1 Introduction to the World of Mobile Device Forensics
In 2014, Cisco’s Visual Networking Index (VNI) Global Mobile Data Traffic Forecast Update indicated that the number of mobile devices in use exceeded the world’s population. In February 2017, the same study by Cisco revealed that “mobile devices and connections in 2016 grew to 8 billion.” In the mobile world, wearables are the latest and most easily noticeable digital devices. Cisco reported that there were 325 million wearable devices in use globally, with a subset (11 million) having a cellular connection as well. It should come as no surprise that mobile device sales have outpaced PC sales three-to-one since 2003, as reported in a study conducted by the National Institute of Standards and Technology (NIST). And between 2010 and 2016, the ratio increased to almost five-to-one, as reported by MarketWatch in 2016.
Statistically, the examination of mobile device data should be proportionally similar to computer examinations, but unfortunately, this is not the case. In actuality, computer evidence is still more prevalently used in civil and criminal cases, but use of mobile device evidence is on the rise, though not at the rate of induction of the actual devices. In fact, in each and every venue in which law enforcement has been surveyed, participants have unequivocally stated that they receive more requests for the analysis of mobile device data than for any other type of electronic evidence.
A common theme with mobile forensic experts in both law enforcement and enterprises is the overwhelming inundation of electronic evidence from mobile devices, which is increasing at an alarming rate—so much so that the groups I’ve surveyed from both law enforcement and corporate organizations indicate that they’ve hired or assigned specialists who examine and collect only data from mobile devices. What is truly alarming is the fact that most of these examiners also indicated that little consideration is given to the actual content of the mobile device when a computer is also part of the electronic evidence scene. When an American adult spends an average of 34 hours on the Internet using a mobile device, versus only 27 hours using a PC (as reported in 2016 by Nielson, a global research company), shouldn’t a forensics examination reflect that? This mentality is based primarily upon the limited amount of information available on correctly processing, analyzing, and reporting on the data from a mobile device, whereas computer forensics has been time-tested and is accepted by examiners and courts across the globe.
The proliferation of mobile devices will only increase with the world’s population growth and as the population’s dependency on technology accelerates (see Figure 1-1). Now should be the time to accept and understand that the information contained on a mobile device details, documents, and exposes the thoughts, actions, and deeds of a user substantially more than any data stored on a personal computer.

FIGURE 1-1 There are currently more mobile devices on Earth than people.
With this unprecedented amount of electronic evidence comes the need for highly skilled mobile device forensics investigators. This book is a comprehensive, how-to guide that leads investigators through the process of collecting mobile devices, analyzing the data found, and disseminating their findings. This holistic approach to mobile device forensics will not only feature the technical approach to data collection and analysis, but it will also explore the legal aspects of mobile device forensics. It is widely known that today’s digital forensics examinations have been “dumbed” down, with a heavy reliance placed on using tools to extract and collect data. These methods have bred a systemic influx of “data collectors,” rather than mobile device forensic examiners. This book attempts to counter this trend as it approaches and readies not only the newest examiners, but seasoned digital experts as well, with skills and knowledge that surpass the simple “easy button” approach.
The successful examination of digital evidence from a mobile device requires an intimate understanding of the data, and not the medium that produced it. This fact is especially important when it comes to the examination of the artifacts left behind by a mobile device. Often the unique aspects of mobile devices are overlooked by examiners and students when encountering these small-scale digital devices, because their first impressions are often clouded by the actual size of the device. It is a common belief that the small size of the device implies that it contains only primitive and rudimentary data, and this equates to the belief that the examination of the device should be consistent with its physical size. The size of today’s device has no bearing on the storage, however, with most of today’s smart devices having a storage capacity far greater than that of PCs less than ten years ago. In practice, many believe data forensics should be as easy as inserting a flash drive and hitting the “find evidence” button. However, because of this tactic, most examiners, and quite honestly the majority of examinations, fail at the critical part of the evidence life cycle—the dissemination of the facts. In short, the size of today’s modern smart device is in no way an indication of its storage capacity. Moreover, it is important to remember that although the physical device that holds the data may be different, the data and artifacts produced by the underlying operating system are what the examiner must focus on.
An examiner who must testify to his or her findings will quickly realize that it is not acceptable to testify to the fact that he or she pushed the “get evidence” button and then believe that the resulting reasoning/explanation will suffice in court. An examiner must be ready to answer the question, “Where did the phone book come from?” and not answer, “From the phone.” The true expert digital forensics witness will be ready to give the location of the phone book’s contents as they relate to the phone’s file system and to specify how the user data was not altered during the examination. Unfortunately, for most, this is a daunting task because it takes additional training, for which many admit they have neither the time nor the resources. By reading this book, understanding the principles discussed, and, most importantly, working through the various scenarios, your experience as an examiner will have already surpassed the majority of the people conducting mobile device examinations today.
The primary goal of this book is to suggest methods and procedures for the collection and analysis of digital data from a mobile device so that your examination will stand up to the scrutiny of court. This book also aims to dispel the mobile device size myth and to prove that today’s mobile devices contain more relevant and transactional data than a personal computer 100 times its size. Armed with a full understanding of the wealth of information available for discovery contained in this book, you will be prepared with not only the knowledge of how to use mobile device forensics tools to conduct investigations but also with a holistic understanding of how and what these tools are doing.
A Brief History of the Mobile Device
Welcome to the world of mobile device forensics. The examination of data is no different from the examination of the words in any book or manuscript. To understand the words in a book, the reader must have an understanding of the letters that form the words and the words themselves to form a thought or sentence. Without this initial understanding, reading would not be possible. The same goes with understanding a mobile device. To be a truly good forensic practitioner, the examiner must understand the specimen. Before we begin a discussion of mobile forensics, let’s begin with a history of the evolution of mobile devices themselves.
Mobile phones for cars and other vehicles preceded the handheld mobile phone and by all accounts were initiated by Bell Labs in 1946 in St. Louis, Missouri. This book will focus on the handheld mobile device that followed a little more than 26 years later.
Martin Cooper
In 1973, Martin Cooper from Motorola began developing a device that would enable a person to walk the streets while making calls without the need for attached wires—a portable handheld mobile phone. On April 3, 1973, Cooper demonstrated the portable phone with a call to Joel Engle of Bell Labs, Motorola’s main competitor, to let Engle know he was calling on a portable handheld phone from the streets of New York City. The call was routed via a base station Motorola installed atop the Burlingame House into the AT&T landline telephone system. Cooper had been working on the development of a radio phone for many years. Ten years after he used this device to call his rival, it was brought to the mainstream market. This radio phone employed the same technology used by the military to communicate on the battlefield.
Cooper developed the DynaTAC (DYNamic Adaptive Total Area Coverage) 8000x portable phone, which enabled users to call another portable phone, landline, or radio phone. This device was approved by the U.S. Federal Communications Commission (FCC) on September 21, 1983, and was offered commercially in 1984. It weighed 2.5 pounds, with the battery contributing the majority of the size and weight. The talk time was approximately 20 minutes, and it took approximately 10 hours to charge the device between uses. This first device was, by today’s standards, impractical due to its size and weight. Picture the 1980s TV show Miami Vice and the main character played by Don Johnson, with white cotton pants and matching jacket, with a large, angular phone and protruding black antenna—that was the DynaTAC 8000x.
The price tag of the device made it extremely impractical for widespread use against the prevalent pager or beeper of the age. When mobile radio devices came to market, prices ranged from U.S. $2000 to $4000, and they seldom worked outside of only a few major markets. The DynaTAC 8000x was priced at $3995.
Despite the introduction of the DynaTAC, car phones continued to be more popular, mainly because of the large mobile phone price tag. By 1984, the car phone was a large device with a very heavy base and typically a curly cord that ran to the handset. These devices had much better transmission and reception rates because of the constant battery power that exceeded the current ranges of the DynaTAC. Car phones were typically mounted and hardwired in vehicles and looked like a normal kitchen phone of the day. Users wanted phones that were more portable, however, so manufacturers began making the devices capable of being removed from the vehicle. The bag phone was born. (“Bag phone” was not the official name, but it stuck simply because the device could be carried in a zippered bag.) Impractical and extremely heavy, this device was not around for long. Who is to say what the impact of the electrical radiation might be?
Size Evolution
Shortly after the DynaTAC, cellular devices began to be manufactured in smaller form factors. In 1989, the Motorola MicroTAC was released. This device was much smaller than the DynaTAC series but still large and expensive enough that mainstream consumers were not buying. It was not until 1996 when the StarTAC series entered the market that things changed. The first cell phone to make a sizable impact with consumers was the full clamshell feature phone, which could be carried around in a pocket or small purse. The price point for the Motorola StarTAC was $1000. Because these portable devices only made and received calls, the price tag versus necessity was still out of reach for most consumers, however, so the progression away from the landline to the cell phone was not immediate.
The price for the mobile device started to drop when the technology, components, competition, and assembly became cheaper. In the mid- to late 1990s, there was a shift to make the smallest device possible, but in the early 2000s, the size paradigm started to shift the other way. Today, consumers are speaking into mobile devices the size of small laptops, conveniently termed “phablet,” for phone tablet. What has become important is the type and amount of data that can be transmitted, as well as what components are inside.
Data Evolution
Cell phone users quickly saw the need to send messages that they could type into a QWERTY keyboard or pound down the keys in a series of taps instead of speaking to someone. From this need, Short Message Service (SMS) was born. Limited to 140 characters, SMS enabled users to express themselves via a short sentence to other mobile device users. Today, 140 characters is still the limit. Concatenated SMS, or what some call Protocol Data Unit (PDU) mode SMS, is more widely used and provides 160 characters by changing from using 8 bits per character to 7. This was a significant advancement that moved the pager away from the businessman’s belt loop and to the eventual demise of this type of communication service. The cell phone soon advanced away from the simple walkie-talkie. Mobile device users next needed storage for these text-based messages, and soon for pictures, videos, calendars, and e-mails as well—who would have foreseen the application revolution?
![]()
The walkie-talkie, invented by Donald L. Hings, was first used as a portable field radio for pilots flying around Canada. In 1937, when the first walkie-talkie was built, Hings referred to the device as a “two-way radio,” and it has been used ever since.
Storage Evolution
Most of the original mobile phones did not contain a media type that would support the storage of data, because most were engineered to use the space as a scratch pad to run the needed process, remove the process, and move to the next process. Storage of nonvolatile data, or data that would continue to exist without constant power, onto a device’s memory chip was not possible initially. This meant that any data that was visible on the device would not be stored, and as soon as the device was shut down, all the data disappeared. Because initially the mobile phone was used only to make and receive calls, this was not observed as a limitation.
Because of this, no phone book storage or any other settings could be maintained. The first cell phones were merely a block of circuitry that had the same combinations of buttons included on the well-known landline. The functionality was the same—attempt to recall the number of a contact from memory and key in the number (think about that—having to remember all of those phone numbers).When TDMA (Time Division Multiple Access) devices in the United States began to transition to GSM (Global System for Mobile Communications), which had already arrived in Europe, device information such as a phone book and SMS could be stored onto the SIM (subscriber identity module). Storage areas for contacts, SMS, and last numbers dialed had already been built into the SIM standards developed by the ETSI (European Telecommunications Standards Institute), where this data could be written to and stored to the smart chip.
Since SIM cards were already storing phone data that was used in the authentication process, why not add values that stored the contacts, SMS, and last numbers dialed? The SIM card was already being used in the device as a “key” to the cellular network, assisting in the authentication of the device using stored values. TDMA devices could store a set number of contacts that users could look up and select to be dialed, plus a limited number of SMS (15–25 typically; that’s it!) that could be reread, even if the device was shut off. Other carriers that did not have SIM cards started to develop devices that used nonvolatile memory so data could be stored and saved even if the device was turned off completely or the battery was removed or drained. The older feature phones used an acronym—NVM, for nonvolatile memory—to designate this type of data within their file systems and prefix the file and/or folder name. This was where data was actually written to the phone and the start to the recovery of a goldmine of data.
Mobile Device Data: The Relevance Today
Mobile devices have come a long way since their inception. Data contained on a mobile device can now be compared to the written notes of a daily diary (often with pictures and videos), containing a company’s most secure documents, our financial status, and, most importantly, our everyday habits, patterns, and routines. If a picture of an individual were painted with the personal data recovered from a PC, the picture would be a blurry representation with no clear edges. If, however, the data recovered from a mobile device were examined, it would most likely paint a very personal, and potentially embarrassing, picture of the individual.
Mobile Devices in the Media
Every day, the world media reports cases solved using evidence from mobile devices or stories about how a mobile device was involved in a crime—either a text message or chat was sent or received; a social media post was sent or interpreted; or a voicemail was heard, recorded, or hacked. In January 2018, the Pew Research Center reported that 95 percent of U.S. adults owned a cellular phone, which translates to about 309 million cell phone users. It is no wonder that law enforcement digital examiners are looking to these devices as an evidence treasure trove. Mobile device data is today’s equivalent to yesterday’s DNA evidence.
One day, a mobile device that shows up in the lab or in the field may hold data that has never been seen by the world—the grassy knoll, the shot heard ’round the world, the missing plane’s last communication, and the smoking gun. Quite simply, you can fill in the blank to determine what a mobile device might be involved in when contemplating the events of today.
Digital data from a mobile device holds the key. To the forensic examiner, this data is critical in many investigations. The sidebar “Mobile Devices on the Scene” details the relevance of data on a mobile device and how its recovery is critical.
The Overuse of the Word “Forensic”
NIST describes “forensic science” as “the application of science to the law.” Forensics can include the scientific examination of fossils, a crime scene, metals, vehicles, postmortem bodies, and of course, digital data in many different forms. Digital examiners get lost in this meaning and sometimes interpret forensic science to indicate that a software application or a hardware device is forensically sound. But according to the NIST definition, the use of the tools by the examiner in a way conforming to known scientific processes and procedures is the forensic science, not the tool itself. A perfect example is the use of a write blocker when processing digital data.
Write Blockers and Mobile Devices
NIST and its Computer Forensics Tool Testing Program specifically state that the central requirement of a proper forensic procedure is that the examined original evidence must not be changed or modified in any way. One of NIST’s listed requirements for a layered defense is to use a hard disk write-blocker tool to intercept any inadvertent disk writes.
![]()
Many different kinds of write-blocking equipment have been created by many different companies. Any mention of a specific unit here is not an endorsement of the tool; it simply indicates that the tool was used in the case or test.
A write blocker is a software or hardware device that stops specific communication from a computer to a mass storage device. Write blockers come in many different types. Software-based write blockers can use a simple Windows Registry change; hardware units are sophisticated boxes that are coupled to the examination computer via cables, with the device to be examined attached to the other side. Some allow a connection directly to the pins located on the actual hard drive and then to the computer conducting the forensic analysis, while others have USB connections to plug a removable USB hard drive or flash drive into an available port.
Hardware tools can be used to protect disk access through the interrupt 13 BIOS interface of a PC. Because the mass storage device is attached to the hardware write blocker, all input and output (I/O) commands sent from the PC are monitored. Any commands that could modify the hard drive are not passed onto the hard drive, but intercepted by the write-blocking device. Software write-blocking tools also block the writing to attached drives plugged into the USB drive, mounted drives, and by device classes, if needed. This can be changed by editing the Registry of the Windows PC or using many of the available software tools.
Essentially, the write blocker acts as a traffic signal to data requests made by the computer. The computer makes requests to receive data from the connected device, which are accepted and processed; if a request to write data to the protected device on the other side of the write protector is made, these requests are stopped and not allowed to reach the device. The write-blocking hardware or software tool is not considered forensically sound, but the employment of the device and methods as part of the process is. To test this theory, obtain any write-protecting hardware device and attach a mobile device; then follow along in the upcoming sidebar, “Real-World Example: Testing the Theory,” in the next section.
Mobile Device Technology and Mobile Forensics
Mobile device forensics is likely the most rapidly advancing discipline that digital forensics has ever seen or ever will see, primarily because of the rapidly changing environment of the actual devices. Device operating systems have become more advanced, and the storage capacity on the current devices is astronomical. Today’s devices are mobile computing platforms, but accessing the data contained on these devices is much more difficult than accessing data from any other digital device. Communication to these devices with software is much different from communicating with other media containing digital data. Users must use tools specifically designed for mobile devices, and they use many different software tools on one device. This brings a new wrinkle in the examination process. A lot of seasoned digital forensic examiners are disappointed and turned off by the limitations imposed by software to these mobile devices, believing that mobile devices should behave like a computer’s hard drive. Also, many mobile device forensic software products have their roots in the sync software world and not in the forensics world. This does not help their credibility with examiners coming from the computer forensics lineage.
From Data Transfer to Data Forensics
Mobile sync software enables the user to add or delete items such as contacts and calendars from a mobile device. This is extremely satisfying to the standard mobile device owner, because it allows the easy addition of hundreds of contacts and contact details. No longer does the user have to key in every contact via the keypad; now, with the assistance of PC software and a cable, this information can be quickly added to the device.
Adding and deleting user data would never be something a forensic examiner would desire, a fact that was realized by companies developing sync/data transfer software. So these companies began to create models and versions that were intended for the forensic examiner. The software and hardware were no different from the sync software, with one exception: The write/transfer button or selection was not enabled. These devices and applications simply allowed the data to be read from the device, not written to it. Sometimes the forensics updates involved a removal of a button, and sometimes it was merely adding new instructions in the manual. The underlying code base in the equipment or software was the same; only the implementation was different—along with the manufacturer’s suggested retail price (MSRP).
Processes and Procedures
If automated tools will be used in any forensic examination of digital data, examiners must have a set of processes and procedures in place; using an automated tool without such direction could be a detriment to the entire process. An understanding of the processes and procedures of mobile device forensics is required in this age of mobile computing because of the many automated tools, variances among them, lack of complete coverage, and diverse training levels. Ultimately, understanding the processes and the steps needed, interpreting results, analyzing output, and documenting the data, all while maintaining case integrity, should be the goals.
People use mobile devices every day to buy groceries, send birthday wishes, break up with a lover, transfer millions of dollars, and unfortunately commit crimes. Gaining an intimate knowledge of how to collect valuable data from these devices, uncover valuable data, and present the data will put you ahead of the rest. Chapter 2 will discuss how to compile standard operating procedures for collecting the physical mobile devices and accessing data on those devices. Your understanding of the device and the progression into the actual digital investigation is critical for a successful outcome.
Examination Awareness and Progression
When mobile devices contained volatile data storage, the only examination of the mobile device consisted of removing the SIM card and reading the information stored on it. This made for a quick examination of the smart chip, and the device was seldom examined forensically. So essentially the first introduction anyone had to the examination of a mobile device started at the SIM card. The first software for mobile device collection also read the data from a SIM card. (In Chapter 8, you will be shown the various collection methods and software used for SIM cards.) As mobile devices advanced in terms of how data was stored, the methods used to collect the data from the internal memory, or nonvolatile area, did not progress in tandem.
The awareness of the data was there, but collecting it by means other than scrolling through the device and documenting the information was extremely limited. The first examinations of data by law enforcement on a Motorola StarTAC or Nokia 1610 Plus involved simply turning on the device after reading the data from the SIM, scrolling through the menus, and writing by hand the calls made and received and the contact information. This information was then transferred to a report, and the first mobile device examination was out the door. This worked well because the devices held a limited number of calls and contacts, but imagine using this process with a mobile device of today! Imagine documenting 5000 contacts into a spreadsheet by hand, including all the associated e-mail addresses, phone numbers, and addresses, not to mention scrolling through the selfies.
Cameras eventually began to play a role in the documentation of data for mobile devices. Important SMS messages, images, or contacts could be documented using a webcam or digital camera. These images were then placed into a report for review. Several companies built systems to enable the examiner to lay out the evidence, document the size, and more.
Soon the examination progressed to using software as a few software applications became available. The early mobile device software applications used in the examinations of cell phones were developed by engineers to deal with their own personal mobile device problems—such as how a phone book could be saved, edited, changed, modified, and exported without having to use the phone’s number pad to reenter information.
Software applications such as BitPim, initially developed by Roger Binns, is a perfect example. Binns created an application that would enable him to transfer data, primarily his contacts, from an old phone to a new phone. He explained that it had been extremely tedious to add contacts, get pictures, and move information on and off an LG phone, so he decided to write an application to make it easier, and BitPim was born. At first, BitPim enabled data to be written to and read from the cell phones supported, which was forensically sound. At the time, Binns had not seen the need to allow only data to be read, but soon he was contacted by a mobile forensic examiner and asked if he would allow users to turn off the ability to write data to the phone. BitPim software was being used in Mobile Forensic, Inc., courses and primarily for law enforcement officers, so Binns kindly accepted the reasoning and soon he added a Block Writing Anything To The Phone checkbox to the settings, as shown in the following illustration. BitPim was limited mostly to CDMA devices, but because protocols were based upon the Qualcomm chipset, some Samsung GSM devices could be supported as well. GSM devices, however, were never officially supported by BitPim, and the software’s last official build was on January 24, 2010.
More and more developers began to contribute, and more and more devices were added. More applications from actual cell phone manufacturers such as Nokia and Samsung were developed for the transfer of user contacts, SMS, and more. These proprietary software suites began to be used regularly by law enforcement officers to perform extractions and collections so they did not have to go “commando style” on a cell phone to get the information manually. Applications such as Paraben Cell Seizure, TULP2G, SIMCon, and MOBILedit began to be used in training courses and forensic labs around the world. These applications gathered data from mobile devices by using the same protocols reverse-engineered from tools such as Nokia Suite and Samsung PC Suite. Today, as in the beginning, the same problem exists: not all mobile devices are supported by a single solution. Now, bring in drones, IoT (Internet of Things) devices, wearables, infotainment, and other mobile-to-mobile (M2M) devices, and the extraction and examination issues are only exacerbated. There is not and will not be a single solution to extract and collect data from all digital mobile devices, simply because there are too many kinds of devices, and new devices are being added and changed continuously.
![]()
Using multiple tools to examine digital data from a mobile device should never be observed as poor practice. Quite the opposite is true: using multiple tools enables not only verification of data, but more importantly, it enables you to uncover additional data the initial tool either did not support or simply missed.
Examiners in the beginning of the mobile forensic time line had two types of evidence to process: a SIM card and the mobile device. Sometimes the only data that could be collected from a mobile device came from a SIM card. There were, and still are, many variables to be considered: Did the actual device even have a connection to communicate with the software? Did the device store data internally? More importantly, was the device even supported? At this time, a new trend emerged: devices were now capable of holding data on a removable card, known as a memory card. Yes, the first cards were not microSD cards, but large PCMIA (Personal Computer Memory Card International Association) cards primarily used for PCs. These obviously were very large, so transitioning to CompactFlash (CF) cards moved them from the PC to the camera and into the many PDA devices for storage.
With the addition of removable media, mobile device forensics expanded to three pieces of evidence to collect during any examination. CF cards are still available, but the Secure Digital (SD) cards are now most prevalent in mobile devices. These small SD cards range in storage capacity, but the devices of today are no longer limited to reading 128GB, 256GB, or even 400GB—some devices tout the ability to read 2TB cards! Obviously, devices can contain multiple SD cards or SIM cards, but the primary items to be examined and collected will remain the same: device, SIM, removable media, and sometimes a backup of the mobile device that is located on another type of media, such as a PC. Today’s mobile devices primarily use the microSD card as the de facto external storage medium.
With the ability to extract and decode data from the cloud, today’s examiner now has an additional repository for mobile device evidence. In Chapter 4, the discussion turns to the storage of today’s devices and another treasure trove of evidence. Digital devices for years have been storing data on servers located around the globe. This fact is easily observable every time a user upgrades to a new mobile device. The user simply downloads the app to the new device, signs in, and all his or her history magically appears within the app, kindly planting the server’s data contents on the new device. Only recently have mobile device examiners had easy access to these endpoint storage cabinets with automated software. So now add another evidence area the savvy examiner must become familiar with.
To help you understand the multiple points of examination of a mobile device, let’s take a general look at these data storage points and what information might be stored on each.
Data Storage Points
With multiple places to store data, mobile devices and cellular technologies, along with their forensic examinations, have become more advanced as the years have progressed (see Figure 1-2).
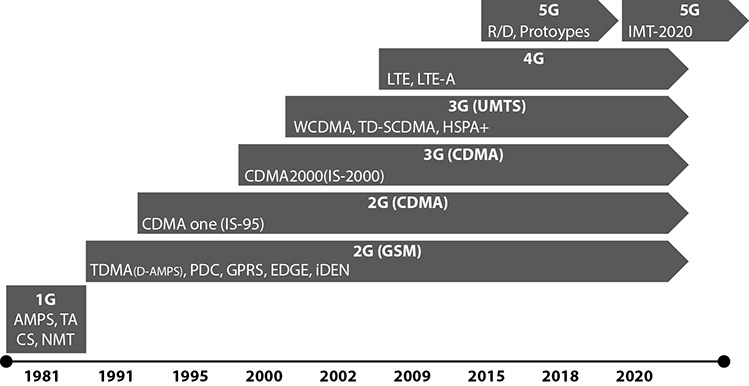
FIGURE 1-2 The cellular generational time line represents the various transitions in technology related to mobile devices from 1G to our current LTE-A, and soon 5G.
Mobile Technology Terminology and Acronyms
It is important that you understand the current terminology used in the industry before you read more about using storage points for evidence. Acronyms are used throughout the book and also in most digital forensic reference materials. Technological terms, reference documents, and government agencies all use acronyms, and the following list includes the most prevalent terms in the industry. Some terms describe cellular network functions and transmission techniques.
![]()
The following provides an overview, rather than a complete, detailed description. There are entire books describing these transmission methods in great detail. This book is intended to expose these terms generally, so, if needed, you can conduct further research on your own.
AMPS/NMT/TACS
In the 1980s, the Advanced Mobile Phone System (AMPS) was the analog standard used in the United States, Nordic Mobile Telephone (NMT) was the analog standard in the Nordic countries, and Total Access Communications Systems (TACS) was the analog standard in the United Kingdom. Analog transmissions operated in the 800 MHz band between the frequencies of 824 MHz and 894 MHz in the United States, 450 MHz and 900 MHz in the Nordic countries, and in the 900 MHz range for Europe. The transmission and the reception of the data ranged from 20 kHz to 50 kHz so transmissions did not collide. Obviously, with the limited number of devices that could operate simultaneously, it was easy to listen to conversations on radio devices tuned to the same frequency. This technology was later termed 1G, for first-generation, cell phone transmission technology. AMPS expired February 18, 2008.
Governing bodies for mobile device transmission understood that additional data should be included in the transmission, such as text messages, while also allowing for more mobile devices to use the same frequency channel. For this reason, analog would need to transition to digital data. Mobile devices purchased for use that were labeled single-band indicated that the device could use only a single cellular band. Because of the varying frequency differences among countries, a device might not work in another country if the cellular band was not the frequency band within which the device was capable of operating. Because of this limitation, device manufacturers began to add hardware capabilities to allow for multiband frequency support, moving first to dual-band, then tri-band, and eventually quad-band support.
TDMA/GSM/CDMA
Time Division Multiple Access (TDMA) and Code Division Multiple Access (CDMA) are 2G (second-generation) technologies, and these devices entered the handheld wireless scene in the 1990s. The main standards for 2G are GSM, Interim Standard 95 (IS-95) (CDMA), IS-136 (digital amps), and iDEN (Integrated Digital Enhanced Network). The biggest change was from analog to digital with the advent of 2G systems, along with digital encryption of the transmission. The first commercial 2G network on the GSM network was first made available by Radiolinja, a Finnish operator.
2G also brought the ability to send data other than voice over the wireless network; SMS was born, with the first text reportedly sent from a computer to a mobile device on December 3, 1992, from Neil Papworth to his colleagues at Vodafone, that said, “MERRY CHRISTMAS.” 2G technologies slowly improved, and the progression toward 3G was slow. 2.5G, or GPRS (General Packet Radio Service), improved network stability, and 2.75G, or EDGE (Enhanced Data rates for GSM Evolution), improved the speed of transmission and was a large leap from 2G technologies.
![]()
It used to be extremely easy to distinguish the various GSM or CDMA wireless companies simply by looking under the device battery. If the device had a SIM card, the device was a GSM device; if it did not have a SIM card, it was a CDMA device. In today’s world with multiple-band devices, it has become common to see SIM card slots in CDMA devices.
UMTS/CDMA2000
Universal Mobile Telecommunications System (UMTS) and IS-2000 (CDMA2000) are the 3G, or third-generation, cellular systems established by specifications outlined in IMT-2000 (International Mobile Telecommunications), which introduced large gains with Internet access and video and data streaming in the early 2000s. The Third Generation Partnership Project (3GPP) standardized UMTS, and 3GPP2 (Third Generation Partnership Project 2) standardized CDMA2000. UMTS uses W-CDMA (wide-band CDMA) for transmission and CDMA2000 using EV-DO (Evolution–Data Optimized). UMTS was used with GSM devices in Europe, China, Japan, and most other areas of the world, while CDMA2000 and CDMA devices were used primarily in North America and South Korea.
UMTS upgraded to HSDPA (High-Speed Downlink Packet Access) and was combined with HSUPA (High-Speed Uplink Packet Access) to form HSPA (High-Speed Packet Access), which is still the most widely deployed technology globally. What might be referred to as 3.5G is debated as HSPA+ and also LTE (Long Term Evolution). LTE is often mentioned with regard to 4G technologies, but the data upload and download rates do not meet the standards set forth by the ITU (International Telecommunication Union) to call it 4G. The first commercial LTE networks were launched in Norway and Sweden in 2009.
LTE-Advanced
LTE-Advanced (LTE-A) is also defined by the ITU, and it is a true 4G system. LTE-A was standardized in 2010 by the 3GPP and is dependent not only on the infrastructure of the underlying cellular network but also on the processors within the mobile devices.
IMT-2020 (5G) International Mobile Telecommunications (IMT) systems 2020 is also defined by the ITU, and it is currently a theoretical 5G system. As of this writing, IMT-2020 is being debated and developed, and is said to be a single unified standard for mobile communication and data. The current specifications from ITU indicate a 20Gbps (gigabits per second) download capacity for a single cell as a minimum, with support for one million connected devices per one square kilometer (0.39 square miles). Compared to the current LTE download capacity of 1Gbps, the infrastructure and demand on the telecommunication companies around the world will be significant. Features will include simultaneous wireless connections to a single device using a new Wireless World Wide Web (WWWW). This type of wireless connection will significantly impact the use of wearables and other IoT devices.
Mobile Device
The mobile device evolved from a simple handheld device to communicate via voice into a mobile computing device capable of transmitting large amounts of data instantly. The movement in technologies and the air-side of the network was never intended to create a clearer conversation, but to increase how much information one could send or receive in the shortest amount of time.
A mobile device can contain many pieces of information, from contacts, SMS, and call logs in early devices, to complex documents, applications, media, SMS, Multimedia Messaging Service (MMS), call logs, e-mail, calendar, notes, and contacts in today’s devices, which are actually small computing devices. Built-in applications, or apps, can store additional data types, communicate with the Internet, launch rockets, play music, map a house, direct a vehicle to a destination, determine internal body vitals, and conduct bank transactions. There is almost nothing that a person cannot do with these smart devices—including activities that only ten years ago required devices thousands of times their size. Today’s current smart devices come with standard apps, but a user can also install one of approximately seven million apps available on various mobile phone app distribution points, which makes a “standard examination” of the contents of mobile devices a nearly impossible exercise.
Mobile devices come in all shapes and sizes and have progressed from holding circuits to more than 256GB of storage space. What is most important for the mobile device forensic examiner is the underlying operating system. Knowing the type of operating system will help you determine the course of action you should take in the examination. Knowing this will also determine the actual software that you should use to complete the collection. As you read through this book, you’ll learn more about these devices, and it will become apparent that your examination should start with an understanding of various types of evidence.
SIM and UICC
Subscriber identity modules, or SIM cards, were developed to enable portability and, more importantly, to store information to enable authentication on the cellular network. Authentication in this sense means that the device can register and enable users to make and receive calls. With the SIM card acting as the key to the network, a user can switch equipment by removing the small smart chip and inserting it in a different GSM device. As SIM cards began to enable the storage of user data such as contacts, SIM removal also meant that users could take their contacts with them to the new device. When a SIM card is inserted into the new device, the user can access contacts and make and receive calls. Storage on the SIM card makes it easy to move from one device to another. Along with contacts, SMS are also stored, as are the last numbers dialed.
All data types on a SIM card are not infinite, and the amount of data that can be stored is a static value determined by GSM standards. As outlined in the initial documents by ETSI (European Telecommunications Standards Institute) and later adopted by 3GPP, the “Technical Specification Group Terminals Specification of the Subscriber Identity Module” outlines the type of data along with how many records can be stored for each type of data. The SIM cards in today’s GSM and CDMA devices are called UICCs (Universal Integrated Circuit Cards) and assist in the operation of the UMTS, HSPA, and LTE systems. It can be said that the UICC will work on all mobile telecommunication networks.
Some say, incorrectly, that a SIM card is the same as a USIM (Universal Subscriber Identity Module) card. Although technically SIM cards are physical cards that operate only on 2G GSM systems, a USIM is an application on the UICC. The USIM application enables the mobile device to be identified on the UMTS, HSPA, and LTE systems. UICCs also contain a SIM application that allows for backward-compatibility to the 2G networks and may also contain another application called the CSIM (CDMA SIM), which allows access to CDMA networks, and an application called ISIM (IP-multimedia Subsystem Subscriber Identity Module). The ISIM allows for secure use of the Internet Protocol multimedia subsystem and is the backbone of the LTE network. This means support for voice over IP (VoIP), SMS, and emergency calls without a network can occur securely. One of the biggest advantages of the UICC is this ability to store multiple applications on it.
![]()
Earlier CDMA SIM cards were called R-UIM (removable user identify module) cards and contained a primitive version of the CSIM application and a SIM application for GSM.
Like the SIM, the UICC also allows for the storage of contacts, SMS, and other user histories. What has not changed from the SIM to the UICC or USIM application is the ability to store more SMS messages or more call detail data. The reason behind that has to do with the understanding that today’s devices default to storing data to the handset, not the SIM card. Along with the velocity and volume of this data, this is not likely to change. In Chapter 11, you can read about the actual structure and the evidence locations for specific SIM and UICC data.
Media Storage Cards
SD cards were created in an effort to expand the available storage for mobile devices. SD cards are of four different types: Standard-Capacity (SDSC), High-Capacity (SDHC), Extended-Capacity (SDXC), and a newer type not used currently with mobile devices, called Input/Output (SDIO). These four types come in three different form factors: the original, which measures 32-by-24 mm; the mini, which measures 21.5-by-20.0 mm; and the micro, which measures 11-by-15 mm.
![]()
External micro-sized SD cards typically come with an adapter that enables the cards to be read using a standard-size SD card reader. Important to remember is that most SD card full-size adapters have a “lock” that disables writes to the SD card media. When processing these storage mediums, you must set the card to locked to enable the write-protection feature built into the card.
Today, mobile device equipment often contains a slot to accommodate a small storage card that stores saved images, videos, or other media, but can also store documents, applications, and more. Important to remember is the fact that external media cards are another form of evidence. In the early years of mobile devices, external media cards were sized at 256 to 512MB. The most prevalent type and form factor used in today’s devices are the original and microSDHC cards. The SDHC standard, released in 2006, supports a total capacity of 32GB, and the micro size is the most prevalent type of card with mobile devices. The SDXC, released in 2009, supports up to 2TB of data by using Microsoft’s exFAT (Extended File Allocation Table) file system, and some current mobile devices will support and recognize cards in the micro size up to 2TB. However, the purchase of legitimate operational 400GB SDXC for a mobile device is now possible.
![]()
To help you understand just how much data can be stored in a gigabyte, let’s discuss what a gigabyte is. A gigabyte is equivalent to a device’s ability to store 10,000 one-page documents in the Times New Roman font, 12-point, single-spaced; 520,000 text messages; 1074 regular sized photos; and approximately 250 songs that are each four minutes in length. With the sheer volume of data that can be stored on media smaller than a postage stamp, it becomes apparent that omitting this type of evidence from your mobile forensic exam could be catastrophic.
Many new devices, especially those running the Android operating system, also have internal microSDHC and SDXC cards soldered to the internal circuitry to add internal storage capacity. This is an inexpensive way to expand the capacity of a device. Understanding and recognizing that a device has internal microSD storage is very important during your digital exam. This internal storage is in the range of 4 to 64GB, which can hold an astronomical amount of data. More devices today contain both internal and external microSD cards. During a proper examination, if possible, you should collect and analyze both storage locations.
![]()
To determine whether a device contains both internal and external SD card components, research the device before starting your examination. This information can be obtained from web sites discussed in the coming chapters.
Mobile Device Backups
The last type of associated data for mobile devices is the backup that some devices create on media such as PCs, Macs, and other operating systems. Today’s devices also use the Cloud to store backups. Devices such as Apple iPhone and iPad and the new BlackBerry smart phones create backups that you can later analyze. Apple iOS devices create a backup using the Apple iTunes software. You’ll find these backups in different locations depending on the type of computer operating system and version.
For Windows computers, the backup default location for an Apple iOS device will depend on the operating system version:
• Windows XP Documents and Settings<username>Application DataApple ComputerMobileSyncBackup
• Windows Vista, Windows 7, 8, 10 Users<username>AppDataRoamingApple ComputerMobileSyncBackup
• macOS ~/Library/Application Support/MobileSync/Backup/
These areas contain valuable data and can also contain multiple backups of the same device. For an iOS device, the data that is typically backed up as outlined by Apple in the support wiki (http://support.apple.com/en-us/HT4946) is listed here:
• Camera Roll photos, screenshots, images saved, and videos; for devices without a camera, Camera Roll is called Saved Photos
• Contacts and Contact Favorites
• Calendar accounts and subscribed calendars
• Calendar events
• Safari bookmarks, cookies, history, offline data, and currently open pages
• Autofill for web pages
• Offline web app cache/database
• Notes
• Mail accounts (mail messages aren’t backed up)
• Microsoft Exchange account configurations
• Call history
• Messages (iMessage and carrier SMS or MMS pictures and videos)
• Voicemail token (not the voicemail password; the token is used for validation when connecting and is restored only to a phone with the same phone number on the SIM card)
• Voice memos
• Network settings (saved Wi-Fi hotspots, VPN settings, and network preferences)
• Keychain (includes e-mail account passwords, Wi-Fi passwords, and passwords entered into web sites and some apps—can be recovered in an iTunes backup only if the backup has been encrypted)
• App Store app data (except the app itself, its .tmp file, and Caches folder)
• App settings, preferences, and data, including documents
• In-app purchases
• Game Center account
• Wallpapers
• Location service preferences for apps and web sites you’ve allowed to use your location
• Home screen arrangement
• Installed profiles
• Map bookmarks, recent searches, and the current location displayed in Maps
• Activity and Health (can be recovered in an iTunes backup only if the backup has been encrypted)
• Paired Bluetooth devices (only if restored to the same phone that did the backup)
• Keyboard shortcuts and saved suggestion corrections
• Trusted hosts that have certificates that cannot be verified
• Web clips
Some items are not contained within an iTunes backup reported by Apple (https://support.apple.com/en-us/HT204136), including the following:
• Content from iTunes and App Stores, or PDFs downloaded directly to iBooks
• Content synced from iTunes, such as imported MP3s or CDs, videos, books, and photos
• Photos already stored in the cloud, such as My Photo Stream, and iCloud Photo Library
• Touch ID settings
• Apple Pay information and settings
![]()
A series of files and folders are created for the iOS device backups at these storage positions. If the user has elected to encrypt backups via the iTunes interface, the backups will not be readable unless the iTunes password is known.
BlackBerry also creates backups using the BlackBerry Desktop Management software, or Link as it is known today for some new BlackBerry devices. These backups are also located in a default location:
• Windows My DocumentsBlackBerryBackup
• Mac /Users/<name>/Documents/BlackBerry Backups
![]()
A user can always change the backup location using the BlackBerry Backup Software.
Depending on the version of BlackBerry software that was used to create the backup, the file will either have an .ipd or a .bbb extension. Files with an .ipd extension will have been created with earlier versions of BlackBerry Desktop Manager (versions up to 6), while .bbb files are created by BlackBerry Desktop Manager version 7 and the new Link software. The .bbb files that are created by Link are fully encrypted, and known BlackBerry user information must be used to decrypt the data.
![]()
Both iOS and BlackBerry backups contain very valuable data that you can analyze in commercial tools such as Oxygen Forensic Detective and Analyst, MSAB XRY, and Cellebrite Physical Analyzer, along with free tools such as iPhone Backup Browser and MagicBerry. The collection and analysis of backups can assist your investigation if the device cannot be located or accessed, but examinations of the backups are also a way to compare the data from the backup to the actual device for a historical perspective.
BlackBerry Enterprise Server (BES) technology was the first platform that allowed an enterprise to store data from a mobile device in a central location on the company premises. This added great security to a company’s critical and confidential data by enabling local storage of e-mail, documents, messages, event data, and company materials. This information could be accessed by company enterprise security teams to ensure compliance and gain visibility into the device if law enforcement requested data not stored on a device or data that had been deleted. Security administers of the BES can also remotely unlock a device if it is under control of the enterprise, which is also of great benefit to law enforcement. BES12 is an endpoint mobility management (EMM) tool and can contain data that is not accessible on the physical device, so don’t overlook this information while conducting an investigation of a BlackBerry device.
As mentioned, devices can also create backups in the Cloud. iOS devices use a service called iCloud, which launched in October 2011, with almost 800 million users currently. The iCloud service enables the user to store user data, applications, documents, pictures, and more on a server maintained and owned by Apple. This information can be retrieved using tools such as Oxygen Forensics Detective Cloud Extractor or Elcomsoft’s Phone Breaker with the user’s Apple ID and password.
![]()
For iCloud backups, a user can obtain most of the data from a standard iTunes backup with a few exceptions. The following items, as indicated by Apple’s support site (https://support.apple.com/en-us/HT204136), are not included in an iCloud backup:
—Data that’s already stored in iCloud, such as Contacts, Calendars, Notes, My Photo Stream, and iCloud Photo Library
—Data stored in other cloud services, such as Gmail and Exchange mail
—Apple Pay information and settings
—Touch ID settings
—iCloud Music Library and App Store content (if it’s still available in the iTunes, App, or iBooks Store, you can tap to re-download your already purchased content)
Because of many security concerns with unauthorized access to iCloud backups, Apple utilizes end-to-end encryption as long as the device owner has turned on two-factor authentication. This security update has added another hurdle for law enforcement when legally obtaining information stored using the iCloud service and tools.
Storing backups on the Cloud has moved to Android to include Samsung Cloud, Google Cloud, Huawei Cloud, OPPO Cloud, and many others with onboard applications downloadable from the Google Play Store; BlackBerry has moved new devices to BlackBerry Protect. With many new devices moving to the Cloud, investigators must be cognizant of these locations as well. These cloud services, as well as methods to extract and analyze this data, will be covered in Chapter 4.
Educational Resources
You should always begin any investigation with research of the device to be examined. Knowing as much information about a device as possible will ensure that you won’t miss internal and external components. Knowing, for example, that a device has a built-in 64GB internal SD card is very good information to know before you start an examination. Several resources online can assist you in identifying the many nuances of the millions of devices available.
Phone Scoop
Phone Scoop (www.phonescoop.com/phones/finder.php) contains valuable information to assist in the identification and research of the device to be examined. You can search by device model, make, or operating system to see information such as the current operating system and version, processor, memory (both internal and external), whether or not there is a SIM card, and the type, memory slots, and the FCC ID.
Phone Scoop has images of the device to help the investigator quickly identify the device visually and also contains links to query the FCC database. Querying the FCC database provides detailed summaries of the internal components, what the original equipment looks like, and where the label should be located and what it should look like.
Phone Scoop stores information on devices for North America only. Using this resource will help you as you research to gain a better understanding of the device, its features, and how to begin an examination.
GSMArena
GSMArena (www.gsmarena.com/search.php3) is much like Phone Scoop, but this site contains only GSM devices and is primarily for devices outside of North America. GSMArena is an information repository for reviews of the devices; phones searchable by model number, manufacturer name, and common name; and mobile device specifics. Mobile phone manuals are available for most devices, along with all the specifications, including but not limited to, size, memory, SIM type, operating system, hardware specs, USB port, and detailed images of the device.
Forums
Although Phone Scoop and GSMArena are valuable resources, obtaining information about what software might have been used on a specific device, tricks that you should know, and processing ideas all come from real experience. Forums are a way to connect with examiners and ask specific questions, search large databases for a device to see what software works best with that particular device, and so much more. The key to gaining experience and knowledge is by gathering as much intelligence prior to starting the actual examination of the device.
Here is a list of several forums that are good sources for information.
Forums with Databases
This forum contains a database that you can query in search of a device and the software to use.
• Mobile Forensics Central (www.mobileforensicscentral.com/mfc/) Use Mobile Forensics Central by searching its database to locate a phone report that lists the mobile device software and additional information needed for processing. MFC is a free site but requires registration.
Technical Information Forums
Use these forums to ask and search for mobile forensic technical questions.
• Forensic Focus (www.forensicfocus.com/computer-forensics-forums) This forum is for general forensic comments and questions based in Europe. This forum has a subforum for mobile forensics and contains tips, tricks, software information, and more.
• Android Developers Forum (http://developer.android.com/index.html) In this forum you’ll find developer information on the Android operating system; you can also obtain all drivers for Android devices and download the Android Emulator along with prereleases of the Android operating system.
• XDA Developers Forum (www.xda-developers.com/) This site contains a forum along with development resources for smart devices, primarily Windows and Android. In 2010, a sister site, iPhone-Developers.com, was launched. The XDA name represents the first device, a Windows PDA, for which the site was developed.
Preparing for Your Journey
Mobile device forensics is no different from any other technical discipline. All demand a respect of the details along with an effort to understand every variable and contingency that you might encounter. There will be many bumps in the road with respect to tools and devices and, more times than not, a mixture of both. Working through each and every problem for a solution will arm you with knowledge that many others in today’s mobile forensic world relegate to a tool.
Mobile devices will continue to be involved in the lives of nearly every human being on this Earth. They will continue to be used in some way in crimes, conversations, transactions, meetings, and Internet access for years to come and beyond. Mobile device examinations are not like any other digital examination discipline. To conduct thorough mobile device examinations, you need a constant appetite for research and training with this rapidly evolving discipline. Be patient, but more importantly, question the tools, understand what is under the hood, and prepare for anything!
Chapter Summary
Mobile device forensics is nothing like any discipline in the range of digital data examination because of the many different types of media associated with the single device (SIM, device, SD card, the Cloud, and even backups). Furthermore, the ways of acquiring the data from the devices are atypical to the standard digital forensic exam. The standard device collection is not the “bit-by-bit” image you would expect in other disciplines. Having a firm grasp on the basics will give you a strong foundation that will withstand the staunchest critique and challenge. Without having an underlying foundation, your examination will surely crumble under the scrutiny of an opponent.
