Management Interfaces
You must configure firewalls for proper performance and the security functions you expect of them. Every firewall has a management interface used to configure its functions and features. Through the management interface, you can control and define all aspects of a firewall.
A firewall’s management interface may be command-line based (FIGURE 8-6) or graphical based (FIGURE 8-7). A graphical user interface (GUI) might be a standalone client application you must install onto a host, or it may be a web interface hosted on the firewall’s own internal mini-web server.
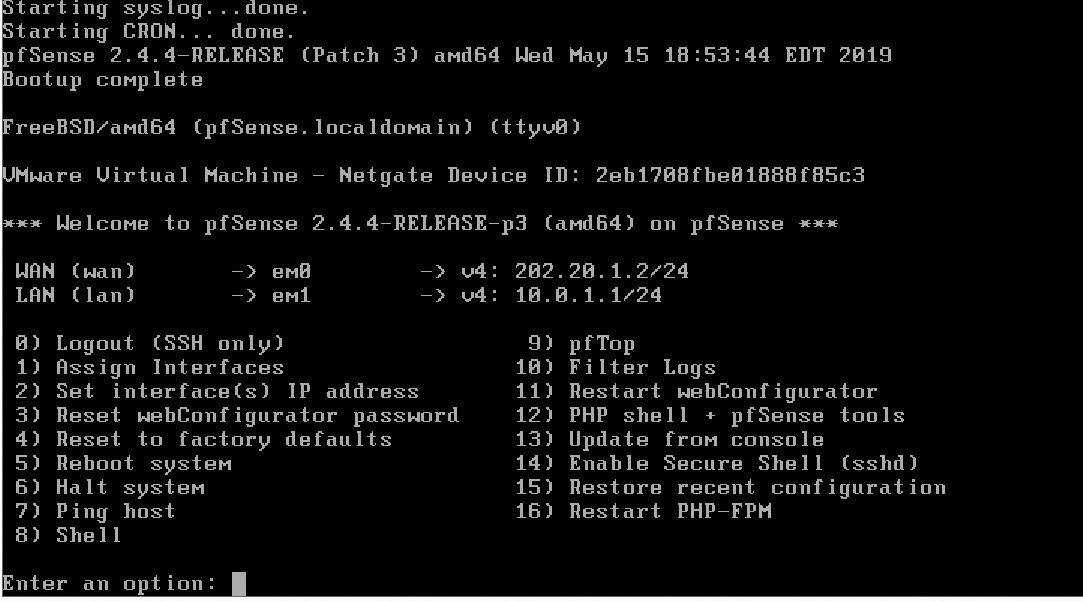
FIGURE 8-6 An example of accessing a firewall (pfSense) via command line (SSH).
© pfSense
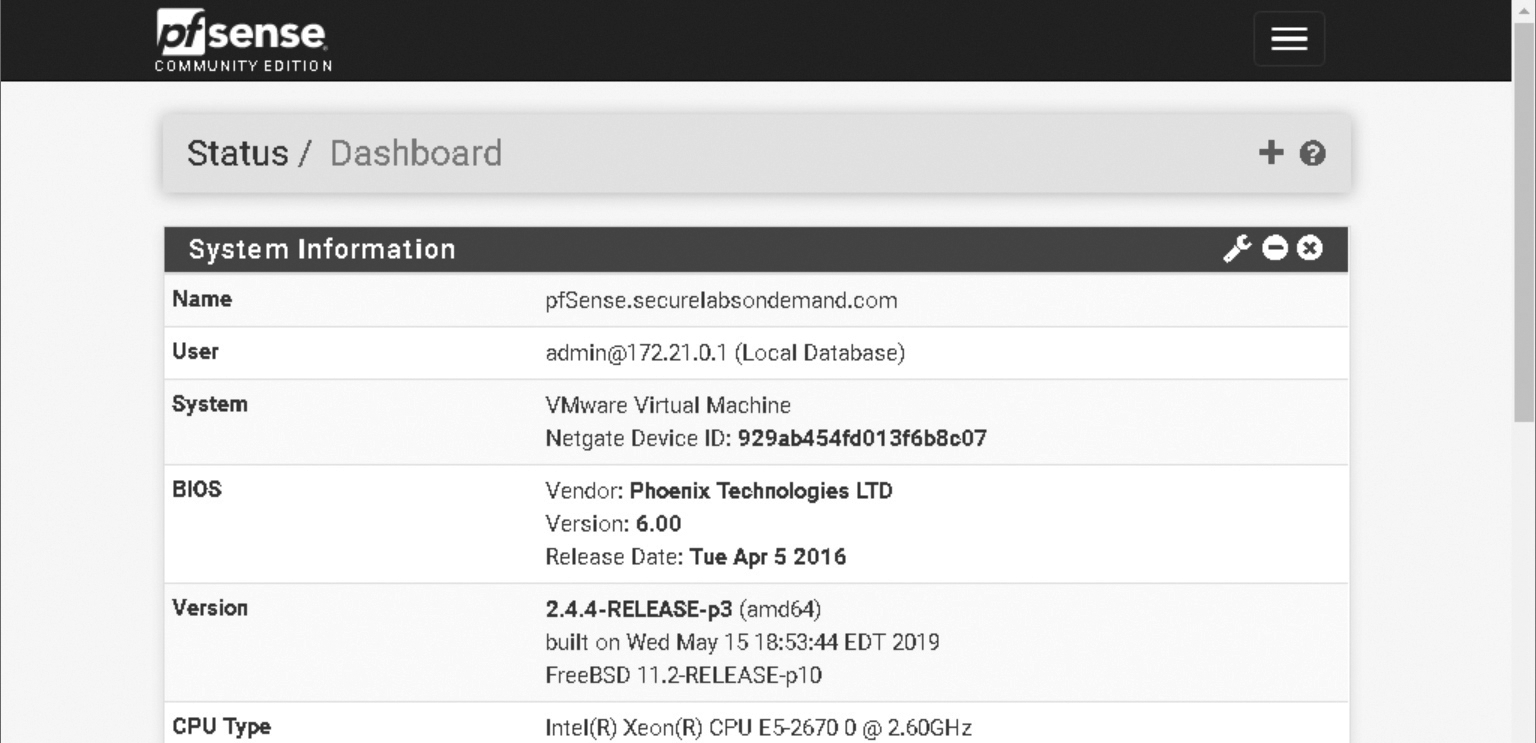
FIGURE 8-7 An example of a GUI firewall interface (pfSense).
© pfSense
A firewall’s management interface may offer encrypted access by default. If the firewall does not offer encryption of the management interface, then you should replace it with a firewall that does. Always enable the encryption so that all future access to the management interface is protected from eavesdropping, interception, and session hijacking. Encryption of the session accessing a firewall’s management interface is the most important and critical aspect of management interface configuration.
Secure a firewall’s management interface both physically and logically. This implies that direct physical contact with the firewall device, or firewall host, will be limited and restricted to authorized administrative personnel only. Prohibit any physical contact or proximity to external or unauthorized entities.
Secure all logical access to the firewall’s management interface through a strong authentication process. If multifactor authentication is supported, use it. If not, require long and complex passwords. Ensure that administrators do not reuse the same password on any other system. Administrators, as well as all users, should never reuse an old password on any system once it expires. Passwords are like milk—they last only so long, even with proper care and storage, and once expired, it should never be reused.
Technical TIP
The first step in deploying a new firewall is to change the default password of the administrator account. Better yet, modify every predefined user account and every default access code of any type. Use something unique, original, and difficult to predict. Be sure to properly document and securely store this information so it can be retrieved when needed but protected from unauthorized use.
Limit the methods to access a firewall’s management interface. Manufacturers often enable all possible avenues of access to ensure ease of installation upon initial deployment. However, you should disable all methods of accessing the management interface, except for the sole secure mechanism selected for use by your organization. Potentially available avenues of access include telnet, encrypted telnet, web, encrypted web, SSH, and other proprietary options. Select one of the secure options and disable the rest. Test access via the disabled methods to ensure that the rules written and the exclusions made actually are working properly.
Also, consider the communication pathways for accessing the management interface. Usually, the physical cable connection port—often labeled as CON for console, TER for terminal, or ADM for administration—cannot be disabled through software. This port is usually a dedicated port used for direct physical connection management and not for any other purpose. A crossover cable or a special console cable (often RS-232 based) is necessary to connect a computer directly to the firewall to gain access to the management interface.
However, most in-network or over-the-network logical access pathways can be disabled. Be sure to disable access to the management interface on every physical network interface or port that faces outward. In other words, the less-secure NIC ports should not support access to the management interface.
If more than one NIC port exists on the secure side, then limit access to only one of those ports. If the firewall is a multifunctional device that also supports wireless connectivity, disable management interface access over a wireless connection. The resulting configuration should allow management interface access only via the physical CON connection and one logical pathway. Disable all other methods of access.
Configure the firewall to record every attempted and successful connection to the management interface into a log file. It might also be a good idea to record all subsequent configuration changes made via the management interface. This log can serve as a component of change documentation and will assist with future troubleshooting, investigations, and reconfiguration.
Finally, periodically verify manually that all settings remain as configured. This is done by viewing the configuration or management interfaces and comparing the live settings to those defined in your documentation. Whenever you discover a discrepancy, investigate and repair it at once.
