CHAPTER 13
Information Governance for Social Media*
By Dr. Patricia Franks and Robert Smallwood
Information is the lifeblood of every organization, and an increasing volume of information today is created and exchanged through the use of social networks and Web 2.0 tools like blogs, microblogs, and wikis.
Corporations use public social media technology to create a visible brand, strengthen relations with current customers while attracting new connections and clients, highlight their products and services, and gather intelligence that can be used in decision making.
Governments use public social media technologies to consult with and engage citizens, provide services, and keep pace with fast-moving events (e.g., natural disasters).
Both types of enterprises also benefit from the use of internal social media solutions that facilitate communication and collaboration, improve employee engagement, and boost productivity and efficiency.
Content created through or posted to these new social media platforms must be managed, monitored, and, quite often, archived. Content that meets the organization's definition of a record (i.e., documents business activities) must be retained in accordance with the organization's records retention and disposition policy.
Too often, social media content is not managed by information governance (IG) policies or monitored with controls that ensure protection of the brand and critical information assets and preservation of business records.
Types of Social Media in Web 2.0
The term “Web 2.0” was coined to characterize the move from static Web sites that passively provided information to consumers to more participative, interactive, collaborative, and user-oriented Web sites and Web applications that allow for input, discussion, and sharing. Users can add content, increasing the value of the Web site or service. Examples include blogs and Web pages containing podcasts (digital media, usually audio) where readers can post comments or pose questions; wikis that hyperlink to related information to create a knowledge base that shows interrelationships and allow users to add content; and RSS (really simple syndication) feeds that provide a stream of fresh content to the user or consumer.
Web 2.0 is the term used to describe the second generation of the World Wide Web, which is comprised of a combination of technologies that allow consumers of Web content to participate, collaborate, and share information online. The improved functionality reflects consumer needs and preferences that surfaced as a result of increased use of the Web for daily information and communications.
Social media sites like LinkedIn, Twitter, and Facebook encourage social interactions by allowing users to create their own close network of business associates or friends—essentially a hand-picked audience—and to post their own content in the form of comments, links, photos, videos, and so forth. Others in their social network may view, forward, share, organize, and comment on this content.1
Web 2.0 and social media platforms began as outward-facing, public Web services that could link users from around the world. Subsequently, businesses discovered that social media technology could also be leveraged for internal use in various ways, such as by creating a directory and network of subject matter experts that users can search when working on special projects or by sending out microblog messages to keep their workforce informed. These internal social networks may be extended to include external stakeholders, such as suppliers and customers, in a controlled environment. A number of platform and software options exist for enterprise social media development and use.
According to the U.S. National Archives and Records Administration:
Social media platforms can be grouped into the categories below. Some specific platforms may fit into more than one category depending on how the platform is used.
- Web Publishing. Platforms used to create, publish, and reuse content.
- Microblogging (Twitter, Plurk)
- Blogs (WordPress, Blogger)
- Wikis (Wikispaces, PBWiki)
- Mashups (Google Maps, popurls)
- Social networking. Platforms used to provide interactions and collaboration among users.
- Social networking tools (Facebook, LinkedIn)
- Social bookmarks (Delicious, Digg)
- Virtual worlds (Second Life, OpenSim)
- Crowdsourcing/Social voting (IdeaScale, Chaordix)
- File sharing/storage. Platforms used to share files and host content storage.
- Photo libraries (Flickr, Picasa)
- Video sharing (YouTube, Vimeo)
- Storage (Google Drive, Dropbox)
- Content management (SharePoint, Drupal)
Agencies [and businesses] use a variety of software tools and platforms. The examples given above are not meant to be an exhaustive list.2
Additional Social Media Categories
Breaking out the categories of social media further, we can see in Table 13.1 examples of the wide range of social media applications that exist in the marketplace today. These categories will increase and fluctuate as the market matures and the companies providing the social media technologies and services expand, merge, are acquired, or die off.
There are certainly additional categories, and the categories will continue to grow. In addition, social media companies do not always fit neatly into one category. Applications (apps) for smartphones and tablets offer instant gratification and combine several functions. For example, Snapchat allows the sender to share an experience by snapping an image or video, adding a caption, and sending it to a friend.3 The image, unless saved by the recipient, is visible only for the number of seconds set by the sender. The goal is to share a moment in time by sending a fleeting message. Another app, Vine, introduced by Twitter in early 2013, allows anyone to capture and share short looping videos.4 Popular for personal use, a number of firms (e.g., GE, Urban Outfitters, and 20th Century Fox) have begun to integrate Vine into their marketing/branding strategy, including major brands.
Table 13.1 Social Media by Application Type
| Category | Examples |
| Content curation | Buzzfeed, Flipboard, Skygrid, Storify, Summify |
| Content sharing | Yelp, Scribd, Slideshare, Digg, Topix |
| Photo sharing | Flickr, Picasa, SmugMug, Photobucket |
| Social ad networks | Lifestreet, AdKnowledge, Media6degrees, BurstMedia |
| Social analytics | Awe.sm, Bluefin Labs, Mixpanel, Webtrends |
| Social bookmarking | BibSonomy, Delicious, Diigo, Folkd |
| Social business software | Lithium, Jive, Pluck, Mzinga, Telligent, Ingage, Leverage Software, Huddle, Cubetree, Yammer (Microsoft), Socialcast, Igloo, Socialtext, Watchtoo, Acquia* |
| Social brand engagement | Socialvibe, Mylikes, Adly, Sharethrough |
| Social commerce platforms | Ecwid, Moontoast, Shop Tab, Dotbox, Storenvy, VendorShop |
| Social community platforms | Ning, Mixxt, Grou.ps, Groupsite |
| Social data | GNIP, DataSift, Rapleaf, RavenPack |
| Social intelligence software | SDL, Netbase, Postrank, Google Analytics, Trendrr, Trackur, Visible |
| Social marketing management | Shoutlet, Syncapse, Objective Marketer, Immobi, MediaFunnel |
| Social promotion platforms | Offerpop, Seesmic, Strutta, Votigo, Fanzila, Zuberance, Extole, Social AppsHQ, Social Amp |
| Social publishing platforms | Hootsuite, Spredfast, Hearsaysocial, MutualMind, SproutSocial, Flowtown, Socialware |
| Social referral | 500Friends, Curebit, Tip or Skip, Turnto |
| Social search and browsing | StumbleUpon, Topsy, Wink, Kurrently, SocialMention |
| Social scoring | Klout, EmpireAvenue, PeerIndex |
Source: Luma Partners and Terry Kawaja, http://static5.businessinsider.com/image/4fb5077becad045f47000003-960/buddy-media-social-marketing.jpg (accessed May 21, 2012).
Social Media in the Enterprise
Public-facing social media integrates Internet-based applications, technology, social interaction, and content creation to enable communication, collaboration, and content sharing within and across subnetworks of millions of public users. Implementing tight security on these types of mass networks would likely slow response time and inhibit the user experience, and it may not provide a sufficient level of security to warrant the investment on the part of the social media provider.
While popular consumer-based technologies (Facebook, Twitter, and LinkedIn) top the list of social media technologies used in enterprises today,5 these services were not designed with the business in mind. Enterprises that need tight security but wish to take advantage of the many benefits of social media use are increasingly implementing enterprisewide social media solutions in addition to or in place of public-facing social media.
In the business world, Facebook-like social networking software is offered for private, closed networks with a finite number of users. In this computing environment, implementing security is more manageable and practical. Some services are cloud based; others operate internally behind the enterprise firewall; and some operate either way or in conjunction as hybrid architecture. Usage statistics that reflect trends, adoption rates, and areas of content interest can be provided to help feed the metrics needed to chart the progress and effectiveness of the enterprise social network.6
Enterprise social networking is being adopted by business and public-sector entities at a rapid rate. With the entry of Generation Gmail into the workforce, many of these initiatives took on an experimental, “cool” image. However, it is crucial to establish social media business objectives, to define time-limited metrics, and to measure progress. There does need to be some leeway, as calculating return on investment (ROI) for enterprise social networks is very new, and all the benefits (and pitfalls) have not yet been discovered or defined. Certainly the network load and required bandwidth for e-mail and attachments will decrease; instead of sending a 25MB PowerPoint file back and forth among 10 coworkers, the file can sit in a common workspace for collaboration.
Another intangible benefit is the competitive value in being a market leader or industry innovator. But to keep that edge, companies need to continually scan the horizon for new technologies and services. Engaging in online conversations with customers and other stakeholders is the norm rather than the exception. One sign of a progressive-thinking organization is its ability to leverage social media technology to refine operations, improve customer services, and make employees' lives easier. An organization with a strong social media reputation likely will be better able to attract, recruit, and retain qualified, high-achieving employees.
Implementing security is more manageable and practical with enterprise social networking software.
Key Ways Social Media Is Different from E-Mail and Instant Messaging
Social media offers some of the same functionality as other communication and collaboration systems like e-mail and instant messaging (IM), yet its architecture and underlying assumptions are quite different.
When implementing enterprise versions of social media applications, a company may exert more control over the computing and networking environment through in-house implementation rather than outsourcing. Consumer-oriented social media applications, such as Facebook and Twitter, reside on application servers outside the enterprise controlled by third-party providers. This creates IG and records management (RM) challenges and poses legal risks.7
Obviously, social media is an emerging technology, so standards, design, and architecture are in flux, whereas e-mail has been stable and established for 15 to 20 years. E-mail is a mature technology set, meaning it is unlikely to change much. There are standard e-mail communications protocols, and the technology's use is pervasive and constant. So when e-mail IG policies are formed, less updating and fine-tuning are required over time. With social media, new features are being added, standards are nonexistent, privacy settings change overnight, and the legalese in terms of service agreements is continually modified to include new features and settings, which means that your social media policy must be more closely monitored and frequently fine-tuned.
E-mail, IM, and social media are all communication tools used to share content and collaborate, but social media also offers user interaction features, such as “Like” on Facebook or “retweet” (copying and posting a 140-character tweet) on Twitter, that bring attention to the content in the user's network and can be construed as an endorsement or rejection of content based on user opinions expressed and associated with the content.8
Further confounding the organization's ability to control the social media environment is the fact that the social media sites are dynamic and ever changing, with comments and opinions being published in real time. This is not true with e-mail and IM systems, which are more structured, stable, and technologically mature.
Biggest Risks of Social Media
Social media is the Wild West of collaboration and communication. Vulnerabilities still are being exposed, and rules still are being established. Users often are unsure of exactly who can see what they have posted. They may believe that they have posted a comment only for the eyes of a friend or colleague, not realizing it may have been posted publicly. “One of the biggest risks that social networking poses to organizations is that employees may be exposing information that's not meant for public consumption, especially in highly regulated environments like banking and healthcare, in industries that rely heavily on proprietary research and development, or even in the military”9 (emphasis added).
Social media differs greatly from e-mail use. E-mail is mature and stable. Social media is not. These distinctions have important ramifications for IG policy development.
Organizations that believe they can ban social media in order to avoid risks are mistaken. Prohibition of social media can result in social media use being driven underground. Employees accustomed to the ease of communicating and collaborating through social networks may turn to the use of personal devices and accounts outside the control of the organization. Even strict adherence to a nonuse policy can harm the organization's reputation, finances, ability to gather information that can be used to improve operations, and ability to remain competitive.
Once an organization decides it will engage in social media initiatives, it must identify different types of risks to initiate its IG effort in this area. According to Chris Nerney of Network World, two of the greatest social media security threats are:
- Lack of a social media policy. Many organizations are just now discovering the extent to which social media has popped up in various pockets of their organization. They may believe that their e-mail and communications policy will pretty much cover social media use and that it is not worth the time and expense to update IG policies to include social media.
This invites complexities, vagaries, and potential disaster. A simple Twitter comment could invite litigation: “Our new project is almost ready, but I'm not sure about the widget assembly.” It's out there. There is a record of it. Instant potential liability in 140 characters or less.
Social media can add value to an organization's efforts to reach out to customers and other stakeholders, but this must be weighed carefully against the accompanying risks.
The objectives of a social media initiative must be spelled out, and metrics must be in place to measure progress. But more than that, who can utilize social media on behalf of the company and what they can state needs to be established with clarity in the IG policy. If not, employees are essentially flying blindly without controls, and they are more likely to put the enterprise at risk.10
More than policy development is needed. If your organization is going to embark on a social media program, it needs an executive sponsor to champion and drive the program, communicating policy to key leaders. You will also need to conduct training—on a consistent basis. Training is key, since social media is a moving target.
- Employees—the accidental and intentional insider threat. This may be in part due to lack of social media policy or due to lack of monitoring and enforcement. Sometimes an employee harms an organization intentionally. Remember Private Bradley Manning's release of hundreds of thousands of classified government documents to WikiLeaks?11 But most times employees do not realize the negative impact of their behavior in posting to social media sites. People might use social media to vent about a bad day at work, but the underlying message can damage the company's reputation and alienate coworkers and clients. Other times a post that is seemingly unrelated to work can backfire and take a toll on business. We're all human and sometimes emotion gets the better of us, before we have rationally thought out the consequences. And that is especially true in the new world of social media, where it may be unclear exactly who can see a comment.
The dangers of social media are quite different from those posed by an isolated, off-color, or offensive verbal comment made in the workplace, or even one errant e-mail. With social media it is possible that the whole world will be able to see a comment meant only for a limited and controlled audience. For example, consider Ketchum public relations vice president James Andrews, who in 2009 “fired off an infamous tweet trashing the city of Memphis, hometown of a little Ketchum client called FedEx, the day before he was to make a presentation to more than 150 FedEx employees (on digital media, no less!).” FedEx employees complained to Ketchum and their own executives, pointing out that while they suffered salary reductions, money was being spent on Ketchum, which had been clearly disrespectful of FedEx. Andrews was forced to make a “very public and humiliating apology.”12
This story shows that high-level executives must be just as careful as lower-level employees. Andrews was not only a corporate vice president, but also a public relations, communications, and social media expert, well versed in the firm's policies and mission. He also had no ill intent. Knowing this, consider what a rogue employee intent on damaging the company might do. Such impact could be much worse. For instance, what if a chief executive's assistant were to release details of strategic plans, litigation, or ethics investigations to the public? Or embarrassing details of the CEO's private life? The impact could be quite costly.
Legal Risks of Social Media Posts
With over 554 million active registered users and an estimated average of 58 million tweets per day in 2013 to the microblogging site Twitter,13 a number that continues to increase, surely some employees in your organization are tweeting. As of the first quarter of 2013, more than 225 million professionals in over 200 countries and territories were members of the LinkedIn network, and the network continues to expand, with students and recent college graduates being the fastest-growing segment. Approximately 33 percent of members are in the United States.14
The casual use of public comments can easily create liability for a company. With no IG policy, guidelines, monitoring, or governance, legal risks of using social media increase significantly. This is an avoidable risk.
Many people are posting birthday wishes and pictures of what they had for dinner, but others may be venting about specific companies and individuals within those companies. There's a difference between “I can't stand Wall Street,” and “Goldman is run by Satan, and his name is John Smith. We're going to sue his butt off.” Instant liability.
Two of the biggest threats of social media use for organizations come from the lack of a social media policy and threats presented by employee use.
With no IG policy, guidelines, monitoring, or governance, legal risks of using social media increase significantly. This is an avoidable risk.
The specifics of where and how an employee posted or tweeted a message may mean whether a lawsuit against your company is successful or not. If a personal Linked In or Twitter account is used, and it was posted after hours using a PC from home, the company may be off the hook. But if it was done using a company computer or network, or from a company-authorized account, a defense will be difficult. Opposing counsel likely will ask questions about the policy for posting first. One thing is true: “Much of this remains unsettled ground.”15
Just when compliance and records managers thought they had nailed down IG for e-mail, IM, and electronic records, social media came on the scene creating new, dynamic challenges!
Even though not all social media content will rise to the level of a record, according to the definition in use, the organization still may be responsible for managing the nonrecord content. For example, an organization may consider a social networking profile a record but consider comments nonrecords. That decision will have an impact on what must be retained according to the records retentions schedule. It does not, however, absolve the organization from monitoring and evaluating the comments.16
“Tweets are no different from letters, e-mail, or text messages—they can be damaging and discoverable, which is especially problematic for companies that are required to preserve electronic records, such as the securities industry and federal contractors. Yet another compliance headache is born.”
Blogs are simply Web logs, a sort of online journal that is focused on a particular topic. Blog readers can become followers and receive notices when new content is posted as well as add their own comments, which may be moderated or restricted. It seems confounding, but with the explosion in the use of blogs, there have been actual incidents where employees have “disclosed trade secrets and insider trading information on their blogs. Blogs have also led to wrongful termination and harassment suits.”
So the liability and potential for leakage or erosion of information assets is not theoretical; it is real.
To safeguard the enterprise that sanctions and supports blog use, IG policies must be clear, and real-time capture and management of blog posts should be implemented. Remember, these can be business records that are subject to legal holds, and authenticity and accuracy are crucial in supporting a legal case. So a true and original copy must be retained. This may, in fact, be a legal or regulatory requirement, depending on the industry.
If content-posting guidelines are not clear, then the informal nature of social media posts potentially can be damaging to an organization. The usual fact checking and vetting that is done for traditional press releases and advertising may not be conducted, so social media posts can be unscreened and unfiltered, which poses problems when IG policies are not clear and fully enforced.17 Beyond that, the consequences of violating policy should be severe and clearly stated in policies, as should the penalties imposed, a message that should be reinforced consistently over time.
Tools to Archive Social Media
New approaches to capture, manage, and archive social media are emerging. Some are free or inexpensive and appropriate for personal and small business use. Others require a more substantial investment of resources but better meet the needs of midsize and large organizations.
Public Social Media Solutions
Launched as a personal cloud organizing service in March 2012, Jolicloud took a file system approach to social media so Facebook, Flickr, Instagram, Picasa, and Twitter content that was previously interacted with or shared could be sorted and searched.18 The service “slurps” (extracts) content from social media sites and makes it available for viewing through any mainstream Internet browser, tablet, or smartphone. As users perform social media functions like sharing, “liking,” and “favoriting” content on their various social media services, the content is automatically saved to their Jolicloud account, which can later be sorted and searched.
Jolicloud has similarities with other “personal social Web memory” products, such as Facebook Timeline and TimeHop. In 2013, Jolicloud added the ability to view and edit files and rebranded its unified cloud platform Jolidrive.19
If you prefer to maintain copies of all files on your own computer, an alternative to Jolicloud is a product called SocialFolders. This app lives on your computer and connects directly to your favorite social media sites so you can manage, backup, and sync your photos, videos, and documents in a centralized location.20
Since Facebook and Twitter initially did not provide archiving tools, some third-party applications have popped up to perform the task.
TwInbox is a free MS Outlook plug-in that archives Twitter postings and allows users to install a (Twitter) menu option to send tweets directly from Outlook; these tweets are archived into a standard Outlook folder. The folder can be configured to capture tweets that a user sends outside of Outlook, so that everything is stored in one folder.
TweetTake is a free utility that archives followers and tweet posts. It does not require a software download, and the archive can be stored as a zip file and then imported into a spreadsheet (e.g., Excel) for further analysis. By the time this book goes to press, there will be even more options, and the existing ones will have changed and (it is hoped) improved.
If your organization uses Twitter and social media archiving is required by law, regulations, or internal IG policies, a good place to start your research is with software like TwInbox (if you operate in a Microsoft Office environment) and TweetTake as well as other new entrants to the market or other options your organization may have.21
For archiving Facebook posts, there are several options. Facebook users can download and archive their Facebook data from their account settings page. Also, there are free plug-ins for Mozilla's Firefox browser. One comes directly from Mozilla, which archives everything but fan pages into a zip file. Another is a Firefox add-on called ArchiveFacebook, which allows you to save Facebook content directly to your hard drive and view the content exactly as it looks on Facebook. Other tools, including SocialSafe, PageFreezer, and Wayback Machine, charge a small fee. All of these options and new ones need to be evaluated when selecting an archiving solution for Facebook that meets your organization's requirements.
For archiving LinkedIn posts and information, SocialSafe, PageFreezer, and Way-back Machine can be used, and other tools will surface.
To convert records to a standard format for use outside of the social media application, there are also options to create PDF documents out of social media posts using products like PDF995 and PrimoPDF.22 Nuance Software also provides PDFCreate.
Additional archiving tools are being developed as the social media market matures. Bear in mind that tools developed by third parties always carry some risk that tools directly from the software or service provider do not.
These tools may not provide a legally defensible audit trail in court. Choosing among the tools requires a critical analysis and may require additional technology layers. Other alternatives, such as real-time content archiving tools and even in-house developed customizations, also have to be considered.
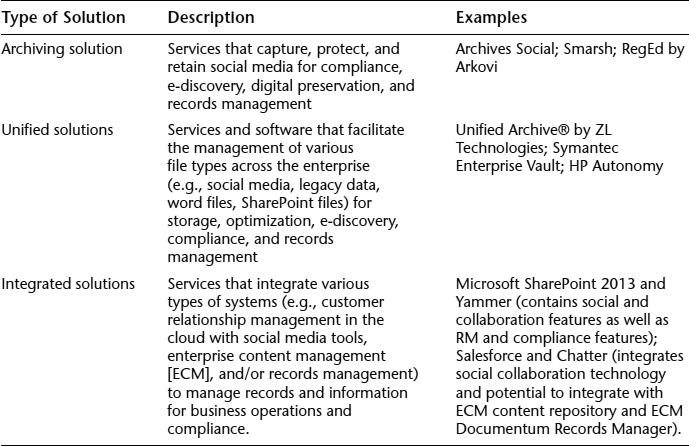
Government and Industry Solutions
Most of the products and methods that could be of use for personal or small business archiving of social media content involves manual intervention, which can be time consuming. All organizations must focus on their core business and would benefit from tools and services that streamline and automate the archiving process as much as possible—however, there is a cost. Midsize and large organizations, often using both public and enterprise social media technologies, may find the investment in commercial products and services worth the additional cost, especially those products that integrate and manage social media content with other enterprise content. Capture and management of social media content is an area that must be addressed as part of an overall IG strategy. Some of the solutions available at this time are described in Table 13.2; however, because of the recent increased focus on archiving solutions for public and enterprise social media content, the landscape will continue to become more efficient, effective, and possibly unified.
In addition to providing archiving functions, unified and integrated solutions provide business intelligence applications and tools to enable the enterprise to better achieve its organizational goals, processes, and performance requirements.
IG Considerations for Social Media
The report “How Federal Agencies Can Effectively Manage Records Created Using Social Media Tools” addresses building an IG framework for social media. An IG model provides the overarching policies, guidelines, and boundaries for social media initiatives.23
An IG framework for social media should incorporate social media policy, controls, and operational guidelines as well as spell out consequences for violations. Best practices for social media still are being established, and those that have been established are evolving. In addition to establishing policies to govern the use of social media across the organization, best practices should include industry-specific, vertical market considerations. A cross-section of functional groups within the enterprise should provide input into the policy-making process. At the very minimum, internal audit, marketing, finance, information technology (IT), legal, human resources, and RM must be consulted, and all business units should be represented. Clear roles and responsibilities must be spelled out, and controls must be established to govern acceptable use—essentially what is allowed and what is not. Even writing style, logo format, branding, and other marketing considerations should be weighed. The enterprise's image and brand are at risk, and prudent steps must be taken to protect this valuable, intangible asset. And most important, all legal and regulatory considerations must be folded into the new IG policy governing the use of social media.
Table 13.2 Social Media Archiving and Management Software
Key Social Media Policy Guidelines
Your social media policy development process can begin by examining the published policies of major organizations in your industry or closely related industries. It should also be based on changes in the workplace as well as established standards, such as guidance developed as the result of a January 2013 ruling by the National Labor Relations Board. More important, social media policies must be hand-crafted and customized for each organization.
An IG framework for social media should incorporate social media policy, controls, and operational guidelines, and spell out consequences for violations.
A prudent and properly crafted social media policy:
- Specifies who is authorized to create social media accounts for the organization.
- Authorizes specifically who can speak on the organization's behalf and who cannot (by role/responsibility).
- Outlines the types of negative impact on the company's brand and reputation that unscreened, poorly considered posts may have.24
- Draws clear distinctions between business and personal use of social media and specifies whether personal access is allowed during work hours.
- Underscores the fact that employees should not have any expectation of privacy when using social media for corporate purposes, just as in using other forms of communications such as e-mail, IM, and voicemail, which may be monitored.
- Clearly states what is proper and allowed on the organization's behalf and what is forbidden in social media posts or using organization resources.
- Instructs employees to always avoid engaging in company-confidential or even controversial discussions.
- Encourages/requires employees to include a standard disclaimer when publishing content that makes clear the views shared are representative of the employee and not the organization.
- Strictly forbids the use of profanity and uses a professional business tone, albeit more informal than in other corporate communications.
- Strictly forbids any statements that could be construed as defamatory, discriminative, or inflammatory.
- Outlines clear punishments and negative actions that will occur to enforce social media policy.
- Draws clear rules on the use of the company name and logo.25
The policy need not be long but should be clear. Best Buy's social media policy, for example, uses the slogan, “Be smart. Be respectful. Be human.”26 It then breaks the guidance into two major sections: what you should do and what you should never disclose. A word of caution contained in the Best Buy Social Media Policy explains the rationale for the employee to abide by the social media policy: Protect the brand, protect yourself.
To ensure compliance with the organization's IG strategy, it is also necessary to include a reference to the organization's related policies, including the records and information management policy.
Records Management and Litigation Considerations for Social Media
Legal requirements and demands trump all others when making decisions about capturing and preserving social media records. Social media is no different from other forms of electronically stored information (ESI) in that it is potentially discoverable during litigation.27 Not all ESI residing in social media are records, but all are discoverable. If an organization employs social media and makes a conscious decision not to archive all or some portion of that data, it is taking risks. A legally defensible records retention schedule must be in place, and it must be based on specific laws that identify the records that must be retained and to a records retention policy that explains the process for identifying, categorizing, and managing information and records.
U.S. corporations that utilize social media are compelled to preserve those records, including metadata and associated linked content, according to Rule 34 of the Federal Rules of Civil Procedure (FRCP), which states that opposing parties in litigation may request “any designated documents or ESI—including writings, drawings, graphs, charts, photographs, sound recordings, images, and other data or data compilations—stored in any medium from which information can be obtained either directly or, if necessary, after translation by the responding party into a usable form.” This echoes a key principle of the Sedona Conference®, a leading RM and legal retention think tank. Also, Rule 26 of the FRCP requires that any and all information that might be discoverable or “potentially responsive” must be preserved and produced if requested by the opposing party. So it is clear that there is a legal duty to preserve social media records.
From an RM perspective, it is critical to consider that social media posts are more than the posts themselves; for legal or compliance purposes, they include metadata and hyperlinks to external content—and that external content in its native format—that must also be preserved, preferably in real time. That external content may be a PDF document, a PowerPoint presentation, Web site content, or even a video on YouTube, which would require that video archiving, along with associated metadata, is in place.
To truly capture the necessary content required by law, records and compliance managers must understand how software programs communicate with each other in order to recommend possible solutions to the IT department. One way to preserve the Web-based data of social media applications is to use the application programming interfaces (APIs) that social media providers offer. APIs offer standard “hooks” into an application. Another way, perhaps preferable, is to enlist a service that can capture and archive information from multiple social networks. Further innovations in tools and services that will make capturing these records easier are being developed.
Content found in social media networks can be static or dynamic. Profiles in Facebook and blog posts are examples of static content. They can be captured before being posted to the Web. Blog comments and endorsements through “liking” or “favoriting” a post are examples of dynamic content. The ideal method from a RM standpoint is to capture all dynamic social media content in real time in order to be able to prove authenticity and fight claims of records spoliation (corruption or adulteration of evidence) in the event of a discovery request.
Regardless of method of capture, social media content that meets record status criteria should be moved to a repository in an electronic records management (ERM) system application. Then business rules for retention should be applied to those records. Typical functions of an ERM system include these:
U.S. corporations must archive social media records under Rule 34 of the FRCP.
Social media policy must be unique to each particular organization.
- Marking an electronic document as a read-only electronic record
- Protecting the record against modification or tampering
- Filing a record against an organizational file plan or taxonomy for categorization
- Marking records as vital records
- Assigning disposal (archival or destruction rules) to records
- Freezing and unfreezing disposal rules
- Applying access and security controls (Security rules may differ from the source electronic document in an electronic document management system or enterprise content management [ECM] software.)
- Executing disposal processing (usually an administrative function)
- Maintaining organizational/historical metadata that preserves the business context of the record in the case of organizational change
- Providing a history/audit trail28
Robust search capabilities are perhaps the most crucial component of a social media ERM or archiving solution. It is fine to preserve the records and their associated metadata perfectly, but if you cannot easily find and produce the information, compliance and e-discovery efforts will fall short and may cost the organization dearly.
Social media policy will be unique to each particular organization. It is fine to start with a social media policy example or template, but it must be tailored to the needs of the organization for it to be effective and legally defensible.29
Records Retention Guidelines
Here are some basic records retention guidelines:
- Make records threshold determinations. Examine the content to see if it in fact constitutes a record by your own organization's definition of a record, which should be contained in your IG policies. This records determination process likely also will require consultation with your legal counsel. If the social media site has not been kept operating, or it was used for a specific project that has been completed (and all pertinent records for that project have been retained), then its content may not require retention of records.30
- Use existing retention schedules if they apply. If your organization already has retention policies for, say, e-mail, then any e-mail sent by social media should adhere to that same scheduling guideline, unless there is some legal reason to change it.
- Apply basic content management principles. Focus on capturing all related content for social media posts, including conversation threads, and associated metadata that may be required in legal discovery to provide context and maintain the completeness, authenticity, and integrity of the records.
- Risk avoidance in content creation. Instruct and reinforce the message to employees participating in corporate social media that content on the Web stays there indefinitely and that it carries potential legal risks. In addition, once something is posted on the Web, completely erasing and destroying the content at the end of its retention period is nearly impossible.
Content Control Models
There are several basic ways to manage social media content, ranging from tightly controlling it through one single, accountable person, to delegating control to the business unit level, all the way to letting the social media participants post their thoughts, unmoderated and unfettered, to encourage spontaneity and enthusiastic use of the tool. The approach your organization takes will depend on the specified business objectives you have for utilizing social media and your organization's appetite for risk.
Emerging Best Practices for Managing Social Media Records
Best practices for managing social media business records are still evolving, and will continue to develop as records and information practitioners gain more experience with social media records. Here are some emerging best practices:
- Identify records during the social media planning stage. Both a social media policy and the records and information policy should refer to a form to be completed by the person or unit proposing a new social media initiative. The person completing the form should indicate if records will be created and, if so, how they will be managed.
- Promote cross-functional communications. A social media team of representatives from various departments, such as IT, social media, legal, compliance, records management, and other stakeholders, is formed, and communication and collaboration is encouraged and supported.
- Require consultation in policy development. Extending beyond the social media team, input and advice from multiple stakeholder groups is essential for creating IG policies that cover social media records management.
- Establish clear roles and responsibilities. The cross-functional social media team must lay out clear expectations and responsibilities and draw lines of accountability so that stakeholders understand what is expected of them.
- Utilize content management principles. Management of social media content should fall under an ECM software implementation, which can capture and track content, including associated metadata and external content, and manage that social media content through its life cycle.
- Implement RM functionality. Management by an ERM system that offers features that enable records retention and disposition, implementation of legal holds, and lifting of legal holds is essential.
- Control the content. Clear guidelines and monitoring mechanisms must be in place to control and manage content before it gets published on the Web, when possible (e.g., static content on blogs and profiles in social networks) if there is any potential legal risk at all.
- Capture content in real time. By implementing a real-time content capture solution for content posted directly to social media (e.g., comments on blogs and posting of someone else's content or retweets), organizations will begin their control and management of the content at soonest point and can more easily prove it is authentic and reliable from a legal perspective.
- Champion search capabilities. After capture and preservation of records and associated metadata, search capabilities are the single most important feature that the technology must provide.
- Train, train, train. Social media is a new and emerging technology that changes rapidly. Users must be trained, and that training must be updated and reinforced on a regular basis so that employees have clear guidelines, understand the technology, and understand the business objectives for its use.
CHAPTER SUMMARY: KEY POINTS
- Organizations are increasingly using social media and Web 2.0 platforms to connect people to companies and government.
- Social media use presents unique challenges because of key differences with other electronic communications systems, such as e-mail and IM.
- Two of the biggest risks that social networking poses to organizations are (1) not having a social media policy; and (2) employees may be—intentionally or not—exposing information that is not meant for public consumption.
- Enterprise social networking software has many of the features of consumer social applications such as Facebook, but with more oversight and control, and they come with analytics features to measure adoption and use.
- Various software tools have become available in recent years for archiving social media posts and followers for RM purposes.
- An IG framework provides the overarching policies, guidelines, and boundaries for social media initiatives, so that they may be controlled, monitored, and archived.
- Social media posts are more than the post itself; they include metadata and also include hyperlinks to external content—and that external content must be preserved in its native format to meet legal standards.
- Robust search capabilities are the most crucial component of a social media ERM or archiving solution.
- Social media policy will be unique to each particular organization.
- Best practices for managing social media business records are still evolving but include forming cross-functional social media teams with clear responsibilities, encouraging communication, and capturing complete content in real time.
Notes
1. U.S. National Archives and Records Administration, NARA Bulletin 2011-02, “Guidance on Managing Records in Web 2.0/Social Media Platforms,” October 20, 2010, www.archives.gov/records-mgmt/bulletins/2011/2011-02.html.
3. See www.snapchat.com/ (accessed June 3, 2013).
4. See http://vine.com/ (accessed June 3, 2013).
5. Nancy Gohring, “Facebook and Twitter Rule the Enterprise, Too,” May 20, 2013, www.citeworld.com/social/21893/facebook-twitter-rule-enterprise (accessed June 4, 2013).
6. Andrew Conry-Murray, “Can Enterprise Social Networking Pay Off?” Internet Evolution, March 21, 2009, www.internetevolution.com/document.asp?doc_id=173854.
7. Patricia C. Franks, “How Federal Agencies Can Effectively Manage Records Created Using New Social Media Tools,” IBM Center for the Business of Government, San Jose State University, 2010, www.businessofgovernment.org/sites/default/files/How%20Federal%20Agencies%20Can%20Effectively%20Manage%20Records%20Created%20Using%20New%20Social%20Media%20Tools.pdf, pp. 20–21 (accessed March 30, 2012).
9. Paul McDougall, “Social Networking Here to Stay Despite Security Risks,” Information Week, May 12, 2011, www.informationweek.com/news/security/privacy/229500138.
10. Chris Nerney, “5 Top Social Media Security Threats,” Network World, May 31, 2011, www.network-world.com/news/2011/053111-social-media-security.html.
11. C. Savage, “Soldier Admits Providing Files to WikiLeaks,” New York Times, February 23, 2013, www.nytimes.com/2013/03/01/us/bradley-manning-admits-giving-trove-of-military-data-to-wikileaks.html?ref=bradleyemanning—_r=0 (accessed May 19, 2013).
13. Twitter Statistics, Statistic Brain, www.statisticbrain.com/twitter-statistics/ (accessed May 18, 2013).
14. LinkedIn, “About Us,”www.linkedin.com/about-us (accessed May 18, 2013).
15. Sharon Nelson, John Simek, and Jason Foltin, “Capturing Quicksilver: Records Management for Blogs, Twittering and Social Networks,” Sensei Enterprises, 2009, www.senseient.com/storage/articles/Capturing_Quicksilver.pdf (accessed December 10, 2013).
16. This discussion and the next quotes in this section are from Patricia C. Franks, Records and Information Management (Chicago: American Library Association Neal-Schuman, 2013), p. 179.
17. Sharon Nelson and John Simek, “Mitigating Legal Risks of Using Social Media,” Information Management 45, no. 5 (September/October 2011), ARMA International.
18. Liz Gannes, “Saving the Social Web for Later Use: Jolicloud Organizes Everything You've Shared, Liked, and Favorited,” March 19, 2012, http://allthingsd.com/20120319/saving-the-social-web-for-later-use-jolicloud-organizes-everything-youve-shared-liked-and-favorited/.
19. Nick Summers, “Jolicloud Rebrands Its Unified Cloud Platform as Jolidrive, Adds the Ability to View and Edit Files,” TNW, March 6, 2013, http://thenextweb.com/insider/2013/03/06/jolicloud-rebrands-its-unified-cloud-service-as-jolidrive-adding-the-ability-to-edit-and-view-files/ (accessed May 18, 2013).
20. Social Folders, “About Us,” http://socialfolders.me/about-us/ (accessed May 18, 2013).
21. Andy Opsahl, “Backing Up Twitter and Facebook Posts Challenges Governments,” Government Technology, January 20, 2010, www.govtech.com/policy-management/Backing-Up-Twitter-and-Face-book-Posts.html?utm_source=related—utm_medium=direct&utm_campaign=Backing-Up-Twitter-and-Facebook-Posts.
23. The next discussion is based on Franks, “How Federal Agencies Can Effectively Manage Records.”
24. Nelson and Simek, “Mitigating Legal Risks of Using Social Media.”
26. Best Buy Social Media Policy, http://forums.bestbuy.com/t5/Welcome-News/Best-Buy-Social-Media-Policy/td-p/20492 (accessed December 10, 2013).
27. The next discussion is based on Rakesh Madhava, “10 Things to Know about Preserving Social Media,” Information Management (September/October 2011): 34–35, 37. ARMA International.
28. Franks, Records and Information Management, p. 151.
30. Guidelines here and in the next section are from New York State Archives, “Records Advisory: Preliminary Guidance on Social Media,” May 24, 2010, www.archives.nysed.gov/a/records/mr_social_media.shtml.
* Portions of this chapter are adapted from Chapter 13, Robert F. Smallwood, Managing Electronic Records: Methods, Best Practices, and Technologies, © John Wiley — Sons, Inc., 2013. Reproduced with permission of John Wiley — Sons, Inc.
