Chapter 11
Mobile Devices
In This Chapter
![]() Seeking out the common weaknesses in laptops, phones, and tablets
Seeking out the common weaknesses in laptops, phones, and tablets
![]() Executing security tests to uncover crucial mobile flaws
Executing security tests to uncover crucial mobile flaws
![]() Exploring the security vulnerabilities associated with the Internet of Things (IoT)
Exploring the security vulnerabilities associated with the Internet of Things (IoT)
![]() Minimizing mobile security risks
Minimizing mobile security risks
Mobile computing is the new target for business — and for hacking. It seems that everyone has a mobile device of some sort for either personal or business use; often both. If not properly secured, mobile devices connected to the enterprise network represent thousands upon thousands of unprotected islands of information floating about, out of your control.
Because of all the phones, tablets, and laptops running numerous operating system platforms chock-full of apps, an infinite number of risks are associated with mobile computing. Rather than delving into all the variables, this chapter explores some of the biggest, most common mobile security flaws that could impact you and your business.
Sizing Up Mobile Vulnerabilities
It pays to find and fix the low-hanging fruit on your network. That’s where you get the most bang for your buck. The following mobile laptop, phone, and tablet weaknesses should be front and center on your priority list:
- No encryption
- Poorly implemented encryption
- No power-on passwords
- Easily guessed (or cracked) power-on passwords
For other technologies and systems (web applications, operating systems, and so on), you can usually find just the testing tool you need. However, for finding mobile-related flaws, relatively few security testing tools are available. Not surprisingly, the more expensive tools often enable you to uncover the big flaws with the least amount of pain and hassle.
Cracking Laptop Passwords
Arguably the greatest threat to any business’s security is unencrypted laptops. Given all the headlines and awareness about this effectively inexcusable security vulnerability, I can’t believe it’s still so prevalent in business. This section explores tools you can use to crack unencrypted laptop passwords on Windows, Linux, or Mac OS X systems. You then find out about the basic countermeasures to prevent this vulnerability.
Choosing your tools
My favorite tool to demonstrate the risks associated with unencrypted laptops running Windows is ElcomSoft System Recovery (www.elcomsoft.com/esr.html). You simply burn this tool to a CD and use it to boot the system you want to recover (or reset) the password from, as shown in Figure 11-1.

Figure 11-1: ElcomSoft System Recovery is great for cracking and resetting Windows passwords on unprotected laptops.
You have the option to reset the local administrator (or other) password or have it crack all passwords. It’s really that simple, and it’s highly successful, even on the latest operating systems, such as Windows 8.1 or Windows 10. The most difficult and time-consuming thing about ElcomSoft System Recovery is downloading and burning it to CD.
You can also use an older tool for Windows called NTAccess (www.mirider.com/ntaccess.html) for resetting local Windows accounts. This program isn’t pretty or fancy, but it does the job. There are others available as well. As with ophcrack (discussed a little later in this section), ElcomSoft and NTAccess provide an excellent way to demonstrate that you need to encrypt your laptop hard drives.
After you reset or crack the local administrator (or other) account, you can log in to Windows and have full access to the system. By simply poking around using WinHex (www.winhex.com/winhex) or similar or AccessEnum (https://technet.microsoft.com/en-us/library/bb897332.aspx), you can find sensitive information, remote network connections, and cached web connections to demonstrate the business risk. If you want to dig even deeper, you can use additional tools from ElcomSoft (www.elcomsoft.com/products.html), such as ElcomSoft Internet Password Breaker, Proactive System Password Recovery, and Advanced EFS Data Recovery for uncovering additional information from Windows systems. Passware (www.lostpassword.com) offers many similar commercial tools as well.
If you’re budget-strapped and need a free option for cracking Windows passwords, you can use ophcrack as a standalone program in Windows by following these steps:
- Download the source file from
http://ophcrack.sourceforge.net. Extract and install the program by entering the following command:
ophcrack-vista-livecd-3.6.0.exe(or whatever the current filename is)- Load the program by starting the ophcrack icon from your Start menu.
Click the Load button and select the type of test you want to run.
In this example, shown in Figure 11-2, I’m connecting to a remote server called server1. This way, ophcrack will authenticate to the remote server using my locally logged-in username and run pwdump code to extract the password hashes from the server’s SAM database. You can also load hashes from the local machine or from hashes extracted during a previous pwdump session.
The extracted password hash usernames will look similar to those shown in Figure 11-3.
Click the Launch icon to begin the rainbow crack process.
If you see that password hashes are only in the NT Hash column as shown in Figure 11-3, you’ll need to make sure you have downloaded the proper hash tables from
http://ophcrack.sourceforge.net/tables.phpor elsewhere. A good one to start with would be Vista special (8.0GB). In order to load new tables, you click the Tables icon at the top of the ophcrack window as shown in Figure 11-4.

Figure 11-2: Loading password hashes from a remote SAM database in ophcrack.

Figure 11-3: Usernames and hashes extracted via ophcrack.

Figure 11-4: Loading the required hash tables in ophcrack.
If necessary, relaunch the rainbow crack process in Step 5. The process can take just a few seconds to several days (or more) depending on your computer’s speed and the complexity of the hashes being cracked.
There’s also a bootable Linux-based version of ophcrack (available at http://ophcrack.sourceforge.net/download.php?type=livecd) that allows you to boot a system and start cracking passwords without having to log in or install any software.
Countermeasures
The best safeguard against a hacker using a password reset program against your systems is to encrypt your hard drives. You can use BitLocker in Windows, WinMagic SecureDoc (www.winmagic.com/products), or other preferred product for the platform your systems are running on.
Power-on passwords set in the BIOS can be helpful as well, but they’re often a mere bump in the road. All a criminal has to do is reset the BIOS password or, better yet, simply remove the hard drive from your lost system and access it from another machine. You also need to ensure that people can’t gain unauthorized physical access to your computers. When a hacker has physical access and your drives are not encrypted, all bets are off. That said, full disk encryption is not foolproof — see the nearby sidebar, “The fallacy of full disk encryption.”
Cracking Phones and Tablets
I don’t envy IT administrators and information security managers for many reasons but especially when it comes to the bring your own device (BYOD) movement taking place in business today. With BYOD, you have to trust that your users are making good decisions about security, and you have to figure out how to manage each and every device, platform, and app. This management task is arguably the greatest challenge IT professionals have faced to this point. Further complicating matters, you have criminal hackers, thieves, and other hooligans doing their best to exploit the complexity of it all, and it’s creating some serious business risks. The reality is that very few businesses — and individuals — have their phones and tablets properly secured.
Plenty of vendors claim that their mobile device management (MDM) solutions are the answer to phone and tablet woes. They’re right … to an extent. MDM controls that separate personal information from business information and ensure the proper security controls are enabled at all times can help you make a big leap toward locking down the mobile enterprise.
One of the greatest things you can do to protect phones and tablets from unauthorized use is to implement this nifty security control that dates back to the beginning of computers: passwords. Yep, your phone and tablet users should employ good old-fashioned passwords (technically passphrases) that are easy to remember yet hard to guess. Passwords are one of the best controls you can have. Yet there are plenty of mobile devices with no passwords or passwords that are easily cracked.
In the following section, I demonstrate accessing mobile devices by using a commercial forensics tool. Keep in mind that such tools are typically restricted to law enforcement personnel and security professionals, but they could certainly end up in the hands of the bad guys. Using such tools for your own information security testing can be a great way to demonstrate the business risk and make the case for better mobile controls.
Cracking iOS passwords
I’d venture to guess that many phone and tablet passwords (really, they’re just 4-digit PINs, or passcodes) can be guessed outright. A mobile device gets lost or stolen and all the person recovering it has to do is try some basic number combinations such as 1234, 1212, or 0000. Soon, voilà! — the system is unlocked.
Many phones and tablets running iOS and Android are configured to wipe the device if the incorrect password is entered X number of times (often 10 failed attempts). A reasonable security control indeed. But what else can be done? Some commercial tools can be used to crack simple passwords/PINs and recover information from lost or stolen devices or devices undergoing a forensics investigation.
ElcomSoft’s iOS Forensic Toolkit (http://ios.elcomsoft.com) provides a means for demonstrating just how easily passwords/PINs on iOS-based phones and tablets can be cracked up through iOS version 7. Here’s how:
Plug your iPhone/iPod/iPad into your test computer and place it into Device Firmware Upgrade (DFU) mode.
To enter DFU mode, simply power the device off, hold down the Home button (bottom center) and sleep button (often the upper right corner) at the same time for 10 seconds, and continue holding down the Home button for another 10 seconds. The mobile device screen goes blank.
Load the iOS Forensic Toolkit by inserting your USB license dongle into your test computer and running Tookit.cmd.
You see the screen shown in Figure 11-5.
Load the iOS Forensic Toolkit Ramdisk onto the mobile device by selecting option 2 LOAD RAMDISK.
Loading the RAMDISK code allows your test computer to communicate with the mobile device and run the tools needed for cracking the password (among other things).
Select the iOS device that’s connected, as shown in Figure 11-6.
I selected option 14 because I have an iPhone 4 with GSM.
You now see the toolkit connect to the device and confirm a successful load, as shown in Figure 11-7. You should see the ElcomSoft logo in the middle of your mobile device’s screen as well.
To crack the devices password/PIN, simply select option 6 GET PASSCODE on the main menu.
iOS Forensic Toolkit will prompt you to save the passcode to a file. You can press Enter to accept the default of passcode.txt. The cracking process will commence and, with any luck, the passcode will be found and displayed as shown in Figure 11-8.
So, having no password for phones and tablets is bad, and a 4-digit PIN such as this is not much better. User beware!
You can also use iOS Forensic Toolkit to copy files and even crack the keychains to uncover the password that protects the device’s backups in iTunes (option 5 GET KEYS).
 Using ElcomSoft’s iOS Forensic Toolkit to crack iOS versions 8 and up won’t be quite as fruitful for now as Apple has finally started to really lock down the operating system. Apple iOS is still not without its flaws. As recently as iOS 9, there was an exploit that allowed attackers to bypass the login screen altogether.
Using ElcomSoft’s iOS Forensic Toolkit to crack iOS versions 8 and up won’t be quite as fruitful for now as Apple has finally started to really lock down the operating system. Apple iOS is still not without its flaws. As recently as iOS 9, there was an exploit that allowed attackers to bypass the login screen altogether.If anything, you need to be thinking about how your business information, which is most certainly present on phones and tablets, is going to be handled in the event one of your employee’s devices is seized by law enforcement personnel. Sure, they’ll follow their chain-of-custody procedures, but overall, they’ll have very little incentive to ensure the information stays protected in the long term.

Figure 11-5: iOS Forensic Toolkit’s main page.
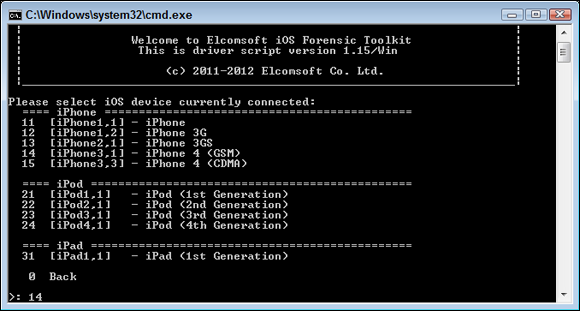
Figure 11-6: Select the appropriate iOS device from the list.

Figure 11-7: iOS Forensic Toolkit Ramdisk loading successfully.

Figure 11-8: Cracking a 4-digit PIN on an iPhone.
Oxygen Forensic Suite (www.oxygen-forensic.com) is an alternative commercial tool that can be used for cracking iOS-based passwords as well as additional recovery functionality for Android-based systems. Figure 11-9 shows the Oxygen Forensic Suite interface and types of information that can be extracted from an Android-based device. The Oxygen Forensic Suite Extractor tool can connect and extract this information relatively quickly — something that can, of course, be used against your organization when mobile devices are lost or stolen.

Figure 11-9: Oxygen Forensic Suite.
Oxygen Forensic Suite is also great for performing security assessments of mobile apps, which I cover in Chapter 15.
Countermeasures against password cracking
The most realistic way to prevent such password cracking is to require — and continually enforce — strong passwords such as multi-digit PINs consisting of 5 or more numbers or, better yet, complex passphrases that are very easy to remember yet practically impossible to crack such as Progressive_r0ck_rules!. MDM controls can help you enforce such a policy. You’ll likely get pushback from employees and management, but it’s the only sure bet to help prevent this attack. I cover getting buy-in for your security initiatives in Chapter 20. Good luck!

 People will tell you they don’t have anything important or sensitive on their laptops. They do. Even seemingly benign laptops used for training or sales can have tons of sensitive information that can be used against your business. This includes spreadsheets that users have copied from the network to work on locally, VPN connections with stored login credentials, web browsers that have cached browsing history, and even worse, website passwords that users have chosen to save.
People will tell you they don’t have anything important or sensitive on their laptops. They do. Even seemingly benign laptops used for training or sales can have tons of sensitive information that can be used against your business. This includes spreadsheets that users have copied from the network to work on locally, VPN connections with stored login credentials, web browsers that have cached browsing history, and even worse, website passwords that users have chosen to save. Mobile apps can introduce a slew of security vulnerabilities into your environment, especially certain apps available for Android via Google Play that aren’t properly vetted. In recent source code analysis using Checkmarx’s CxSuite (see
Mobile apps can introduce a slew of security vulnerabilities into your environment, especially certain apps available for Android via Google Play that aren’t properly vetted. In recent source code analysis using Checkmarx’s CxSuite (see