What Is a Firewall?
A firewall is like a border sentry. Think of a firewall as a guard along the border of a country. On a network, a firewall is a filtering device that enforces network security policy and protects the network against external attacks. A packet is a unit of information that is routed between one point and another over the Internet or any other network. The packet header includes information such as source, type, size, and origin and destination address. As a filtering device, a firewall watches for traffic that fails to comply with the rules defined by the firewall administrator.
Firewalls can focus on the packet header, the packet payload (the essential data of the packet) or both; or on the content of a session, the establishment of a circuit, and possibly other assets. Most firewalls focus on only one of these. The most common filtering focus is on the header of the packet, with the payload of a packet a close second.
FYI
The term “firewall” comes from a building and automotive construction concept of a wall that is built to prevent the spread of fire from one area into another. The firewall in a building or car engine compartment is a physical block against the spread of fire.
A firewall is an important part of an organization’s comprehensive security policy. A security policy defines the goals, objectives, and procedures of security. Every security policy focusing on network security requires the deployment of a firewall. The firewall’s job is to impose all restrictions and boundaries defined in the security policy on all network traffic. A firewall enforces your organization’s network security policy, just as a traffic policeman enforces the motor vehicle laws of a town or state. A firewall policy ensures the success of your network’s firewall. A company-wide security policy ensures the success of your organization’s security infrastructure. Firewalls are in no way a substitute for such a security policy.
FYI
A firewall enforces the network traffic access control security policy. A firewall is the physical embodiment of the security policy. It is the most obvious or direct enforcement of access control on your network’s traffic. No other device is as directly involved as your firewall in allowing authorized traffic and denying all else.
Firewall filtering compares each packet received to a set of exception rules. These rules state that content in the packet is either allowed or denied. If the packet matches an allow rule, it continues on to its destination. If the packet matches a deny rule, the packet is dropped. Hence, a deny rule prevents the packet from reaching its destination. If a packet fails to match any rule, the firewall drops the packet by default.
If properly configured, filtering allows what you want on your network and denies what you do not want. Filtering relies on filtering rules. Each rule identifies a pattern of concern and a response the firewall will make if an incoming element matches the pattern.
Firewalls follow a philosophy or stance of security known as deny by default/allow by exception. All the rules on a firewall are exceptions. Some exception rules define what you allow. Some exception rules define what you wish to deny. The final option, sometimes called the final rule, is that anything that did not match one of the exceptions is denied by default.
The filtering rules are the exceptions to the deny-all rule that is the final and absolute rule of a firewall. In fact, if a deny by default rule did not exist, the filtering device would not be a firewall at all. Instead, it would be more like a router or switch, allowing traffic to pass, even if it did not match an expected pattern or rule.
Technical TIP
Keep in mind the security stance of deny by default/allow by exception. A firewall is a filtering device that helps support this stance.
Network security administrators use the term “firewall” to refer to a device or service that allows some traffic but denies other traffic. This is not the same as a building’s firewall, which allows a fire to spread only if the firewall fails. In network security, firewalls allow traffic through that is considered safe—or at least authorizes traffic without the entire firewall failing. Additionally, if a firewall does fail, it fails into a secured state known as fail-safe or fail-secure. This means that when the firewall is offline, locked or frozen, or otherwise experiences a problem, the firewall stops all traffic rather than allowing all traffic through.
A gateway is an entrance or exit point to access a controlled space. Gateways are important because high levels of traffic typically pass through a gateway. Thus, positioning a firewall at a network gateway is an aspect of secure design. If the gateway already exists in the network infrastructure, then positioning the firewall at that point is an obvious security improvement. A firewall so positioned intercepts and verifies all traffic crossing that gateway point.
Some other places that firewalls are often deployed include in front of (i.e., on the public Internet side), behind (inside the data center), or in load-balancing systems—or, as they are most often called, load balancers. Load balancers are reasonably well-named because that is what these devices do: They take the load coming into a set of servers and ensure that the load is balanced between or among the servers, based on a variety of factors. It is a funnel point for traffic that is an ideal place to enforce policy, and that is done through the firewall.
If a network is still in its design phase, a network designer might make the secure choice to create a gateway in the network’s layout. However, in this situation, the concentration point would be known as a chokepoint instead of a gateway. If a gateway is an access point to other areas of resources, a chokepoint is a specialized kind of gateway that focuses on traffic to a single concentrated pathway to simplify the process of filtering.
You can also think of a firewall as a traffic-control device. A significant amount of network security is little more than controlling traffic. Authorized traffic passes through the digital intersection, while unauthorized, unwanted, abnormal, or obviously malicious traffic is blocked. Knowing how to distinguish the differences in the traffic is often difficult, requiring you to rely on well-crafted rules.
The very basic and original form of the modern firewall was a screening router. Routers analyze traffic based on destination address. The best-known available route to the destination informs the forwarding decision. However, screening routers added additional rules that could discard traffic based on destination or source address. Once filtering expanded to address protocols and even ports, the screening router became the basic static packet filtering firewall.
In addition to a firewall, a transparent proxy (also called an in-line proxy) can aid in filtering requests from outside the network. A transparent proxy is most often installed immediately between the firewall, protecting against Internet intrusions, and a web server. A proxy is something that stands in place of something else. In this case, it is a server that stands in place of and behaves initially as if it were the web server. When a request comes in for the web server, it is passed to the proxy if it meets the firewall rules. Upon receipt, the web server proxy either acts on the request or passes the request to the actual web server. This provides a buffer between the web server and the rest of the network.
In addition to filtering, firewalls can also offer routing functions, which are a holdover from this router ancestry. A multi-homed firewall can grant traffic access to one or another interface or segment based on the results of filtering. Traffic for a private local area network (LAN) could traverse one segment, while traffic destined for the demilitarized zone (DMZ) could follow another (see FIGURE 5-1). A firewall is an efficient, necessary traffic control device on the highway that is your network.
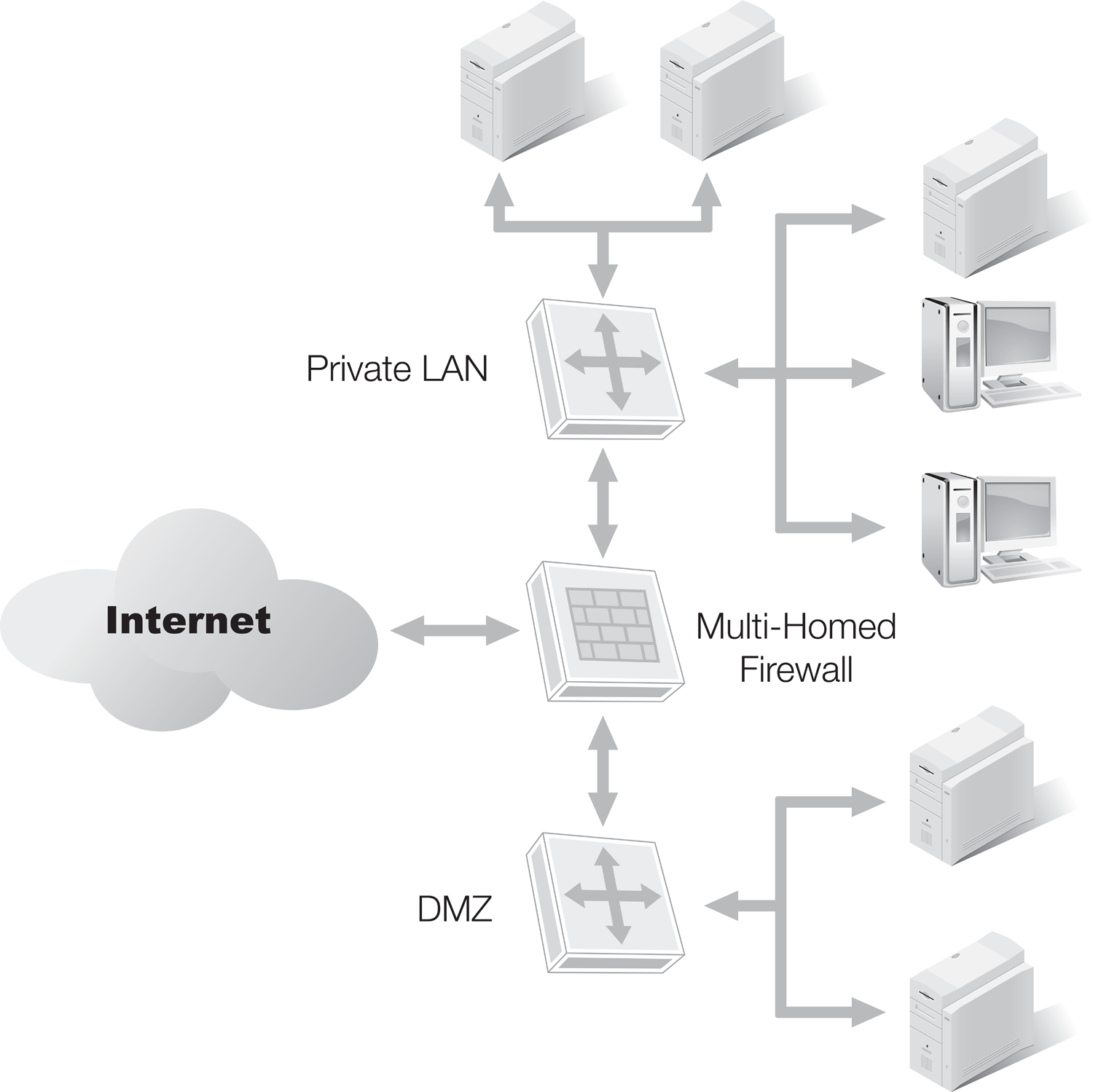
FIGURE 5-1 A basic multi-homed firewall filtering and routing for two network segments.
A firewall’s critical function is to protect your network against external attacks. It is no accident that some threats to computer networks are called viruses; external threats seem to continuously change and evolve. Some attacks are targeted specifically for your network or organization. Other attacks are untargeted and random. Instead, these attacks are directed toward any host that happens to have a specific vulnerability. Malicious code relentlessly infects and compromises unprotected computer systems. Flooding attacks attempt to interrupt timely Internet communications. These are only some of the external threats facing your organization’s network.
Whether labeled as a gateway for resource access or a chokepoint to control security, the result is the same. A firewall positioned at a gateway provides filtering services across all traffic. The chokepoint provides filtered access to resources. As a wise poet once said, “Good fences make good neighbors.” Similarly, good gateways and well-positioned firewalls make secure networks.
Understanding these definitions and distinctions is only the beginning of understanding firewalls.
What Firewalls Cannot Do
When used properly, firewalls provide reliable and consistent security from external threats. However, firewalls have limitations and are only part of the complete security strategy. By itself, a firewall cannot protect a network against every threat.
A firewall is an essential part of network security, but it is not the whole network security. Don’t make the mistake of deploying a firewall while ignoring other security management activities. A firewall is only one piece of the large complex puzzle to address network security. A firewall cannot do all things.
Authentication Server
A firewall is primarily for network traffic filtering. It is not an authentication system. Firewalls are not designed to check logon credentials, compare biometric scans, or even confirm the validity of digital certificates. These are the functions of an authentication service, typically hosted on a domain controller or primary network server.
That said, you might find it necessary for a firewall to allow authentication before granting access to a resource or allowing a session. Some firewalls can have enhancement features that provide for firewall-hosted authentication services. However, in many cases, a better solution would be to have the firewall offload that task to a dedicated authentication server or service, such as 802.1x, public key infrastructure (PKI), or directory services. Most security experts do not recommend using a firewall to authenticate users, or at least not as a replacement for a network’s directory service or centralized authentication solution.
Remote Access Server
A firewall is not a remote access server. Connections from remote users do not have an endpoint at the firewall. Instead, the endpoint is a remote access server (RAS) or network access server (NAS). A firewall may function before or after the RAS/NAS to filter remote access traffic. However, that doesn’t mean the firewall is the RAS/NAS.
Your firewall should filter all remote traffic, especially because remote traffic is much more likely to be purposefully malicious or accidentally damaging than local traffic. Why? An organization has much more control over who can connect to its network locally than it does when it allows remote connectivity.
Encrypted Packets
Unlike Superman, your firewall does not have X-ray vision into encrypted traffic; in other words, it cannot see the contents of encrypted traffic. A firewall can filter on the header of traffic using transport mode encryption, since the original header is in plaintext form. However, a firewall cannot filter the original header of traffic using tunnel mode encryption, since the only plaintext component is a temporary tunnel header that only includes information about the endpoints of the tunnel. It would be like trying to guess what’s in the boxcars of a train by observing only the locomotive and the caboose.
Position your firewall where it can be most effective. If the security design requires that all traffic content be examined by a firewall, then you need to position the firewall after encryption is removed from the traffic. If the security design requires filtering only on non-encrypted traffic, then positioning the firewall is not as critical.
Firewalls designed for use by web e-commerce sites may have an additional ability to act as the endpoint of a Secure Sockets Layer (SSL) or Transport Layer Security (TLS) tunnel from an Internet client. This grants the client protection for its data as the information traverses the Internet. This allows a firewall to filter the content of the traffic before the web server receives and processes the information.
Encryption is one method to evade filtering. Users and hackers can employ client-side encryption solutions that encode the data before transmission, or create unauthorized encrypted encapsulation tunnels to prevent firewall filtering. In this situation, your network security policy may stipulate that the firewall needs to block encrypted transmission initiated by clients, especially if the destination is on the Internet.
Malicious Code Scanner
A firewall is also not a malicious code scanner. Firewalls are traditionally rule-based filtering products. These rule sets usually have only a few dozen to at most a few hundred rules. To filter malicious code, the rule list would need millions of entries. In December 2009, the AVG Anti-Virus definition database #270.14.88/2538 was tracking 24,303,360 malicious code infection definitions. By 2018, that number grew into the hundreds of millions. That number of entries is simply impractical to include in a firewall rule set.
Some firewall products include an enhancement or add-on module for malicious code scanning. Such an enhancement is just an add-on component, not a core feature of a firewall. In most cases, it is more efficient and more secure to use separate anti-malware scanners than to add this function to your firewall.
Many firewall rules block traffic with spoofed addresses, uncommon ports, unauthorized protocols, invalid header constructions or values, and so on. Such rules block a significant amount of traffic caused by malicious code, but these rules do not directly block malware from entering or leaving a network.
Intrusion Detection
A firewall is not an intrusion detection system (IDS). An IDS is a type of network burglar or intruder alarm that detects and responds to unauthorized activity inside your network. An IDS performs this task by monitoring all network traffic. Although an IDS can be deployed on a network border or outside the network against the Internet, most operate inside private networks and provide the ability to watch all internal network traffic.
A firewall can detect malicious traffic only when such traffic enters one of the firewall’s interfaces. Firewalls usually do not watch over general interior network activity. Firewalls are either border devices for networks and subnets, or they are software products watching over a single host. In either case, they cannot see the same traffic, nor can they perform the same tasks as an IDS. A firewall, therefore, is not interchangeable with a good IDS.
Insider Attacks and Social Engineering
A common misconception is that firewalls protect against insider attacks. A firewall can be a border device, or a firewall can be software on a host. A border firewall can filter traffic entering or leaving a network or subnet. A border firewall is unable to see any interior traffic (FIGURE 5-2). When an attacker from an inside client attacks a target that is also an internal host, a border firewall is not part of the communication; thus, it can neither detect nor block the attack. A host software firewall can only see the traffic entering or leaving that one host. A host software firewall is unable to see any other interior traffic.
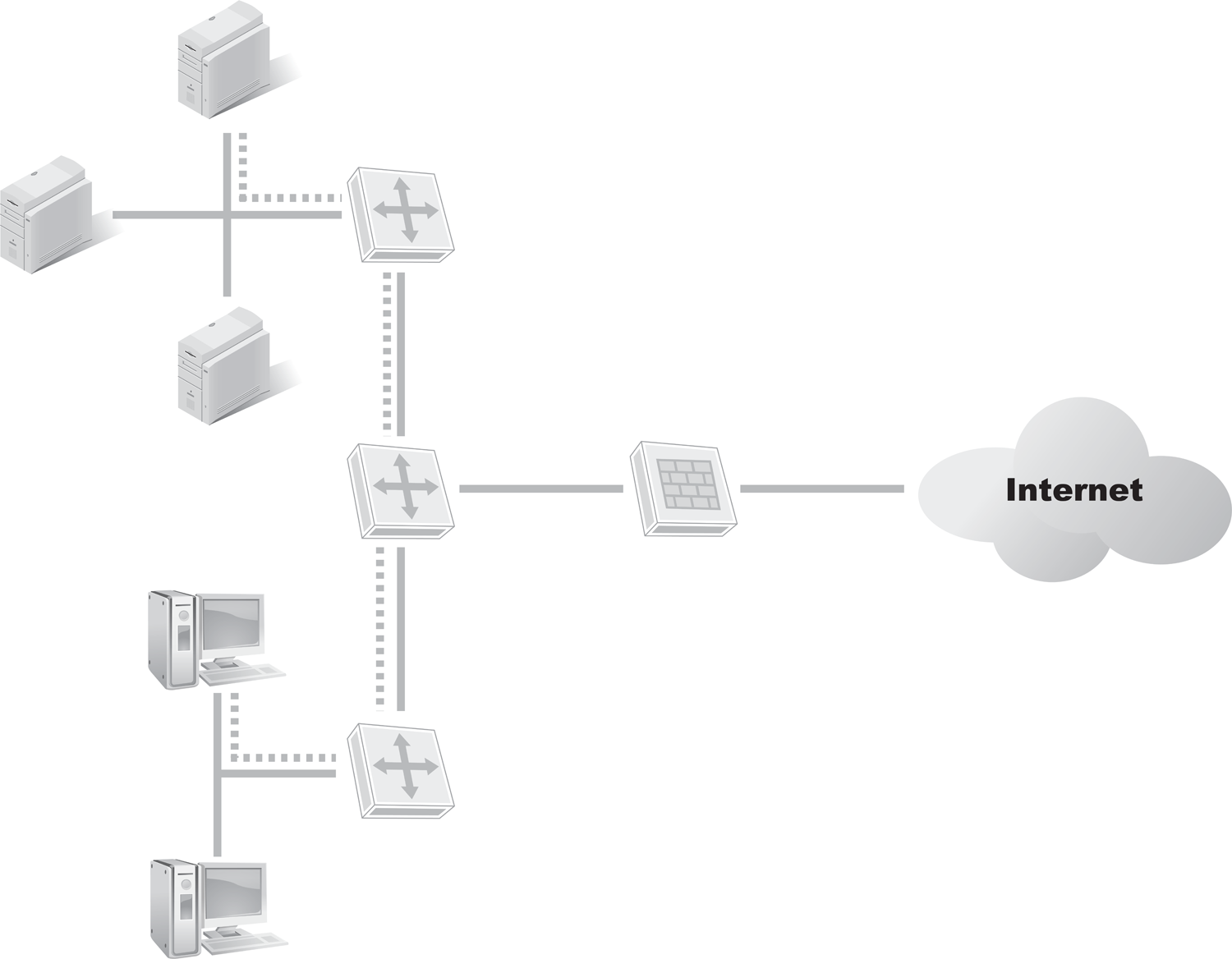
FIGURE 5-2 Border firewalls cannot filter internal communications.
Of course, if traffic does not pass through its interfaces, a firewall cannot filter the traffic. A firewall can filter only what it sees. If malicious or unwanted traffic does not enter an interface of a firewall, the firewall will not be able to filter that traffic. For the best strategy, you should place firewalls on each host, on every border gateway or chokepoint, and between each significant subnet or interior network division.
Another thing firewalls cannot do is protect against social engineering. Social engineering is a category of attacks that focus on the personnel of an organization. These attacks get information from people just by asking for it in clever ways or convincing someone to perform an action that breaches network security. The only real protection against social engineering is worker training and awareness.
 NOTE
NOTE
IDSs can detect a plethora of unwanted activities, use several methods of detection, and perform a wide range of responses, both passive and active.
Removable Media
A firewall cannot protect against the significant threat posed by the use of removable media. There are many different types of removable media: USB hard drives, USB thumb drives, CDs, DVDs, Blu-ray discs, HD-DVD discs, other optical discs, flash memory cards, FireWire storage devices, tape media, email attachments, a smartphone connected via USB cable, and more. A firewall is not involved in the use of removable media or in any of the contents these devices may contain. A firewall cannot protect your network against the ongoing threat posed by removable media. Again, the best defense against this threat is good company policy, worker training, and awareness.
Physical Attacks
A firewall, of course, cannot protect against physical incursions or attacks. Physical attacks bypass any and all logical and electronic protection mechanisms. A firewall does not protect against theft of devices, planting of eavesdropping mechanisms, disconnection of cables, connecting a rogue device to an open node, destruction of equipment, dousing electronics with liquids, building fires, or any other form of physical attack. Only effective physical defenses can deter physical attacks. A firewall is not designed or intended to thwart physical attacks.
Misconfigurations and Security Management
Computer equipment and software can do only what each is designed and programmed to do. If an administrator misconfigures a security device, the device does not automatically compensate for that oversight. If a security administrator fails to learn about all of the features and defaults of new equipment, the product cannot secure itself autonomously.
Security requires training, research, careful planning, thoughtful implementation, and ongoing review and maintenance. This process is known as security management—and it takes work. The old expression was never more true than it is today: “Garbage in, garbage out.” What you put into network security is precisely what you will get out of it. So, remember that a firewall cannot compensate for ineptitude or ignorance on the part of administrators.
Firewalls cannot compensate for poor security management. Proactive security management is essential for the success of any security endeavor. Security management is the process of reviewing, testing, tuning, and updating an organization’s security policies and security infrastructure. This is an ongoing effort that requires knowledge, research, and vigilance. The threats and risks facing an organization are constantly evolving to become more persistent and virulent. Your security strategy should be just as rigorous and purposeful in defense. Keeping up-to-date on current threats and trends in network security is a big part of this job. Networking with security professionals, attending relevant conferences, and reading the latest industry literature are ways to keep yourself and your security efforts sharp.
Finally, firewalls are not a perfect solution. They cannot self-adjust to changing conditions or future threats. Firewalls are mostly software (even when operating on dedicated hardware) and are written by fallible humans; therefore, they are subject to bugs and flaws. Fortunately, in spite of all the things a firewall is not, a firewall is a solid filtering solution. It can and should protect the borders of networks and individual hosts as part of a complete security infrastructure.
