3 New Era of Digital Devices: IoT, Infotainment, Wearables, and Drones
Our world is wired. We were inundated with cell phones, then smart phones, and now IoT (Internet of Things) devices, infotainment devices, wearables, and drones. This chapter deals with a small set of device categories within the Internet of Things. Although infotainment devices and wearables could be categorized as IoT devices, because of their consumer functions and popularity, I’ll discuss them as separate entities here. Many, including drone manufacturers, have argued that drones, or technically unmanned aircraft systems (UASs), could also be lumped into the IoT category.
Today’s examiner faces a huge challenge with numerous devices more complicated than the smart phone. Just when mobile phone examiners were making progress in the “Wild West” methodologies, IoT devices, in-vehicle systems, wearables, and drones rode into town. Manufacturers of smart phones did not lay out their file system formats, and even today there are only a few published books that intelligently cover processing these devices. A limited number of articles have been written and research conducted regarding the devices discussed in this chapter, and they have been done completely by research and development groups, without assistance or documentation from any manufacture resource.
With these devices, it seems forensic examiners have returned to the Wild, Wild West. However, this time, not only must the examiner work with more types of devices, but he or she faces many more obstacles in the pursuit of forensic data—from finding the storage location, to gaining access to the controller, to “speaking” to the device, to extracting the data, and, most importantly, to understanding the data format and layout.
![]()
These hurdles are similar to those I faced when I started in the mobile forensic field, but I believe the problems associated with this current field of devices surpasses those faced by mobile forensic pioneers in the early days.
Research into these types of devices, their investigation, and their analysis should be a priority. Delving and probing into the functionality of these devices and their relationship to investigations should drive this prioritization. By prioritization, I’m referring to increased understanding how and if a connected device or devices are or can be involved in the case or investigation that is underway.
As discussed in previous chapters, the methods we use to conduct a proper search for digital devices in a crime scene have changed with today’s connected devices. In the triage of the crime scene, the investigator must be cognizant of connected devices. With so many electronic possibilities—from refrigerators, doors, windows, lights, thermostats, and televisions, to personal assistance devices (such as Alexa and Google Home), wearables (such as Fitbit or Apple Watch), and other devices—one thing is clear: nothing in digital forensics is absolute or routine. Today’s investigator must be familiar with a radically confusing “electronic scene.” Moreover, it is ever important that the investigator triage based upon various conditions, including involvement in the case, probability of extraction, and the likelihood of parsing/decoding the data. A simple example could be determining whether or not to seize a refrigerator. If the fridge is simply an “intelligent” refrigerator, or one that uses sensors to monitor the device and/or contents without network connectivity but the investigation involves a cyber crime, a seizure would not make sense. However, if the fridge was a truly connected device (an IoT device), seizing it as evidence could make sense if details from other sources such as a router or gateway pointed to this device. Or consider a wearable device found at the scene of a violent crime or a drone found at a residence known for drug trafficking. Today’s crime scene triage has become a daunting task with the widespread use of these types of devices, not only for the fact of identifying them but also for processing and exploring the data they contain.
This chapter introduces the various connected devices, provides examples of related devices, discusses how they fit in the digital forensic investigation cycle, and shows how the investigation cycle might affect the approach of the examiner if, and when, such a device comes into the forensic lab.
IoT Devices
An IoT device is an electronic device that has been embedded with technology to be controlled and to interact over the Internet. Forbes magazine, back in 2014, said that anything that has an on and off switch to connect to the Internet and/or to another device can be considered an IoT device. Much like mobile devices, the number of IoT devices has exceeded the world’s population—and the number is increasing at a much faster pace. In 2017, Gartner stated that there were currently 8.4 billion IoT devices in use globally; it also reported that by 2020, the IoT set of devices that are available throughout the world will reach 20.4 billion.
Figure 3-1 shows, in simple terms, what an IoT device is and what makes this technology quite useful for today’s connected world. The implications of the device’s digital footprint are limitless. Requests are made from a remote or local device through the Internet, and data is returned to the device, often with asynchronous communication between connected devices and/or remotely controlled devices. With both inbound and outbound communications, the exposure of the device to the outside world is a given, and with few security precautions available in many devices, cases involving unauthorized access will skyrocket.
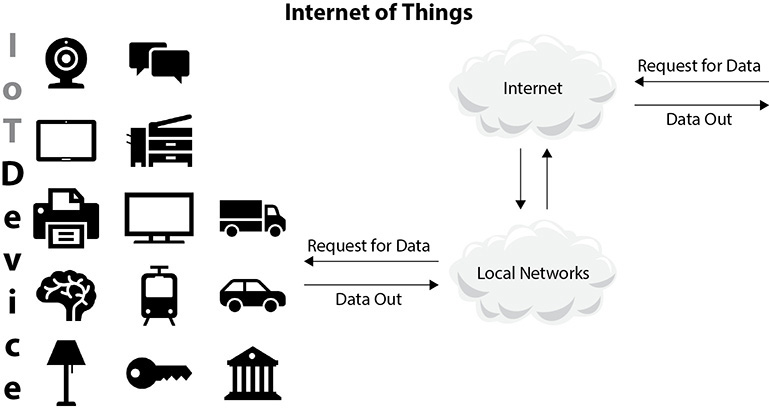
FIGURE 3-1 Simple communication of various devices through an Internet gateway and back
![]()
Visit the Shodan web site to see just how many IP webcams and security cameras around the world have been exploited and compromised.
A noticeable change to the device architecture for an IoT device from that of a mobile device is the underlying operating system (OS) in most connected devices. In today’s mobile device operating systems for both Androids and iOS, and even in the PC OS for Windows, there are limitations regarding the small embedded devices in the IoT world. One big limitation is simply the size, or footprint, of the traditional OS. Another issue with traditional OS and connected embedded systems is speed or timing of computations. Embedded devices within a vehicle, such as an air bag or automatic braking, that report back to the onboard computer and then to the manufacturer, or even data monitoring companies (such as OnStar), rely on timing from action to results. If a crash is detected, the safety mechanisms must respond without delay. This is where a traditional OS would be a detriment and a real-time OS is required. Enter the Real Time Operating System (RTOS) format.
RTOS uses absolute time iterations to complete the processing of an event. RTOS is not new: it is used in the firmware of Android baseband processors and feature phones, both old and new. Samsung’s proprietary operating system is based on RTOS, as are devices from LG. (These feature phones are covered in Chapter 12, as are the file systems that are produced.) With today’s connected devices and their embedded systems, it makes sense for manufacturers to utilize an RTOS because of its small footprint, low power requirement, and lack of latency—and in the case of medical and safety equipment, RTOS is a necessity.
Categories of Connected Devices
Connected devices can be placed into several categories based primarily on their functionality and use—primarily consumer, enterprise, and industrial devices. Most devices encountered by investigators will be consumer-based devices, but in certain circumstances other types can be involved.
Consumer Devices
Consumer connected devices include stereos, televisions, appliances, thermostats, windows, doors, garage doors, and lights—to name a few. Most consumer IoT devices generally have the added word “smart” to the product name (smart TV, smart refrigerator, or smart thermostat, for example). With the availability of consumer devices increasing around the world, from high-end electronic stores to the local big box store, the likelihood an investigator will deal with “smart” devices grows every day. Consumer devices, much like all other connected devices, come with an operating system, which could be a simple Android system, or RTOS, Linux, Tizen, and many other variants. The OS in use is highly dependent on the size of the connected device—for example, the OS on a wearable is drastically different from that of a smart TV.
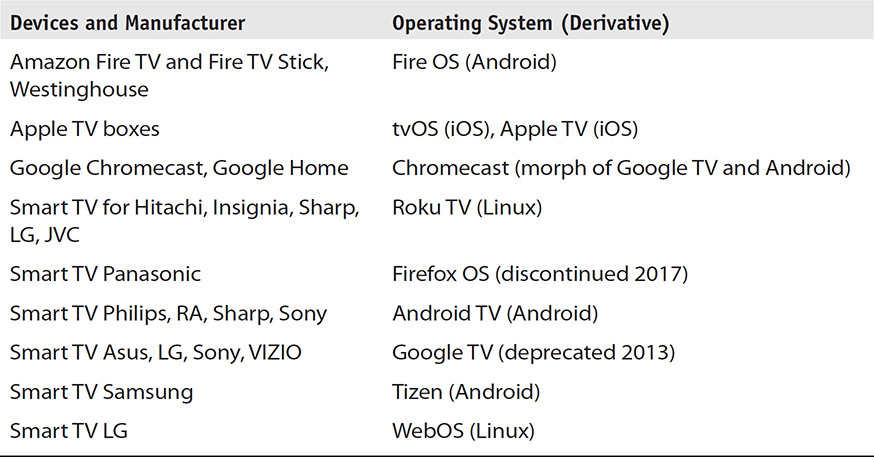
Table 3-1 lists some of the operating systems found in smart TVs that could help direct an examination of an embedded file system. Many of the operating systems listed are also found in appliances ranging from refrigerators to interactive thermostats with full-featured access to the Internet, as well as third-party applications.
TABLE 3-1 Common Smart TVs and Their Underlying Operating Systems
![]()
Various file system examples will be covered in Chapter 16 along with a discussion of worthwhile artifacts within the systems of these devices.
Just because a device may have an OS does not necessarily make it a part of the IoT family. As mentioned, and clearly referenced in the acronym, the IoT device must be connected to the Internet. Consumer devices are generally connected via Wi-Fi, Bluetooth, and Ethernet. Most of these devices, for sheer portability and range, use Wi-Fi to transmit and receive data and to communicate with other IoT devices; many use ZigBee or Z-Wave as well. Connection information could be good artifacts to harvest in an investigation simply because the device can leave identifying IDs such as media access control (MAC) addresses. The MAC address is a unique electronic fingerprint that is assigned and embedded on the device when it’s manufactured. Using this unique hardware number can lead the investigator to the connected device involved in a particular event. A connected IoT garage door or thermostat will have a unique address if it is used to communicate via a gateway to other connected devices or to the Internet. By understanding the gateway and control, you can start your investigations involving IoT devices that have been compromised from a more informed position.
With access to the Internet, a smart TV becomes an all-in-one computer, whether the user is browsing the Internet via the built-in web browser, using Facebook, viewing YouTube, talking on Skype, or even reading messages sent from a mobile device. All of this information can be available on the connected smart device. From Wi-Fi cameras to doorbells with video, data evidence of an event may be held within theses devices or their storage containers. The examiner must be prepared to dig deep into their file systems, because commercial tools do not currently support these types of device images and artifacts.
Enterprise Devices
Enterprise IoT devices offer connectivity from one device to another within the general enterprise sector. Enterprise devices include VoIP telephones, videoconferencing equipment, IP-connected security cameras (CCTV), smart HVAC systems, smart printers, and many other connected devices. With the proliferation of devices connected at the enterprise, in addition to mobile devices, it is no surprise that hacking attempts are at the forefront of business infiltration.
As with devices in consumer and industrial sectors, the security of an enterprise device is not the top priority of most manufacturers. In 2016, an ethical hacker reported in darkreading.com about the ease of hacking into such a device in the article “Common Enterprise IoT Devices Are Hackable in Under Three Minutes” (www.darkreading.com/iot/common-enterprise-iot-devices-are-hackable-in-under-three-minutes/d/d-id/1327300). This article may be several years old, but today’s IoT devices are still vulnerable to attack with little difficulty due to the proliferation of devices within an enterprise. Enterprises can face security issues if IoT devices are unchecked for installed security measures. These days, the weakest links in the enterprise are consumer wearables (watches, sound devices, video devices, smart TV, and so on) that connect to the network. Consumer-grade IoT devices often have lower standards for security, and as a result, the user of the consumer wearable often inadvertently exposes the enterprise network.
From an infiltrated network creating zombies of IoT devices, to hackers unleashing attacks on external targets or gaining access via a device to spy on, listen to, or destroy a network, today’s attack surfaces are immense with the introduction of IoT devices. Currently, network infection can occur in under three minutes, with a dwell time (compromise to discovery) of 101 days on average, according to FireEye’s report “M-Trends 2018” (www.fireeye.com/content/dam/collateral/en/mtrends-2018.pdf). This problem will likely increase around the globe with the proliferation of IoT devices. Today’s response plan and investigator must be educated to understand these enterprise-connected devices.
Industrial Devices
Industrial IoT devices, as a general definition, offer connectivity from a device to another device within the transport, energy, and industrial sectors. Within the transport sector, both machinery and vehicles can offer connected solutions, while the energy sector includes oil, gas, and water machinery as well as the power grid. Industrial solutions can include machinery interconnected to larger machinery and monitoring equipment. These examples do not represent the entire application for industrial IoT but easily paint a picture of the possible investigation implications.
The connection, or rather infiltration or damage, to any of these sectors via compromised IoT devices can have catastrophic effects on not only local populations but also globally. This possibility is why many of the industrial applications claim to be “air-gapped.” An air-gapped device or series of devices is not directly connected to an external network. The device essentially operates autonomously, without the possibility of external infiltration, in theory. Of course, penetration is possible—remember Stuxnet, the worm introduced to an air-gapped system using USB drives and new innovations such as LED data transmission interception? What does all this have to do with IoT devices? Actually a lot, because a large number of devices in air-gapped systems, especially those involved in coordinating maintenance needs, levels, and downed systems, must be connected to external sources.
A perfect example of this is the maintenance of airplanes. The United States Title 14 of the Code of Federal Regulations (14 CFR) part 91, § 91.1109 “Aircraft maintenance: Inspection program” and FAR 91.409 outline the requirements for mandatory inspections of aircraft. Within these requirements are sections that outline classes of inspection that state that airlines must maintain an “airworthiness” certificate. The minimum requirements are services every 12 months, 100 hours of service, and preflight checks. However, U.S. airlines utilize different guidelines on maintenance to indicate that an inspection must be made every 12 months (1–2 weeks out of service), every 6 months (1–3 days out of service), and 500 hours (10 hours out of service). Mentioned are the weeks, days, and hours out of service, which cost the airlines tens of thousands of dollars every day. In an effort to respond to, or rather predict, such issues, IoT devices are used to detect potential failure of parts before they actually fail. Sensors placed throughout the airplane machinery gather information, and the data is analyzed constantly to create the maintenance schedule, as well as order parts and the technician for the aircraft, all in an effort to predict the life cycle of each part. Are you ready to analyze tampering in infiltration of such a system?
![]()
This book, of course, will not cover the triage of sensors or systems used in the aerospace industry, but you can be sure that experts in these areas are needed in the event of disasters or civil litigation.
Common Consumer Types
The investigator will likely run into consumer-based IoT devices more often than those within the enterprise or industrial sector. Two consumer-based devices are covered in this section: Amazon Alexa and Google Home. The information covered includes an introduction to the device, the device’s value to an investigation, what artifacts might be gleaned, and how well the device is supported by commercial or open source tool sets. Chapter 16 will discuss details on file system artifacts, Cloud data, and advanced topics on both devices.
Amazon Alexa
On August 31, 2012, a patent was filed by Amazon for a device built as an artificial intelligence machine. Alexa was born just two years later, but not as a device: Alexa is the assistant that is used in the Echo family of devices (which includes Dot, Tap, Echo, Echo Plus, Spot, Look, and Show). Alexa will interact with built-in functions to play music, order items from Amazon, provide news and weather information, set timers and alarms, recite movie listings, update calendars, and more. Currently, Alexa can interact with other smart devices within the connected home (lights, thermostats, and so on) via Alexa Voice Service (AVS).
Alexa does not stop there, however. Amazon enables Alexa to use a crowd-sourcing mentality to build Alexa’s “skills,” the term used by Amazon to define what Alexa can do and how it can interact. Because there are thousands of other IoT devices, and even companies, that want to be able to be reached, Amazon allows these entities and devices to do so via Alexa. The Alexa Skills Kit is an API collection that facilitates the building of Alexa’s vocabulary (skills), allowing the device to recognize thousands of additional terms to provide thousands of additional functions. From placing orders to Starbucks, to contacting Uber, to answering Jeopardy quizzes and question of the day, you can simply add skills and ask Alexa. The Amazon Echo Plus also began to utilize ZigBee to communicate with other IoT devices along with the standard wireless technologies, and now it can be considered an IoT hub as well.
Alexa needs user interaction to begin to use its skills base. This interaction is known as the “wake word.” Alexa’s original wake word is “Alexa,” but with Amazon devices, the current wake words are Alexa, Echo, Amazon, and Computer. Most devices, however, enable you to change the wake word within the Alexa app. (The only exception to this is on the Tap. When a user utters a wake word, the device is set to listen to the next request. This request could be “find a recipe for tri-tip,” “what is the score of the Washington Nationals game?,” or even “what is the weather in Jamaica this week?”)
The interesting thing about Alexa is the “learning” that goes on behind the scenes, on the Amazon servers. The learning side of these devices enables your requests to move from saying “Washington Nationals” to simply saying “Nationals” on subsequent requests. The recording will stay on the server, and a user can keep track of requests on his or her mobile device via the Alexa app. This information is stored in Settings | History. Here, the user can see what is on the server and remove the information one item at a time. If all items are to be purged, a user can use the app to clear the entire history all at once. The words stored on the Amazon servers are used for targeted advertisements and to learn as much about the user as possible.
So if a wake word is used to start using the tool, wouldn’t that mean the device is always listening? The answer to this is yes; the device is always listening, but Amazon insists that nothing is recorded to the servers until the wake word is mentioned. In a patent filed by Amazon (US8798995B) and granted in 2014, and again submitted in 2017 under US20170323645A1, some language is included that should cause anyone to wonder whether the wake word really starts the recording process. Within both patents, Amazon specifically says otherwise and mentions actively listening to conversations. Here’s an excerpt from the patent application:
While phone conversations are described in many of the examples herein, it should be understood that there can be various situations in which voice data can be obtained. For example, a user might talk to a friend about purchasing a mountain bike within an audio capture distance of that user’s home computer. If the user has authorized the home computer to listen for, and analyze, voice content from the user, the computer can obtain keywords from the conversation and automatically provide recommendations during the conversation, such as by displaying one or more Web sites offering mountain bikes, performing a search for mountain bikes, etc. If the user discusses an interest in a certain actor, the computer could upload that information to a recommendations service. ...
In April 2018, several news outlets, from BBC to Wired, suggested that Amazon had filed a patent for a “voice-sniffing” technology that would allow the device to listen to any conversation within its range and send that data to Amazon servers. This use, of course, was denied by Amazon, but the company did indicate that the patent was filed as a “forward-thinking” application. However, in May 2018, a user of the Echo product contacted Amazon as well as media outlets to report that a private conversation she and her husband had while in their house was, unbeknownst to them, sent to a contact in their phone book. Amazon admitted that the technical issue was a bug, and the company said it would fix the problem as soon as possible. But this is not the last time voice-sniffing will be in the news—or spoken about in the forensic lab.
Where Is Alexa Hiding the Data?
The devices that house Alexa are generally using approximately 256MB of RAM and 4GB of storage space. Currently, no commercially available tools can access the device via noninvasive means (such as cable or Bluetooth), nor are any tools available to process a raw file system that is acquired by invasive means (JTAG, ISP, chip-off), but access to the valuable data is achievable. If a raw file system is obtained, the underlying OS will be determined by the version of the hardware. Prior to the second-generation Echo Dot, the OS was generic Linux, which then switched to pure Android and continues to run Android but has transitioned to the forked version of Android, called Fire OS. Again, commercial tools are not currently extracting data directly from the device or supporting the direct parsing of an imported file system.
Alexa, however, stores data within the user’s Amazon Cloud account and the Alexa app, as observed in research, as well as documented in Digital Investigation 22 (2017) S15-S25, “Digital forensic approaches for Amazon Alexa ecosystem.” Information such as account, searches, communication (calls/messages), Wi-Fi (passwords), linked calendars, lists of skills, lists of third parties, user activity, devices using the service, and the voice file (utterance and actual user’s voice) are stored on the Cloud. Information on the mobile device is generally stored within SQLite databases and can include token information, user identification, and a web cache. The web cache can contain valuable historical data to include URLs, searches, and more.
The information that can be obtained from this type of consumer IoT device is quite amazing and could be used in many different types of investigations. In fact, in 2015, a case in Arkansas was in the spotlight and hinged on Alexa data. After a murder occurred at a residence, the owner of the house was arrested. Subsequently, digital devices at the residence were seized, which included an Amazon Echo. Police sought to determine whether anything had been recorded on the device at the time of the crime. Via a warrant, prosecutors requested that Amazon release the data, which Amazon refused to do, indicating that the request was over-reaching. In 2017, the homeowner gave his consent to release the data from the device. Once released, however, the data was not used in the case and the murder charge was eventually dismissed. The data was not usable in this particular case, but as described, Amazon would not release the data even with a search warrant, most likely because the supporting facts in the affidavit did not support “why” this data may be relevant or “what” could be obtained.
Google Home
Google Home was released as a smart speaker in 2016, with Google Assistant added as the artificial intelligence operator for the device. Google Assistant had been preceded by Google Now, which was the voice search function within Android devices since 2012. The device, along with Google Assistant, enables the user to play music, control other smart devices for home automation, set a calendar, make calls, read news, and much more.
In 2017, two other devices in the Home series were released, the Home Mini and Home Max. All devices, much like the Amazon Echo, respond to voice commands. The wake word (or hotword) for Google Home is “Ok Google” or “Hey Google.” A difference in Google Home hardware versus, say, the Amazon Echo Plus is the Amazon product’s distinction as an IoT hub. Google Home hardware is not considered a hub in that it cannot relay data from one IoT device to another IoT device, primarily because it lacks a common, global wireless protocol such as ZigBee or Z-Wave.
Similar to Alexa’s skills, the Google Assistant has “actions.” Actions are how Google Assistant’s functionality can be extended. Utilizing an API via the Google Client Library, a developer can build a story based upon what the user wants to do and the fulfillment of the action. Actions are available on the “Actions on Google” page at https://assistant.google.com/explore. All actions are carried out within the Cloud, so the voice request is recorded, sent to the Cloud and analyzed, and then returned to Google Assistant for a reply. All requests, either by stock Assistant functions or a third party, are logged in the user’s Google account.
The Google Assistant and Alexa have many things in common, but one feature that can be of interest for investigators is the number of supported voices. Google Assistant and its Home products were first to allow the recognition of multiple individuals and deliver content based on the person speaking and/or making the request. Alexa, however, made this functioning available only recently. Both devices record requests to their servers, and investigators can play the recorded content to determine, by voice, who made the requests.
Google Home devices can be controlled and maintained by the Google Home app. Within the Home app any device (such as Chromecast or Google Home) can be controlled and viewed. The activity for the device can be viewed by selecting the device from More Settings | Devices, clicking the three dots in the upper-right corner of the screen, and selecting My Activity. Also, data can be found under the user account at myactivity.google.com.
Where Is Google Home Hiding the Data?
Like the Amazon Echo, Google Home devices do not have large storage disks or RAM; the Home device has less storage. Google Home devices have built-in 256MB flash for storage and 512MB synchronous DRAM (SDRAM). The operating system of the device is built on Chromecast, which happens to be based on Android and is called Chrome OS. Currently, commercial tools cannot physically attach to the device to extract data using regular means (such as USB or Bluetooth). Other invasive techniques are available to include the removal of the flash module. However, as with the Echo, parsing of Google Home device data will be manual because commercial tools do not support the file system artifacts.
Because of the format and functionality of the Google Home device, and much like the Amazon devices, the data is almost completely Cloud-based. The Google Home app, as well as the Google Assistant app, stores settings for the devices, but the data travels to the Cloud, is processed, and then returns to be delivered. Clicking any of the settings for activity within the Google Home app, the user is sent to the myactivity.google.com site, which is further evidence of the lack of persistent data within the app itself. An investigation of the data that is recovered from the Cloud store under a user account is extremely verbose. Items include location, with date and times, voice and audio transcribed and recorded, search history, and third-party app usage (such as Spotify, Facebook, and so on) via Google Assistant. All this information is displayed in the myactivity.google.com site for the user (Figure 3-2). Several commercial tools, including Oxygen Forensic Detective and Cellebrite UFED Cloud Analyzer, support the extraction of the Google My Activity.
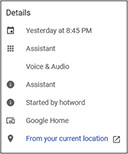
FIGURE 3-2 A quick look at recorded details of a Google Home request that includes incredible data for an investigator
Infotainment Systems
Infotainment devices built into today’s vehicles (in-car entertainment) are considered a subcategory of an IoT device, by definition, with “extra features.” However, this inclusion speaks primarily to the user interaction area. But what about the car’s performance or other systems that interact with the car’s manufacturer, other components, or other vehicles? A clearer name, as it relates to data for an investigation, would be “in-vehicle-information system.” In 2018, Gartner projected that more than 50 million automobiles were connected to the Internet through these devices. Gartner also mentioned that in the United States and Europe alone, each vehicle system produced more than 50GB of data per hour. In this section, these systems will be explained to help the investigator understand how important they can be to a forensic investigation.
What can an examiner expect from device systems within a vehicle that is involved in an investigation? From location data within built-in navigational systems, to the connected mobile devices, to what is or has been occurring in and around the car during driving time and stopping time—data can be available. To be more precise, vehicle forensics is an emerging technology in the digital forensic world that deals with vehicle telematics, GPS data, and the onboard infotainment system. Obtaining diagnostic information such as a check engine light, transmission, or other mechanical information is authorized by all vehicle manufacturers, and one can simply take the vehicle to an authorized shop to decipher the transmission. Extracting data from an infotainment system and/or telematics, however, is not an authorized service provided by the automotive industry, nor do car manufacturers outline the methods required to obtain this information. With many different vehicle models and vehicle manufacturers, this type of investigation can be extremely difficult. Much like the investigations in the early days in mobile forensics, it involves a lot of hit and miss.
The investigation of a vehicle’s system can serve many different facets of an event or series of events. A vehicle’s data can often fill in the blanks where a mobile device, CCTV, or other investigative tools lack a certain time frame. Obtaining information from a vehicle can help identify whether a vehicle was at a geographic location at a particular date and time, as well as the vehicle’s route of travel. Furthermore, using a linked mobile device to an infotainment system in a vehicle can show a link between the two, and even identify the number of occupants in the vehicle—not to mention contents of messages and other artifacts. Think about determining a time line of travel, the stops made, and which doors were opened and closed; all of this data, and more, can be recovered from the vehicles of today.
Obtaining Data from Vehicles
Like data from any other digital device, vehicle data must be obtained to process and decode into a format to assist in an investigation. The on-board diagnostic (OBD) port can be used by investigators to recover diagnostic and vehicle information, as can a USB, or investigators can remove the infotainment center if one exists.
Both the OBD port and USB methods are considered noninvasive, since both can be connected to plugs and cables supplied by commercially available tools. However, the removal of the infotainment console to obtain a physical collection often requires the removal of the entire, or a portion of, the dashboard.
OBD-II
In 1988, the SAE (Society of Automotive Engineers) outlined and set a standard plug and diagnostic test signals and further expanded the set in 1996 using OBD-II. The OBD port is used by vehicle maintenance providers, diagnostic tools, forensic investigators, and even insurance companies. The OBD-II can hold valuable information for crash investigations and has been used for many years.
![]()
The Verizon Hum has a great web site (www.hum.com/port) to help you find the location of the OBD-II port in a car.
The OBD port can communicate with the electronic control unit (ECU) or engine/electronic control module (ECM) to obtain information from sensors and other diagnostic controls that involve the vehicle’s engine, powertrain, fluid levels, and so on. An addition on most vehicles with airbag support is the recording of events by the ECU, which acts much like the black box of an airplane. Although the name event data recorder (EDR) is often used, technically the EDR is a function of the ECU. The data often comprises the short time before and after a crash, including impact area, airbag deployment, speed, and acceleration. Vehicle manufacturers are not forthcoming on exactly what is stored on the ECU as it relates to crash diagnostics or other vehicle data, but since 2010 all vehicle manufacturers are required to give access to this data via the OBD-II port.
![]()
CDR Vehicle Software used by crash reconstructionists provides a list of the currently supported vehicles that can be referred to in the event the OBD-II port becomes part of an investigation (www.boschdiagnostics.com/cdr/sites/cdr/files/CDR_v17.7_Vehicle_Coverage_List_R1_0_0.pdf).
There are many control modules, and each module may need to be interrogated to recover data. It may seem that there is only one ECU in the vehicle and that it holds all of the data needed for an investigation. But as Ben LeMere, CEO and cofounder of Berla Corporation, has explained during conversations, there are many modules throughout the engine compartment that hold valuable data, and gaining an understanding of what module holds the necessary data for the investigation at hand is paramount to the investigation.
USB Port
Access to data within the infotainment system of the vehicle can be obtained from the USB port, which is generally located in the center console or glove compartment. The USB port typically is coded as the media access to which the occupant can connect a mobile device to play music or perform other operations. This type of extraction is noninvasive and would be classified as a logical extraction. A standard connection to this port is not used (such as USB/USB), since the protocol will not be USB, but serial.
Tools such as Berla’s iVe have a USB-to-Ethernet adapter that connects to this port to conduct the extraction of data. This type of extraction can obtain information such as Bluetooth and Wi-Fi of the connected devices, contacts if synced to the system, calls and SMS messages if a device was connected, any connected storage devices and/or media, the vehicle odometer reading, saved locations on the in-car navigational system and track logs, and more. What can be extracted is highly dependent on the vehicle manufacture. Extraction of this data often takes no more than 20 minutes, but as with mobile devices, if there is a considerable amount of media, this could affect the time considerably.
Physical
For some vehicles, the only avenue of analysis outside of the OBD port will be the removal of the infotainment system. This is an invasive and involved physical acquisition. It is invasive because the module must be removed from the vehicle, often requiring that the dashboard be dismantled, and physical because the circuit board is removed from the infotainment module and read by software. Once the board is removed, it is connected to specialized hardware and software and current is provided, generally using an external power supply for the extraction to commence. Recovered data is often quite verbose, as should be expected with this type of extraction.
Data recovered can contain all the information of a logical extraction, but also information from vehicle events. The events can include door openings and closings, gear shifting, parking light status, and time and system updates. Having this type of information, along with the standard infotainment extractions (such as SMS, Calls, Contacts, Bluetooth, Wi-Fi, and so on), can paint a much better collective picture of the event.
![]()
Currently the most utilized software in vehicle forensics is Berla iVe software. The hardware and software can conduct the extractions and process both logical methods (OBD and USB) and physical methods.
Wearables
The term “wearable” is used thought the IoT industry to describe a computational connectable device that may be implanted in or worn on the body. Wearable technology is not new. In fact, the first wearable computer was used not to improve fitness or health, but to predict gaming outcomes in roulette. Granted, the device was not technically a member of the IoT world, simply because the Internet had not been invented in 1955.
In that year, Edward O. Thorp theorized that a wearable device could predict and inform a subject of the outcome while playing roulette. Roulette is a gambling game in which a small ball is launched around a circular wheel in one direction while the wheel is spun in the opposite direction. When the ball begins to slow down, it drops through various “pockets,” or deflectors, before landing and stopping at a number. Thorp built a pocket-sized computer that could fit within a person’s shoe. The wearable computer was activated by a wearer by the use of the big toe. Codes (musical notes) were sent via radio signal to the person making the bets at the other end of the roulette wheel. Differences in the sound would be used by the player to decide on the bet. Thorp and Claude Shannon put the computer into use in 1961 in Las Vegas. In 1998, Thorp penned a document describing this first wearable: “The Invention of the First Wearable Computer.”
Additional wearables continued to be manufactured, such as the large calculator watch popular in the 1980s, digital hearing aids, Bluetooth headsets for phone calls, and several other wearable computers. The Nike+iPod Sport Kit was one of the first athletic tracking devices developed by Nike in 2006. This device has a small transmitter placed in or on the wearer’s shoe, and a variety of information is transmitted to an available device (such as an iPod touch, iPhone, or iPod nano). In 2008, the first-generation Fitbit devices came to the market as the Fitbit Tracker, which measured distance, calories, duration, and floors climbed. Also, as an addition to the activity tracker, a sleep function that measured sleep cycles was included. The data on the device could be uploaded to the user’s account on the Fitbit servers.
The first smart watch, Pebble, hit the scene in 2012. What is interesting in the history of the Pebble is the fact that it was brought to the world in a Kickstarter campaign and would be able to interact with both Android and iOS devices, a first of its kind to bring the smart phone to a smart watch. The product was short-lived, but the company and intellectual property were purchased by Fitbit in December 2016 for $40 million.
In 2012, Google released Google Glass, a form of glasses that included a camera and Internet access. The operator could interact with the glasses with voice commands to capture video, images, and information from the Web and specific apps. It soon became apparent, however, that society was not ready for the glasses because of privacy concerns. Stories of businesses banning the devices and obvious limitations shut the door on the device in 2015. However, in 2017 a better target was selected: the enterprise. Now factory workers can receive instructions and more from the safety glasses they wear and send instantaneous feeds via video of their work. Google Glass was reborn, but for the enterprise—and into IoT.
During the same time Google Glass was being marketed, the first Samsung smart watch was released. In the race for the smart watch, the first Samsung Galaxy Gear was released in 2013, with 4GB of storage and 512MB of RAM. The device, as with the rest of the Gear series, enables the user to receive notifications from apps, calls, messages, and alerts, as well as health apps. In 2015, Apple released a watch that helped make wearable tech convenient and was developed with the intention of encouraging people to stare at their phones less but still maintain connection for notifications. A wearable iPhone generation was born. The Apple Watch enables users to interact with their iPhone and receive messages, calls, app alerts, and more, like the Samsung Gear series. Both Apple and Samsung devices interact via Bluetooth to the device, but they also can interact via Wi-Fi if the device is not within range. For both Samsung and Apple, new devices now also come with an embedded Universal Integrated Circuit Card (UICC) that allows for interaction with the LTE system without a device.
Gartner reported in 2017 that consumer wearables would grow at almost 17 percent worldwide annually. In 2017 alone, 310 million wearable devices were in use, with the Apple Watch leading the way. This, to the investigator in digital forensics, should sound some alarms. Once smart phones were the unknown, but now the industry has to deal with smart wearables.
Adding another source of data to an investigation is often just another problem to tackle, but with the number of users relying on data from their smart wearables, the investigator should take this evidence seriously. Most commercial tools still only extract data from Cloud sources for parsing, with some parsing the applications that support these wearables.
With the massive number of wearables that are available to the world, the impact to investigators will only increase. Understanding the various types of wearables that are available, and their general capabilities, can help shape the type of investigation that will be conducted.
Classification of Wearable Devices
Wearable smart devices can be classified into distinct areas that are generally based on the activity or job the wearable performs for the individual user. From heath care, to fitness trackers, to wearable cameras, glasses, and watches—there are many different types of devices and even more manufacturers.
Health Care Devices
The health care industry is utilizing wearables to help assist in remote monitoring of patients via surgically implanted wearables or unobtrusive wearables. These medical devices relay data wirelessly to a base that then transmits the data via the Internet to a collection point—typically the doctor’s office or clinic. Not only are the devices used by doctors, but individuals also use them for self-monitoring. For example, under-the-skin implanted devices can be worn to monitor cardiac arrhythmias. The wearable wirelessly sends data through a hub to the cardiologist daily for several years. The use of wearable IoT devices in this industry has been quite dramatic, and today’s investigators should be prepared to deal with them.
Fitness Tracking Devices
This wearable technology is based on the fitness industry. Forbes reported in 2017 that 59 percent of all wearable sales involved a fitness tracker within a smart watch. Nike+, Fitbit, Samsung, Garmin, and Apple wearables each have fitness tracking capabilities. With Fitbit leading the way in fitness tracking, Apple and Samsung pivoted from providing only app notifications to adding heath and fitness information. Investigators should be very cognizant of these devices during an investigation.
Cameras
You might not think of cameras as a wearable IoT device, but think about the proliferation of the GoPro revolution. From sporting events, to hunting trips, to law enforcement, and even weddings—people are wearing these portable cameras on their bodies. Many of these devices have internal storage, but many can and do transmit data via Bluetooth or Wi-Fi to a terminal or smart phone and then directly to the Internet. Google Glass is not only a camera but also has a built-in monitor to view messages, Internet feeds, and more. Video data that is stored and transmitted by these devices should not be overlooked by the investigator.
Other Smart Wearables
From smart rings to clothing, the world is becoming a digital investigator’s dream (or nightmare). Wearable jewelry—rings, bracelets, and even cufflinks—can be purchased and worn to track activity and alert the wearer of calls and text messages. Because most of these devices offer minimal storage, evidence would be located on the smart device in the form of a Bluetooth link to a connected device and possibly an associated app.
Smart clothing includes shirts, pants, headbands, and more. Because most wearables focus on health and fitness, the smart clothing industry is 100 percent focused on this group. Companies such as Polar have always offered heart rate bands, but they now offer simple compression shirts that not only monitor heart rate but also track motion, duration, and GPS. This data is sent through a hub (typically an app on a watch or phone) in real time to whomever the wearer would like to view the data. One of the most innovative pieces of clothing is the Levi Commuter Trucker Jacket by Google’s Project Jacquard. This jacket enables the wearer to answer phone calls, get directions, listen to music, and more, simply by swiping or double-tapping the cuff. Most investigators will have the evidence on the mobile device or hub, but seeing a data-storing denim jacket on the forensic lab table is not just for the future anymore—it is now.
Smart Watches
As mentioned, most smart watches focus on the wearer’s fitness activity, primarily because the industry is providing products to supply that specific demand. However, the smart watch has many other functions—paying for merchandise; notifying the user of calls; enabling the user to make calls, send texts, receive texts, view application responses, and so much more. Typically, the smart watch interacts with a paired smart phone, but newer devices from Samsung and Apple have LTE capabilities and do not need the associated smart phone to operate independently since they have embedded UICCs. These devices will be the most prevalent for the investigator in all the different types of wearable investigations. Three major types of smart watches are on today’s market: Apple Watch, Fitbit, and Samsung Gear.
Apple Watch The Apple Watch was the first new product from Apple since the iPad in 2010. The device was also the first new interface from Apple since the 2007 iPhone. The Apple Watch has since seen three generations after the first classic Apple Watch (series 0). The first-generation watch, as well as the second and third, all run a variant of iOS called watchOS, with the API kit called WatchKit. The current version of watchOS 5 on the new fourth-generation Apple Watch is 4.3.1, based on iOS 12. The hardware contained within the device is an S1, S2, or S3 processor (the number corresponds to the series), with 8GB of flash storage, near field communication (NFC), Wi-Fi, an accelerometer, a gyroscope, a heart rate monitor, a microphone, and a speaker. Newer devices from series 2 also include a built-in GPS and ambient light sensors. Series 3 devices added a barometric altimeter and Siri voice feedback.
The Apple Watch enables a user to receive notification of fitness activities (such as distance, steps, calories, and heart rate), outside temperatures, calendar, mail, maps, calls, messages, app notifications, and more. The Apple Watch uses the same methods the iPhone does to back data up (iTunes or iCloud). The interesting thing is that the device automatically backs up the data to the paired iPhone, so this information is found within the device iTunes or iCloud backup. Many commercial tools miss this data in the parsing of the iTunes or iCloud backup and simply report the health data.
Several interesting artifacts are contained in the Apple Watch backup. (Specific details and paths will be covered in Chapter 16.) The following list, from Apple Support (https://support.apple.com/en-us/HT204518), shows the items that are available in the backup:
• App-specific data (for built-in apps) and settings (for built-in and third-party apps) For example, maps, distance, units, and settings for mail, calendar, stocks, and weather
• App layout on the home screen
• Clock face settings Includes current watch face, customizations, and order
• Dock settings Includes the order, whether user sorts by favorites or recent settings, and available apps
• General system settings Includes watch face, brightness, sound, and haptic settings
• Health and fitness data Includes history, achievements, workout, and activity calibration data from the Apple Watch and user-entered data
• Notification settings
• Playlists, albums, and mixes These are synced to the Apple Watch and music settings
• Siri Voice Feedback Controls when Siri speaks
• Synced photo albums
• Time zone
Information that is not backed up includes Bluetooth pairing, credit cards used by Apple Pay on the watch, and the passcode for the watch. However, the data that is synced between the paired device and Apple Watch is retrievable from the watch backup that is contained in the paired device’s backup. Information includes a synched address book, call logs, messages, Wi-Fi, MAC address, e-mail, voicemail, and any other shared third-party apps.
![]()
When an Apple Watch is unpaired from the device, a backup of the device is automatically created and the data on the watch is erased. If the device is out of range of the paired iPhone when unpaired, the data will not be the most current in the backup.
A tool called iBus (S1, S2/S3) connector can attach to all Apple Watches and was manufactured to enable the device to be restored using the diagnostic port under the band of the watch. This connector, coupled with MFC software and a dongle, can read the details of the device, including iCloud account details. As with all tools in the wild, it is incumbent on the investigator to test and validate all tools prior to using them on evidence.
Fitbit Fitbit’s entry into the smart watch world was in 2015 with the Surge. This device enables the standard watch capabilities but includes fitness functions such as steps, floors, heart rate, sleep monitor, and a built-in GPS. Fitbit’s versions of smart watches progressed through the Blaze, Ionic, and now Versa, which added the ability to receive basic notifications from the paired smart phone to include calls, messages, and calendar; Fitbit has since added notifications from all supported apps in both the Ionic and Versa.
The Fitbit brand of smart watches has slimmer specifications than the Apple Watch with a max of 4GB of storage on the Versa, but still supports Wi-Fi, Bluetooth, NFC (on some models), accelerometer, gyroscope, altimeter, and a spO2 (saturation of oxygen in the blood) sensor. The Fitbit brand runs a proprietary operating system called Fitbit OS. As discussed earlier, Fitbit purchased Pebble in 2016, and the Fitbit OS is based upon the purchased IP.
How about the investigation of a Fitbit device? The device has already been used as a witness in several cases. One prolific homicide case in 2015 involved a tale of a husband and an alleged struggle and home burglary in Connecticut. The husband had alleged that the wife had struggled with intruders at the home around Christmas, while he was tied up. However, the Fitbit that recorded the health and the steps taken by the wearer painted a different picture of the events proffered by the husband. By recording almost 1300 steps taken by the victim at the time of the crime, as well as health and activity readings contradicting the events as explained by the husband, Fitbit became a new silent witness.
Fitbit users create an account, so the data is accessible online (Fitbit dashboard) and within the supported device’s Fitbit app. The actual data on the Fitbit physical device is extremely limited because of the amount of code space for the underlying OS, apps, and music. However, data is stored in the Fitbit Cloud as well as the installed Fitbit app.
Data listed by Fitbit (https://help.fitbit.com/articles/en_US/Help_article/1133) that can be recovered from the Fitbit cloud includes the following:
• Body Weight, BMI, body fat percentage
• Foods Any logged food and water
• Activities Device data such as steps, floors, calories burned, and more
• Sleep Time asleep and time in various forms of sleep
Data found within the application on the device is paired with the device and syncs every time the app is opened. The data found within the app includes information listed previously, as well as any notifications that might have been received on the device. (Artifacts and additional analysis of this data will be covered in Chapter 16.)
Samsung Gear The Samsung Gear series of smart watches was first released in 2013. The devices have progressed from the Gear, to the Gear 3, which is available as of this writing. All devices in the family have 4GB of storage like the Fitbit, but the operating system used by the Samsung devices are largely based on their built-in operating system, Tizen. Tizen is an open source software like Android, and the interface of devices running Tizen is like that of the Android. Samsung’s operating system is based on Linux, like Android, and the device has a USB debugging mode much like Android devices. Some of the Samsung Gear smart watches, such as the Samsung Gear Live, run on the Android Wear operating system. The devices have Wi-Fi, Bluetooth, NFC, accelerometer, gyroscope, barometer, heart rate, GPS, and ambient light detector.
The Samsung support includes much of the same features as both the Apple Watch and Fitbit to include health features from the S Health app, and also interfaces with the paired device to show notifications from calls, messages, and any supported apps. The device is also able to utilize Samsung Pay to store and manage credit cards using NFC.
The Samsung Gear devices utilize the Samsung Gear app for both iOS and Android, use Samsung Cloud for backups as well as on the mobile device with which it is paired, and store data within the actual watch. Accessing this data is often the biggest challenge for the investigator. The connection to the device running Tizen is often hampered by either no USB connection on the actual watch or simply lack of support by any commercial tool. Most commercial tools simply parse the app from the mobile device or extract the data from the Cloud service. Note that there is a Backup & Restore setting within the mobile device Samsung Gear app. The watch device can be backed up to a paired mobile phone, and the backup can be found in the mobile device file system at data/data/com.samsung.android.hostmanager/files/backup/.
With Tizen on the device, the first step in attempting to access the device directly is to place it into USB debugging. The watch can be placed into USB debugging by choosing Settings | About | Software Version and tapping 7 to 10 times. If the device has a cradle that can be used to plug into a PC, the computer should recognize the device if the current Samsung drivers are installed. However, if the device does not have connection to the device, such as the Samsung Gear 3, an ad hoc Wi-Fi network is created by turning on the Wi-Fi, connecting to the network access point, and on the computer finding the IP address of the device and using this IP address when conducting the communication via the PC and Smart Development Bridge (SDB) as outlined by Samsung in their development manual (https://developer.samsung.com/gear/develop/testing-your-app-on-gear). SDB is similar, if not identical, to Android Debug Bridge (ADB), where an investigator can pull data from the file system. Another similarity to the Android OS is the ability to obtain and the manner of obtaining root on the Tizen device by using Samsung Odin. (A deeper examination of SDB and the Samsung Gear file system will be covered in Chapter 16.)
Unmanned Aircraft Systems
This section will cover the proliferation of recreational drones and their impact on today’s digital incident response. In the document “Drone Year in Review: 2017,” the Center for the Study of the Drone at Bard College estimated that there were almost 900,000 hobby users of unmanned aircraft systems (UASs) in the United States alone. This number continues to grow each day, as new UAS users hit the streets armed with drones that can fly at great distances, record crystal-clear video, and even carry a payload. UASs are currently regulated by the FAA, which has provided guidelines to local law enforcement on how to handle drone incidents (www.faa.gov/uas/resources/law_enforcement/media/FAA_UAS-PO_LEA_Guidance.pdf). Another document produced by Bard College, “Drone Incidents: A Survey of Legal Cases,” specifically speaks to the legal issues of UASs, to include privacy, crashes, airspace, restricted areas, and smuggling. The following sections will summarize the data and speak to the massive forthcoming law enforcement issues.
![]()
All UAS pilots who fly in the United States must register their crafts with the FAA and affix registration numbers to the device. Furthermore, devices have a built-in geofencing mechanism that is set up to disallow the UAS to enter into any airspace listed as restricted. The firmware of the device, replicated on the controller, is updated continually to provide the most current no-fly areas. The FAA maintains a web site (www.faa.gov/uas/where_to_fly/) for information on restrictions, no-drone zones, and a mobile app. The pilot must affix the registration number on the device, and they can also disable the geofencing capability of the drone.
Privacy
With the ability of the drone to be controlled by radio link, the device’s distance from the person controlling it can be great. With every drone now equipped with a video camera that can live-feed the information back to the flyer, many people—rightfully so—have privacy concerns. No federal laws cover the use of a drone and privacy—only guidelines outlined by the FAA discuss the issue. The laws covering public concerns come down to state and local governments.
It is easy to imagine how a drone could easily invade the privacy of a person or place. Many state and local cases involve users flying a drone around businesses, in windows, and around homes. One documented case in Utah in 2017 involved the seizure of a DJI Phantom device, where a couple was charged with voyeurism using concealed or disguised electronic equipment. A person saw the drone hovering outside his bathroom and followed it until it landed in a parking lot. The subject removed the drone’s SD card and read it via his computer, saw images of multiple people in bathrooms and bedrooms, and took the card to the police. The police located evidence on the card to identify a possible suspect from the video footage and later arrested the couple (http://archive.sltrib.com/article.php?id=4946115&itype=CMSID).
Crashes
Drones can travel at speeds up to 75 mph and at altitudes greater than 1000 feet, and they have spinning blades that can be made of hard plastic and even metal. Often, the pilot crashes the device into a building, tree, or other structure and the device plummets to the ground and onto an unsuspecting person below. In a case cited within the document by Bard College, a subject lost control of a drone and it crashed into a group of people at a parade. A motion to dismiss the case upon grounds that law enforcement could not prove the accused was operating the drone was made and is still under appeal as of this writing. This tactic is important to remember, but there are many artifacts stored on the drone, in the Cloud, and on the SD card that can help establish the owner and flyer.
Airspace
A UAS can fly at incredible heights, and the FAA has placed restrictions not only on altitude but also on proximity to airports. Aircraft pilots having to deal with birds is one thing, but they shouldn’t have to deal with drones as well. The majority of cases cited involving airspace issues have to do with drones flying in and around a scene in which first responders are involved. News crews use drones to film the action from a better vantage point, and citizens use them to try to get a better view. Again, being able to identify the device owner from the information located in the various storage locations is critically important.
Restricted Areas
Depending on the location and laws, a UAS will not be allowed to fly in some areas. Airports, as discussed, are obviously no-UAS zones, but there are many other no-fly locations as well. From national parks, to museums, sporting venues, concert venues, government buildings, government facilities/bases, and prisons—each authority has different restrictions. The investigator must be familiar with the various regulations in the area to asses the crime properly.
Smuggling
Within the United States and United Kingdom, the use of drones to smuggle contraband into prisons or over borders has become a problem for law enforcement. What is quite interesting is that the FAA has not enacted specific requirements for flights over prisons, and it comes down to the state to create such laws. Many drones can carry a payload, and there are documented cases in which cell phones, tobacco, alcohol, and drugs have been smuggled into prisons. In a 2016 case in Georgia, subjects actually made several drops with drones of cell phones in a drug-smuggling conspiracy ring (www.justice.gov/usao-sdga/pr/16-defendants-indicted-federal-drug-trafficking-charges).
Obtaining Evidence from Drones
As outlined in the various cases, subjects can affect every facet of law enforcement by nefariously utilizing drones. With the availability of these devices at low prices, almost anyone can become a drone user, and investigations of these types of devices is still in its infancy. However, many commercial tools now support the processing of data from these devices. The drone evidence can be found on the device, the SD card, the mobile device, the controller, and the Cloud service, depending upon the manufacturer and product. The most prevalent family of drones produced for the public are from DJI and include the Phantom, Phantom 2, Phantom 3, Phantom 4, Inspire, Mavic series, and Spark.
In most cases that are processed in drone investigations, the data simply comes from the SD card. In most drones, an SD card is plugged into the device, and the card records the video/images and often log files. In the case of DJI recreational drones, the log files are known as .dat files and contain valuable information that includes altitude, direction of travel, speed, latitude/longitude, and additional device information.
The drone’s internal flash memory is accessible via only a few commercial products. Oxygen Forensics Detective software enables the physical acquisition of the flash memory on the DJI family of drones. There is a caveat, however: For physical acquisition, the device must be turned on. Research has found that having to turn the device back on will reset the last logs from the device. The information on the device will contain only the latest flight logs because of the acquisition of a new home location. If the device can remain turned on and charged and isolated from any type of network, the acquisition will contain data not available if the device has acquired a signal or been turned on from the initial contact. Another free method that is also unobtrusive allows for the acquisition of the internal flash media.
![]()
Removing the chip and/or using Joint European Test Action Group (JTAG) methods will not have the limitation imposed by a restart, and these are considered better methods for obtaining the information from the drone’s internal flash memory.
The following guide will help the investigator gather information on all DJI devices, with only minor changes:
1. Use an iOS device or Android with installed DJI Go app (Phantom 3/Inspire only).
2. Turn on the remote controller (RC) that belongs to the DJI drone (Phantom 3/Inspire only).
3. Have the latest DJI Assistant software installed on the Mac or PC.
4. Connect the iOS device or Android device to the Wi-Fi broadcast by the RC. The SSID is usually located on the RC. The default password is 12341234 (Phantom 3/Inspire only).
5. Obtain a DJI Free account, and log in. Select the device name from the upper-left corner.
6. Launch DJI Assistant and log in with the user created in step 5.
7. Select Advanced mode and select Enter Flight Mode Data. (Phantom 3/Inspire only).
8. Connect the drone.
9. In DJI Assistant, select the device and enable SD card.
10. Use tools such as FTK Imager, Oxygen Forensic Detective, and Cellebrite to create a physical image of the device.
(The data acquired using these methods and artifacts will be discussed in Chapter 16.)
With both Android and iOS devices, the DJI Go app holds a tremendous amount of user information, including the device user registration e-mail address, user account information, device logs, media uploaded by the user, and more. Most commercial tools will parse and decode the information from the DJI Go app. (This application and the contents will be described in Chapter 16.)
DJI devices also transmit data from the DJI Go app to the DJI Cloud server. The DJI Cloud account holds a tremendous amount of saved user data, shared data, and flight information. Having access to the DJI Cloud can help the investigator if the drone or event associated controller device (RC controller, mobile device) has not been located or has been damaged.
Many of the recreational drones that may come into the forensic lab follow the guidelines outlined in this chapter: storage on the device, the Cloud, within the app, and on the external media. Data locations and additional information will be covered in Chapter 16.
Chapter Summary
Today’s digital forensic investigators have their hands full with IoT devices, including devices that control lights, refrigerators, home security, and temperature; wearables; and connected vehicles. The amount of data that is gathered into Cloud-based services is unfathomable. Information that can be obtained from these sources will undoubtedly assist in any investigation.
The Internet of Things does not necessarily deal only with items in the home, enterprise, or industry sectors. The number of connected devices in the world has far exceeded imagination. We are a connected society, and our need to consume and transmit digital data is insatiable. Not only do we need to be connected using our smart devices, but we need to be connected using our watches, glasses, and even our clothing. Enter the ability to soar to great heights to video, photograph, and simply pilot a UAS, and some people have unfettered access to tools that can take a simple investigation into a digital device to a new level. The digital investigator who was an expert only a few years ago has so much to learn today.
This chapter briefly outlined the tech that is available to the user and general ways to access the data. As mentioned, Chapter 16 will cover specific locations and artifacts that can be examined to help solidify the digital forensic investigation of these devices.
