What Is a Virtual Private Network?
A virtual private network (VPN) is a mechanism to establish a secure remote access connection across an intermediary network, often the Internet. VPNs allow remote access, remote control, and highly secured communications within a private network. VPNs employ encryption and authentication to provide confidentiality, integrity, and privacy protection for network communications.
The term VPN has its origins in the telecommunications world. A telephone VPN created a PBX-like system for businesses without the need for deployment of true private branch exchange (PBX) hardware. Instead, the system used a public telephone service and the PBX services at the telco’s central offices. This service/product sold under the name Centrex (a combination of central and exchange) in the 1960s through the 1980s.
After the proliferation of computer networks and Internet connectivity, the term VPN evolved to refer to tunneling connections across network links. Early computer VPNs focused on the tunneling or encapsulation processes and rarely included encryption services. Today, VPNs are almost always secured using encryption. However, you should never assume that anything is totally secure, especially connections over public networks. Always confirm that a product performs encryption properly before you depend on it for sensitive operations.
A VPN creates or simulates a network connection over an intermediary network. But what makes a VPN private? Several possible mechanisms exist:
- The primary organization owns all of the network infrastructure components, including switches, routers, and cables. A true private VPN occurs when a single organization owns all of the hardware supporting its VPN. However, few organizations actually own all of the connections between their locations, so this is usually impractical or prohibitively expensive. This wholly owned and operated system constitutes a trusted VPN.
- A dedicated set of channels is used across leased telco connections. This method provides physical isolation even on third-party equipment; hence, privacy is maintained. This type of system is more practical, but it is still expensive. This can also be called a trusted VPN, since you must be able to trust the owner of the hosting infrastructure to protect network communications against eavesdropping.
- Encryption ensures privacy even over public networks, such as the Internet. This method is the most reliable, as the other two options are still at risk to eavesdropping. Additionally, encryption to provide privacy is not only practical, it is the least expensive option as well. This system can be called a secured VPN.
- A hybrid VPN establishes a secure VPN over trusted VPN connections. A trusted VPN allows an organization to know and control the pathway of its transmissions. However, a trusted VPN does not protect against eavesdropping or alteration. A secure VPN protects the confidentiality and integrity of data, but it does not control or ensure the transmission path. When you combine these two VPN techniques, you create a potentially more secure and practical solution. Two possible layouts of hybrid VPNs are shown in FIGURES 9-1 and 9-2.
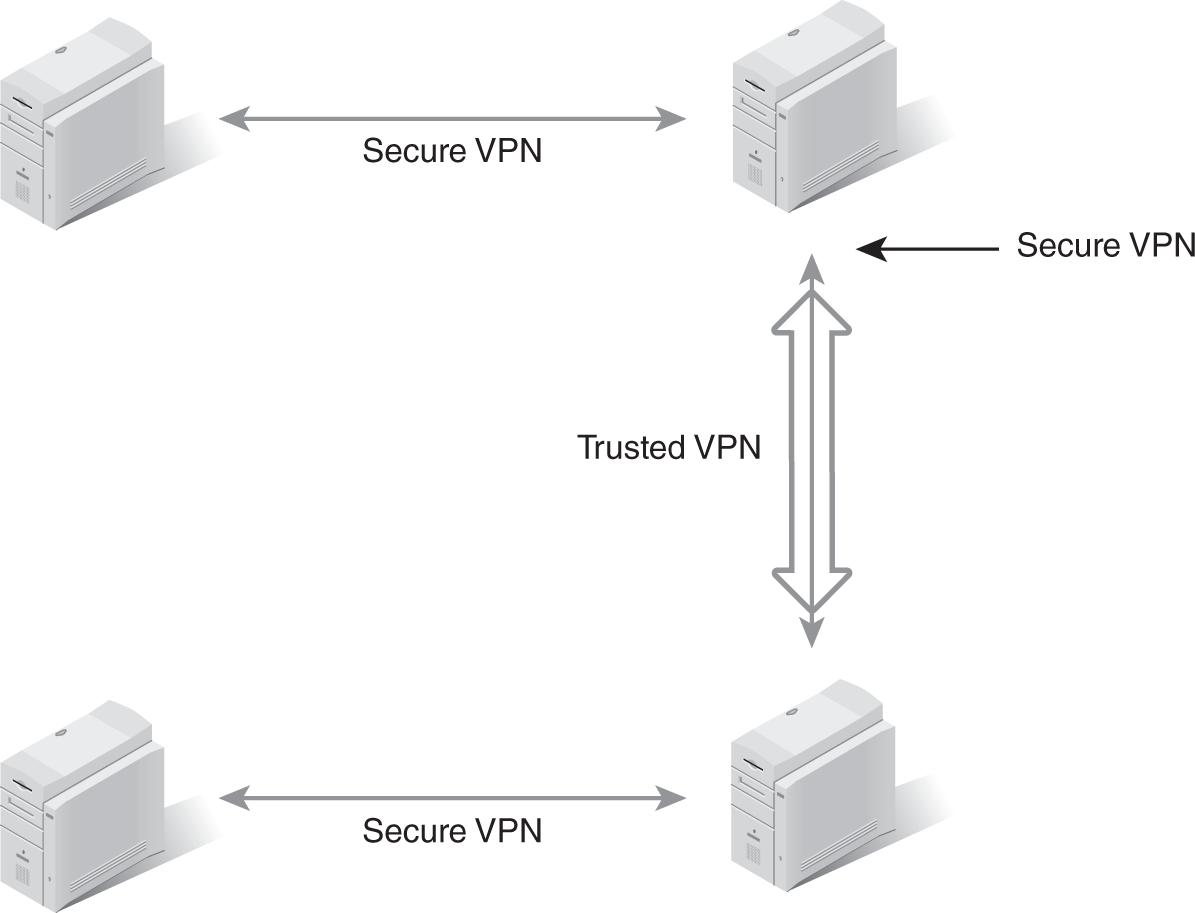
FIGURE 9-1 A hybrid VPN consisting of a secure VPN across an intermediary trusted VPN.
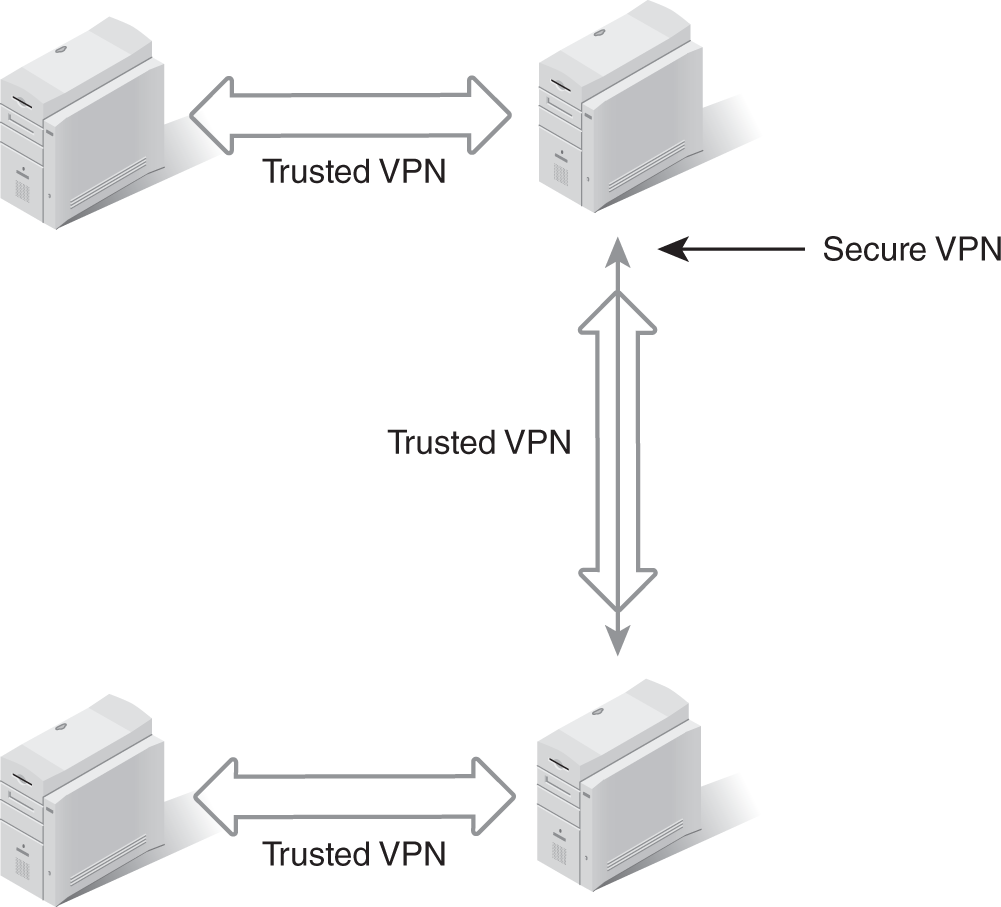
FIGURE 9-2 A hybrid VPN consisting of a secure VPN segment within a trusted VPN.
VPNs are often associated with remote access or remote control. However, these associations need clarification to have value. Remote control is the ability to use a local computer system to remotely take control of another computer. In a way, this process is the application of the thin-client concept on a fully capable modern workstation to simulate working against a mainframe or to virtualize your physical presence. This application is generally the same as a VPN, which creates a remote network connection rather than a remote control session.
With a remote control connection in place, the local monitor, keyboard, and mouse control a remote system. This process looks and feels as though you are physically present at the keyboard of the remote system, which could be located in another city or even on the other side of the world. Every action you perform locally acts as if you were physically present at that remote computer virtually via the remote control connection. The only limitations are the speed of the intermediary network link and the inability to physically insert or remove media and peripherals.
You might think of remote control as a form of software-based thin-client or terminal client. In fact, many thin-client and terminal client products sell as remote control solutions. Many modern operating systems include remote control features, such as Remote Desktop, found in most versions of Windows. Once enabled, a Remote Desktop connection remotely controls another Windows system from across the network.
Remote access is different from remote control. A remote access link enables access to network resources using a WAN link to connect to the geographically distant network. In effect, remote access creates a local network link for a system not physically near the network. Over a remote access connection, a client system can technically perform all of the same tasks as a locally connected client. Network administrators can impose restrictions on which resources and services a remote access VPN client can use.
Remote access and VPNs were originally supported over dial-up telephone links using modems. Today, remote access encompasses a variety of connection types, including Integrated Services Digital Network (ISDN), digital subscriber line (DSL), cable modem, satellite, mobile broadband, and more. Due to the wide availability of high-speed Internet connections, VPNs and other remote access solutions have become popular for both personal and business purposes.
In many cases, a remote access connection is created from a remote client back to a primary network. If the remote client needs to connect directly to the local area network (LAN), such as over a dial-up connection, a remote access server (RAS) will host a modem to accept the connection. If the remote client can use the Internet to access the LAN, then a local Internet connection is necessary. Once a normal LAN connection or Internet connection runs from the client, the VPN link is possible. Once the connection is established, the remote client can interact with the network as if it were locally connected.
In FIGURE 9-3, a LAN and a remote client have a connection to the Internet. These two connections are independent of each other. The LAN’s connection is usually a permanent or dedicated connection supporting both inbound and outbound activities with the Internet. The remote client can have a dedicated or nondedicated connection to the Internet. In the latter case, the connection is established before a VPN can be created. Once both endpoints have a connection to the intermediary network, in this case the Internet, the VPN can be created. In FIGURE 9-4, a new network connection is established from the remote client to the LAN across the intermediary network. This new network connection is the VPN.
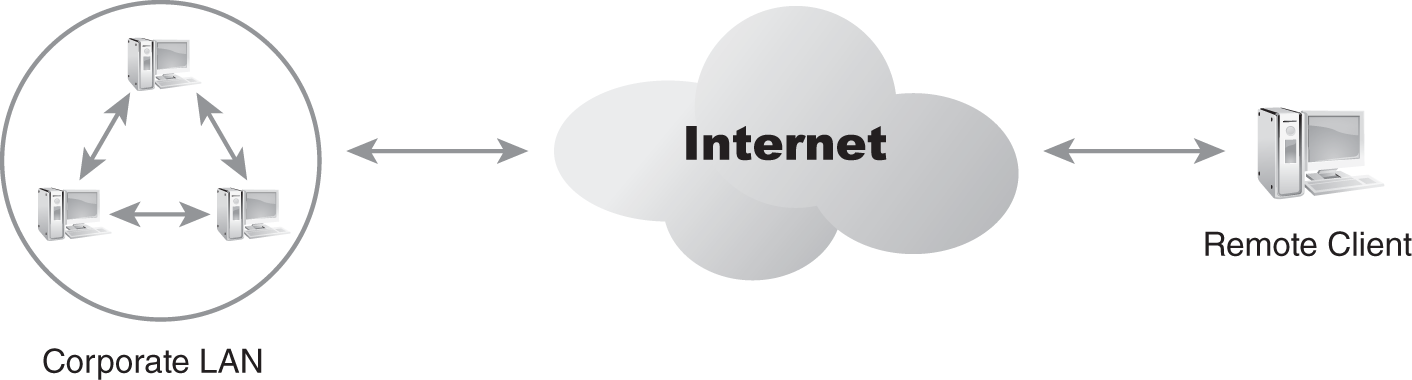
FIGURE 9-3 A corporate LAN and a remote client with Internet connections.

FIGURE 9-4 A VPN established between a remote client and a LAN over the Internet.
VPNs can operate over standard Internet connections or dedicated business communication circuits, such as Multi-Protocol Label Switching (MPLS), Asynchronous Transfer Mode (ATM), and Frame Relay. However, the additional expense of a dedicated, isolated, and even secured business circuit is not necessary with a VPN.
A VPN can operate securely over the Internet and still provide high levels of security through encryption. This allows inexpensive insecure links to replace expensive business-leased lines without sacrificing security.
VPNs are one of the most efficient and cost-effective means to provide secure remote connectivity. VPNs take advantage of cheap long-distance connections when established over the Internet, since both endpoints need only a local Internet link. The Internet serves as a “free” long-distance carrier. Because the speed of the VPN depends on the speed of the local Internet link, you still might want an optical carrier (OC) line (such as an OC-1 at 51.84 Mbps up to OC-768 at 40 Gbps) for high-speed connectivity.
Connections from a LAN to an intermediary network can support VPN traffic only, or they can allow a combination of both VPN and normal non-VPN traffic. The latter configuration is less secure, but it offers flexibility as to whether all communications must be VPN-secured or not. An Internet connection reserved solely for VPN use, therefore, is not necessary. An OC-1 line is more than capable of supporting one or more VPN links—in addition to numerous non-VPN Internet sessions—with no difficulty or latency. Latency is a delay in the transfer of data that is not desired or planned.
Setting up VPNs can require extensive knowledge and expertise on the part of the IT or security administrator. For example, some important concerns of secure VPNs include:
- All VPN traffic must be authenticated and encrypted. A VPN without authentication is not private, and a VPN without encryption is insecure.
- All VPN endpoints must abide by the same security parameters and algorithms. Each VPN tunnel must have corresponding encryption key sets to securely exchange encrypted content. Additionally, the same security policy should govern all endpoints.
- Proper encryption protocols must ensure that no external third party can affect the security of the VPN. Weak encryption makes a “secure” VPN vulnerable to attacks.
When you use a trusted VPN, you need to consider these concerns:
- A trusted VPN is based on the provider’s ability to limit and control access to the VPN’s content. Only the trusted VPN provider should be able to modify the channels or pathway of the VPN.
- Only the trusted VPN provider can add, remove, or change data in the trusted channel. Violating this violates the trust the client places in the provider.
- The addressing and routing performed within the trusted VPN must be defined before the VPN goes online. These services are usually predefined in the SLA (service level agreement), but they may be dynamically modified for each VPN connection.
Even hybrid VPNs have an important focus for concern, namely that the segments of the VPN that are trusted versus secured need clear definition. Mistaking security for trust—or vice versa—can have devastating results.
VPNs use tunneling or encapsulation protocols. Tunneling protocols encase the original network protocol so that it can traverse the intermediary network. In many cases, the tunneling protocol employs encryption so that the original data traverses the intermediary network securely. The protocols that create VPNs include IPSec (Internet Protocol Security), PPTP (Point-to-Point Tunneling Protocol), L2TP (Layer 2 Tunneling Protocol), SSH (Secure Shell), SSL (Secure Sockets Layer), OpenVPN, and TLS (Transport Layer Security). The dominant forms of secure VPNs use IPSec or SSL/TLS as the tunneling/encapsulation protocol. Most VPNs use software that operates on top of the OS of a host. However, some VPN appliances can support VPN connectivity without adding any software to the host. A host VPN software product allows a single host access to VPN services, while a VPN appliance allows an entire network to access VPN services.
VPNs simplify many business networking problems by providing an easy and efficient means to securely connect headquarters, remote offices, traveling workers, and telecommuters.
