzing the copy. It’s usually best to create an exact image of the media and verify that it matches the original before continuing the investigation. It’s rare to examine the original evidence for any investigation that might end up in court. For other types of investigations, however, forensic investigators might perform a targeted examination on the original evidence. For example, assume the job is to examine a user’s home folder on a server for suspected inappropriate material. It might be impossible or extremely difficult to create a mirror image of the disk drive, but the disk can be scanned for existing or deleted files while it is in use. Although examining media while in use might not always be the best practice, informal investigations use this technique frequently.
To Copy or Not to Copy?
Whenever possible, create a duplicate of the original evidence, verify the copy, and then examine the copy. Always invest the time and effort to copy original media for any investigation that might end up in a court of law. If you are sure your investigation will not end up in court, you might decide to analyze the original evidence directly. This is possible and desirable in cases where copying media would cause service interruptions.
Your choice of tools to use depends on several factors, including:
- Operating system(s) supported
- Operating system(s) in which the tool runs
- File systems the tool supports
- Price
- Functionality
- Personal preference
The following sections list some tools used to create and verify media copies. Some products appear in two places in the chapter. That’s because several products play multiple roles. This section lists several products that are part of larger forensic software suites. While most suites of forensic software handle image acquisition, this section highlights those tools investigators tend to use most frequently.

The list in this chapter is not exhaustive. There are many useful tools not listed here; thus, the exclusion of any tool need not diminish its merit. Where possible, web addresses and URLs have been included for tools examined.
dd
The dd utility tool is a mainstay in UNIX/Linux environments. This handy tool is installed with most UNIX/Linux distributions and is used to copy and convert files. As briefly discussed in Chapter 5, “Capturing the Data Image,” dd is commonly used in forensics to copy an entire UNIX/Linux environment. Using dd you can specify the input and output file, as well as conversion options. This utility uses two basic arguments:
if specifies the input file
of specifies the output file
The dd utility abides by operating system file size limits (normally 2 GB) and truncates individual files larger than the limit. (The 2 GB limit does not apply when using the dd utility with device files.) Use caution when copying large files with dd.
If you want only to copy files smaller than the maximum file size, dd is a handy tool to keep in your forensic toolbox.
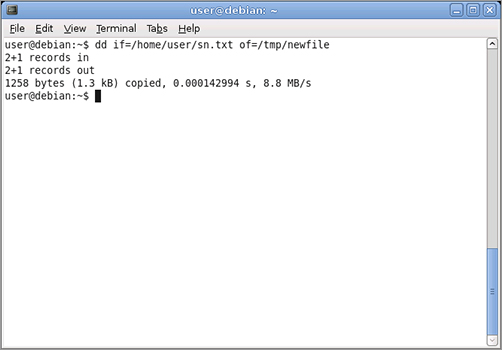
For example, to copy a simple file from a source (such as /home/user/sn.txt) to a destination (such as /tmp/newfile), you would issue the following command:
dd if=/home/user/sn.txt of=/tmp/newfile
Figure 8-1 shows the results of the above command.
Figure 8-1: Using the dd utility to copy a text file
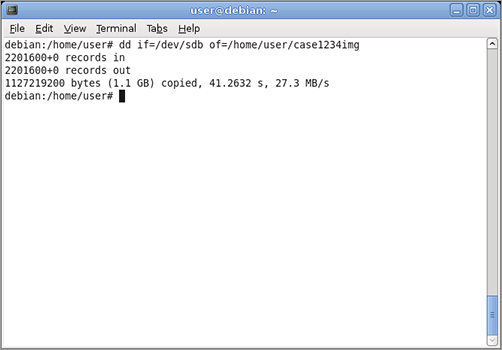
Using similar syntax, an entire hard disk drive can easily be copied. To copy a drive located at /dev/sdb to an image file named /home/user/case1234img, use this command:
dd if=/dev/sdb of=/home/user/case1234img
Figure 8-2 shows the results of the above command.
Figure 8-2: Using the dd utility to copy an entire hard disk drive
The dd utility is already on any computer running UNIX or Linux, and an Internet search produces a list of places to obtain dd for Windows. Chrysocome provides a version of dd for Windows at http://chrysocome.net/dd. Type man dd in UNIX or Linux for a man (manual) page that documents the command syntax.
DriveSpy
DriveSpy is a DOS-based disk imaging tool, developed by Digital Intelligence, Inc. An extended DOS forensic shell, DriveSpy provides an interface similar to the MS-DOS command line, along with additional and extended commands. The entire program is only 125 KB and easily fits on a DOS boot floppy disk. Unfortunately, DOS boot floppy disks aren’t as common as they once were. Also, it takes some work to prepare media to use DriveSpy. The payoff is usually worth the effort. DriveSpy does a great job of capturing and searching disk content. All you have to do is create a DOS bootable device with the DriveSpy executable on it. The most common portable boot devices are CD/DVDs and USB devices.
To create a DOS bootable device:
1. Start DriveSpy and use the DRIVES or V command to list the drives and partitions attached to a computer. (See Figure 8-3.)
Figure 8-3: Listing the drives on a system
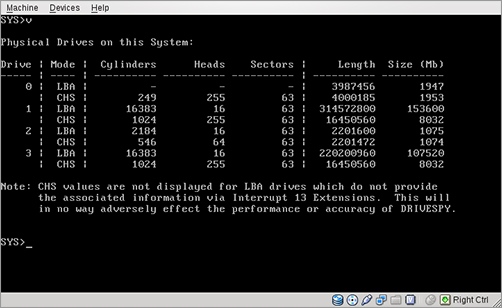
2. Choose a drive and partition for the investigation target from the SYS> prompt.
3. Select Drive 3 from the D3 command.
4. Select partition 1 at the P1 command. The partition information is displayed. (See Figure 8-4.)
Figure 8-4: Partition information
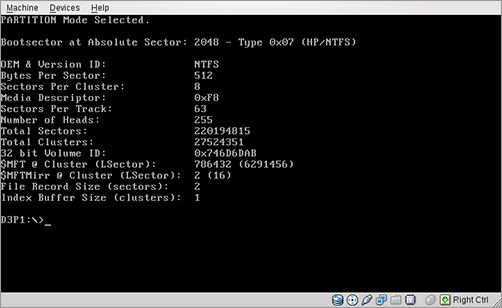
DriveSpy provides many functions necessary to copy and examine drive contents. The program logs all activities, optionally down to each keystroke. Logging can be disabled at will. Forensic investigators can examine DOS and non-DOS partitions and retrieve extensive architectural information for hard drives or partitions. DriveSpy does not use operating system calls to access files, and it does not change file access dates.
DriveSpy also lets you perform the following tasks:
- Create a disk-to-disk copy (supports large disk drives).
- Create a MD5 hash for a drive, partition, or selected files.
- Copy a range of sectors from a source to a target, where source and target can span drives or reside on the same drive.
- Select files based on name, extension, or attributes.
- Unerase files.
- Search a drive, partition, or selected files for text strings.
- Collect slack and unallocated space.
- Wipe a disk, partition, unallocated, or slack space.
DriveSpy provides basic command-line functionality and is portable enough to carry on a simple boot device or media to use at the scene. For pricing and more information, visit the Digital Intelligence, Inc. Web site at http://www.digitalintelligence.com/software/disoftware/drivespy/.
EnCase
forensic suite
Set of tools and/or software programs used to analyze a computer for collection of evidence.
The EnCase product family from Guidance Software is one of the most complete forensic suites available. More of EnCase’s functionality and its different products are covered in the “Forensic Tools” section later in this chapter. EnCase is also included in this section owing to its drive duplication functions.
In addition to providing tools and a framework in which to manage a complete case, EnCase includes a drive duplicator (also known as a drive imager). The drive imager creates an exact copy of a drive and validates the image automatically (See Figure 8-5 and Figure 8-6). It either creates complete images or splits drive images to economize storage. EnCase copies virtually any type of media, creating an identical image for analysis. EnCase calls this static data support.
Figure 8-5: Using EnCase to select a drive for duplication
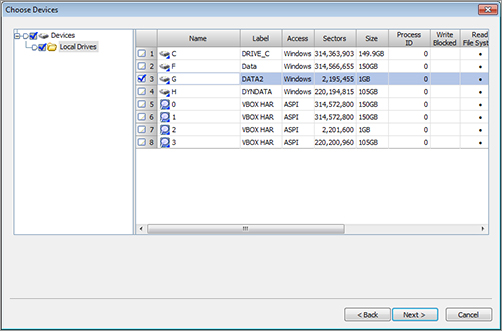
Figure 8-6: EnCase acquisition status message with an assigned globally unique identifier (GUID) and MD5
EnCase Enterprise Edition also provides support for volatile data. This feature snapshots Random Access Memory (RAM), the Windows Registry, open ports, and running applications. It provides potentially valuable information that disappears when a computer is shut down.
Guidance Software also sells a complete line of hardware disk-write blockers. Their Tableau products provide an extra measure of assurance that no writes occur on a device. You can use the hardware write blocker with EnCase or rely on EnCase’s own software write blocking to protect original media. Forensic investigators can also use Tableau hardware write blockers with non-EnCase software.
The EnCase products run on Windows workstation and server operating systems. For more information on the EnCase product line and specific system requirements, visit the Guidance Software Web site at www.guidancesoftware.com.
Forensic Replicator
Forensic Replicator, from Paraben Forensic Tools, is another disk imaging tool that accommodates many types of electronic media. Forensic Replicator runs on the Windows operating system. It provides an easy-to-use interface, as shown in Figure 8-7 and Figure 8-8, to select and copy entire drives or portions of drives. It also handles most removable media, including Universal Serial Bus (USB) micro drives. Forensic Replicator stores media images in a format that the most popular forensic programs can read.
Figure 8-7: Paraben’s Forensic Replicator Acquisition Wizard
Figure 8-8: Paraben’s Forensic Replicator primary user interface
Forensic Replicator also provides the ability to compress and split drive images for efficient storage. The ISO option allows you to create CDs or DVDs from evidence drives that you can browse for analysis. This option makes drive analysis much easier and more accessible for general computers. Copies of the suspect drive don’t need to be mounted on a dedicated forensic computer. Standard searching utilities can be used to search the CDs or DVDs. Forensic Replicator also offers the option of encrypting duplicate images for secure storage.
Paraben also sells a FireWire or USB-to-IDE/SATA write blocker, called Paraben’s Lockdown V3, as a companion product.
For additional information about the Paraben forensic tools product line, see the “Forensic Tools” section later in this chapter. For more information on the Forensic Replicator product, visit the Paraben Web site at http://www.paraben-forensics.com/replicator.html.
FTK Imager
FTK (Forensic Toolkit) Imager from AccessData Corporation is a Windows-based set of forensic tools that includes powerful media duplication features. (See Figure 8-9.) This free imaging tool allows you to mount a forensic image of the suspect computer so that the suspect’s image becomes a letter drive on the investigator’s computer.
Figure 8-9: AccessData FTK Imager
FTK can create media images from many different source formats, including:
- NTFS and NTFS compressed
- FAT12, FAT16, and FAT32
- Linux ext2, ext3, and ext4
- HFS, HFS+, CDFS, and VXFS
Figure 8-10 shows the image creation progress message.
Figure 8-10: FTK Imager creating an image
FTK generates CRC or MD5 hash values, as do most products in this category, for disk-copy verification. In addition, FTK provides full searching capability for media and images created from other disk imaging programs. Image formats that FTK reads include:
- EnCase
- SMART
- Expert Witness
- ICS
- Ghost
- dd
- Advanced Forensic Format (AFF)
- AccessData Logical Image (ADI)
For more information about FTK Imager, visit the AccessData Corporation Web site at www.accessdata.com.
Norton Ghost
Norton Ghost, from Symantec, is not strictly a forensic tool, but it does provide the ability to create disk copies that are almost exact copies of the original. You can verify the copies you make and ensure each partition is an exact copy, but a complete drive image that Ghost creates commonly returns a different hash value than a hash of the original drive. This means that, although Ghost is a handy tool, it may not provide evidence that is admissible in a court of law. The most common uses for Ghost include backup/restore and creating installation images for multiple computers. Even though Ghost’s primary use is not forensics, its utility merits a place in our list of useful tools. (See Figure 8-11.)
Figure 8-11: Norton Ghost
Norton Ghost is a Windows application and requires a Windows operating system. For more information on Norton Ghost, visit the Symantec Web site at http://us.norton.com/ghost.
ProDiscover
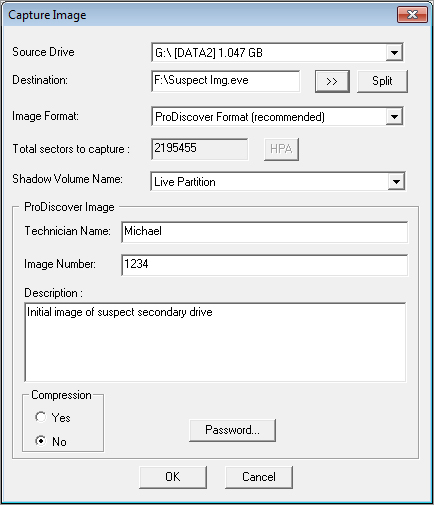
ProDiscover, from Technology Pathways, is another suite of forensic tools worth considering for your forensic toolkit. Like other forensic software suites, ProDiscover provides disk imaging and verification features. (See Figure 8-12.)
Figure 8-12: Capturing a disk image with ProDiscover
ProDiscover can create a bit stream copy of an entire suspect disk, including host protected hardware protected area (HPA) sections, to keep original evidence safe. The HPA is an area of a hard disk drive that the disk controller does not report to the BIOS or the operating system. Some disk drive manufacturers use the HPA to hide utilities from the operating system. (For more information, see Chapter 5.)
Another interesting feature of ProDiscover is that it allows you to capture a disk image over a network without being physically connected to a suspect computer.
ProDiscover also automatically creates and records MD5 or SHA-1 hashes for evidence files to prove data integrity. Figure 8-13 shows the main project window.
Figure 8-13: ProDiscover project
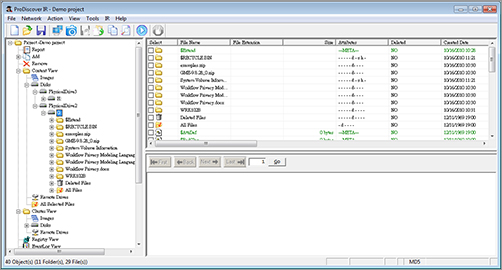
Technology Pathways provides several different versions of ProDiscover, to meet specific forensic needs. As with other forensic suites, we cover additional features in a later section of this chapter.
All Technology Pathways products include disk imaging and verification and require a Windows operating system. For more information on ProDiscover, visit the Technology Pathways Web site at www.techpathways.com.
SMART Acquisition Workshop (SAW)
The SMART Acquisition Workshop (SAW) product from ASR Data Acquisition & Analysis, LLC, is a stand-alone utility that creates forensic-quality images from storage devices. SAW runs on Windows, Linux, and Mac computers. Regardless of the operating system, SAW uses a GUI that makes creating images of evidence data easy. (See Figure 8-14.)
Figure 8-14: SAW interface
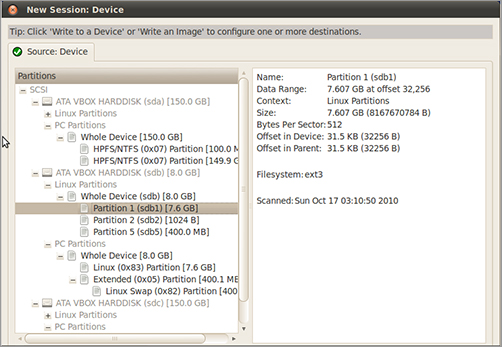
Although SAW works as a stand-alone utility, it also works with another ASR Data utility, SmartMount. SmartMount uses image files from SAW and several other imaging tools, to ensure fast performance for many common forensic activities. ASR Data states that SmartMount exceeds competitors’ performance by running up to twenty times faster for searches, indexing, and analysis operations.
Even without SmartMount, SAW provides a solid method to create images of many different types of storage media using a straightforward GUI. For more information on SAW, visit the ASR Data Acquisitions & Analysis Web site at http://www.asrdata.com/forensic-software/saw/.
SMART
SMART comes from the same organization that produces the SAW utility, ASR Data Acquisition & Analysis, LLC. The suite comprises several tools integrated into a full-featured forensic software package. Two tools in the package are SMART Acquisition, which provides disk imaging, and SMART Authentication, which provides verification functionality.
SMART runs in Linux and provides a graphical view of devices in a system (Figure 8-15). The first step in creating a disk image is to calculate a hash value for the source device.
Figure 8-15: SMART displays devices in a system.
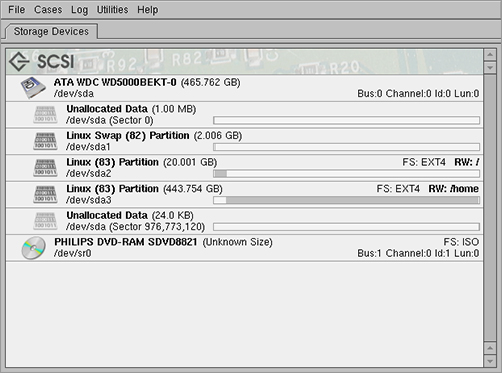
After SMART generates and stores the hash value, it creates one or more device images. SMART can create multiple image files, use compression, split images to fit on smaller devices, and associate images with existing case files (Figure 8-16).
Figure 8-16: Creating an image file with SMART
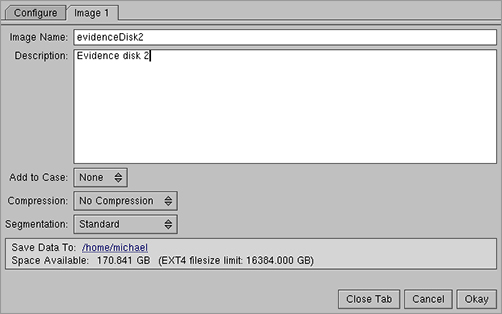
For more information on SMART, visit the ASR Web site at http://www.asrdata.com/forensic-software/smart-for-linux/.
WinHex
WinHex, from X-Ways Software Technology AG, is a Windows-based universal hexadecimal editor and disk management utility. It supports recovery from lost or damaged files and general editing of disk contents. Its disk cloning feature is most relevant to this section.
WinHex clones any connected disk (see Figure 8-17 and Figure 8-18) and verifies the process using checksums or hash calculations.
Figure 8-17: Starting the clone process in WinHex
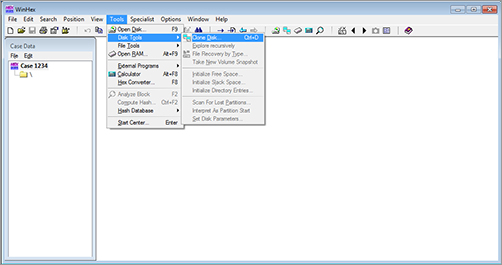
Figure 8-18: The Clone Disk dialog box in WinHex
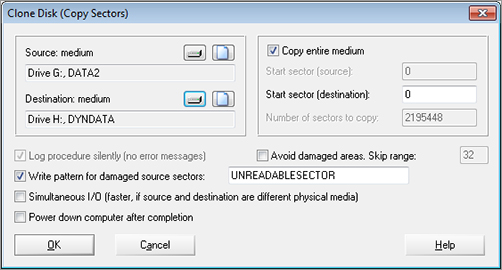
WinHex provides many features beyond disk imaging and verification. You can use WinHex to examine, and optionally edit, disk contents. You can also search disks for text strings using WinHex’s search engine. Its support for various data types and its ability to view data in different formats make WinHex a valuable forensic tool.
For more information on WinHex and its additional capabilities, visit the X-Ways Software Technology Web site at http://www.x-ways.net/winhex/.
